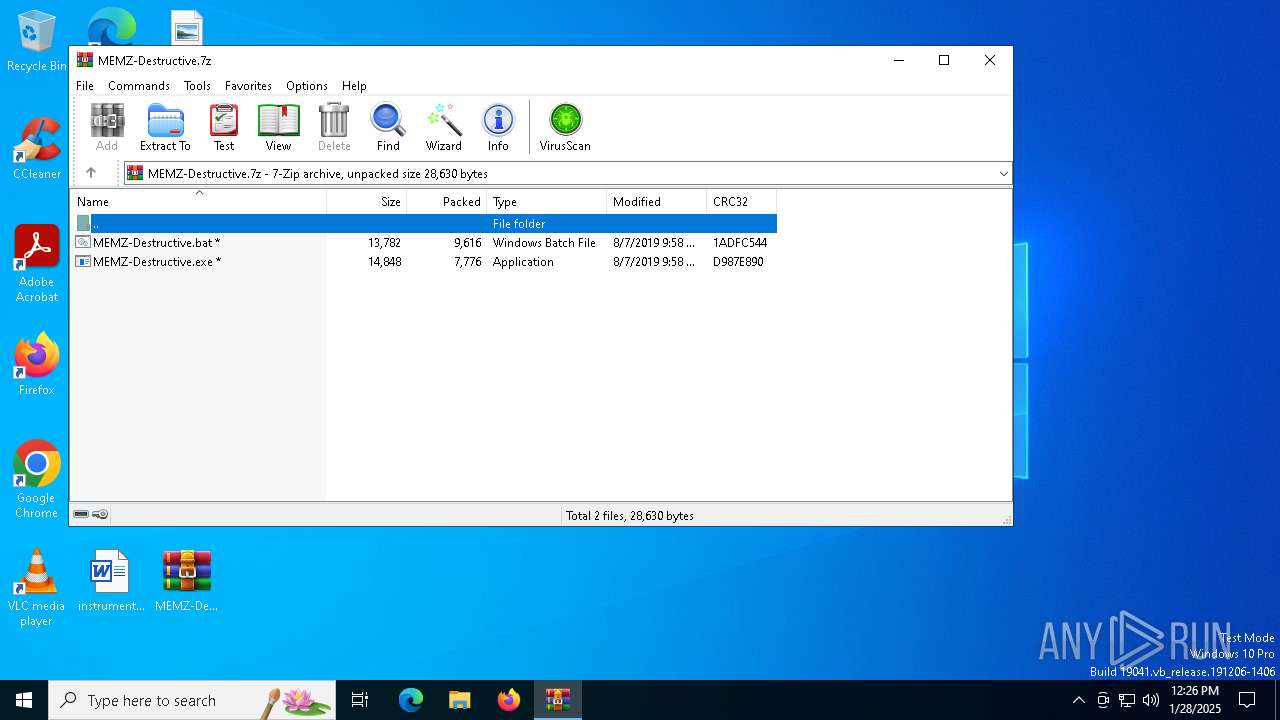
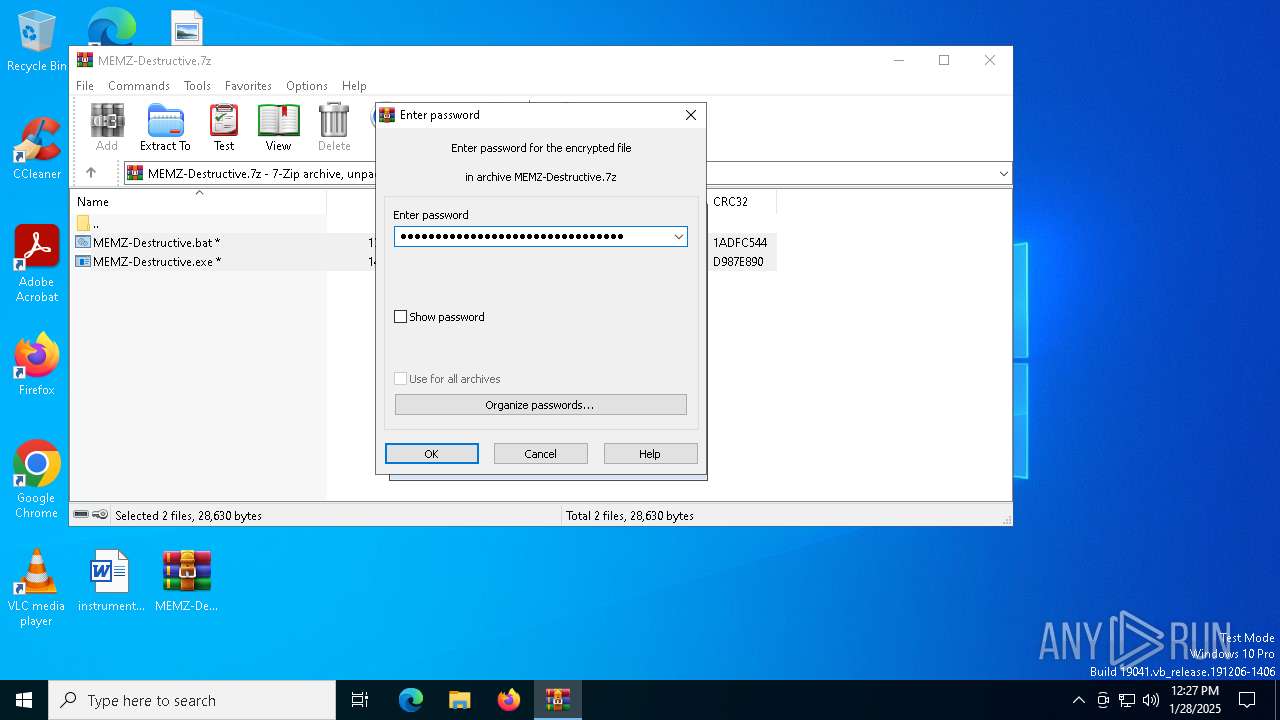
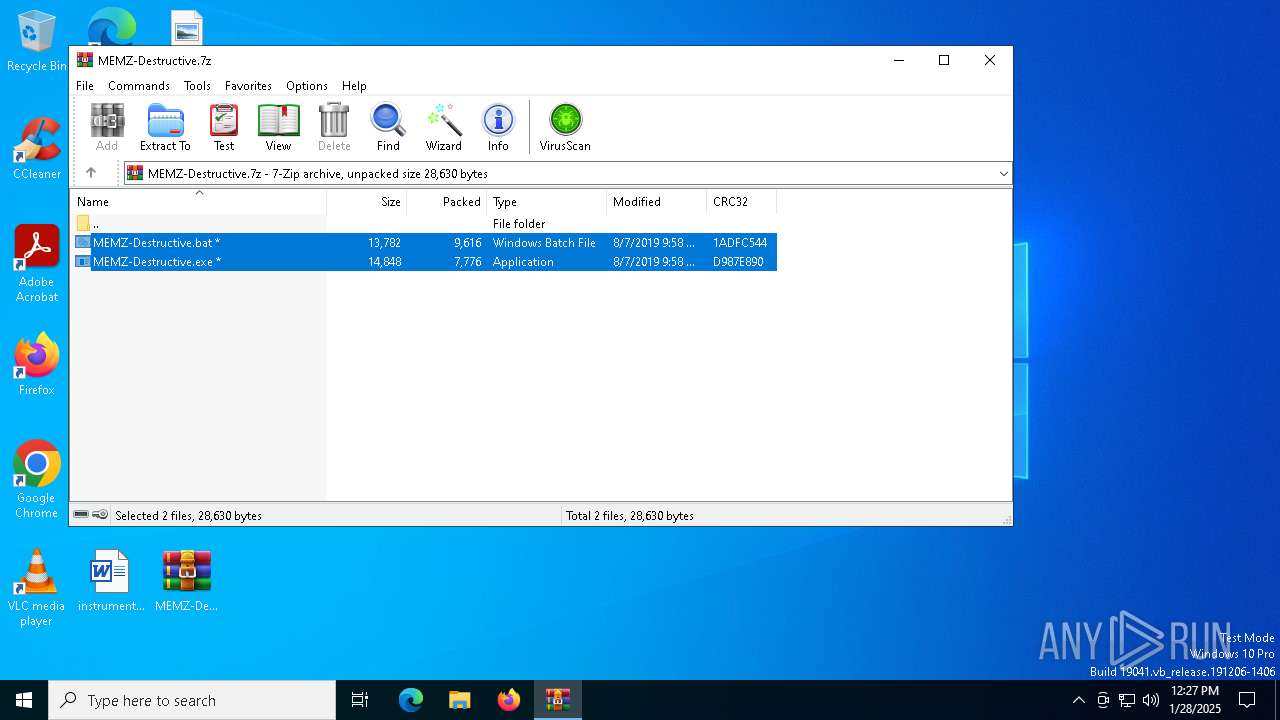
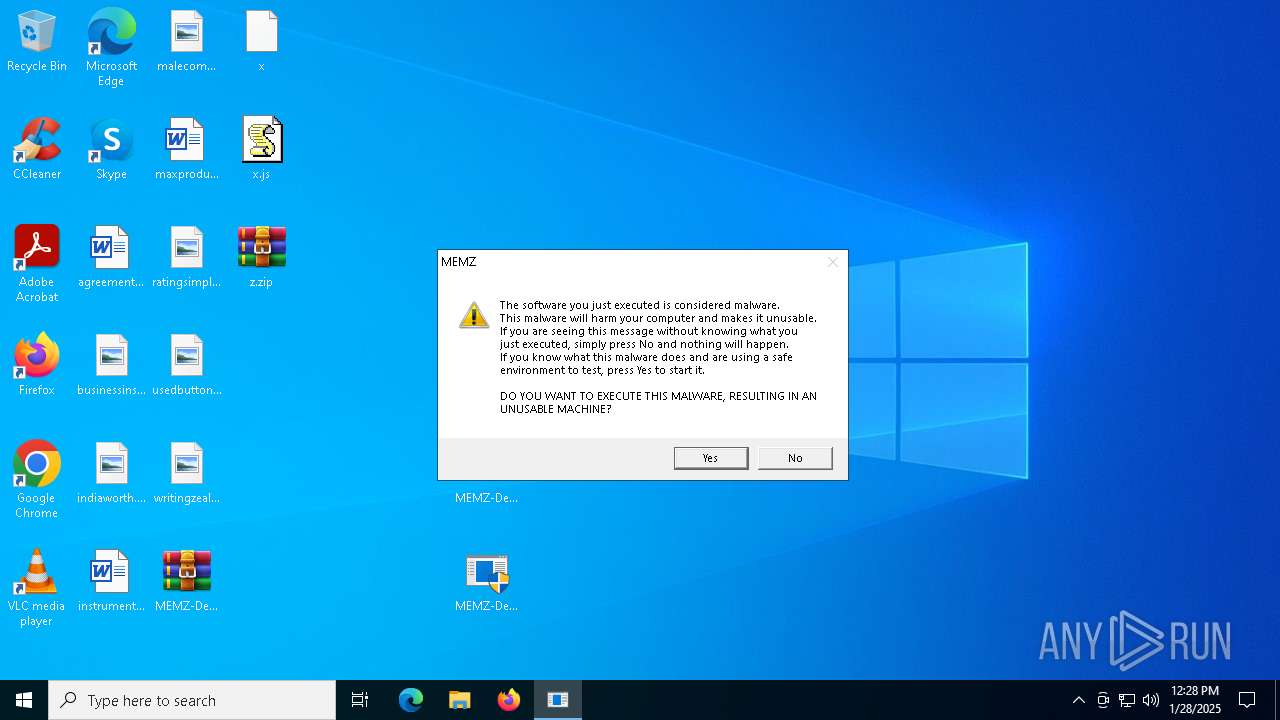
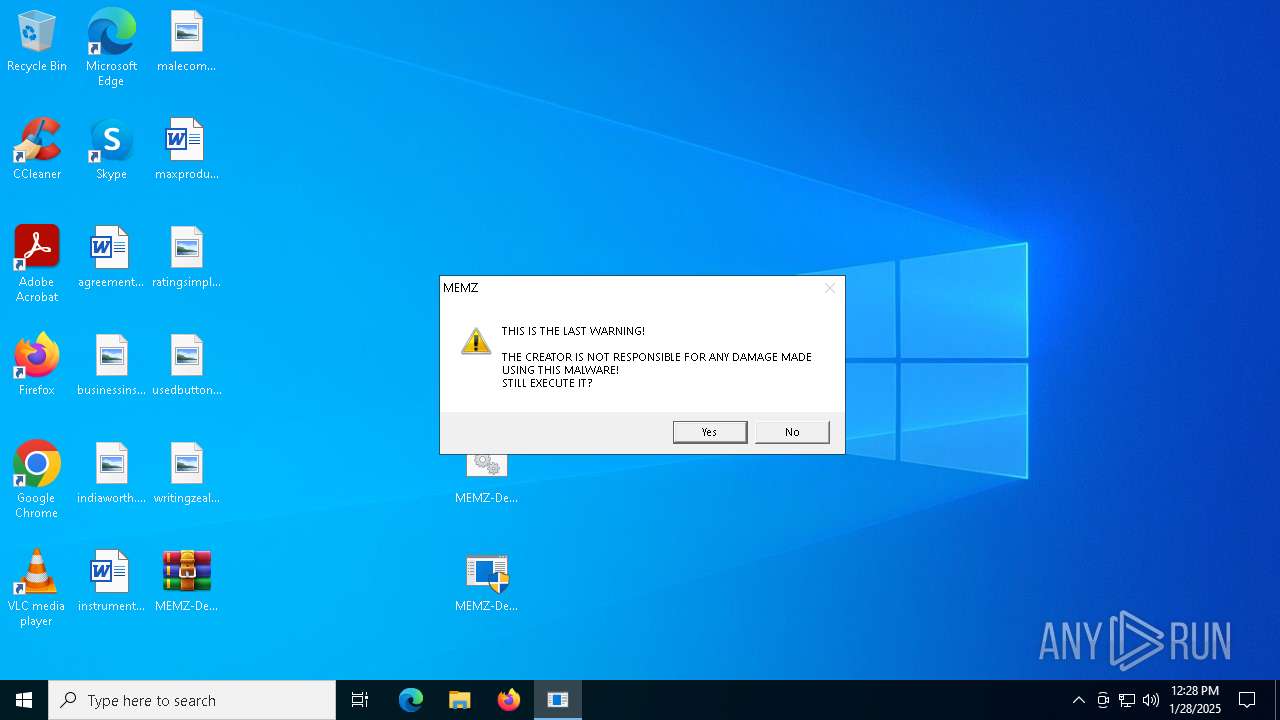
| File name: | MEMZ-Destructive.7z |
| Full analysis: | https://app.any.run/tasks/dac334c1-55b8-49da-95cd-35cdc0fde094 |
| Verdict: | Malicious activity |
| Analysis date: | January 28, 2025, 12:25:54 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | D91A65636B8D4B7437983E064E2580FA |
| SHA1: | 2BFAF387D22B7E9C1A54C35D8AB33FA84006ECE3 |
| SHA256: | C547F9193B8FCB681DBB93968D54AC9912901097E1912FF7AD11C5A9EE13062C |
| SSDEEP: | 384:CxpNbARMGzvkdrUUAhybY4GfheFQb4M4ecf3iQ/FF87u20VoDWXeQT:Cxp6RLzMtUUVMsFQb4ycfiQ/o10XeQT |
MALICIOUS
Uses base64 encoding (SCRIPT)
- cscript.exe (PID: 4044)
Gets a file object corresponding to the file in a specified path (SCRIPT)
- cscript.exe (PID: 4044)
SUSPICIOUS
The process executes JS scripts
- cmd.exe (PID: 5588)
Script creates XML DOM node (SCRIPT)
- cscript.exe (PID: 4044)
Creates XML DOM element (SCRIPT)
- cscript.exe (PID: 4044)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- cscript.exe (PID: 4044)
Sets XML DOM element text (SCRIPT)
- cscript.exe (PID: 4044)
Saves data to a binary file (SCRIPT)
- cscript.exe (PID: 4044)
Executable content was dropped or overwritten
- cscript.exe (PID: 4044)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 4044)
Writes binary data to a Stream object (SCRIPT)
- cscript.exe (PID: 4044)
Creates a Folder object (SCRIPT)
- cscript.exe (PID: 4044)
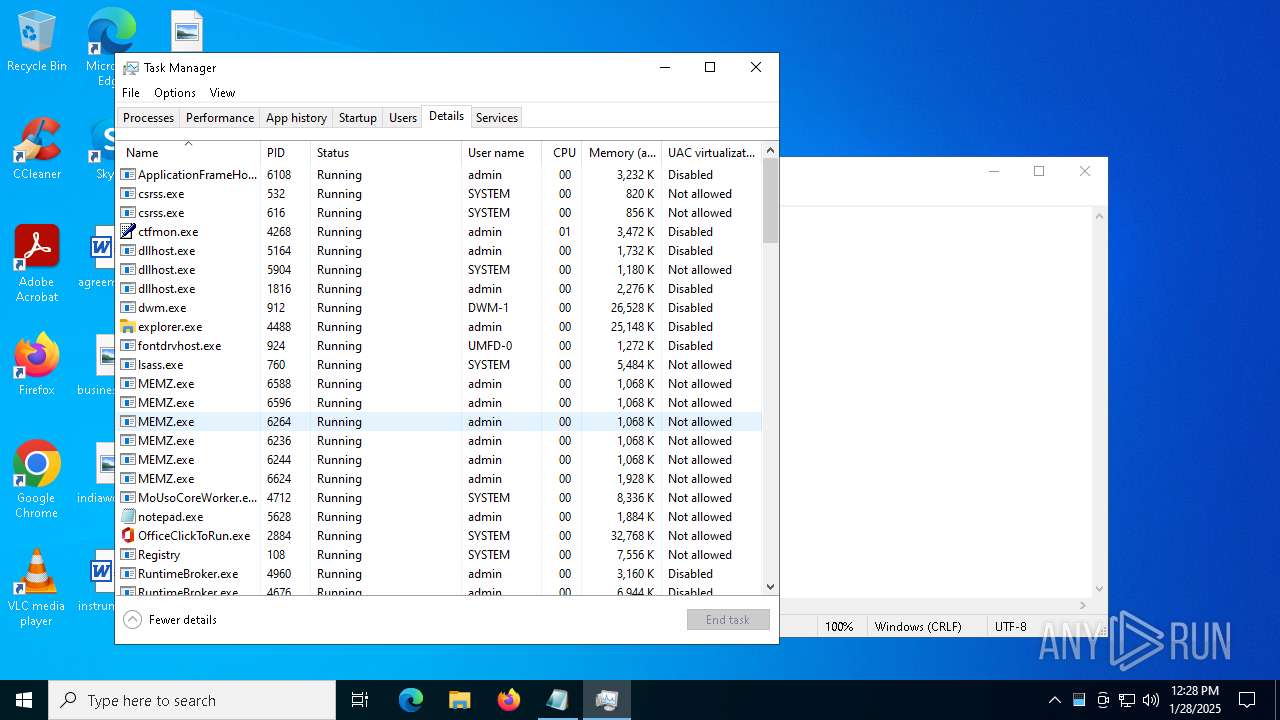
Reads security settings of Internet Explorer
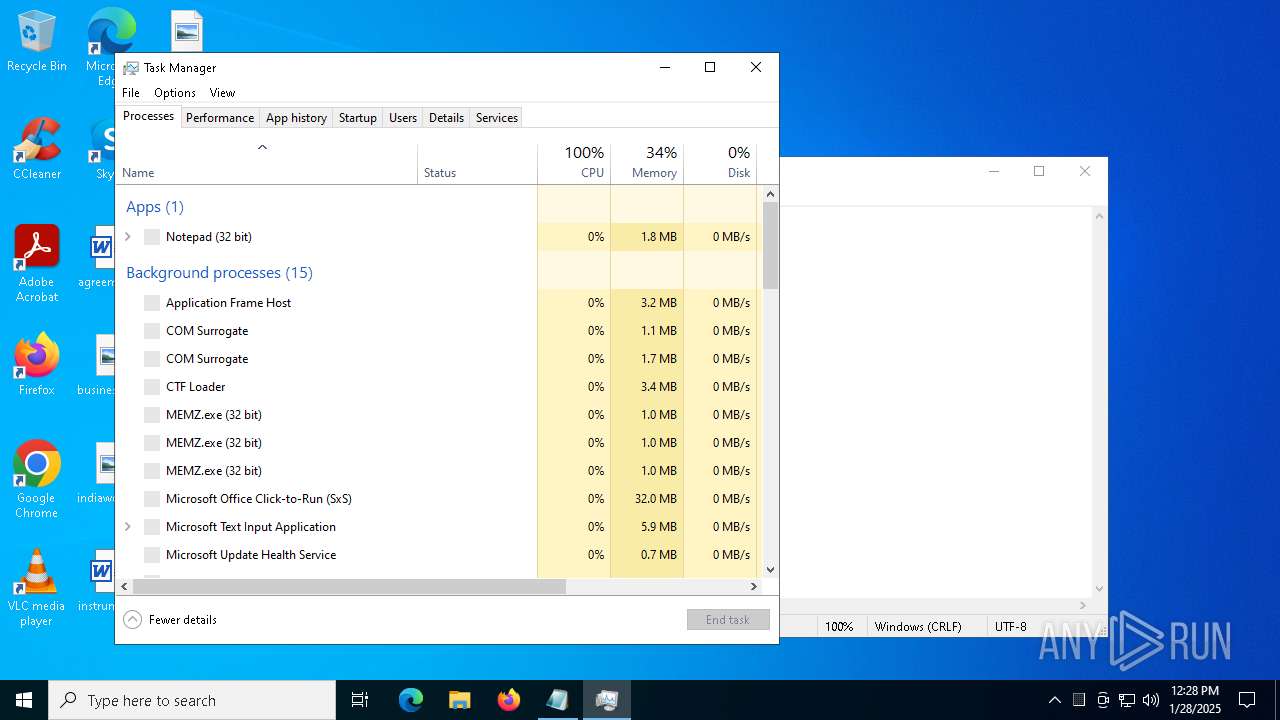
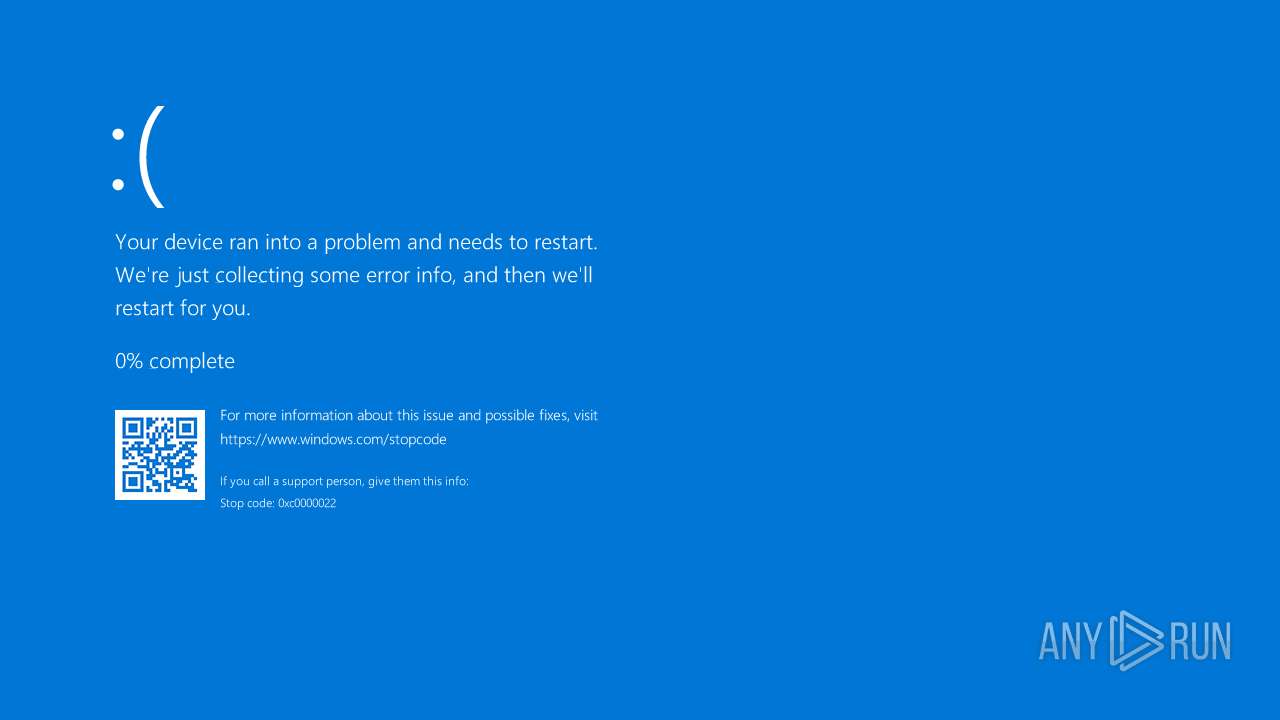
- MEMZ.exe (PID: 6424)
- MEMZ.exe (PID: 6624)
Application launched itself
- MEMZ.exe (PID: 6424)
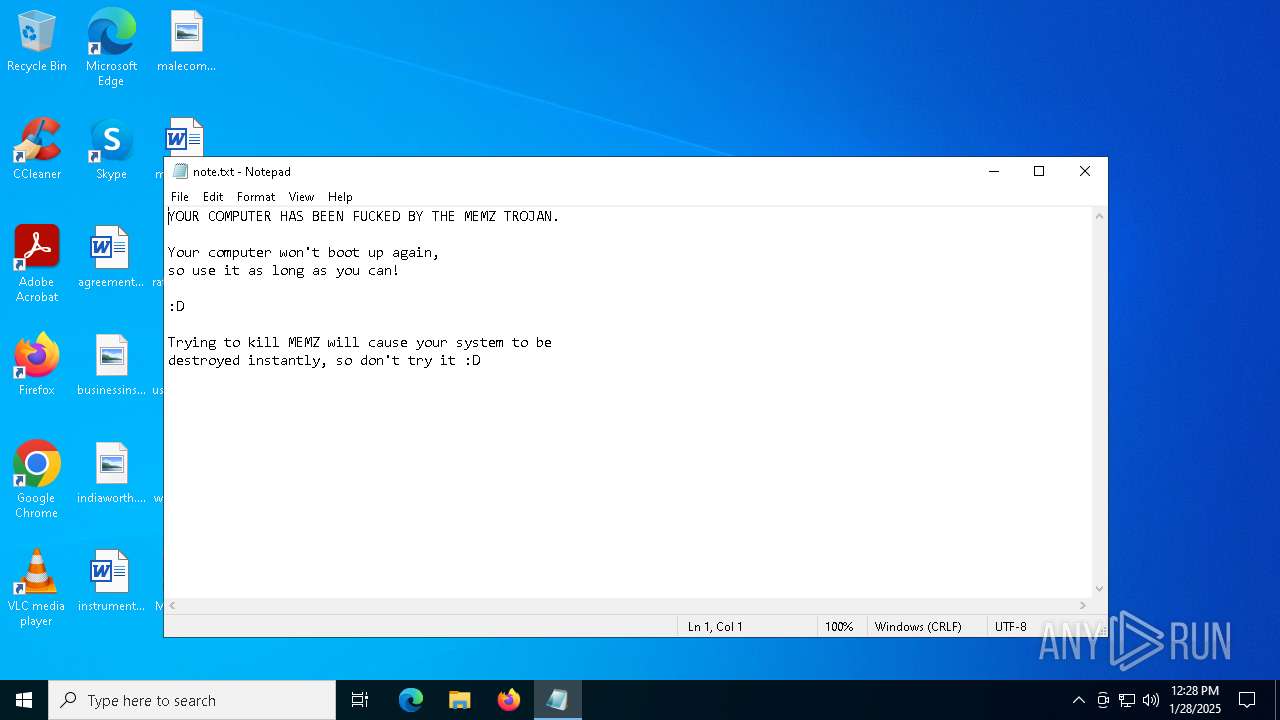
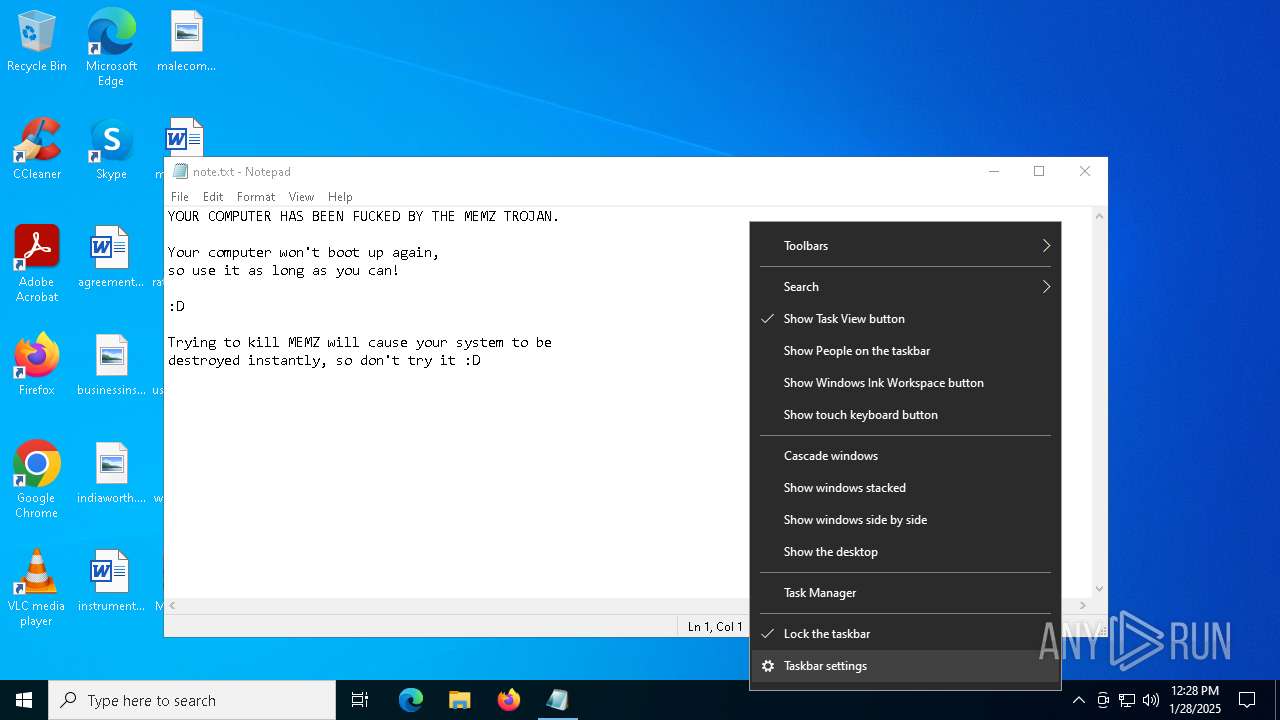
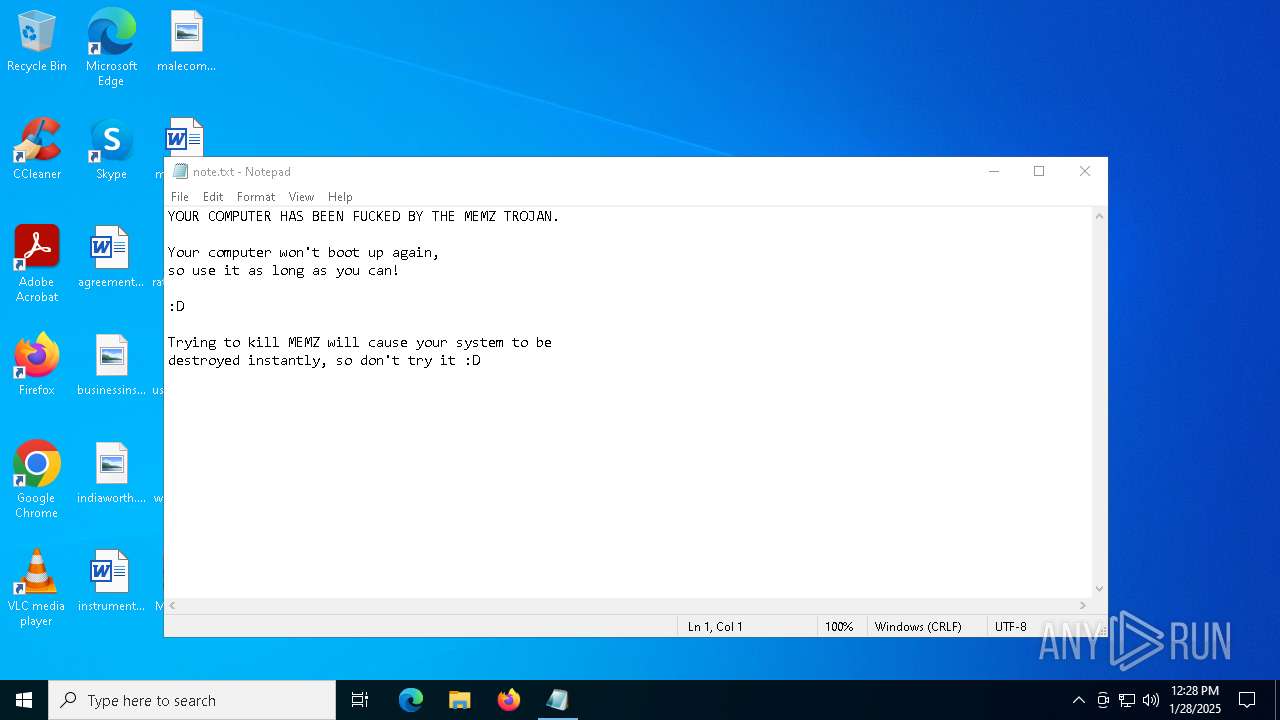
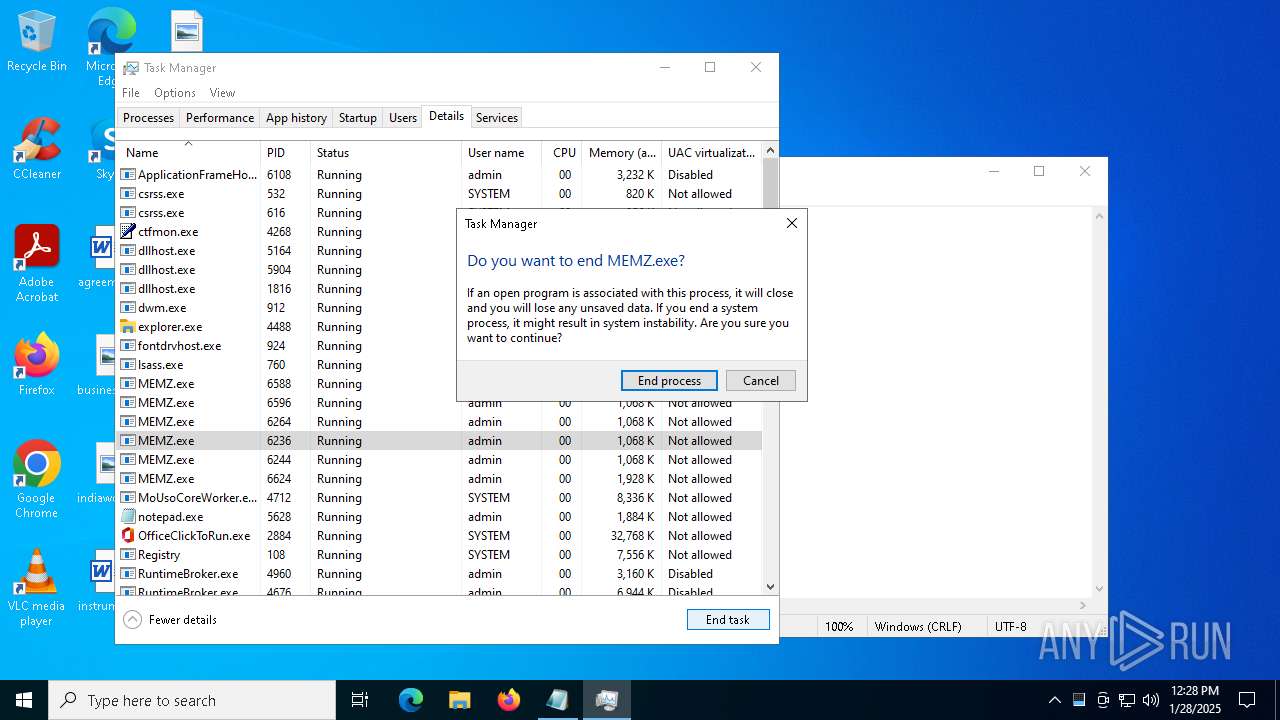
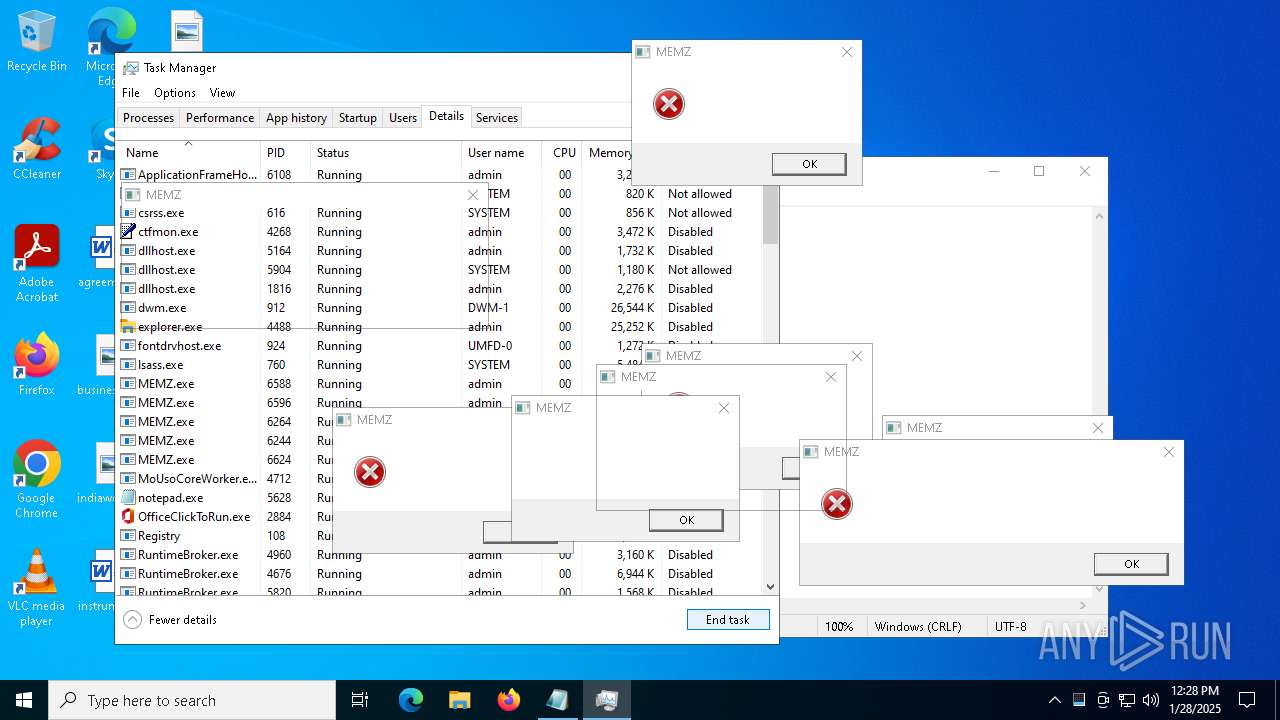
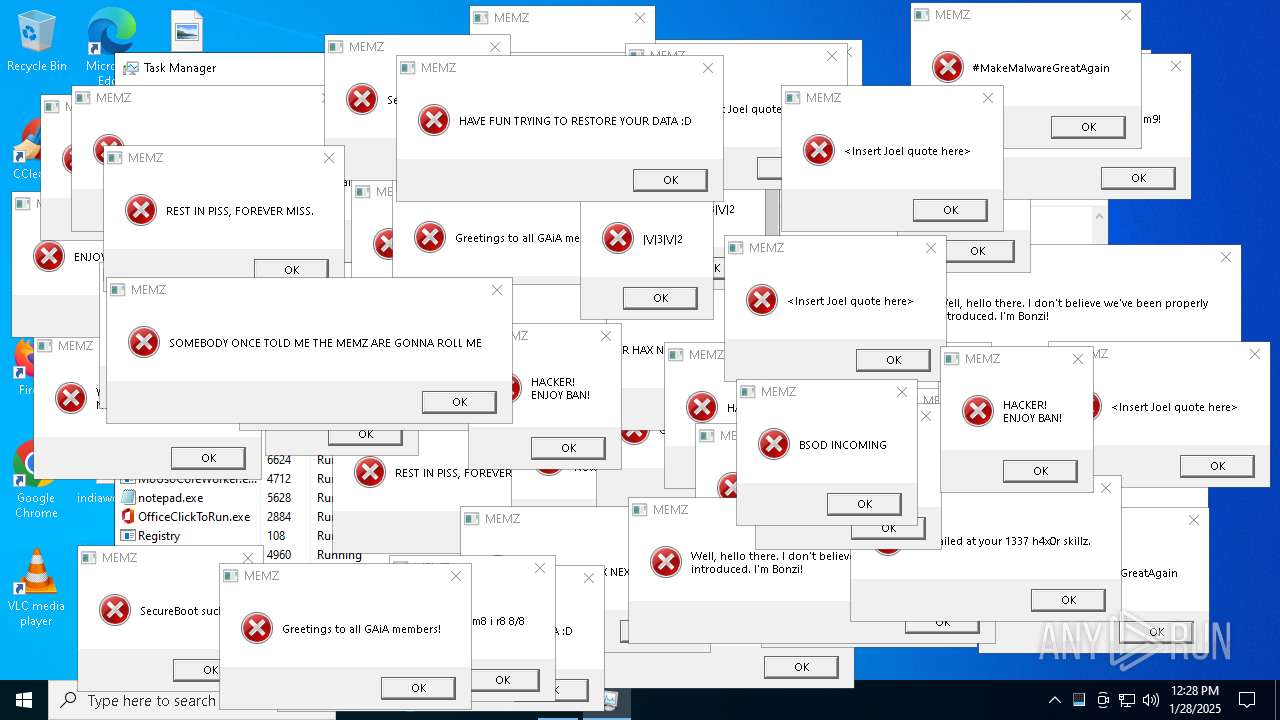
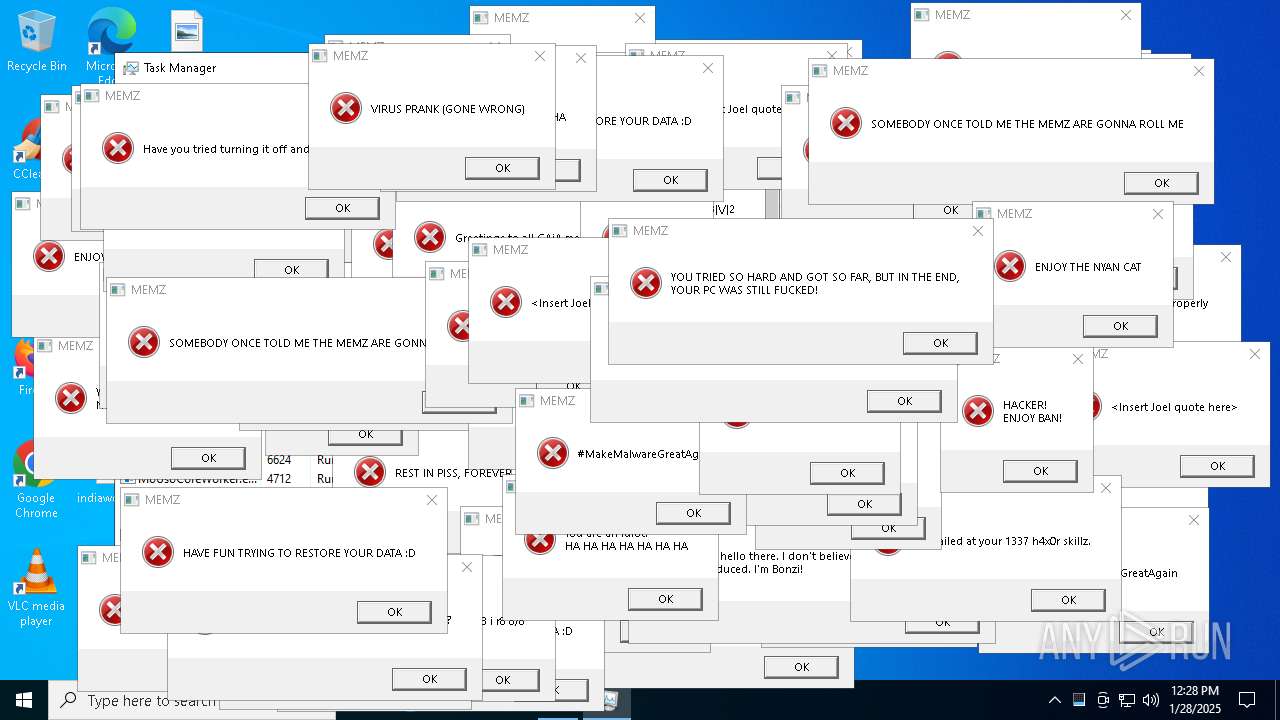
Start notepad (likely ransomware note)
- MEMZ.exe (PID: 6624)
Creates file in the systems drive root
- MEMZ.exe (PID: 6624)
- notepad.exe (PID: 5628)
There is functionality for taking screenshot (YARA)
- MEMZ.exe (PID: 6588)
- MEMZ.exe (PID: 6596)
INFO
Manual execution by a user
- cmd.exe (PID: 5588)
- Taskmgr.exe (PID: 6708)
- Taskmgr.exe (PID: 6876)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5448)
Reads security settings of Internet Explorer
- cscript.exe (PID: 4044)
- notepad.exe (PID: 5628)
- Taskmgr.exe (PID: 6876)
Creates files or folders in the user directory
- cscript.exe (PID: 4044)
Checks supported languages
- MEMZ.exe (PID: 6424)
- MEMZ.exe (PID: 6264)
- MEMZ.exe (PID: 6236)
- MEMZ.exe (PID: 6244)
- MEMZ.exe (PID: 6624)
- MEMZ.exe (PID: 6588)
- MEMZ.exe (PID: 6596)
Process checks computer location settings
- MEMZ.exe (PID: 6424)
- MEMZ.exe (PID: 6624)
Reads the computer name
- MEMZ.exe (PID: 6624)
- MEMZ.exe (PID: 6424)
- MEMZ.exe (PID: 6244)
- MEMZ.exe (PID: 6596)
- MEMZ.exe (PID: 6588)
- MEMZ.exe (PID: 6264)
Reads the machine GUID from the registry
- MEMZ.exe (PID: 6244)
- MEMZ.exe (PID: 6588)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2019:08:07 09:58:42+00:00 |
| ArchivedFileName: | MEMZ-Destructive.bat |
Total processes
148
Monitored processes
16
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3524 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4044 | cscript x.js | C:\Windows\System32\cscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 4668 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 5032 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 5448 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\MEMZ-Destructive.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 5588 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\MEMZ-Destructive.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5628 | "C:\Windows\System32\notepad.exe" \note.txt | C:\Windows\SysWOW64\notepad.exe | — | MEMZ.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6236 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 6244 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 6264 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
Total events
5 356
Read events
5 333
Write events
22
Delete events
1
Modification events
| (PID) Process: | (5448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\MEMZ-Destructive.7z | |||
| (PID) Process: | (5448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (5448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
2
Suspicious files
2
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6624 | MEMZ.exe | \Device\Harddisk0\DR0 | — | |
MD5:— | SHA256:— | |||
| 4044 | cscript.exe | C:\Users\admin\Desktop\z.zip | compressed | |
MD5:63EE4412B95D7AD64C54B4BA673470A7 | SHA256:44C1857B1C4894B3DFBACCBE04905652E634283DCF6B06C25A74B17021E2A268 | |||
| 5448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb5448.48454\MEMZ-Destructive.exe | executable | |
MD5:19DBEC50735B5F2A72D4199C4E184960 | SHA256:A3D5715A81F2FBEB5F76C88C9C21EEEE87142909716472F911FF6950C790C24D | |||
| 5588 | cmd.exe | C:\Users\admin\Desktop\x | text | |
MD5:CFC1E7E18B9F9B70310C88F922E59B29 | SHA256:3DCF309E134AE67CAED27FA52782267C90646B405C4A9594041B284733B8E346 | |||
| 5448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb5448.48454\MEMZ-Destructive.bat | text | |
MD5:4E2A7F369378A76D1DF4D8C448F712AF | SHA256:5E2CD213FF47B7657ABD9167C38FFD8B53C13261FE22ADDDEA92B5A2D9E320AD | |||
| 6876 | Taskmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\3534848bb9f4cb71\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
| 4044 | cscript.exe | C:\Users\admin\AppData\Roaming\MEMZ.exe | executable | |
MD5:19DBEC50735B5F2A72D4199C4E184960 | SHA256:A3D5715A81F2FBEB5F76C88C9C21EEEE87142909716472F911FF6950C790C24D | |||
| 6624 | MEMZ.exe | C:\note.txt | binary | |
MD5:AFA6955439B8D516721231029FB9CA1B | SHA256:8E9F20F6864C66576536C0B866C6FFDCF11397DB67FE120E972E244C3C022270 | |||
| 5588 | cmd.exe | C:\Users\admin\Desktop\x.js | text | |
MD5:D94C93F882CF030ED9D66CC35796731D | SHA256:F7941E6BE49D757B46B9D6FB5ECB15392EC36A64E8906692D2EEB2BA9FC67CB6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
32
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5872 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6968 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6968 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6308 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5872 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3464 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5064 | SearchApp.exe | 92.123.104.30:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1076 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |