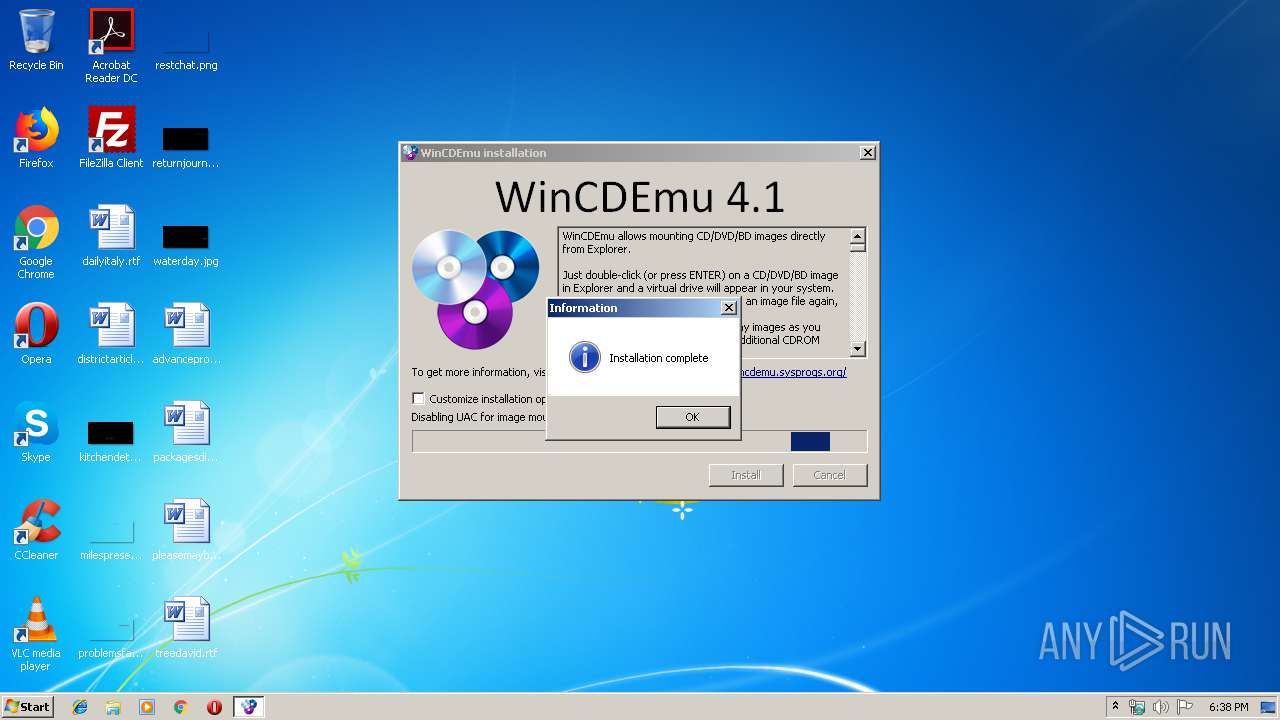
| File name: | WinCDEmu-4.1.exe |
| Full analysis: | https://app.any.run/tasks/87eef481-a0f0-40b2-a1ac-1438ccb015a2 |
| Verdict: | Malicious activity |
| Analysis date: | April 23, 2019, 17:37:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 4E53BEFE779F677B1CCEC54B84F60A8C |
| SHA1: | 9FF4F2ED41D5BD09496D2CFB6E09C4B31659DC19 |
| SHA256: | C47763631D20120057766F2F71F781BF958E22712DA4AC933B21DB0D615DC93C |
| SSDEEP: | 49152:kCFdVNpsRKZdJ0ya6wWfumwumbp/afUD+6EVV4dDD/:kaVNpsIF0ya6wWf32p/69Z4dDj |
MALICIOUS
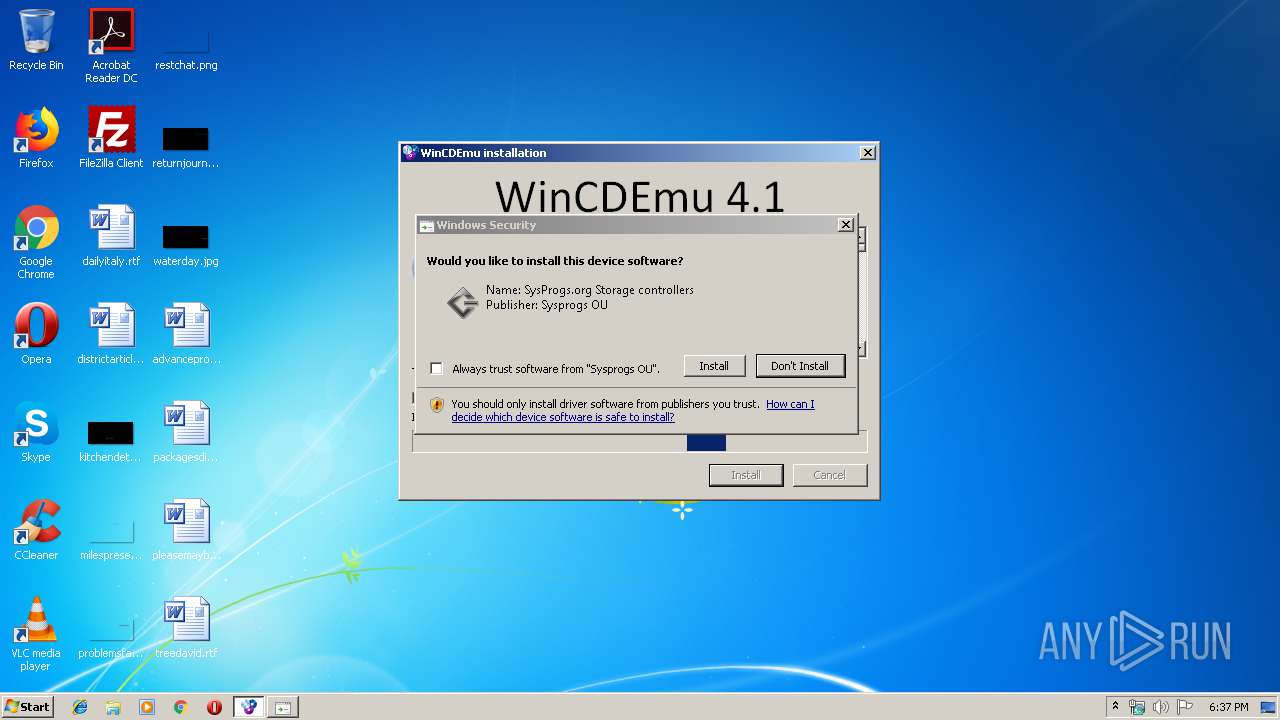
Registers / Runs the DLL via REGSVR32.EXE
- uninstall.exe (PID: 2356)
Loads dropped or rewritten executable
- regsvr32.exe (PID: 2816)
- regsvr32.exe (PID: 884)
Application was dropped or rewritten from another process
- uninstall.exe (PID: 2356)
- VirtualAutorunDisabler.exe (PID: 3388)
- drvinst32.exe (PID: 3356)
- vmnt.exe (PID: 3932)
Changes settings of System certificates
- drvinst32.exe (PID: 3356)
SUSPICIOUS
Creates files in the program directory
- WinCDEmu-4.1.exe (PID: 3888)
Executable content was dropped or overwritten
- WinCDEmu-4.1.exe (PID: 3888)
- drvinst32.exe (PID: 3356)
- DrvInst.exe (PID: 3060)
- DrvInst.exe (PID: 3408)
Modifies the open verb of a shell class
- WinCDEmu-4.1.exe (PID: 3888)
Adds / modifies Windows certificates
- drvinst32.exe (PID: 3356)
Creates COM task schedule object
- regsvr32.exe (PID: 884)
- regsvr32.exe (PID: 2816)
Creates files in the Windows directory
- DrvInst.exe (PID: 3408)
- DrvInst.exe (PID: 3060)
Creates files in the driver directory
- DrvInst.exe (PID: 3408)
- DrvInst.exe (PID: 3060)
Removes files from Windows directory
- DrvInst.exe (PID: 3408)
- DrvInst.exe (PID: 3060)
Uses RUNDLL32.EXE to load library
- DrvInst.exe (PID: 3408)
Searches for installed software
- DrvInst.exe (PID: 3408)
Creates a software uninstall entry
- WinCDEmu-4.1.exe (PID: 3888)
INFO
Changes settings of System certificates
- DrvInst.exe (PID: 3408)
Low-level read access rights to disk partition
- vssvc.exe (PID: 1380)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (39.3) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (38.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (9.5) |
| .exe | | | Win32 Executable (generic) (6.5) |
