| File name: | DSD+2.395 FL_START_FIX_DMR.zip |
| Full analysis: | https://app.any.run/tasks/95e32a38-25cc-47cd-b753-dcad64482528 |
| Verdict: | Malicious activity |
| Analysis date: | August 26, 2024, 05:27:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | F8EE3DCA542028AD3BE2B6E5E6E5D028 |
| SHA1: | F94BEEF75AA05C5FB1C9A53861B788827B380A95 |
| SHA256: | C5A62DAB1105DEEB60685950357FD48E940777F44F41160B3FAD5A7FE6943517 |
| SSDEEP: | 98304:Tnn3naYw4cqvazbV7Mofzqo2mbrlVRx1zxOT05+Qx7rk0eeu2eZTgxjnunIQQHUe:d+GX/Sot/PiAX/K |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 6708)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6708)
Manual execution by a user
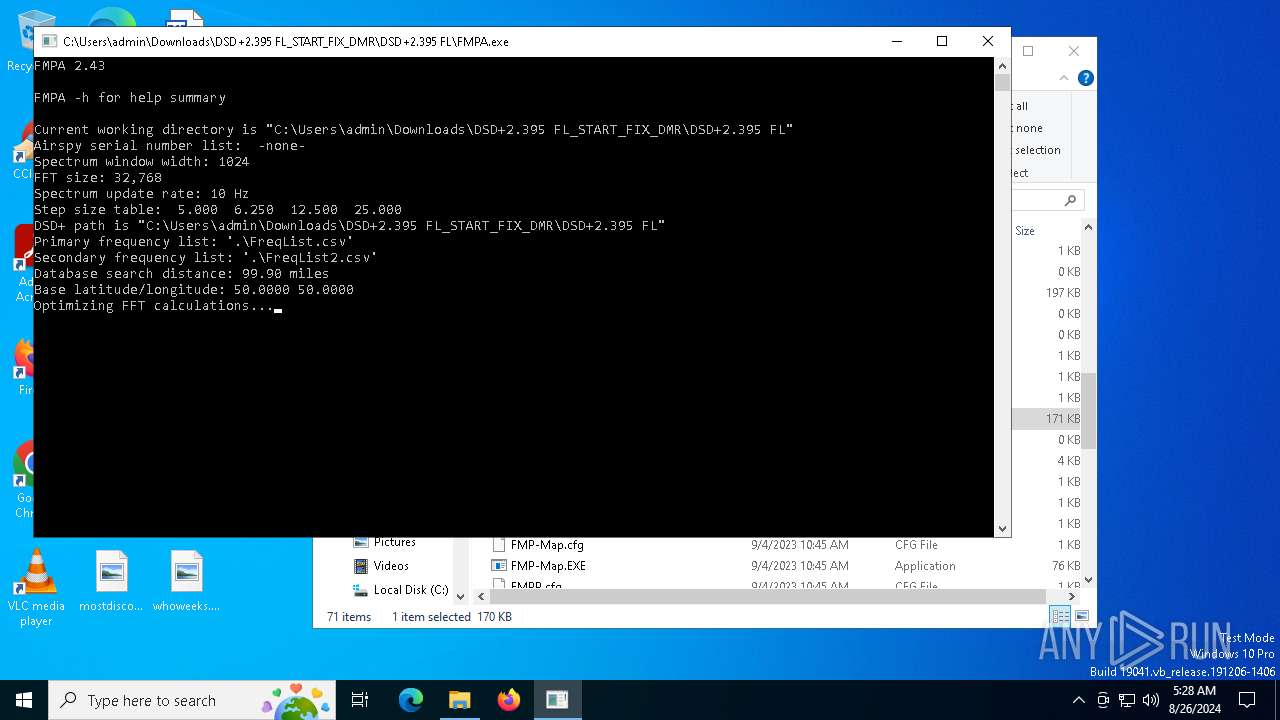
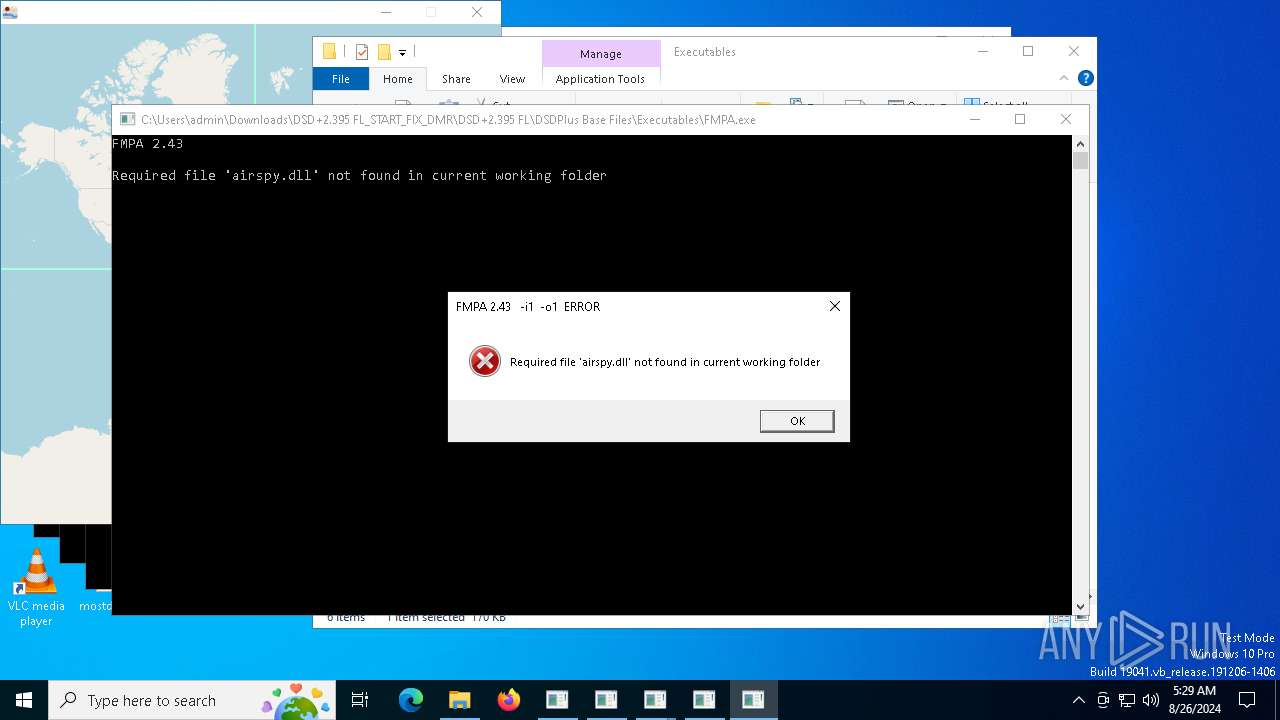
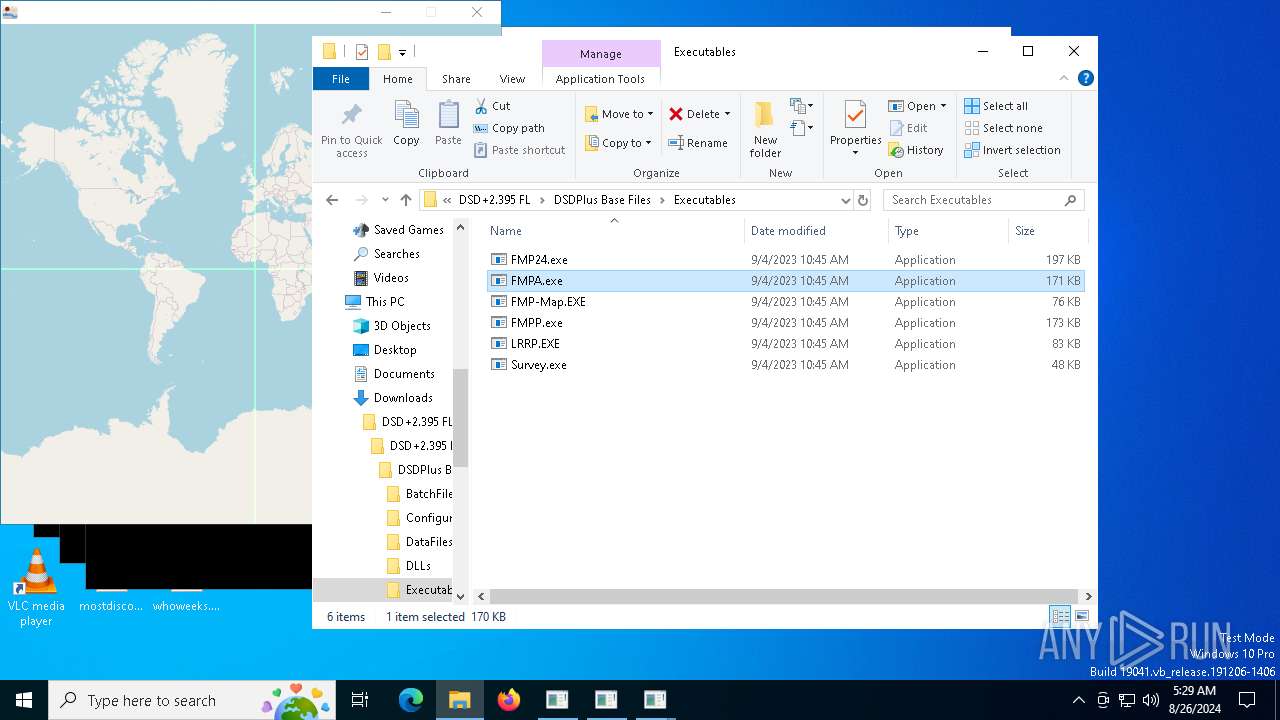
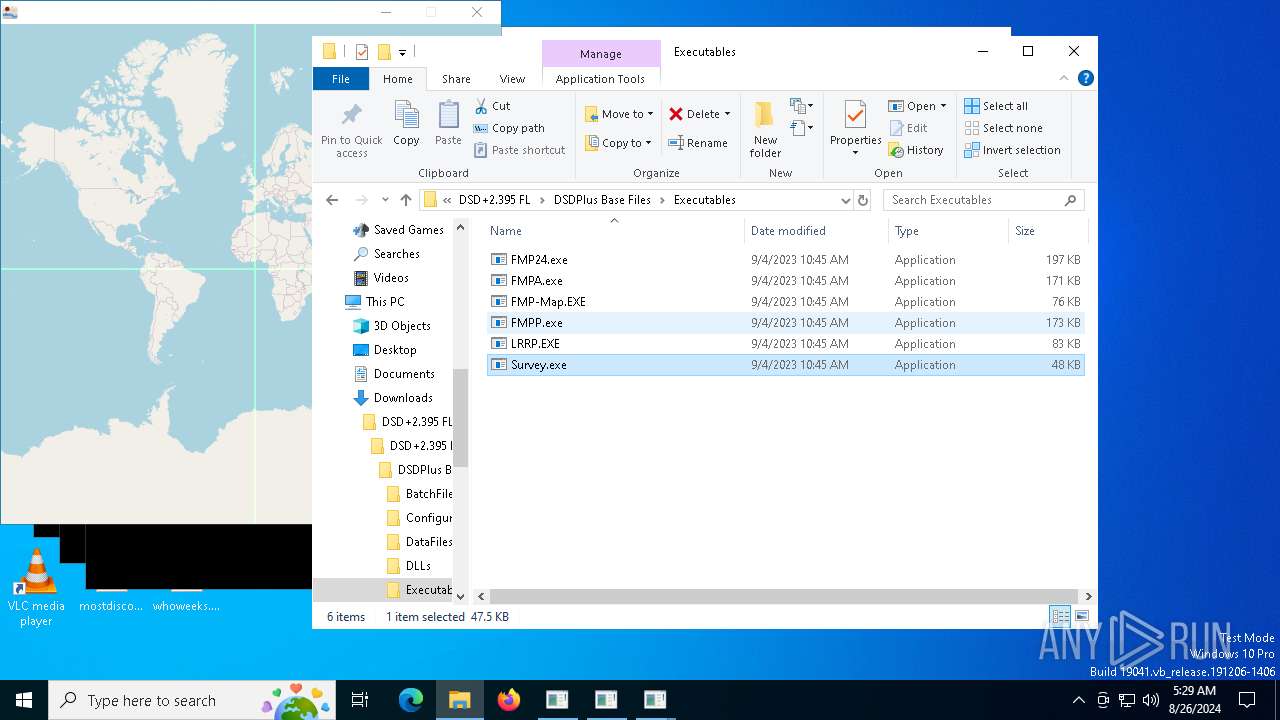
- FMPA.exe (PID: 6220)
- FMP-Map.EXE (PID: 6532)
- FMP24.exe (PID: 6368)
- FMPA.exe (PID: 2092)
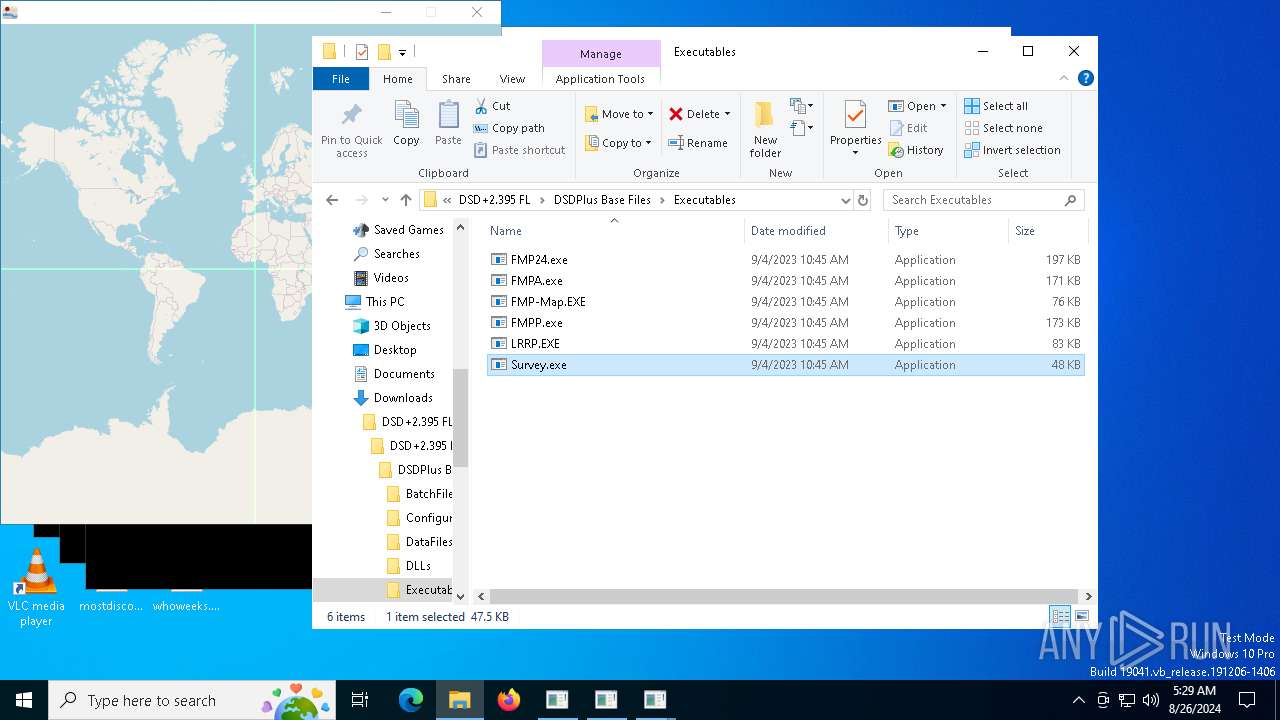
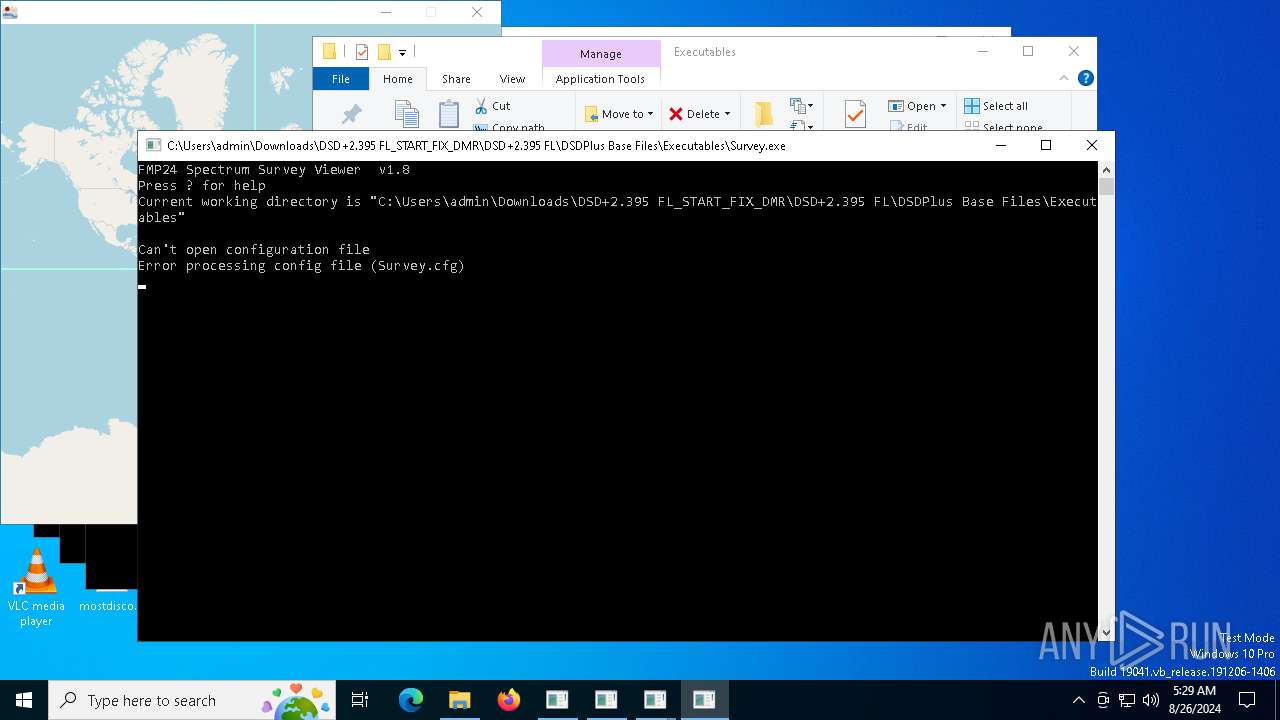
- Survey.exe (PID: 7040)
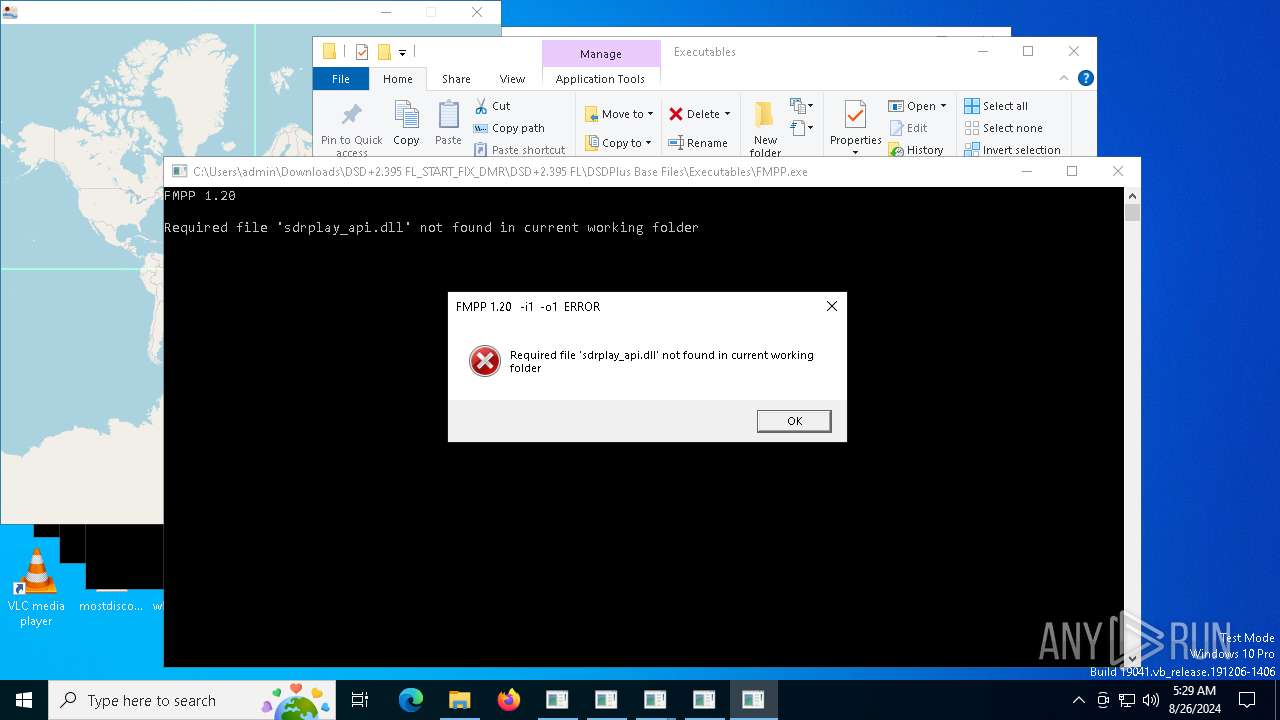
- FMPP.exe (PID: 3236)
Checks supported languages
- FMPA.exe (PID: 6220)
- FMP24.exe (PID: 6368)
- FMP-Map.EXE (PID: 6532)
- Survey.exe (PID: 7040)
- FMPA.exe (PID: 2092)
- FMPP.exe (PID: 3236)
Reads the computer name
- FMP-Map.EXE (PID: 6532)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:09:04 10:45:28 |
| ZipCRC: | 0x6d88006a |
| ZipCompressedSize: | 173 |
| ZipUncompressedSize: | 6148 |
| ZipFileName: | DSD+2.395 FL/.DS_Store |
Total processes
139
Monitored processes
14
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2068 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | FMPP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
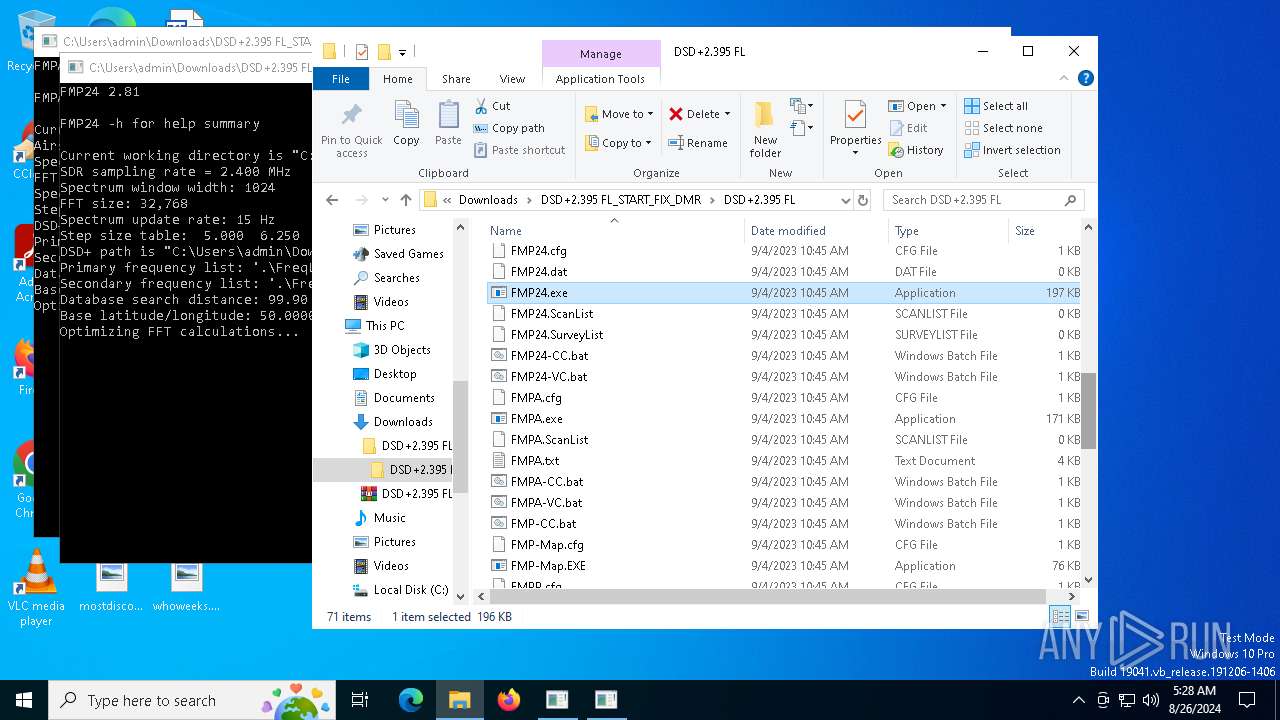
| 2092 | "C:\Users\admin\Downloads\DSD+2.395 FL_START_FIX_DMR\DSD+2.395 FL\DSDPlus Base Files\Executables\FMPA.exe" | C:\Users\admin\Downloads\DSD+2.395 FL_START_FIX_DMR\DSD+2.395 FL\DSDPlus Base Files\Executables\FMPA.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 2524 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | FMPA.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3236 | "C:\Users\admin\Downloads\DSD+2.395 FL_START_FIX_DMR\DSD+2.395 FL\DSDPlus Base Files\Executables\FMPP.exe" | C:\Users\admin\Downloads\DSD+2.395 FL_START_FIX_DMR\DSD+2.395 FL\DSDPlus Base Files\Executables\FMPP.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6220 | "C:\Users\admin\Downloads\DSD+2.395 FL_START_FIX_DMR\DSD+2.395 FL\FMPA.exe" | C:\Users\admin\Downloads\DSD+2.395 FL_START_FIX_DMR\DSD+2.395 FL\FMPA.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6308 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | FMPA.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6364 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | FMP24.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
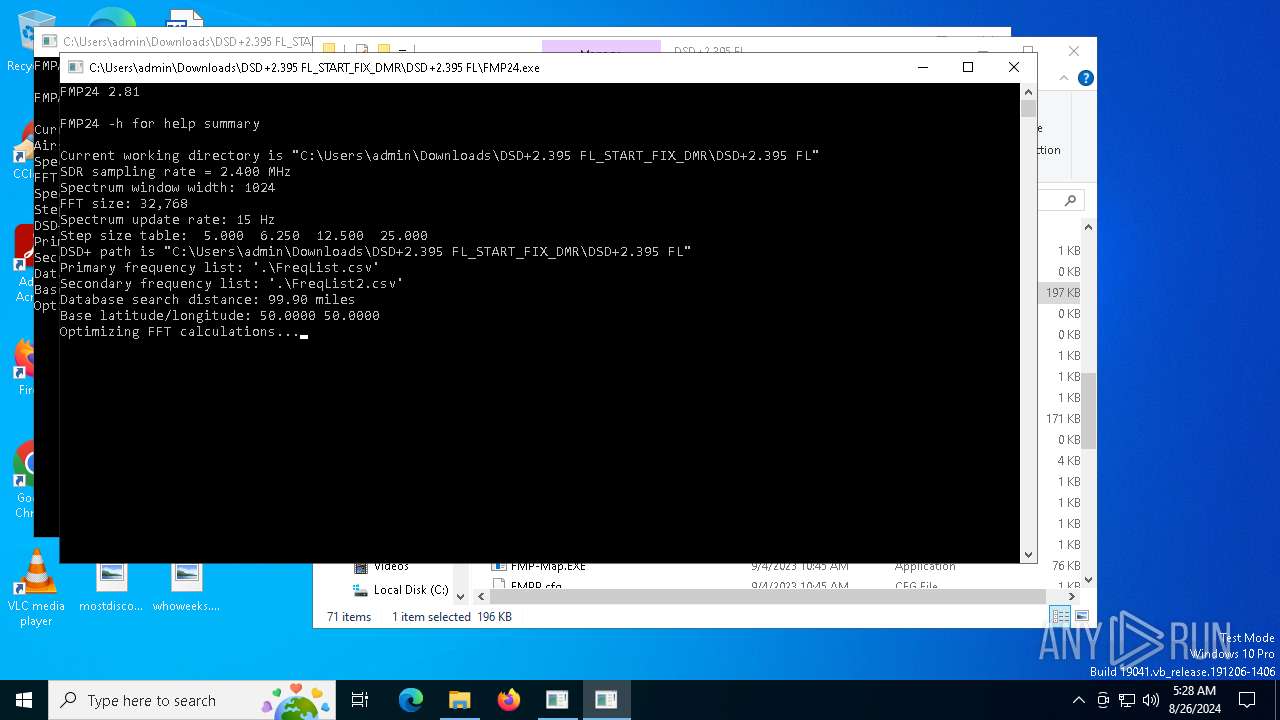
| 6368 | "C:\Users\admin\Downloads\DSD+2.395 FL_START_FIX_DMR\DSD+2.395 FL\FMP24.exe" | C:\Users\admin\Downloads\DSD+2.395 FL_START_FIX_DMR\DSD+2.395 FL\FMP24.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6500 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
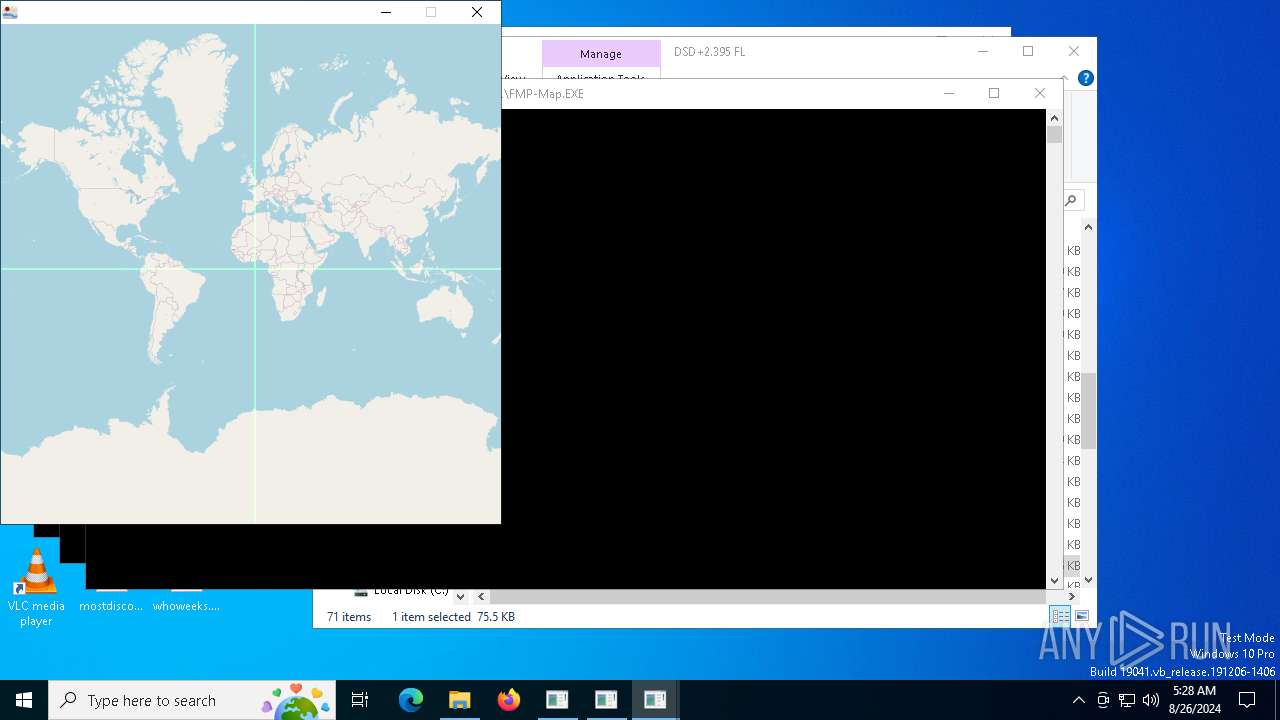
| 6532 | "C:\Users\admin\Downloads\DSD+2.395 FL_START_FIX_DMR\DSD+2.395 FL\FMP-Map.EXE" | C:\Users\admin\Downloads\DSD+2.395 FL_START_FIX_DMR\DSD+2.395 FL\FMP-Map.EXE | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
4 933
Read events
4 913
Write events
20
Delete events
0
Modification events
| (PID) Process: | (6708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\DSD+2.395 FL_START_FIX_DMR.zip | |||
| (PID) Process: | (6708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\DSD+2.395 FL_START_FIX_DMR | |||
| (PID) Process: | (6708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000200000003000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
36
Suspicious files
3
Text files
61
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6708 | WinRAR.exe | C:\Users\admin\Downloads\DSD+2.395 FL_START_FIX_DMR\DSD+2.395 FL\DSDPlus Base Files\BatchFiles\1R.bat | text | |
MD5:C0789B5ACD8A94EC93032BD2C3766253 | SHA256:3891A2F9C0F940D9311271585A8A3C0B8814D58A4A4D0675A408EAC44664FBC5 | |||
| 6708 | WinRAR.exe | C:\Users\admin\Downloads\DSD+2.395 FL_START_FIX_DMR\DSD+2.395 FL\1R.bat | text | |
MD5:C0789B5ACD8A94EC93032BD2C3766253 | SHA256:3891A2F9C0F940D9311271585A8A3C0B8814D58A4A4D0675A408EAC44664FBC5 | |||
| 6708 | WinRAR.exe | C:\Users\admin\Downloads\DSD+2.395 FL_START_FIX_DMR\DSD+2.395 FL\DSDPlus Base Files\BatchFiles\FMP24-CC.bat | text | |
MD5:9E279AE07CCF3155161A4CF51A61A9CD | SHA256:A9D3D79F872E0F88F9B0FCBC0753D5D8F1AE5F07DA9A6E16DFE0EC320CE07EC3 | |||
| 6708 | WinRAR.exe | C:\Users\admin\Downloads\DSD+2.395 FL_START_FIX_DMR\DSD+2.395 FL\DSDPlus Base Files\BatchFiles\CC.bat | text | |
MD5:1C4FF2D70B18D7ACF8B69DB7E7CF90AE | SHA256:88F987BC13B8CE4A98760CB7007FAFF001604BB628EECFE1818DE06BF100874A | |||
| 6708 | WinRAR.exe | C:\Users\admin\Downloads\DSD+2.395 FL_START_FIX_DMR\DSD+2.395 FL\DSDPlus Base Files\BatchFiles\FMPP-CC.bat | text | |
MD5:CEE6FDF079A8153313070D8095AE5EF0 | SHA256:EDA3D418971ED4D3AF7EDB8B6836235277E1771868F2BC97F8863C44F54BB017 | |||
| 6708 | WinRAR.exe | C:\Users\admin\Downloads\DSD+2.395 FL_START_FIX_DMR\DSD+2.395 FL\DSDPlus Base Files\BatchFiles\FMPA-CC.bat | text | |
MD5:A307F39B461D0556306699D5700DD9F0 | SHA256:4881DA6FA378EE55AEF3DB79A95A0B156307E95B59151004449D85584871934E | |||
| 6708 | WinRAR.exe | C:\Users\admin\Downloads\DSD+2.395 FL_START_FIX_DMR\DSD+2.395 FL\DSDPlus Base Files\ConfigurationFiles\FMP24.cfg | text | |
MD5:6DCA47D53C7FAABF14AE5ACC07C9FA90 | SHA256:D72FD86AE1F1B55CA6DF5CFE98A72367B250DBF2E92CA7CDD40912F6EF975ED0 | |||
| 6708 | WinRAR.exe | C:\Users\admin\Downloads\DSD+2.395 FL_START_FIX_DMR\DSD+2.395 FL\DSDPlus Base Files\ConfigurationFiles\FMPP.cfg | text | |
MD5:B9558ABF67D2E8880E224FE3B7395386 | SHA256:BD507B640DA72320ABD14A76D8A89EDA8D50F6BF7CFBB3E4278A479C33CC99D1 | |||
| 6708 | WinRAR.exe | C:\Users\admin\Downloads\DSD+2.395 FL_START_FIX_DMR\DSD+2.395 FL\DSDPlus Base Files\BatchFiles\FMPP-VC.bat | text | |
MD5:91A338B30B2F6FACDFFA28F834627E62 | SHA256:1F3B896ABBDD205198112332E890E910CC480DD269C4241D5FA5E79D9C526708 | |||
| 6708 | WinRAR.exe | C:\Users\admin\Downloads\DSD+2.395 FL_START_FIX_DMR\DSD+2.395 FL\DMRFL.bat | text | |
MD5:9FC907D0AAB30614F3BE7858AB142237 | SHA256:C23785F4B5EC1CC339686EA100ED4B98E4898B10D5EF0E6EC7CEE1356E0E09C7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
25
DNS requests
15
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6620 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6532 | FMP-Map.EXE | GET | 200 | 151.101.65.91:80 | http://tile.openstreetmap.org/1/0/1.png | unknown | — | — | whitelisted |
6532 | FMP-Map.EXE | GET | 200 | 151.101.65.91:80 | http://tile.openstreetmap.org/1/1/0.png | unknown | — | — | whitelisted |
6532 | FMP-Map.EXE | GET | 200 | 151.101.65.91:80 | http://tile.openstreetmap.org/1/0/0.png | unknown | — | — | whitelisted |
6532 | FMP-Map.EXE | GET | 200 | 151.101.65.91:80 | http://tile.openstreetmap.org/1/1/1.png | unknown | — | — | whitelisted |
5904 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6620 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3992 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
1492 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3992 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6620 | SIHClient.exe | 20.12.23.50:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
6620 | SIHClient.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
tile.openstreetmap.org |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6532 | FMP-Map.EXE | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
6532 | FMP-Map.EXE | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
6532 | FMP-Map.EXE | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
6532 | FMP-Map.EXE | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |