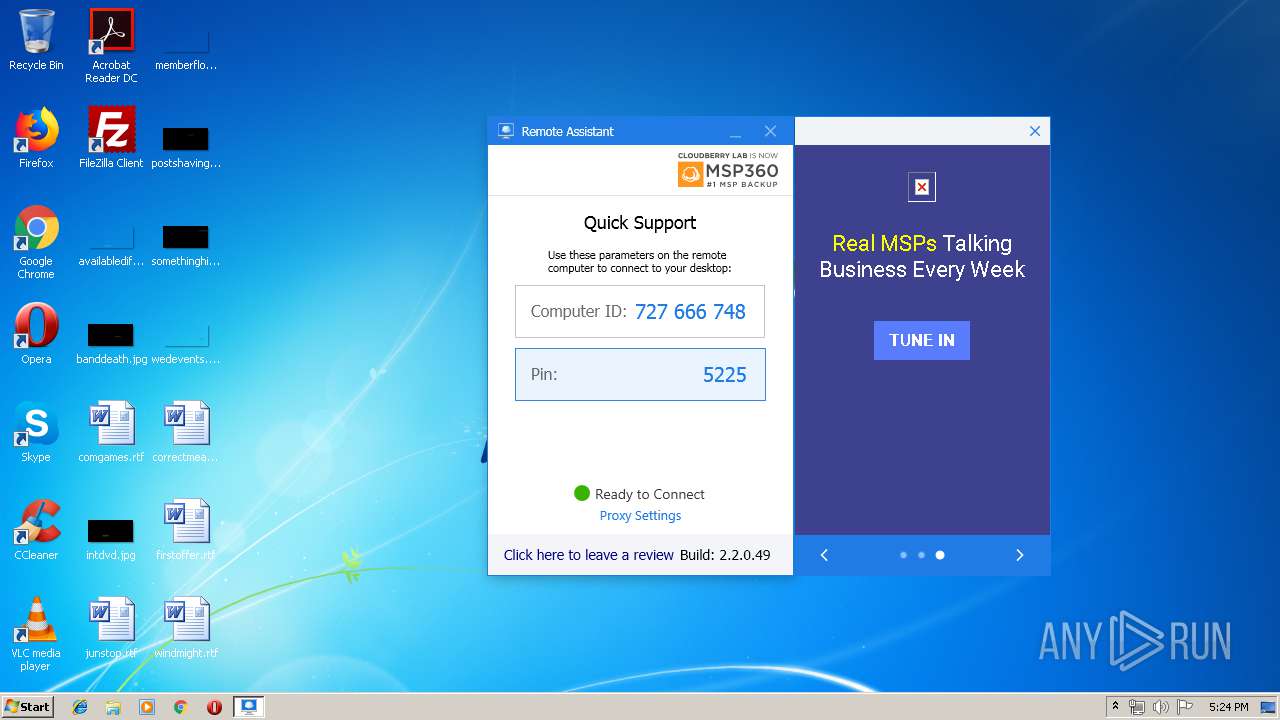
| download: | RemoteAssistant.exe |
| Full analysis: | https://app.any.run/tasks/7314790e-d1aa-4f6c-aa64-5a92dc351d18 |
| Verdict: | Malicious activity |
| Analysis date: | November 08, 2019, 17:23:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 54D52B3DCC18E33D5A23608A7FC289F3 |
| SHA1: | 6F84E9940C18D4278FE43D4658EF6D42E4971EC9 |
| SHA256: | C49E9382673C45D87E28384B2292DE029E104E8BE87912061D04301582616A15 |
| SSDEEP: | 49152:xlb/PlTGJoMAEkbihgoMQZfd43GsIOHtuTFyNNq2DoLJHIRtYnH7Hn8Apdi5Qddi:vrtTNagoxZ23GsIDsJMLJHTH7HdIN+0 |
MALICIOUS
Loads dropped or rewritten executable
- RemoteAssistant.exe (PID: 3172)
- Remote Assistant.exe (PID: 4076)
Application was dropped or rewritten from another process
- Remote Assistant.exe (PID: 3032)
- Remote Assistant.exe (PID: 4076)
SUSPICIOUS
Executable content was dropped or overwritten
- RemoteAssistant.exe (PID: 3172)
Reads Environment values
- Remote Assistant.exe (PID: 4076)
Reads Internet Cache Settings
- Remote Assistant.exe (PID: 4076)
Reads internet explorer settings
- Remote Assistant.exe (PID: 4076)
INFO
Dropped object may contain Bitcoin addresses
- RemoteAssistant.exe (PID: 3172)
Reads settings of System Certificates
- Remote Assistant.exe (PID: 4076)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:04:02 05:21:43+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26112 |
| InitializedDataSize: | 169984 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x35a5 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.2.0.49 |
| ProductVersionNumber: | 2.2.0.49 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | ASCII |
| CompanyName: | CloudBerry Lab Inc. |
| LegalCopyright: | Copyright 2019 CloudBerry Lab Inc. |
| ProductName: | Remote Assistant |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 02-Apr-2016 03:21:43 |
| Detected languages: |
|
| CompanyName: | CloudBerry Lab Inc. |
| LegalCopyright: | Copyright 2019 CloudBerry Lab Inc. |
| ProductName: | Remote Assistant |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 02-Apr-2016 03:21:43 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000065BF | 0x00006600 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.47825 |
.rdata | 0x00008000 | 0x000012EE | 0x00001400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.16943 |
.data | 0x0000A000 | 0x000271B8 | 0x00000E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.99201 |
.ndata | 0x00032000 | 0x00010000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x00042000 | 0x0005B338 | 0x0005B400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.01059 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.22372 | 947 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 5.09026 | 67624 | UNKNOWN | English - United States | RT_ICON |
3 | 5.39256 | 16936 | UNKNOWN | English - United States | RT_ICON |
4 | 5.52179 | 9640 | UNKNOWN | English - United States | RT_ICON |
5 | 5.48902 | 4264 | UNKNOWN | English - United States | RT_ICON |
6 | 5.17467 | 1128 | UNKNOWN | English - United States | RT_ICON |
7 | 0 | 296 | UNKNOWN | English - United States | RT_ICON |
103 | 2.51066 | 104 | UNKNOWN | English - United States | RT_GROUP_ICON |
105 | 2.73893 | 514 | UNKNOWN | English - United States | RT_DIALOG |
106 | 2.89384 | 248 | UNKNOWN | English - United States | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
39
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3032 | "C:\Users\admin\AppData\Local\Temp\Remote Assistant Quick Support\Remote Assistant.exe" | C:\Users\admin\AppData\Local\Temp\Remote Assistant Quick Support\Remote Assistant.exe | — | RemoteAssistant.exe | |||||||||||
User: admin Company: CloudBerry Lab Integrity Level: MEDIUM Description: Remote Assistant Exit code: 3221226540 Version: 2.2.0.49 Modules
| |||||||||||||||
| 3172 | "C:\Users\admin\AppData\Local\Temp\RemoteAssistant.exe" | C:\Users\admin\AppData\Local\Temp\RemoteAssistant.exe | explorer.exe | ||||||||||||
User: admin Company: CloudBerry Lab Inc. Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4076 | "C:\Users\admin\AppData\Local\Temp\Remote Assistant Quick Support\Remote Assistant.exe" | C:\Users\admin\AppData\Local\Temp\Remote Assistant Quick Support\Remote Assistant.exe | RemoteAssistant.exe | ||||||||||||
User: admin Company: CloudBerry Lab Integrity Level: MEDIUM Description: Remote Assistant Exit code: 0 Version: 2.2.0.49 Modules
| |||||||||||||||
Total events
547
Read events
510
Write events
37
Delete events
0
Modification events
| (PID) Process: | (3172) RemoteAssistant.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3172) RemoteAssistant.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (4076) Remote Assistant.exe | Key: | HKEY_CLASSES_ROOT\CLSID\{06A0E2A6-801E-41D9-8579-31305F8D075E}\QuickSupport\Server |
| Operation: | write | Name: | Id |
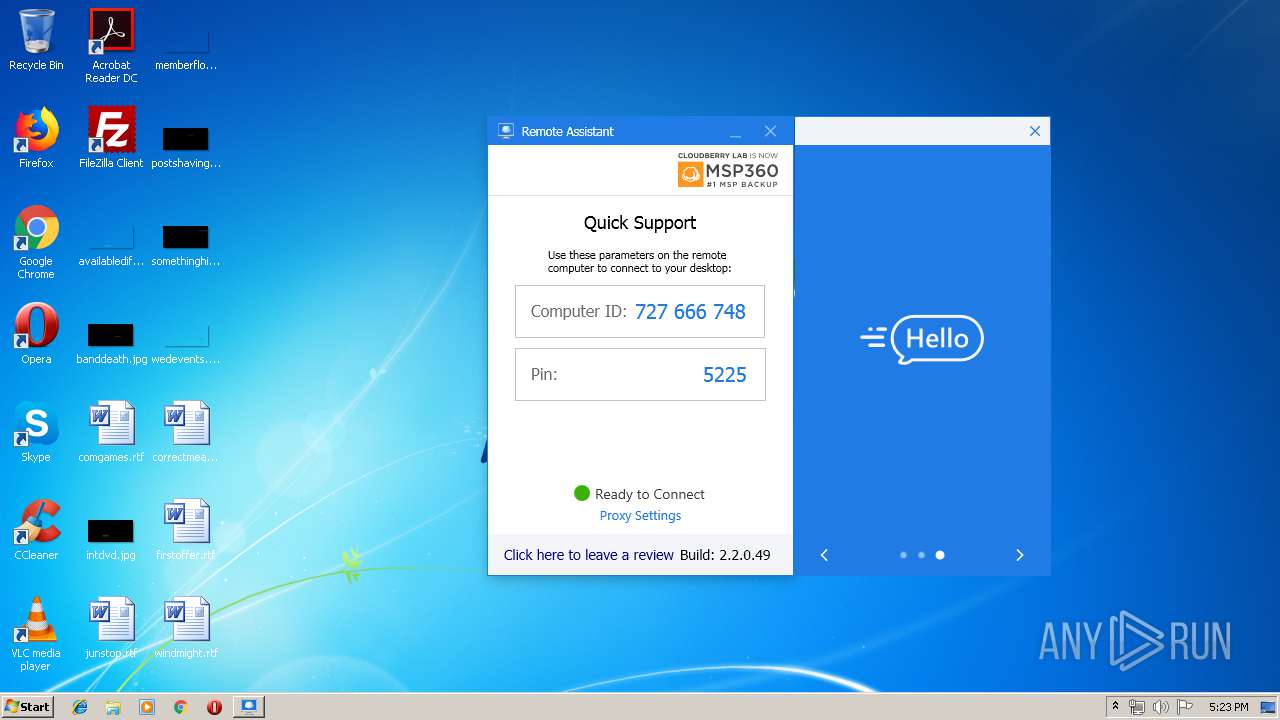
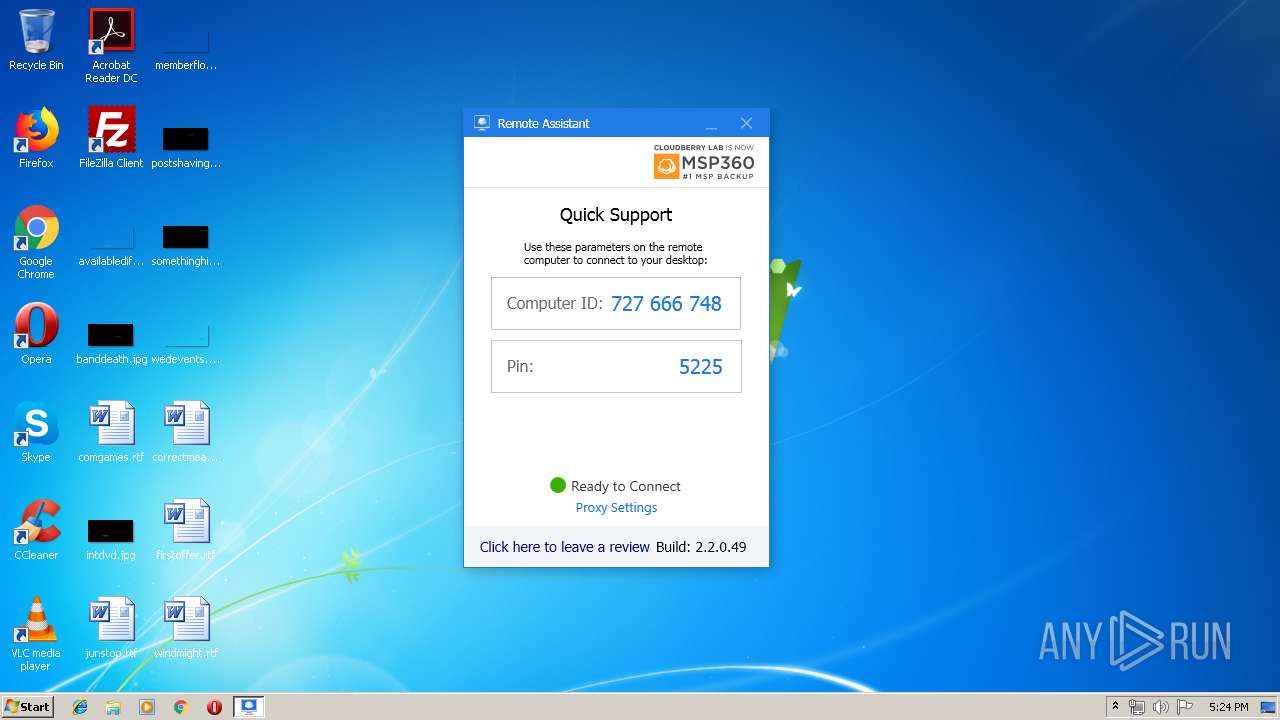
Value: 727666748 | |||
| (PID) Process: | (4076) Remote Assistant.exe | Key: | HKEY_CLASSES_ROOT\CLSID\{06A0E2A6-801E-41D9-8579-31305F8D075E}\QuickSupport\Server |
| Operation: | write | Name: | HardwareId |
Value: {QSUPPORT-78DA-4922-8A44-532E9052E6EF} | |||
| (PID) Process: | (4076) Remote Assistant.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: Remote Assistant.exe | |||
| (PID) Process: | (4076) Remote Assistant.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (4076) Remote Assistant.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (4076) Remote Assistant.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4076) Remote Assistant.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Remote Assistant_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4076) Remote Assistant.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Remote Assistant_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
27
Suspicious files
4
Text files
36
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3172 | RemoteAssistant.exe | C:\Users\admin\AppData\Local\Temp\Remote Assistant Quick Support\Cloud.Ra.ServiceContract.dll | executable | |
MD5:— | SHA256:— | |||
| 3172 | RemoteAssistant.exe | C:\Users\admin\AppData\Local\Temp\Remote Assistant Quick Support\Cloud.Ra.config | xml | |
MD5:98DF379DCF32A97A22AB8174AA125D0F | SHA256:466E9C4CD16300AE2495DFC27A8067E7465AB32D920413D97FE8E501C98F91A7 | |||
| 3172 | RemoteAssistant.exe | C:\Users\admin\AppData\Local\Temp\Remote Assistant Quick Support\Remote Assistant.exe.manifest | xml | |
MD5:— | SHA256:— | |||
| 3172 | RemoteAssistant.exe | C:\Users\admin\AppData\Local\Temp\Remote Assistant Quick Support\CloudRaService.exe | executable | |
MD5:— | SHA256:— | |||
| 3172 | RemoteAssistant.exe | C:\Users\admin\AppData\Local\Temp\Remote Assistant Quick Support\Remote Assistant.exe.config | xml | |
MD5:— | SHA256:— | |||
| 3172 | RemoteAssistant.exe | C:\Users\admin\AppData\Local\Temp\Remote Assistant Quick Support\CloudRaUtilities.exe | executable | |
MD5:— | SHA256:— | |||
| 3172 | RemoteAssistant.exe | C:\Users\admin\AppData\Local\Temp\Remote Assistant Quick Support\Cloud.Base.dll | executable | |
MD5:— | SHA256:— | |||
| 3172 | RemoteAssistant.exe | C:\Users\admin\AppData\Local\Temp\Remote Assistant Quick Support\Cloud.Client.dll | executable | |
MD5:— | SHA256:— | |||
| 3172 | RemoteAssistant.exe | C:\Users\admin\AppData\Local\Temp\Remote Assistant Quick Support\Remote Assistant.exe | executable | |
MD5:— | SHA256:— | |||
| 3172 | RemoteAssistant.exe | C:\Users\admin\AppData\Local\Temp\Remote Assistant Quick Support\Cloud.Backup.RM.SIO.dll | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
19
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3788 | consent.exe | GET | 200 | 91.199.212.52:80 | http://crt.comodoca.com/COMODORSAAddTrustCA.crt | GB | der | 1.37 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3788 | consent.exe | 91.199.212.52:80 | crt.comodoca.com | Comodo CA Ltd | GB | suspicious |
4076 | Remote Assistant.exe | 18.197.126.202:443 | connect.ra.cloudberrylab.com | Amazon.com, Inc. | DE | unknown |
4076 | Remote Assistant.exe | 50.19.243.6:443 | www.cloudberrylab.com | Amazon.com, Inc. | US | unknown |
4076 | Remote Assistant.exe | 172.217.23.138:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
4076 | Remote Assistant.exe | 172.217.23.131:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
4076 | Remote Assistant.exe | 92.122.213.201:80 | www.download.windowsupdate.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crt.comodoca.com |
| whitelisted |
connect.ra.cloudberrylab.com |
| unknown |
www.cloudberrylab.com |
| unknown |
www.download.windowsupdate.com |
| whitelisted |
ec2.us-east-1.amazonaws.com |
| unknown |
ec2.us-east-2.amazonaws.com |
| unknown |
ec2.us-west-1.amazonaws.com |
| unknown |
ec2.us-west-2.amazonaws.com |
| unknown |
fonts.googleapis.com |
| whitelisted |
ec2.ap-northeast-1.amazonaws.com |
| unknown |