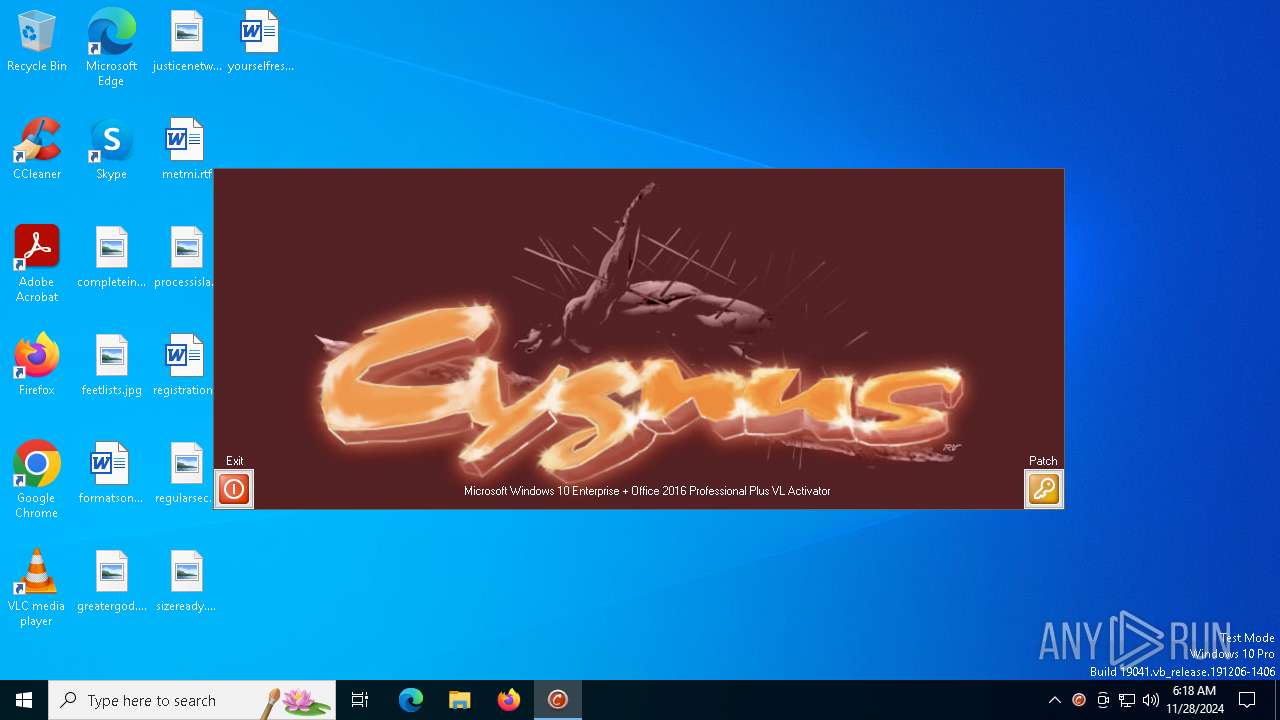
| File name: | win10_activator.exe |
| Full analysis: | https://app.any.run/tasks/0fedf54c-1e7c-489b-acda-2474da75ab82 |
| Verdict: | Malicious activity |
| Analysis date: | November 28, 2024, 06:18:33 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | D85169218CE7E6CC97D340620AB8BB98 |
| SHA1: | 63DE42A381F599CF9FD806A02CFD437D45010E6A |
| SHA256: | C4A0CF2420FA1FEE9EA1B0BAAD61F34F457E2FB76C7E527E0C4AA7FCE1523243 |
| SSDEEP: | 24576:iCdxte/80jYLT3U1jfsWapHRFtKgB9onh3QR:zw80cTsjkWajnKg8n+R |
MALICIOUS
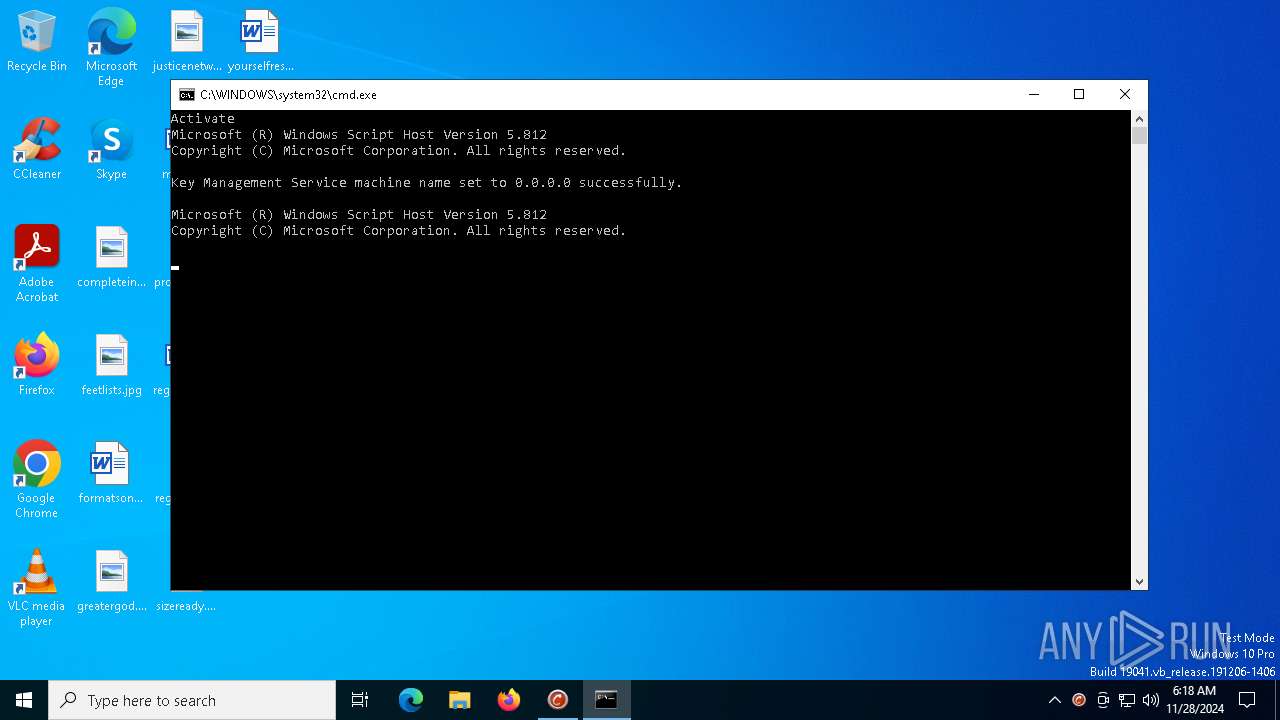
Starts NET.EXE for service management
- net.exe (PID: 5972)
- cmd.exe (PID: 7124)
Opens a text file (SCRIPT)
- cscript.exe (PID: 5036)
- cscript.exe (PID: 5252)
Accesses name of the domain to which a computer belongs via WMI (SCRIPT)
- cscript.exe (PID: 5036)
SUSPICIOUS
The executable file from the user directory is run by the CMD process
- win10_acti_x64.exe (PID: 7012)
- win10_acti_x64.exe (PID: 7044)
- win10_acti_x64.exe (PID: 7096)
Starts CMD.EXE for commands execution
- win10_activator.exe (PID: 6208)
- win10_acti_x64.exe (PID: 7096)
- cmd.exe (PID: 7124)
Executable content was dropped or overwritten
- win10_activator.exe (PID: 6208)
- win10_acti_x64.exe (PID: 7096)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 7124)
Application launched itself
- cmd.exe (PID: 7124)
Executing commands from ".cmd" file
- win10_acti_x64.exe (PID: 7096)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 5036)
- cscript.exe (PID: 5252)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7124)
The process downloads a VBScript from the remote host
- cmd.exe (PID: 3288)
The process executes VB scripts
- cmd.exe (PID: 3288)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 5036)
- cscript.exe (PID: 5252)
Checks whether a specific file exists (SCRIPT)
- cscript.exe (PID: 5036)
- cscript.exe (PID: 5252)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 5036)
- cscript.exe (PID: 5252)
Executes WMI query (SCRIPT)
- cscript.exe (PID: 5036)
- cscript.exe (PID: 5252)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 5036)
- cscript.exe (PID: 5252)
INFO
Checks supported languages
- win10_activator.exe (PID: 6208)
Reads mouse settings
- win10_activator.exe (PID: 6208)
Create files in a temporary directory
- win10_activator.exe (PID: 6208)
The process uses AutoIt
- win10_activator.exe (PID: 6208)
Reads the computer name
- win10_activator.exe (PID: 6208)
Checks operating system version
- cmd.exe (PID: 7124)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2015:12:05 13:50:04+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 12 |
| CodeSize: | 581120 |
| InitializedDataSize: | 624640 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x27f4a |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
Total processes
151
Monitored processes
21
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2356 | sc query sppsvc | C:\Windows\SysWOW64\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3288 | C:\WINDOWS\system32\cmd.exe /c "C:\Users\admin\AppData\Local\Temp\actiw10.cmd" | C:\Windows\SysWOW64\cmd.exe | — | win10_acti_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3688 | C:\WINDOWS\system32\cmd.exe /S /D /c" ver " | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3732 | find /I "Windows XP" | C:\Windows\SysWOW64\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3952 | C:\WINDOWS\system32\net1 stop sppsvc | C:\Windows\SysWOW64\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4504 | find /i "STOPPED" | C:\Windows\SysWOW64\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5036 | cscript slmgr.vbs /skms 0.0.0.0 | C:\Windows\SysWOW64\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 5252 | cscript slmgr.vbs /ato | C:\Windows\SysWOW64\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 5432 | wmic path OfficeSoftwareProtectionService get version | C:\Windows\SysWOW64\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 2147749890 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5464 | C:\WINDOWS\system32\cmd.exe /c ver | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 117
Read events
1 116
Write events
1
Delete events
0
Modification events
| (PID) Process: | (6016) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.exe |
| Operation: | write | Name: | Debugger |
Value: SppExtComObjPatcher.exe | |||
Executable files
7
Suspicious files
1
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7096 | win10_acti_x64.exe | C:\Users\admin\AppData\Local\Temp\7CEB9B2A0E395BD64E74381485A106AF.dll | executable | |
MD5:5AFB011D9DB047BB0400C5C5CA2E450B | SHA256:125FC74E03435B3E0EDE0FF523D625D9C1FBB299286E9E2DBD1442E506150DA6 | |||
| 7096 | win10_acti_x64.exe | C:\Users\admin\AppData\Local\Temp\A1D76FF97175BF79025AB7AA1DDF0A2A.dll | executable | |
MD5:70A3B98D4DCD9C7BF08D228334FBCAB4 | SHA256:08A0599B4CE4F8E963279FFD47642C82325A9C7B98E08DFA42CEC62B454C2BCB | |||
| 6208 | win10_activator.exe | C:\Users\admin\AppData\Local\Temp\~DFC12DC16D33BBF997.TMP | binary | |
MD5:19E52EA79DD6439A495145191C667DDA | SHA256:5739E254C74284CB1D5E6D85DBE4823DB83A6C502270FC9C5B06DD5DF4CAB35F | |||
| 7096 | win10_acti_x64.exe | C:\Users\admin\AppData\Local\Temp\actiw10.cmd | text | |
MD5:F03256583EA095FEA042208B043E356F | SHA256:C16EF54FED387CC9617EC004DA2327A6069073E8C863C199E68063BA7D02A8D7 | |||
| 6208 | win10_activator.exe | C:\Users\admin\AppData\Local\Temp\aut8C85.tmp | executable | |
MD5:7B23C2D38DB9B52E24E0B92DEF9B05D8 | SHA256:FE594D8DE571B5666D41440BBA7FB5F953E7BB8530D8C62E998B3FD6F46468C1 | |||
| 6208 | win10_activator.exe | C:\Users\admin\AppData\Local\Temp\cyg.jpg | image | |
MD5:5D6BC8DD792D50F87852147F82C64C25 | SHA256:DDE234CAB3FD58C8D6D1CE6C41B6ADB6C8489F1109CCE6801E844D859C280B7E | |||
| 6208 | win10_activator.exe | C:\Users\admin\AppData\Local\Temp\aut51AD.tmp | image | |
MD5:5D6BC8DD792D50F87852147F82C64C25 | SHA256:DDE234CAB3FD58C8D6D1CE6C41B6ADB6C8489F1109CCE6801E844D859C280B7E | |||
| 7096 | win10_acti_x64.exe | C:\Windows\System32\SppExtComObjPatcher.exe | executable | |
MD5:367B84F8E2853B05F5DECD1A592192DE | SHA256:6B5FDB57F0C989EBB5B2418453FD0D918BDBDDDF63F7D757A60974DD6A6D3465 | |||
| 7096 | win10_acti_x64.exe | C:\Windows\System32\SppExtComObjHook.dll | executable | |
MD5:AA80F8E8AE8F081E31AB313B1C36176B | SHA256:1D08C83D09163FAEE80202BB17FE1B40DD070E1C42C5234C4B86EFF68B149C46 | |||
| 7096 | win10_acti_x64.exe | C:\Users\admin\AppData\Local\Temp\crack.cmd | text | |
MD5:4DC7A9FCF9D77A80C896D42EF96E1A1C | SHA256:C8C0A808E4E2A4B190C1D443B0B02274AB35F25E96B566E35CB664917B94033B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
32
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6344 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6840 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6840 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.20:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.20:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.216.77.20:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.216.77.20:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 104.126.37.123:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |