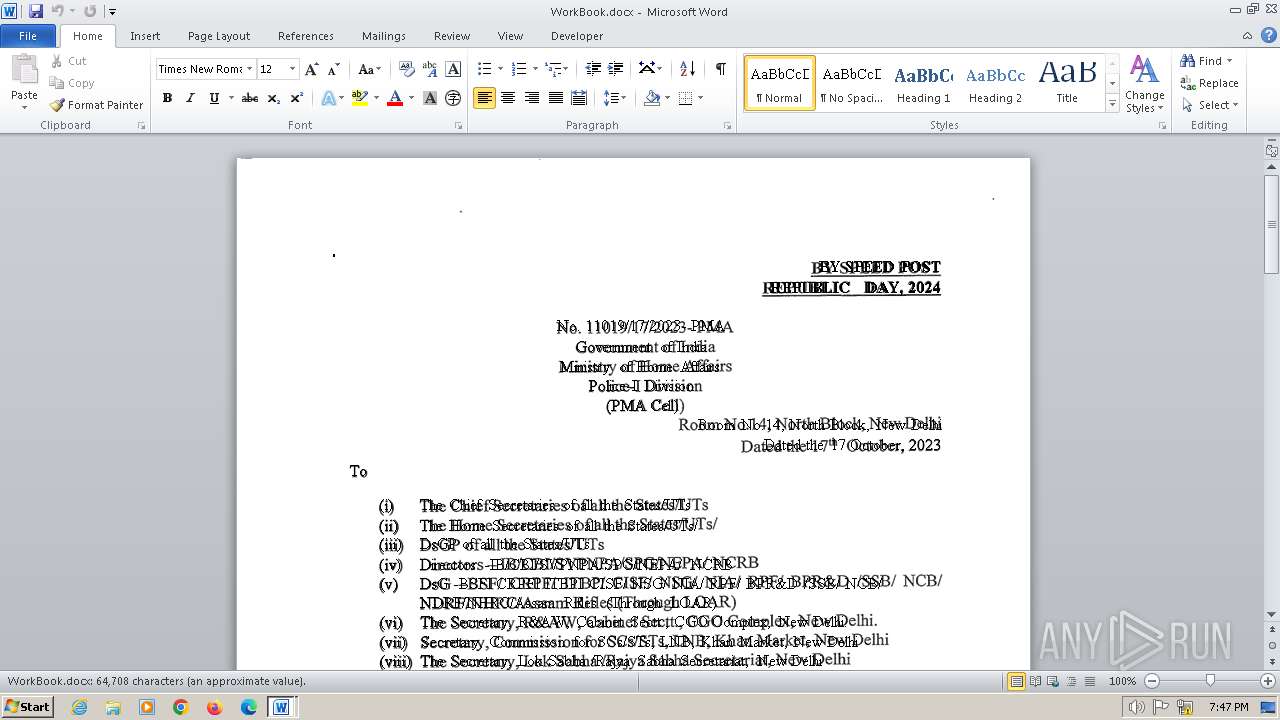
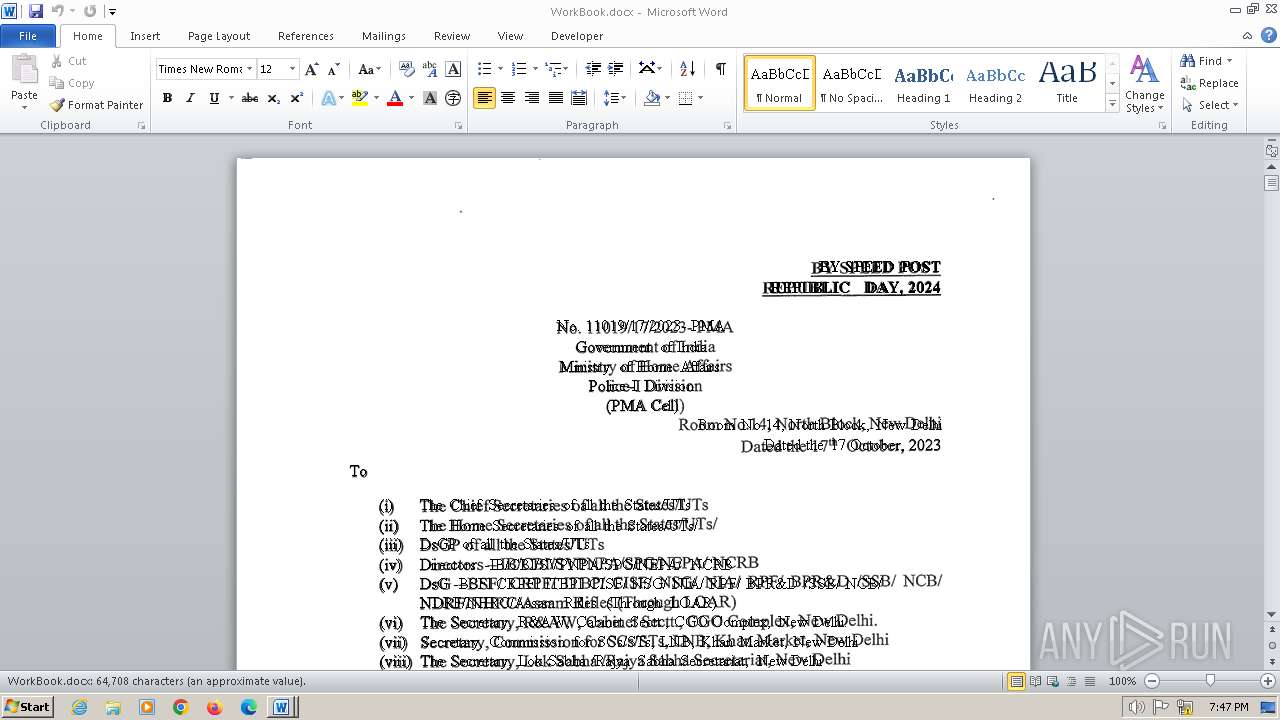
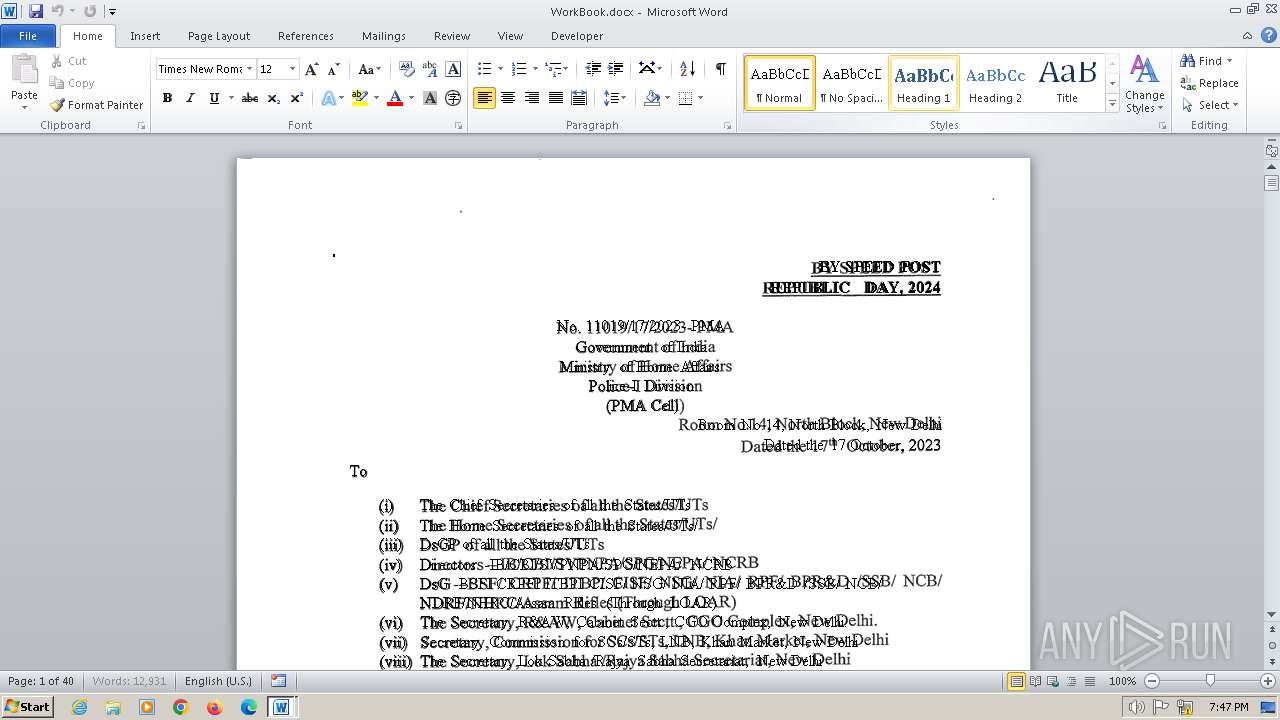
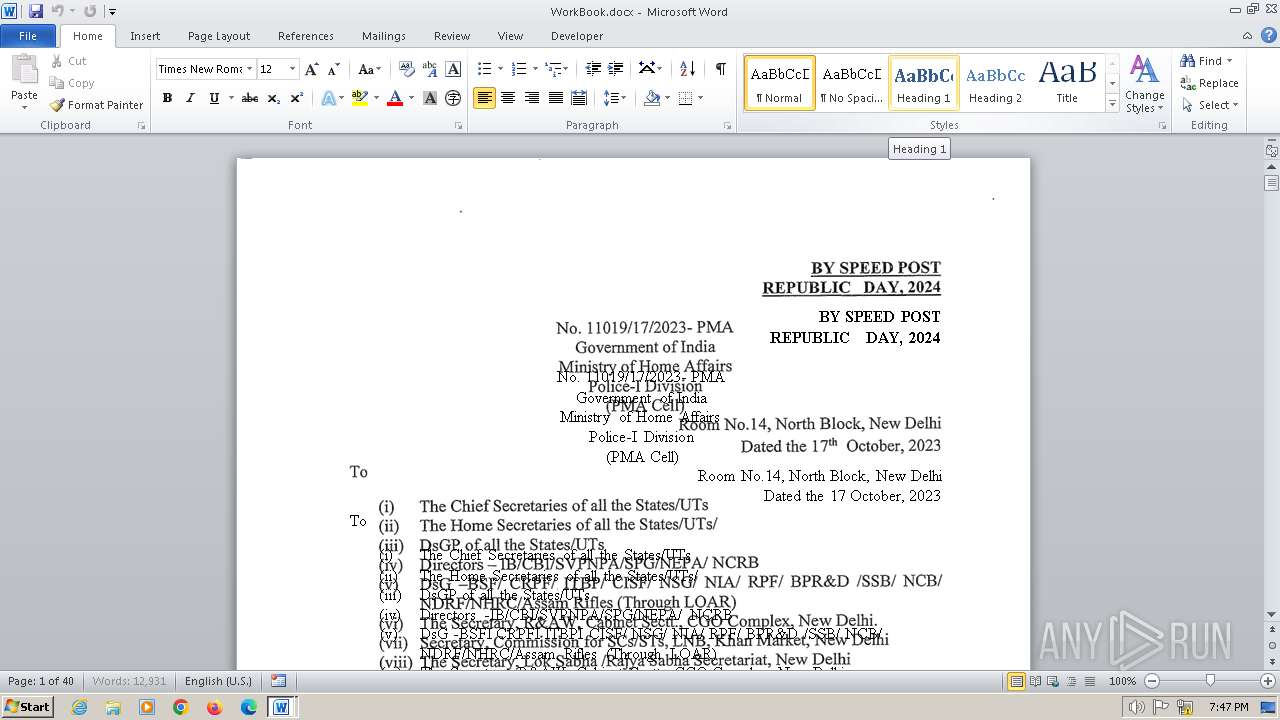
| File name: | c59b2d6a70bc5b84998aebb2d21241a8adef33724838e92db4dee36a1ce46f43.docm |
| Full analysis: | https://app.any.run/tasks/9fa84d36-225a-4900-ab44-a46ffb89c7be |
| Verdict: | Malicious activity |
| Analysis date: | February 02, 2024, 19:46:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | Microsoft OOXML |
| MD5: | A21C2B37EFFE3195665EC5597AFA329F |
| SHA1: | D764529D82A015204D9AB3FE414C0DA5B9829D9A |
| SHA256: | C59B2D6A70BC5B84998AEBB2D21241A8ADEF33724838E92DB4DEE36A1CE46F43 |
| SSDEEP: | 98304:mALh1ZKr/imh4llXwwv3NeSFiusq2b6HeW71Mry8QacL4mPS0K7X4bJ/cG7gjwRg:ourRc1wI3CJpbhYXHJzL9tF/rDyW |
MALICIOUS
Copies file to a new location (SCRIPT)
- WINWORD.EXE (PID: 580)
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 580)
Unusual execution from MS Office
- WINWORD.EXE (PID: 580)
SUSPICIOUS
Runs shell command (SCRIPT)
- WINWORD.EXE (PID: 580)
Connects to unusual port
- itmvroidovss.scr (PID: 2528)
Creates a Folder object (SCRIPT)
- WINWORD.EXE (PID: 580)
Creates FileSystem object to access computer's file system (SCRIPT)
- WINWORD.EXE (PID: 580)
Starts application with an unusual extension
- WINWORD.EXE (PID: 580)
INFO
Reads the machine GUID from the registry
- itmvroidovss.scr (PID: 2528)
Reads the computer name
- itmvroidovss.scr (PID: 2528)
Drops the executable file immediately after the start
- WINWORD.EXE (PID: 580)
Checks supported languages
- itmvroidovss.scr (PID: 2528)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docm | | | Word Microsoft Office Open XML Format document (with Macro) (53.6) |
|---|---|---|
| .docx | | | Word Microsoft Office Open XML Format document (24.2) |
| .zip | | | Open Packaging Conventions container (18) |
| .zip | | | ZIP compressed archive (4.1) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x840a1a99 |
| ZipCompressedSize: | 392 |
| ZipUncompressedSize: | 1503 |
| ZipFileName: | [Content_Types].xml |
Total processes
35
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 580 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\c59b2d6a70bc5b84998aebb2d21241a8adef33724838e92db4dee36a1ce46f43.docm" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.5123.5000 Modules
| |||||||||||||||
| 2528 | "C:\Users\admin\Downloads\itmvroidovss.scr" " | C:\Users\admin\Downloads\itmvroidovss.scr | WINWORD.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Description: itmvroidovs Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
4 887
Read events
4 437
Write events
320
Delete events
130
Modification events
| (PID) Process: | (580) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (580) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (580) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: On | |||
| (PID) Process: | (580) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (580) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (580) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (580) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: On | |||
| (PID) Process: | (580) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: On | |||
| (PID) Process: | (580) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: On | |||
| (PID) Process: | (580) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: On | |||
Executable files
2
Suspicious files
15
Text files
15
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 580 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRAB08.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 580 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\18194088.png | compressed | |
MD5:73A02AF0CC8DC6A65C9902DE4D1B9CCE | SHA256:3AF6C684044A42426FF2726F2C35521773CE2C934290D4724C250F3A526DB60B | |||
| 580 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$9b2d6a70bc5b84998aebb2d21241a8adef33724838e92db4dee36a1ce46f43.docm | binary | |
MD5:B18E2F4E074B409BCD48B0D1FD50C82B | SHA256:0FEFEE7CE78E86E4BDF851C89BFA5A862FEC4D87405AF4FB9274C9D25FDD712E | |||
| 580 | WINWORD.EXE | C:\Users\admin\DOWNLO~1\191747\[Content_Types].xml | xml | |
MD5:5E069572B5A97282537BD790AC465A8A | SHA256:B4FA7F3FAA0510E4D969219BCEEC2A90E8A48FF28E060DB3CDD37CE935C3779C | |||
| 580 | WINWORD.EXE | C:\Users\admin\DOWNLO~1\191747\docProps\app.xml | xml | |
MD5:FC87C54680C80131E5636CA5C70D7906 | SHA256:1FF3154741F92AD924A3726D19E4D91482F8074DC9391E8C8882EBC80866203C | |||
| 580 | WINWORD.EXE | C:\Users\admin\DOWNLO~1\191747\docProps\core.xml | xml | |
MD5:7035900313427FBA18E2ADDB06819FE0 | SHA256:6E0494C4AC7F919D572BCE10AF5697021EBB1EBD39722CA6C39359D42905B781 | |||
| 580 | WINWORD.EXE | C:\Users\admin\DOWNLO~1\191747\word\settings.xml | xml | |
MD5:BE2514DAE096DB0EAE3E6F4368221FA0 | SHA256:A2A430292883D152B1B4C22DA289A821DB384ECDF5872569E8209BD62DA3FD94 | |||
| 580 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\964676E9.png | document | |
MD5:9A50DE0872CCC2D8B02CAA12C6DD8686 | SHA256:669C94E48032E28E29C764631AD8B7DD3E5CE22D194EBA42CB4C1CD60BE6D0B3 | |||
| 580 | WINWORD.EXE | C:\Users\admin\DOWNLO~1\191747\word\fontTable.xml | xml | |
MD5:F4CB870760851B85F695DE0D4BFD6B62 | SHA256:2C06B19CA63F1FBC4B62022D111C44315FF181C2E99CB7D52C63BFD752897598 | |||
| 580 | WINWORD.EXE | C:\Users\admin\DOWNLO~1\191747\word\webSettings.xml | xml | |
MD5:15065D2DE3EDDBB09D84337A09FD7985 | SHA256:CBC26FA167E8052D5DDFB37BD843233F1E61843CCE11C730CA50B27AFC60CF93 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
6
DNS requests
1
Threats
2
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
352 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1220 | svchost.exe | 239.255.255.250:3702 | — | — | — | unknown |
2528 | itmvroidovss.scr | 164.68.122.64:11128 | mus09.duckdns.org | Contabo GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
mus09.duckdns.org |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
352 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
352 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |