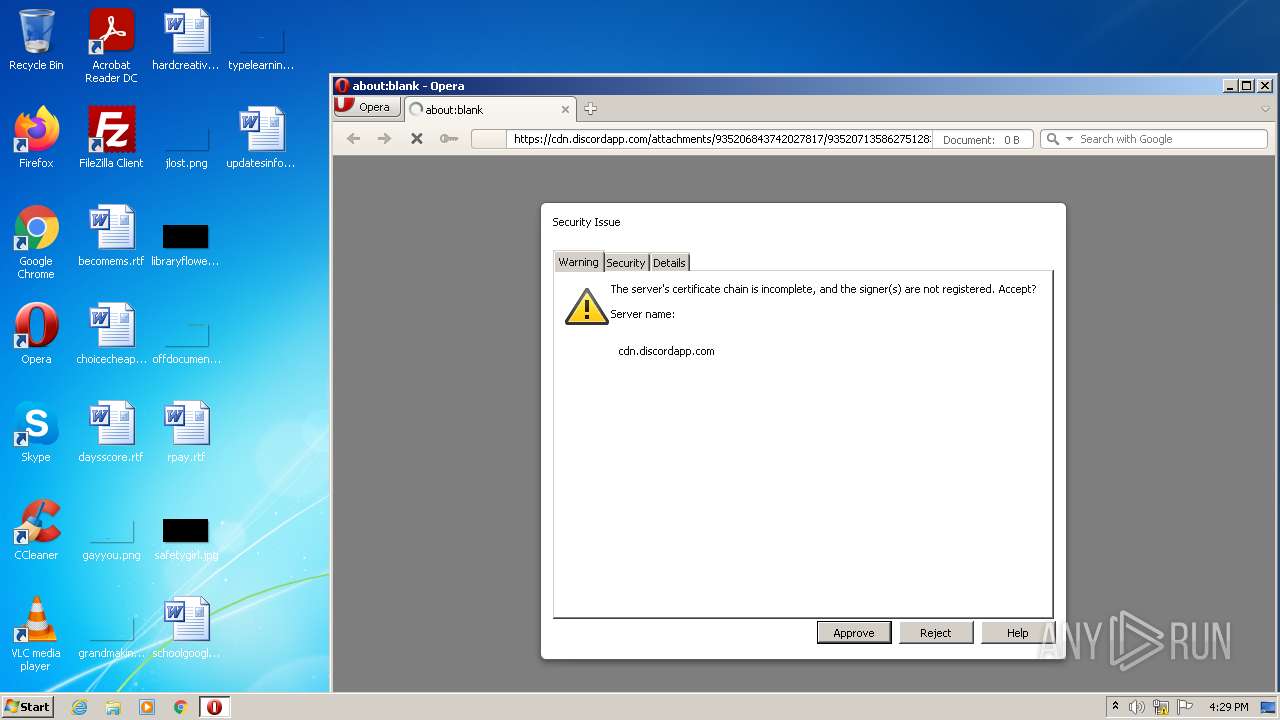
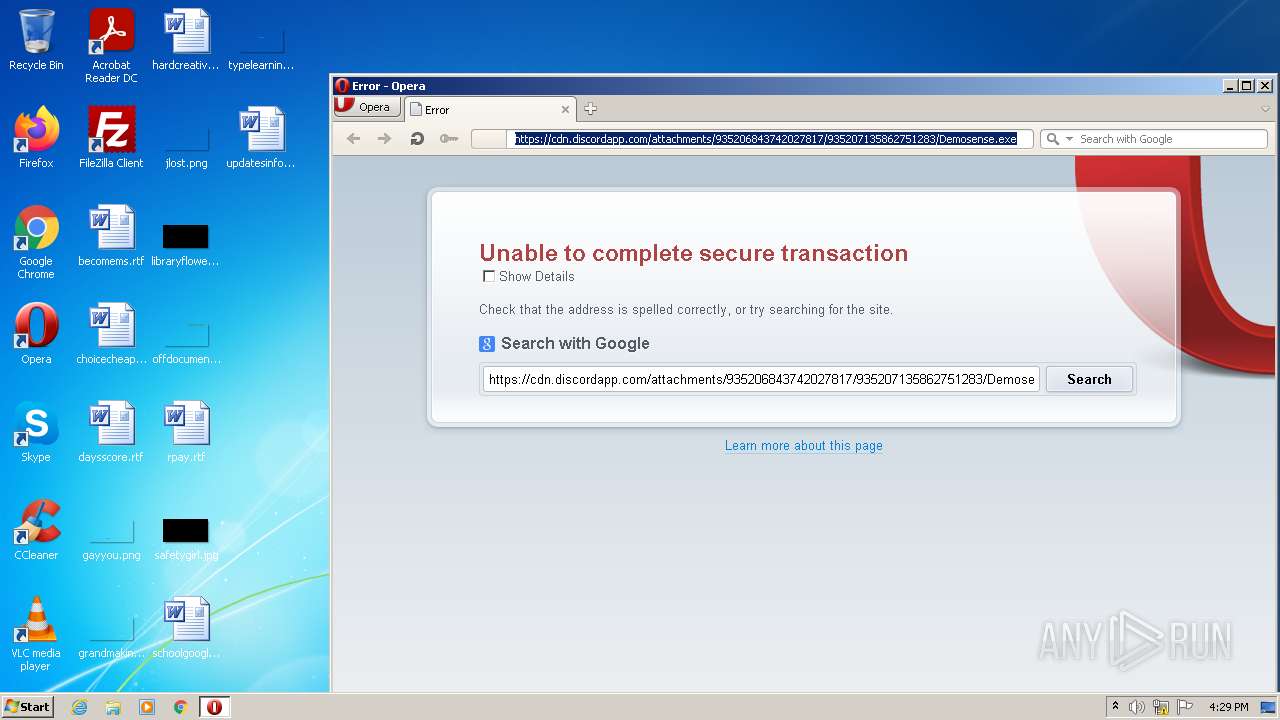
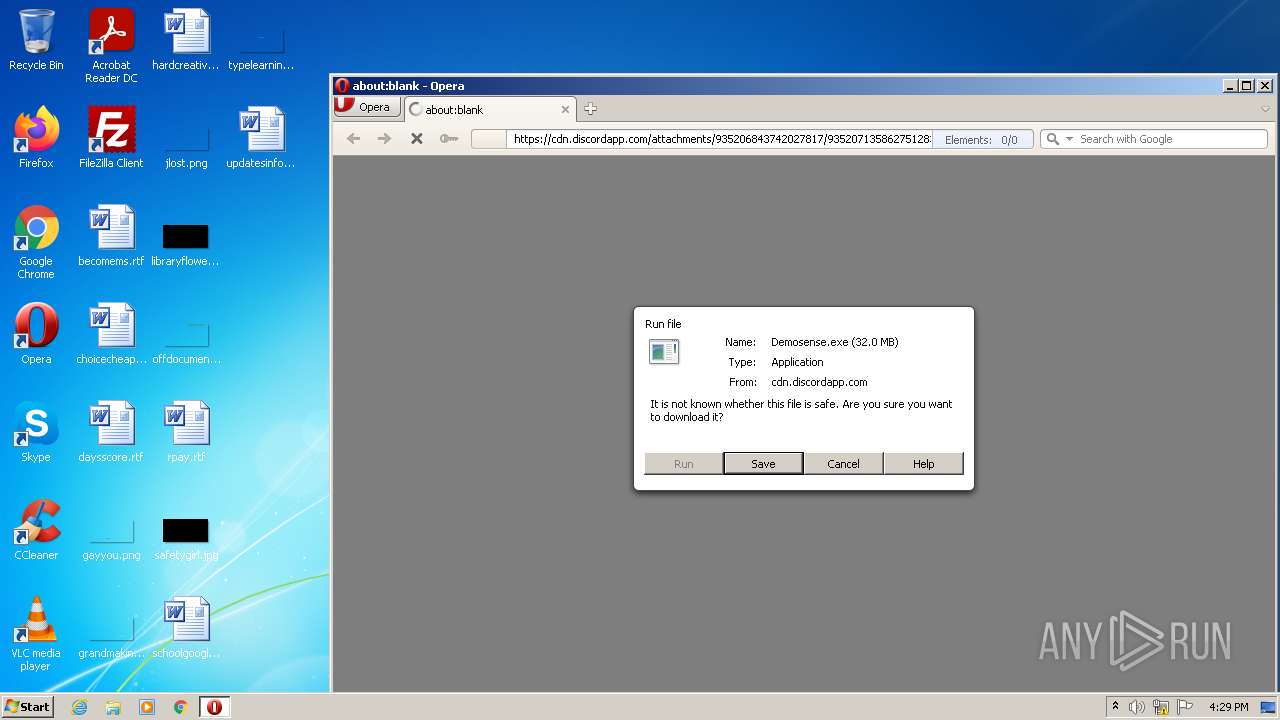
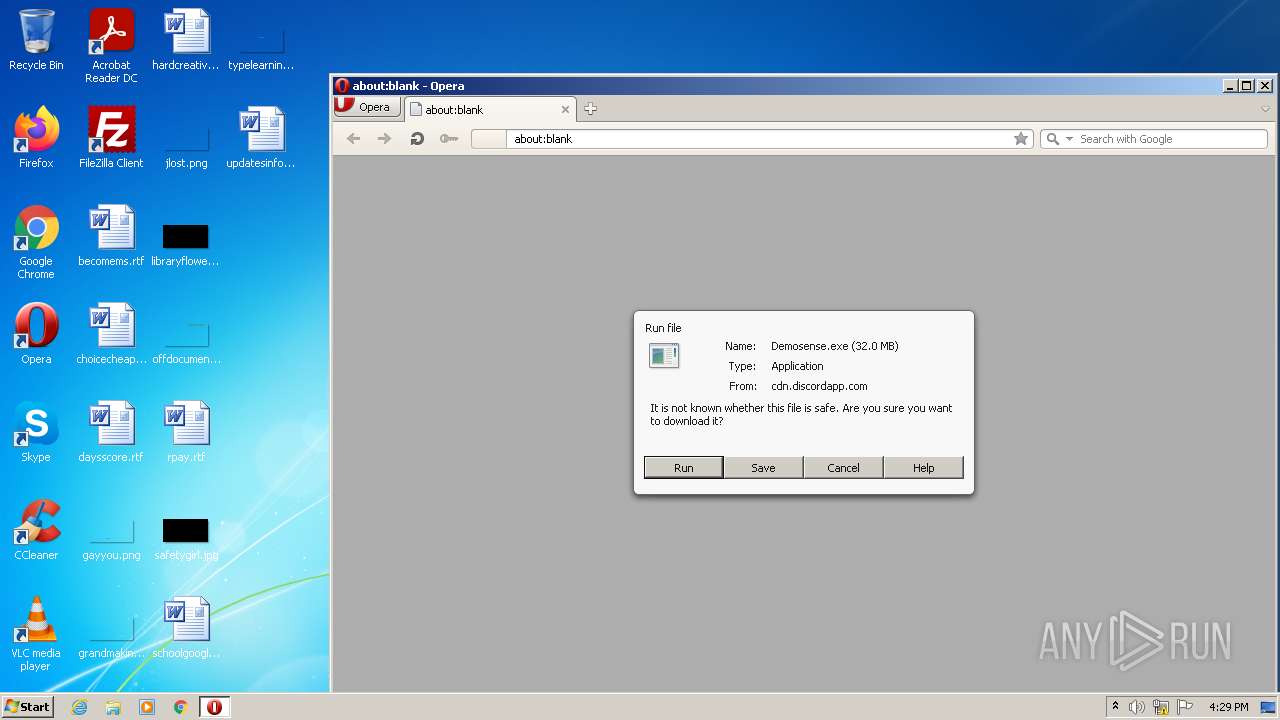
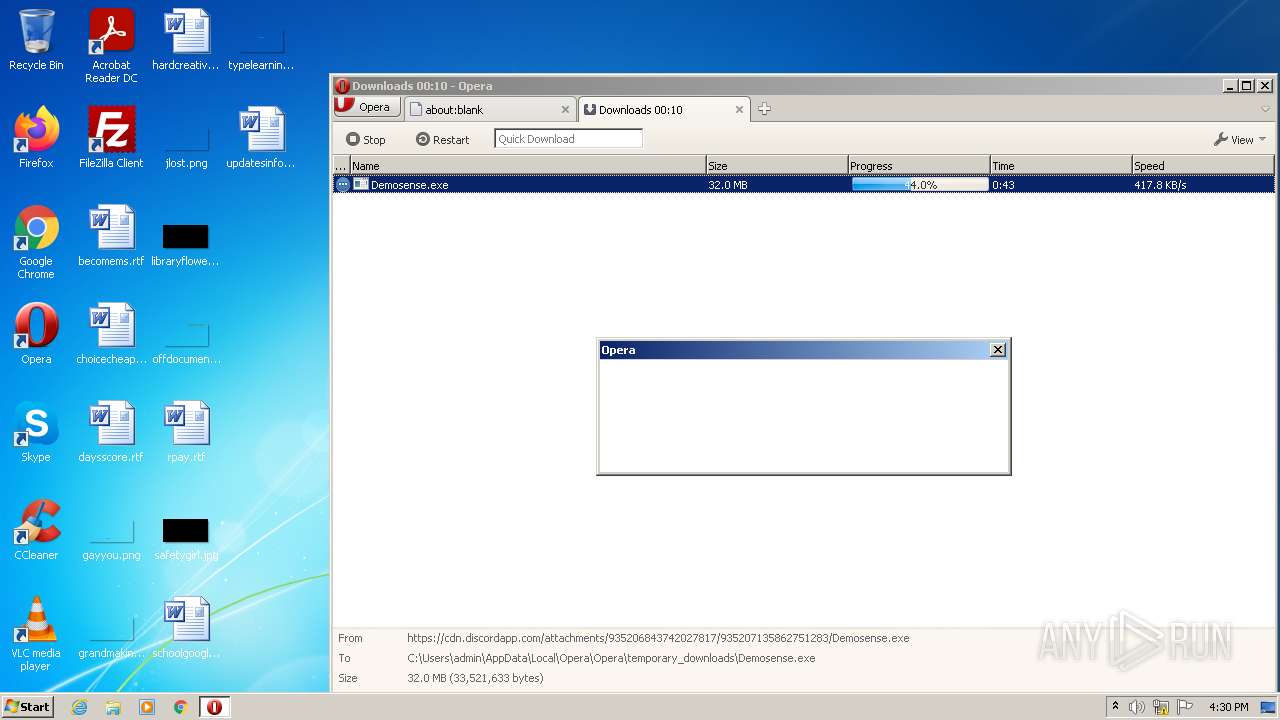
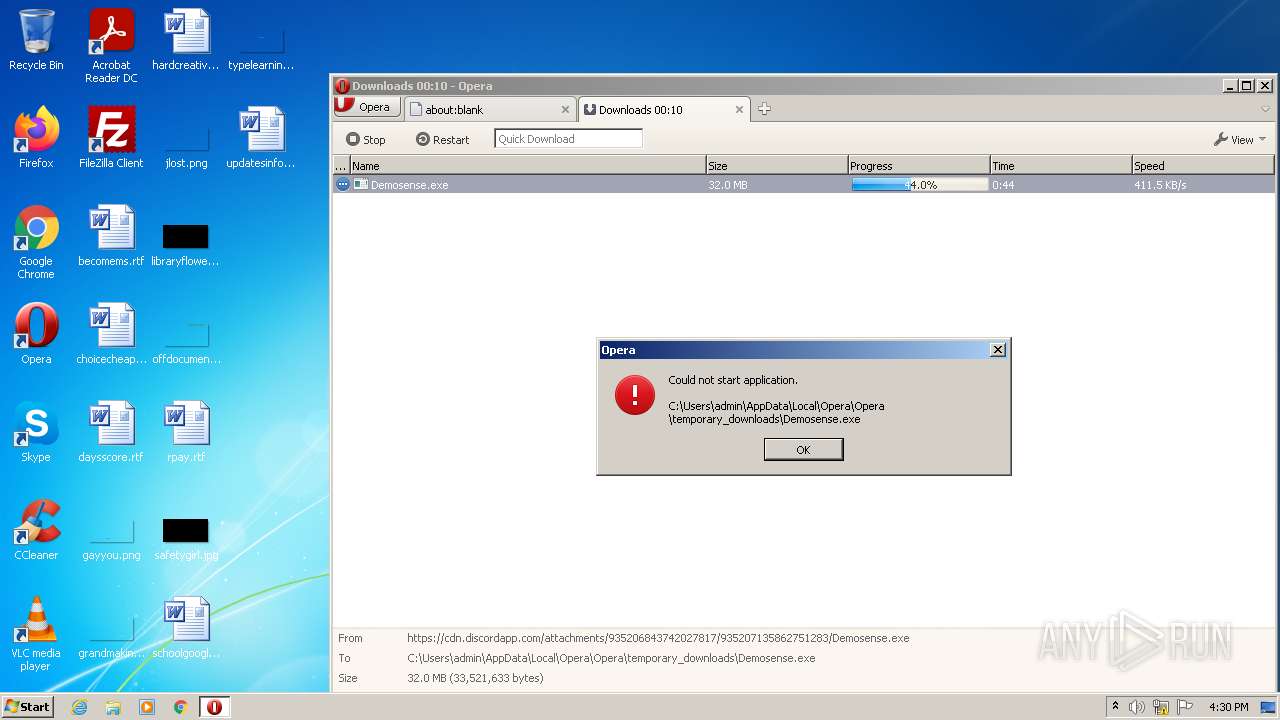
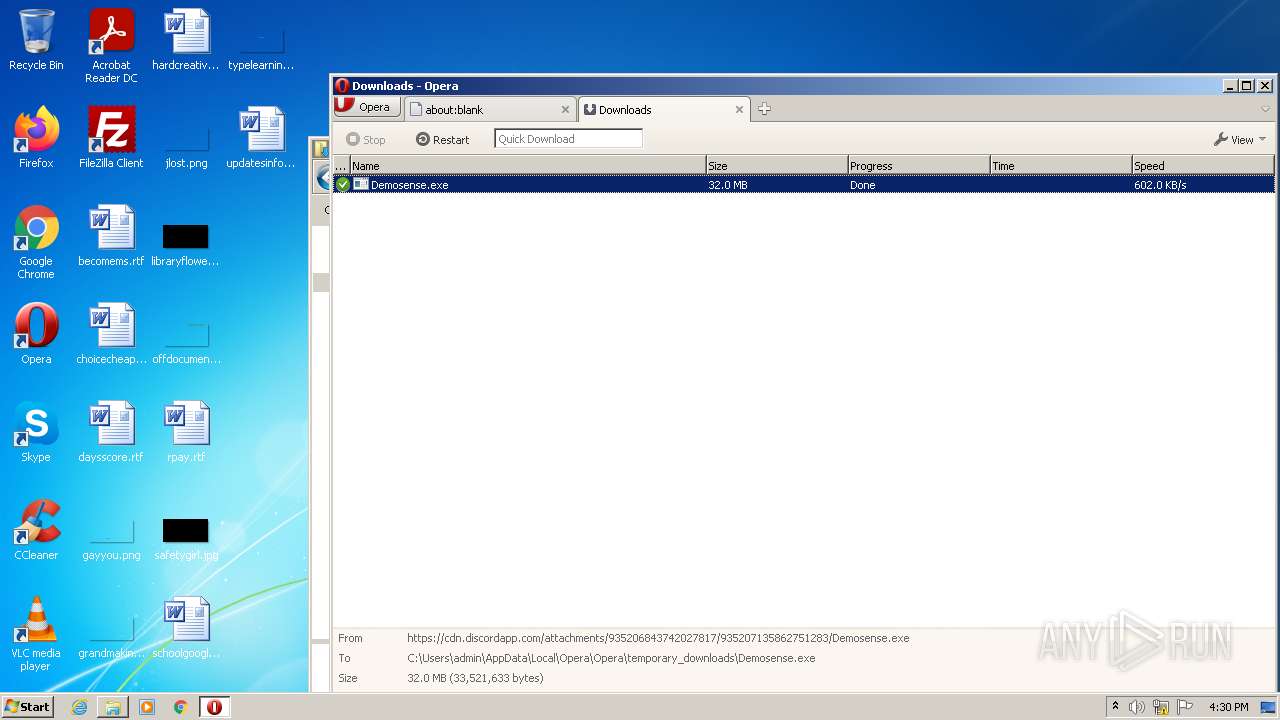
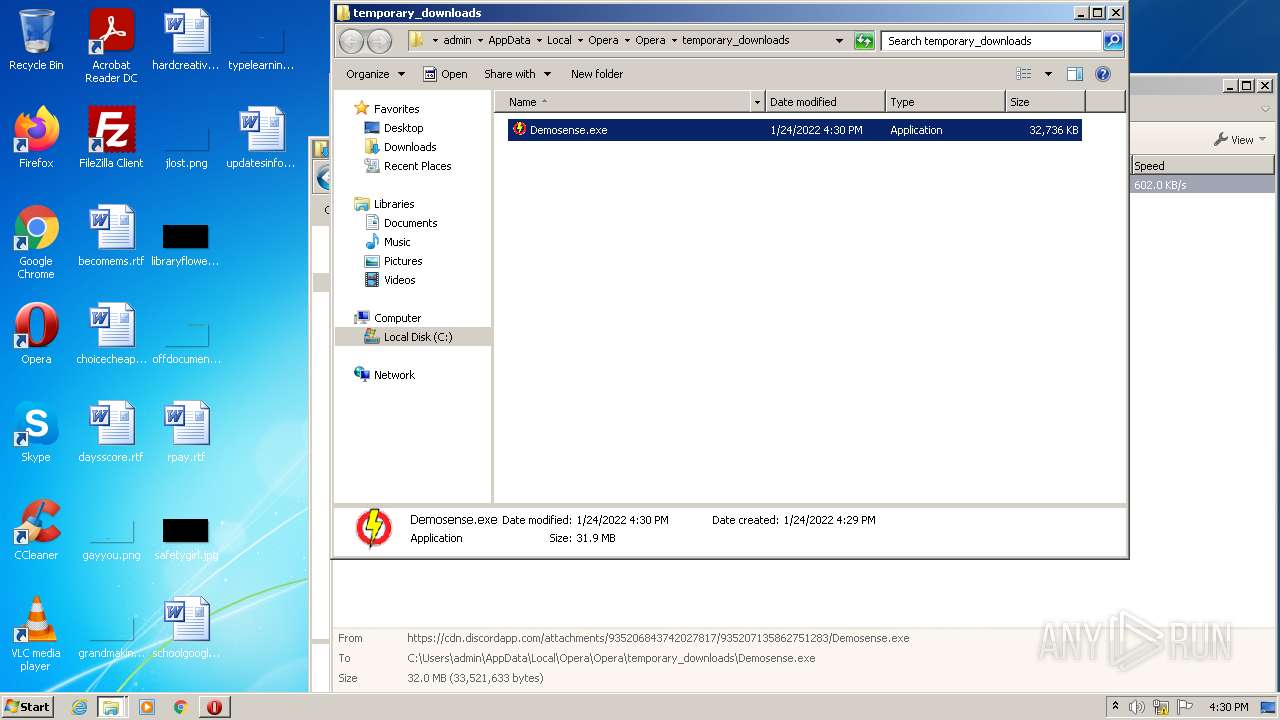
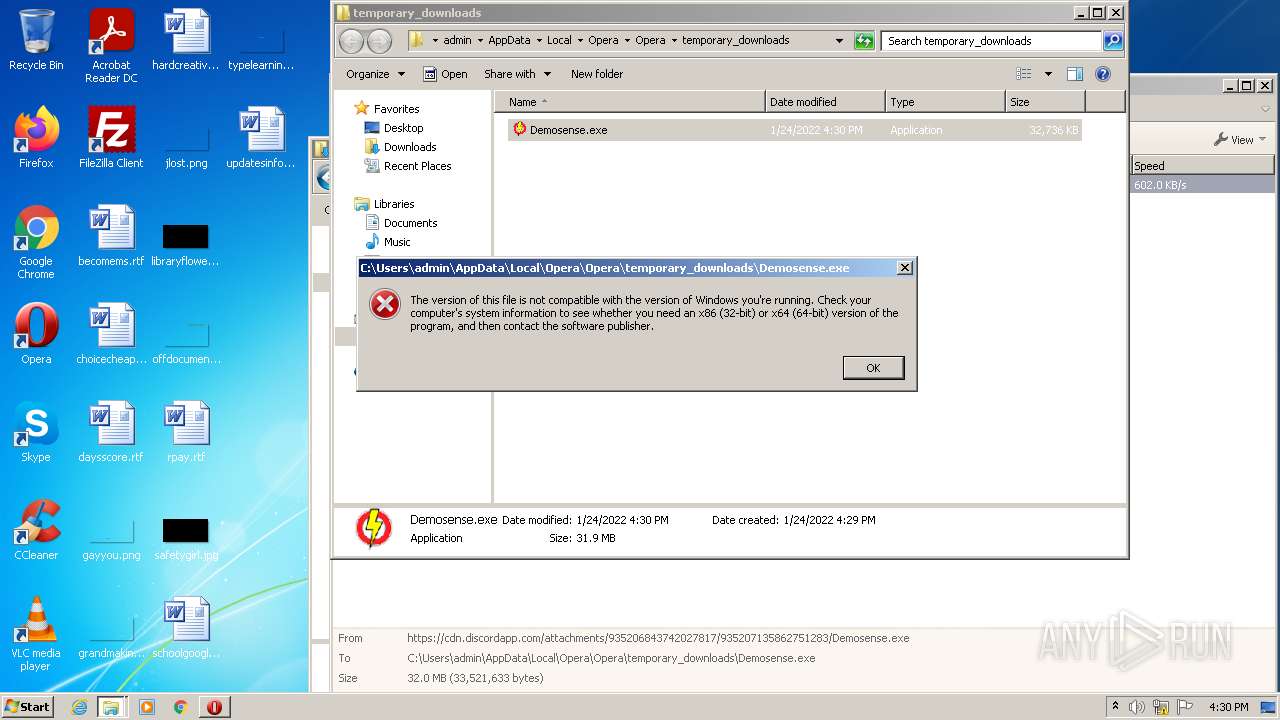
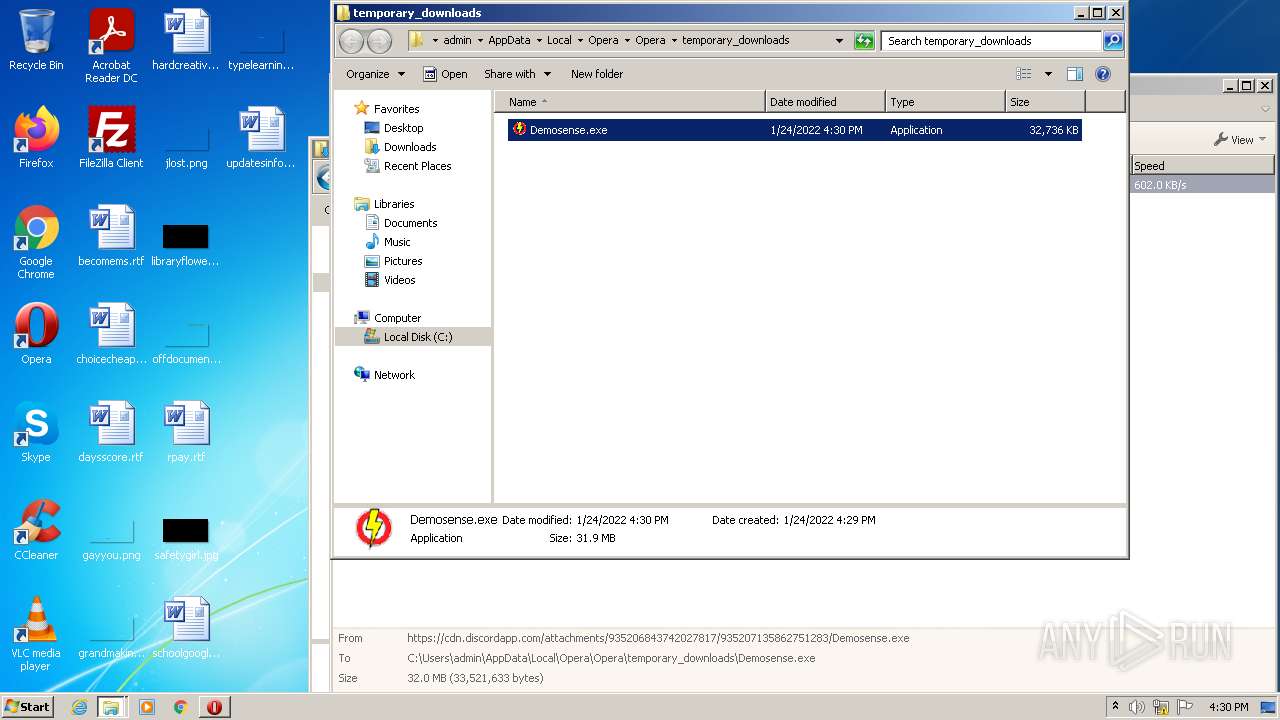
| URL: | https://cdn.discordapp.com/attachments/935206843742027817/935207135862751283/Demosense.exe |
| Full analysis: | https://app.any.run/tasks/ce9af1b2-3533-4ad7-a855-7ae6c238320f |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2022, 16:29:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 004D6ADF715365F71ECBEB1159CB24BA |
| SHA1: | CBA64DE45E569FF2ECF4F7130CEC1F9F3D2E82B6 |
| SHA256: | C48571FF7BBD2CEBD95A822F17AACBDCD0097CCF7AF4BAF10C838D56FD59DCB6 |
| SSDEEP: | 3:N8cCWdy6//nUdRVRFm4oxBHJn:2cry6XnER7Fm4o3p |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3768)
Executable content was dropped or overwritten
- iexplore.exe (PID: 3768)
- opera.exe (PID: 2656)
Executed via COM
- DeviceDisplayObjectProvider.exe (PID: 664)
- DllHost.exe (PID: 1232)
