| File name: | fcdfg.exe |
| Full analysis: | https://app.any.run/tasks/ee35661c-882e-4bee-8c34-2cb73369a113 |
| Verdict: | Malicious activity |
| Analysis date: | September 30, 2020, 04:16:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | C243C0A3E2B6079B9AE736DD954ADAB2 |
| SHA1: | F45085742D3762829152C82A6ED05A3AA868B985 |
| SHA256: | C4BD0BAEC275A7F967ADF3DF4D30FF38BAB699B87C2106CF652EEA8311D26C0D |
| SSDEEP: | 24576:NeLH4AlFanAsf8so7JJnHfjthf/dTYCjQ2au6YFLTnY36nGp0MR5:YjGAHP/ZlUCjDau6YF/nY3CGeM |
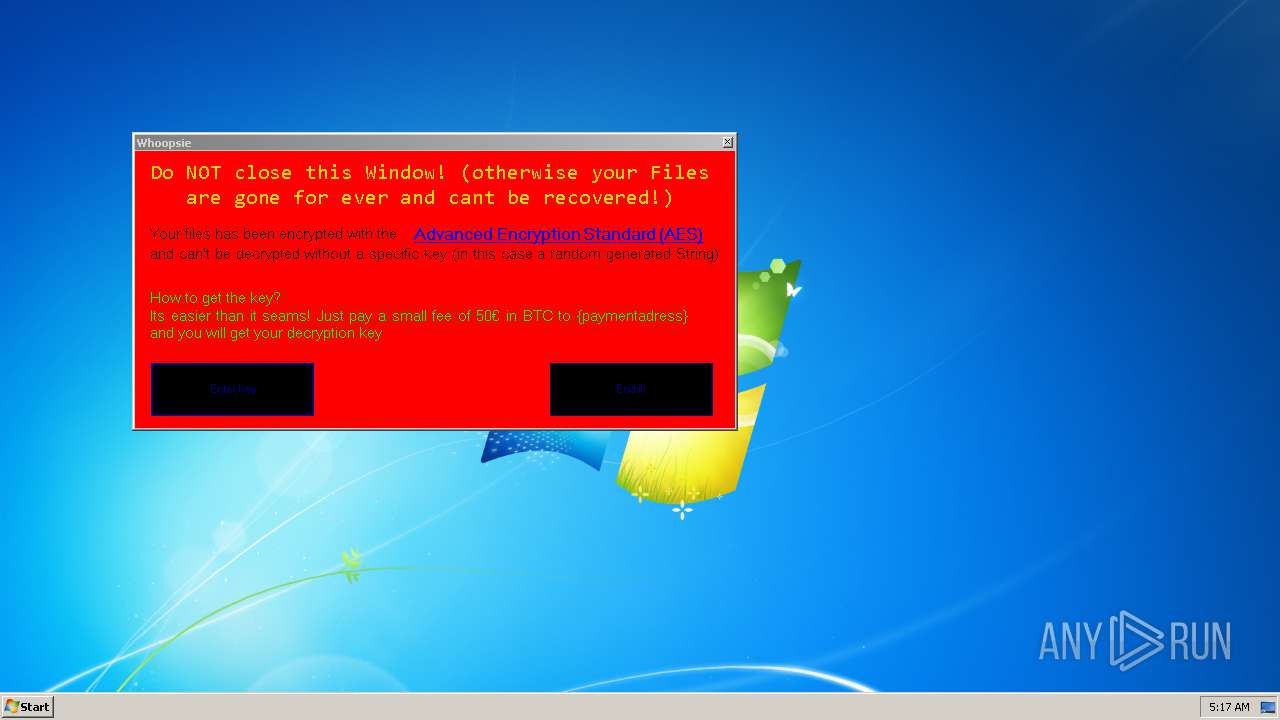
MALICIOUS
Writes to a start menu file
- fcdfg.exe (PID: 3852)
Modifies files in Chrome extension folder
- fcdfg.exe (PID: 3852)
Actions looks like stealing of personal data
- fcdfg.exe (PID: 3852)
SUSPICIOUS
Reads the cookies of Google Chrome
- fcdfg.exe (PID: 3852)
Reads the cookies of Mozilla Firefox
- fcdfg.exe (PID: 3852)
Creates files in the program directory
- fcdfg.exe (PID: 3852)
Creates files in the user directory
- fcdfg.exe (PID: 3852)
INFO
Manual execution by user
- WINWORD.EXE (PID: 2896)
- WINWORD.EXE (PID: 1544)
- NOTEPAD.EXE (PID: 3388)
- rundll32.exe (PID: 2252)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 1544)
- WINWORD.EXE (PID: 2896)
Creates files in the user directory
- WINWORD.EXE (PID: 1544)
- WINWORD.EXE (PID: 2896)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (61.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.6) |
| .exe | | | Win32 Executable (generic) (10) |
| .exe | | | Win16/32 Executable Delphi generic (4.6) |
| .exe | | | Generic Win/DOS Executable (4.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:06:25 17:13:43+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 19456 |
| InitializedDataSize: | 5120 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2b40 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | rw |
| CompanyName: | - |
| FileDescription: | rw |
| FileVersion: | 0.0.0.0 |
| InternalName: | Tree.exe |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | Tree.exe |
| ProductName: | - |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 25-Jun-2018 15:13:43 |
| Comments: | rw |
| CompanyName: | - |
| FileDescription: | rw |
| FileVersion: | 0.0.0.0 |
| InternalName: | Tree.exe |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFilename: | Tree.exe |
| ProductName: | - |
| ProductVersion: | 0.0.0.0 |
| Assembly Version: | 0.0.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 25-Jun-2018 15:13:43 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
0x0000E000 | 0x00280000 | 0x0002BA00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.99834 | |
.rsrc | 0x0000C000 | 0x00002000 | 0x00001200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.90396 |
.data | 0x0028E000 | 0x000E4000 | 0x000E2A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.9786 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.06644 | 3362 | UNKNOWN | UNKNOWN | RT_MANIFEST |
Imports
advapi32.dll |
gdi32.dll |
kernel32.dll |
mscoree.dll |
oleaut32.dll |
shell32.dll |
user32.dll |
version.dll |
Total processes
46
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1544 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\lotspurchase.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
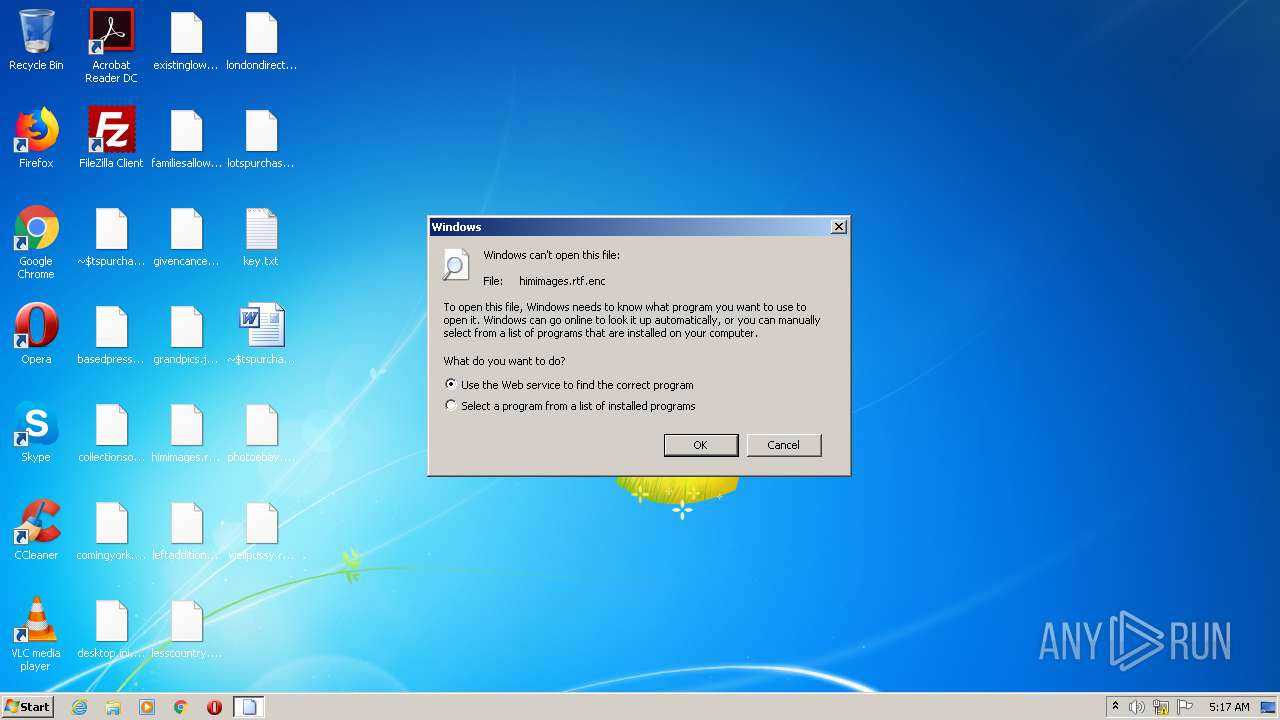
| 2252 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\himimages.rtf.enc | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2896 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\~$tspurchase.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
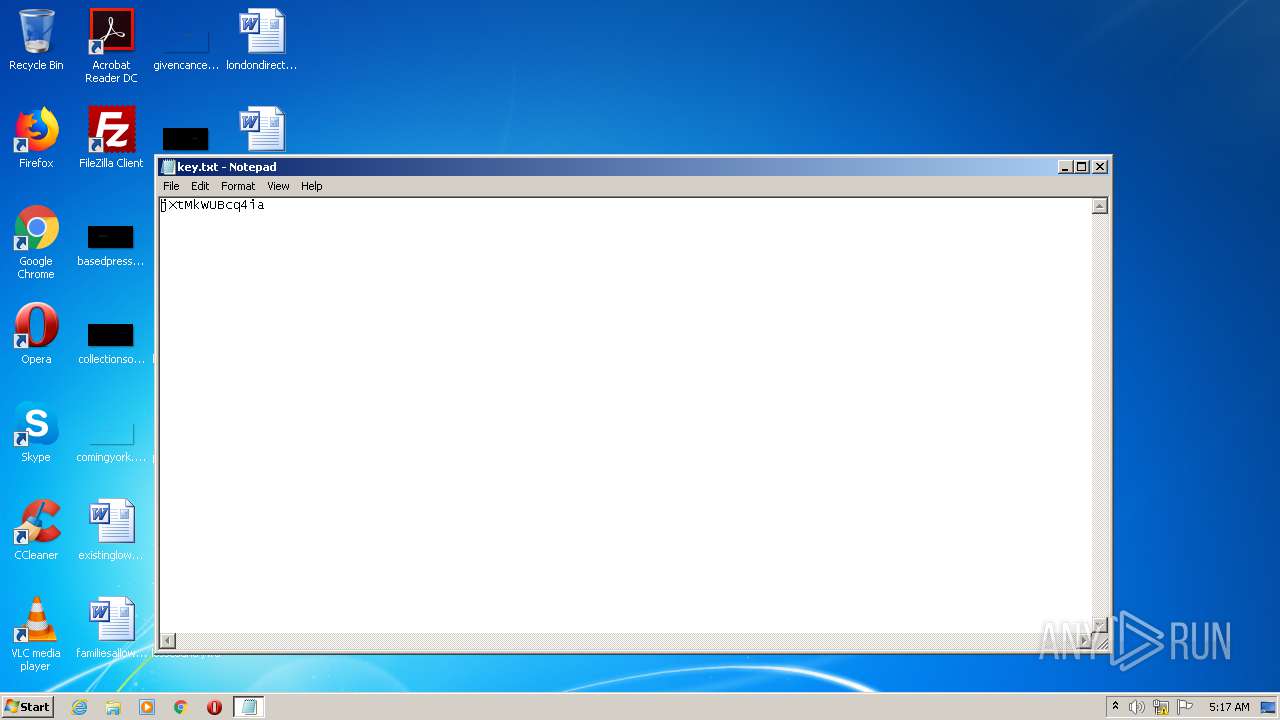
| 3388 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\key.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3852 | "C:\Users\admin\AppData\Local\Temp\fcdfg.exe" | C:\Users\admin\AppData\Local\Temp\fcdfg.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: rw Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
Total events
1 864
Read events
1 264
Write events
300
Delete events
300
Modification events
| (PID) Process: | (1544) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | !lj |
Value: 216C6A0008060000010000000000000000000000 | |||
| (PID) Process: | (1544) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1544) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1544) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (1544) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (1544) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (1544) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (1544) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (1544) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (1544) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
1 842
Text files
7
Unknown types
44
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3852 | fcdfg.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\IconCacheRdr.dat.enc | binary | |
MD5:— | SHA256:— | |||
| 3852 | fcdfg.exe | C:\Users\admin\AppData\Local\Adobe\AcroCef\DC\Acrobat\Cache\data_0.enc | binary | |
MD5:— | SHA256:— | |||
| 3852 | fcdfg.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SharedDataEvents.enc | binary | |
MD5:— | SHA256:— | |||
| 3852 | fcdfg.exe | C:\Users\admin\AppData\Local\GDIPFONTCACHEV1.DAT.enc | binary | |
MD5:— | SHA256:— | |||
| 3852 | fcdfg.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\IconCacheRdr65536.dat.enc | binary | |
MD5:— | SHA256:— | |||
| 3852 | fcdfg.exe | C:\Users\admin\ntuser.ini.enc | binary | |
MD5:— | SHA256:— | |||
| 3852 | fcdfg.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp.enc | binary | |
MD5:— | SHA256:— | |||
| 3852 | fcdfg.exe | C:\Users\admin\AppData\Local\CEF\User Data\Crashpad\metadata.enc | binary | |
MD5:— | SHA256:— | |||
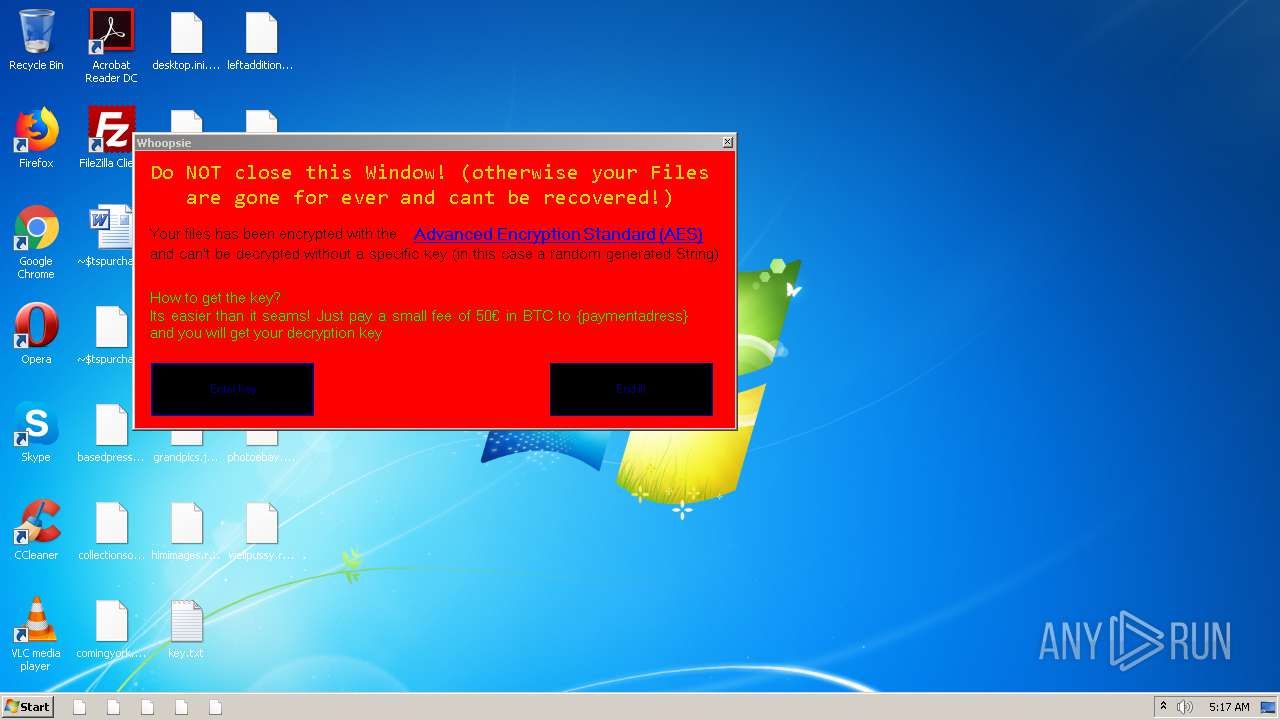
| 3852 | fcdfg.exe | C:\Users\admin\Desktop\key.txt | text | |
MD5:— | SHA256:— | |||
| 3852 | fcdfg.exe | C:\Users\admin\AppData\Local\CEF\User Data\Crashpad\settings.dat.enc | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report