| File name: | Loader.exe |
| Full analysis: | https://app.any.run/tasks/d8d64742-bbd1-4016-a96b-1da38831a11c |
| Verdict: | Malicious activity |
| Analysis date: | October 08, 2024, 16:24:06 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (console) x86-64, for MS Windows |
| MD5: | F6551CD80A2D2D565E307A90CBAB2B8C |
| SHA1: | 344AD877F1CD12E7D18ABA969143A9A68D626039 |
| SHA256: | C5098FE841C34D9F0131D9448C2C034F4762B699F8C682D8778083605EA31605 |
| SSDEEP: | 196608:x6lkWNcjbYHZRfNd2CXZcY13yAg5xDBbG1k8:x6lNNWYHZrdzXZc1Tl+k8 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the BIOS version
- Loader.exe (PID: 5852)
Reads security settings of Internet Explorer
- Loader.exe (PID: 5852)
Reads the date of Windows installation
- Loader.exe (PID: 5852)
Starts SC.EXE for service management
- cmd.exe (PID: 6200)
- cmd.exe (PID: 7112)
- cmd.exe (PID: 6400)
- cmd.exe (PID: 1792)
Starts CMD.EXE for commands execution
- Loader.exe (PID: 5852)
Checks Windows Trust Settings
- Loader.exe (PID: 5852)
Creates files in the driver directory
- Loader.exe (PID: 5852)
Drops a system driver (possible attempt to evade defenses)
- Loader.exe (PID: 5852)
Executable content was dropped or overwritten
- Loader.exe (PID: 5852)
Creates file in the systems drive root
- Loader.exe (PID: 5852)
INFO
Process checks whether UAC notifications are on
- Loader.exe (PID: 5852)
Checks supported languages
- Loader.exe (PID: 5852)
Process checks computer location settings
- Loader.exe (PID: 5852)
Checks proxy server information
- Loader.exe (PID: 5852)
The process uses the downloaded file
- Loader.exe (PID: 5852)
Reads the software policy settings
- Loader.exe (PID: 5852)
Reads the computer name
- Loader.exe (PID: 5852)
Reads the machine GUID from the registry
- Loader.exe (PID: 5852)
Themida protector has been detected
- Loader.exe (PID: 5852)
Attempting to use instant messaging service
- Loader.exe (PID: 5852)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:06:18 06:15:45+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.4 |
| CodeSize: | 8844288 |
| InitializedDataSize: | 3215360 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1bef058 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
130
Monitored processes
20
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | Loader.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1700 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1732 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1792 | "C:\Windows\System32\cmd.exe" /C sc start windowsproc | C:\Windows\System32\cmd.exe | — | Loader.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2184 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | Loader.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3772 | sc create windowsproc type=kernel binpath=C:\Windows\System32\drivers\winhb.sys | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4076 | sc start windowsproc | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5184 | sc delete iqvw64e.sys | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
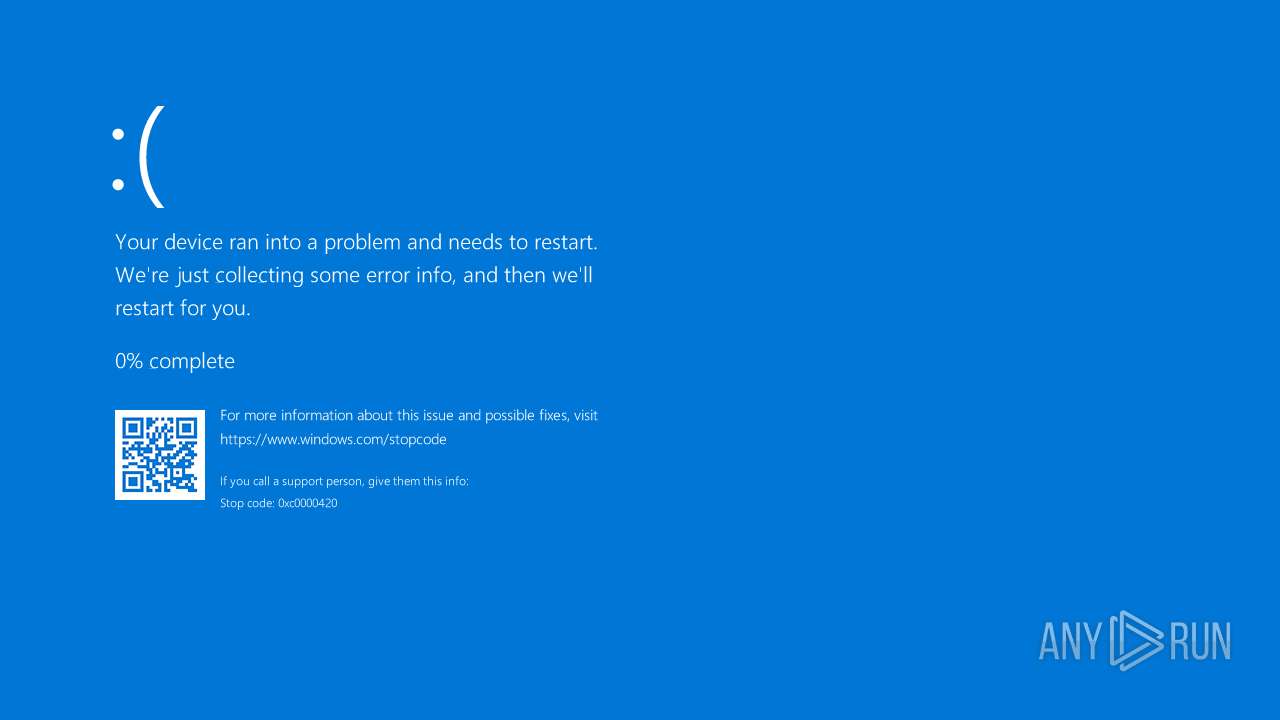
| 5524 | "C:\Users\admin\Desktop\Loader.exe" | C:\Users\admin\Desktop\Loader.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 5644 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 248
Read events
4 245
Write events
3
Delete events
0
Modification events
| (PID) Process: | (5852) Loader.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5852) Loader.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5852) Loader.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
1
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5852 | Loader.exe | \Device\Harddisk0\DR0 | — | |
MD5:— | SHA256:— | |||
| 5852 | Loader.exe | C:\Windows\System32\IME\SHARED\namef.ini | text | |
MD5:6E29C7CB93E6E298C0FB62A6A36B4825 | SHA256:C079ABCD7699BEB83C256BDF331B74FEFE730B5A7094EB62D8A8D7023ABE0C0E | |||
| 5852 | Loader.exe | C:\test.jpg | image | |
MD5:CD2B15E5590C4336618A91B34D6451D3 | SHA256:B3E42F7FC87CA05018DB915369ACB642F5FBE72A39C6B247CF45ABE124B593D7 | |||
| 5852 | Loader.exe | C:\Windows\System32\drivers\winhb.sys | executable | |
MD5:607FA999176AFF89978996E3A9CB27E3 | SHA256:EE1700AF169ADAB64827080F604E9818CDD7D4672E7D66DA137F00681E4E0C38 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
27
DNS requests
8
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 404 | 172.67.133.190:443 | https://download.simpletoolz.fun/Soviet2/0002.txt | unknown | html | 315 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 104.126.37.139:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5852 | Loader.exe | 172.67.133.190:443 | download.simpletoolz.fun | CLOUDFLARENET | US | unknown |
5852 | Loader.exe | 162.159.138.232:443 | discord.com | CLOUDFLARENET | — | whitelisted |
5852 | Loader.exe | 188.114.97.3:443 | systemlocker.net | CLOUDFLARENET | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
download.simpletoolz.fun |
| unknown |
discord.com |
| whitelisted |
systemlocker.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
5852 | Loader.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
5852 | Loader.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |