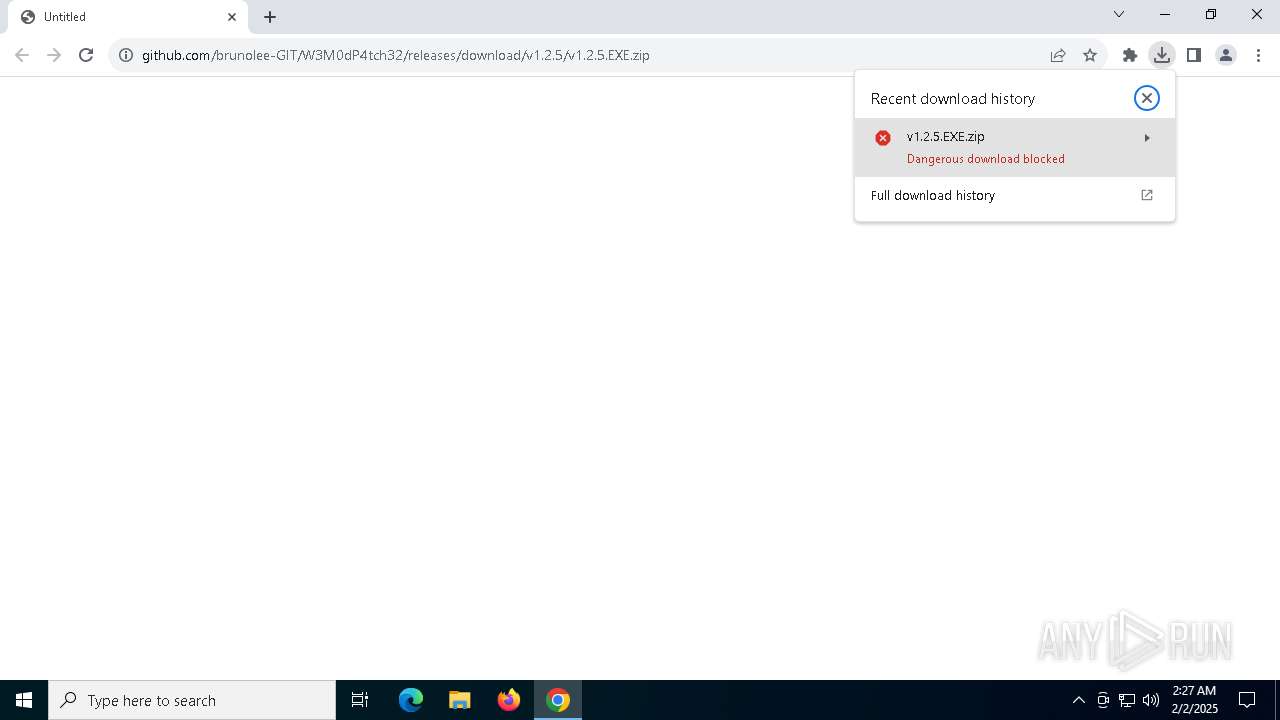
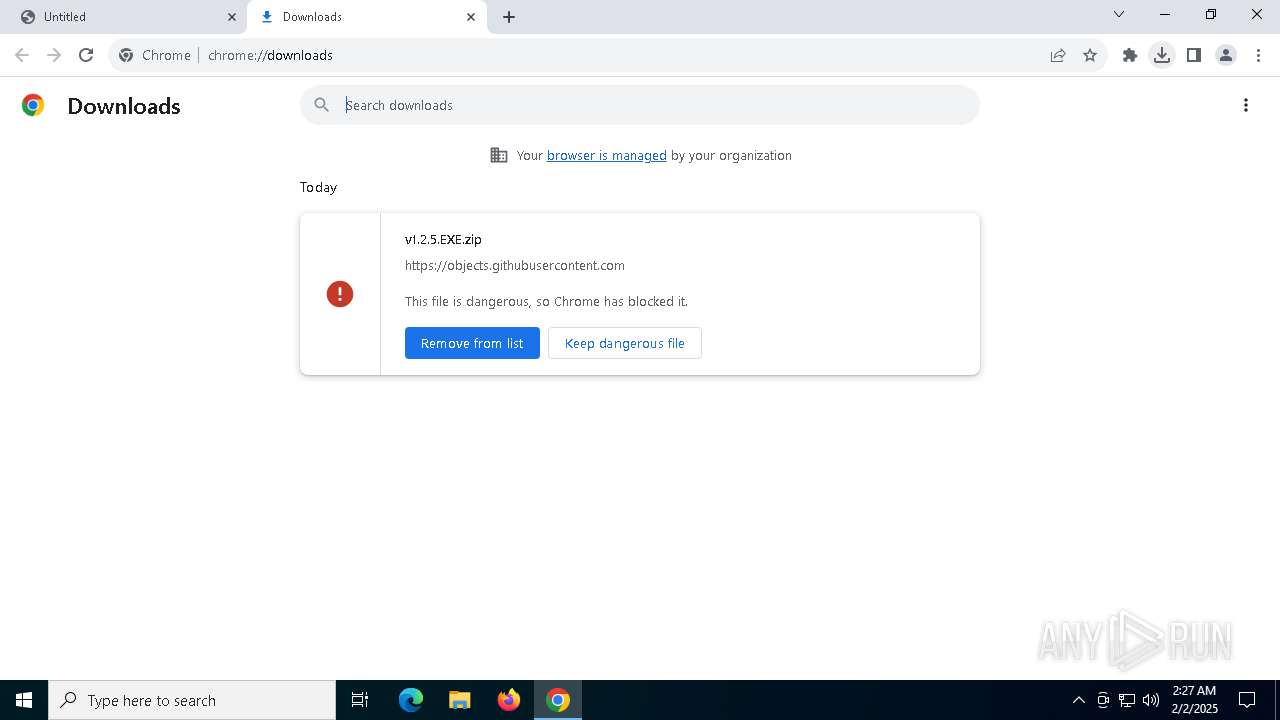
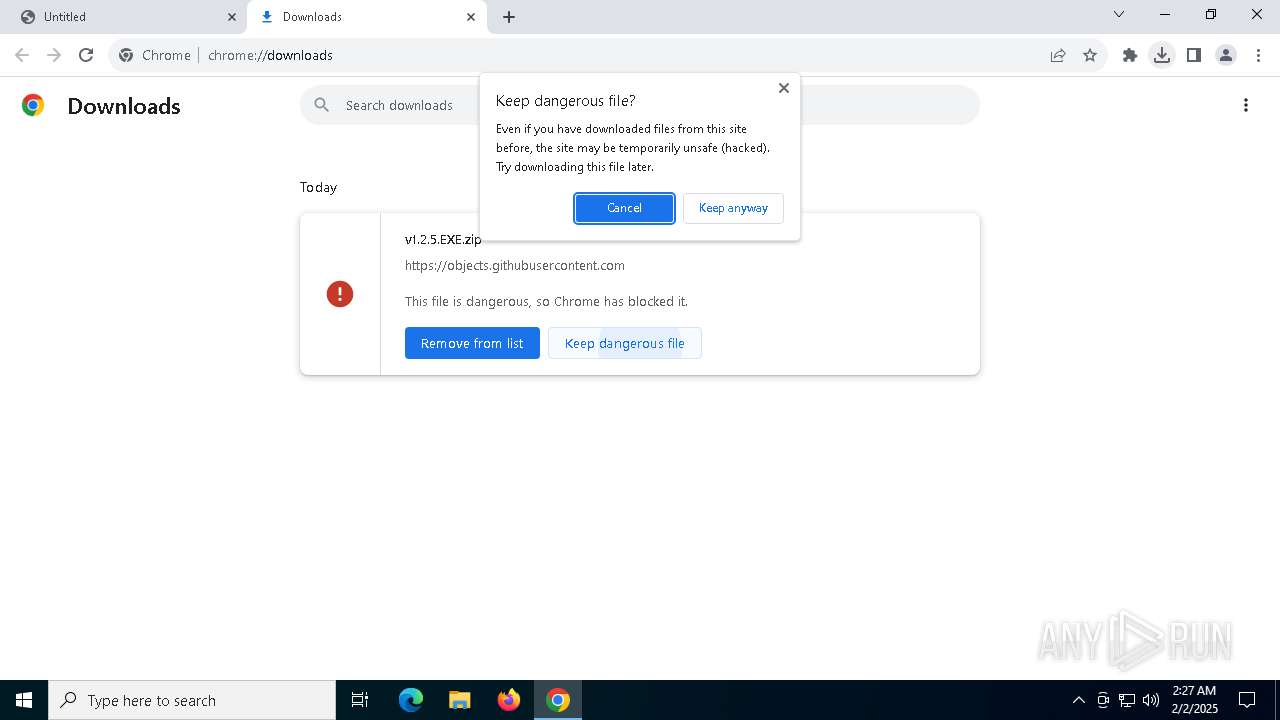
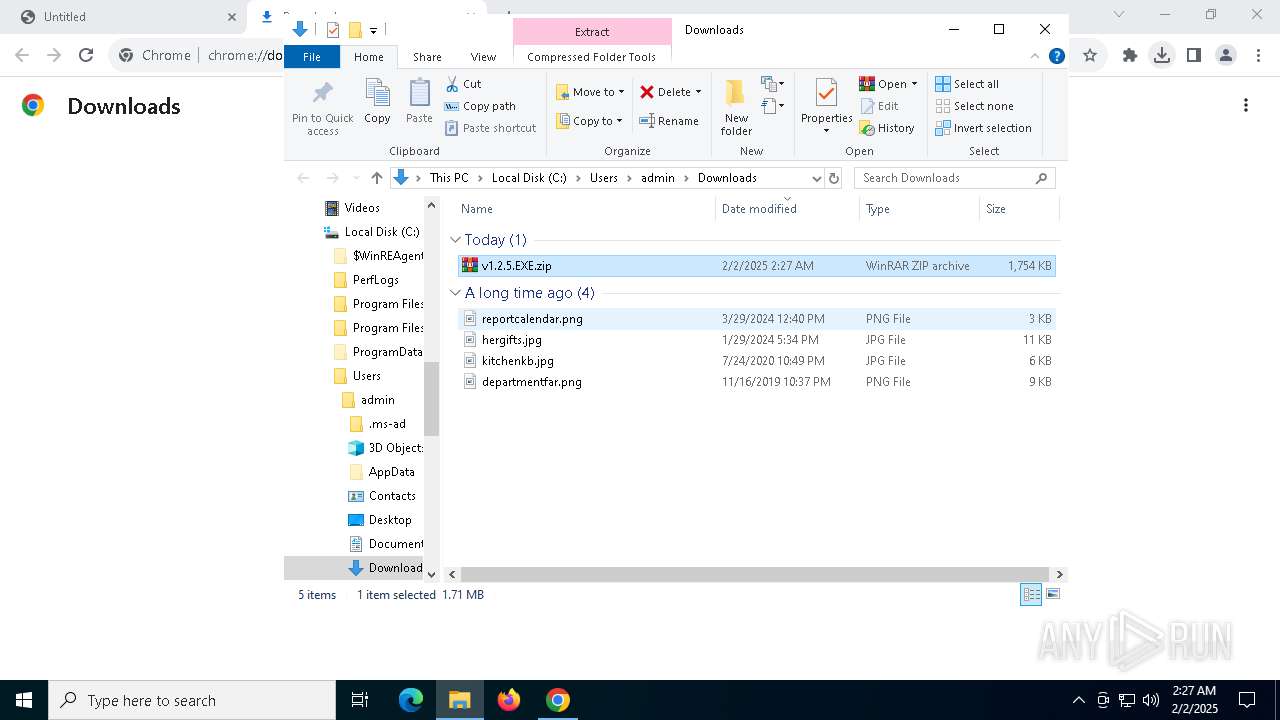
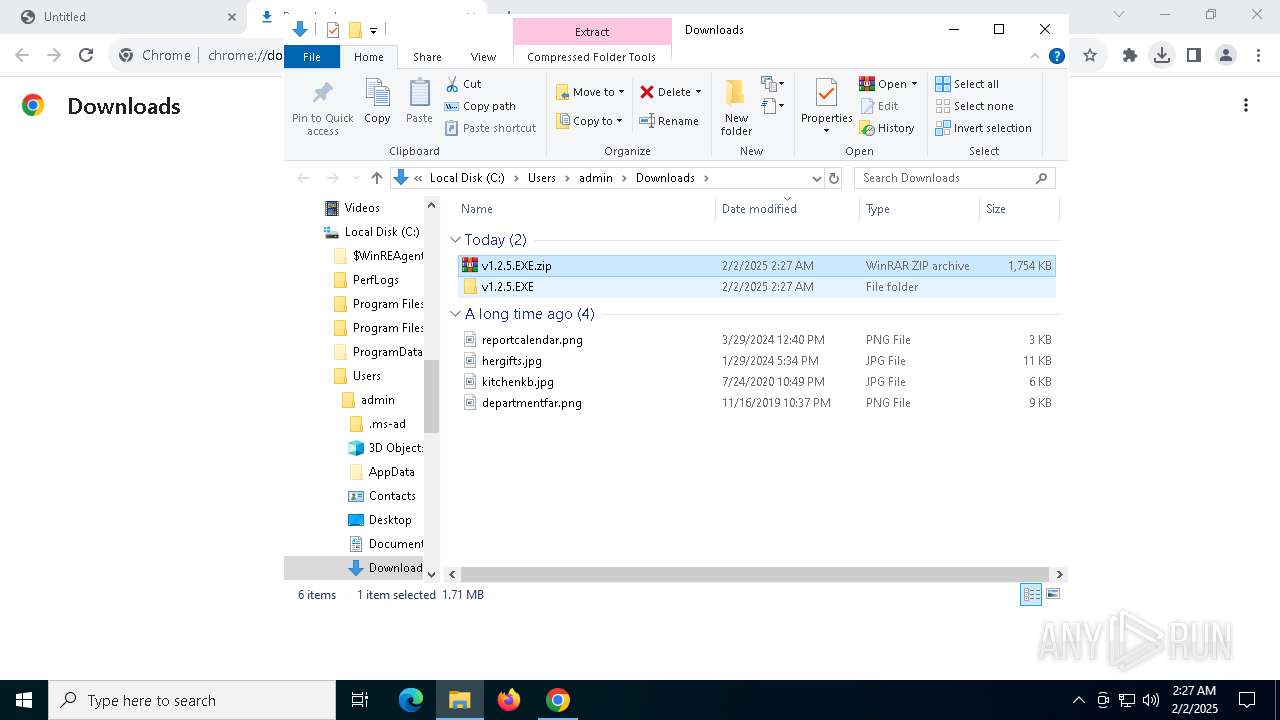
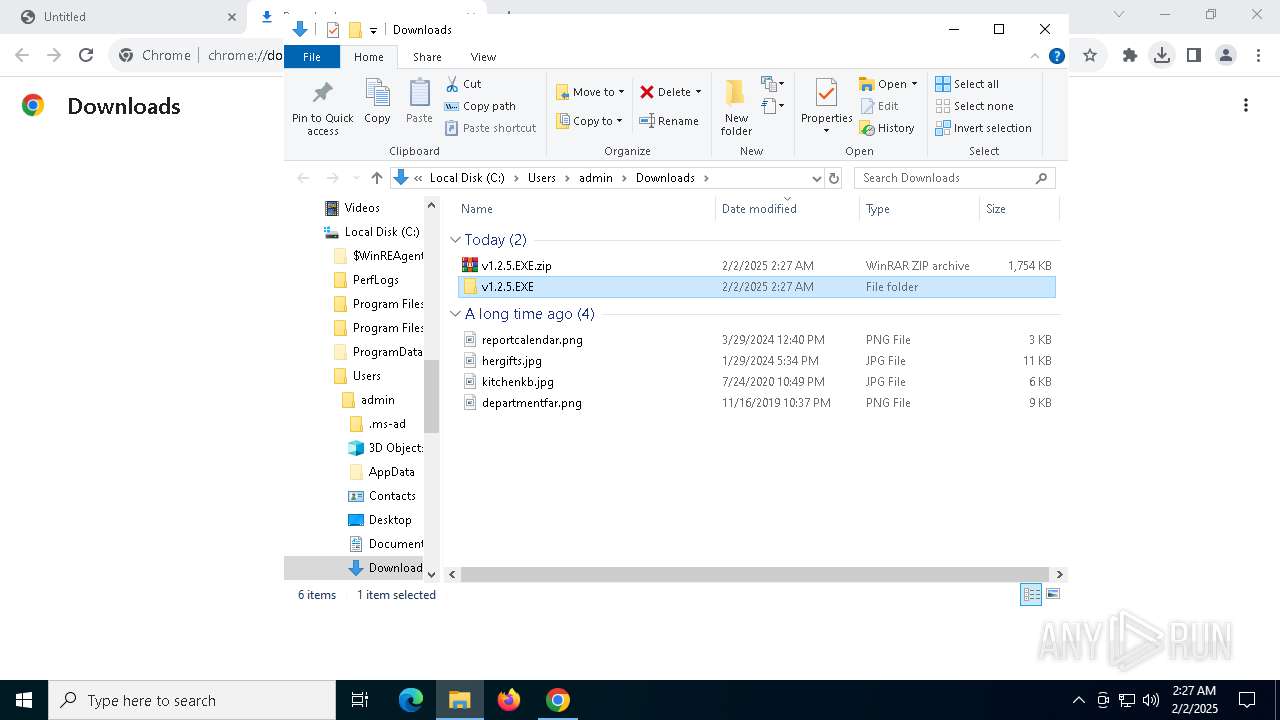
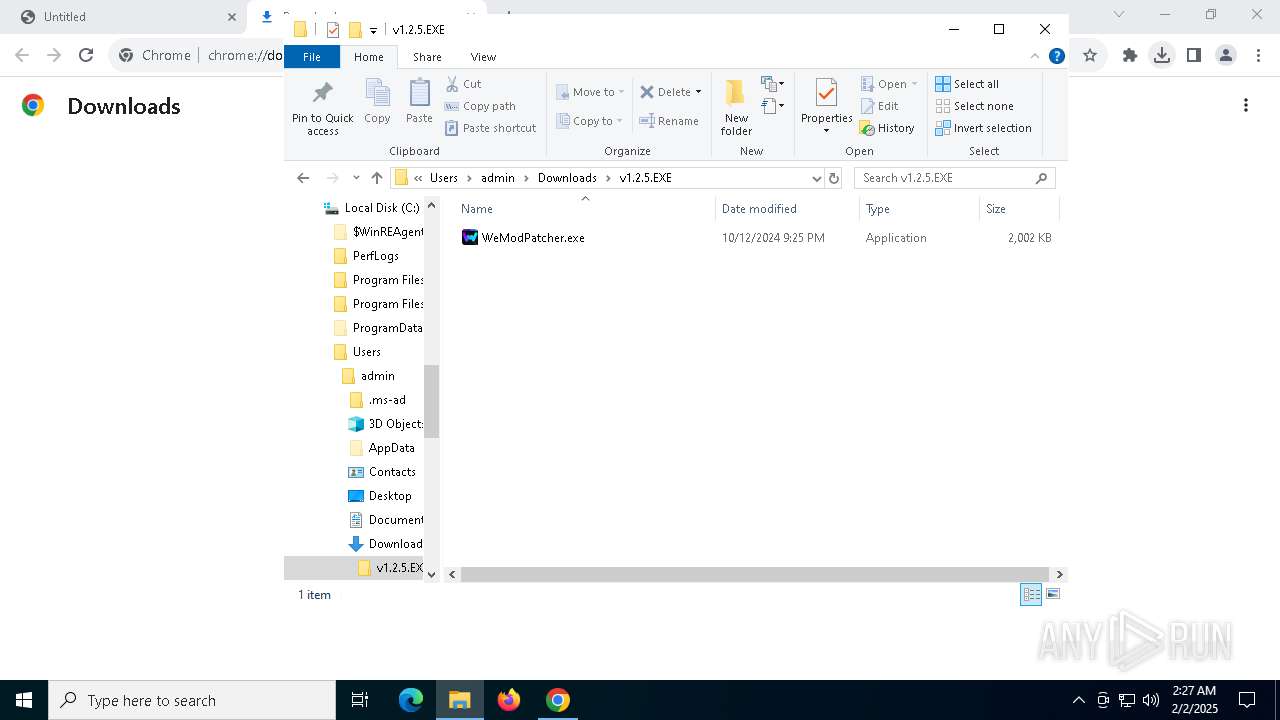
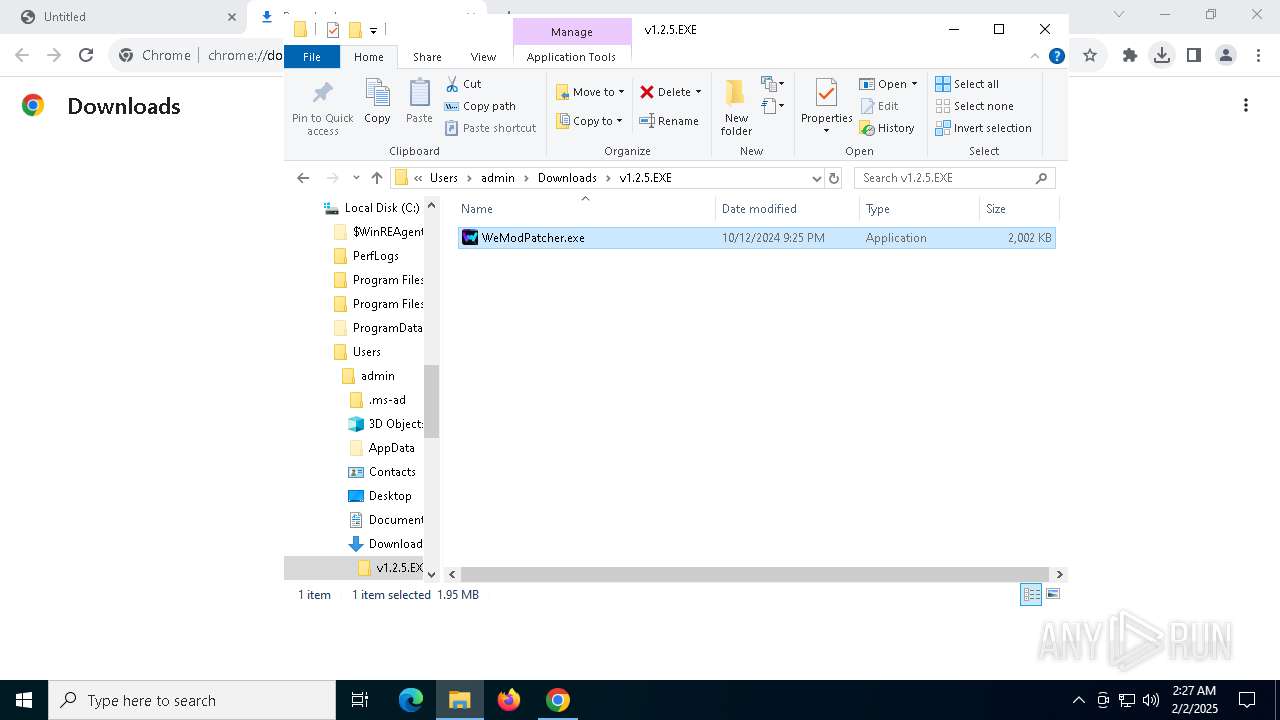
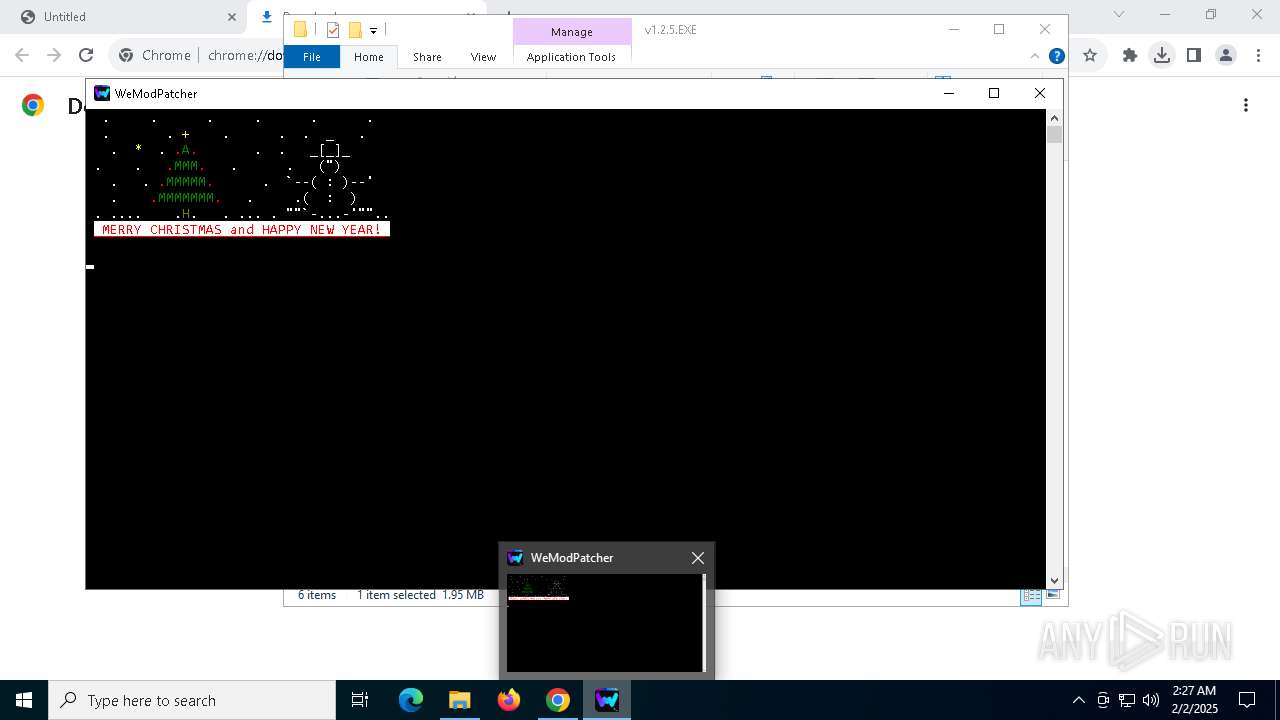
| URL: | https://github.com/brunolee-GIT/W3M0dP4tch32/releases/download/v1.2.5/v1.2.5.EXE.zip |
| Full analysis: | https://app.any.run/tasks/e4fd1765-f575-43f9-91ee-91d246cdf375 |
| Verdict: | Malicious activity |
| Analysis date: | February 02, 2025, 02:26:58 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 9086323B1FC8AE3103A7DC538EF1F45A |
| SHA1: | EE54FC60A6ECFF3DA19176B622655CB70E269D24 |
| SHA256: | C537670E4B741070703249F49F8EDB95944EB13DC6D3730F08FA2001EDD20D20 |
| SSDEEP: | 3:N8tEd3FJlyWkRRG+0kCm/kBOkV:2uxYRGXs/kMkV |
MALICIOUS
No malicious indicators.SUSPICIOUS
Application launched itself
- cmd.exe (PID: 1684)
Starts CMD.EXE for commands execution
- WeModPatcher.exe (PID: 6096)
- cmd.exe (PID: 1684)
Drops 7-zip archiver for unpacking
- WeModPatcher.exe (PID: 6096)
Execution of CURL command
- cmd.exe (PID: 1684)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4428)
- cmd.exe (PID: 3876)
- cmd.exe (PID: 4764)
- cmd.exe (PID: 5992)
- cmd.exe (PID: 1684)
- cmd.exe (PID: 6988)
- cmd.exe (PID: 6072)
- cmd.exe (PID: 5604)
- cmd.exe (PID: 5076)
- cmd.exe (PID: 4428)
Starts NET.EXE to display or manage information about active sessions
- cmd.exe (PID: 1684)
- net.exe (PID: 6072)
Get information on the list of running processes
- cmd.exe (PID: 4764)
- cmd.exe (PID: 7140)
- cmd.exe (PID: 1684)
- cmd.exe (PID: 7156)
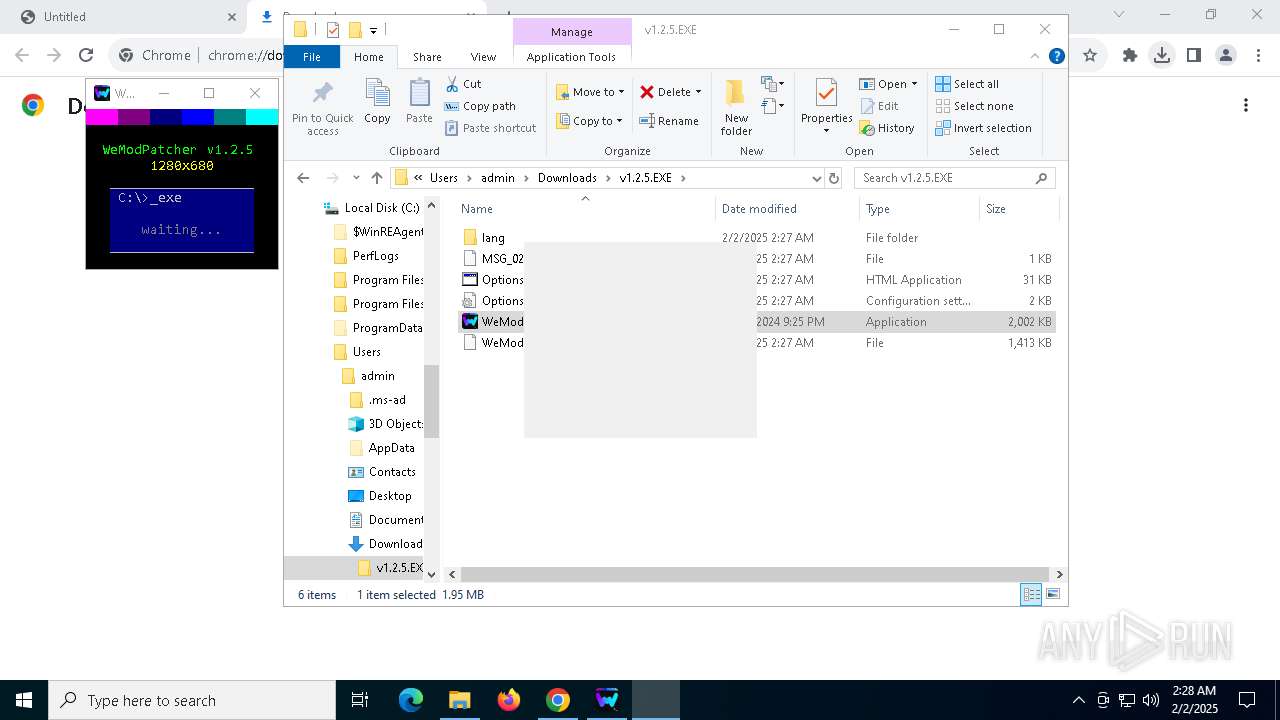
Starts application with an unusual extension
- cmd.exe (PID: 1144)
- cmd.exe (PID: 1684)
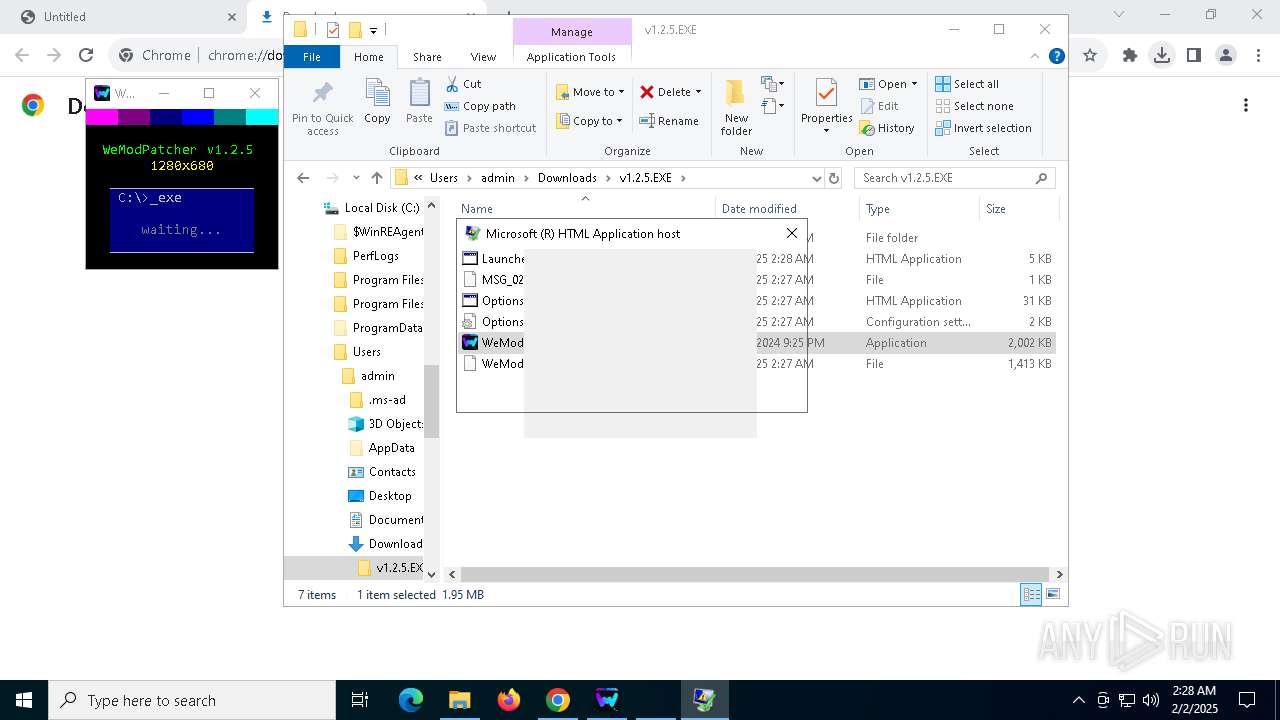
Creates FileSystem object to access computer's file system (SCRIPT)
- mshta.exe (PID: 1612)
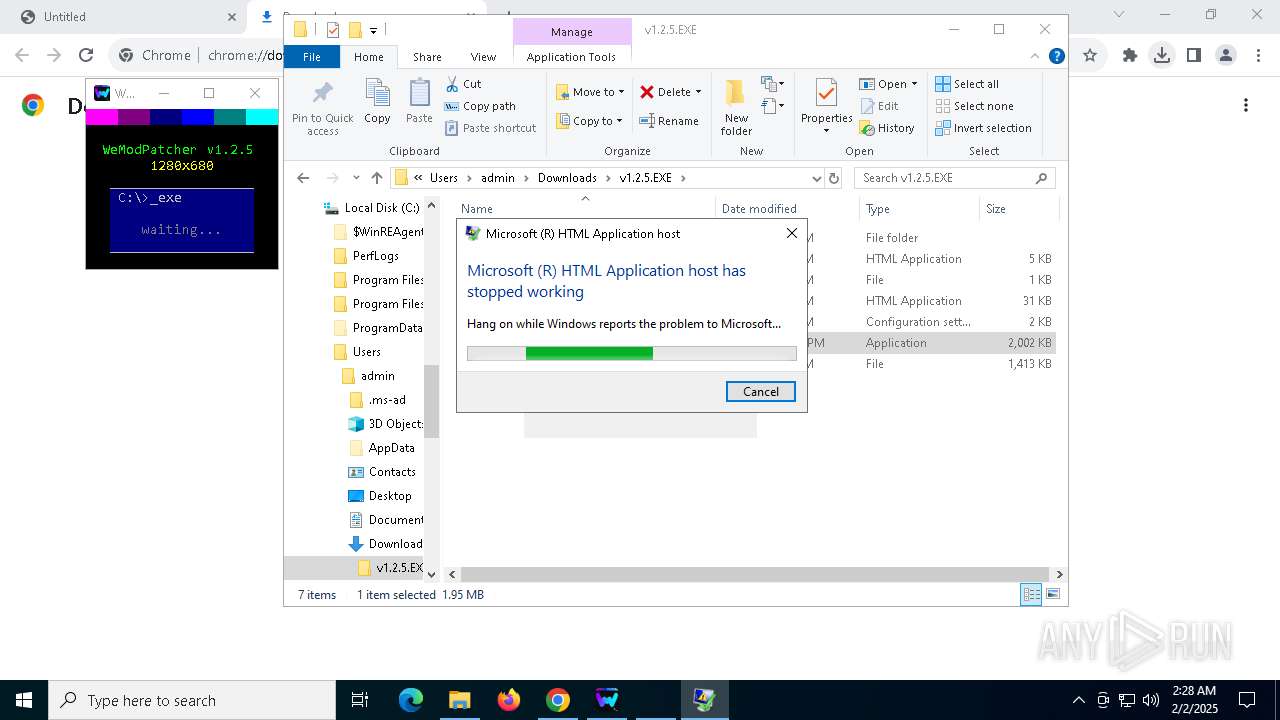
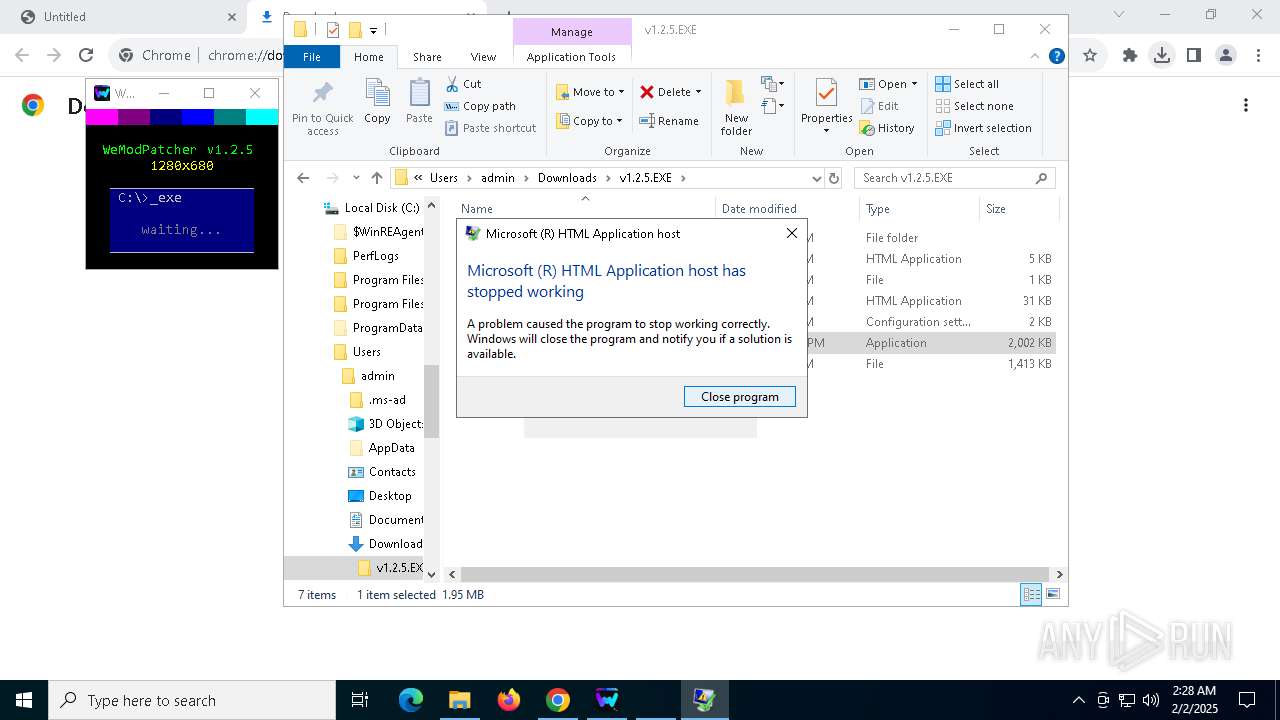
Executes application which crashes
- mshta.exe (PID: 1612)
The process creates files with name similar to system file names
- WerFault.exe (PID: 5392)
Executing commands from a ".bat" file
- WeModPatcher.exe (PID: 6096)
INFO
The sample compiled with english language support
- chrome.exe (PID: 6172)
- chrome.exe (PID: 6480)
- WinRAR.exe (PID: 3560)
- WeModPatcher.exe (PID: 6096)
Application launched itself
- chrome.exe (PID: 6480)
Reads the computer name
- curl.exe (PID: 6192)
Manual execution by a user
- WinRAR.exe (PID: 3560)
- WeModPatcher.exe (PID: 6096)
Executable content was dropped or overwritten
- chrome.exe (PID: 6172)
- WinRAR.exe (PID: 3560)
Execution of CURL command
- cmd.exe (PID: 2744)
Checks supported languages
- curl.exe (PID: 6192)
- chcp.com (PID: 6332)
- chcp.com (PID: 3984)
- mode.com (PID: 6360)
- chcp.com (PID: 432)
- chcp.com (PID: 3032)
- WeModPatcher.exe (PID: 6096)
Changes the display of characters in the console
- cmd.exe (PID: 1144)
- cmd.exe (PID: 1684)
Starts MODE.COM to configure console settings
- mode.com (PID: 6360)
Gets data length (POWERSHELL)
- powershell.exe (PID: 5916)
Reads Internet Explorer settings
- mshta.exe (PID: 1612)
Checks proxy server information
- mshta.exe (PID: 1612)
- WerFault.exe (PID: 5392)
Reads the software policy settings
- WerFault.exe (PID: 5392)
Create files in a temporary directory
- WeModPatcher.exe (PID: 6096)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
188
Monitored processes
58
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 432 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 440 | powershell -Command "(Get-Process -Id 6096).ProcessName" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1144 | C:\WINDOWS\system32\cmd.exe /c chcp | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1220 | powershell -Command "Write-Host -B 0 -F 0 ''.PadRight(8) -NoNewline; Write-Host -B 0 -F 14 '1280x680'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1612 | mshta.exe "C:\Users\admin\Downloads\v1.2.5.EXE\Launcher.hta" | C:\Windows\System32\mshta.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1684 | "C:\WINDOWS\system32\cmd" /c "C:\Users\admin\AppData\Local\Temp\EDCE.tmp\EDCF.tmp\EDD0.bat C:\Users\admin\Downloads\v1.2.5.EXE\WeModPatcher.exe" | C:\Windows\System32\cmd.exe | — | WeModPatcher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1916 | C:\WINDOWS\system32\cmd.exe /c mshta.exe "C:\Users\admin\Downloads\v1.2.5.EXE\Launcher.hta" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2124 | C:\WINDOWS\system32\net1 session | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2132 | powershell -Command "Add-Type -AssemblyName System.Windows.Forms;([System.Windows.Forms.Screen]::AllScreens).WorkingArea.Height" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2380 | powershell -Command "[string]([Version]'1.2.5', [Version]'1.2.5' | measure-object -maximum).maximum" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
63 800
Read events
63 790
Write events
10
Delete events
0
Modification events
| (PID) Process: | (6480) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6480) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6480) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6480) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6480) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (6332) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000303649001A75DB01 | |||
| (PID) Process: | (3560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
2
Suspicious files
48
Text files
59
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6480 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1377e3.TMP | — | |
MD5:— | SHA256:— | |||
| 6480 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6480 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF1377f2.TMP | — | |
MD5:— | SHA256:— | |||
| 6480 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6480 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF1377f2.TMP | — | |
MD5:— | SHA256:— | |||
| 6480 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6480 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF1377f2.TMP | — | |
MD5:— | SHA256:— | |||
| 6480 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6480 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF137802.TMP | — | |
MD5:— | SHA256:— | |||
| 6480 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF137802.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
41
DNS requests
31
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6360 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
6296 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6136 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6136 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
760 | lsass.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAz1vQYrVgL0erhQLCPM8GY%3D | unknown | — | — | whitelisted |
6360 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
6360 | svchost.exe | GET | — | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
5392 | WerFault.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5392 | WerFault.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 20.190.159.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 184.30.131.245:80 | — | AKAMAI-AS | US | unknown |
1076 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
6820 | chrome.exe | 140.82.121.4:443 | github.com | GITHUB | US | whitelisted |
6480 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6820 | chrome.exe | 173.194.79.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
6820 | chrome.exe | 185.199.108.133:443 | objects.githubusercontent.com | FASTLY | US | shared |
5064 | SearchApp.exe | 2.21.65.154:443 | www.bing.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
github.com |
| whitelisted |
accounts.google.com |
| whitelisted |
objects.githubusercontent.com |
| shared |
www.bing.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
www.google.com |
| whitelisted |
safebrowsing.google.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |