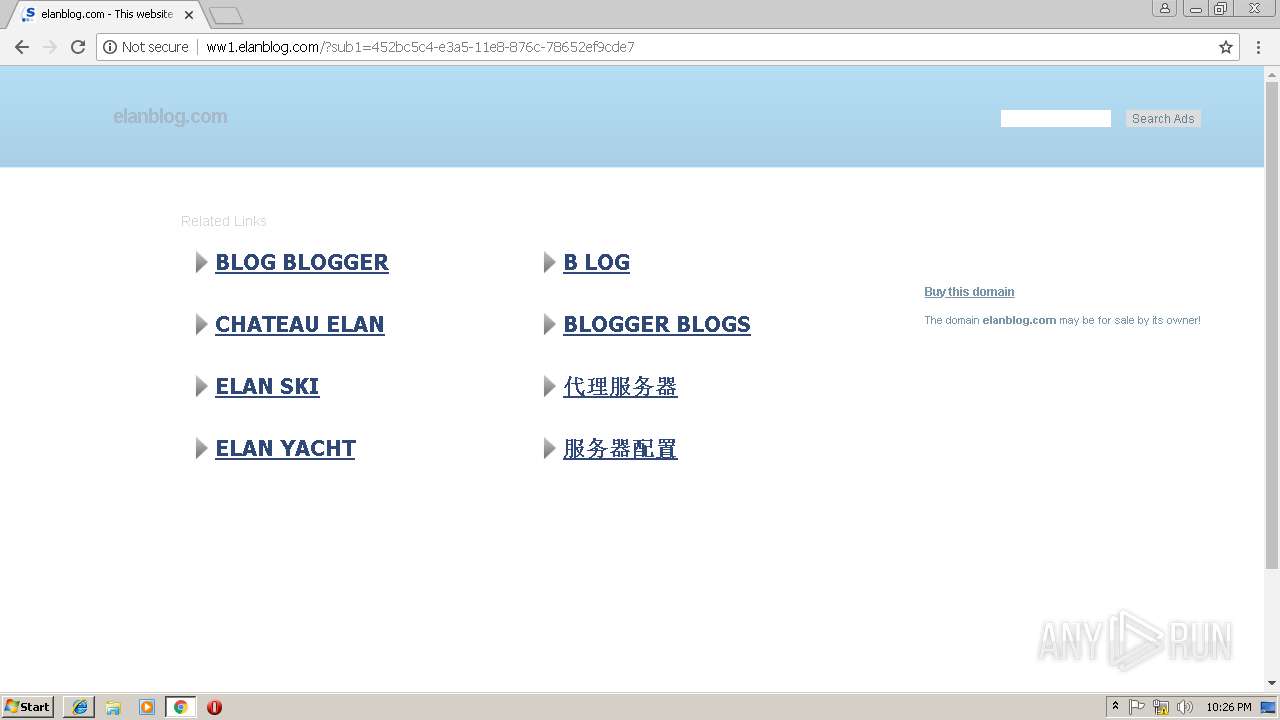
| URL: | http://www.elanblog.com/extensions/service/cdnhosts.txt |
| Full analysis: | https://app.any.run/tasks/62ce7346-419d-4336-8de8-524419483827 |
| Verdict: | Malicious activity |
| Analysis date: | November 08, 2018, 22:24:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 040821F826EAB053CD1AF7E952A78192 |
| SHA1: | 2A3550292572E3C67A8253A213611F8D487B9E7E |
| SHA256: | C57CAEE6FAF10B7D5126CA6DB9EEF92423DA1EAF9B6F7A72F472E33EAE4A1222 |
| SSDEEP: | 3:N1KJS4Rp1dIbTuSzeBP+RT:Cc4R/dIbreBPuT |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 3636)
- chrome.exe (PID: 536)
Reads internet explorer settings
- iexplore.exe (PID: 3776)
Changes internet zones settings
- iexplore.exe (PID: 3636)
Reads Internet Cache Settings
- iexplore.exe (PID: 3776)
Creates files in the user directory
- iexplore.exe (PID: 3776)
Reads settings of System Certificates
- chrome.exe (PID: 536)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
43
Monitored processes
12
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 916 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=68.0.3440.106 --initial-client-data=0x78,0x7c,0x80,0x74,0x84,0x6f8a00b0,0x6f8a00c0,0x6f8a00cc | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2036 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=924,5757226483673637424,11295573891883905885,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=8C27A6A8F18C66F441AB8CF84F7B3D07 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8C27A6A8F18C66F441AB8CF84F7B3D07 --renderer-client-id=6 --mojo-platform-channel-handle=3560 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2136 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=1536 --on-initialized-event-handle=304 --parent-handle=308 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2284 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=924,5757226483673637424,11295573891883905885,131072 --enable-features=PasswordImport --disable-gpu-sandbox --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=52EA9742C0E2023F12A235E5DE7BAE9C --mojo-platform-channel-handle=3568 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2540 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=924,5757226483673637424,11295573891883905885,131072 --enable-features=PasswordImport --service-pipe-token=BCE764A533E9CBB8733274C65157AE9E --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=BCE764A533E9CBB8733274C65157AE9E --renderer-client-id=5 --mojo-platform-channel-handle=1912 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2636 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=924,5757226483673637424,11295573891883905885,131072 --enable-features=PasswordImport --service-pipe-token=CEA3E6CDBF78D554E5CA0B02A757F78C --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=CEA3E6CDBF78D554E5CA0B02A757F78C --renderer-client-id=3 --mojo-platform-channel-handle=2088 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3636 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3704 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=924,5757226483673637424,11295573891883905885,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=DCFF10627638DF5D1749783E4DE9641E --mojo-platform-channel-handle=976 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3776 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3636 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
504
Read events
402
Write events
96
Delete events
6
Modification events
| (PID) Process: | (3636) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3636) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3636) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3636) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3636) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3636) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3636) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {269055E7-E3A5-11E8-9C83-5254004AAD11} |
Value: 0 | |||
| (PID) Process: | (3636) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (3636) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (3636) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E2070B0004000800160019000A006301 | |||
Executable files
0
Suspicious files
58
Text files
72
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3636 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3636 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3776 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\ww1_elanblog_com[1].txt | — | |
MD5:— | SHA256:— | |||
| 536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\f6e9fa52-079b-4872-9fcd-5afe346fab2c.tmp | — | |
MD5:— | SHA256:— | |||
| 536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3776 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\MSHist012018110820181109\index.dat | dat | |
MD5:— | SHA256:— | |||
| 536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3776 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\ww1_elanblog_com[1].htm | html | |
MD5:— | SHA256:— | |||
| 3636 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\History.IE5\MSHist012018110820181109\index.dat | dat | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
33
DNS requests
23
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3776 | iexplore.exe | GET | 200 | 172.217.168.68:80 | http://www.google.com/adsense/domains/caf.js | US | text | 54.3 Kb | malicious |
3776 | iexplore.exe | GET | 200 | 72.52.4.90:80 | http://ww1.elanblog.com/search/tsc.php?200=MjM5NDE2MzM2&21=MjE3LjE0Ny44OS4xOA==&681=MTU0MTcxNTkxMWY3ZTExMTQ3YzBmN2JhN2Y3N2MwZjFjZmYyN2U3ZWZj&crc=685bb3d05daaf00f1f58f99eae63aaf8e42ed6e5&cv=1 | US | compressed | 19.7 Kb | malicious |
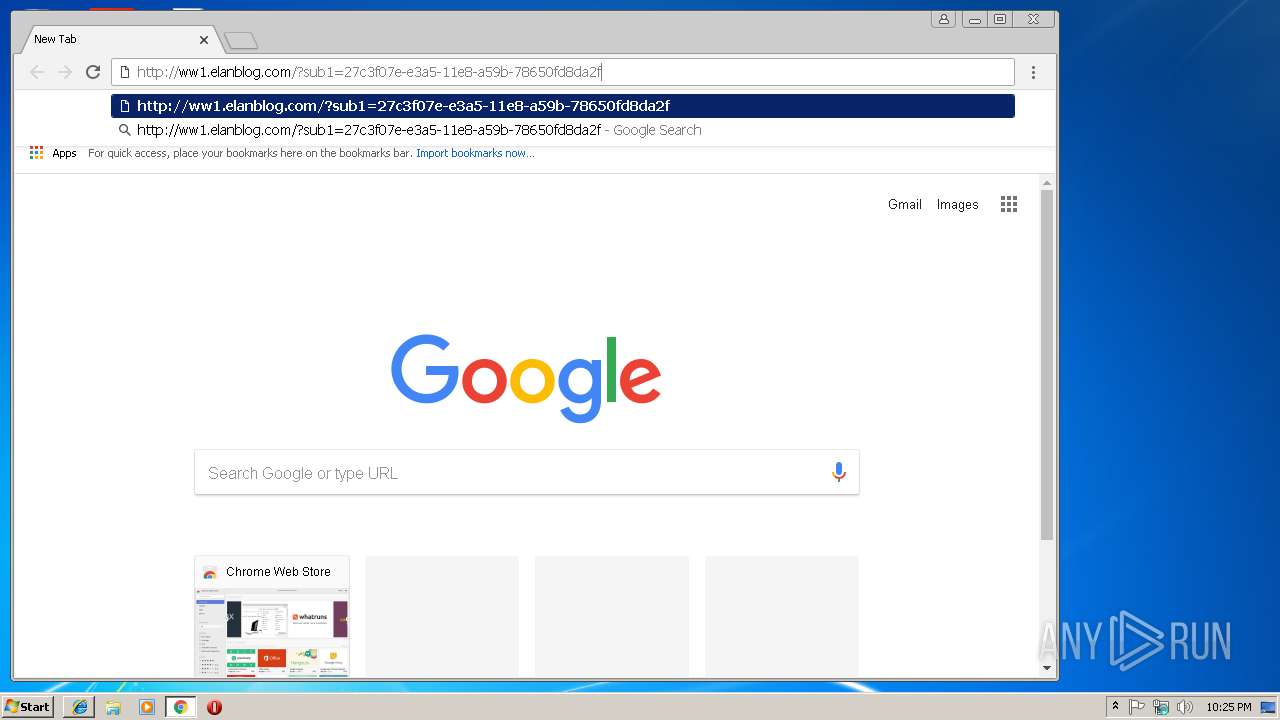
536 | chrome.exe | GET | 200 | 72.52.4.90:80 | http://ww1.elanblog.com/?sub1=27c3f07e-e3a5-11e8-a59b-78650fd8da2f | US | html | 19.7 Kb | malicious |
3776 | iexplore.exe | GET | 200 | 72.52.4.90:80 | http://ww1.elanblog.com/?sub1=27c3f07e-e3a5-11e8-a59b-78650fd8da2f | US | html | 19.7 Kb | malicious |
536 | chrome.exe | GET | 200 | 172.217.168.68:80 | http://www.google.com/dp/ads?r=m&client=dp-sedo85_3ph&channel=cl-047%2Cexp-0051%2Cauxa-control-1%2C187408&hl=en&adtest=off&adsafe=low&type=3&swp=as-drid-2445610912134376&uiopt=false&oe=UTF-8&ie=UTF-8&fexp=21404%2C17300002&format=r10%7Cs&num=0&output=afd_ads&domain_name=ww1.elanblog.com&v=3&preload=true&adext=as1%2Csr1&bsl=8&u_his=2&u_tz=0&dt=1541715932214&u_w=1280&u_h=720&biw=1040&bih=542&psw=1040&psh=102&frm=0&uio=as1sl1sr1-ff3fa2st22sa14lt40-ff2&jsv=14800&rurl=http%3A%2F%2Fww1.elanblog.com%2F%3Fsub1%3D27c3f07e-e3a5-11e8-a59b-78650fd8da2f | US | html | 1.44 Kb | malicious |
536 | chrome.exe | GET | 200 | 172.217.168.68:80 | http://www.google.com/adsense/domains/caf.js | US | text | 54.3 Kb | malicious |
536 | chrome.exe | GET | 200 | 72.52.4.90:80 | http://ww1.elanblog.com/search/tsc.php?200=MjM5NDE2MzM2&21=MjE3LjE0Ny44OS4xOA==&681=MTU0MTcxNTkzMmRjYmMxNjIzYzZmN2YzMjNkMzU4NTJjZWMwZjYzNjQ3&crc=5d1bbb205a96cd103871bc07f0be07e3f85d5219&cv=1 | US | compressed | 19.7 Kb | malicious |
536 | chrome.exe | GET | 200 | 172.217.168.81:80 | http://survey.g.doubleclick.net/insights/consumersurveys/static/413846457441986483/prompt_embed_static.js | US | text | 113 Kb | whitelisted |
536 | chrome.exe | GET | 200 | 172.217.168.81:80 | http://survey.g.doubleclick.net/async_survey?site=kv4ic6olrzkr6 | US | text | 17.6 Kb | whitelisted |
536 | chrome.exe | GET | 200 | 72.52.4.90:80 | http://ww1.elanblog.com/?sub1=27c3f07e-e3a5-11e8-a59b-78650fd8da2f | US | html | 19.6 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
536 | chrome.exe | 216.58.215.234:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
536 | chrome.exe | 172.217.168.78:443 | apis.google.com | Google Inc. | US | whitelisted |
3636 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3776 | iexplore.exe | 109.201.133.71:80 | www.elanblog.com | NForce Entertainment B.V. | NL | malicious |
3776 | iexplore.exe | 205.234.175.175:80 | img.sedoparking.com | CacheNetworks, Inc. | US | suspicious |
536 | chrome.exe | 172.217.168.45:443 | accounts.google.com | Google Inc. | US | whitelisted |
536 | chrome.exe | 172.217.168.68:80 | www.google.com | Google Inc. | US | whitelisted |
536 | chrome.exe | 172.217.168.68:443 | www.google.com | Google Inc. | US | whitelisted |
536 | chrome.exe | 72.52.4.90:80 | ww1.elanblog.com | Akamai Technologies, Inc. | US | whitelisted |
536 | chrome.exe | 172.217.168.81:80 | survey.g.doubleclick.net | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
www.elanblog.com |
| malicious |
ww1.elanblog.com |
| malicious |
img.sedoparking.com |
| whitelisted |
www.google.com |
| malicious |
www.google.de |
| whitelisted |
www.gstatic.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3776 | iexplore.exe | A Network Trojan was detected | SC BAD_UNKNOWN Trojan Unknown JS |
536 | chrome.exe | A Network Trojan was detected | SC BAD_UNKNOWN Trojan Unknown JS |
536 | chrome.exe | A Network Trojan was detected | SC BAD_UNKNOWN Trojan Unknown JS |
536 | chrome.exe | A Network Trojan was detected | SC BAD_UNKNOWN Trojan Unknown JS |