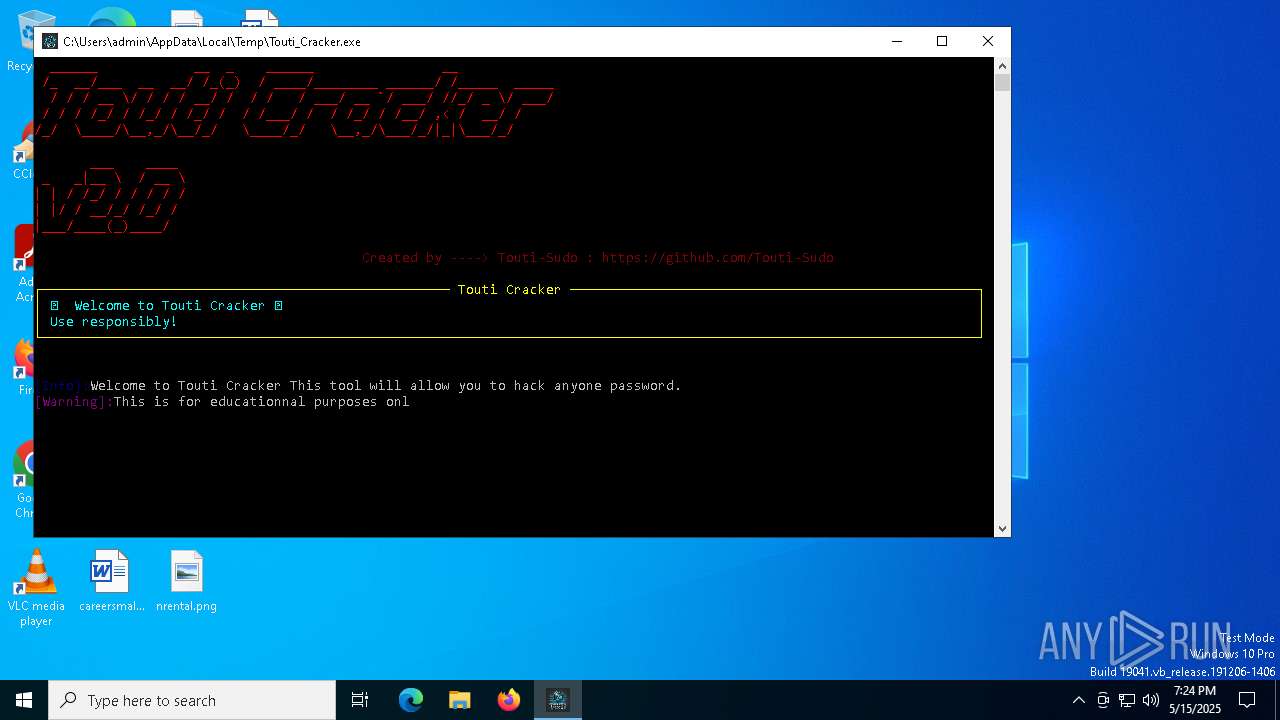
| File name: | Touti_Cracker.exe |
| Full analysis: | https://app.any.run/tasks/7e6d3114-9010-43fe-a80c-8363deafb744 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2025, 19:23:46 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 7 sections |
| MD5: | 4FD9B6C94B08CBB1BE64F492E0AA4B61 |
| SHA1: | 9FDEE7D97E7032EF88DBA64C3286EEA7E5D61AE5 |
| SHA256: | C53ED074235DB4C2CA54FA9337044ABFEA1B14A1C337D9E561E48F6A1C145F13 |
| SSDEEP: | 393216:Vel5nEV1NTy7z0sg6XwQGeETsyts+ohVI4nd2a1:Qy3XLQG9SVHnwa |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops python dynamic module
- Touti_Cracker.exe (PID: 7476)
Process drops legitimate windows executable
- Touti_Cracker.exe (PID: 7476)
The process drops C-runtime libraries
- Touti_Cracker.exe (PID: 7476)
Starts CMD.EXE for commands execution
- Touti_Cracker.exe (PID: 7708)
Application launched itself
- Touti_Cracker.exe (PID: 7476)
Loads Python modules
- Touti_Cracker.exe (PID: 7708)
Executable content was dropped or overwritten
- Touti_Cracker.exe (PID: 7476)
Windows service management via SC.EXE
- sc.exe (PID: 8076)
Starts SC.EXE for service management
- cmd.exe (PID: 8060)
INFO
Checks supported languages
- Touti_Cracker.exe (PID: 7476)
- Touti_Cracker.exe (PID: 7708)
Create files in a temporary directory
- Touti_Cracker.exe (PID: 7476)
Reads the computer name
- Touti_Cracker.exe (PID: 7476)
- Touti_Cracker.exe (PID: 7708)
The sample compiled with english language support
- Touti_Cracker.exe (PID: 7476)
PyInstaller has been detected (YARA)
- Touti_Cracker.exe (PID: 7476)
Checks proxy server information
- slui.exe (PID: 7228)
Reads the software policy settings
- slui.exe (PID: 7228)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:04:06 18:36:31+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.42 |
| CodeSize: | 178688 |
| InitializedDataSize: | 135680 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc380 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
135
Monitored processes
9
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 7228 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7476 | "C:\Users\admin\AppData\Local\Temp\Touti_Cracker.exe" | C:\Users\admin\AppData\Local\Temp\Touti_Cracker.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 7484 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Touti_Cracker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7708 | "C:\Users\admin\AppData\Local\Temp\Touti_Cracker.exe" | C:\Users\admin\AppData\Local\Temp\Touti_Cracker.exe | — | Touti_Cracker.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 7800 | C:\WINDOWS\system32\cmd.exe /c "cls" | C:\Windows\System32\cmd.exe | — | Touti_Cracker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8060 | C:\WINDOWS\system32\cmd.exe /c sc query WinDefend | find "RUNNING" | C:\Windows\System32\cmd.exe | — | Touti_Cracker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8076 | sc query WinDefend | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8084 | find "RUNNING" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8124 | C:\WINDOWS\system32\cmd.exe /c "python --version" | C:\Windows\System32\cmd.exe | — | Touti_Cracker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
829
Read events
829
Write events
0
Delete events
0
Modification events
Executable files
51
Suspicious files
10
Text files
455
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7476 | Touti_Cracker.exe | C:\Users\admin\AppData\Local\Temp\_MEI74762\PIL\_imagingmath.cp312-win_amd64.pyd | executable | |
MD5:D80E23C523BEA5ACA6EC702EF6DCBF8D | SHA256:C480EDC4EBD5757B92F543B0589AF0C6FEBF1153992B948322B7E69F2A0EAF61 | |||
| 7476 | Touti_Cracker.exe | C:\Users\admin\AppData\Local\Temp\_MEI74762\VCRUNTIME140_1.dll | executable | |
MD5:68156F41AE9A04D89BB6625A5CD222D4 | SHA256:82A2F9AE1E6146AE3CB0F4BC5A62B7227E0384209D9B1AEF86BBCC105912F7CD | |||
| 7476 | Touti_Cracker.exe | C:\Users\admin\AppData\Local\Temp\_MEI74762\PIL\_imagingft.cp312-win_amd64.pyd | executable | |
MD5:5F882DE78ED697F0E5A3A5252E9A001F | SHA256:ED62B89028C3127FC7B16E36F37FFCFF88E15707442FDE018D40BBEA096F5B86 | |||
| 7476 | Touti_Cracker.exe | C:\Users\admin\AppData\Local\Temp\_MEI74762\_cffi_backend.cp312-win_amd64.pyd | executable | |
MD5:FCB71CE882F99EC085D5875E1228BDC1 | SHA256:86F136553BA301C70E7BADA8416B77EB4A07F76CCB02F7D73C2999A38FA5FA5B | |||
| 7476 | Touti_Cracker.exe | C:\Users\admin\AppData\Local\Temp\_MEI74762\PIL\_imagingtk.cp312-win_amd64.pyd | executable | |
MD5:6469B7315A33774D1C7EF7459058F889 | SHA256:317E4219DE122F058C86F858F11B9510B6D196FD8027DD35352E7784E6968500 | |||
| 7476 | Touti_Cracker.exe | C:\Users\admin\AppData\Local\Temp\_MEI74762\VCRUNTIME140.dll | executable | |
MD5:862F820C3251E4CA6FC0AC00E4092239 | SHA256:36585912E5EAF83BA9FEA0631534F690CCDC2D7BA91537166FE53E56C221E153 | |||
| 7476 | Touti_Cracker.exe | C:\Users\admin\AppData\Local\Temp\_MEI74762\_asyncio.pyd | executable | |
MD5:A577FF6DE2ADD83120127061D7C294A8 | SHA256:8A12F0E5EF034F5C9FF5C506F701A00E3CD16009E2D3431F54EAD15BC138629F | |||
| 7476 | Touti_Cracker.exe | C:\Users\admin\AppData\Local\Temp\_MEI74762\_bz2.pyd | executable | |
MD5:8BD61EA798D1E3EF58548480ED8EE956 | SHA256:D3214E53519B65A07211F44C2BF8C6464B6CD11308561FA48967C8D2E97C1CAC | |||
| 7476 | Touti_Cracker.exe | C:\Users\admin\AppData\Local\Temp\_MEI74762\_ctypes.pyd | executable | |
MD5:FC2DA679024ED27F02ECD1B05CF14CDA | SHA256:AB0A527BEDFD18E11B2FACC003407B6E565F114E010499F73DE35E1B01B6D340 | |||
| 7476 | Touti_Cracker.exe | C:\Users\admin\AppData\Local\Temp\_MEI74762\PIL\_imaging.cp312-win_amd64.pyd | executable | |
MD5:45ED5B175FF3FEB7D39F8482C5E60848 | SHA256:FFADC62922AAC7F93D4EC6F2EB41CD836104F88D86B45E9FC295087FAD7D262E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
22
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.24.77.35:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7992 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7992 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.24.77.35:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7992 | SIHClient.exe | 52.149.20.212:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |