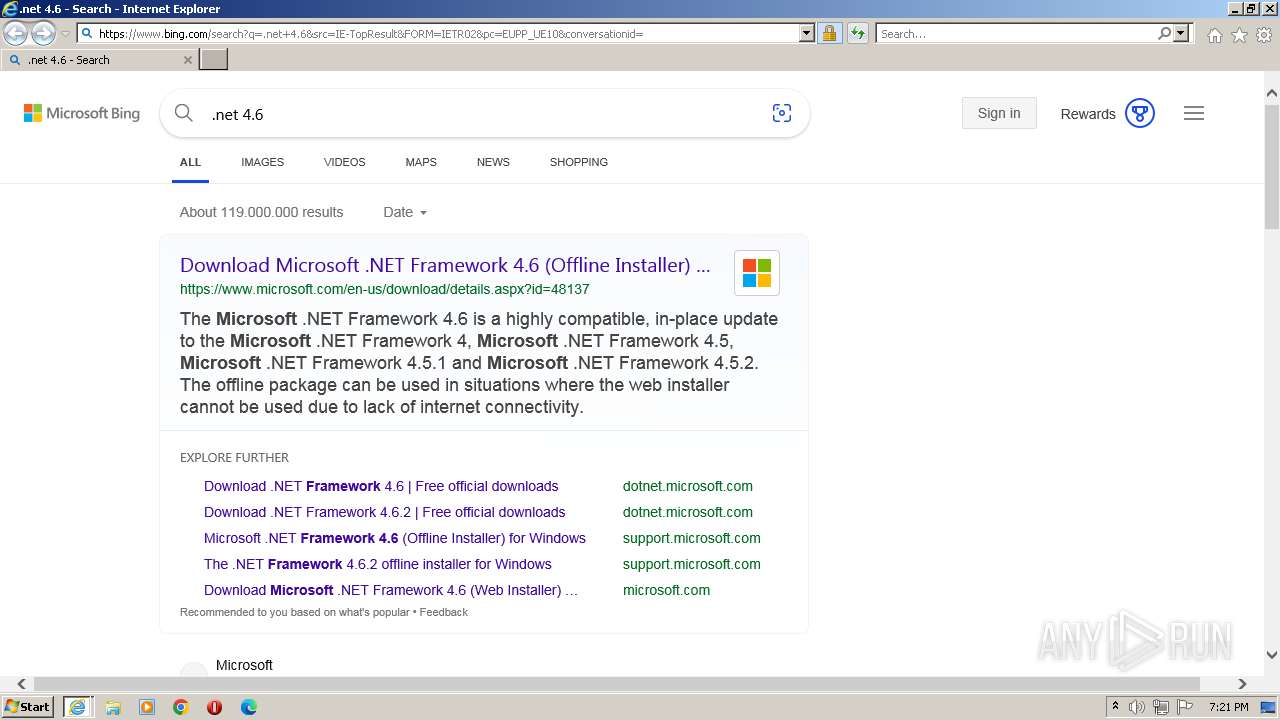
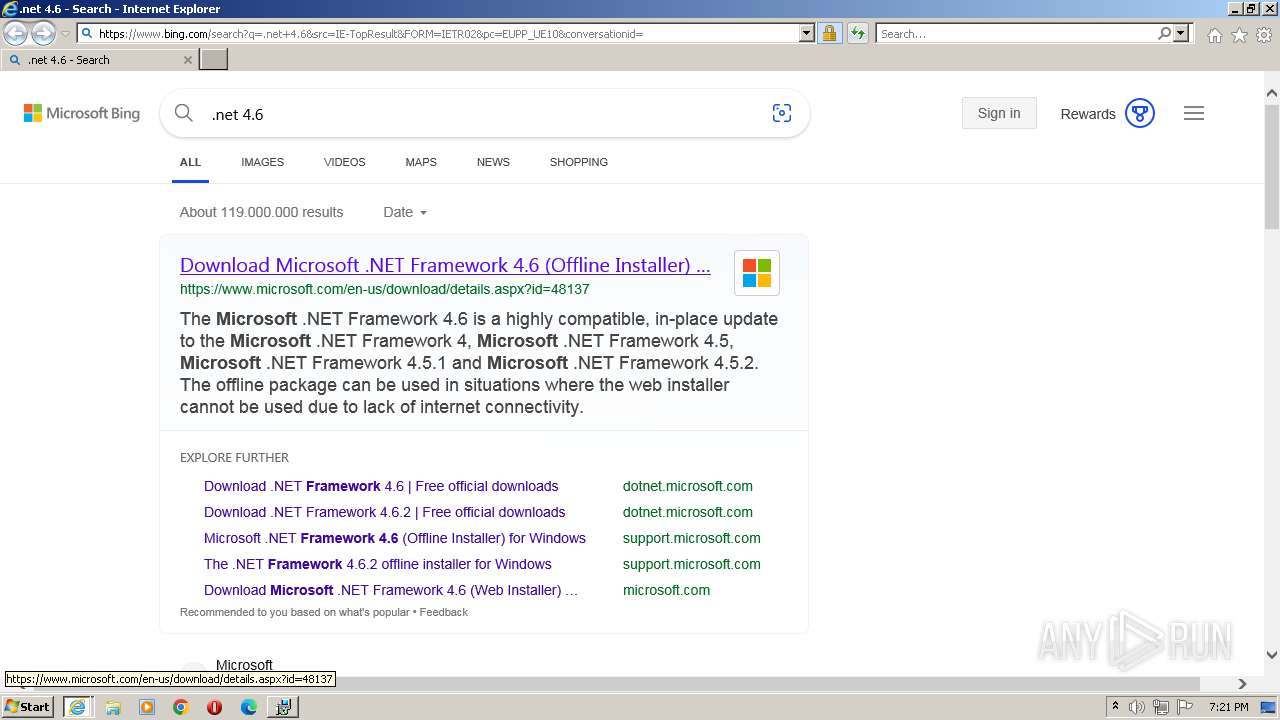
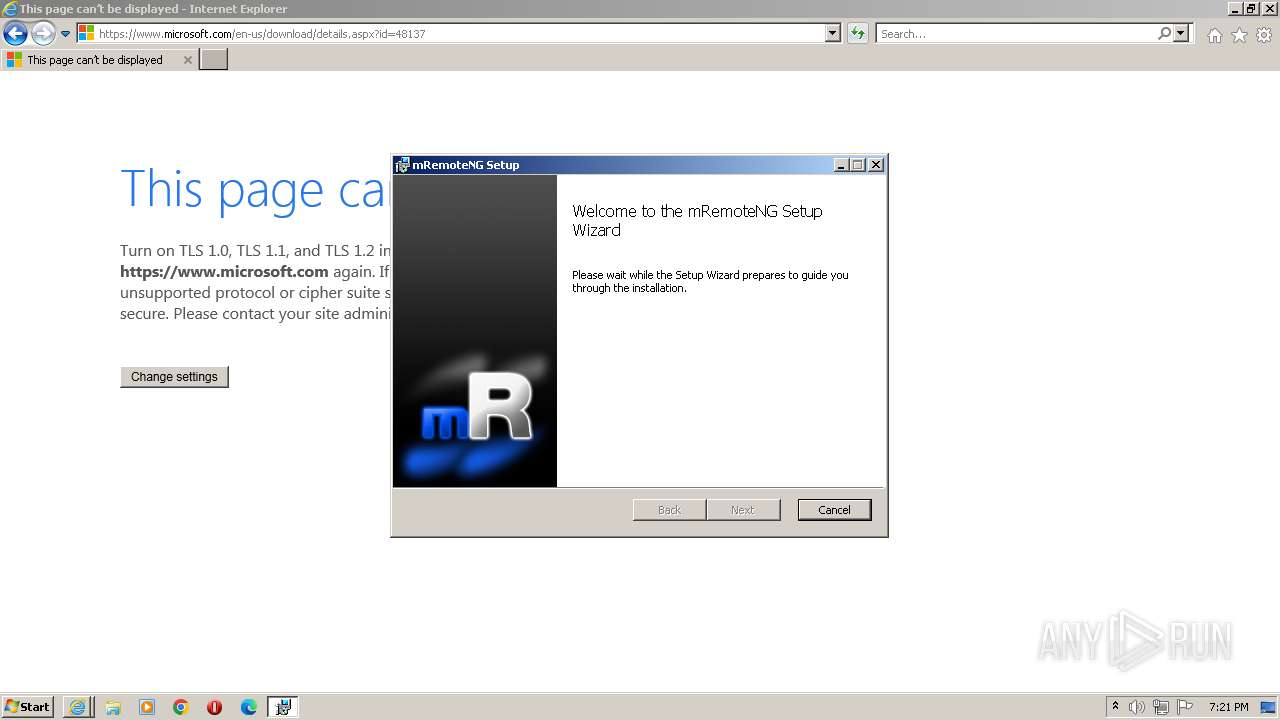
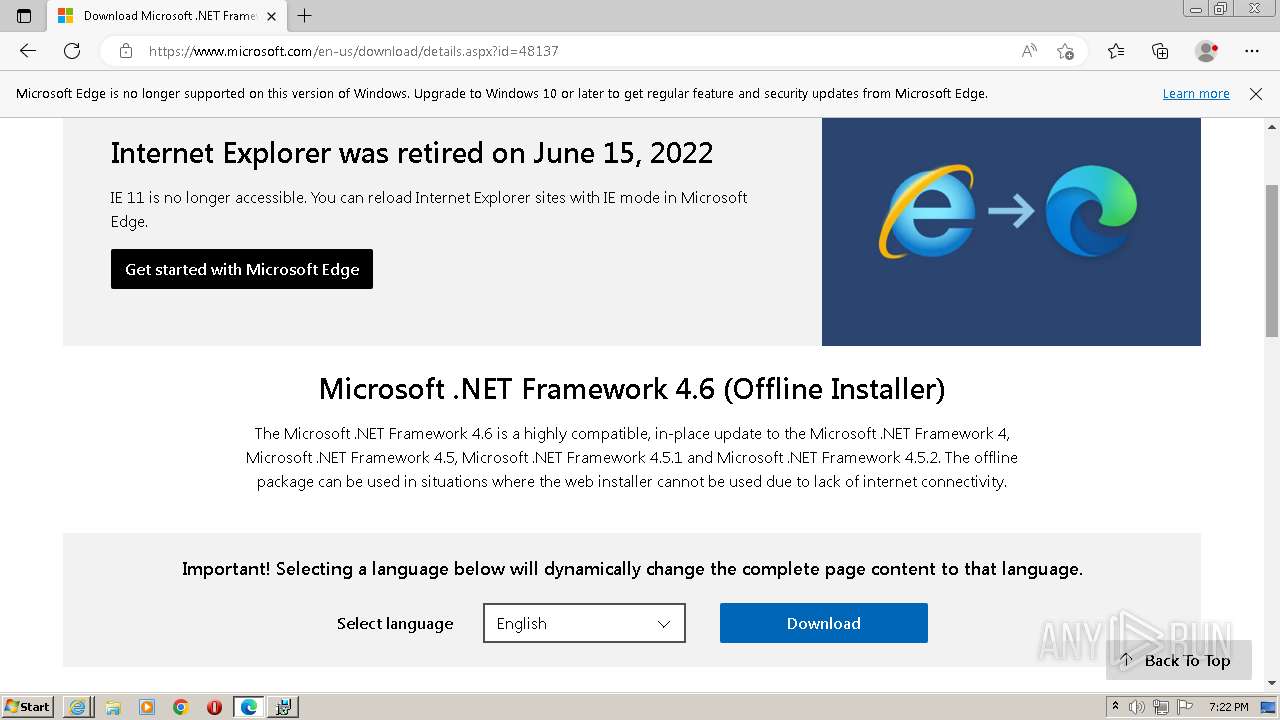
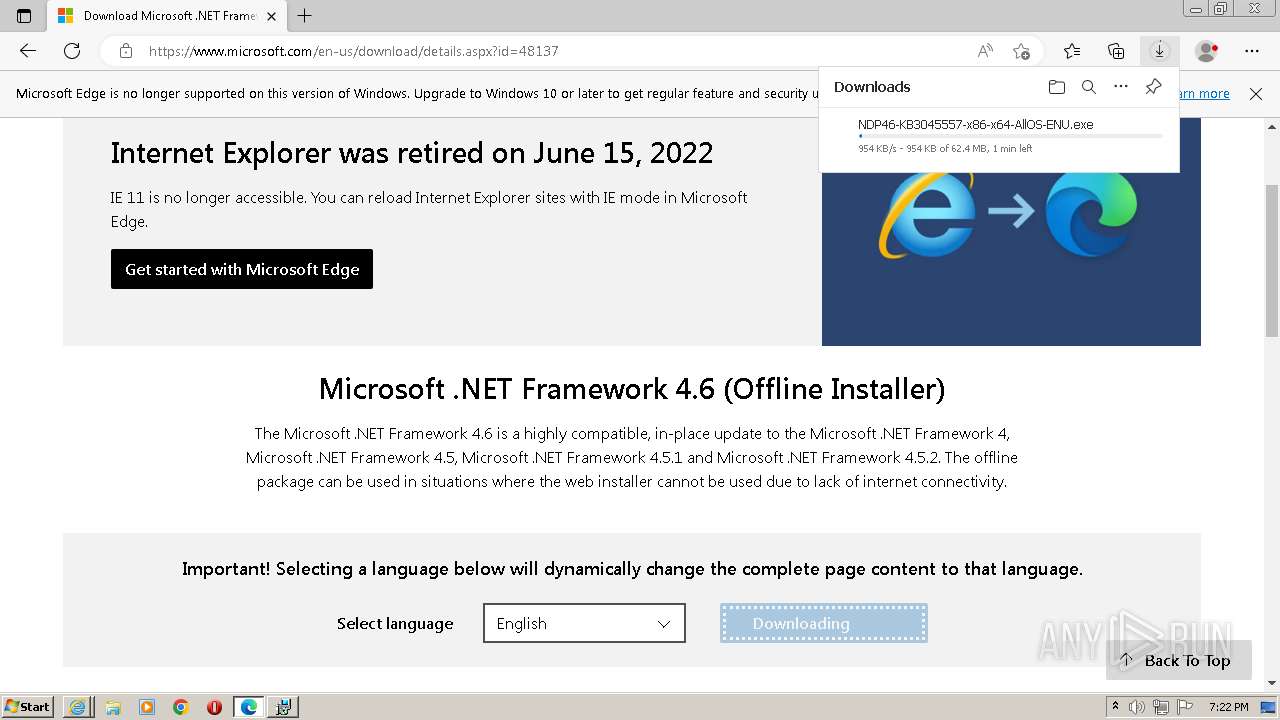
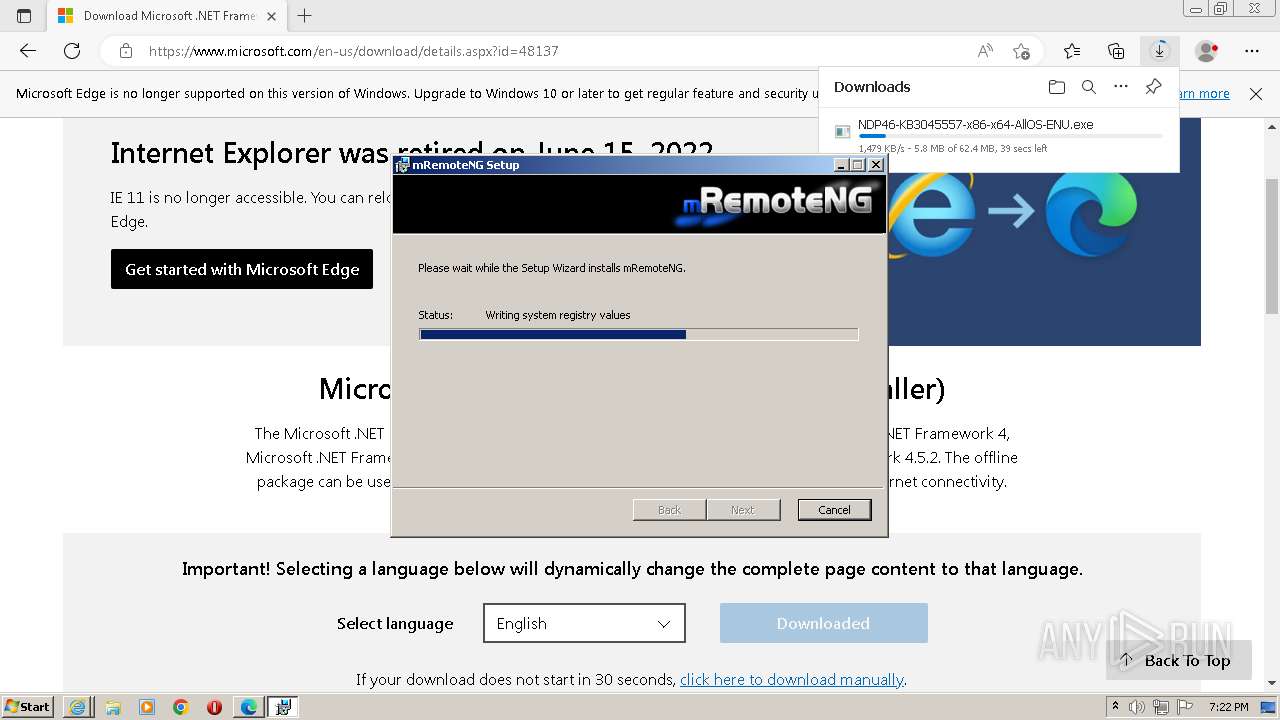
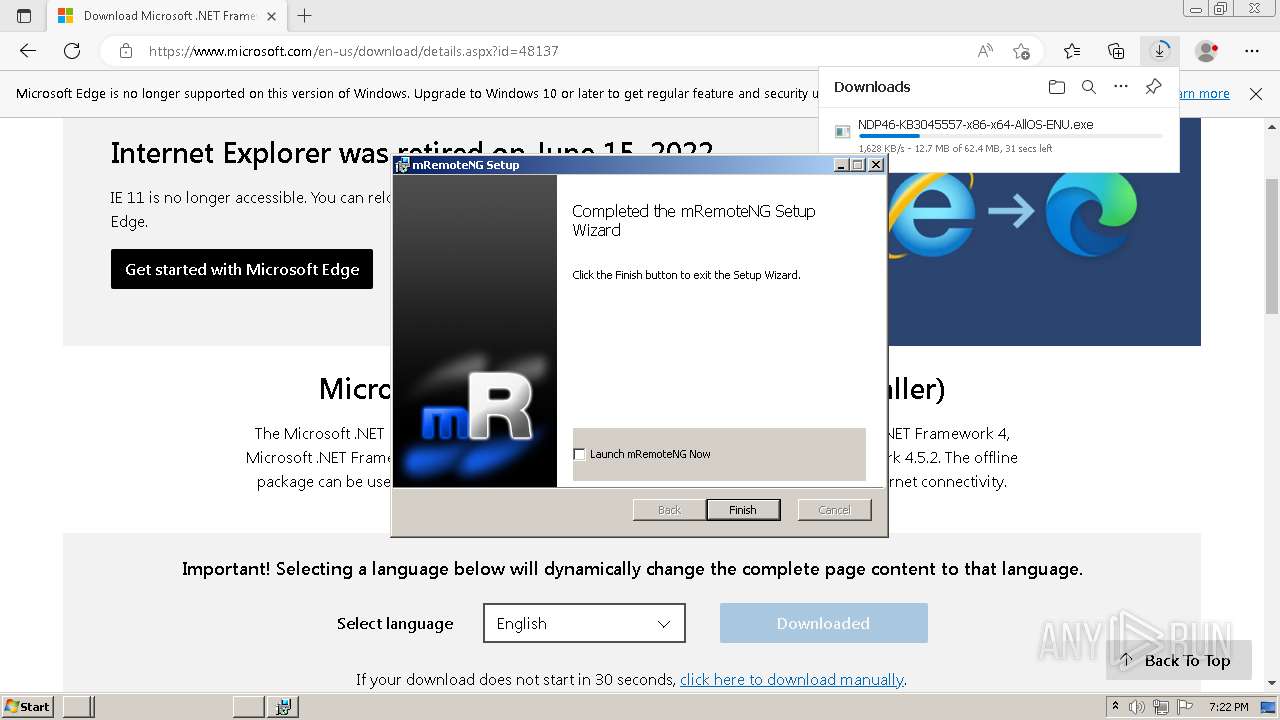
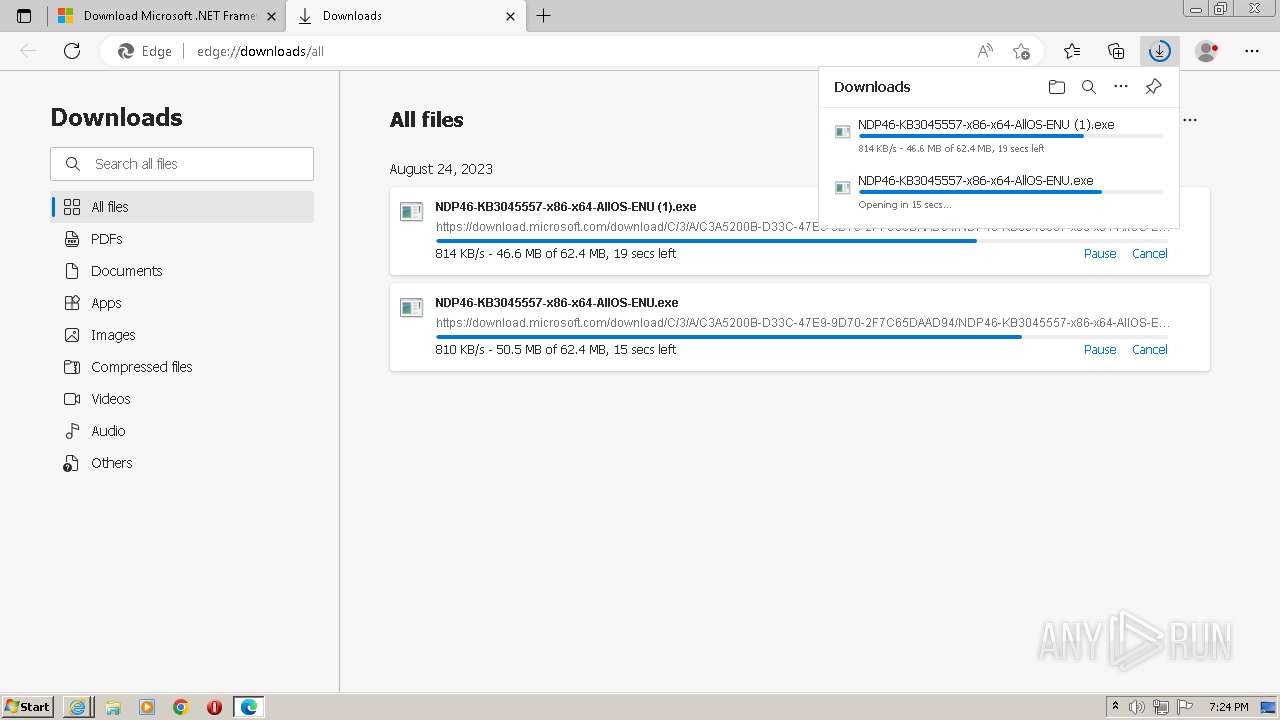
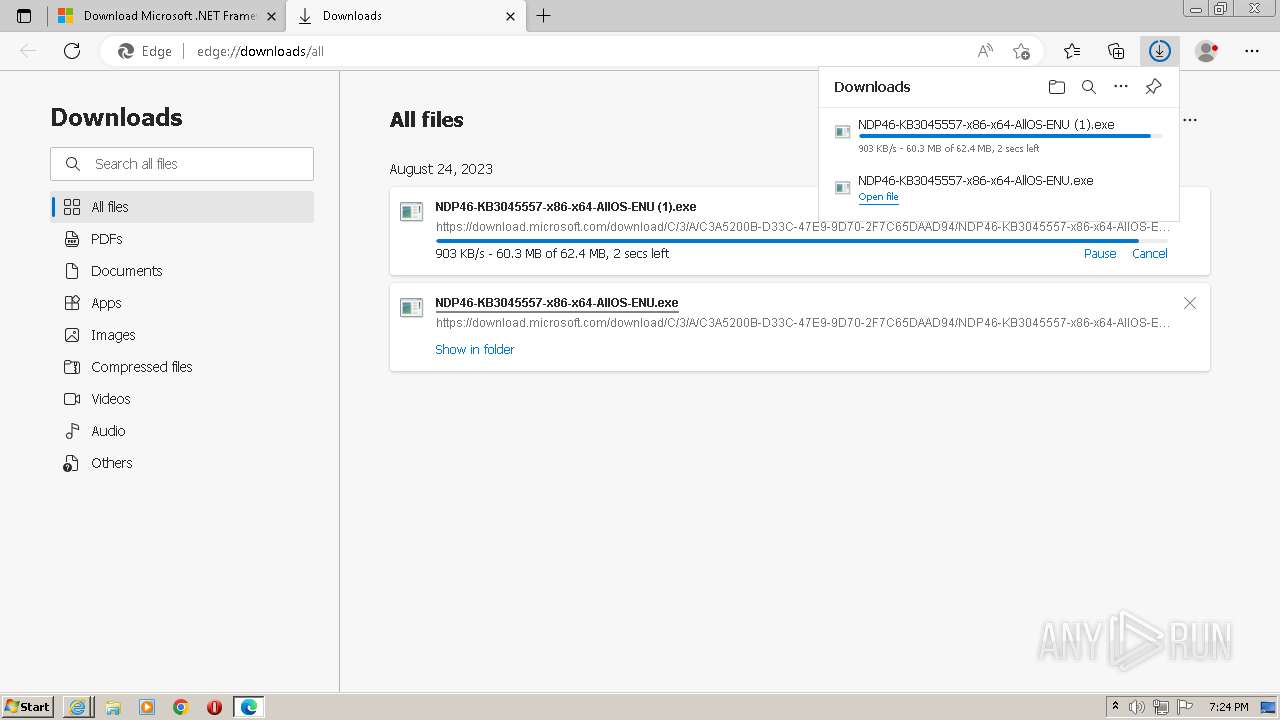
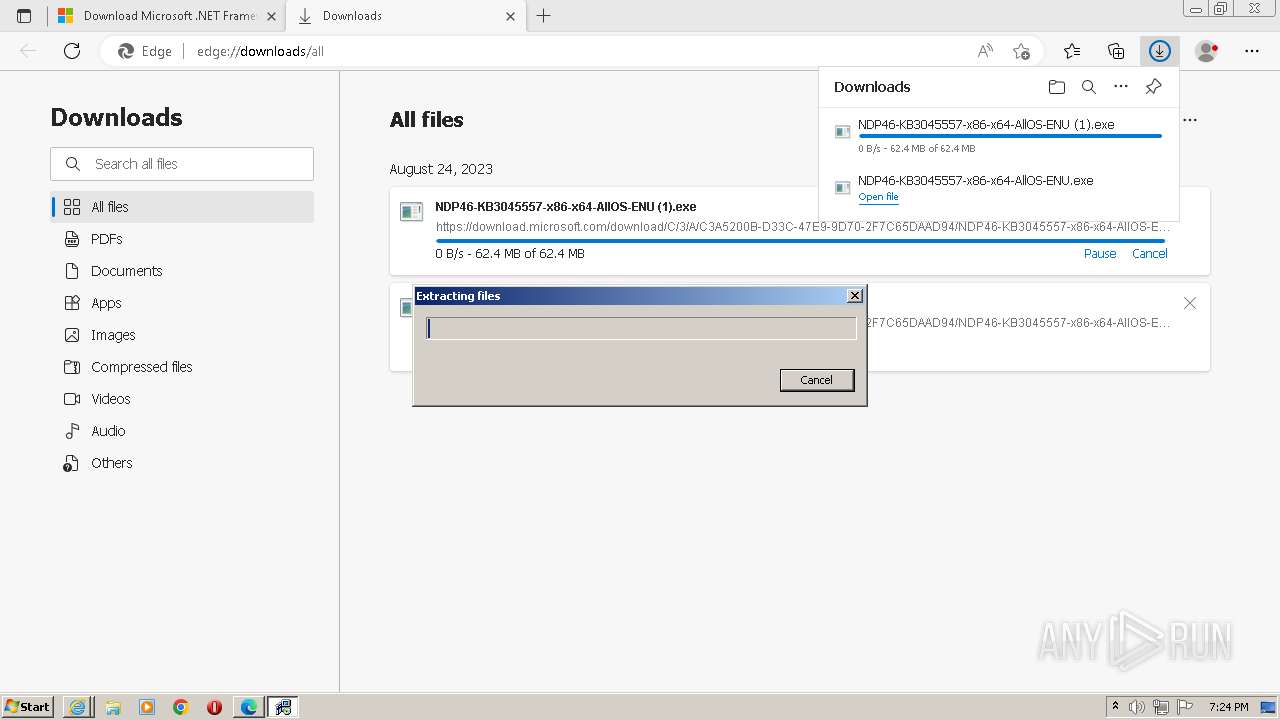
| URL: | https://github.com/mRemoteNG/mRemoteNG/releases/download/v1.76.20/mRemoteNG-Installer-1.76.20.24615.msi |
| Full analysis: | https://app.any.run/tasks/d653fa27-7804-4516-8f66-47a61d90e3d5 |
| Verdict: | Malicious activity |
| Analysis date: | August 24, 2023, 18:20:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 64A48D89D7ABCF465EA755E4F5731B4C |
| SHA1: | FB1C85519FE7A72EFF7D169A5F86954F4B552963 |
| SHA256: | C569865DD7D875F5D9981BC11EBF62E4E0E3ED10E02F67CF8FB4E819673700A0 |
| SSDEEP: | 3:N8tEd43tKmrpsbrpQJh2kCmgk6rrtRBXIS4hlUerM:2uu34cmeKsgXnBXlmOerM |
MALICIOUS
Loads dropped or rewritten executable
- msiexec.exe (PID: 1608)
- rundll32.exe (PID: 2204)
- rundll32.exe (PID: 3768)
- rundll32.exe (PID: 2728)
- msiexec.exe (PID: 3408)
- rundll32.exe (PID: 1456)
- rundll32.exe (PID: 3332)
- rundll32.exe (PID: 1532)
- Setup.exe (PID: 3684)
- msiexec.exe (PID: 3644)
- msiexec.exe (PID: 3140)
- msiexec.exe (PID: 3668)
Application was dropped or rewritten from another process
- mRemoteNG.exe (PID: 2168)
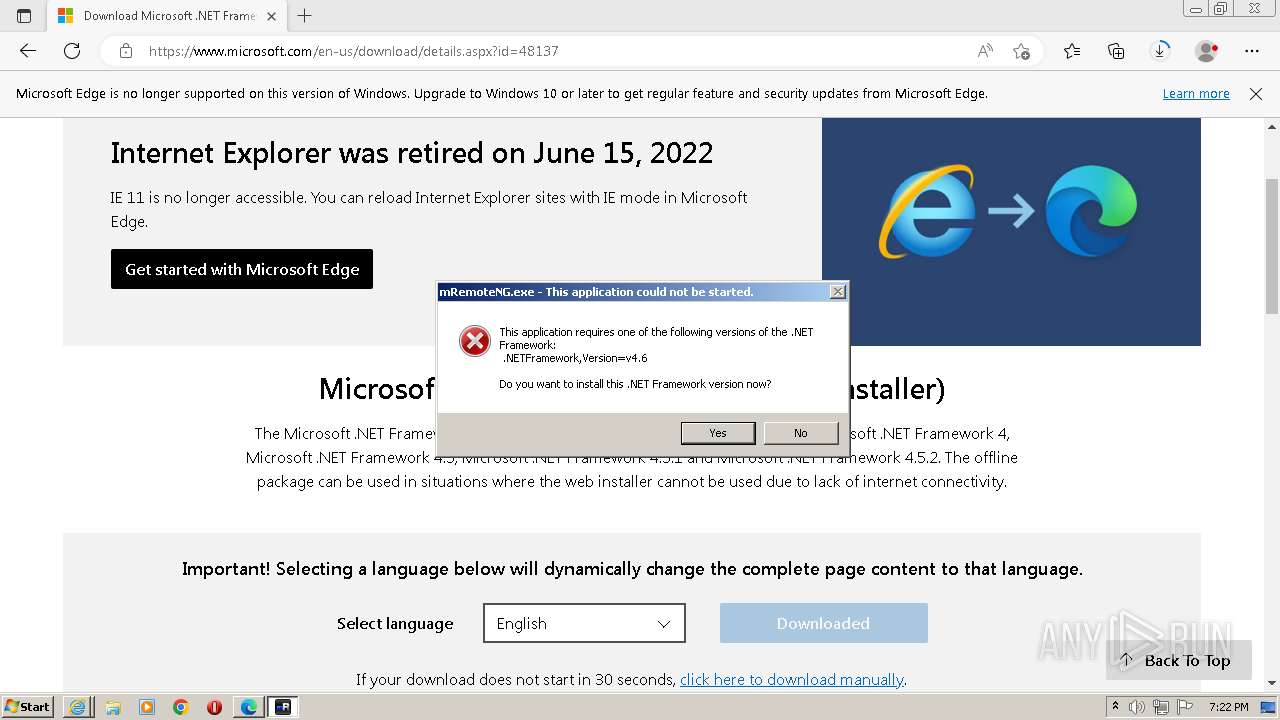
