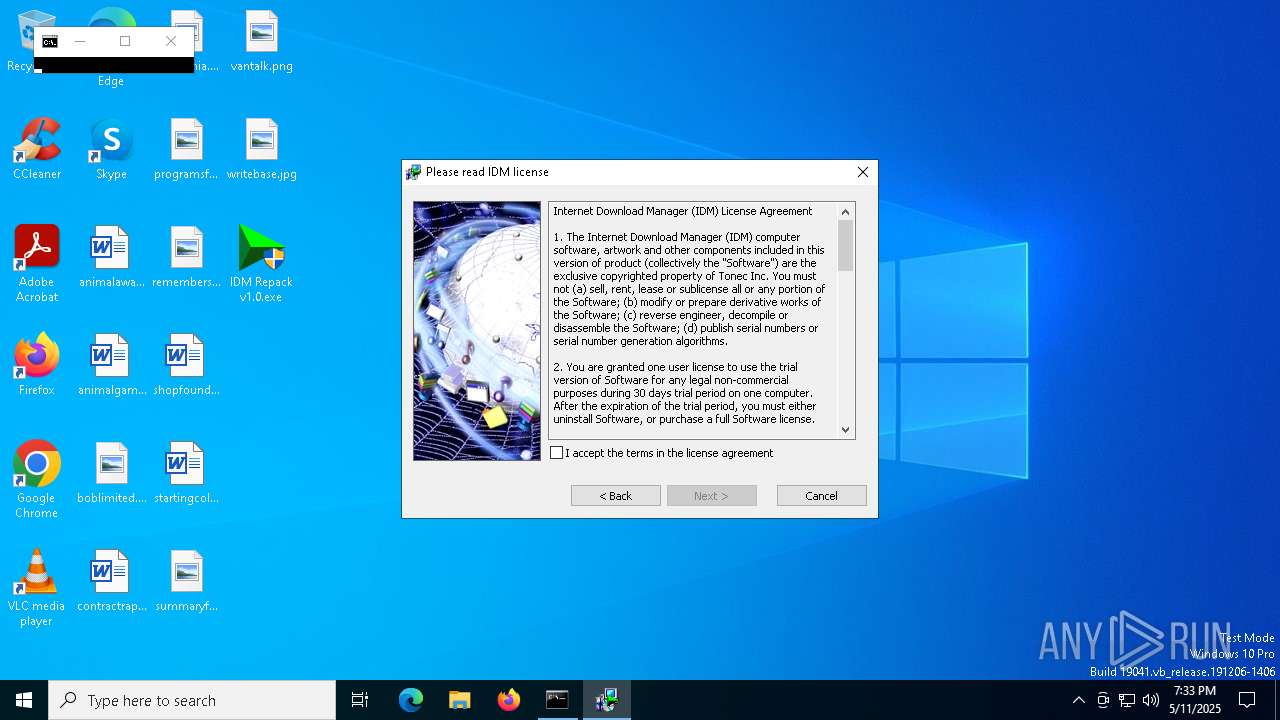
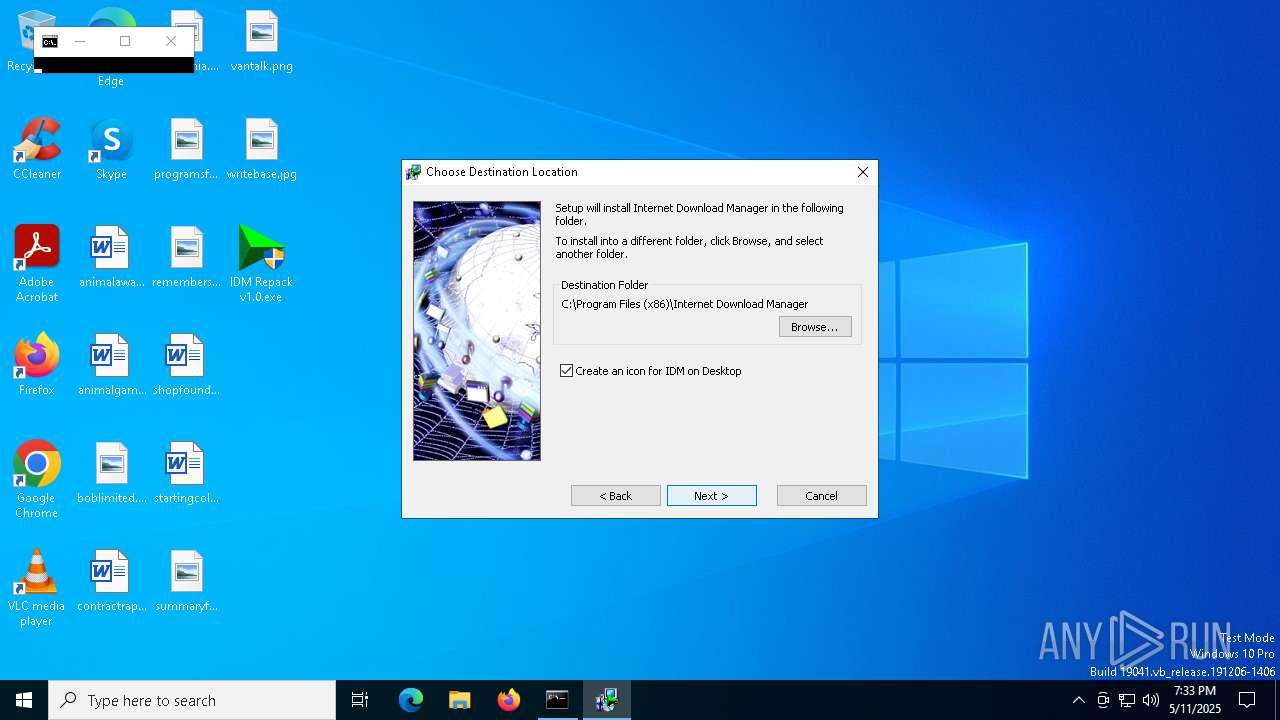
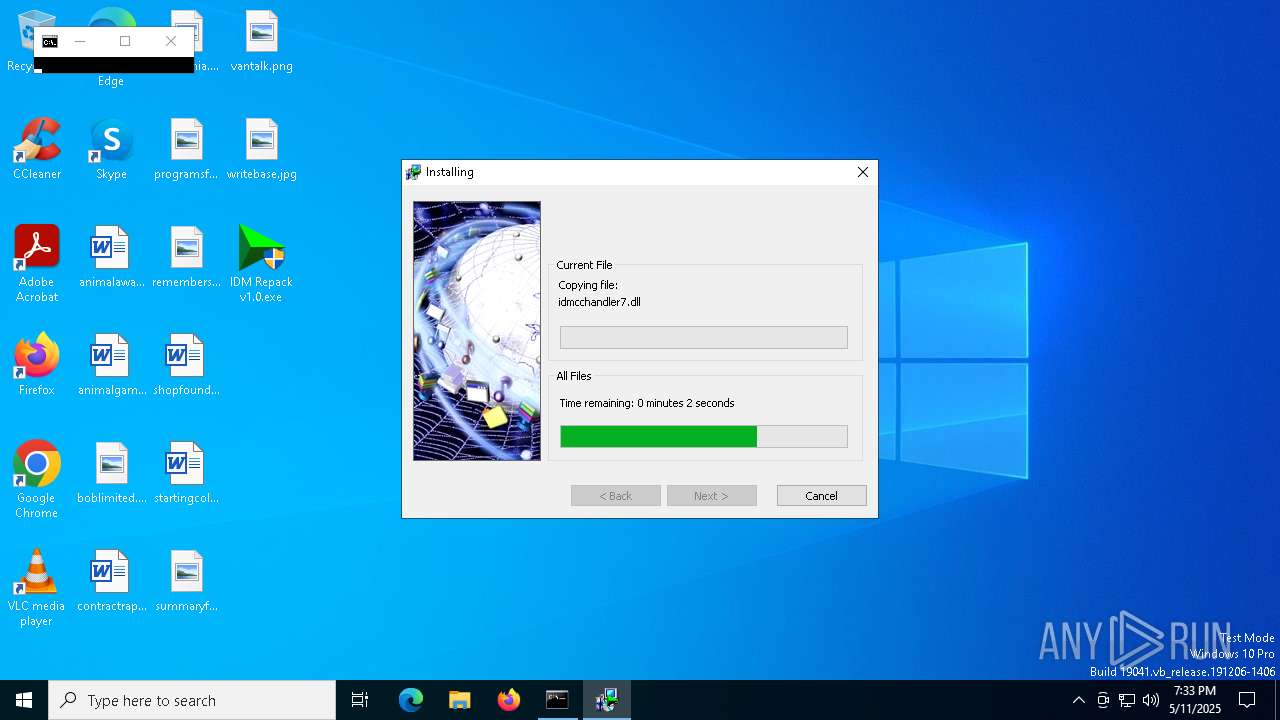
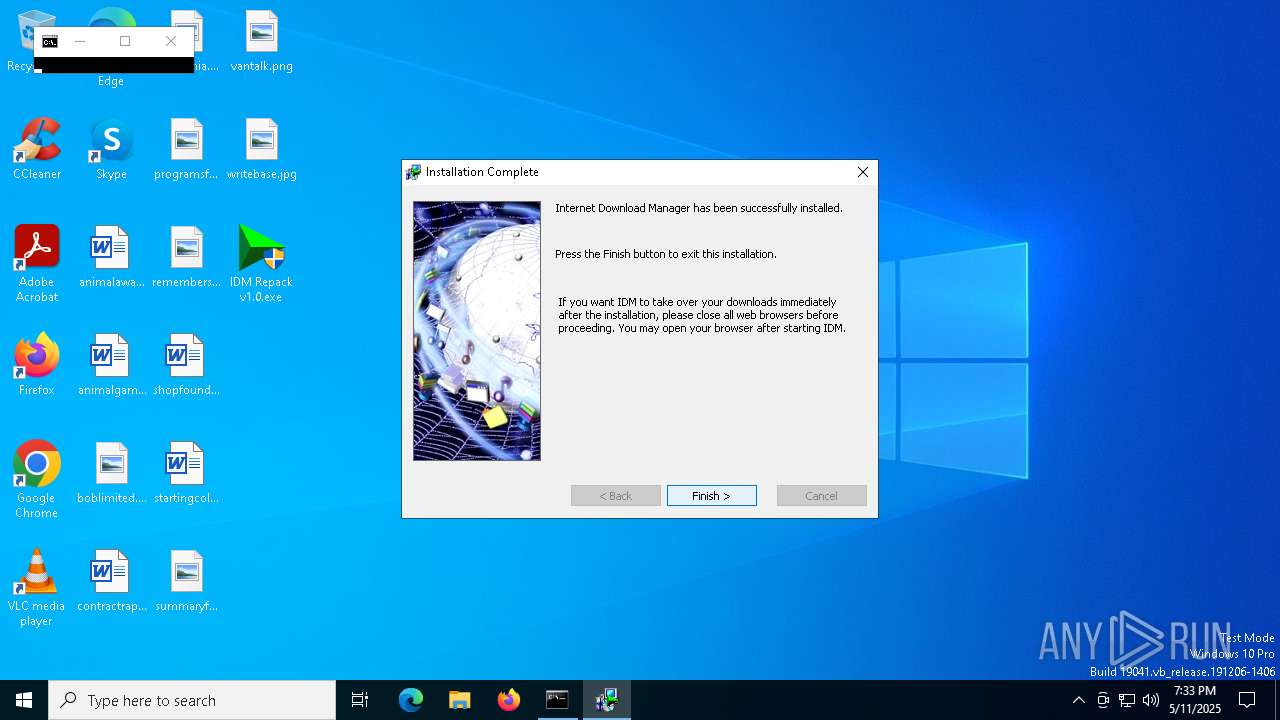
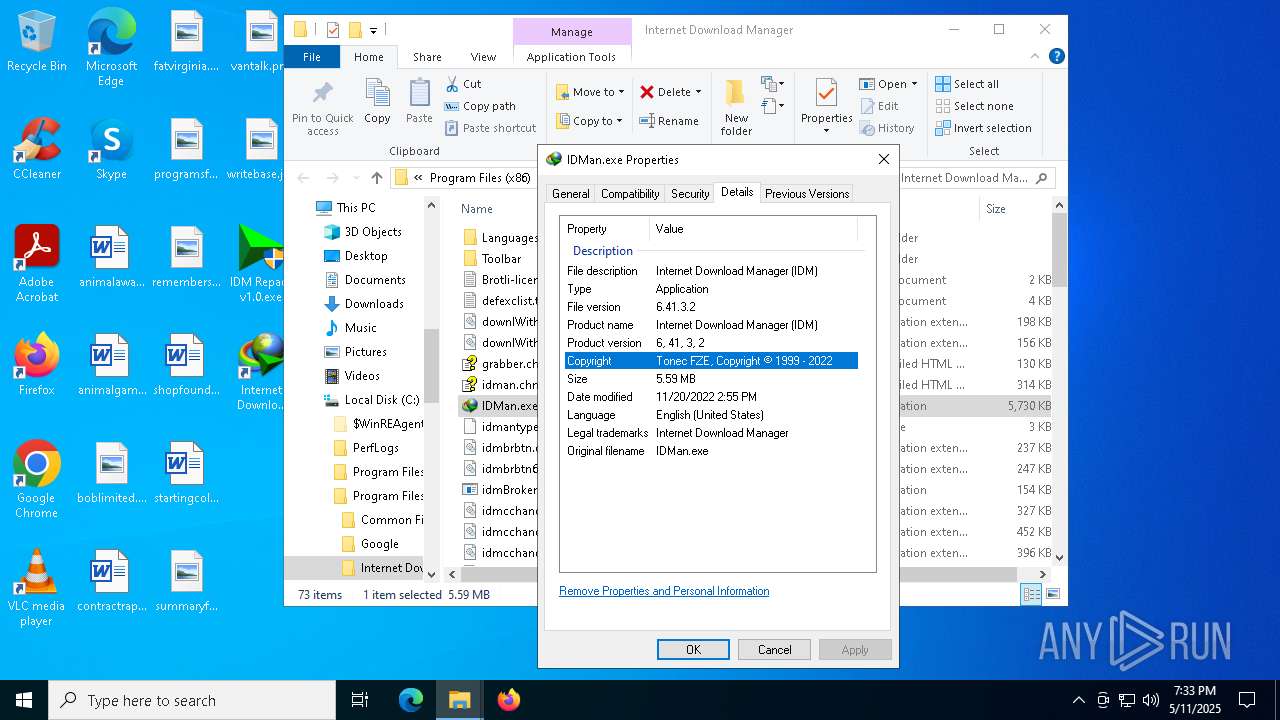
| File name: | IDM Repack v1.0.exe |
| Full analysis: | https://app.any.run/tasks/2d926dde-cf56-4dde-a531-b67ba5dce0e2 |
| Verdict: | Malicious activity |
| Analysis date: | May 11, 2025, 19:32:46 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 4E8F5DC1770A28A5B2C30B7DA438E094 |
| SHA1: | 96B52EDE8579347E487834DDF06110DFC43C9428 |
| SHA256: | C587385AE00D9F600B649869F9C1E2D27771A66AD2B46D3DCB59F54C0AC37FF2 |
| SSDEEP: | 196608:Pf5Vnx92BZeXJlFT69u7PKikdRa4dJkoxX:PfDx9209JzKikZ8EX |
MALICIOUS
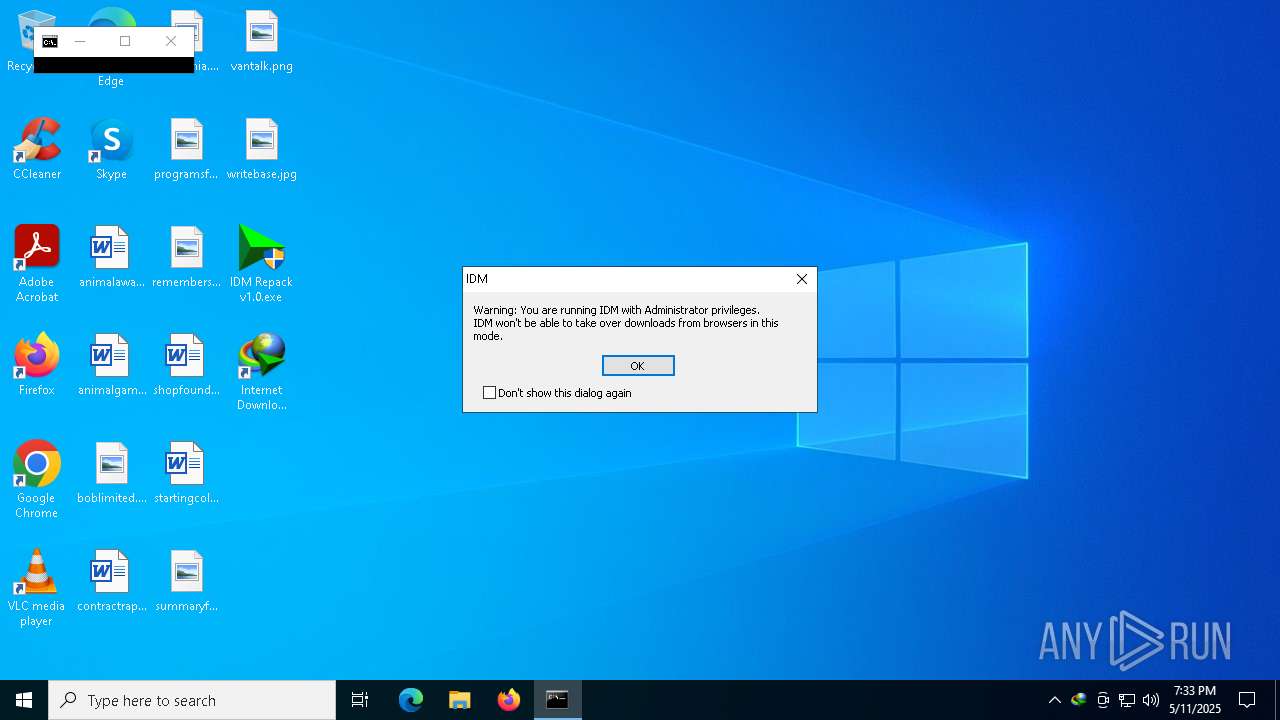
Executing a file with an untrusted certificate
- pslist.exe (PID: 7792)
- pslist.exe (PID: 7844)
- pslist.exe (PID: 7928)
- pslist.exe (PID: 7952)
- pslist.exe (PID: 7980)
- pslist.exe (PID: 8004)
- pslist.exe (PID: 8028)
- pslist.exe (PID: 8084)
- pslist.exe (PID: 8112)
- pslist.exe (PID: 8060)
- pslist.exe (PID: 8136)
- pslist.exe (PID: 8160)
- pslist.exe (PID: 8184)
- pslist.exe (PID: 7212)
- pslist.exe (PID: 7188)
- pslist.exe (PID: 5332)
- pslist.exe (PID: 616)
- pslist.exe (PID: 7300)
- pslist.exe (PID: 7336)
- pslist.exe (PID: 5072)
- pslist.exe (PID: 7236)
- pslist.exe (PID: 2284)
- pslist.exe (PID: 7484)
- pslist.exe (PID: 7392)
- pslist.exe (PID: 7364)
- pslist.exe (PID: 3884)
- pslist.exe (PID: 1812)
- pslist.exe (PID: 7176)
- pslist.exe (PID: 1324)
- pslist.exe (PID: 920)
- pslist.exe (PID: 5244)
- pslist.exe (PID: 2088)
- pslist.exe (PID: 7572)
- pslist.exe (PID: 7836)
- pslist.exe (PID: 7624)
- pslist.exe (PID: 7828)
- pslist.exe (PID: 7904)
- pslist.exe (PID: 7796)
- pslist.exe (PID: 7860)
- pslist.exe (PID: 4000)
- pslist.exe (PID: 7740)
- pslist.exe (PID: 7928)
- pslist.exe (PID: 7916)
- pslist.exe (PID: 8100)
- pslist.exe (PID: 8124)
- pslist.exe (PID: 8148)
- pslist.exe (PID: 7952)
- pslist.exe (PID: 7980)
- pslist.exe (PID: 632)
- pslist.exe (PID: 8172)
- pslist.exe (PID: 536)
- pslist.exe (PID: 7188)
Registers / Runs the DLL via REGSVR32.EXE
- IDMan.exe (PID: 7316)
- IDMan.exe (PID: 5156)
- IDM1.tmp (PID: 7812)
- Uninstall.exe (PID: 7740)
Starts NET.EXE for service management
- Uninstall.exe (PID: 7740)
- net.exe (PID: 7992)
SUSPICIOUS
Executing commands from a ".bat" file
- IDM Repack v1.0.exe (PID: 7512)
Starts CMD.EXE for commands execution
- IDM Repack v1.0.exe (PID: 7512)
Executable content was dropped or overwritten
- IDM Repack v1.0.exe (PID: 7512)
- cmd.exe (PID: 7560)
- IDMan.exe (PID: 5156)
- rundll32.exe (PID: 7836)
The executable file from the user directory is run by the CMD process
- pslist.exe (PID: 7648)
- idmsetup.exe (PID: 7744)
- pslist.exe (PID: 7752)
- pslist.exe (PID: 7792)
- pslist.exe (PID: 7844)
- pslist.exe (PID: 7888)
- pslist.exe (PID: 7952)
- pslist.exe (PID: 7980)
- pslist.exe (PID: 8004)
- pslist.exe (PID: 7928)
- pslist.exe (PID: 8028)
- pslist.exe (PID: 8060)
- pslist.exe (PID: 8112)
- pslist.exe (PID: 8084)
- pslist.exe (PID: 8160)
- pslist.exe (PID: 8136)
- pslist.exe (PID: 8184)
- pslist.exe (PID: 7188)
- pslist.exe (PID: 5332)
- pslist.exe (PID: 616)
- pslist.exe (PID: 7212)
- pslist.exe (PID: 7300)
- pslist.exe (PID: 7336)
- pslist.exe (PID: 7236)
- pslist.exe (PID: 5072)
- pslist.exe (PID: 2284)
- pslist.exe (PID: 7484)
- pslist.exe (PID: 7392)
- pslist.exe (PID: 7364)
- pslist.exe (PID: 3884)
- pslist.exe (PID: 1812)
- pslist.exe (PID: 7176)
- pslist.exe (PID: 920)
- pslist.exe (PID: 5244)
- pslist.exe (PID: 2088)
- pslist.exe (PID: 1324)
- pslist.exe (PID: 7572)
- pslist.exe (PID: 7624)
- pslist.exe (PID: 7740)
- pslist.exe (PID: 7836)
- pslist.exe (PID: 7828)
- pslist.exe (PID: 7796)
- pslist.exe (PID: 7860)
- pslist.exe (PID: 7904)
- pslist.exe (PID: 4000)
- pslist.exe (PID: 7928)
- pslist.exe (PID: 7952)
- pslist.exe (PID: 8100)
- pslist.exe (PID: 7916)
- pslist.exe (PID: 8172)
- pslist.exe (PID: 8124)
- pslist.exe (PID: 7980)
- pslist.exe (PID: 8148)
- pslist.exe (PID: 536)
- pslist.exe (PID: 7188)
- pslist.exe (PID: 632)
The process checks if it is being run in the virtual environment
- pslist.exe (PID: 7648)
- pslist.exe (PID: 7792)
- pslist.exe (PID: 7844)
- pslist.exe (PID: 7752)
- pslist.exe (PID: 7952)
- pslist.exe (PID: 7980)
- pslist.exe (PID: 8060)
- pslist.exe (PID: 8028)
- pslist.exe (PID: 8084)
- pslist.exe (PID: 8004)
- pslist.exe (PID: 8112)
- pslist.exe (PID: 8136)
- pslist.exe (PID: 8160)
- pslist.exe (PID: 8184)
- pslist.exe (PID: 7188)
- pslist.exe (PID: 5332)
- pslist.exe (PID: 616)
- pslist.exe (PID: 7212)
- pslist.exe (PID: 7300)
- pslist.exe (PID: 7336)
- pslist.exe (PID: 7236)
- pslist.exe (PID: 5072)
- pslist.exe (PID: 7364)
- pslist.exe (PID: 7484)
- pslist.exe (PID: 7392)
- pslist.exe (PID: 2284)
- pslist.exe (PID: 3884)
- pslist.exe (PID: 1812)
- pslist.exe (PID: 7176)
- pslist.exe (PID: 2088)
- pslist.exe (PID: 1324)
- pslist.exe (PID: 920)
- pslist.exe (PID: 5244)
Starts application with an unusual extension
- idmsetup.exe (PID: 7744)
There is functionality for taking screenshot (YARA)
- IDM Repack v1.0.exe (PID: 7512)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 7560)
Uses RUNDLL32.EXE to load library
- Uninstall.exe (PID: 7740)
Drops a system driver (possible attempt to evade defenses)
- rundll32.exe (PID: 7836)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7560)
INFO
The sample compiled with english language support
- IDM Repack v1.0.exe (PID: 7512)
- IDMan.exe (PID: 5156)
- rundll32.exe (PID: 7836)
- cmd.exe (PID: 7560)
Create files in a temporary directory
- IDM Repack v1.0.exe (PID: 7512)
- IDM1.tmp (PID: 7812)
- idmsetup.exe (PID: 7744)
The sample compiled with russian language support
- IDM Repack v1.0.exe (PID: 7512)
Checks supported languages
- IDM Repack v1.0.exe (PID: 7512)
- mode.com (PID: 7624)
- pslist.exe (PID: 7648)
- idmsetup.exe (PID: 7744)
- pslist.exe (PID: 7752)
- pslist.exe (PID: 7792)
- IDM1.tmp (PID: 7812)
- pslist.exe (PID: 7844)
- pslist.exe (PID: 7928)
- pslist.exe (PID: 7952)
- pslist.exe (PID: 7980)
- pslist.exe (PID: 7888)
- pslist.exe (PID: 8060)
- pslist.exe (PID: 8028)
- pslist.exe (PID: 8084)
- pslist.exe (PID: 8004)
- pslist.exe (PID: 8136)
- pslist.exe (PID: 8112)
- pslist.exe (PID: 8160)
- pslist.exe (PID: 8184)
- pslist.exe (PID: 7188)
- pslist.exe (PID: 7212)
- pslist.exe (PID: 5332)
- pslist.exe (PID: 7300)
- pslist.exe (PID: 616)
- pslist.exe (PID: 7336)
- pslist.exe (PID: 7236)
- pslist.exe (PID: 5072)
- pslist.exe (PID: 7364)
- pslist.exe (PID: 7484)
- pslist.exe (PID: 7392)
- pslist.exe (PID: 2284)
- pslist.exe (PID: 3884)
- pslist.exe (PID: 1812)
- pslist.exe (PID: 7176)
- pslist.exe (PID: 920)
- pslist.exe (PID: 5244)
- pslist.exe (PID: 2088)
- pslist.exe (PID: 1324)
- pslist.exe (PID: 7572)
Starts MODE.COM to configure console settings
- mode.com (PID: 7624)
Reads the computer name
- pslist.exe (PID: 7648)
- pslist.exe (PID: 7752)
- idmsetup.exe (PID: 7744)
- pslist.exe (PID: 7792)
- IDM1.tmp (PID: 7812)
- pslist.exe (PID: 7844)
- pslist.exe (PID: 7928)
- pslist.exe (PID: 7952)
- pslist.exe (PID: 7980)
- pslist.exe (PID: 7888)
- pslist.exe (PID: 8028)
- pslist.exe (PID: 8060)
- pslist.exe (PID: 8084)
- pslist.exe (PID: 8004)
- pslist.exe (PID: 8112)
- pslist.exe (PID: 8136)
- pslist.exe (PID: 8160)
- pslist.exe (PID: 8184)
- pslist.exe (PID: 7188)
- pslist.exe (PID: 5332)
- pslist.exe (PID: 7212)
- pslist.exe (PID: 616)
- pslist.exe (PID: 7300)
- pslist.exe (PID: 7236)
- pslist.exe (PID: 5072)
- pslist.exe (PID: 7336)
- pslist.exe (PID: 7364)
- pslist.exe (PID: 7484)
- pslist.exe (PID: 7392)
- pslist.exe (PID: 2284)
- pslist.exe (PID: 7176)
- pslist.exe (PID: 3884)
- pslist.exe (PID: 1812)
- pslist.exe (PID: 920)
- pslist.exe (PID: 1324)
- pslist.exe (PID: 5244)
- pslist.exe (PID: 2088)
- pslist.exe (PID: 7572)
INTERNETDOWNLOADMANAGER mutex has been found
- idmsetup.exe (PID: 7744)
- IDM1.tmp (PID: 7812)
Manual execution by a user
- IDMan.exe (PID: 5972)
- IDMan.exe (PID: 6808)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (52.5) |
|---|---|---|
| .scr | | | Windows screen saver (22) |
| .dll | | | Win32 Dynamic Link Library (generic) (11) |
| .exe | | | Win32 Executable (generic) (7.5) |
| .exe | | | Generic Win/DOS Executable (3.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:09:25 21:57:46+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 27136 |
| InitializedDataSize: | 186880 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x352d |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.41.3.1 |
| ProductVersionNumber: | 6.41.3.1 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Russian |
| CharacterSet: | Windows, Cyrillic |
| Comments: | Internet Download Manager installer |
| CompanyName: | Tonec FZE |
| FileDescription: | Internet Download Manager installer |
| FileVersion: | 6.41.3.1 |
| LegalCopyright: | (C) Tonec FZE |
| ProductName: | Internet Download Manager installer |
Total processes
250
Monitored processes
119
Malicious processes
39
Suspicious processes
20
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | REG ADD HKCU\Software\DownloadManager /v "LName" /t REG_SZ /d " " /f | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 536 | PSLIST IDM1 | C:\Users\admin\AppData\Local\Temp\nscBD09.tmp\idmrepack\pslist.exe | — | cmd.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: HIGH Description: Process information lister Exit code: 0 Version: 1.4 Modules
| |||||||||||||||
| 536 | "C:\Windows\System32\regsvr32.exe" /s "C:\Program Files (x86)\Internet Download Manager\IDMGetAll64.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | IDMan.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | PSLIST IDM1 | C:\Users\admin\AppData\Local\Temp\nscBD09.tmp\idmrepack\pslist.exe | — | cmd.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: HIGH Description: Process information lister Exit code: 0 Version: 1.4 Modules
| |||||||||||||||
| 632 | PSLIST IDM1 | C:\Users\admin\AppData\Local\Temp\nscBD09.tmp\idmrepack\pslist.exe | — | cmd.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: HIGH Description: Process information lister Exit code: 1 Version: 1.4 Modules
| |||||||||||||||
| 680 | TASKKILL /F /IM "MediumILStart.exe" /T | C:\Windows\SysWOW64\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | "C:\Program Files (x86)\Internet Download Manager\IEMonitor.exe" | C:\Program Files (x86)\Internet Download Manager\IEMonitor.exe | — | IDMan.exe | |||||||||||
User: admin Company: Tonec Inc. Integrity Level: MEDIUM Description: Internet Download Manager agent for click monitoring in IE-based browsers Exit code: 0 Version: 6, 37, 8, 1 Modules
| |||||||||||||||
| 920 | PSLIST IDMSETUP | C:\Users\admin\AppData\Local\Temp\nscBD09.tmp\idmrepack\pslist.exe | — | cmd.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: HIGH Description: Process information lister Exit code: 1 Version: 1.4 Modules
| |||||||||||||||
| 1056 | TASKKILL /F /IM "IDMGrHlp.exe" /T | C:\Windows\SysWOW64\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1324 | PSLIST IDM1 | C:\Users\admin\AppData\Local\Temp\nscBD09.tmp\idmrepack\pslist.exe | — | cmd.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: HIGH Description: Process information lister Exit code: 0 Version: 1.4 Modules
| |||||||||||||||
Total events
76 664
Read events
75 117
Write events
1 169
Delete events
378
Modification events
| (PID) Process: | (7648) pslist.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\PsList |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (7752) pslist.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\PsList |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (7792) pslist.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\PsList |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (8028) pslist.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\PsList |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (8084) pslist.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\PsList |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (8136) pslist.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\PsList |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (8160) pslist.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\PsList |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (7844) pslist.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\PsList |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (7888) pslist.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\PsList |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (7928) pslist.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\PsList |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
Executable files
15
Suspicious files
28
Text files
9
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7812 | IDM1.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\Internet Download Manager.lnk | binary | |
MD5:1C8B421C58938E55DF22AE7AE8D8B942 | SHA256:23DEC90EF3D803800FCACE094AC6F67B1D7648E3CB0DA7E90F496B467EE092E5 | |||
| 7812 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\license.lnk | lnk | |
MD5:12CB3551B0A2B072D42B7A28D4DD4CB4 | SHA256:138519134F2E619D38038D636F418D8FC7AC0358C9F632F9B3CC3B88DA85F8E9 | |||
| 7812 | IDM1.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\license.lnk | binary | |
MD5:2CB78204E4E311761A1082D70977CF5E | SHA256:767579FA08EFA697678312B9A3BF51CF59A9156BFF9D934BE97F8D912735B492 | |||
| 7812 | IDM1.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\IDM Help.lnk | binary | |
MD5:C47621A2F5CBFC8C27C6E99CA3278A92 | SHA256:D7C2B7E0F06AA99E5D4294F4D816B79E86D5D41536BFA856D9A6333198A618DE | |||
| 7812 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\IDM Help.lnk | binary | |
MD5:CD1CF430FECE31C30039F5F0A8EE4BB0 | SHA256:235474A5B0B8D43F66FCED8B7C4EA22ED32E4F9217932D8EA59B38C7A60538B1 | |||
| 7812 | IDM1.tmp | C:\Program Files (x86)\Internet Download Manager\IDMSetup2.log | binary | |
MD5:9A4E524A56467799F3410529BC64D6D6 | SHA256:8908F162432B9A8193B8D6D90F8E6B88E6CC1E059B19F29FDA9C59C4F663554A | |||
| 7812 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\TUTORIALS.lnk | binary | |
MD5:6BD1F09628F60195029062A6074EB9C1 | SHA256:A5803BDA8FB46E15D40B5C7980DC196C61F5E76844765F49233FAC4595BF4D8D | |||
| 7512 | IDM Repack v1.0.exe | C:\Users\admin\AppData\Local\Temp\nscBD09.tmp\idmrepack\launcher.bat | text | |
MD5:A31586630E7E26E6717FA69CCF99245D | SHA256:5388017A92CB7F76934FAD64E219FE183DF95CDD06E7EC5BCD07119A4C421185 | |||
| 7812 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\Internet Download Manager.lnk | binary | |
MD5:5BE80F9BCC3261225EEAF56EDCF388CD | SHA256:B74887F65C13F07F27A891FA82C15C32020FB92ECE5D56EF9B251DB859DE959C | |||
| 7812 | IDM1.tmp | C:\Users\admin\AppData\Local\Temp\~DFB3364B75BA0C40F7.TMP | binary | |
MD5:504BB3EA0E68D44D296999F9AE0FEBE2 | SHA256:E7BD695141B884DD6FD992623DED1E79D212A93346CD67E8EEB3B8810D6802A7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
19
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6512 | SIHClient.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6512 | SIHClient.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
6512 | SIHClient.exe | 20.12.23.50:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6512 | SIHClient.exe | 104.119.109.218:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |