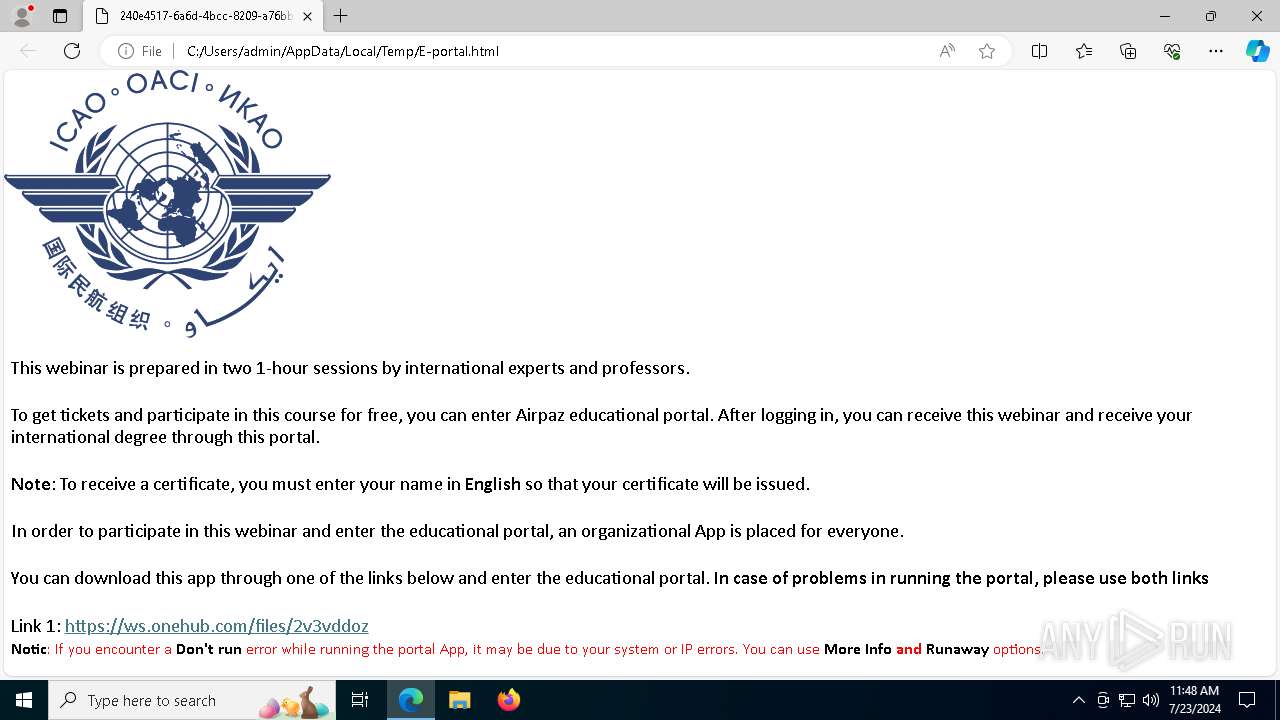
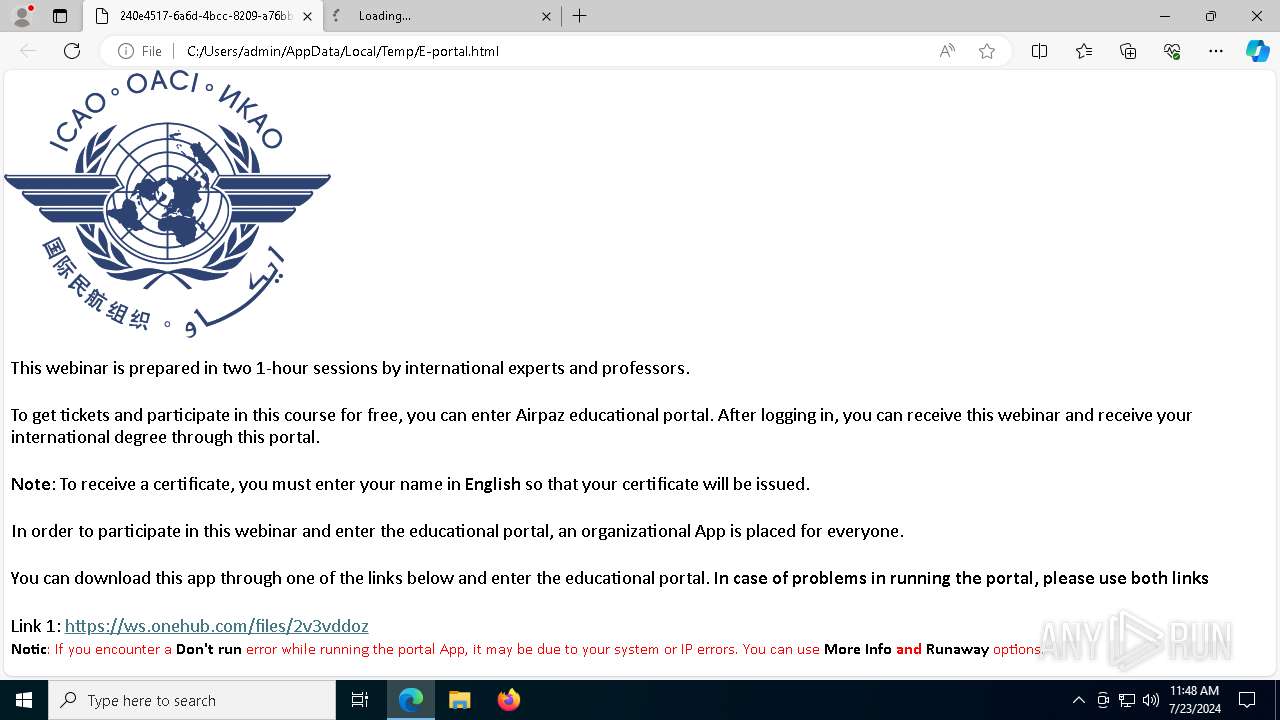
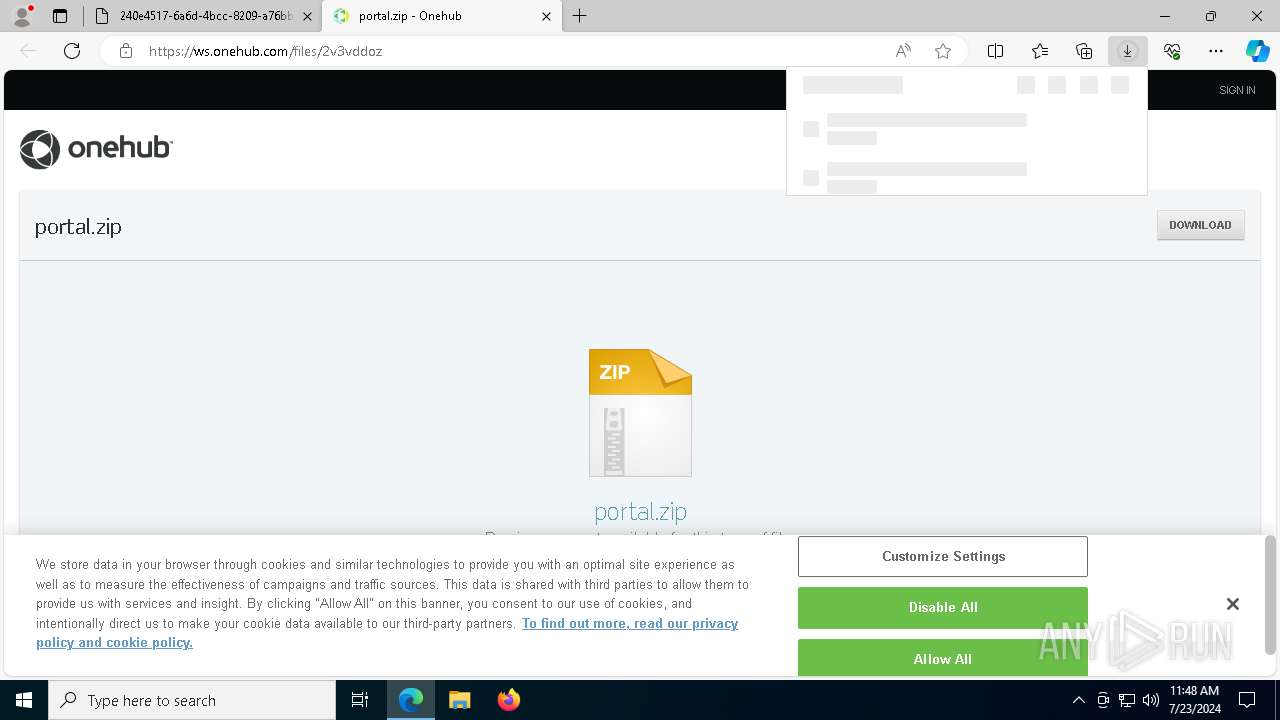
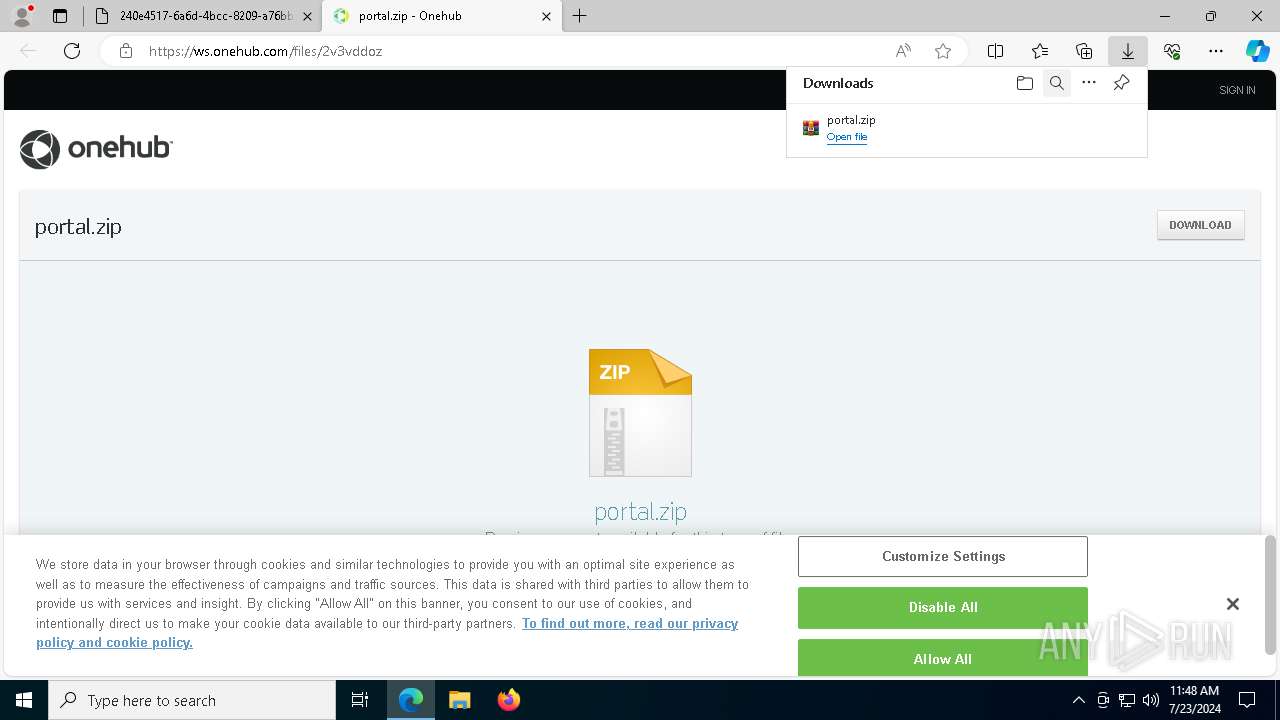
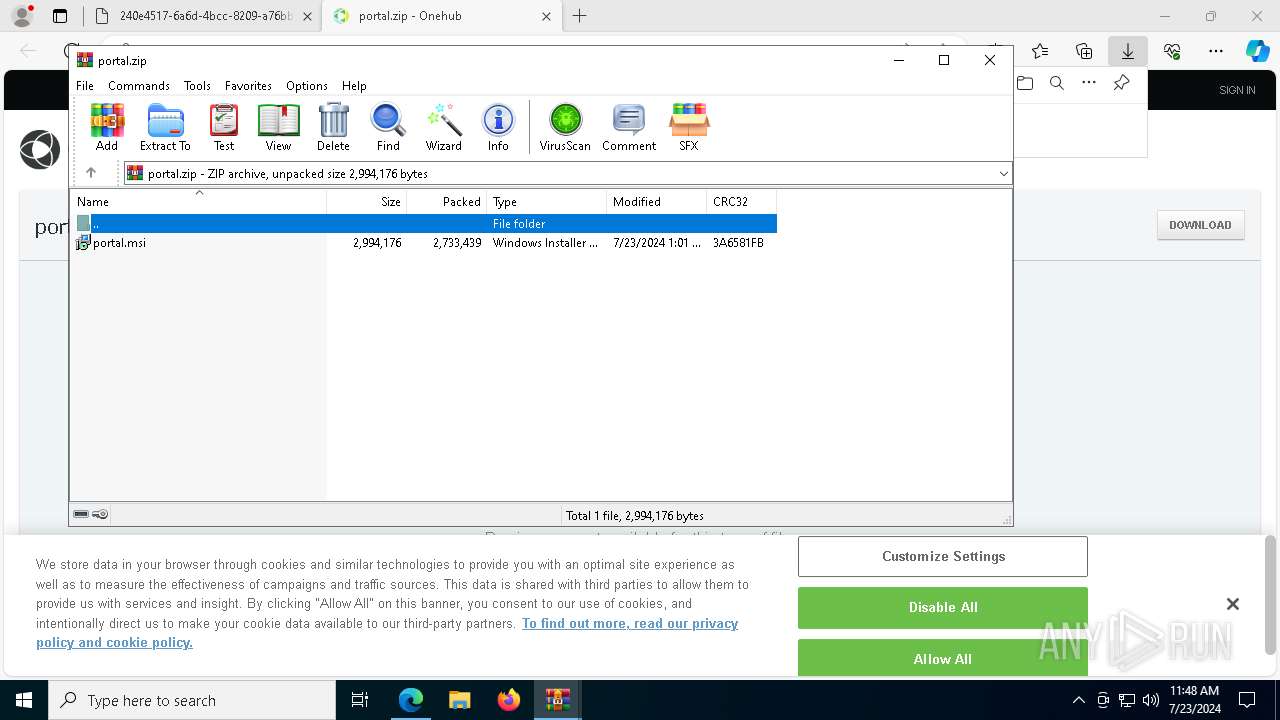
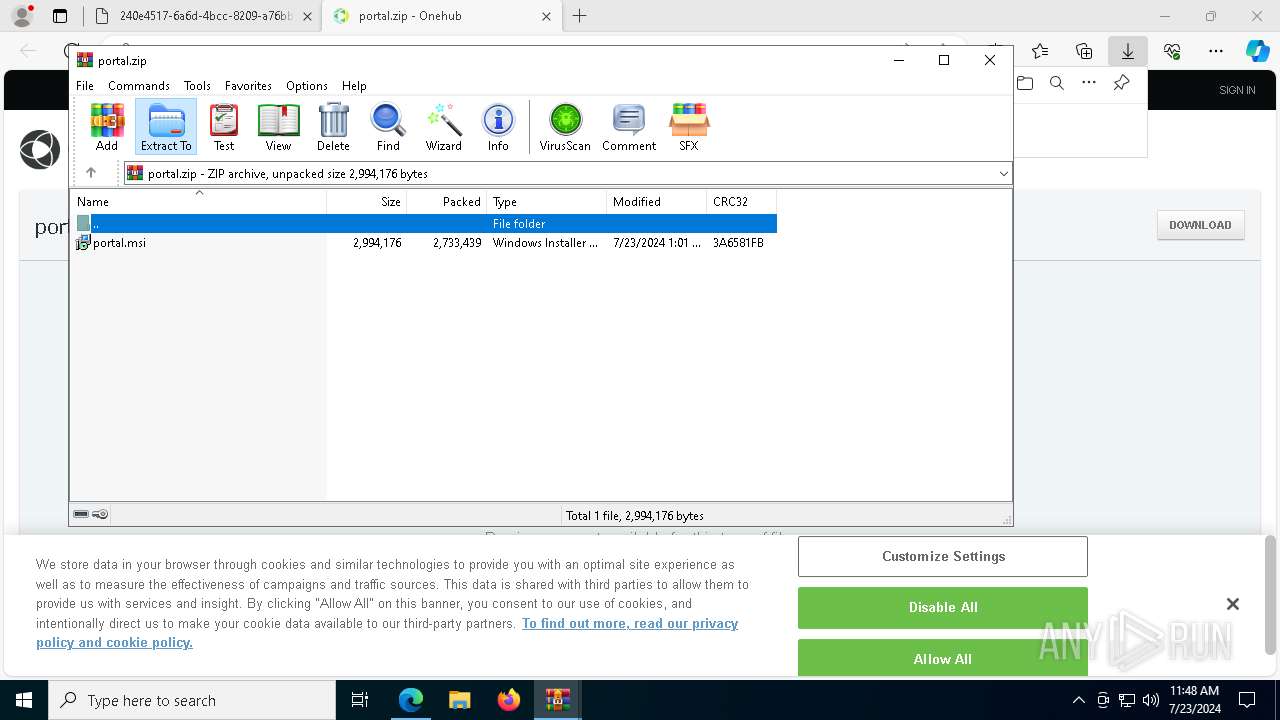
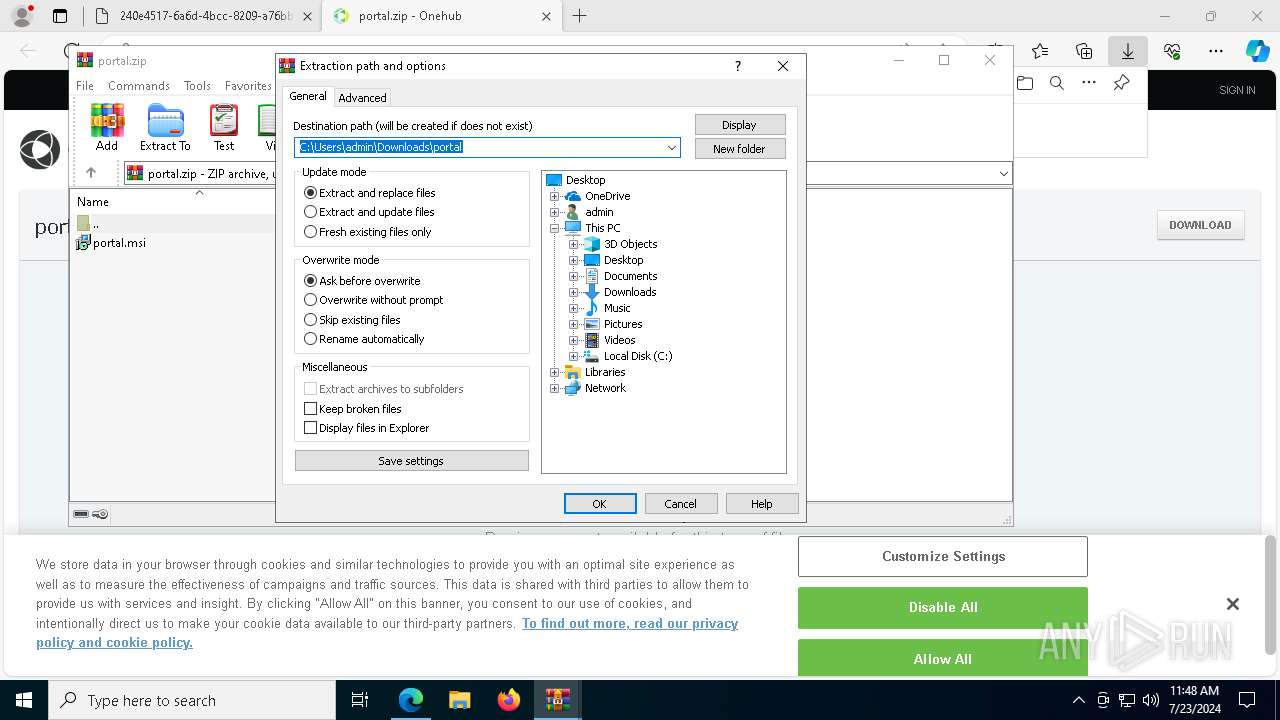
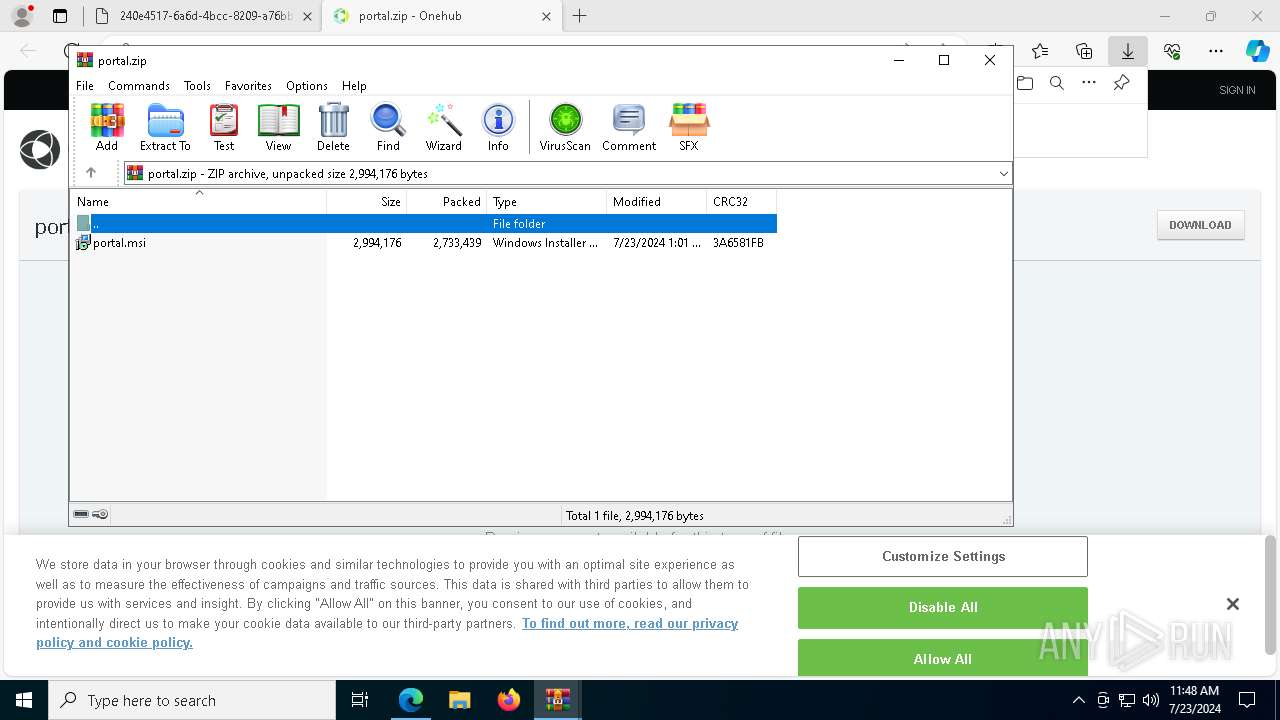
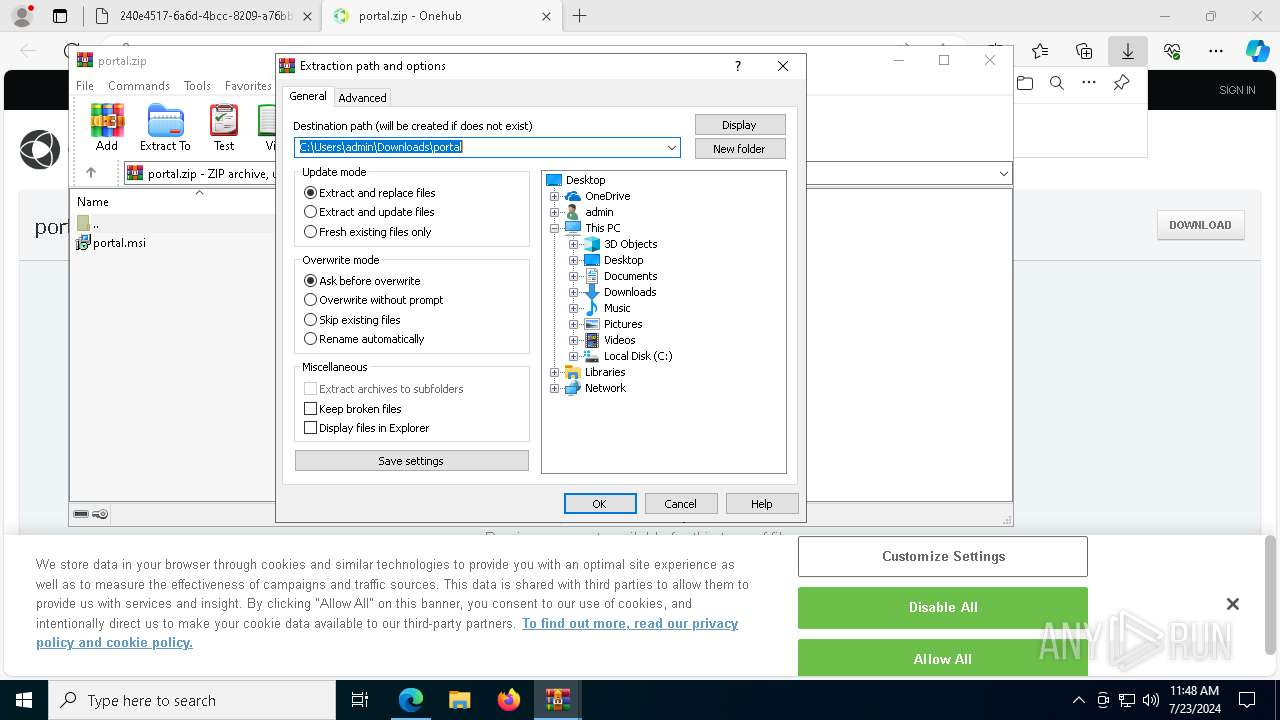
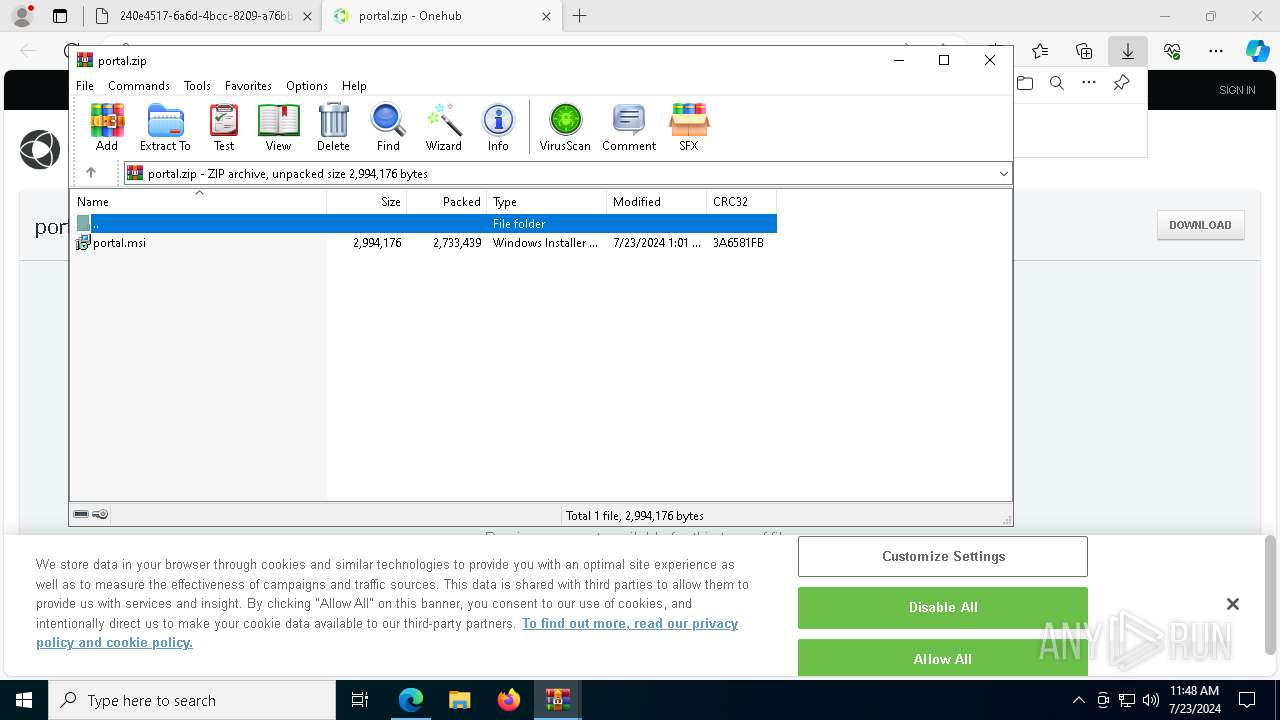
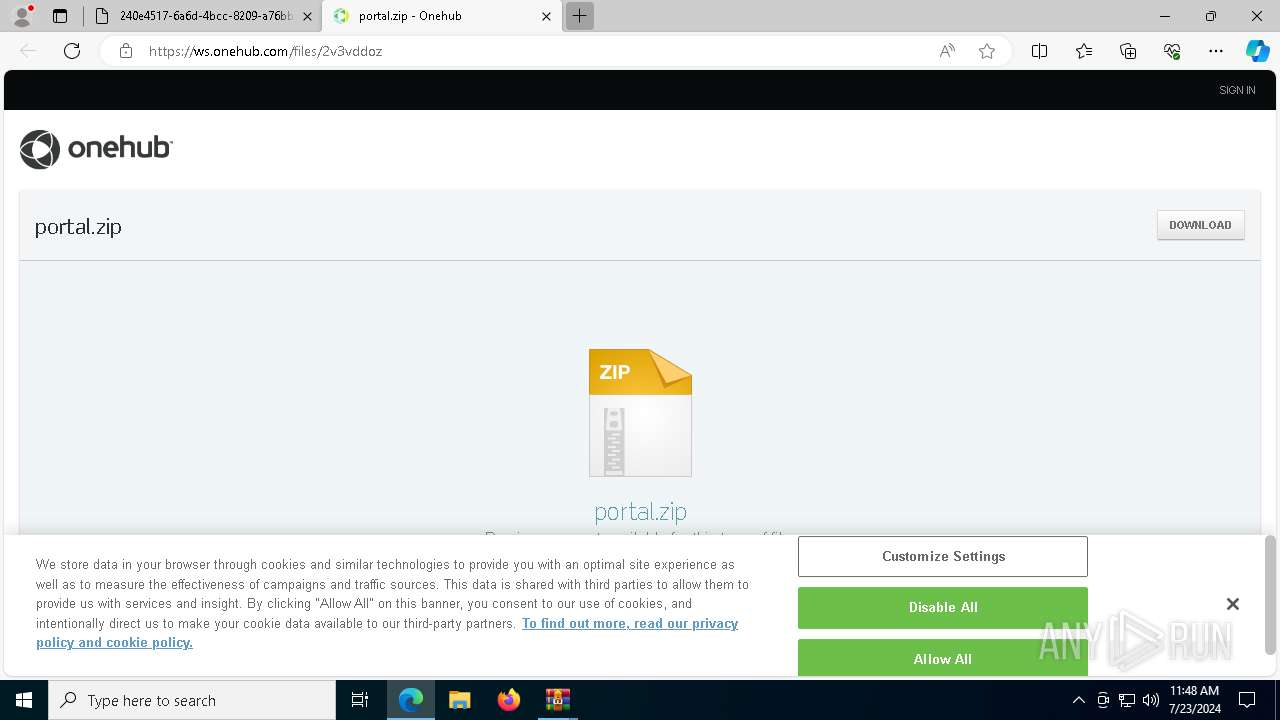
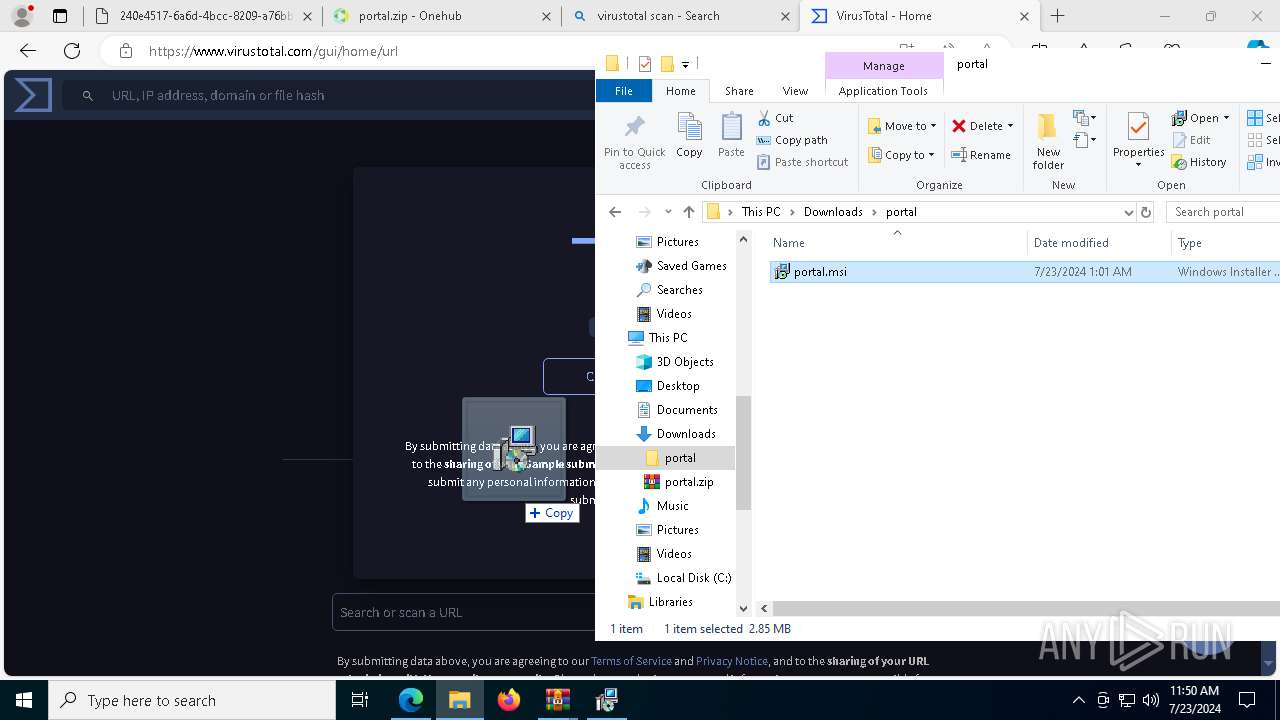
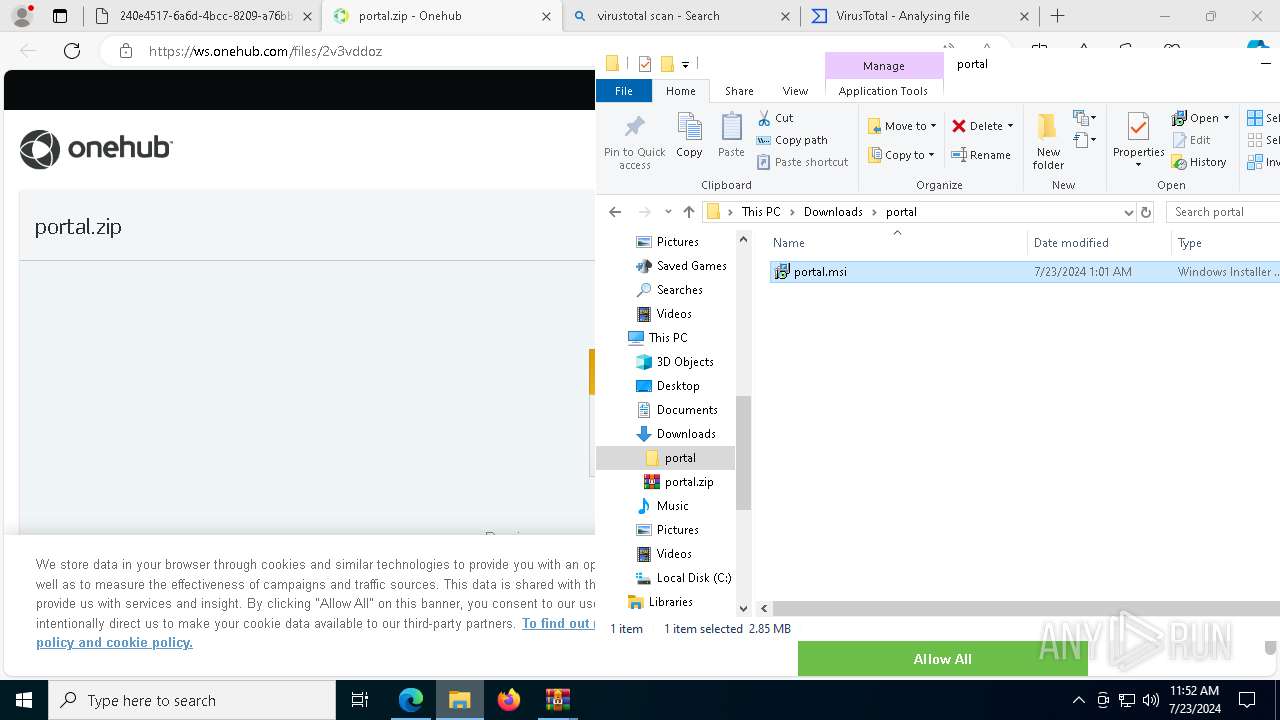
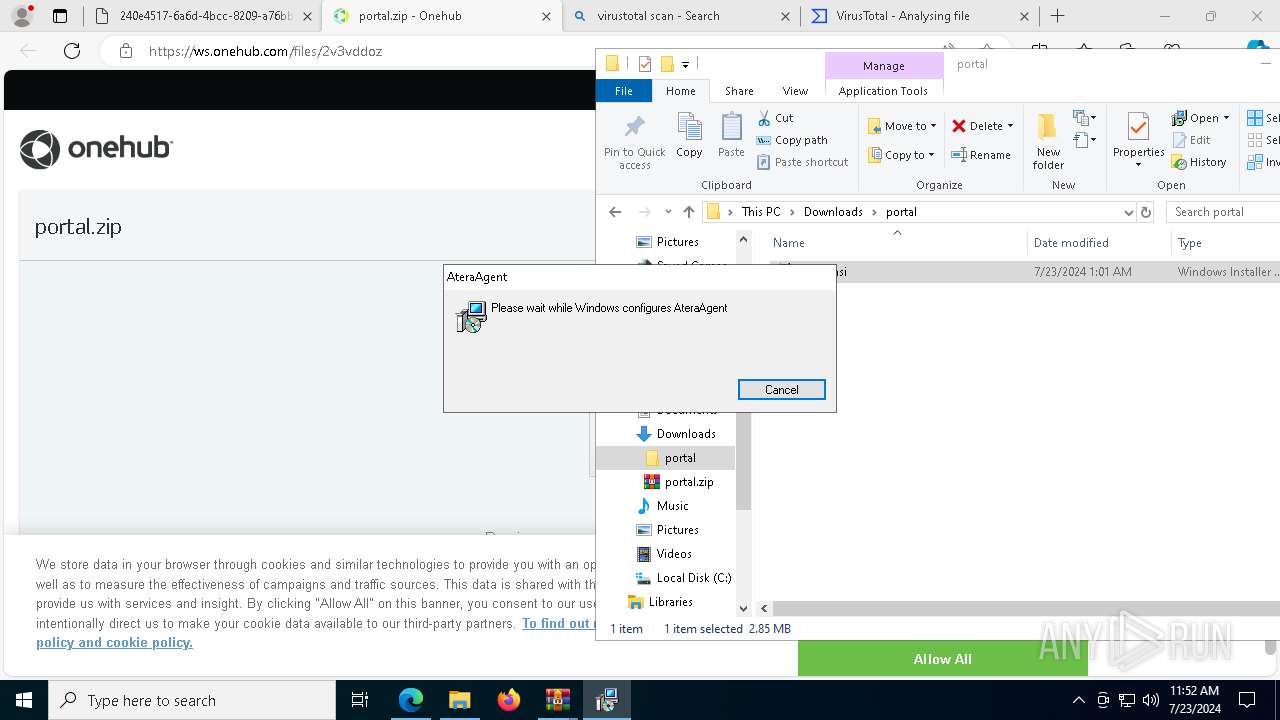
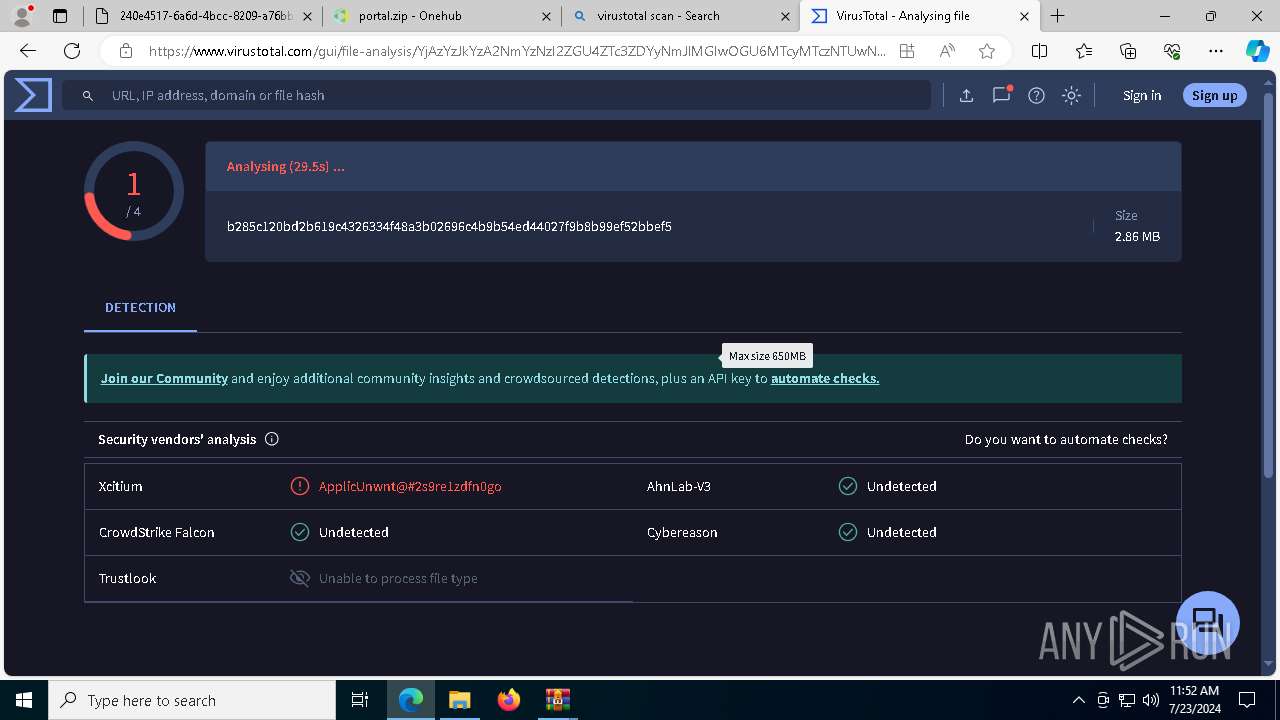
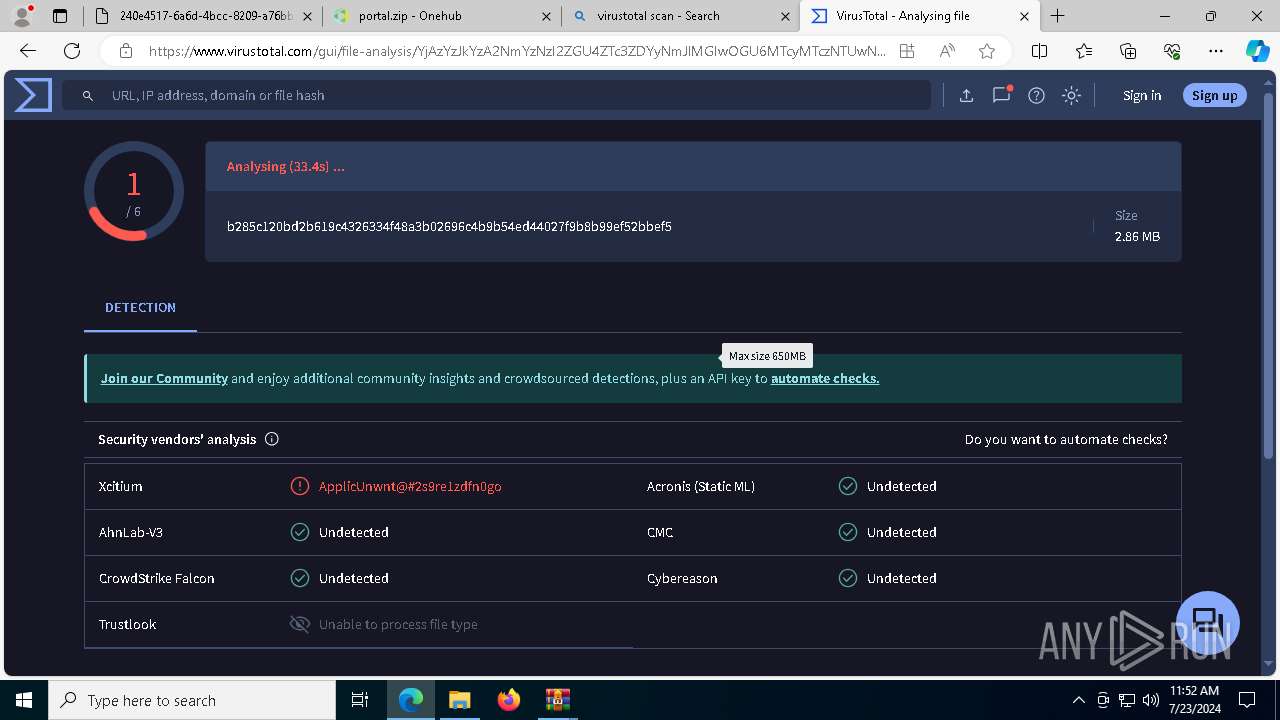
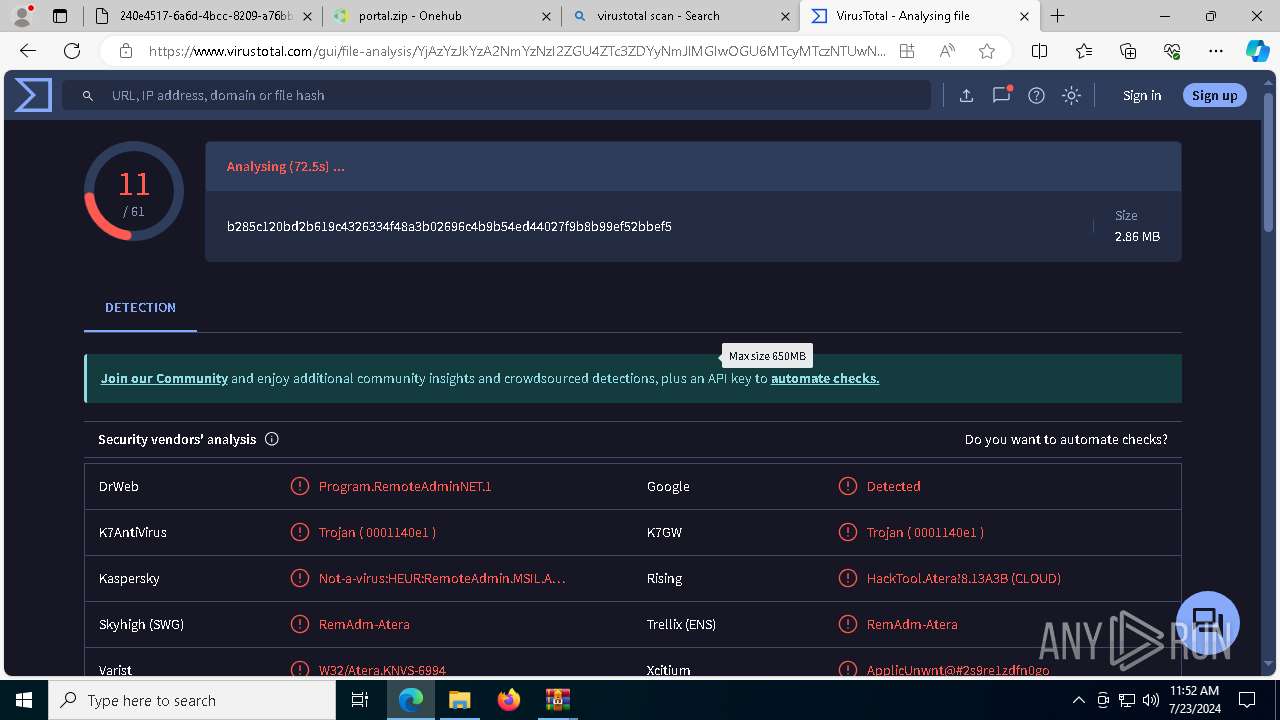
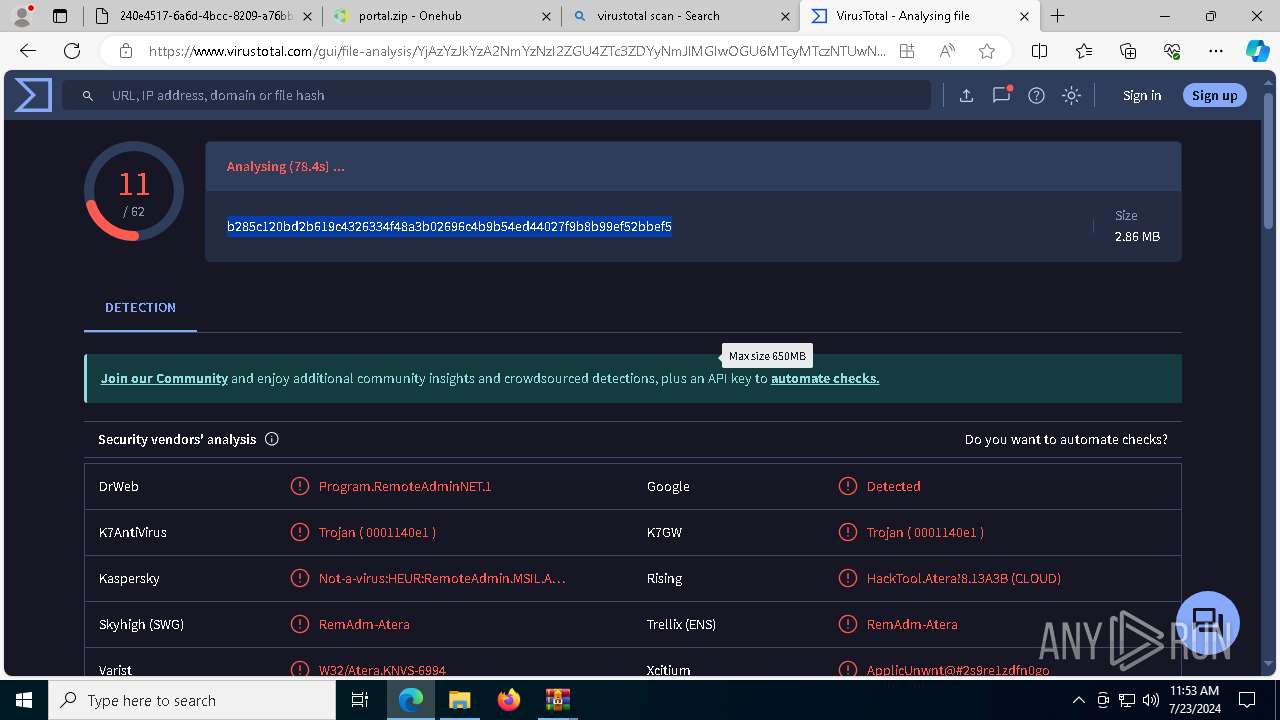
| File name: | E-portal.html |
| Full analysis: | https://app.any.run/tasks/29bc8b66-458b-474f-9c6d-a6ad6d1af313 |
| Verdict: | Malicious activity |
| Analysis date: | July 23, 2024, 11:48:08 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, ASCII text, with very long lines (64414) |
| MD5: | EF4D30FCC1E37EBC362F81918824EF8D |
| SHA1: | 21118ACD97C0780FB4F7C5DAC8736158988FEFDB |
| SHA256: | C44939E5E44096B8BACBA52BC8B7F1B9F0934EDB6DB5C733CE525996F6374E0A |
| SSDEEP: | 3072:sVUSNnIGCqh2/xS5i7zfEL8C9h+ZdhVvyg+E/1:rcIGN58TELdT+ZAgR/1 |
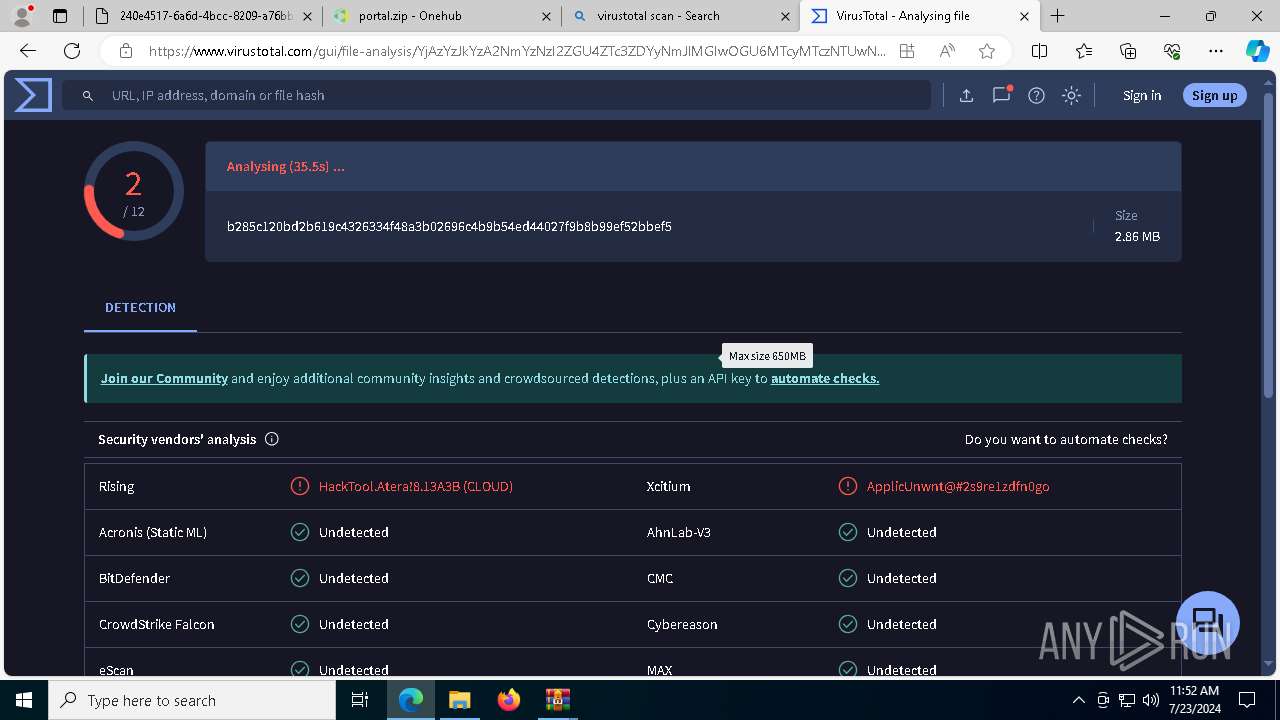
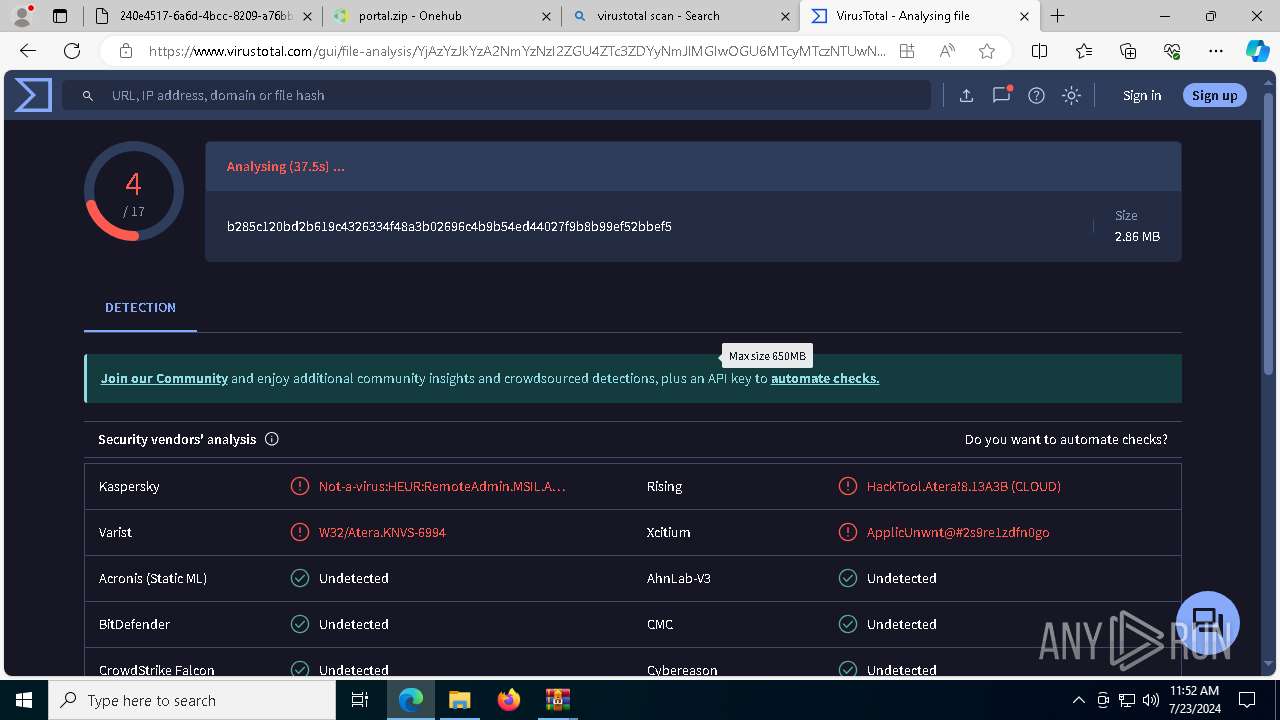
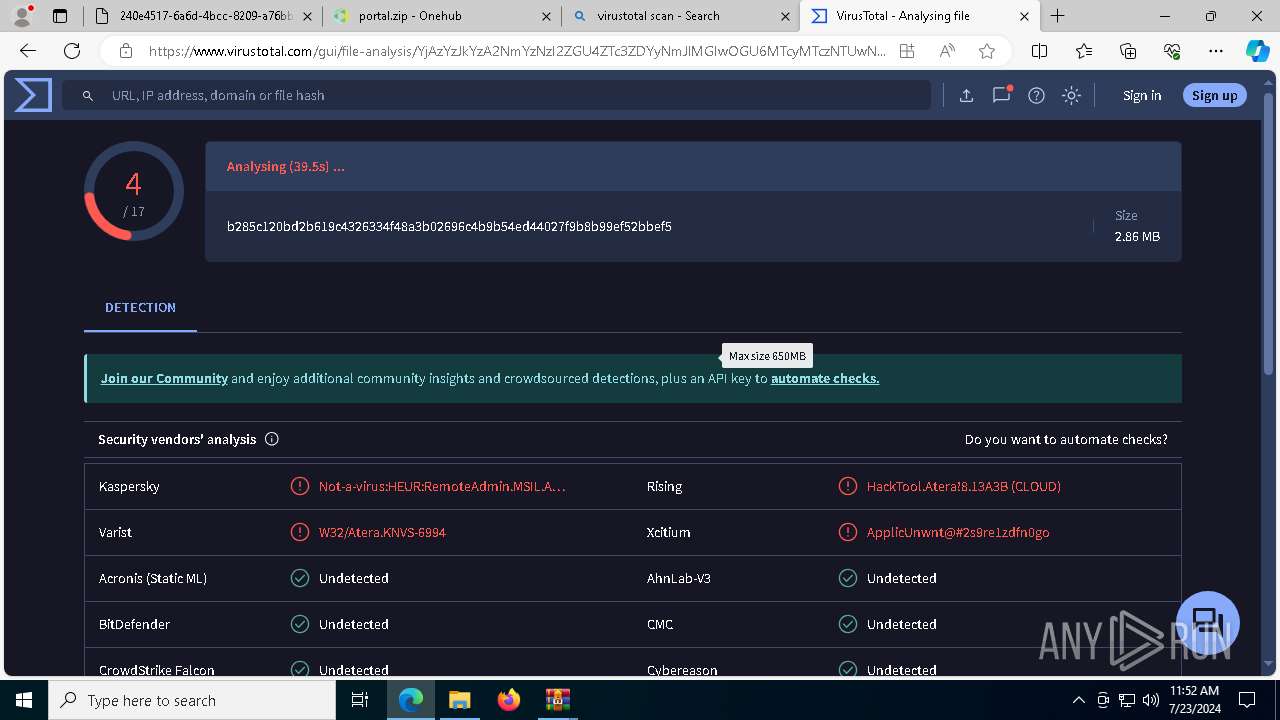
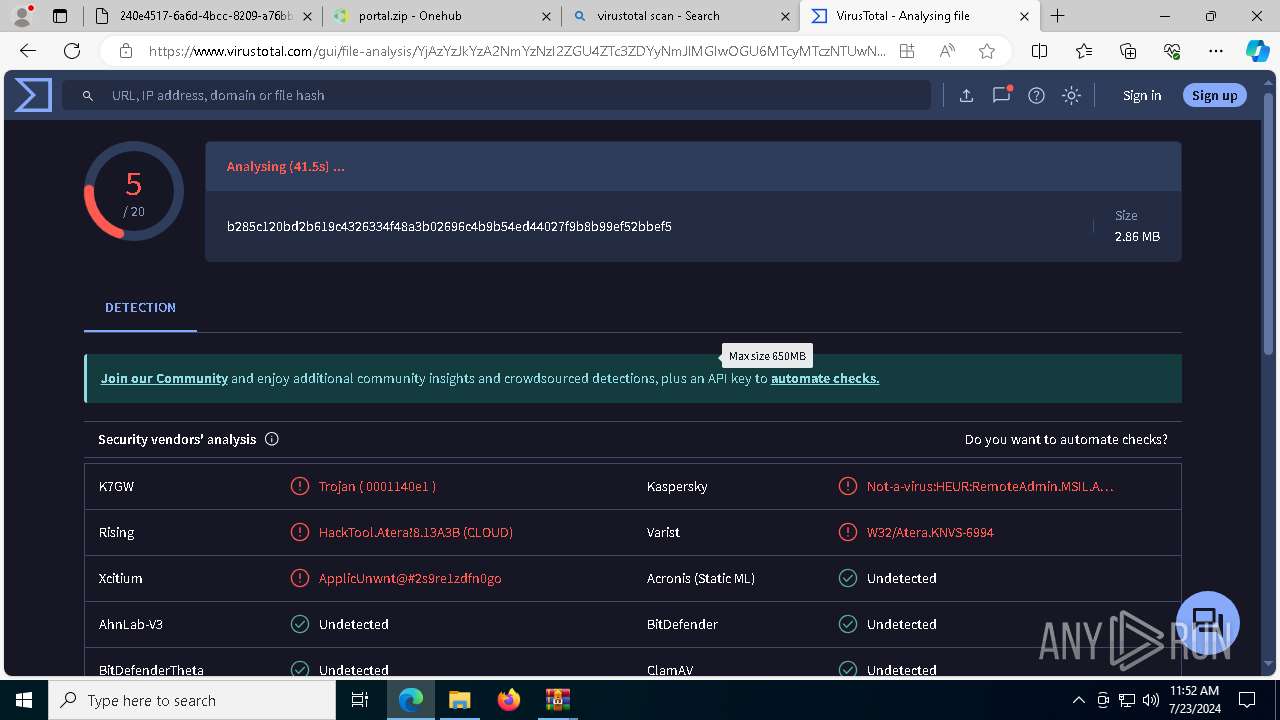
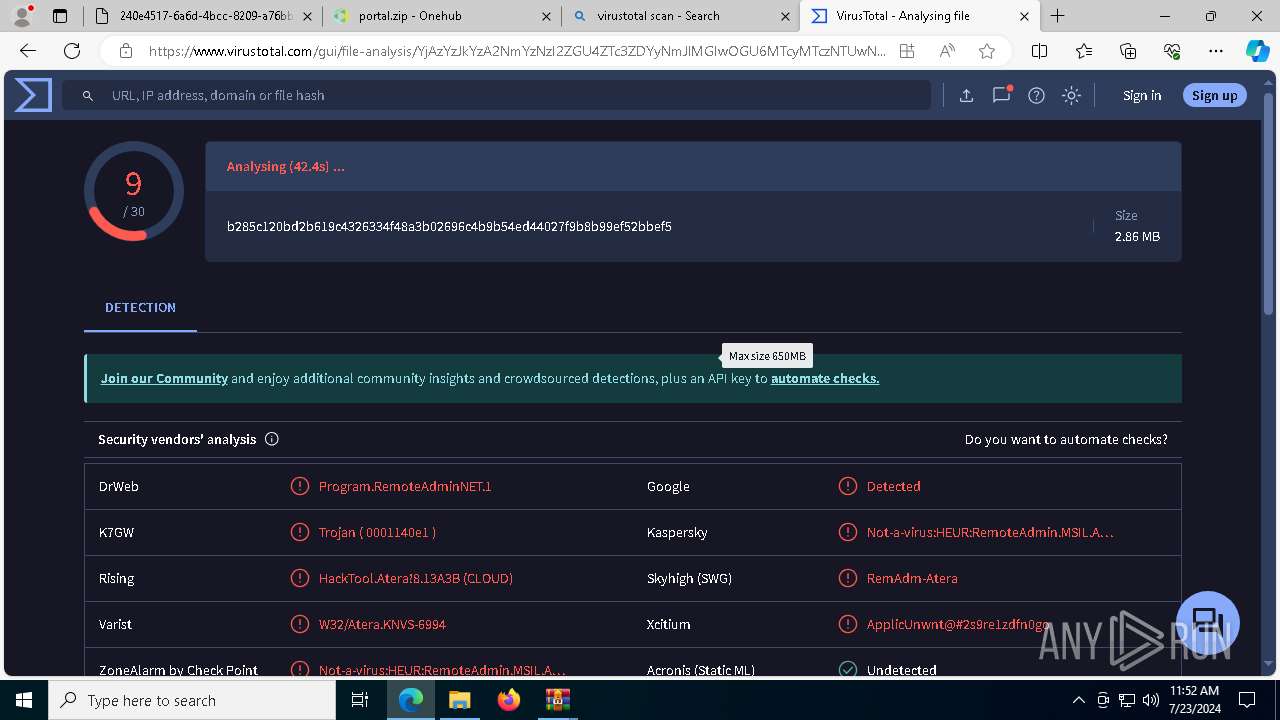
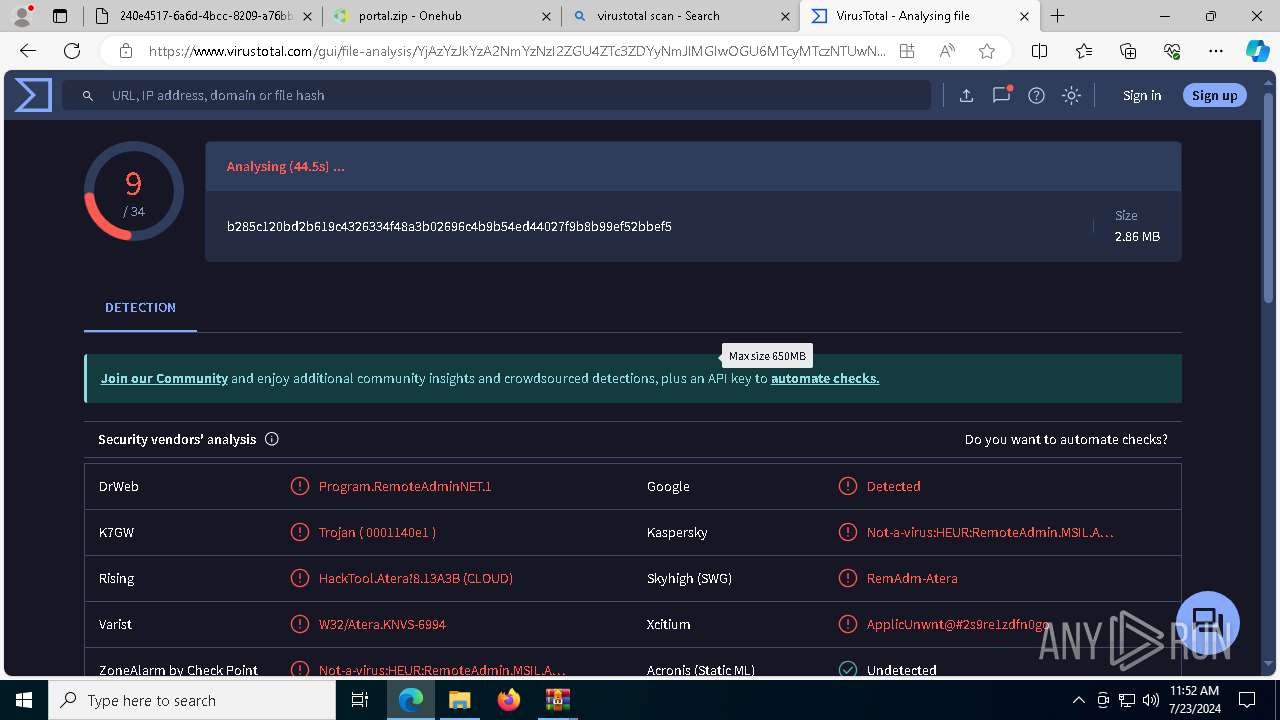
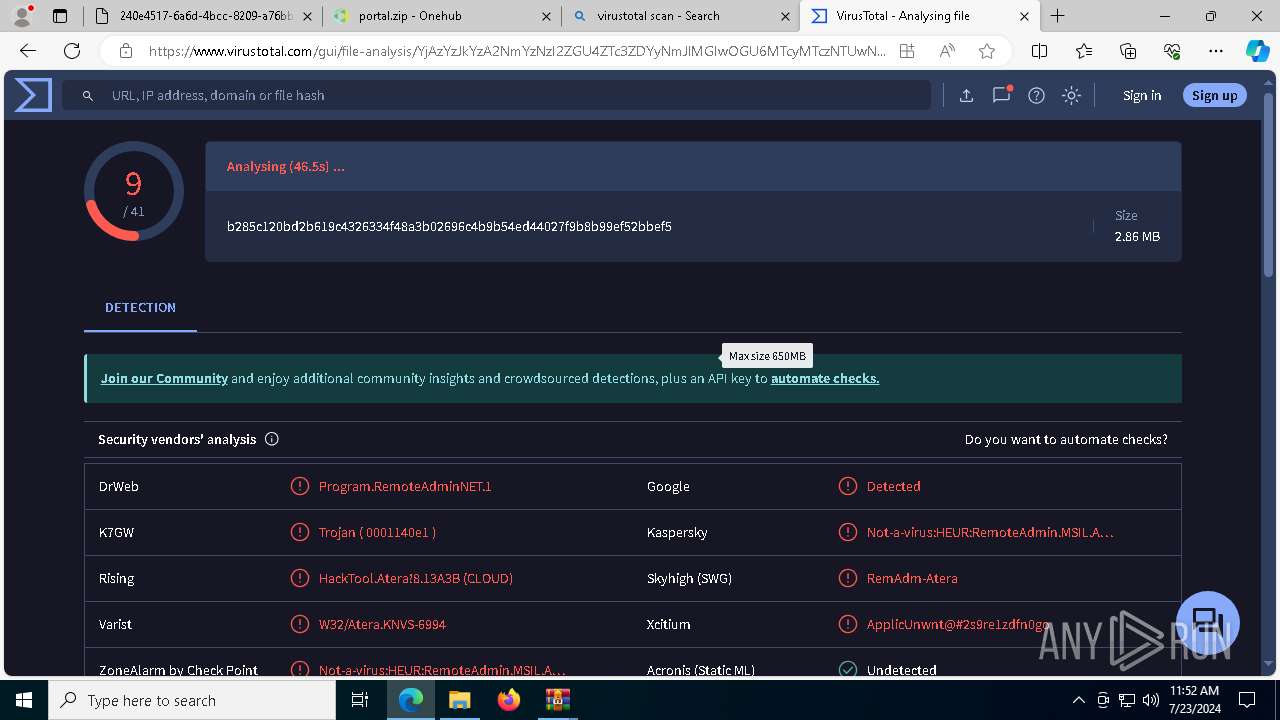
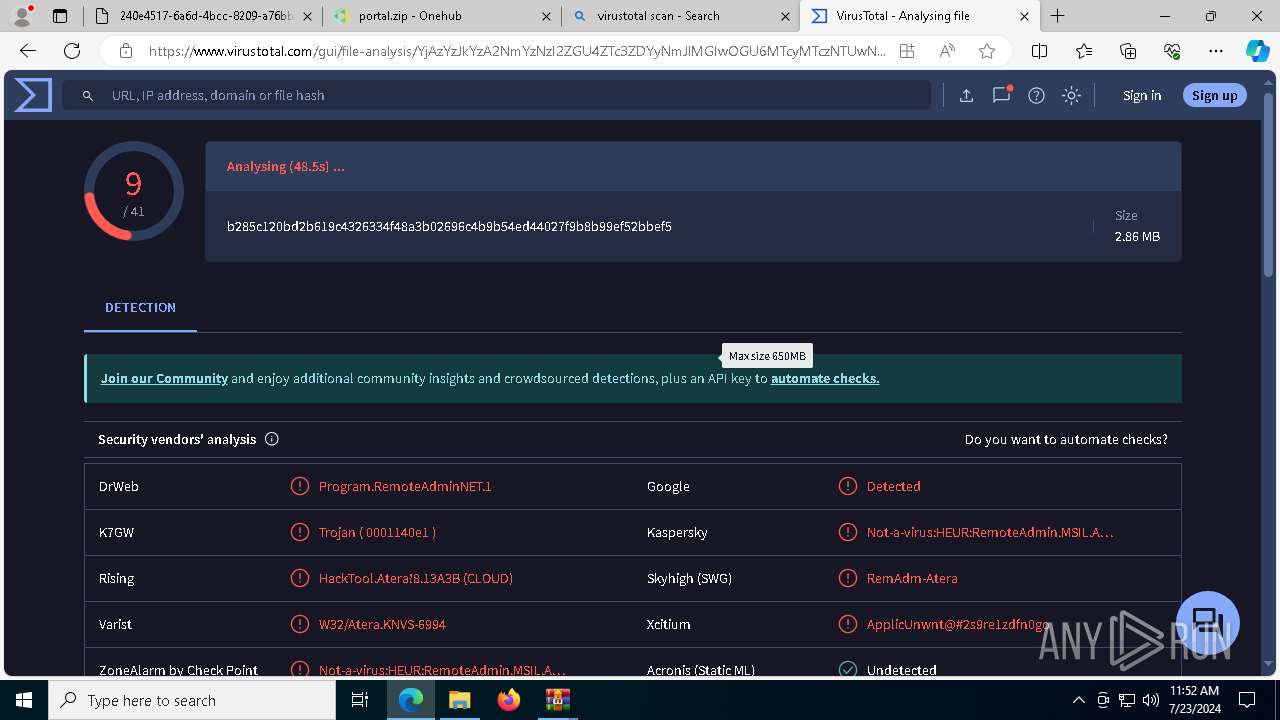
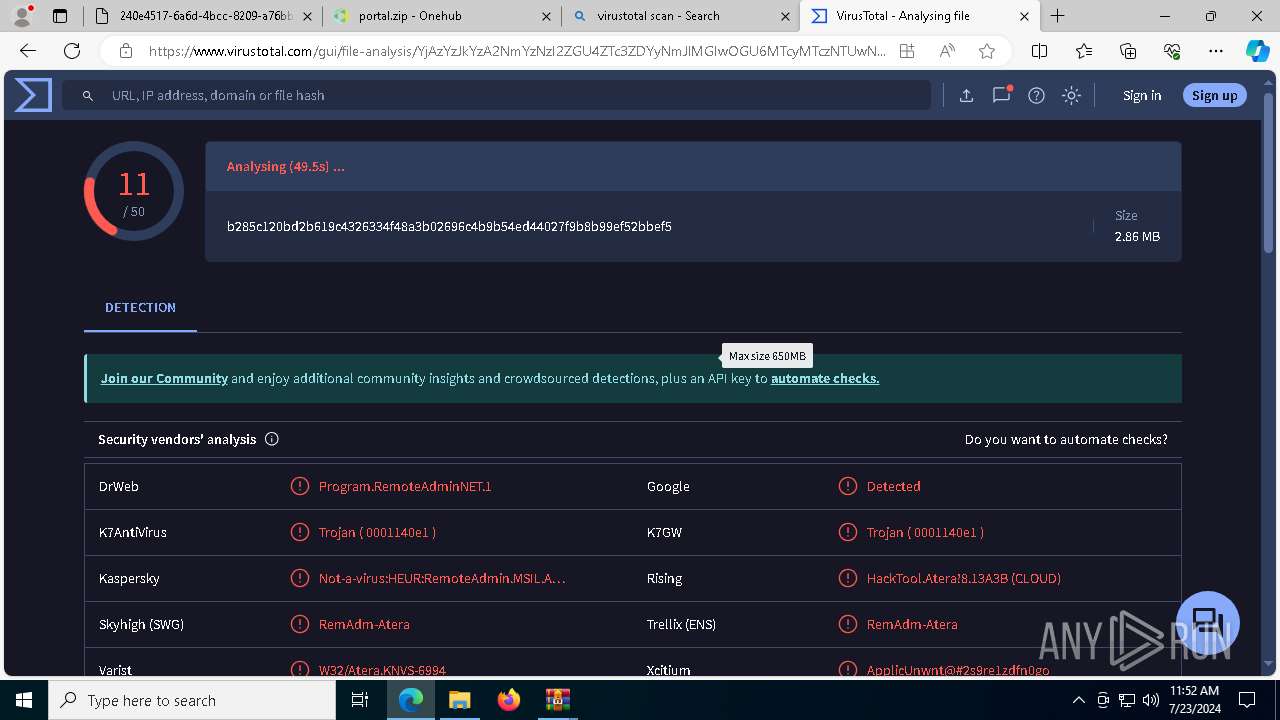
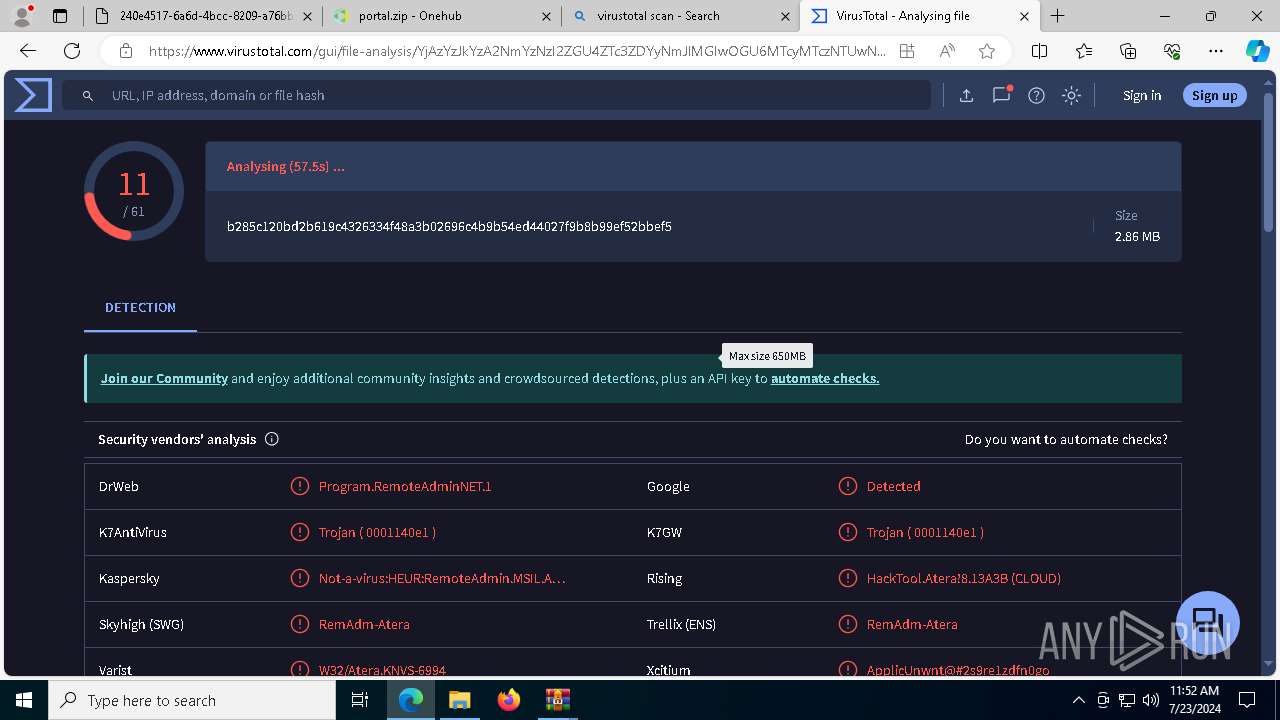
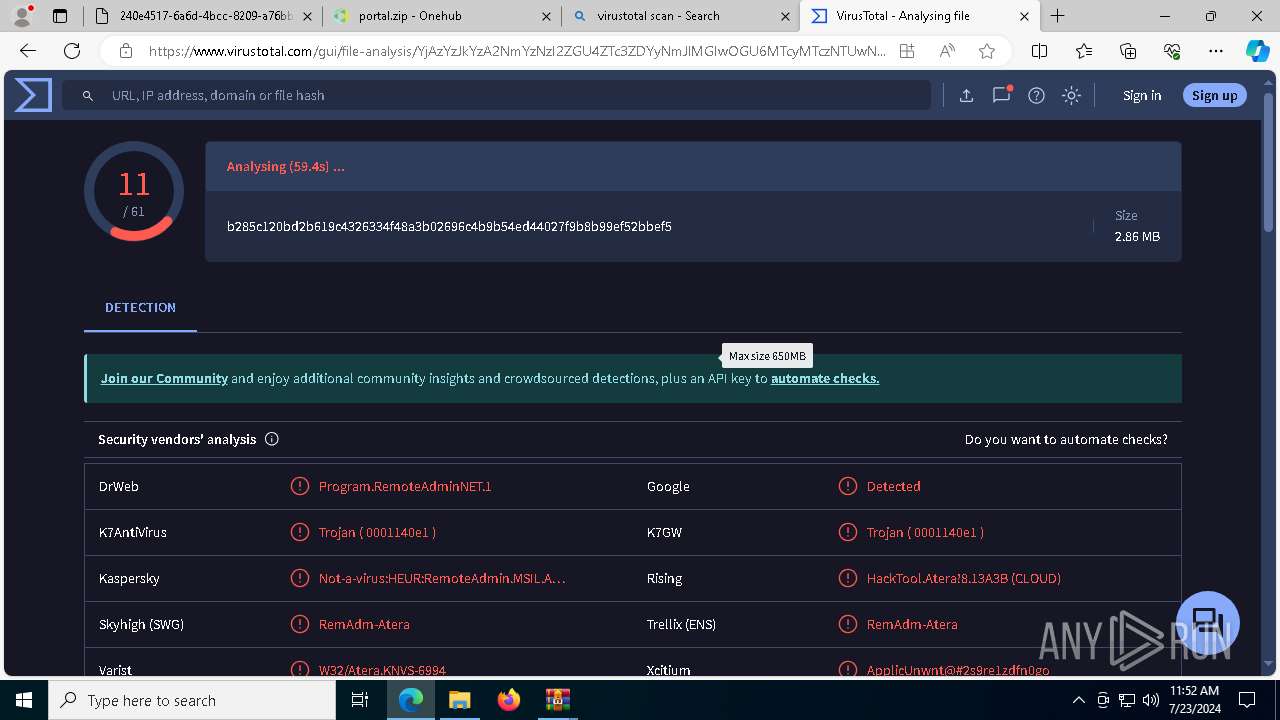
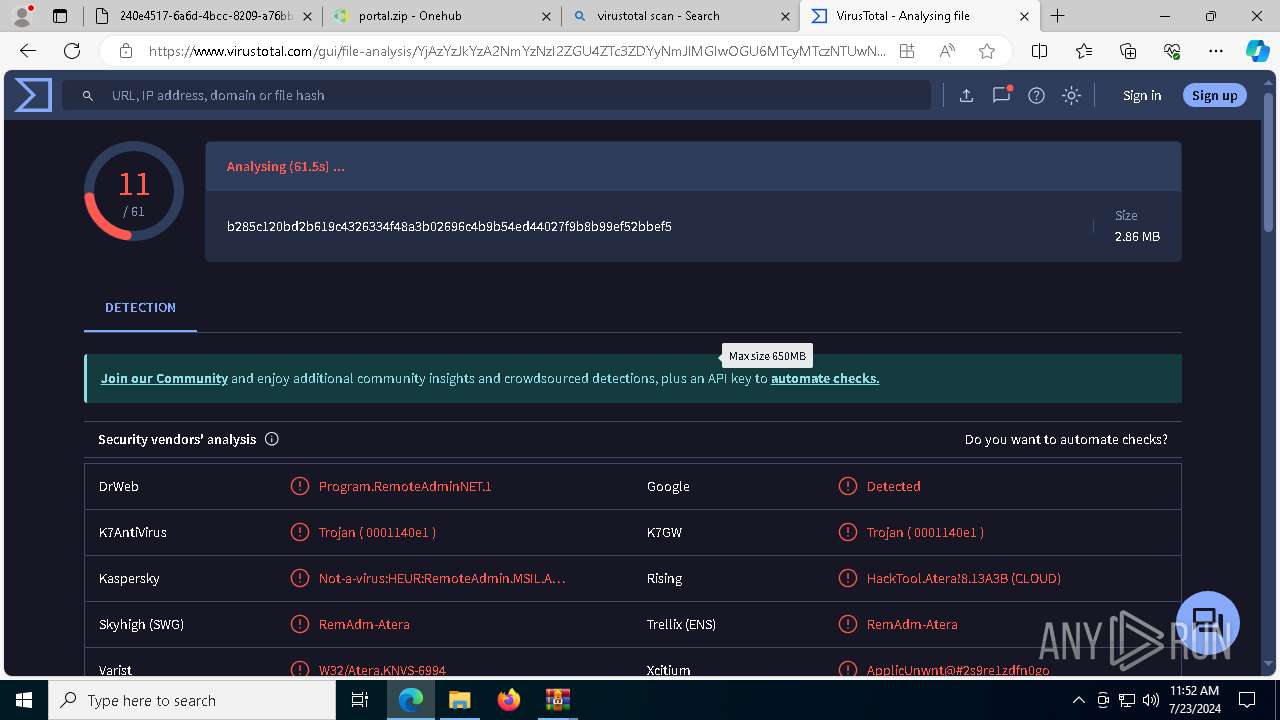
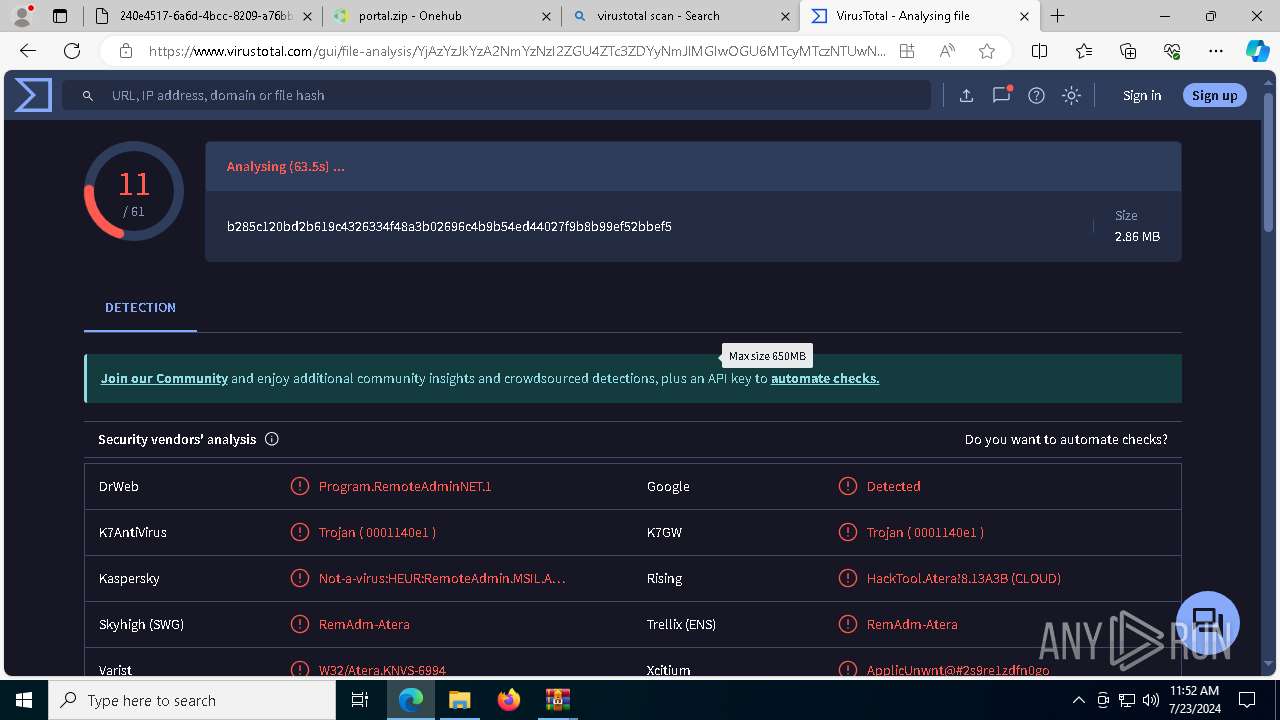
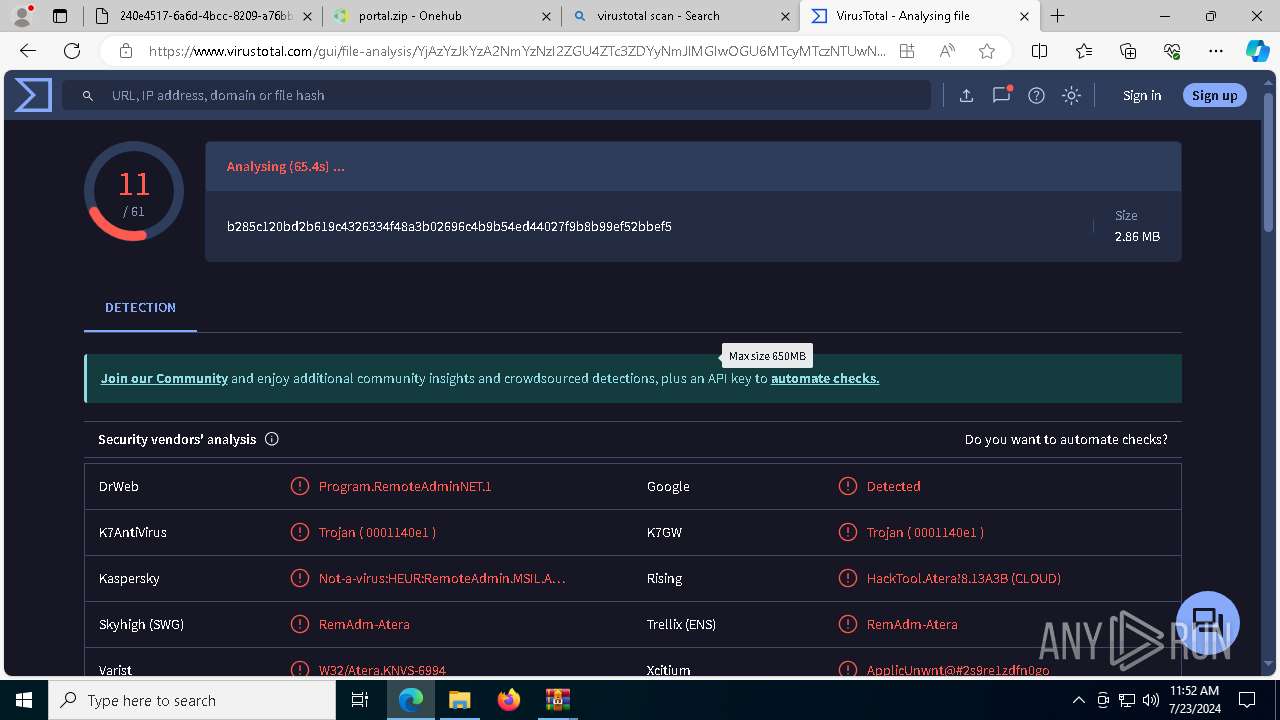
MALICIOUS
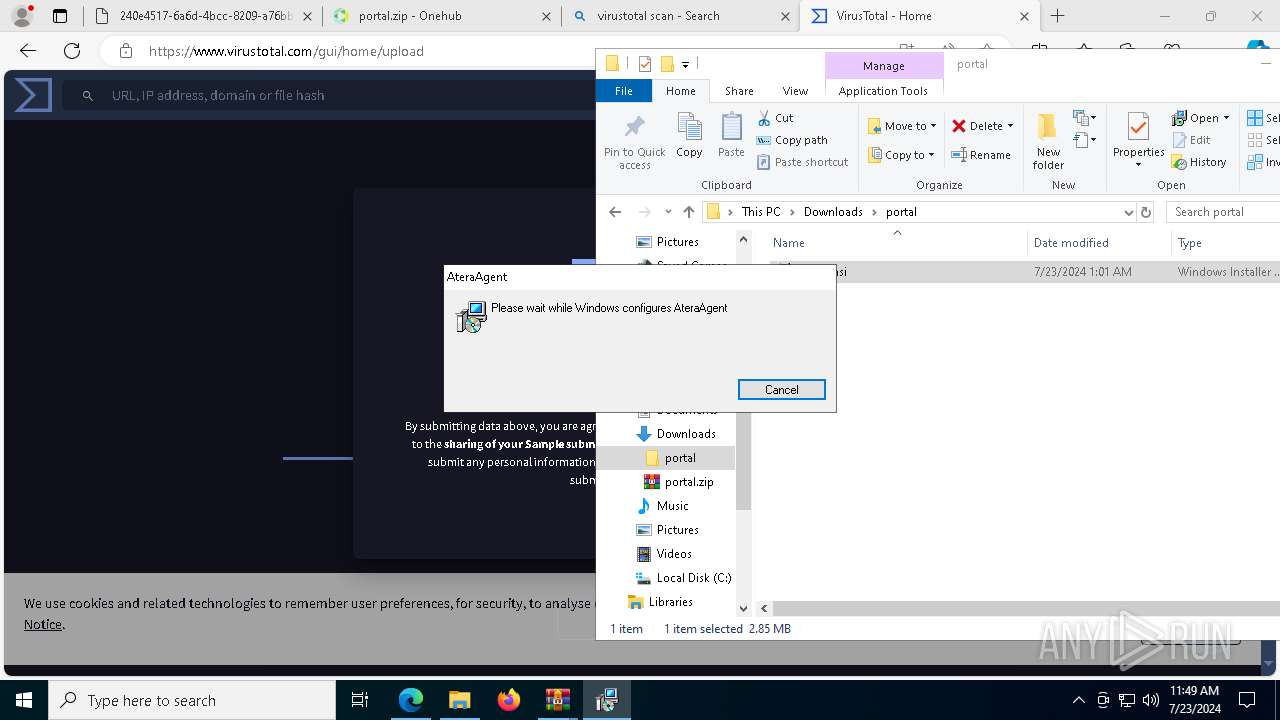
ATERAAGENT has been detected (YARA)
- msiexec.exe (PID: 3800)
- msiexec.exe (PID: 5904)
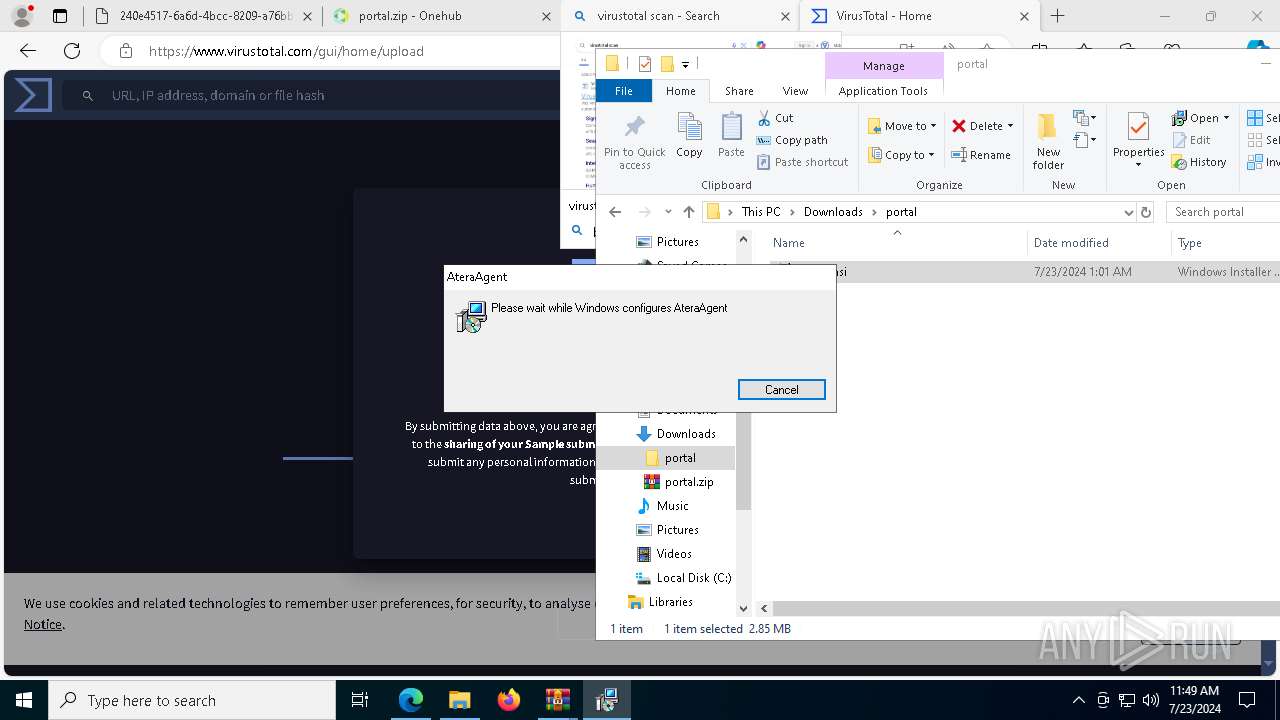
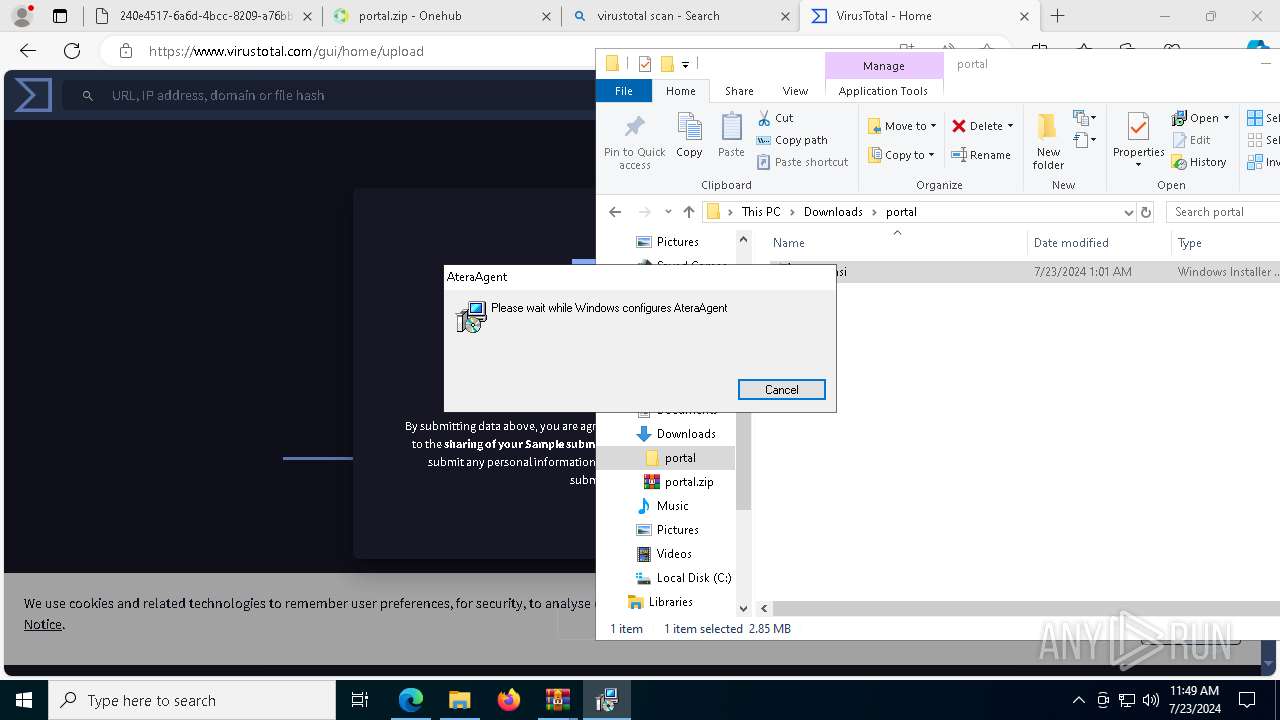
Drops the executable file immediately after the start
- msiexec.exe (PID: 5904)
- AteraAgent.exe (PID: 1956)
Starts NET.EXE for service management
- msiexec.exe (PID: 3068)
- net.exe (PID: 1148)
- net.exe (PID: 2120)
- msiexec.exe (PID: 7156)
SUSPICIOUS
Process drops legitimate windows executable
- msedge.exe (PID: 4328)
- WinRAR.exe (PID: 7248)
- msedge.exe (PID: 5052)
- msiexec.exe (PID: 5904)
- rundll32.exe (PID: 1148)
- rundll32.exe (PID: 8148)
- rundll32.exe (PID: 5928)
- rundll32.exe (PID: 1148)
Checks Windows Trust Settings
- msiexec.exe (PID: 5904)
- AteraAgent.exe (PID: 7628)
- AteraAgent.exe (PID: 5808)
Executes as Windows Service
- VSSVC.exe (PID: 1564)
- AteraAgent.exe (PID: 1956)
- AteraAgent.exe (PID: 7848)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 5904)
Executable content was dropped or overwritten
- rundll32.exe (PID: 1148)
- rundll32.exe (PID: 8148)
- rundll32.exe (PID: 5928)
- rundll32.exe (PID: 1148)
- AteraAgent.exe (PID: 1956)
Uses TASKKILL.EXE to kill process
- msiexec.exe (PID: 3068)
- msiexec.exe (PID: 7156)
Reads security settings of Internet Explorer
- AteraAgent.exe (PID: 7628)
- AteraAgent.exe (PID: 1956)
- AteraAgent.exe (PID: 7848)
- AteraAgent.exe (PID: 5808)
Starts SC.EXE for service management
- AteraAgent.exe (PID: 1956)
- AteraAgent.exe (PID: 7848)
Reads the date of Windows installation
- AteraAgent.exe (PID: 1956)
- AteraAgent.exe (PID: 7848)
Potential Corporate Privacy Violation
- rundll32.exe (PID: 1148)
- AteraAgent.exe (PID: 1956)
- AgentPackageAgentInformation.exe (PID: 7452)
- AgentPackageAgentInformation.exe (PID: 5684)
- AteraAgent.exe (PID: 7848)
- AgentPackageAgentInformation.exe (PID: 8168)
- rundll32.exe (PID: 8148)
- AgentPackageAgentInformation.exe (PID: 3380)
INFO
Reads the computer name
- identity_helper.exe (PID: 7180)
- TextInputHost.exe (PID: 3056)
- msiexec.exe (PID: 5904)
- msiexec.exe (PID: 5748)
- msiexec.exe (PID: 3068)
- AteraAgent.exe (PID: 7628)
- AteraAgent.exe (PID: 1956)
- AgentPackageAgentInformation.exe (PID: 3380)
- AgentPackageAgentInformation.exe (PID: 7452)
- AgentPackageAgentInformation.exe (PID: 5684)
- msiexec.exe (PID: 2864)
- msiexec.exe (PID: 7156)
- AteraAgent.exe (PID: 5808)
- AteraAgent.exe (PID: 7848)
- AgentPackageAgentInformation.exe (PID: 8168)
Reads Microsoft Office registry keys
- msedge.exe (PID: 5052)
The process uses the downloaded file
- msedge.exe (PID: 6112)
- WinRAR.exe (PID: 7248)
- msedge.exe (PID: 5052)
Reads Environment values
- identity_helper.exe (PID: 7180)
- AteraAgent.exe (PID: 1956)
- AgentPackageAgentInformation.exe (PID: 3380)
- AgentPackageAgentInformation.exe (PID: 7452)
- AgentPackageAgentInformation.exe (PID: 5684)
- AteraAgent.exe (PID: 5808)
- AteraAgent.exe (PID: 7628)
- AteraAgent.exe (PID: 7848)
- AgentPackageAgentInformation.exe (PID: 8168)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 7248)
- msedge.exe (PID: 5052)
- msedge.exe (PID: 4328)
- rundll32.exe (PID: 1148)
- rundll32.exe (PID: 8148)
- rundll32.exe (PID: 5928)
- rundll32.exe (PID: 1148)
Application launched itself
- msedge.exe (PID: 5052)
Checks supported languages
- TextInputHost.exe (PID: 3056)
- msiexec.exe (PID: 5904)
- msiexec.exe (PID: 5748)
- identity_helper.exe (PID: 7180)
- msiexec.exe (PID: 3068)
- AteraAgent.exe (PID: 7628)
- AteraAgent.exe (PID: 1956)
- AgentPackageAgentInformation.exe (PID: 7452)
- AgentPackageAgentInformation.exe (PID: 3380)
- AgentPackageAgentInformation.exe (PID: 5684)
- msiexec.exe (PID: 7156)
- msiexec.exe (PID: 2864)
- AteraAgent.exe (PID: 5808)
- AteraAgent.exe (PID: 7848)
- AgentPackageAgentInformation.exe (PID: 8168)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 3800)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7248)
- msiexec.exe (PID: 5904)
Checks proxy server information
- slui.exe (PID: 8052)
- msiexec.exe (PID: 3800)
- rundll32.exe (PID: 8148)
- rundll32.exe (PID: 1148)
Manual execution by a user
- msiexec.exe (PID: 3800)
- msiexec.exe (PID: 6672)
Reads the software policy settings
- slui.exe (PID: 8052)
- msiexec.exe (PID: 5904)
- rundll32.exe (PID: 8148)
- AteraAgent.exe (PID: 7628)
- AteraAgent.exe (PID: 1956)
- rundll32.exe (PID: 1148)
- msiexec.exe (PID: 3800)
- AgentPackageAgentInformation.exe (PID: 7452)
- AgentPackageAgentInformation.exe (PID: 3380)
- AgentPackageAgentInformation.exe (PID: 5684)
- AteraAgent.exe (PID: 5808)
- AteraAgent.exe (PID: 7848)
- AgentPackageAgentInformation.exe (PID: 8168)
Reads the machine GUID from the registry
- msiexec.exe (PID: 5904)
- AteraAgent.exe (PID: 7628)
- AteraAgent.exe (PID: 1956)
- AgentPackageAgentInformation.exe (PID: 3380)
- AgentPackageAgentInformation.exe (PID: 7452)
- AgentPackageAgentInformation.exe (PID: 5684)
- AteraAgent.exe (PID: 5808)
- AteraAgent.exe (PID: 7848)
- AgentPackageAgentInformation.exe (PID: 8168)
Create files in a temporary directory
- rundll32.exe (PID: 1148)
- rundll32.exe (PID: 8148)
- rundll32.exe (PID: 5928)
- rundll32.exe (PID: 1148)
Disables trace logs
- rundll32.exe (PID: 8148)
- rundll32.exe (PID: 1148)
- AteraAgent.exe (PID: 1956)
- AgentPackageAgentInformation.exe (PID: 3380)
- AgentPackageAgentInformation.exe (PID: 7452)
- AgentPackageAgentInformation.exe (PID: 5684)
- AteraAgent.exe (PID: 7848)
- AgentPackageAgentInformation.exe (PID: 8168)
Creates a software uninstall entry
- msiexec.exe (PID: 5904)
Creates files in the program directory
- AteraAgent.exe (PID: 7628)
- AteraAgent.exe (PID: 1956)
Creates files or folders in the user directory
- msiexec.exe (PID: 3800)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .htm/html | | | HyperText Markup Language with DOCTYPE (80.6) |
|---|---|---|
| .html | | | HyperText Markup Language (19.3) |
EXIF
HTML
| ContentType: | text/html; charset=utf-8 |
|---|---|
| Title: | 240e4517-6a6d-4bcc-8209-a76bb55f78db |
| Author: | Philip Rowell |
Total processes
250
Monitored processes
102
Malicious processes
4
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 204 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=39 --mojo-platform-channel-handle=7828 --field-trial-handle=2336,i,1926823333321066362,16573315184114593770,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1148 | rundll32.exe "C:\WINDOWS\Installer\MSI9699.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1021750 2 AlphaControlAgentInstallation!AlphaControlAgentInstallation.CustomActions.GenerateAgentId | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1148 | "NET" STOP AteraAgent | C:\Windows\SysWOW64\net.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1148 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=9116 --field-trial-handle=2336,i,1926823333321066362,16573315184114593770,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1148 | rundll32.exe "C:\WINDOWS\Installer\MSIB544.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1029484 32 AlphaControlAgentInstallation!AlphaControlAgentInstallation.CustomActions.ReportMsiEnd | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1552 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=26 --mojo-platform-channel-handle=6860 --field-trial-handle=2336,i,1926823333321066362,16573315184114593770,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1564 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1956 | "C:\Program Files (x86)\ATERA Networks\AteraAgent\AteraAgent.exe" | C:\Program Files (x86)\ATERA Networks\AteraAgent\AteraAgent.exe | services.exe | ||||||||||||
User: SYSTEM Company: ATERA Networks Ltd. Integrity Level: SYSTEM Description: AteraAgent Exit code: 1 Version: 1.8.7.2 Modules
| |||||||||||||||
| 1996 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | net.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2100 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5148 --field-trial-handle=2336,i,1926823333321066362,16573315184114593770,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
73 810
Read events
73 168
Write events
600
Delete events
42
Modification events
| (PID) Process: | (5052) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5052) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5052) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (5052) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (5052) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5052) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (5052) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (5052) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
| (PID) Process: | (5052) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (5052) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | urlstats |
Value: 0 | |||
Executable files
59
Suspicious files
675
Text files
203
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5052 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RFe0ccd.TMP | — | |
MD5:— | SHA256:— | |||
| 5052 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RFe0ccd.TMP | — | |
MD5:— | SHA256:— | |||
| 5052 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RFe0ccd.TMP | — | |
MD5:— | SHA256:— | |||
| 5052 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5052 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5052 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5052 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RFe0ccd.TMP | — | |
MD5:— | SHA256:— | |||
| 5052 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5052 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RFe0ccd.TMP | — | |
MD5:— | SHA256:— | |||
| 5052 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
32
TCP/UDP connections
203
DNS requests
196
Threats
22
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 2.16.241.13:80 | http://apps.identrust.com/roots/dstrootcax3.p7c | unknown | — | — | whitelisted |
880 | svchost.exe | GET | 206 | 23.50.131.72:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/6e6d05a2-47e8-42b8-85a0-e8b7ee48333a?P1=1722298066&P2=404&P3=2&P4=e4Zrj5zsbJ4c%2b2hjaK2QZU4t5UFXo5sO%2bpUHDQtqbZfqRtHlRGXhkd0HNN6zUOf7b1SnKh4BnF1chZiiFK6HIw%3d%3d | unknown | — | — | whitelisted |
4328 | msedge.exe | GET | 304 | 2.23.197.184:80 | http://r3.i.lencr.org/ | unknown | — | — | whitelisted |
880 | svchost.exe | HEAD | 200 | 23.50.131.72:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/6e6d05a2-47e8-42b8-85a0-e8b7ee48333a?P1=1722298066&P2=404&P3=2&P4=e4Zrj5zsbJ4c%2b2hjaK2QZU4t5UFXo5sO%2bpUHDQtqbZfqRtHlRGXhkd0HNN6zUOf7b1SnKh4BnF1chZiiFK6HIw%3d%3d | unknown | — | — | whitelisted |
880 | svchost.exe | GET | 206 | 23.50.131.72:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/6e6d05a2-47e8-42b8-85a0-e8b7ee48333a?P1=1722298066&P2=404&P3=2&P4=e4Zrj5zsbJ4c%2b2hjaK2QZU4t5UFXo5sO%2bpUHDQtqbZfqRtHlRGXhkd0HNN6zUOf7b1SnKh4BnF1chZiiFK6HIw%3d%3d | unknown | — | — | whitelisted |
3800 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
880 | svchost.exe | GET | 206 | 23.50.131.72:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/6e6d05a2-47e8-42b8-85a0-e8b7ee48333a?P1=1722298066&P2=404&P3=2&P4=e4Zrj5zsbJ4c%2b2hjaK2QZU4t5UFXo5sO%2bpUHDQtqbZfqRtHlRGXhkd0HNN6zUOf7b1SnKh4BnF1chZiiFK6HIw%3d%3d | unknown | — | — | whitelisted |
880 | svchost.exe | GET | 206 | 23.50.131.72:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/07b2b28d-48a0-4636-b791-6e6129c8a3da?P1=1722298065&P2=404&P3=2&P4=TPjiMKqZGlZpL90gciS%2bP7JTH%2bNWqmUXyJtfJMq8IKhdwH5OW68P%2bqaXDhbj1OS7uWLUtUoiN3wUYLBX4fBM2w%3d%3d | unknown | — | — | whitelisted |
880 | svchost.exe | HEAD | 200 | 23.50.131.72:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/07b2b28d-48a0-4636-b791-6e6129c8a3da?P1=1722298065&P2=404&P3=2&P4=TPjiMKqZGlZpL90gciS%2bP7JTH%2bNWqmUXyJtfJMq8IKhdwH5OW68P%2bqaXDhbj1OS7uWLUtUoiN3wUYLBX4fBM2w%3d%3d | unknown | — | — | whitelisted |
880 | svchost.exe | GET | 206 | 23.50.131.72:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/07b2b28d-48a0-4636-b791-6e6129c8a3da?P1=1722298065&P2=404&P3=2&P4=TPjiMKqZGlZpL90gciS%2bP7JTH%2bNWqmUXyJtfJMq8IKhdwH5OW68P%2bqaXDhbj1OS7uWLUtUoiN3wUYLBX4fBM2w%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4548 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6012 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4220 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 184.86.251.11:443 | www.bing.com | Akamai International B.V. | DE | unknown |
4204 | svchost.exe | 4.209.32.67:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
5052 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4328 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4328 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
edgeservices.bing.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4328 | msedge.exe | Misc activity | ET INFO File Sharing Service Related Domain in DNS Lookup (ws .onehub .com) |
4328 | msedge.exe | Misc activity | ET INFO Observed File Sharing Service Related Domain (ws .onehub .com in TLS SNI) |
4328 | msedge.exe | Misc activity | ET INFO File Sharing Service Related Domain in DNS Lookup (ws .onehub .com) |
4328 | msedge.exe | Misc activity | ET INFO Observed File Sharing Service Related Domain (ws .onehub .com in TLS SNI) |
4328 | msedge.exe | Misc activity | ET INFO Observed File Sharing Service Related Domain (ws .onehub .com in TLS SNI) |
4328 | msedge.exe | Misc activity | ET INFO Observed File Sharing Service Related Domain (ws .onehub .com in TLS SNI) |
4328 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
4328 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
14 ETPRO signatures available at the full report