- explorer.exe (PID: 2432)
INFO
Checks supported languages
- iexplore.exe (PID: 3312)
- iexplore.exe (PID: 3768)
- opera.exe (PID: 2556)
- chrome.exe (PID: 2804)
- chrome.exe (PID: 3000)
- chrome.exe (PID: 2768)
- chrome.exe (PID: 3668)
- chrome.exe (PID: 3800)
- chrome.exe (PID: 2492)
- chrome.exe (PID: 188)
- chrome.exe (PID: 1088)
- chrome.exe (PID: 1028)
- chrome.exe (PID: 2476)
- opera.exe (PID: 2656)
- DeviceDisplayObjectProvider.exe (PID: 664)
- explorer.exe (PID: 2744)
- DllHost.exe (PID: 1232)
- explorer.exe (PID: 2432)
Application launched itself
- iexplore.exe (PID: 3312)
- chrome.exe (PID: 2804)
Reads the computer name
- opera.exe (PID: 2556)
- iexplore.exe (PID: 3768)
- iexplore.exe (PID: 3312)
- chrome.exe (PID: 3800)
- chrome.exe (PID: 2804)
- chrome.exe (PID: 3668)
- DllHost.exe (PID: 1232)
- DeviceDisplayObjectProvider.exe (PID: 664)
- opera.exe (PID: 2656)
- explorer.exe (PID: 2744)
- explorer.exe (PID: 2432)
- chrome.exe (PID: 1088)
Checks Windows Trust Settings
- iexplore.exe (PID: 3312)
- iexplore.exe (PID: 3768)
Creates files in the user directory
- opera.exe (PID: 2556)
- opera.exe (PID: 2656)
Reads settings of System Certificates
- iexplore.exe (PID: 3312)
- iexplore.exe (PID: 3768)
- chrome.exe (PID: 3800)
Check for Java to be installed
- opera.exe (PID: 2556)
- opera.exe (PID: 2656)
Manual execution by user
- opera.exe (PID: 2556)
- chrome.exe (PID: 2804)
- opera.exe (PID: 2656)
Dropped object may contain Bitcoin addresses
- opera.exe (PID: 2556)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3312)
Reads the date of Windows installation
- opera.exe (PID: 2556)
- iexplore.exe (PID: 3312)
- opera.exe (PID: 2656)
Changes internet zones settings
- iexplore.exe (PID: 3312)
Reads the hosts file
- chrome.exe (PID: 2804)
- chrome.exe (PID: 3800)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
55
Monitored processes
18
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1032,3497861482697458,13322452240370053754,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2852 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 664 | C:\Windows\system32\DeviceDisplayObjectProvider.exe -Embedding | C:\Windows\system32\DeviceDisplayObjectProvider.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Device Display Object Function Discovery Provider Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1028 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,3497861482697458,13322452240370053754,131072 --enable-features=PasswordImport --lang=en-US --instant-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1836 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1088 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1032,3497861482697458,13322452240370053754,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --use-gl=swiftshader-webgl --mojo-platform-channel-handle=2968 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1232 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2432 | C:\Windows\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2476 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1032,3497861482697458,13322452240370053754,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2956 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2492 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,3497861482697458,13322452240370053754,131072 --enable-features=PasswordImport --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2288 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2556 | "C:\Program Files\Opera\opera.exe" | C:\Program Files\Opera\opera.exe | Explorer.EXE | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Internet Browser Exit code: 0 Version: 1748 Modules
| |||||||||||||||
| 2656 | "C:\Program Files\Opera\opera.exe" | C:\Program Files\Opera\opera.exe | Explorer.EXE | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Internet Browser Exit code: 0 Version: 1748 Modules
| |||||||||||||||
Total events
30 207
Read events
29 812
Write events
393
Delete events
2
Modification events
| (PID) Process: | (3312) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3312) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3312) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30937407 | |||
| (PID) Process: | (3312) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3312) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30937407 | |||
| (PID) Process: | (3312) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3312) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3312) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3312) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3312) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
4
Suspicious files
55
Text files
65
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3312 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2556 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\operaprefs.ini | text | |
MD5:— | SHA256:— | |||
| 2556 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr5B1E.tmp | xml | |
MD5:— | SHA256:— | |||
| 2556 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\tasks.xml | xml | |
MD5:— | SHA256:— | |||
| 2556 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr5ACF.tmp | text | |
MD5:— | SHA256:— | |||
| 3312 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:— | SHA256:— | |||
| 3312 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\StructuredQuery.log | text | |
MD5:— | SHA256:— | |||
| 2556 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\GGC0LT6ER4E74NWAFL47.temp | binary | |
MD5:— | SHA256:— | |||
| 2556 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opssl6.dat | binary | |
MD5:— | SHA256:— | |||
| 2804 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-61EED3EE-AF4.pma | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
61
DNS requests
24
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2656 | opera.exe | GET | 301 | 142.250.184.206:80 | http://youtube.com/ | US | — | — | whitelisted |
2556 | opera.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 592 b | whitelisted |
3768 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
3312 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
2656 | opera.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/Omniroot2025.crl | US | der | 7.68 Kb | whitelisted |
3312 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
2656 | opera.exe | GET | — | 142.250.185.110:80 | http://clients1.google.com/complete/search?q=youtube&client=opera-suggest-omnibox&hl=de | US | — | — | whitelisted |
2556 | opera.exe | GET | 200 | 185.26.182.110:80 | http://redir.opera.com/favicons/google/favicon.ico | unknown | image | 5.30 Kb | whitelisted |
3312 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?eebe35231b25f1cc | US | compressed | 4.70 Kb | whitelisted |
3312 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ce5e98476f0082cc | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2556 | opera.exe | 162.159.129.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
3768 | iexplore.exe | 162.159.129.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
3312 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
3312 | iexplore.exe | 13.107.22.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3312 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3768 | iexplore.exe | 13.107.5.80:443 | api.bing.com | Microsoft Corporation | US | whitelisted |
3768 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3768 | iexplore.exe | 162.159.135.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
3800 | chrome.exe | 142.250.74.206:443 | clients2.google.com | Google Inc. | US | whitelisted |
3800 | chrome.exe | 142.250.186.77:443 | accounts.google.com | Google Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cdn.discordapp.com |
| shared |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
certs.opera.com |
| whitelisted |
crl3.digicert.com |
| whitelisted |
sitecheck2.opera.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2556 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2556 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2556 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2656 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |