| File name: | Sample_5bfd1df5881d4511b4af1fe8.exe |
| Full analysis: | https://app.any.run/tasks/d80a6a03-bcf6-4292-94ce-f31bfe56fc06 |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2018, 15:18:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | CD0F7F29E337F2EBE455BA4A85FB2B70 |
| SHA1: | 1C719C8A8262A07682D6DFA1BFA595D5435F06B8 |
| SHA256: | C546B8DC641F33E24D6BBFEC825854B4E5A9B104C13153CC8F110E382A897D47 |
| SSDEEP: | 6144:aDjjxPFc3D9DGxPFcc+3DXm3LueuPxPFc3D9DGxPFcc+31Xm3ZDD4nomq:g8vx3Ovx3k4nI |
MALICIOUS
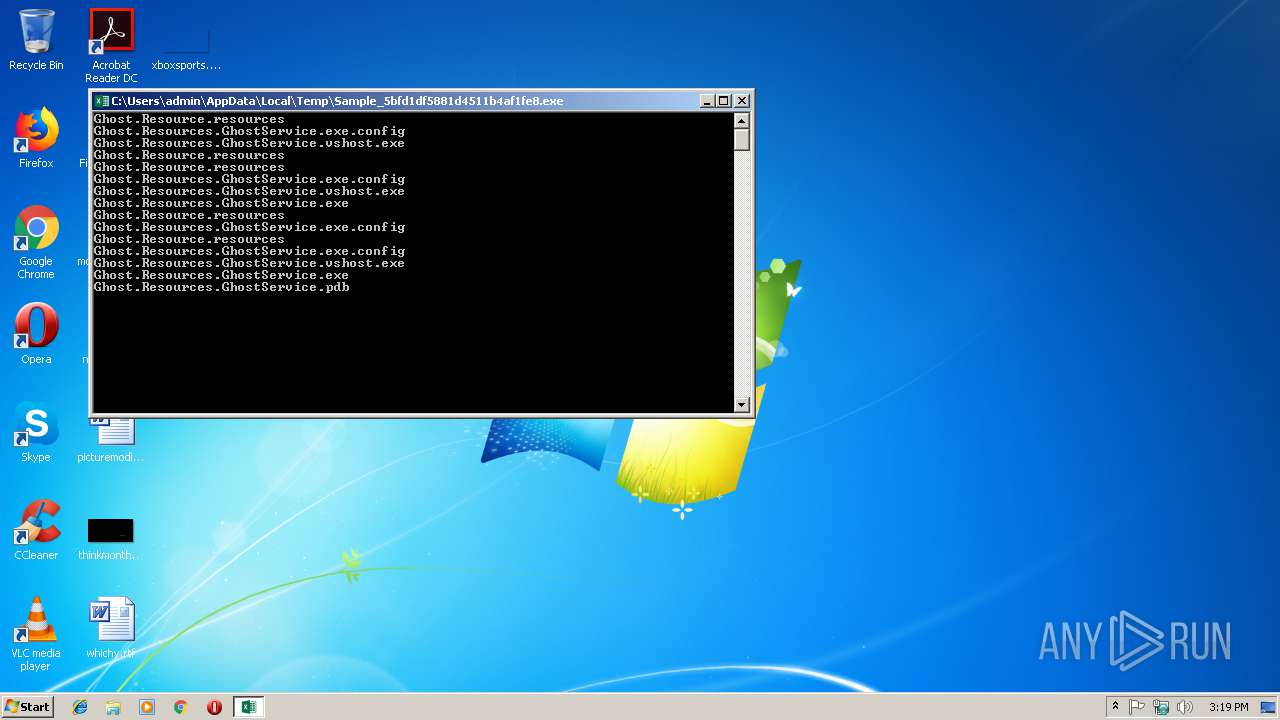
Application was dropped or rewritten from another process
- GhostService.exe (PID: 2972)
- GhostForm.exe (PID: 2820)
Loads dropped or rewritten executable
- GhostService.exe (PID: 2972)
- GhostForm.exe (PID: 2820)
SUSPICIOUS
Creates files in the user directory
- Sample_5bfd1df5881d4511b4af1fe8.exe (PID: 3896)
Executable content was dropped or overwritten
- Sample_5bfd1df5881d4511b4af1fe8.exe (PID: 3896)
- GhostService.exe (PID: 2972)
Starts CMD.EXE for commands execution
- Sample_5bfd1df5881d4511b4af1fe8.exe (PID: 3896)
Starts SC.EXE for service management
- cmd.exe (PID: 4008)
INFO
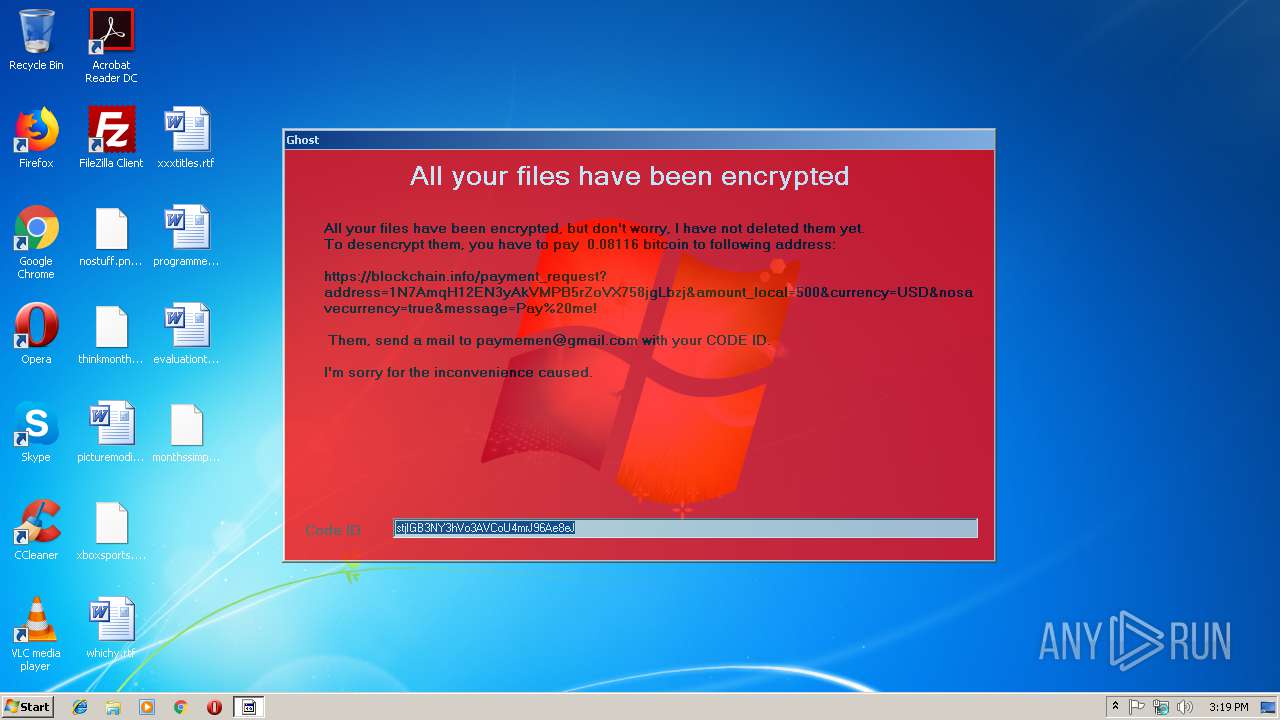
Dropped object may contain Bitcoin addresses
- Sample_5bfd1df5881d4511b4af1fe8.exe (PID: 3896)
- GhostService.exe (PID: 2972)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:10:07 17:26:04+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 499712 |
| InitializedDataSize: | 151040 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x7bf9e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | Ghost |
| FileVersion: | 1.0.0.0 |
| InternalName: | Ghost.exe |
| LegalCopyright: | Copyright © 2018 |
| OriginalFileName: | Ghost.exe |
| ProductName: | Ghost |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_CUI |
| Compilation Date: | 07-Oct-2018 15:26:04 |
| Debug artifacts: |
|
| FileDescription: | Ghost |
| FileVersion: | 1.0.0.0 |
| InternalName: | Ghost.exe |
| LegalCopyright: | Copyright © 2018 |
| OriginalFilename: | Ghost.exe |
| ProductName: | Ghost |
| ProductVersion: | 1.0.0.0 |
| Assembly Version: | 1.0.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 07-Oct-2018 15:26:04 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00002000 | 0x00079FA4 | 0x0007A000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.88369 |
.rsrc | 0x0007C000 | 0x00024B68 | 0x00024C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 3.51622 |
.reloc | 0x000A2000 | 0x0000000C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.10191 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.03363 | 3087 | UNKNOWN | UNKNOWN | RT_MANIFEST |
2 | 4.65199 | 1128 | UNKNOWN | UNKNOWN | RT_ICON |
3 | 4.41591 | 2440 | UNKNOWN | UNKNOWN | RT_ICON |
4 | 3.89581 | 4264 | UNKNOWN | UNKNOWN | RT_ICON |
5 | 3.43032 | 9640 | UNKNOWN | UNKNOWN | RT_ICON |
6 | 3.17734 | 16936 | UNKNOWN | UNKNOWN | RT_ICON |
7 | 2.90561 | 38056 | UNKNOWN | UNKNOWN | RT_ICON |
8 | 2.77271 | 67624 | UNKNOWN | UNKNOWN | RT_ICON |
9 | 7.72407 | 5780 | UNKNOWN | UNKNOWN | RT_ICON |
32512 | 2.98029 | 118 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
Imports
mscoree.dll |
Total processes
41
Monitored processes
6
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2732 | SC CREATE "GhostService" password= "FromHell" DisplayName= "Ghost" start= "auto" binPath= "C:\Users\admin\AppData\Roaming\Ghost\GhostService.exe" | C:\Windows\system32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2820 | "C:\GhostForm.exe" | C:\GhostForm.exe | — | GhostService.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: GhostForm Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2972 | C:\Users\admin\AppData\Roaming\Ghost\GhostService.exe | C:\Users\admin\AppData\Roaming\Ghost\GhostService.exe | services.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Description: GhostService Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3472 | "C:\Users\admin\AppData\Local\Temp\Sample_5bfd1df5881d4511b4af1fe8.exe" | C:\Users\admin\AppData\Local\Temp\Sample_5bfd1df5881d4511b4af1fe8.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Ghost Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3896 | "C:\Users\admin\AppData\Local\Temp\Sample_5bfd1df5881d4511b4af1fe8.exe" | C:\Users\admin\AppData\Local\Temp\Sample_5bfd1df5881d4511b4af1fe8.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Ghost Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 4008 | cmd /c ""C:\Users\admin\AppData\Roaming\Ghost\Ghost.bat" " | C:\Windows\system32\cmd.exe | — | Sample_5bfd1df5881d4511b4af1fe8.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
429
Read events
421
Write events
8
Delete events
0
Modification events
| (PID) Process: | (3896) Sample_5bfd1df5881d4511b4af1fe8.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3896) Sample_5bfd1df5881d4511b4af1fe8.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2972) GhostService.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\eventlog\GhostLog |
| Operation: | write | Name: | MaxSize |
Value: 524288 | |||
| (PID) Process: | (2972) GhostService.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\eventlog\GhostLog |
| Operation: | write | Name: | AutoBackupLogFiles |
Value: 0 | |||
| (PID) Process: | (2972) GhostService.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\eventlog\GhostLog\GhostLog |
| Operation: | write | Name: | EventMessageFile |
Value: C:\Windows\Microsoft.NET\Framework\v4.0.30319\EventLogMessages.dll | |||
| (PID) Process: | (2972) GhostService.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\eventlog\GhostLog\Ghost |
| Operation: | write | Name: | EventMessageFile |
Value: C:\Windows\Microsoft.NET\Framework\v4.0.30319\EventLogMessages.dll | |||
Executable files
6
Suspicious files
21
Text files
3
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3896 | Sample_5bfd1df5881d4511b4af1fe8.exe | C:\Users\admin\AppData\Roaming\Ghost\Ghost.bat | text | |
MD5:— | SHA256:— | |||
| 3896 | Sample_5bfd1df5881d4511b4af1fe8.exe | C:\Users\admin\AppData\Roaming\Ghost\GhostService.pdb | pdb | |
MD5:— | SHA256:— | |||
| 3896 | Sample_5bfd1df5881d4511b4af1fe8.exe | C:\Users\admin\AppData\Roaming\Ghost\GhostService.exe | executable | |
MD5:— | SHA256:— | |||
| 2820 | GhostForm.exe | C:\Users\admin\Desktop\nostuff.png.Ghost | binary | |
MD5:— | SHA256:— | |||
| 2972 | GhostService.exe | C:\autoexec.bat.Ghost | binary | |
MD5:— | SHA256:— | |||
| 2820 | GhostForm.exe | C:\Users\admin\Desktop\monthssimply.png.Ghost | binary | |
MD5:— | SHA256:— | |||
| 2820 | GhostForm.exe | C:\Users\admin\Documents\Outlook Files\honey@pot.com.pst.Ghost | binary | |
MD5:— | SHA256:— | |||
| 2820 | GhostForm.exe | C:\Users\admin\Desktop\thinkmonth.jpg.Ghost | binary | |
MD5:— | SHA256:— | |||
| 2820 | GhostForm.exe | C:\Users\admin\Desktop\xboxsports.png.Ghost | binary | |
MD5:— | SHA256:— | |||
| 2820 | GhostForm.exe | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst.Ghost | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.12312312eewfef231.com |
| unknown |