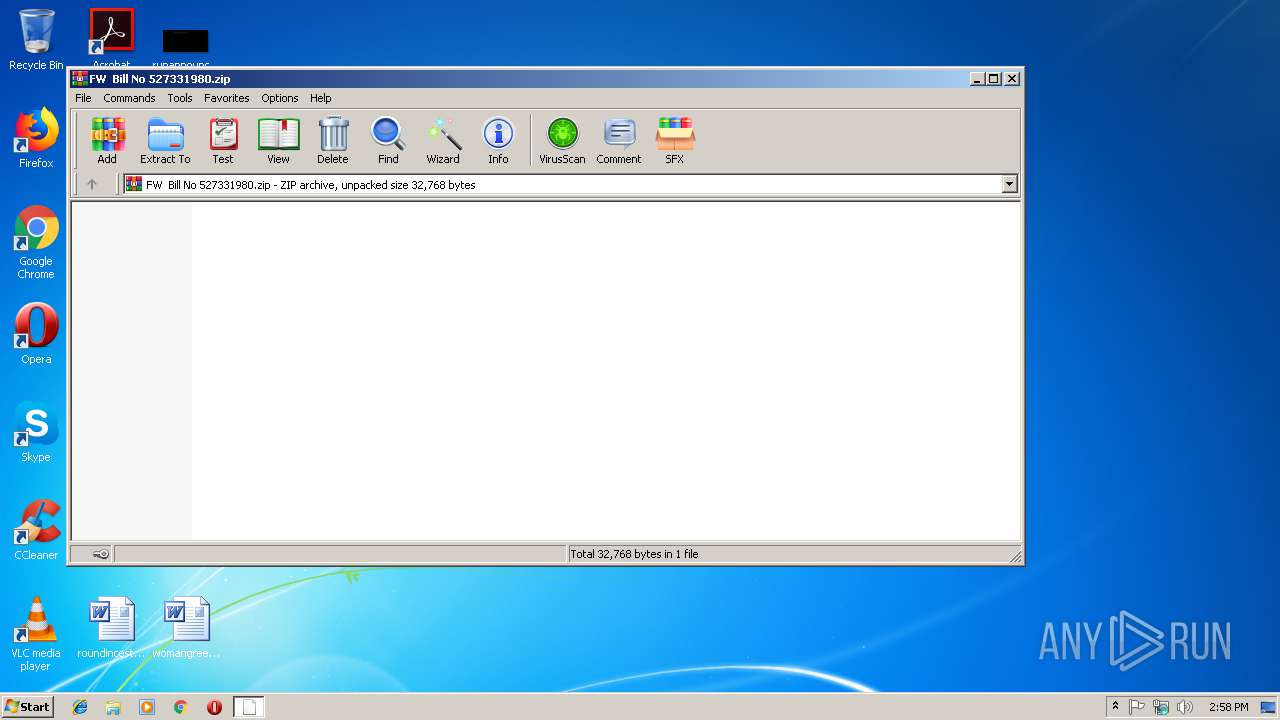
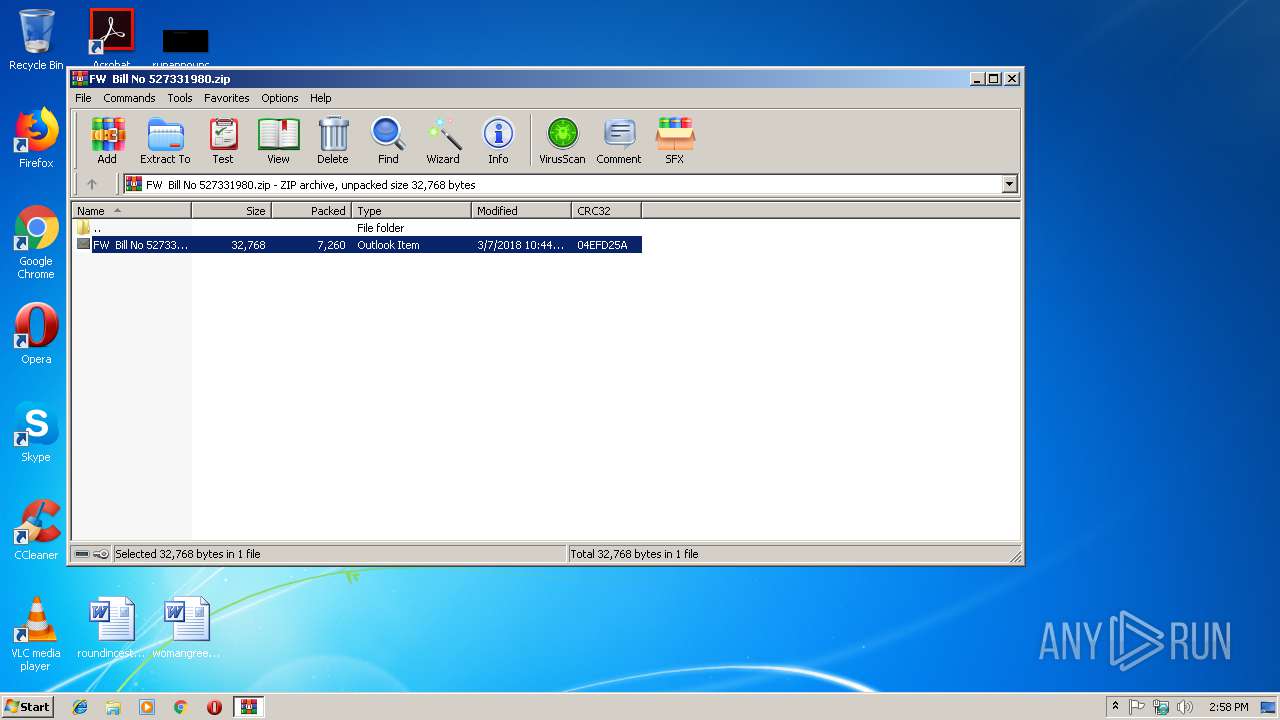
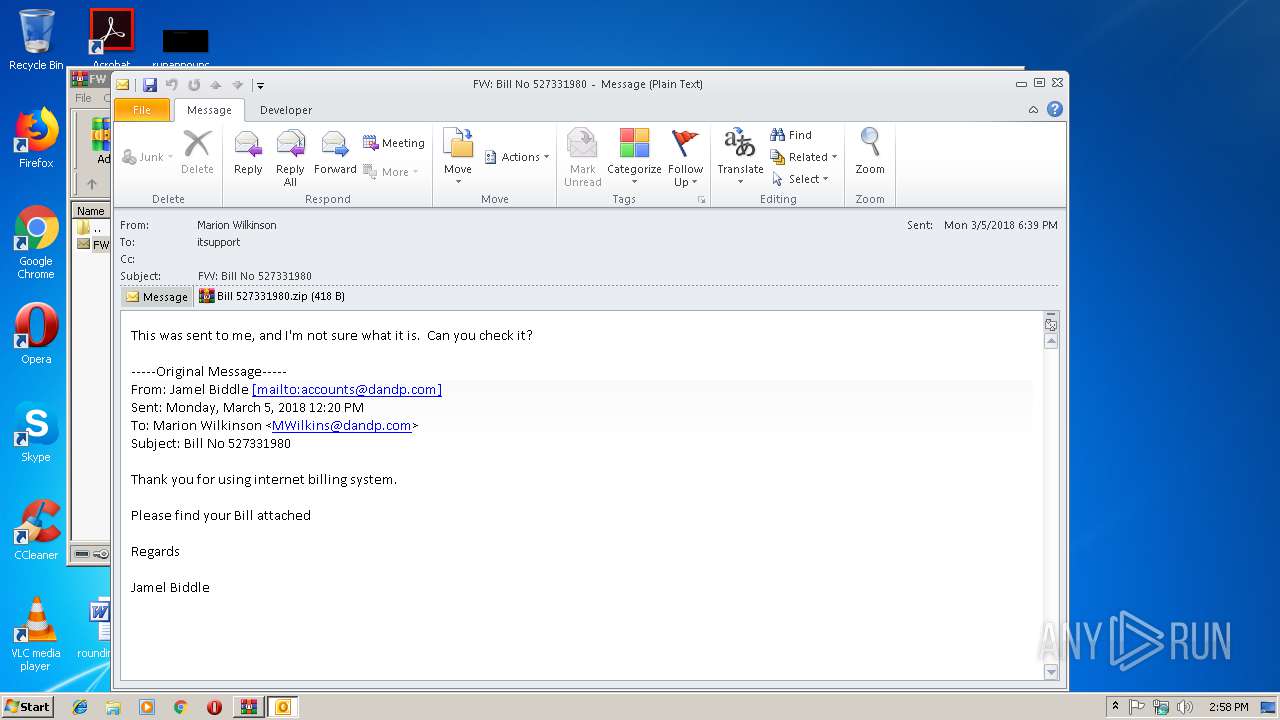
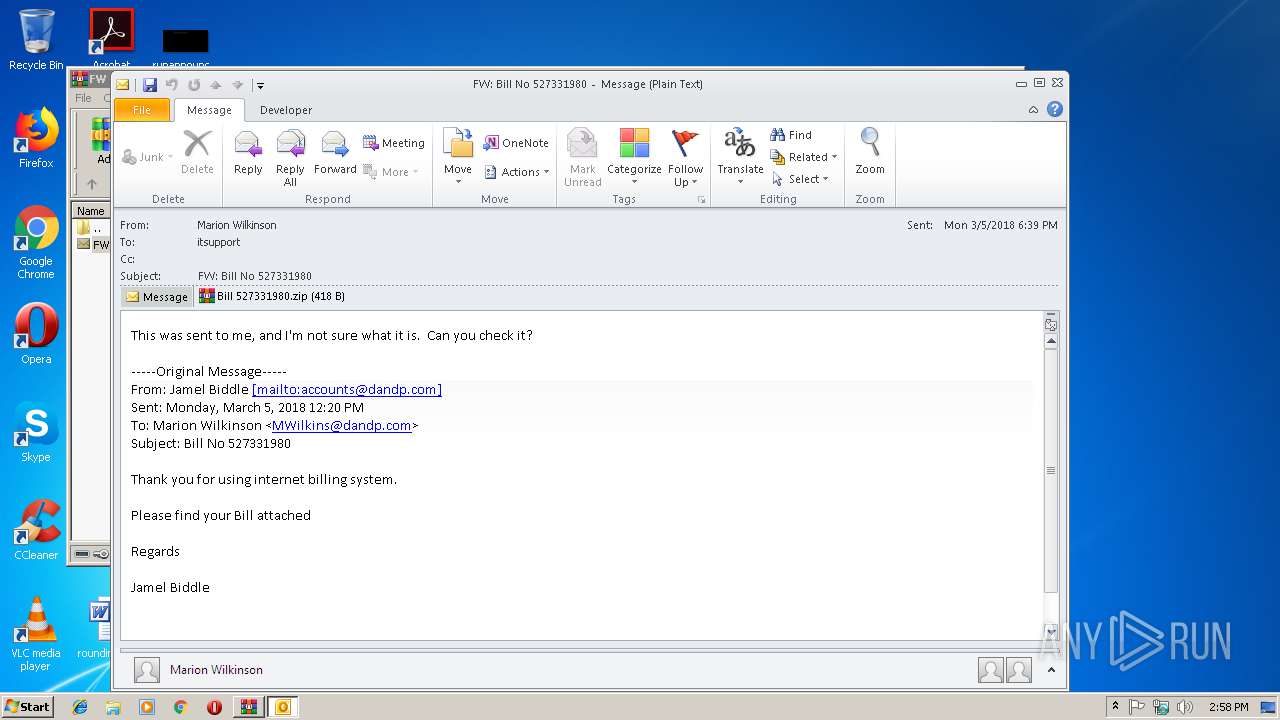
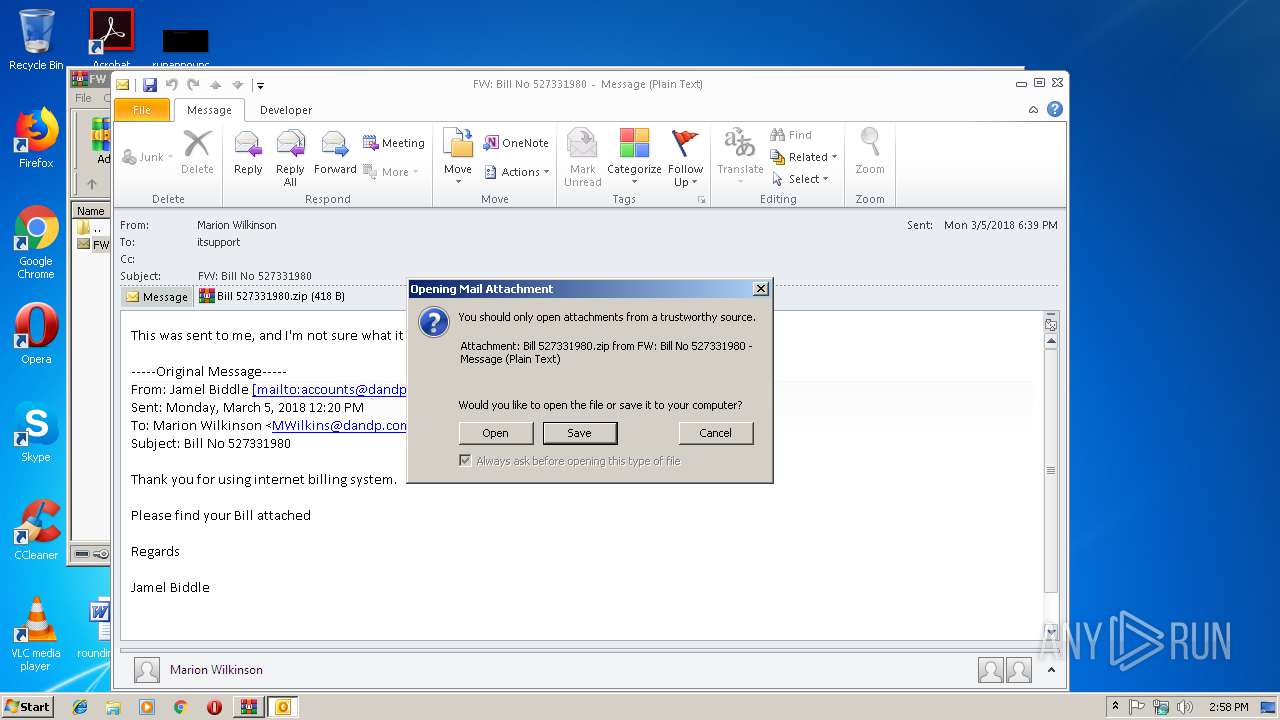
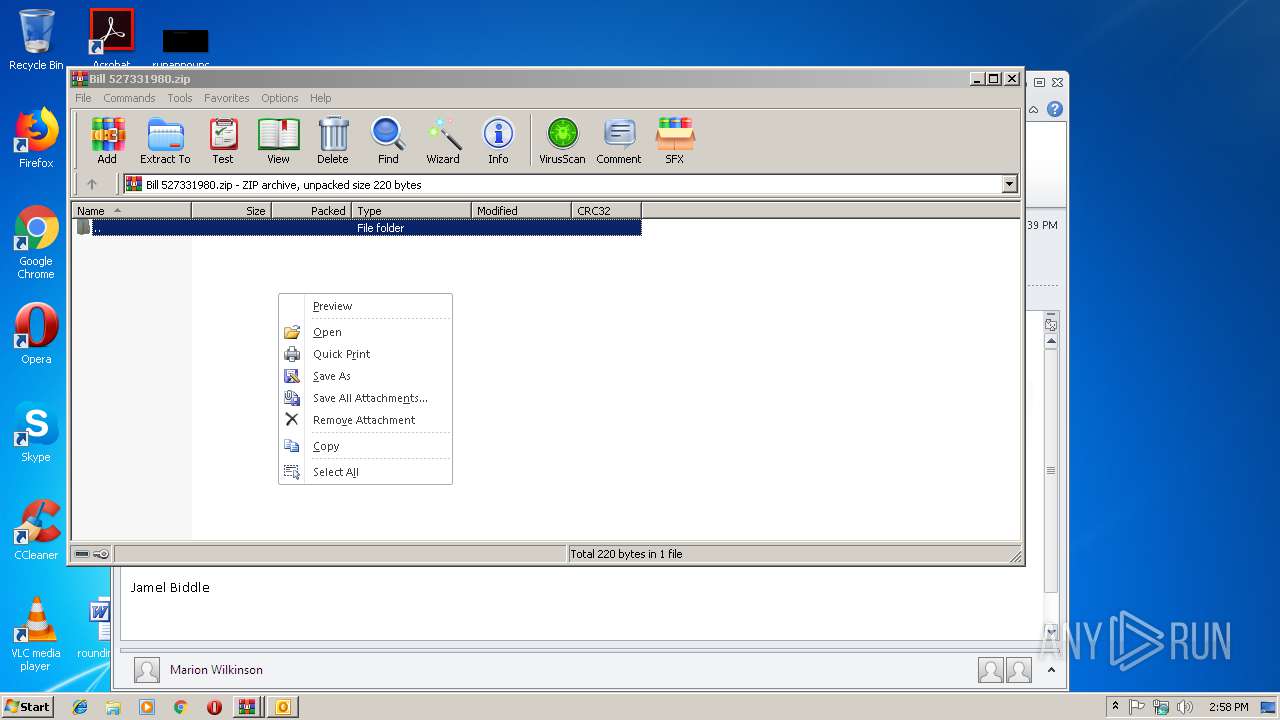
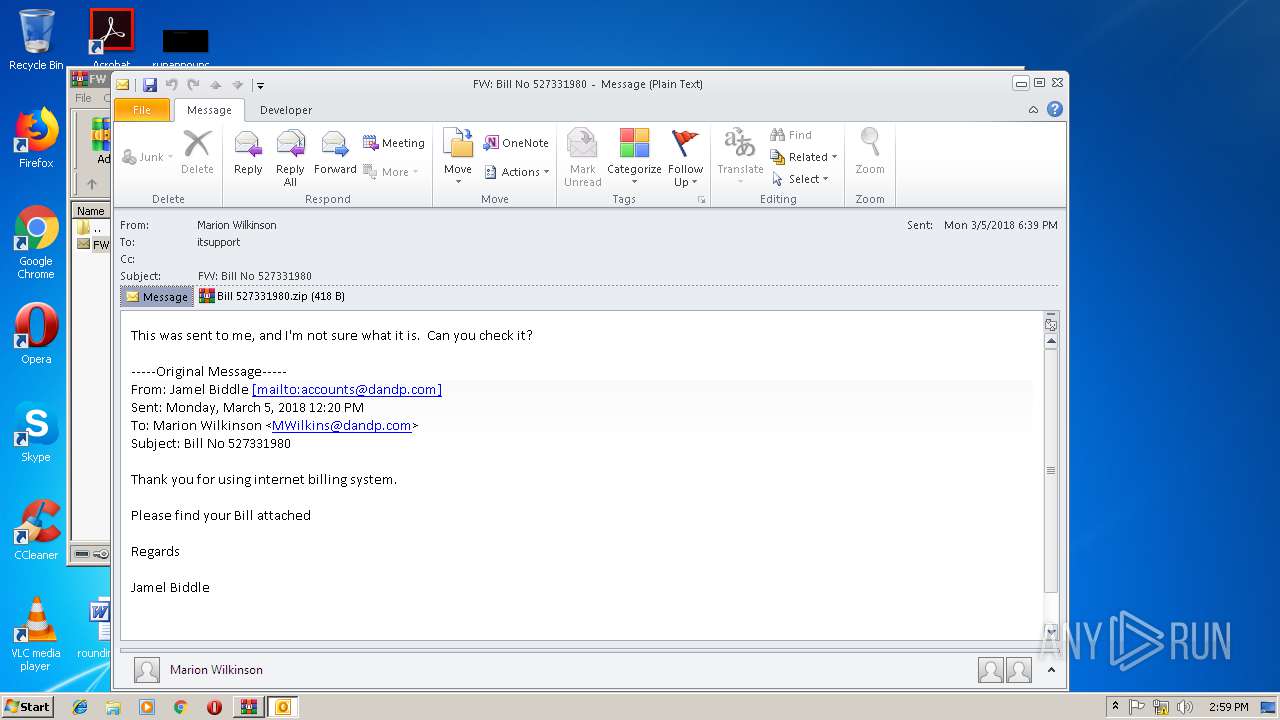
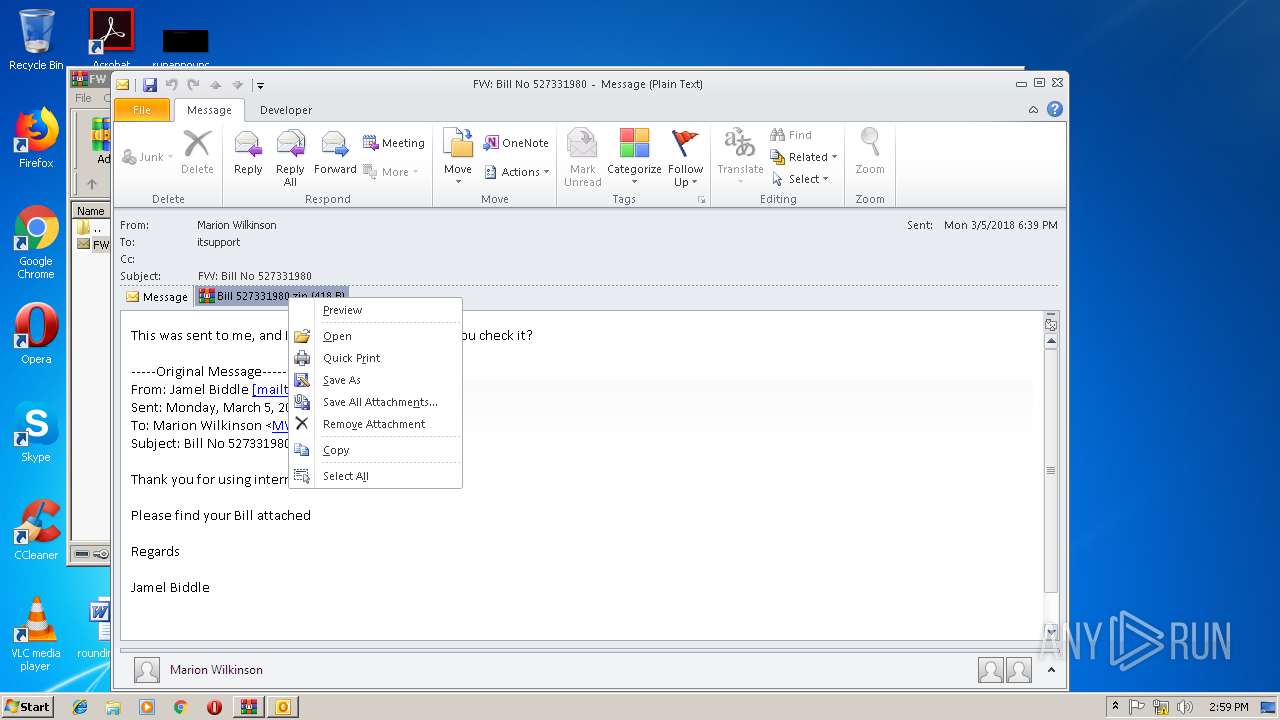
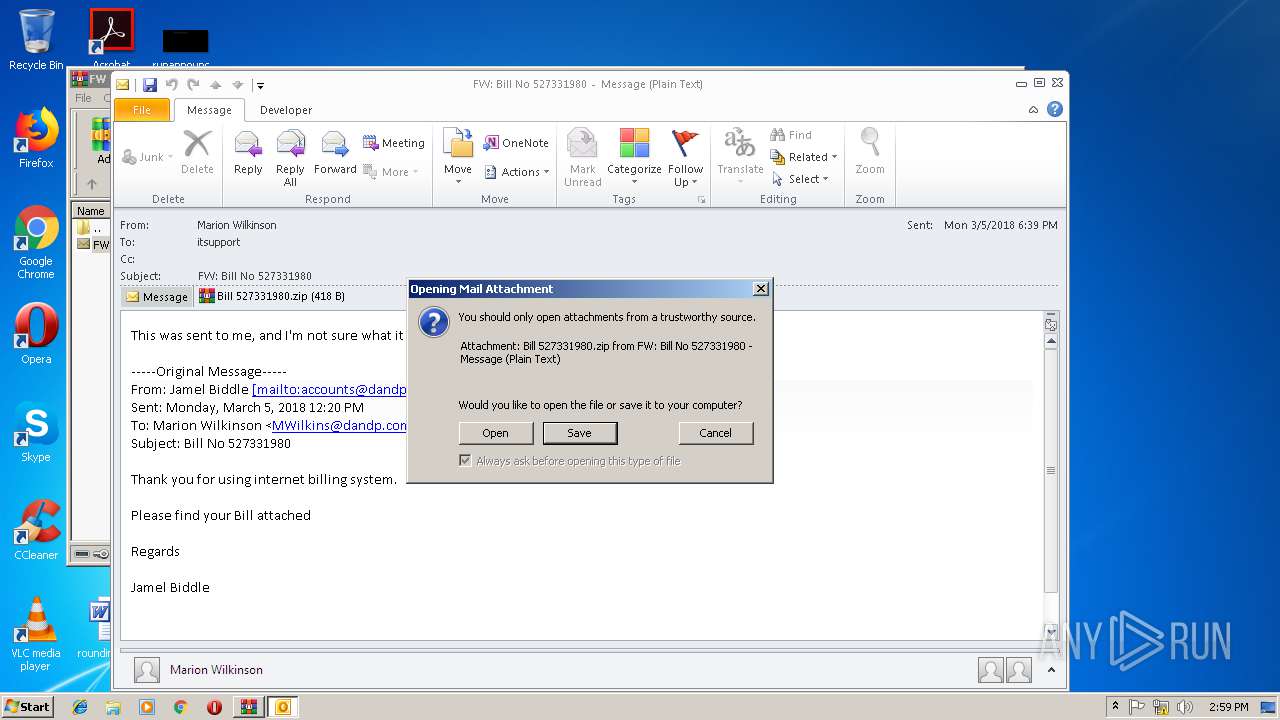
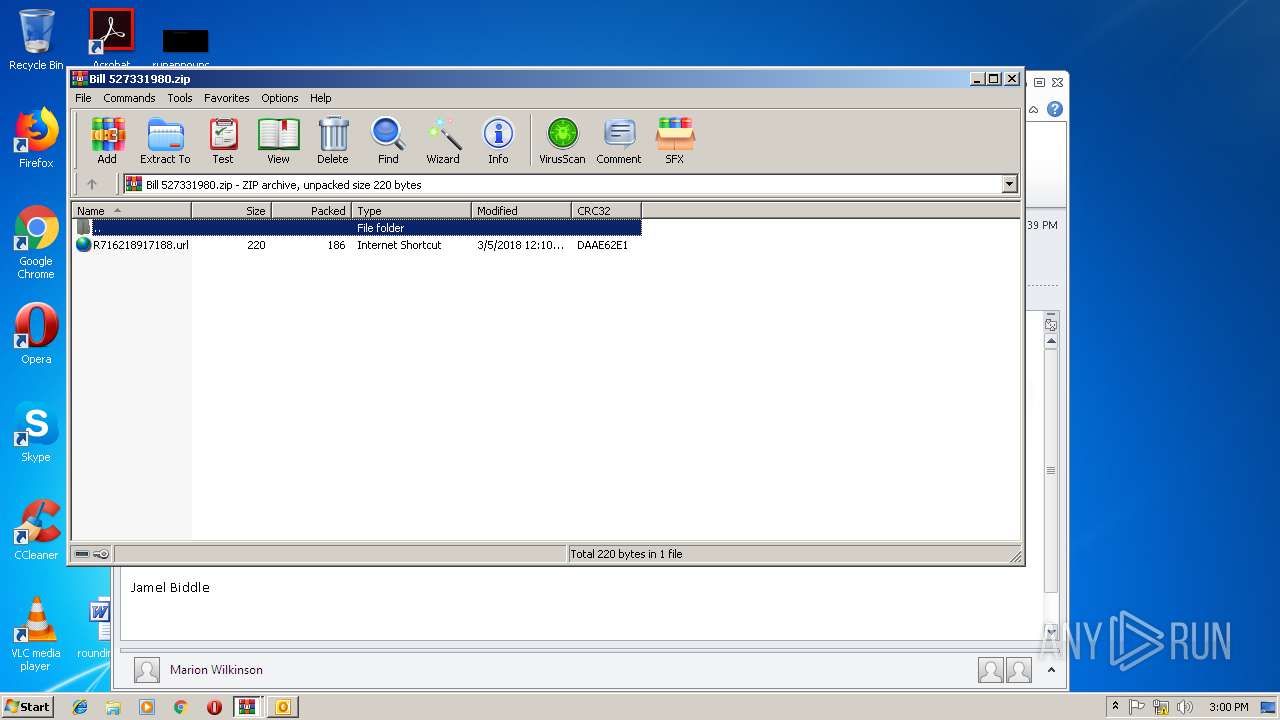
| File name: | FW Bill No 527331980.zip |
| Full analysis: | https://app.any.run/tasks/06569fa0-5b34-4891-87a9-0f6392c2aa27 |
| Verdict: | Malicious activity |
| Analysis date: | March 14, 2019, 14:58:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 6FBBD18F9A79C775BCF223EF7E6354BA |
| SHA1: | 191244EDF40C3E5CD3038487A4321902F3FB2105 |
| SHA256: | C42EA4C7EBB1CD9FB901FF2B220F28542595C2C042E81C4CA21C9C581A82ADDB |
| SSDEEP: | 192:NZGe4ndGqvIZuDxSwBCMikP8/SGBBfRF3kmt:NsmZuD0pMiTL33ft |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 3752)
SUSPICIOUS
Starts Microsoft Office Application
- WinRAR.exe (PID: 3460)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 3752)
Creates files in the user directory
- OUTLOOK.EXE (PID: 3752)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3752)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:03:07 10:44:15 |
| ZipCRC: | 0x04efd25a |
| ZipCompressedSize: | 7260 |
| ZipUncompressedSize: | 32768 |
| ZipFileName: | FW Bill No 527331980.msg |
Total processes
36
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2620 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\XAK8UTLW\Bill 527331980.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3460 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\FW Bill No 527331980.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3712 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\XAK8UTLW\Bill 527331980.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3752 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\Rar$DIa3460.1326\FW Bill No 527331980.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
Total events
2 976
Read events
2 522
Write events
435
Delete events
19
Modification events
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\FW Bill No 527331980.zip | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {0006F045-0000-0000-C000-000000000046} {000214FA-0000-0000-C000-000000000046} 0xFFFF |
Value: 01000000000000007870976276DAD401 | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {0006F045-0000-0000-C000-000000000046} {000214EB-0000-0000-C000-000000000046} 0xFFFF |
Value: 01000000000000002C359C6276DAD401 | |||
Executable files
0
Suspicious files
2
Text files
26
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3752 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRA6F4.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3752 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\XAK8UTLW\Bill 527331980 (2).zip\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3460.1326\FW Bill No 527331980.msg | msg | |
MD5:— | SHA256:— | |||
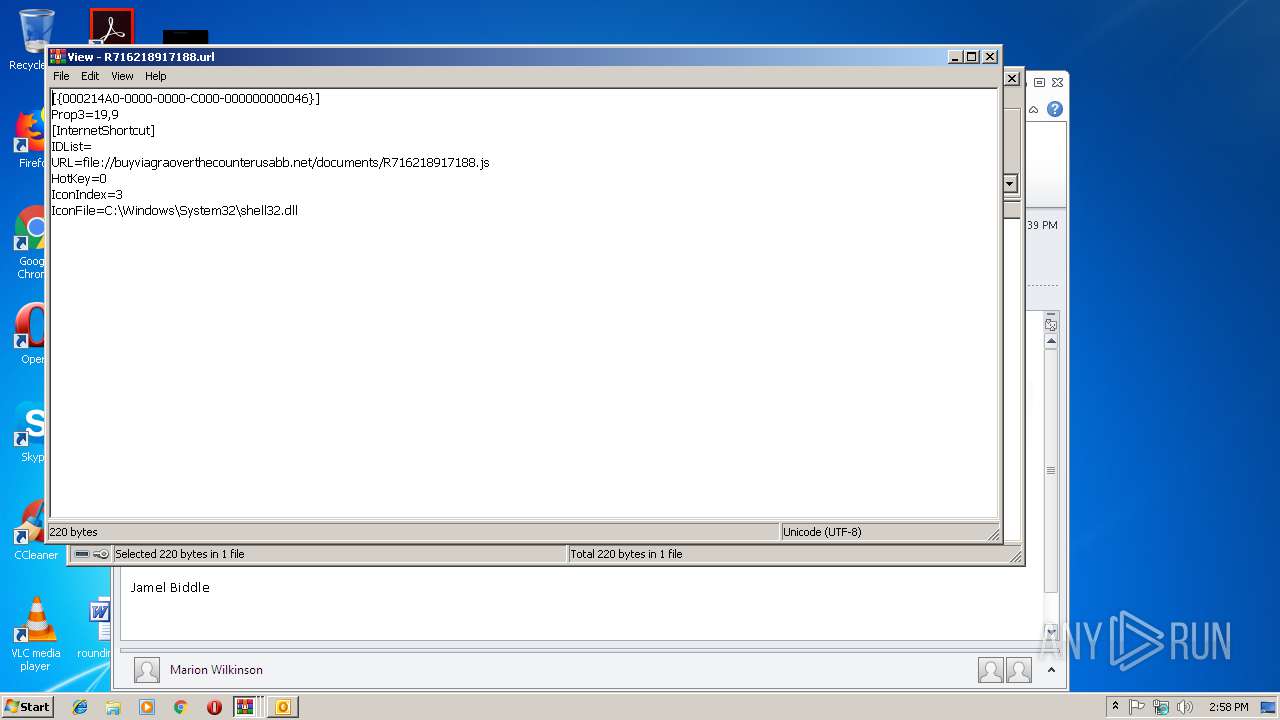
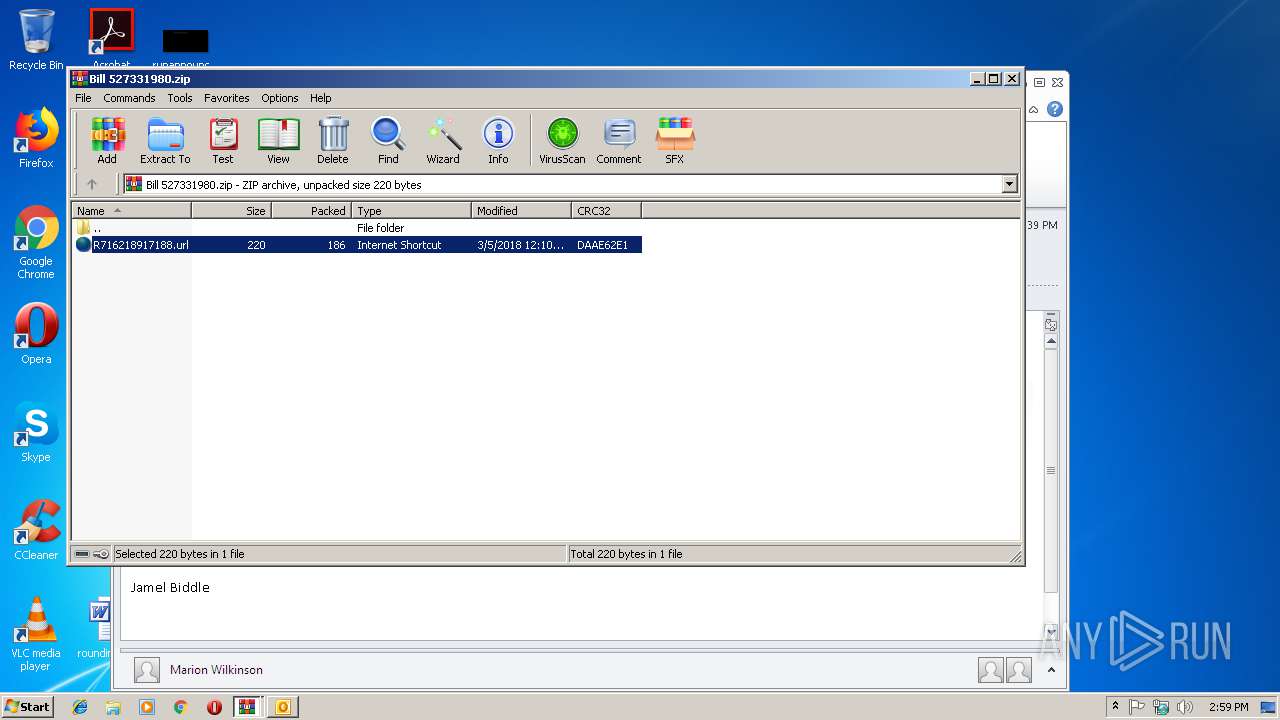
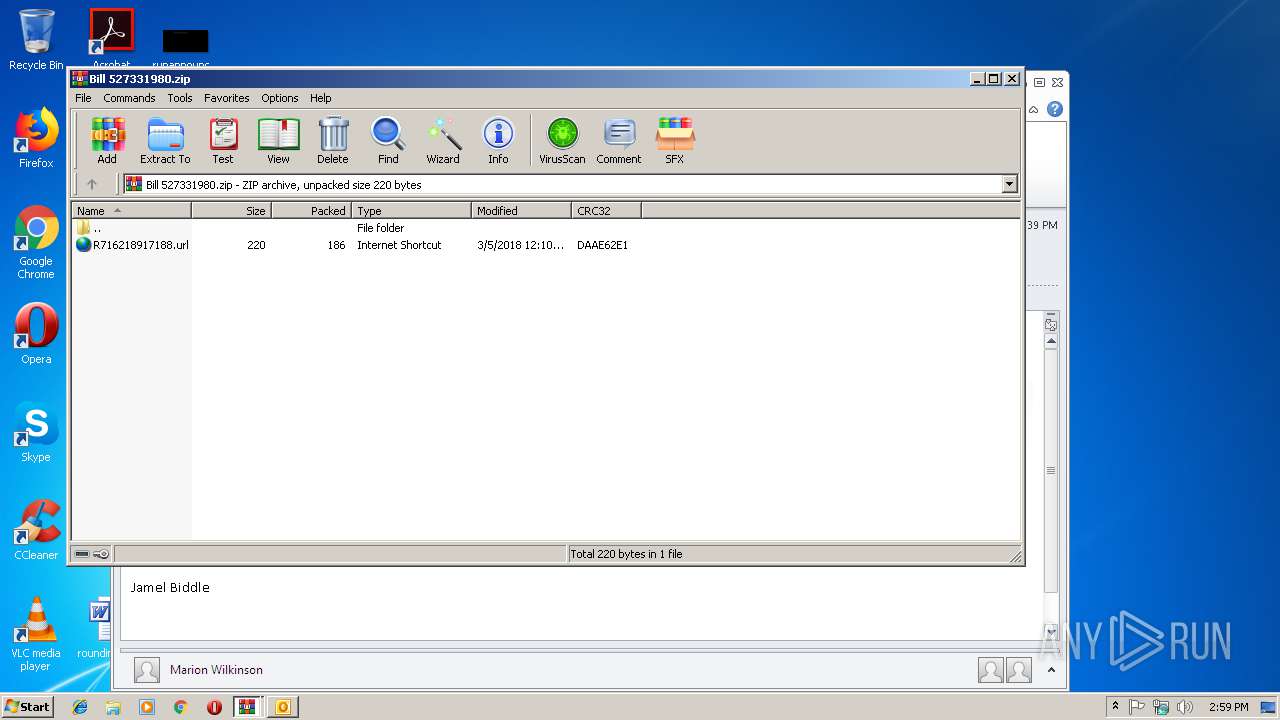
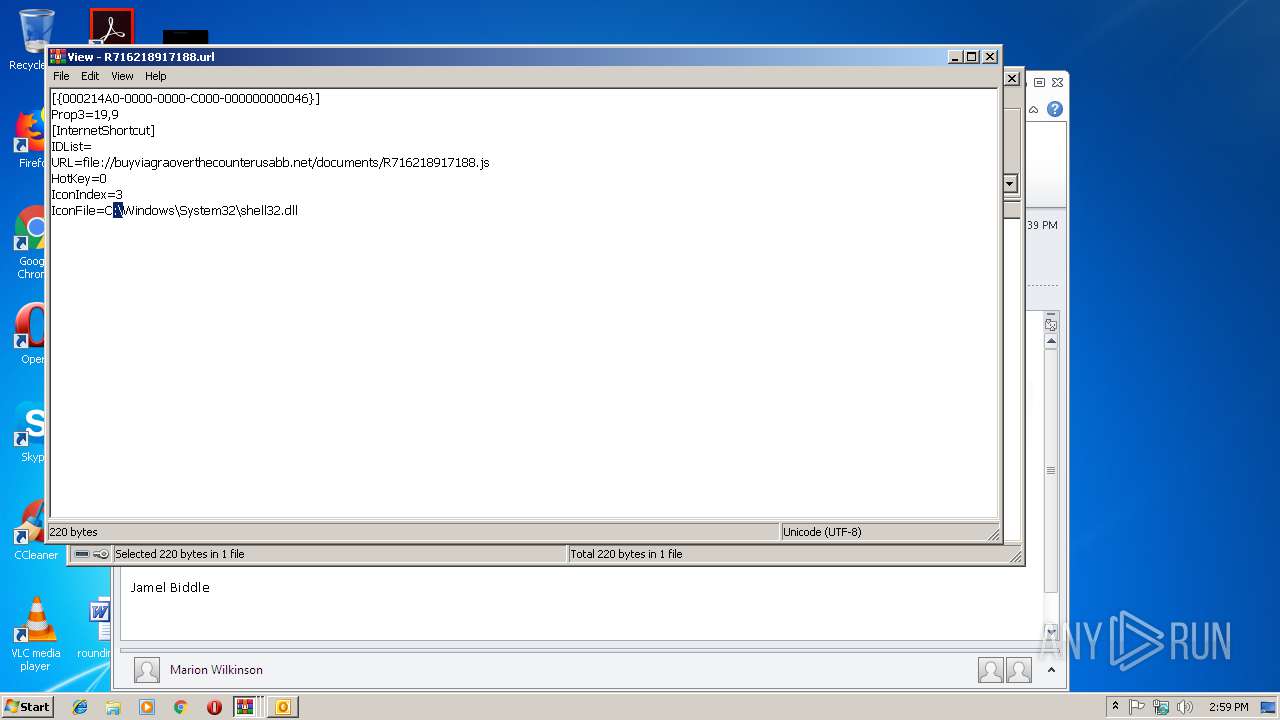
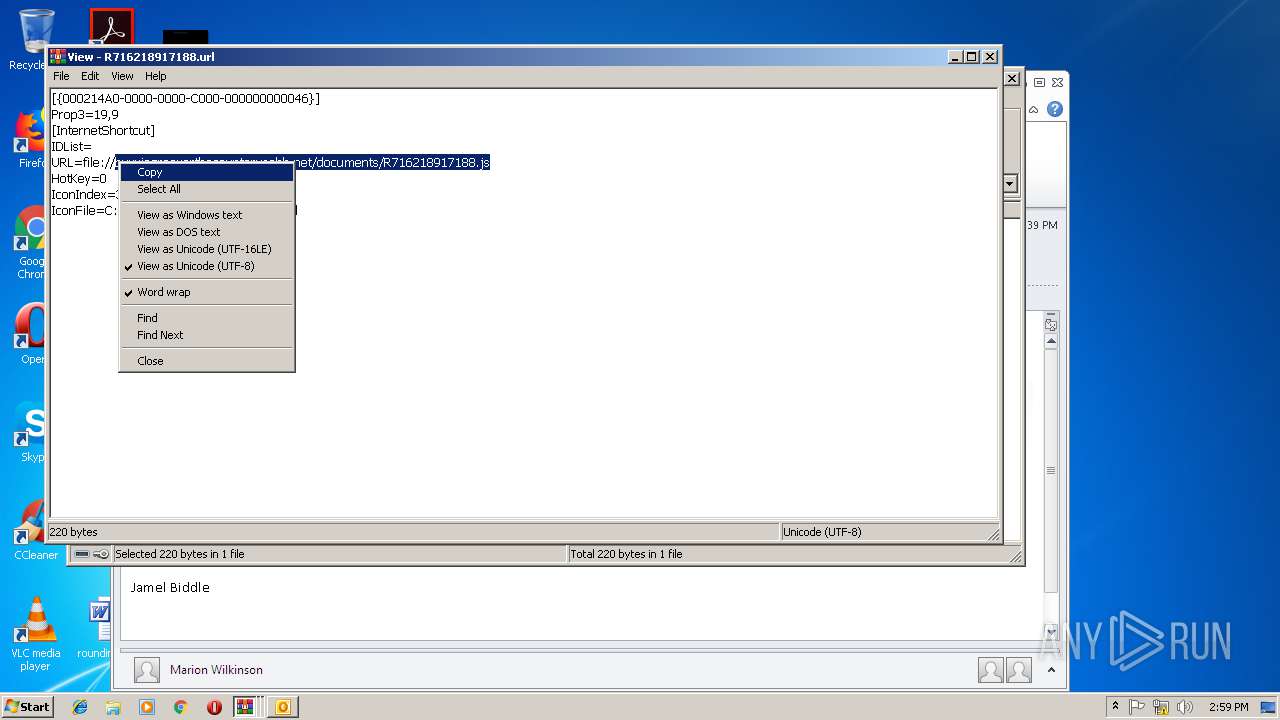
| 2620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2620.3006\R716218917188.url | text | |
MD5:— | SHA256:— | |||
| 3752 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\XAK8UTLW\Bill 527331980.zip | compressed | |
MD5:— | SHA256:— | |||
| 3752 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\XAK8UTLW\Bill 527331980 (2).zip | compressed | |
MD5:— | SHA256:— | |||
| 2620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2620.4839\R716218917188.url | text | |
MD5:— | SHA256:— | |||
| 3752 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3752 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\{3D213749-4131-4BF4-BB29-34700B806CCC}\{1C306CB1-771E-4B4B-A902-86E897877F5B}.png | image | |
MD5:7D80C0A7E3849818695EAF4989186A3C | SHA256:72DC527D78A8E99331409803811CC2D287E812C008A1C869A6AEA69D7A44B597 | |||
| 3752 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:48DD6CAE43CE26B992C35799FCD76898 | SHA256:7BFE1F3691E2B4FB4D61FBF5E9F7782FBE49DA1342DBD32201C2CC8E540DBD1A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3752 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3752 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
buyviagraoverthecounterusabb.net |
| unknown |