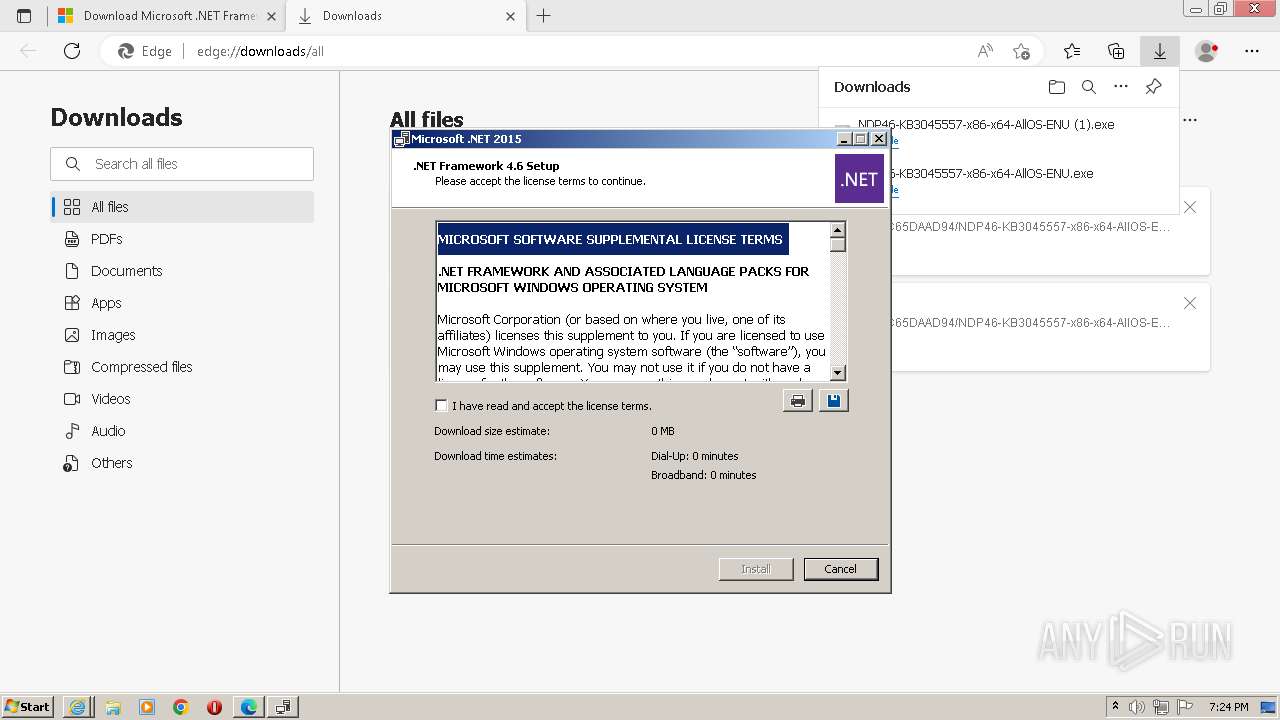
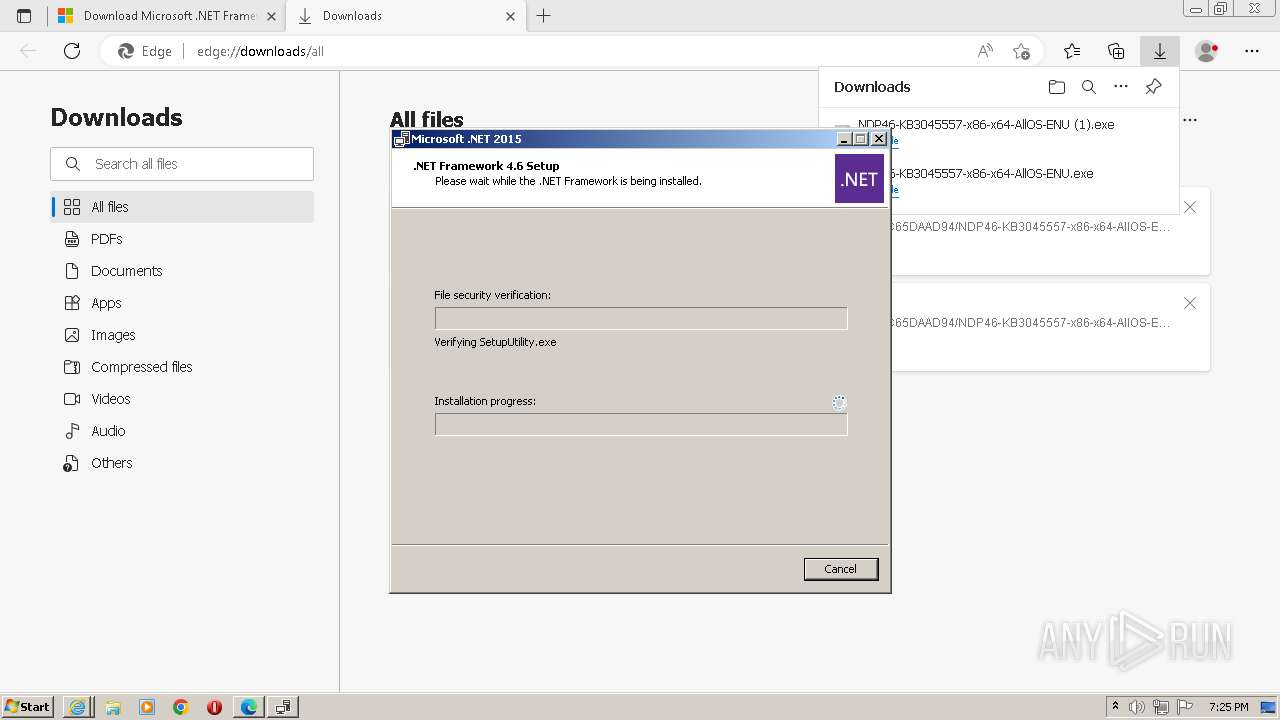
- NDP46-KB3045557-x86-x64-AllOS-ENU.exe (PID: 3628)
- NDP46-KB3045557-x86-x64-AllOS-ENU.exe (PID: 2412)
- Setup.exe (PID: 3684)
- SetupUtility.exe (PID: 2776)
- SetupUtility.exe (PID: 3480)
Creates a writable file the system directory
- msiexec.exe (PID: 3668)
SUSPICIOUS
Executable content was dropped or overwritten
- rundll32.exe (PID: 2204)
- rundll32.exe (PID: 3768)
- rundll32.exe (PID: 2728)
- rundll32.exe (PID: 1456)
- rundll32.exe (PID: 3332)
- rundll32.exe (PID: 1532)
- NDP46-KB3045557-x86-x64-AllOS-ENU.exe (PID: 2412)
Uses RUNDLL32.EXE to load library
- msiexec.exe (PID: 1608)
- msiexec.exe (PID: 3408)
Executes as Windows Service
- VSSVC.exe (PID: 3976)
Checks Windows Trust Settings
- msiexec.exe (PID: 3668)
- Setup.exe (PID: 3684)
Reads the Internet Settings
- msiexec.exe (PID: 1608)
- Setup.exe (PID: 3684)
Reads settings of System Certificates
- Setup.exe (PID: 3684)
Reads security settings of Internet Explorer
- Setup.exe (PID: 3684)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 3668)
The process creates files with name similar to system file names
- msiexec.exe (PID: 3668)
INFO
Reads the computer name
- msiexec.exe (PID: 1608)
- msiexec.exe (PID: 3668)
- msiexec.exe (PID: 3408)
- NDP46-KB3045557-x86-x64-AllOS-ENU.exe (PID: 2412)
- Setup.exe (PID: 3684)
- SetupUtility.exe (PID: 2776)
- SetupUtility.exe (PID: 3480)
- msiexec.exe (PID: 3644)
- msiexec.exe (PID: 3140)
Application launched itself
- msiexec.exe (PID: 3668)
- iexplore.exe (PID: 3492)
- msedge.exe (PID: 1196)
- msedge.exe (PID: 3544)
Reads the machine GUID from the registry
- msiexec.exe (PID: 3668)
- msiexec.exe (PID: 1608)
- msiexec.exe (PID: 3408)
- NDP46-KB3045557-x86-x64-AllOS-ENU.exe (PID: 2412)
- Setup.exe (PID: 3684)
- SetupUtility.exe (PID: 2776)
- msiexec.exe (PID: 3644)
- msiexec.exe (PID: 3140)
Checks supported languages
- msiexec.exe (PID: 1608)
- msiexec.exe (PID: 3668)
- msiexec.exe (PID: 3408)
- mRemoteNG.exe (PID: 2168)
- NDP46-KB3045557-x86-x64-AllOS-ENU.exe (PID: 2412)
- Setup.exe (PID: 3684)
- SetupUtility.exe (PID: 2776)
- SetupUtility.exe (PID: 3480)
- msiexec.exe (PID: 3644)
- msiexec.exe (PID: 3140)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 2468)
Create files in a temporary directory
- msiexec.exe (PID: 2468)
- rundll32.exe (PID: 3768)
- rundll32.exe (PID: 2204)
- rundll32.exe (PID: 2728)
- rundll32.exe (PID: 1456)
- rundll32.exe (PID: 3332)
- rundll32.exe (PID: 1532)
- msiexec.exe (PID: 3668)
- NDP46-KB3045557-x86-x64-AllOS-ENU.exe (PID: 2412)
- Setup.exe (PID: 3684)
- SetupUtility.exe (PID: 2776)
The process uses the downloaded file
- iexplore.exe (PID: 3492)
- msedge.exe (PID: 3544)
- msedge.exe (PID: 876)
- msedge.exe (PID: 2756)
Manual execution by a user
- msedge.exe (PID: 1196)
- msedge.exe (PID: 3544)
Executable content was dropped or overwritten
- msiexec.exe (PID: 3668)
- msiexec.exe (PID: 2468)
- msedge.exe (PID: 3544)
- msedge.exe (PID: 1200)
Reads CPU info
- Setup.exe (PID: 3684)
Creates files or folders in the user directory
- Setup.exe (PID: 3684)
Reads Environment values
- Setup.exe (PID: 3684)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
115
Monitored processes
66
Malicious processes
7
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 272 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1204 --field-trial-handle=1328,i,2859336128407249032,1248196233477633759,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 328 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=4572 --field-trial-handle=1328,i,2859336128407249032,1248196233477633759,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 876 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=4764 --field-trial-handle=1328,i,2859336128407249032,1248196233477633759,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 952 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=3324 --field-trial-handle=1328,i,2859336128407249032,1248196233477633759,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1180 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --instant-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2268 --field-trial-handle=1376,i,2346292133828864167,13174474769165969931,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1196 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --profile-directory=Default | C:\Program Files\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1196 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=4556 --field-trial-handle=1328,i,2859336128407249032,1248196233477633759,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1200 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=888 --field-trial-handle=1328,i,2859336128407249032,1248196233477633759,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1456 | rundll32.exe "C:\Windows\Installer\MSI9443.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1086671 1 CustomActions!CustomActions.CustomActions.IsRdpDtlsUpdateInstalled | C:\Windows\System32\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1532 | rundll32.exe "C:\Windows\Installer\MSIB7AB.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1095593 15 CustomActions!CustomActions.CustomActions.IsLegacyVersionInstalled | C:\Windows\System32\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
49 086
Read events
48 779
Write events
271
Delete events
36
Modification events
| (PID) Process: | (3492) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3492) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3492) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3492) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3492) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3492) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3492) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3492) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3492) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3492) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
597
Suspicious files
1 426
Text files
647
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3492 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\StructuredQuery.log | text | |
MD5:DF0F3530AF1B22A2A8CAC1E390B2BBC5 | SHA256:87EA99A163B8D02ED9BA195816283AC952E502F51DA017FB71308340D72A7B89 | |||
| 2392 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 2392 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_ADE4E4D3A3BCBCA5C39C54D362D88565 | der | |
MD5:E9740C7278A4243A2D48997D7A8D974F | SHA256:1578FCFD7C6C3C1CB96DB3106A44BB6B77BDD6D759E9A17067E56A1AC7DB834A | |||
| 2392 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\50CD3D75D026C82E2E718570BD6F44D0_D222662A57BAA60D2F5EA0D2CC7B2F1C | binary | |
MD5:EAC05A9A9A4120060FF12001DF62E437 | SHA256:1590EA19A88E925F8C8131C1C78B13E580F542978F1966799603AB0FEAAA89CF | |||
| 3492 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:834D7739919DE3EC2F4FE9E3A60B22AB | SHA256:64394A1B0507AEEB12C9A4EEAF4D816932EC6254FBD4C7203B623E92B6A1A5A7 | |||
| 3492 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3492 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:753780AF70C08B0772F51E140EC02A30 | SHA256:1D3402915BF8CB0460ED3451221A55FC4454C4920FA9EAD2C5CED1924D4E984B | |||
| 2392 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_ADE4E4D3A3BCBCA5C39C54D362D88565 | binary | |
MD5:F29FA47FDC20692F1A8CB1AA50383A02 | SHA256:6A46272F75406C880442DCE34A3191725EED69C0368A4EC61D56DDA055388190 | |||
| 2392 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | der | |
MD5:440078A42A723CA473F838A1A2319FB5 | SHA256:382F1B09B7BDFBB35B810AC670E11CB54BF4F50FB6ACB6D3608E49778E9B2C60 | |||
| 2392 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\50CD3D75D026C82E2E718570BD6F44D0_D222662A57BAA60D2F5EA0D2CC7B2F1C | der | |
MD5:32F99536F99959AACABBB96CB04155E5 | SHA256:35164D018C5FB56EA7CF90C955C79DDFD7F7241991D31426CDD12A5FD979C707 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
147
DNS requests
225
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3944 | iexplore.exe | GET | 304 | 8.238.30.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a5256b7cd0a73053 | US | — | — | whitelisted |
3492 | iexplore.exe | GET | 304 | 67.27.159.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?7b4d5311b636771a | US | — | — | whitelisted |
3944 | iexplore.exe | GET | 304 | 8.238.30.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?39b0d86c07908f07 | US | — | — | whitelisted |
3944 | iexplore.exe | GET | 304 | 8.238.30.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6debcfdda257cfea | US | — | — | whitelisted |
2392 | iexplore.exe | GET | 200 | 8.238.30.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8b1d7f45eceaeba4 | US | compressed | 4.70 Kb | whitelisted |
2392 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQrHR6YzPN2BNbByL0VoiTIBBMAOAQUCrwIKReMpTlteg7OM8cus%2B37w3oCEAzQqL7GMs%2FmReygqbCE%2Bxw%3D | US | der | 314 b | whitelisted |
3492 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
2392 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | US | der | 471 b | whitelisted |
3492 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
2392 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAfy81yHqHeveu%2FpR5k1Jb0%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2392 | iexplore.exe | 140.82.121.3:443 | — | GITHUB | US | suspicious |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2392 | iexplore.exe | 8.238.30.126:80 | ctldl.windowsupdate.com | LEVEL3 | US | suspicious |
2392 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2392 | iexplore.exe | 185.199.110.133:443 | objects.githubusercontent.com | FASTLY | US | malicious |
3492 | iexplore.exe | 92.123.104.34:443 | www.bing.com | Akamai International B.V. | DE | suspicious |
3284 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2392 | iexplore.exe | 13.107.5.80:443 | api.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
objects.githubusercontent.com |
| shared |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
r.bing.com |
| whitelisted |
th.bing.com |
| whitelisted |
login.microsoftonline.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1900 | msedge.exe | Potential Corporate Privacy Violation | AV POLICY Observed TikTok Domain in TLS SNI (tiktok.com) |