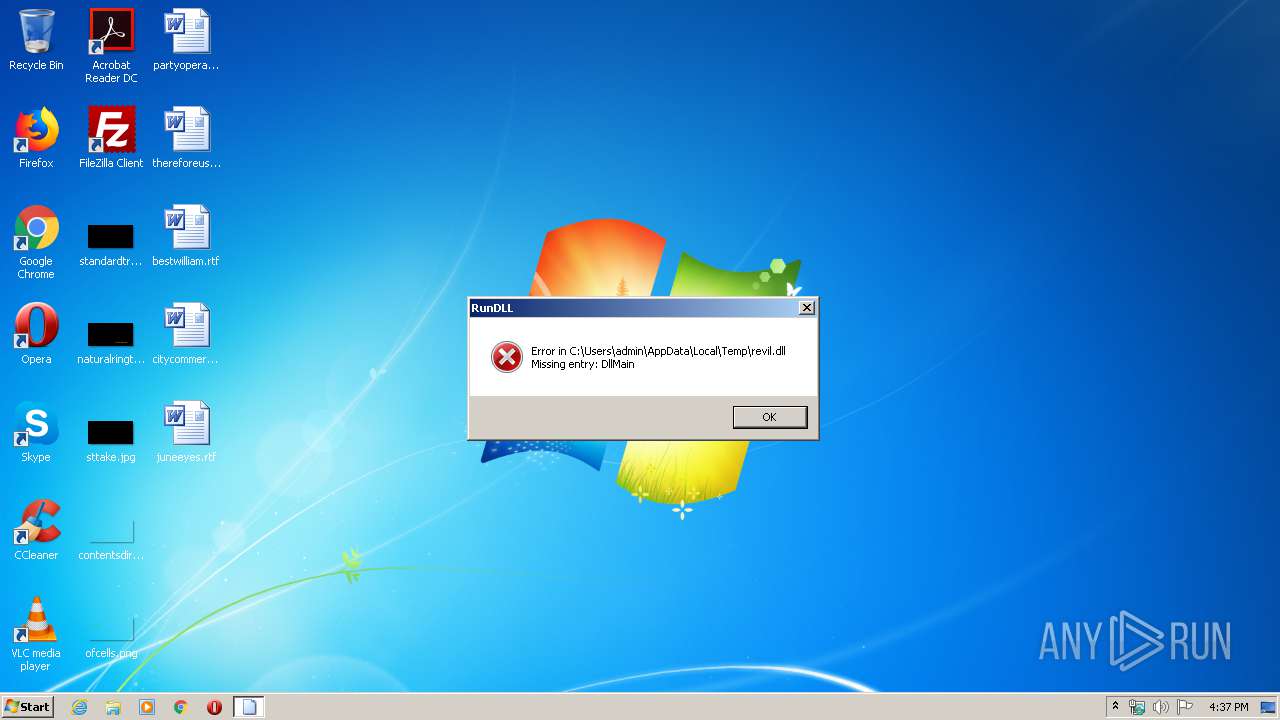
| File name: | revil.dll |
| Full analysis: | https://app.any.run/tasks/1f4fa411-f107-48dd-9561-9f277914d77e |
| Verdict: | Malicious activity |
| Analysis date: | February 21, 2020, 16:37:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (DLL) (GUI) Intel 80386, for MS Windows |
| MD5: | B979913C1157D8E0E1066AFBD296E3F3 |
| SHA1: | 1016B7581EA09468B93CF635DBE0FF760BCF1428 |
| SHA256: | C40DFD58E6DA0AADE75D09B6A659CF165F072BA89AEF2D60C10C153793535EE7 |
| SSDEEP: | 3072:JLFrb30BRtBZZg+i2ayyYOCWGPyLydrkxMT3QmMlRNv3WQ/YC:NJ0BXScFyfC3Hd4ygmyL3Hg |
MALICIOUS
Loads dropped or rewritten executable
- rundll32.exe (PID: 2516)
SUSPICIOUS
Application launched itself
- rundll32.exe (PID: 3000)
Executes PowerShell scripts
- rundll32.exe (PID: 2516)
Creates files in the user directory
- powershell.exe (PID: 3692)
Uses RUNDLL32.EXE to load library
- rundll32.exe (PID: 3000)
Executed as Windows Service
- vssvc.exe (PID: 4068)
Executed via COM
- unsecapp.exe (PID: 852)
Creates files in the program directory
- rundll32.exe (PID: 2516)
INFO
Loads main object executable
- rundll32.exe (PID: 3000)
Dropped object may contain TOR URL's
- rundll32.exe (PID: 2516)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (43.5) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (29.8) |
| .exe | | | Generic Win/DOS Executable (13.2) |
| .exe | | | DOS Executable Generic (13.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:02:11 21:03:38+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 96768 |
| InitializedDataSize: | 72704 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x10a04 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 11-Feb-2020 20:03:38 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000F8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 11-Feb-2020 20:03:38 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00017974 | 0x00017A00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 7.6382 |
.rdata | 0x00019000 | 0x00002B74 | 0x00002C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.89912 |
.data | 0x0001C000 | 0x00001F90 | 0x00001E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.41442 |
.41hfa | 0x0001E000 | 0x0000C800 | 0x0000C800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.46917 |
.reloc | 0x0002B000 | 0x0000061C | 0x00000800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 5.68528 |
Imports
KERNEL32.dll |
Total processes
43
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 852 | C:\Windows\system32\wbem\unsecapp.exe -Embedding | C:\Windows\system32\wbem\unsecapp.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Sink to receive asynchronous callbacks for WMI client application Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2516 | "C:\Windows\System32\rundll32.exe" C:\Users\admin\AppData\Local\Temp\revil.dll, DllMain | C:\Windows\System32\rundll32.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3000 | "C:\Windows\System32\rundll32.exe" "C:\Users\admin\AppData\Local\Temp\revil.dll", DllMain | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3692 | powershell -e RwBlAHQALQBXAG0AaQBPAGIAagBlAGMAdAAgAFcAaQBuADMAMgBfAFMAaABhAGQAbwB3AGMAbwBwAHkAIAB8ACAARgBvAHIARQBhAGMAaAAtAE8AYgBqAGUAYwB0ACAAewAkAF8ALgBEAGUAbABlAHQAZQAoACkAOwB9AA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4068 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
300
Read events
235
Write events
65
Delete events
0
Modification events
| (PID) Process: | (3000) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3000) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2516) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\GitForWindows |
| Operation: | write | Name: | aaH |
Value: 013499DB2790E43F4F8181A9BBD8C5549794D4024978674C98E3AFCF5E5D390C | |||
| (PID) Process: | (2516) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\GitForWindows |
| Operation: | write | Name: | fdle |
Value: A0F0EA03DBE1261BA447197820E6F8AD8EDE6226109A97EA2BB89466737B1C67 | |||
| (PID) Process: | (2516) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\GitForWindows |
| Operation: | write | Name: | 1TfXk |
Value: 3D5AB4EDC92FC357501DD288F3D3E159B93125DF6413188A03123406D1B51529A1F0DACDE23A306920C72D553D358EDB7F98D47AD0F4588627EA3AF16476DF191E02BC5B5F1D0609F0BB0A75926520D193936501A97F161A | |||
| (PID) Process: | (2516) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\GitForWindows |
| Operation: | write | Name: | 2YEdLY |
Value: 0F19F040DE9DCB9754FF9572BC4D0B1FCE10DC0189B3F0ADEADF9F8DFBFC42A4AFBC53A482C831F26993E5DA239DA01FD157DEEA1885CD3709E30D441546A0F37DF588311F1CDF5C8A5BF1B6AC825F08A481581BA7A14BBF | |||
| (PID) Process: | (2516) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\GitForWindows |
| Operation: | write | Name: | AaZW1s3 |
Value: .15q97741l | |||
| (PID) Process: | (2516) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\GitForWindows |
| Operation: | write | Name: | QaUXNv2P |
Value: 7168EAAB7A135CA7A1F14B932F63C428ED2440D90F778E12129E15B7D34AFD97EA0750B75F77E460EE1B321DFC49A49FE28F230958D246A438496EDEA7357A470622B1FA75210C396F2D2B76081FC8856B428E8C94AED623F2302D4CC93F90F7D6A15B80B483BD09696D10C4C36671A5831E68232149EE8B2240323F2BA29C865402271637204E17724D7C22BC1A5C3F6162936782C88B6984301D499BC525AF139137BD98BA09613FA6B10631EF7D7D8DDDCFBC3DF4A7640A0EA41B70308618D91621AF3671733B8EFA4179DEA708EA5A6B4033328C3CCBCA05ECAF7555A370D05EB074576773F75F4DEE4C9987287565BD9B900608A82CFC114C0A89513F5632869EB22B05508A8B0AC9EFF2B1A3E99479E43CF5D26A876A38437C4B1CA15EF05D936E0A5DF487A27845321A6512544F7D630731F462B0F609E62C08AC77FF2BD4CF4827D006B9792A6F92815813660A392B272987003B06EAED0EFC7B1DB8311B3D9359C611588B2CB045D46F644679CF22640551C0217BD5C0E59F26E190BBF162A715B24060D1817CE4EC53928E9C52BD0EBD6B4EB5E0D87301C389DCE36E70DD4D1A0F97A5CD55F52521BAEC85B15ECB58FBA22AF81D12768AEEBBEFFE89B1F67DDF1E63173D0BCE2AE0C63540F04DACDD13A1CFD8F241D5C441CCC06C9EA9B05F63D264DD4486A6FE7F826F4E54D33495963FB4388DAC349D1070FB91255206485EAECF6C764D2E0D88537EADDB1F6917EE8BA0FAF5CBD945A8949E65625DB24489D42F204572F6B49147D694C1A8D2D13F686B7761E8F76FD356E21B8BB6B91DBE2A5F6E50E35B7F44013CB86B9C8FB7D8A6B76E8D6A28BE7EC553D832EC667BED686E3C440B6B72AFC5576A37F5E3FA821494DE85C66857B0ADD9512D7CF800341D4C0D9FE33C93D1A7EC966EFC067308FFAF9857EAF4814ADBE351F7EE33F0B485460C5B13BCE4E9CBCB2D201B5025E4A72311A9EA13FBB795CC7A0249A438BF14E1728B9452640813DCD3F35DB17D2BE3D5C9A1D7D7CE4A90DDC0BCEBF8408E2A05F0FC31989E6AD63F07FBB096FD0FEBA00FD36DD1A9DE153F2586FD43367A9DEFCDB2B9003EA05E21591F6C2D8E5F31470C723D2B34A990717C3DF8B4E262671DBE5B8908CFDE69740A50717C918FE1FF2F481087D9D2E5FB8890B49D65AABD73D94372F4E54AE1D72DC9173C6A5A517253233DC00196E5E45EA7D904682B4A43FAEB7D4F62C83E7D78F8F35DF559D7A3F49B6199568B3CDDD2CA640C38D5F23DC2D5B2D4E82FD4B64A31F52FBF3BAF0DD6009C66DF75F32863B56FC3B485758EA826743E37B4B9B4DD953FB39ABB058FEC76B101E81C6B8D5A141094034526134CC092E62BC6CBDF1B371D8F7AD62F95C244750F63D1C48A29439F0FB7 | |||
| (PID) Process: | (3692) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
0
Suspicious files
245
Text files
1
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3692 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\6ST9Q4OX7OZUNB8ZM7TL.temp | — | |
MD5:— | SHA256:— | |||
| 2516 | rundll32.exe | C:\autoexec.bat | — | |
MD5:— | SHA256:— | |||
| 2516 | rundll32.exe | C:\ProgramData\ntuser.pol | — | |
MD5:— | SHA256:— | |||
| 2516 | rundll32.exe | C:\15q97741l-readme.txt | binary | |
MD5:— | SHA256:— | |||
| 2516 | rundll32.exe | C:\$recycle.bin\15q97741l-readme.txt | binary | |
MD5:— | SHA256:— | |||
| 3692 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RFa67c3d.TMP | binary | |
MD5:— | SHA256:— | |||
| 2516 | rundll32.exe | c:\autoexec.bat.15q97741l | binary | |
MD5:— | SHA256:— | |||
| 2516 | rundll32.exe | C:\program files\15q97741l-readme.txt | binary | |
MD5:— | SHA256:— | |||
| 2516 | rundll32.exe | C:\$recycle.bin\s-1-5-21-1302019708-1500728564-335382590-1000\15q97741l-readme.txt | binary | |
MD5:— | SHA256:— | |||
| 2516 | rundll32.exe | C:\$recycle.bin\s-1-5-21-1302019708-1500728564-335382590-500\15q97741l-readme.txt | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report