| File name: | _igetintopc.com_Maxon_App_2.1.0.exe |
| Full analysis: | https://app.any.run/tasks/3123b7a5-a365-409a-94ed-d8989d47672b |
| Verdict: | Malicious activity |
| Analysis date: | October 08, 2024, 07:12:21 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 7569769DBF6FE05C8D9527B042E7DA34 |
| SHA1: | 7D9FCD030E47DF7BFFBBFAEEA5316C389E2B3354 |
| SHA256: | C43FB86178186A2F9EE0ADB7F8860DC2718A21DE3E133923E3B96DA574A98823 |
| SSDEEP: | 393216:5f8frSEyy2uxJ5AkMGHJkwmQH0+UtDmoHkH6:5f8DSEyy2wT3BmgUtSoHka |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- _igetintopc.com_Maxon_App_2.1.0.exe (PID: 1884)
- MicrosoftEdgeWebview2Setup.exe (PID: 6928)
- MicrosoftEdgeUpdateSetup.exe (PID: 3836)
- MicrosoftEdgeUpdate.exe (PID: 1988)
- vcredist_x64.12.exe (PID: 5532)
- VC_redist.x64.19.exe (PID: 6364)
The process drops C-runtime libraries
- _igetintopc.com_Maxon_App_2.1.0.exe (PID: 1884)
Reads security settings of Internet Explorer
- _igetintopc.com_Maxon_App_2.1.0.exe (PID: 1884)
Executable content was dropped or overwritten
- _igetintopc.com_Maxon_App_2.1.0.exe (PID: 1884)
- MicrosoftEdgeWebview2Setup.exe (PID: 6928)
- MicrosoftEdgeUpdateSetup.exe (PID: 3836)
- vcredist_x64.12.exe (PID: 5532)
- VC_redist.x64.19.exe (PID: 6364)
- VC_redist.x64.19.exe (PID: 4892)
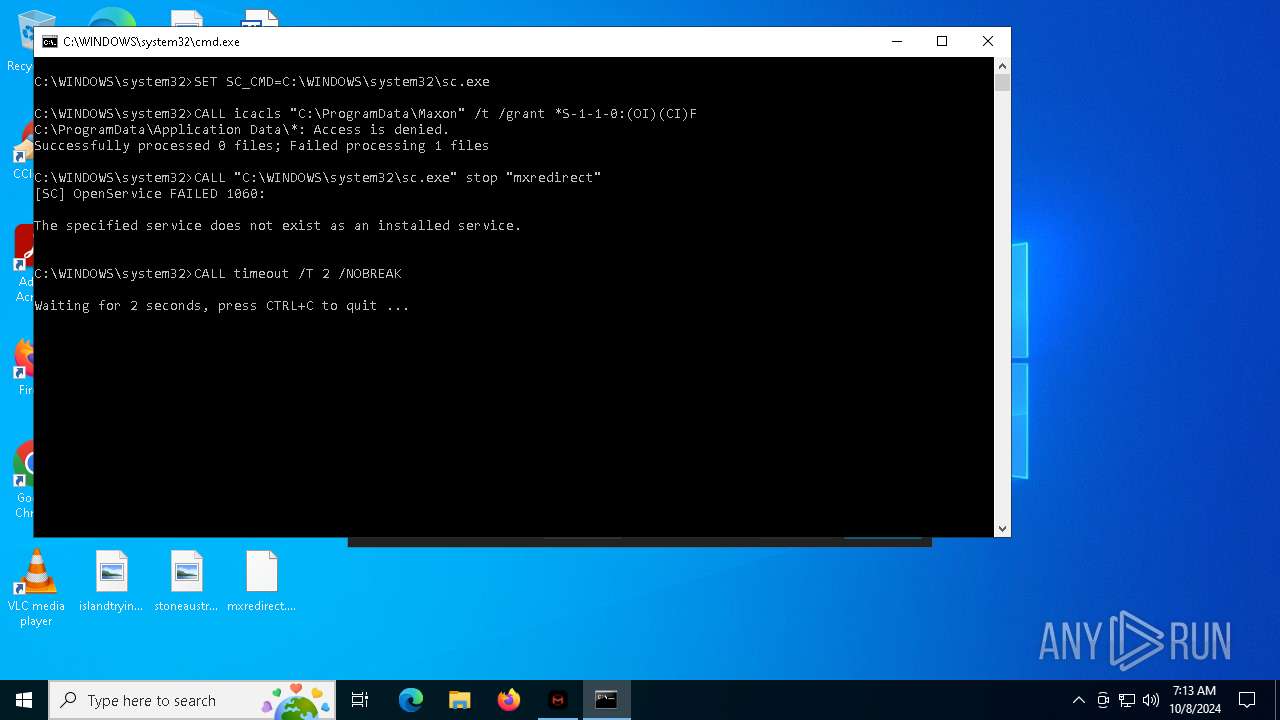
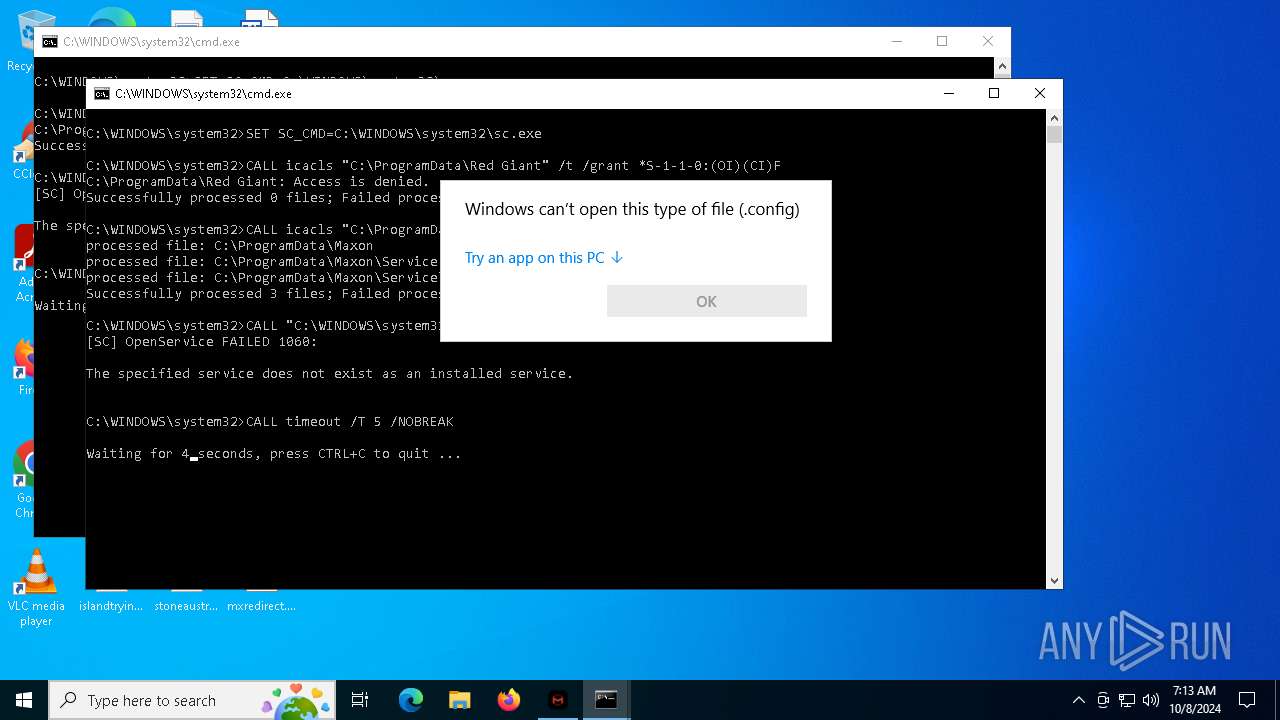
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 2324)
- cmd.exe (PID: 5136)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2324)
- cmd.exe (PID: 3508)
- cmd.exe (PID: 5136)
- cmd.exe (PID: 7132)
Starts SC.EXE for service management
- cmd.exe (PID: 2324)
- cmd.exe (PID: 5136)
Starts NET.EXE to display or manage information about active sessions
- cmd.exe (PID: 3508)
- net.exe (PID: 2264)
- cmd.exe (PID: 7132)
- net.exe (PID: 5300)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 5276)
Starts a Microsoft application from unusual location
- MicrosoftEdgeWebview2Setup.exe (PID: 6928)
- MicrosoftEdgeUpdate.exe (PID: 2824)
- MicrosoftEdgeUpdateSetup.exe (PID: 3836)
- MicrosoftEdgeUpdate.exe (PID: 1988)
- vcredist_x64.12.exe (PID: 5532)
- VC_redist.x64.19.exe (PID: 6364)
- VC_redist.x64.19.exe (PID: 4892)
INFO
Checks supported languages
- _igetintopc.com_Maxon_App_2.1.0.exe (PID: 1884)
- Maxon App Installer.exe (PID: 6172)
- mxredirect.exe (PID: 6460)
- rguninstaller.exe (PID: 1220)
Reads the computer name
- _igetintopc.com_Maxon_App_2.1.0.exe (PID: 1884)
- Maxon App Installer.exe (PID: 6172)
- mxredirect.exe (PID: 6460)
Create files in a temporary directory
- _igetintopc.com_Maxon_App_2.1.0.exe (PID: 1884)
- Maxon App Installer.exe (PID: 6172)
The process uses the downloaded file
- _igetintopc.com_Maxon_App_2.1.0.exe (PID: 1884)
Process checks computer location settings
- _igetintopc.com_Maxon_App_2.1.0.exe (PID: 1884)
Creates files in the program directory
- Maxon App Installer.exe (PID: 6172)
- mxredirect.exe (PID: 6460)
Manual execution by a user
- rguninstaller.exe (PID: 1696)
- mxredirect.exe (PID: 6460)
- OpenWith.exe (PID: 1984)
- cmd.exe (PID: 5136)
- cmd.exe (PID: 3508)
- SerialFiller.exe (PID: 3272)
- cmd.exe (PID: 5276)
- MxNotify.exe (PID: 5056)
- cmd.exe (PID: 7032)
- MicrosoftEdgeWebview2Setup.exe (PID: 6928)
- OpenWith.exe (PID: 5996)
- cmd.exe (PID: 7132)
- rgdeploy.exe (PID: 2868)
- rga-uninstaller-helper.exe (PID: 2264)
- rga-uninstaller-helper.exe (PID: 6764)
- notepad.exe (PID: 4120)
- rguninstaller.exe (PID: 1220)
- vcredist_x64.12.exe (PID: 5532)
- cmd.exe (PID: 3852)
- VC_redist.x64.19.exe (PID: 6364)
- cmd.exe (PID: 2324)
- notepad.exe (PID: 6044)
- cmd.exe (PID: 6336)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 1984)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:05:06 07:00:00+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 105472 |
| InitializedDataSize: | 96768 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x19502 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Maxon Application Installer |
| FileDescription: | Maxon Self-Extracting Installer |
| FileVersion: | 1.0.0.0 |
| InternalName: | - |
| LegalCopyright: | Copyright (c) 2021 Maxon Computer GmbH |
| OriginalFileName: | - |
| ProductName: | Maxon Installer |
| ProductVersion: | 1.0.0.0 |
Total processes
194
Monitored processes
77
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 400 | timeout /T 5 /NOBREAK | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 796 | timeout /T 5 /NOBREAK | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 884 | timeout /T 2 /NOBREAK | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1076 | "C:\WINDOWS\system32\sc.exe" delete "mxredirect" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1080 | timeout /T 2 /NOBREAK | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1220 | "C:\Users\admin\Desktop\rguninstaller.exe" | C:\Users\admin\Desktop\rguninstaller.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 4294967295 Modules
| |||||||||||||||
| 1232 | timeout /T 10 /NOBREAK | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1344 | "C:\WINDOWS\system32\sc.exe" create "Red Giant Service" binpath= "C:\Program Files\Red Giant\Services\Red Giant Service.exe" start= auto obj= "NT AUTHORITY\Localservice" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Service Control Manager Configuration Tool Exit code: 5 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1696 | "C:\Users\admin\Desktop\rguninstaller.exe" | C:\Users\admin\Desktop\rguninstaller.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1884 | "C:\Users\admin\Desktop\_igetintopc.com_Maxon_App_2.1.0.exe" | C:\Users\admin\Desktop\_igetintopc.com_Maxon_App_2.1.0.exe | explorer.exe | ||||||||||||
User: admin Company: Maxon Application Installer Integrity Level: HIGH Description: Maxon Self-Extracting Installer Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
18 222
Read events
18 196
Write events
25
Delete events
1
Modification events
| (PID) Process: | (6696) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (6696) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 040000000E00000010000000030000000F000000000000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (6696) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 040000000000000005000000020000000100000003000000FFFFFFFF | |||
| (PID) Process: | (6696) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Toolbar |
| Operation: | write | Name: | Locked |
Value: 1 | |||
| (PID) Process: | (6696) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Ribbon |
| Operation: | write | Name: | MinimizedStateTabletModeOff |
Value: 0 | |||
| (PID) Process: | (6696) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Ribbon |
| Operation: | write | Name: | QatItems |
Value: 3C7369713A637573746F6D554920786D6C6E733A7369713D22687474703A2F2F736368656D61732E6D6963726F736F66742E636F6D2F77696E646F77732F323030392F726962626F6E2F716174223E3C7369713A726962626F6E206D696E696D697A65643D2266616C7365223E3C7369713A71617420706F736974696F6E3D2230223E3C7369713A736861726564436F6E74726F6C733E3C7369713A636F6E74726F6C206964513D227369713A3136313238222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3136313239222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333532222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333834222076697369626C653D22747275652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333336222076697369626C653D22747275652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333537222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C2F7369713A736861726564436F6E74726F6C733E3C2F7369713A7161743E3C2F7369713A726962626F6E3E3C2F7369713A637573746F6D55493E | |||
| (PID) Process: | (6696) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Toolbar\ShellBrowser |
| Operation: | write | Name: | ITBar7Layout |
Value: 13000000000000000000000020000000100000000000000001000000010700005E01000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6696) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Documents | |||
| (PID) Process: | (6696) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 95 | |||
| (PID) Process: | (1988) MicrosoftEdgeUpdate.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MicrosoftEdgeUpdate.exe |
| Operation: | write | Name: | DisableExceptionChainValidation |
Value: 0 | |||
Executable files
305
Suspicious files
18
Text files
41
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1884 | _igetintopc.com_Maxon_App_2.1.0.exe | C:\Users\admin\AppData\Local\Temp\7zSC57C798F\packages\com.redgiant.app.zip | compressed | |
MD5:67B17FF6F6FAF4D93819F372C1D05B58 | SHA256:2B9E276E7621EDE47C7E157256CEEB0EA81355D80D8ED6DE81096B5F1E53F8F3 | |||
| 1884 | _igetintopc.com_Maxon_App_2.1.0.exe | C:\Users\admin\AppData\Local\Temp\7zSC57C798F\packages\com.redgiant.rguninstaller.zip | compressed | |
MD5:481BA55C1A79AAF08E2DDA2884BB8E25 | SHA256:86260CC408852BBEF163B8B0C518060969FB607A76BD7E15F44EDDAC354FDB18 | |||
| 1884 | _igetintopc.com_Maxon_App_2.1.0.exe | C:\Users\admin\AppData\Local\Temp\7zSC57C798F\packages\com.redgiant.vcredist-x64-2019.zip | compressed | |
MD5:66710D9E8D1DD5DCF3672EDC8B18CA68 | SHA256:F40F8E805895D38DA4C707A9B54C4C958EA1305828A8653DD0B58FECBC899528 | |||
| 1884 | _igetintopc.com_Maxon_App_2.1.0.exe | C:\Users\admin\AppData\Local\Temp\7zSC57C798F\packages\net.maxon.app.json | binary | |
MD5:C8ECE23E4E6C5BD44DA3FF7F64B5BD04 | SHA256:7D41506A405D39B2598CCCA53BD15885CE76CD41C28D6C27BDC1E624708C9B44 | |||
| 1884 | _igetintopc.com_Maxon_App_2.1.0.exe | C:\Users\admin\AppData\Local\Temp\7zSC57C798F\packages\com.redgiant.vcredist-x64-2012.zip | compressed | |
MD5:99E84FD3559704727402D65D44EB973E | SHA256:6872A9BF479348F0BC6CF71178EAD86B4E47168896647722FA8249F4FE258A68 | |||
| 1884 | _igetintopc.com_Maxon_App_2.1.0.exe | C:\Users\admin\AppData\Local\Temp\7zSC57C798F\Maxon App Installer.exe | executable | |
MD5:4A86E1306E466C496D70D219B0EF2844 | SHA256:A9F78158D5B680C317FE53FD755EB89F52B2872B527C2BFFA162966168D906D4 | |||
| 1884 | _igetintopc.com_Maxon_App_2.1.0.exe | C:\Users\admin\AppData\Local\Temp\7zSC57C798F\packages\net.maxon.mxredirect.zip | compressed | |
MD5:274D2EAFAF7B139B1200EEFEB0BD4768 | SHA256:DC82C568CE69BC2DE08DFFD448779B099E3E276F898E46C136682A0C125E8336 | |||
| 5056 | MxNotify.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Maxon App\Maxon Notifications.lnk | binary | |
MD5:83E7785D0EE9449C5BE8B24BA11FDB3F | SHA256:5EA6948445768FF7E06D9AAD39AFEEA74684013DC1826D37C9C258AA3ADA8A3A | |||
| 1884 | _igetintopc.com_Maxon_App_2.1.0.exe | C:\Users\admin\AppData\Local\Temp\7zSC57C798F\packages\net.maxon.mxnotify.zip | compressed | |
MD5:CA8F737DA3A5541048CB735FC593455B | SHA256:2D5E6B28BB20469CD18E05B49C532C641A9CDE91E616F7100DEE3FA07343FDDF | |||
| 5056 | MxNotify.exe | C:\Users\admin\AppData\Local\Maxon\Services\notifications.cfg | binary | |
MD5:4780378DB80D8B807D8885F360E1E32D | SHA256:385CCCAA99B5140AF4C71B75929B5C90058EE14B3E8F6BF8306F33B1B9105B10 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
24
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4744 | svchost.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 304 | 13.107.42.16:443 | https://config.edge.skype.com/config/v1/EdgeUpdate/1.3.145.49?clientId=s:BAD99146-31D3-4EC6-A1A4-BE76F32BA5D4&appChannel_edgeupdate=6&appConsentState_edgeupdate=0&appDayOfInstall_edgeupdate=0&appInstallTimeDiffSec_edgeupdate=0&appLastLaunchTime_edgeupdate=0&appVersion_edgeupdate=1.3.145.49&appUpdateCheckIsUpdateDisabled_edgeupdate=false&hwDiskType=2&hwHasSsse3=true&hwLogicalCpus=4&hwPhysmemory=4&isMsftDomainJoined=false&oemProductManufacturer=DELL&oemProductName=DELL&osArch=x64&osPlatform=win&osVersion=10.0.19045.4046&requestCheckPeriodSec=-1&requestDomainJoined=false&requestInstallSource=taggedmi&requestIsMachine=true&requestOmahaShellVersion=1.3.147.37&requestOmahaVersion=1.3.145.49 | unknown | — | — | unknown |
— | — | POST | 200 | 20.42.73.30:443 | https://browser.pipe.aria.microsoft.com/Collector/3.0/?qsp=true&content-type=application%2Fbond-compact-binary&client-id=NO_AUTH&sdk-version=AWT-Web-CJS-1.2.0&x-apikey=33d70a864599496b982a39f036f71122-2064703e-3a9d-4d90-8362-eec08dffe8e8-7176 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4744 | svchost.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5336 | SearchApp.exe | 20.42.73.30:443 | browser.pipe.aria.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1988 | MicrosoftEdgeUpdate.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |