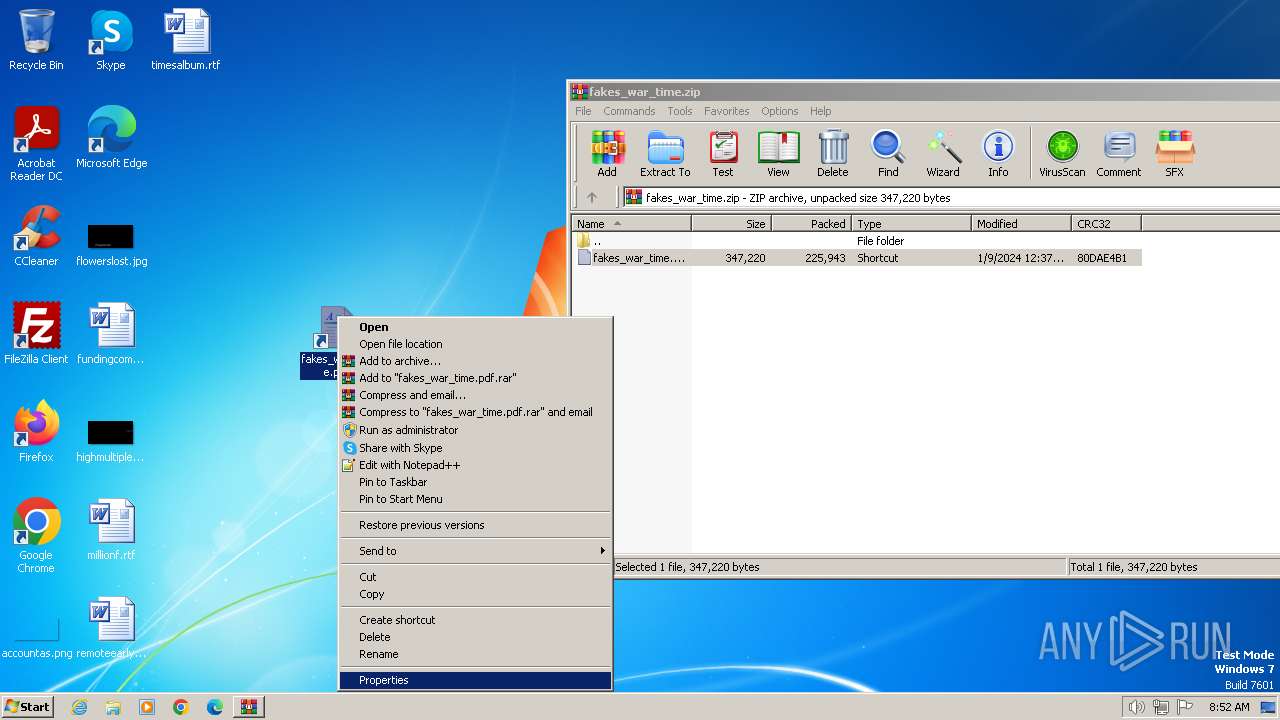
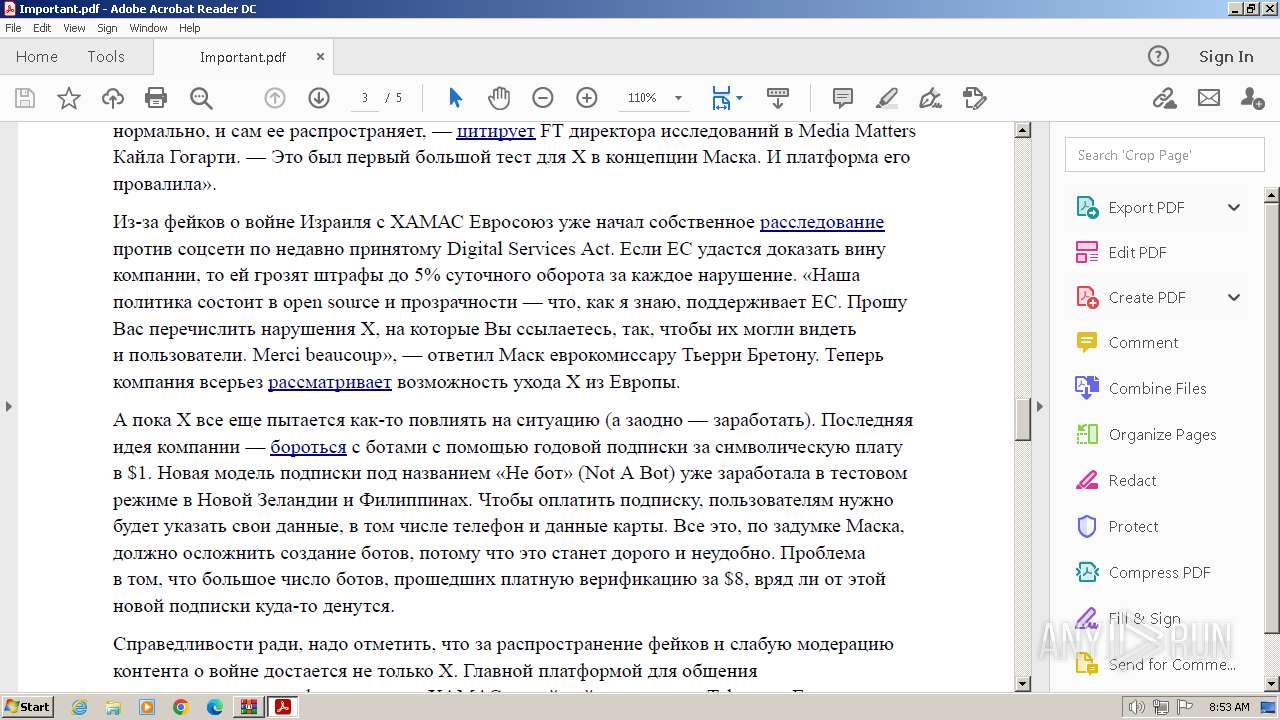
| File name: | fakes_war_time.zip |
| Full analysis: | https://app.any.run/tasks/db1d667d-eff5-42ff-a119-19c2690bb02f |
| Verdict: | Malicious activity |
| Analysis date: | January 12, 2024, 08:52:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | E637C1CD1FBF16B55BDB451765F9EF75 |
| SHA1: | 5AEE0DF4423E4DAA8EAD77BD626F731207D4A155 |
| SHA256: | C3FAAA3A6B0831F1D3974FCEE80588812CA7AFEB53CC173E0B83BCB6787FA13E |
| SSDEEP: | 6144:8m78oOxh6FykzwmEq20CgZNdmL3ZLxnlh38x/kosp:D4oS6fMp0CeO3ZLxlhI/kosp |
MALICIOUS
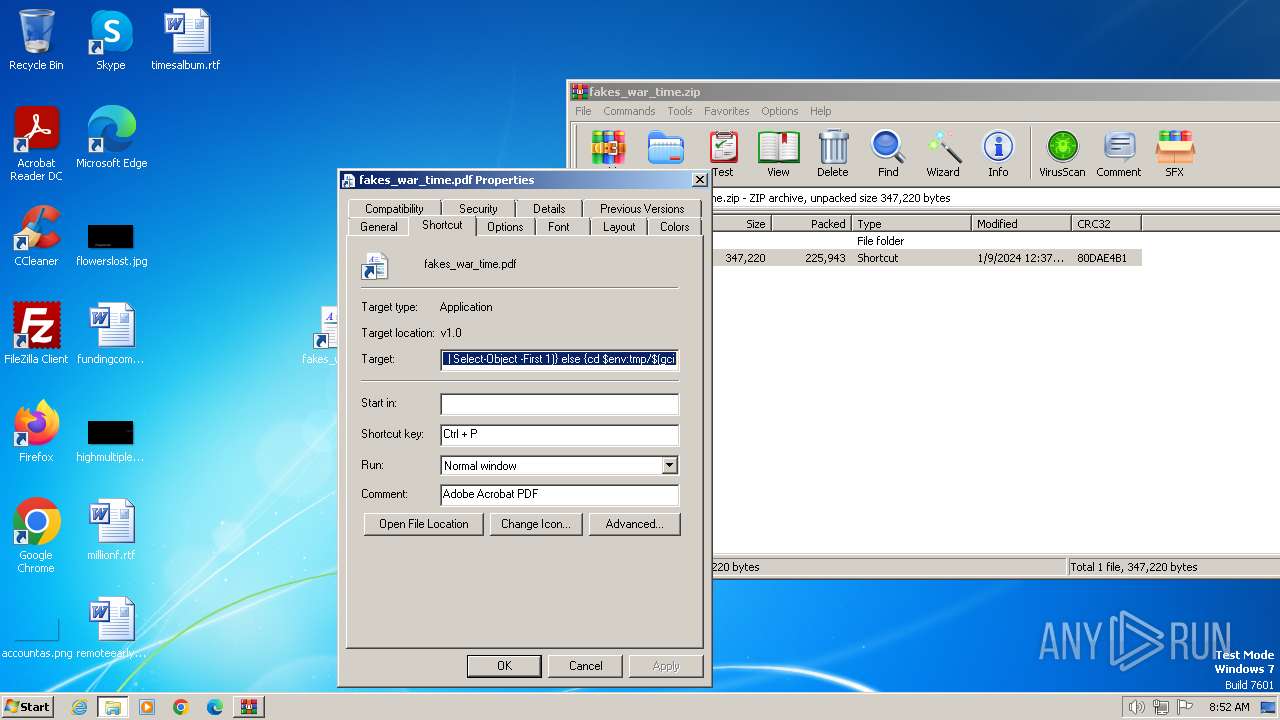
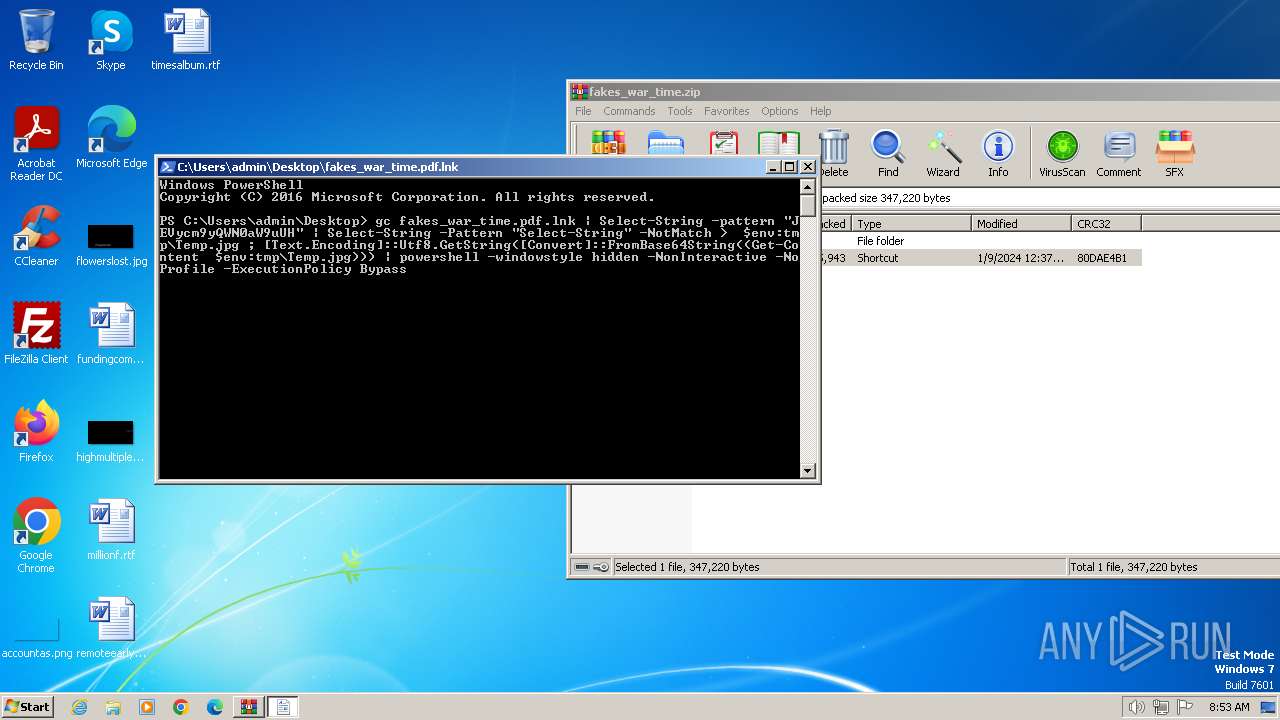
Bypass execution policy to execute commands
- powershell.exe (PID: 1624)
Changes powershell execution policy (Bypass)
- powershell.exe (PID: 584)
Run PowerShell with an invisible window
- powershell.exe (PID: 1624)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 2416)
- powershell.exe (PID: 584)
The process hide an interactive prompt from the user
- powershell.exe (PID: 584)
The process bypasses the loading of PowerShell profile settings
- powershell.exe (PID: 584)
Application launched itself
- powershell.exe (PID: 2416)
- powershell.exe (PID: 584)
Using 'findstr.exe' to search for text patterns in files and output
- powershell.exe (PID: 1624)
Uses ATTRIB.EXE to modify file attributes
- powershell.exe (PID: 1624)
Reads the Internet Settings
- powershell.exe (PID: 1624)
INFO
Manual execution by a user
- powershell.exe (PID: 2416)
Application launched itself
- AcroRd32.exe (PID: 1636)
- RdrCEF.exe (PID: 2736)
- msedge.exe (PID: 568)
- msedge.exe (PID: 3012)
Connects to the CnC server
- powershell.exe (PID: 1624)
Unusual connection from system programs
- powershell.exe (PID: 1624)
HTTPSHELL has been detected (SURICATA)
- powershell.exe (PID: 1624)
The Powershell connects to the Internet
- powershell.exe (PID: 1624)
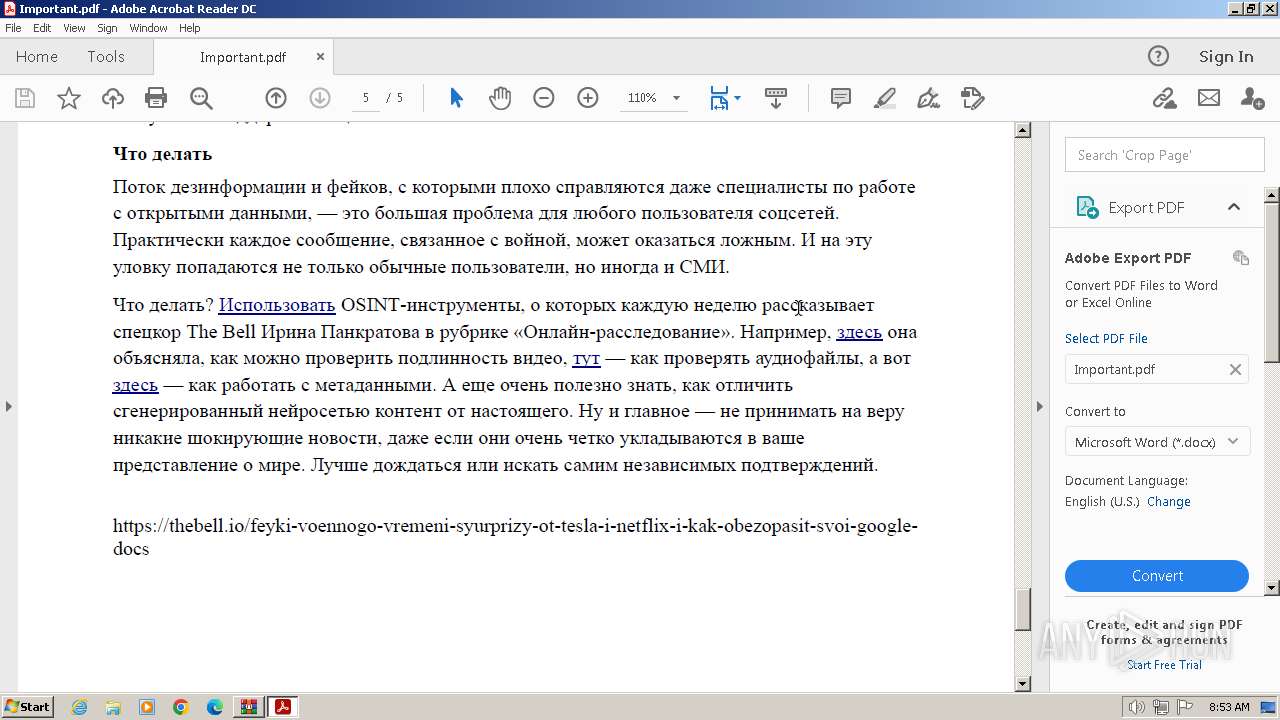
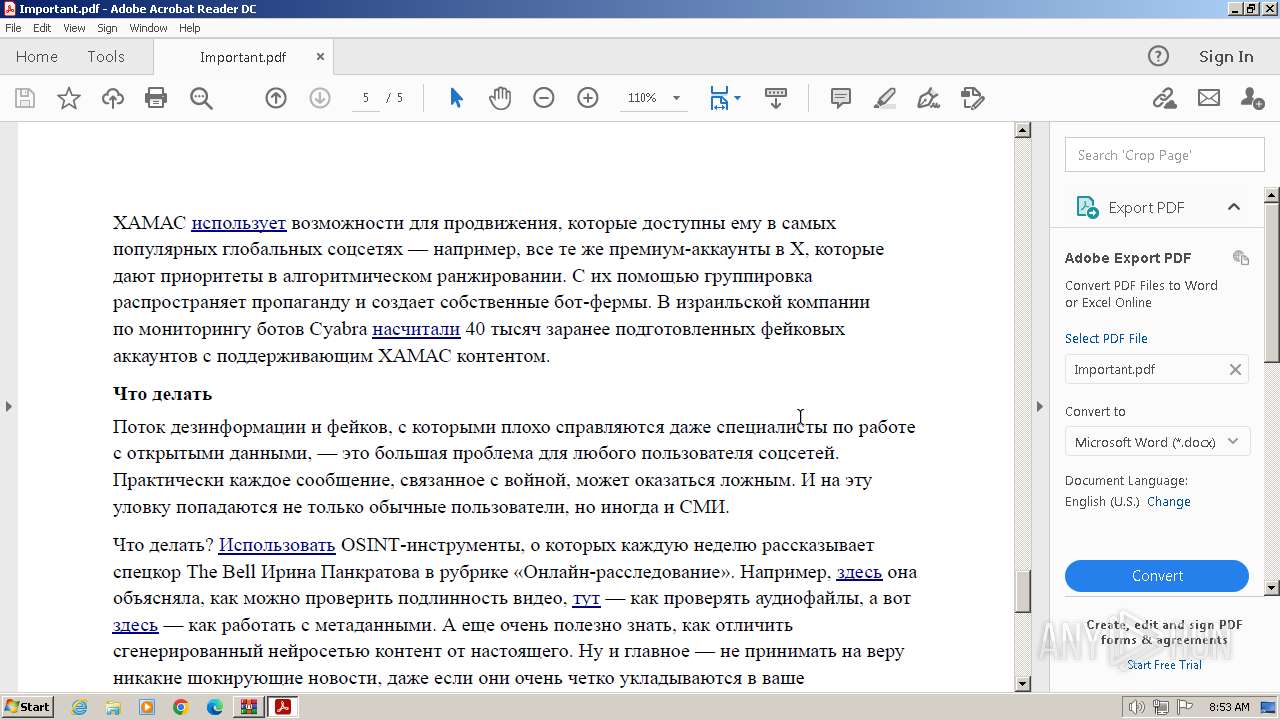
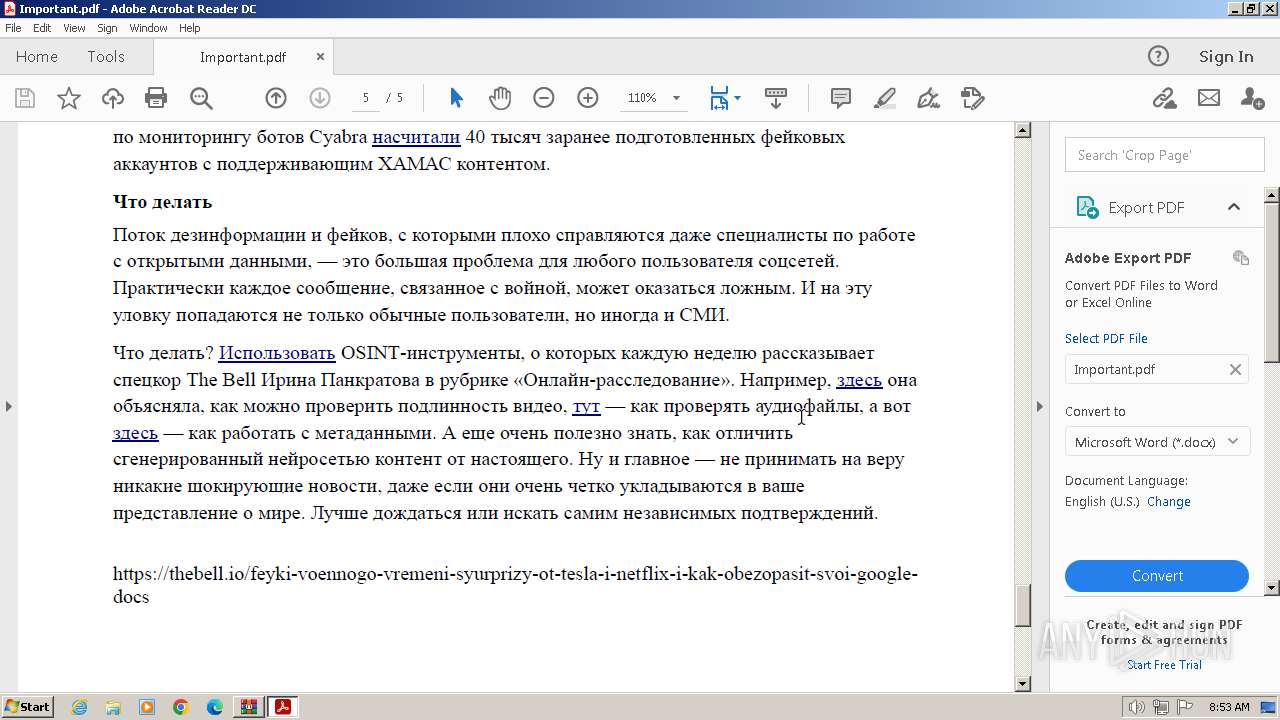
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:01:09 15:37:18 |
| ZipCRC: | 0x80dae4b1 |
| ZipCompressedSize: | 225943 |
| ZipUncompressedSize: | 347220 |
| ZipFileName: | fakes_war_time.pdf.lnk |
Total processes
69
Monitored processes
33
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 568 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --single-argument https://thebell.media/onlayn-rassledovanie-kak-proverit-podlinnost-video | C:\Program Files\Microsoft\Edge\Application\msedge.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 584 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 876 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1172,6971946470486560363,5284178772407191588,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=17538179453506631897 --mojo-platform-channel-handle=1268 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1036 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1172,6971946470486560363,5284178772407191588,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=12498928399717473969 --mojo-platform-channel-handle=1200 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1484 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1172,6971946470486560363,5284178772407191588,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=75096645264243333 --renderer-client-id=8 --mojo-platform-channel-handle=1604 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1624 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -windowstyle hidden -NonInteractive -NoProfile -ExecutionPolicy Bypass | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1636 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\AppData\Local\Temp\Important.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | powershell.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1656 | "C:\Windows\system32\attrib.exe" +h C:\Users\admin\Temp.jpg | C:\Windows\System32\attrib.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1904 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1172,6971946470486560363,5284178772407191588,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=7149564983665704067 --mojo-platform-channel-handle=1200 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1928 | "C:\Windows\system32\findstr.exe" /R JVBERi0xLjcNCiW1tb fakes_war_time.pdf.lnk | C:\Windows\System32\findstr.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
21 366
Read events
21 242
Write events
124
Delete events
0
Modification events
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2416) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
4
Suspicious files
272
Text files
47
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2184 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2184.5135\fakes_war_time.pdf.lnk | binary | |
MD5:BF8A44DF0EA8E72CF03237E166F414A7 | SHA256:5FA3D13366348E7C999CCA9A06E4D2F5EC7F518ACA3B36F0366ECEDBA5F2B057 | |||
| 2416 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\BR08K1ZH0U79DXA2LPTH.temp | binary | |
MD5:05769FA9C3FB9048D63A3F7AEC1C5FBB | SHA256:E6BA6E7919225F9170802BC07EE90336BE9120EC28CB69A16C32DF81161E6BA9 | |||
| 2416 | powershell.exe | C:\Users\admin\AppData\Local\Temp\evbc2yvj.lta.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2416 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\39eecc48a3b0018d.customDestinations-ms | binary | |
MD5:05769FA9C3FB9048D63A3F7AEC1C5FBB | SHA256:E6BA6E7919225F9170802BC07EE90336BE9120EC28CB69A16C32DF81161E6BA9 | |||
| 584 | powershell.exe | C:\Users\admin\AppData\Local\Temp\ohavlujk.2pe.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 568 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RFe7bd3.TMP | — | |
MD5:— | SHA256:— | |||
| 568 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2416 | powershell.exe | C:\Users\admin\AppData\Local\Temp\ops4yr4v.dbw.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 584 | powershell.exe | C:\Users\admin\AppData\Local\Temp\5w5tdqkm.rr0.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1624 | powershell.exe | C:\Users\admin\AppData\Local\Temp\2gm535ts.324.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
82
DNS requests
91
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1624 | powershell.exe | POST | 200 | 141.8.193.27:80 | http://api-gate.xyz/api/v1/Client/Info | unknown | text | 38 b | unknown |
1624 | powershell.exe | GET | 200 | 141.8.193.27:80 | http://api-gate.xyz/api/v1/Client/Token | unknown | text | 7.01 Kb | unknown |
1624 | powershell.exe | POST | 200 | 141.8.193.27:80 | http://api-gate.xyz/api/v1/Client/Debug | unknown | text | 7 b | unknown |
1636 | AcroRd32.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?0225743a2ee7dc35 | unknown | compressed | 4.66 Kb | unknown |
1636 | AcroRd32.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?28bcce63ca23a400 | unknown | compressed | 4.66 Kb | unknown |
1636 | AcroRd32.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | binary | 471 b | unknown |
1624 | powershell.exe | GET | 200 | 141.8.193.27:80 | http://api-gate.xyz/api/v1/Client/Token | unknown | html | 95 b | unknown |
1624 | powershell.exe | POST | 200 | 141.8.193.27:80 | http://api-gate.xyz/api/v1/Client/Info | unknown | text | 38 b | unknown |
1624 | powershell.exe | POST | 200 | 141.8.193.27:80 | http://api-gate.xyz/api/v1/Client/Debug | unknown | html | 95 b | unknown |
1624 | powershell.exe | GET | 200 | 141.8.193.27:80 | http://api-gate.xyz/api/v1/Client/Token | unknown | html | 95 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1624 | powershell.exe | 141.8.193.27:80 | api-gate.xyz | Sprinthost.ru LLC | RU | unknown |
2520 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2520 | msedge.exe | 20.105.95.163:443 | nav-edge.smartscreen.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2520 | msedge.exe | 13.107.22.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2520 | msedge.exe | 188.114.96.3:443 | thebell.media | CLOUDFLARENET | NL | unknown |
2520 | msedge.exe | 172.67.220.17:443 | thebellmirror3.com | — | — | unknown |
568 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api-gate.xyz |
| malicious |
config.edge.skype.com |
| whitelisted |
nav-edge.smartscreen.microsoft.com |
| whitelisted |
thebell.media |
| unknown |
edge.microsoft.com |
| whitelisted |
thebellmirror3.com |
| unknown |
data-edge.smartscreen.microsoft.com |
| whitelisted |
yandex.ru |
| whitelisted |
platform.instagram.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1624 | powershell.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
1624 | powershell.exe | Malware Command and Control Activity Detected | SHELL [ANY.RUN] HTTP-Shell Multiplatform Reverse Shell Check-In |
1624 | powershell.exe | A Network Trojan was detected | ET MALWARE OrbitalBeam CnC Token Request |
1624 | powershell.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
1624 | powershell.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
1624 | powershell.exe | A Network Trojan was detected | ET MALWARE OrbitalBeam CnC Activity (Debug) |
1624 | powershell.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
1624 | powershell.exe | Malware Command and Control Activity Detected | SHELL [ANY.RUN] HTTP-Shell Multiplatform Reverse Shell Check-In |
1624 | powershell.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
1624 | powershell.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
Process | Message |
|---|---|
msedge.exe | [0112/085316.676:ERROR:exception_handler_server.cc(527)] ConnectNamedPipe: The pipe is being closed. (0xE8)
|