| .exe | | | Generic Win/DOS Executable (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2015:09:30 20:31:31+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 118784 |
| InitializedDataSize: | 40960 |
| UninitializedDataSize: | 249856 |
| EntryPoint: | 0x5a900 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.1.0.0 |
| ProductVersionNumber: | 4.1.0.0 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | http://wincdemu.sysprogs.org/ |
| CompanyName: | Sysprogs OU |
| FileDescription: | WinCDEmu installer |
| FileVersion: | 4.1 |
| LegalCopyright: | LGPL |
| LegalTrademarks: | Sysprogs |
| OriginalFileName: | WinCDEmu-installer.exe |
| ProductName: | WinCDEmu |
| ProductVersion: | 4.1 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 30-Sep-2015 18:31:31 |
| Detected languages: |
|
| Comments: | http://wincdemu.sysprogs.org/ |
| CompanyName: | Sysprogs OU |
| FileDescription: | WinCDEmu installer |
| FileVersion: | 4.1 |
| LegalCopyright: | LGPL |
| LegalTrademarks: | Sysprogs |
| OriginalFilename: | WinCDEmu-installer.exe |
| ProductName: | WinCDEmu |
| ProductVersion: | 4.1 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000F8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 30-Sep-2015 18:31:31 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
UPX0 | 0x00001000 | 0x0003D000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
UPX1 | 0x0003E000 | 0x0001D000 | 0x0001CC00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.92791 |
.rsrc | 0x0005B000 | 0x0000A000 | 0x00009A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.51966 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.20785 | 886 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 7.41892 | 498 | Latin 1 / Western European | Russian - Russia | RT_DIALOG |
3 | 7.42632 | 528 | Latin 1 / Western European | Russian - Russia | RT_DIALOG |
4 | 7.42614 | 432 | Latin 1 / Western European | Russian - Russia | RT_DIALOG |
5 | 6.89497 | 374 | Latin 1 / Western European | Russian - Russia | RT_DIALOG |
6 | 7.61588 | 744 | Latin 1 / Western European | Russian - Russia | RT_ICON |
7 | 7.56565 | 872 | Latin 1 / Western European | Russian - Russia | RT_ICON |
8 | 7.67495 | 1248 | Latin 1 / Western European | Russian - Russia | RT_STRING |
9 | 7.39595 | 702 | Latin 1 / Western European | Russian - Russia | RT_STRING |
70 | 7.25449 | 626 | Latin 1 / Western European | UNKNOWN | RT_STRING |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.DLL |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
48
Monitored processes
14
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 884 | "C:\Windows\System32\regsvr32.exe" /s "C:\Program Files\WinCDEmu\x86\VirtualAutorunDisablerPS.dll" | C:\Windows\System32\regsvr32.exe | — | uninstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1380 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2356 | "C:\Program Files\WinCDEmu\uninstall.exe" /UPDATE | C:\Program Files\WinCDEmu\uninstall.exe | — | WinCDEmu-4.1.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2600 | C:\Windows\System32\rundll32.exe shell32.dll,SHCreateLocalServerRunDll {995C996E-D918-4a8c-A302-45719A6F4EA7} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2816 | "C:\Windows\System32\regsvr32.exe" /s "C:\Program Files\WinCDEmu\x86\WinCDEmuContextMenu.dll" | C:\Windows\System32\regsvr32.exe | — | uninstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3060 | DrvInst.exe "2" "211" "ROOT\SCSIADAPTER\0000" "C:\Windows\INF\oem4.inf" "bazisvirtualcdbus.inf:Standard:BazisVirtualCDBus_Device:4.1.1.0:root\bazisvirtualcdbus" "6aa431c33" "0000053C" "000005D0" "000005E4" | C:\Windows\system32\DrvInst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3084 | "C:\Users\admin\AppData\Local\Temp\WinCDEmu-4.1.exe" | C:\Users\admin\AppData\Local\Temp\WinCDEmu-4.1.exe | — | explorer.exe | |||||||||||
User: admin Company: Sysprogs OU Integrity Level: MEDIUM Description: WinCDEmu installer Exit code: 3221226540 Version: 4.1 Modules
| |||||||||||||||
| 3148 | DrvInst.exe "1" "200" "STORAGE\VolumeSnapshot\HarddiskVolumeSnapshot18" "" "" "6792c44eb" "00000000" "000005E4" "000005E0" | C:\Windows\system32\DrvInst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3240 | rundll32.exe C:\Windows\system32\pnpui.dll,InstallSecurityPromptRunDllW 20 Global\{35c71a00-44c9-7ea7-2a6f-1a64fc668f75} Global\{703a2c06-5c15-497e-d598-3007c0d8326e} C:\Windows\System32\DriverStore\Temp\{3c1b5b34-ce6f-09a5-6988-2c65f0a7ec4a}\bazisvirtualcdbus.inf C:\Windows\System32\DriverStore\Temp\{3c1b5b34-ce6f-09a5-6988-2c65f0a7ec4a}\BazisVirtualCDBus.cat | C:\Windows\system32\rundll32.exe | — | DrvInst.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3356 | C:\Users\admin\AppData\Local\Temp\ssi187D.tmp\drvinst32.exe instroot "root\BazisVirtualCDBus" "C:\Program Files\WinCDEmu\BazisVirtualCDBus.inf" | C:\Users\admin\AppData\Local\Temp\ssi187D.tmp\drvinst32.exe | WinCDEmu-4.1.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
695
Read events
368
Write events
327
Delete events
0
Modification events
| (PID) Process: | (3888) WinCDEmu-4.1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Applications\vmnt.exe\shell\open\command |
| Operation: | write | Name: | |
Value: "C:\Program Files\WinCDEmu\vmnt.exe" "%1" | |||
| (PID) Process: | (3888) WinCDEmu-4.1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Windows.IsoFile\shell\open\command |
| Operation: | write | Name: | |
Value: "C:\Program Files\WinCDEmu\vmnt.exe" "%1" | |||
| (PID) Process: | (3888) WinCDEmu-4.1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.iso |
| Operation: | write | Name: | Application |
Value: vmnt.exe | |||
| (PID) Process: | (3888) WinCDEmu-4.1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\VLC.cue\shell\Open\command |
| Operation: | write | Name: | |
Value: "C:\Program Files\WinCDEmu\vmnt.exe" "%1" | |||
| (PID) Process: | (3888) WinCDEmu-4.1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.cue |
| Operation: | write | Name: | Application |
Value: vmnt.exe | |||
| (PID) Process: | (3888) WinCDEmu-4.1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.img |
| Operation: | write | Name: | Application |
Value: vmnt.exe | |||
| (PID) Process: | (3888) WinCDEmu-4.1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\.nrg |
| Operation: | write | Name: | |
Value: BazisVirtualCD.Nrg | |||
| (PID) Process: | (3888) WinCDEmu-4.1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\BazisVirtualCD.Nrg |
| Operation: | write | Name: | |
Value: Nero CD/DVD image | |||
| (PID) Process: | (3888) WinCDEmu-4.1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\BazisVirtualCD.Nrg\DefaultIcon |
| Operation: | write | Name: | |
Value: %SystemRoot%\System32\shell32.dll,11 | |||
| (PID) Process: | (3888) WinCDEmu-4.1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\BazisVirtualCD.Nrg\shell\open\command |
| Operation: | write | Name: | |
Value: "C:\Program Files\WinCDEmu\vmnt.exe" "%1" | |||
Executable files
21
Suspicious files
63
Text files
245
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3888 | WinCDEmu-4.1.exe | C:\Program Files\WinCDEmu\x64\WinCDEmuContextMenu.dll | executable | |
MD5:E3526F364347D94C329A8CA6D8DF17DA | SHA256:0CA454FA57A90A4D899E0797D0AFF5364260F3649B963D21582FA7010E419C2A | |||
| 3888 | WinCDEmu-4.1.exe | C:\Program Files\WinCDEmu\batchmnt.exe | executable | |
MD5:5E6561921A7722EA025A79172E7B443E | SHA256:C694D42D19DAA784687B9146D19B7797B937E151A8AA7155904F54A1A6FD7A84 | |||
| 3888 | WinCDEmu-4.1.exe | C:\Program Files\WinCDEmu\mkisofs.exe | executable | |
MD5:298B00E6DC408F5EA4FAD8FF173028D5 | SHA256:19F7C8771CCE642A15984C73C4BEE2B441D6C47236958D8F5A7EB05738B0DA4B | |||
| 3888 | WinCDEmu-4.1.exe | C:\Program Files\WinCDEmu\uninstall.exe | executable | |
MD5:168CF87105D81FD649C2D49F91C53496 | SHA256:6A8F9819384A46411ACD85297D895D650766271D476EFEB3392134D6784680C5 | |||
| 3888 | WinCDEmu-4.1.exe | C:\Program Files\WinCDEmu\x64\WinCDEmuContextMenu.bak | executable | |
MD5:03A9955EC55C5C6E00A3281602B30132 | SHA256:24B62E505F0A612FED69A425A9FD0F3459E76941ADD8FB6CCC3F43C64F12A7BE | |||
| 3888 | WinCDEmu-4.1.exe | C:\Program Files\WinCDEmu\batchmnt64.exe | executable | |
MD5:EF5F980E1E1DBDF454673206751BF255 | SHA256:4A363E27B849A994250E6F2E4C9B4DD56F70F7CF9FF78375B3EE23244F1F9B6E | |||
| 3888 | WinCDEmu-4.1.exe | C:\Program Files\WinCDEmu\vmnt64.exe | executable | |
MD5:BF26C935FFD4C25FFF6731DBF73D2212 | SHA256:40DBCF0EC787455837EC5D7439874B1CE6F586A570AF8D5132F09CEC531B97C7 | |||
| 3888 | WinCDEmu-4.1.exe | C:\Program Files\WinCDEmu\langfiles\vmnt_Bengali.lng | binary | |
MD5:D23C884983ACDD3E39D905B456A93810 | SHA256:A7F22EA0BBBF9C22AC7E3B6F72785E41CABEAB35A762A55CDD0782015A5DD029 | |||
| 3888 | WinCDEmu-4.1.exe | C:\Program Files\WinCDEmu\vmnt.exe | executable | |
MD5:EEAE83A94A6364A8A640E0F6CACCFD85 | SHA256:6B642BABB6E9AC67CBB35AD29A5437E774DC4E82442A3F23EE3889DF07D54039 | |||
| 3888 | WinCDEmu-4.1.exe | C:\Program Files\WinCDEmu\langfiles\vmnt_bahasaindonesia.lng | binary | |
MD5:EE1B69AD806DC238CDB3494D15EDAFAB | SHA256:42C1AC4600E24BF102D4F1ABE41275B275BF9A10196219049EEA33F1B21DE40C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report