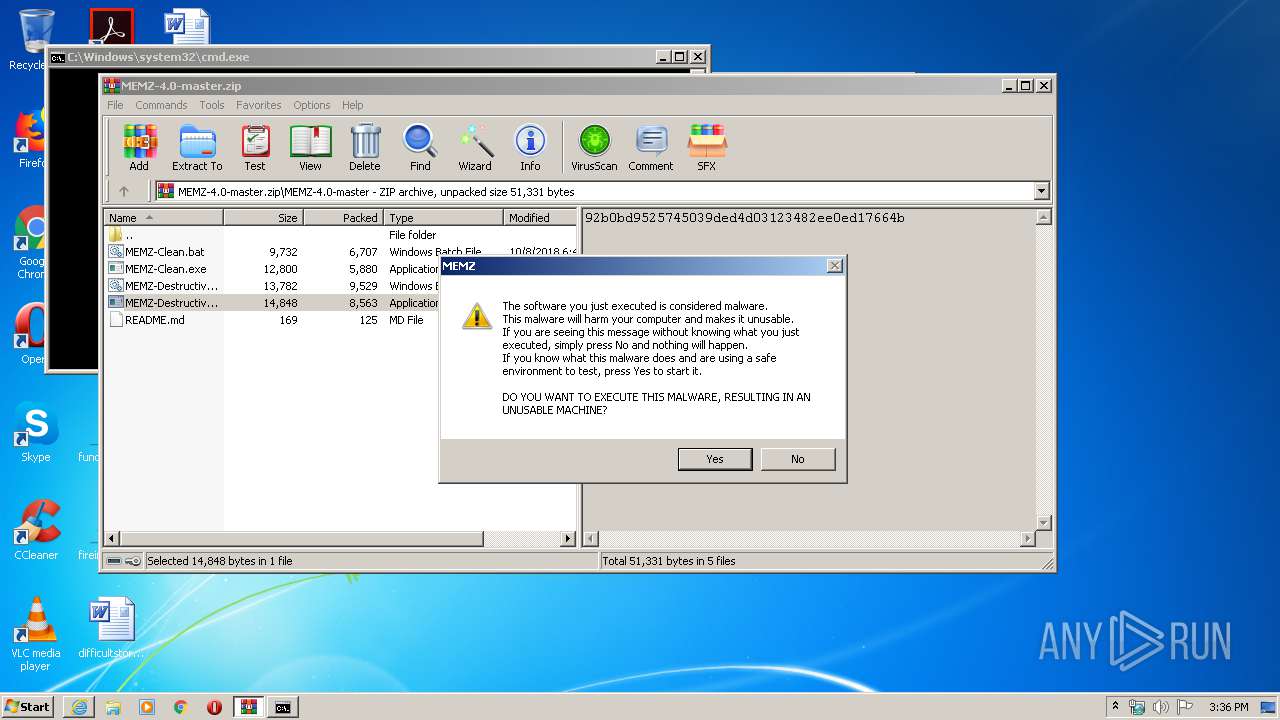
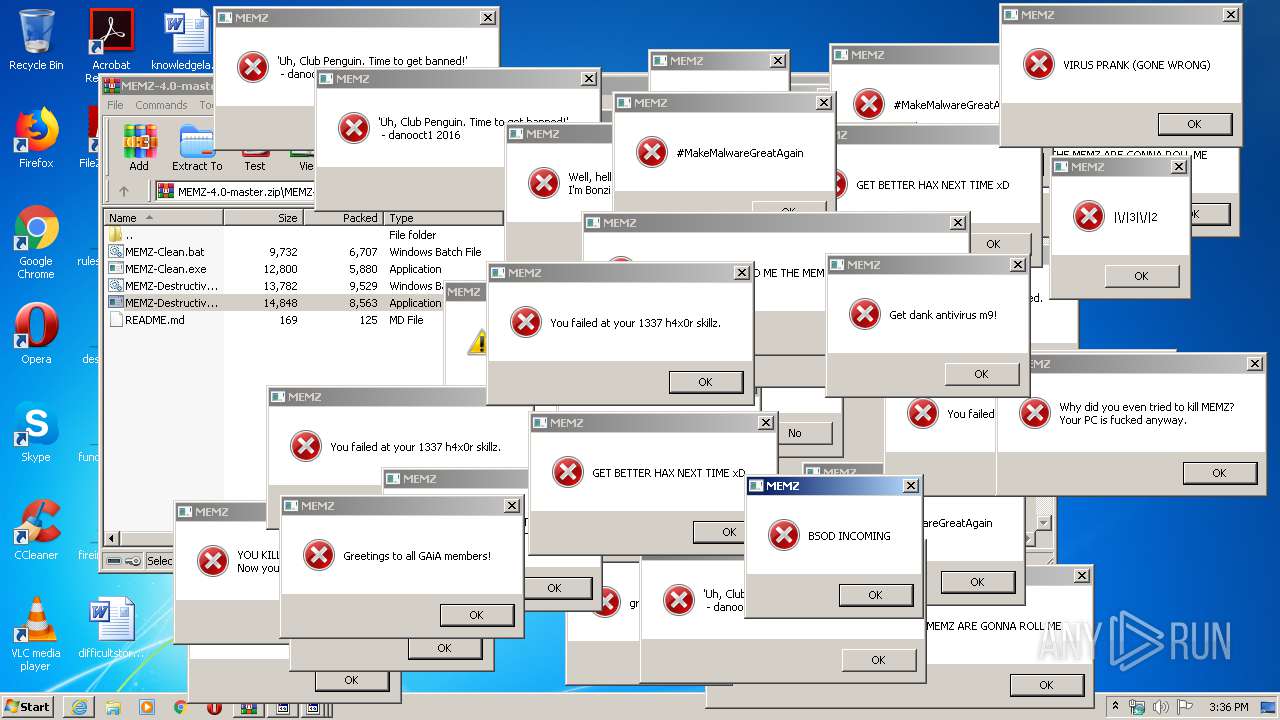
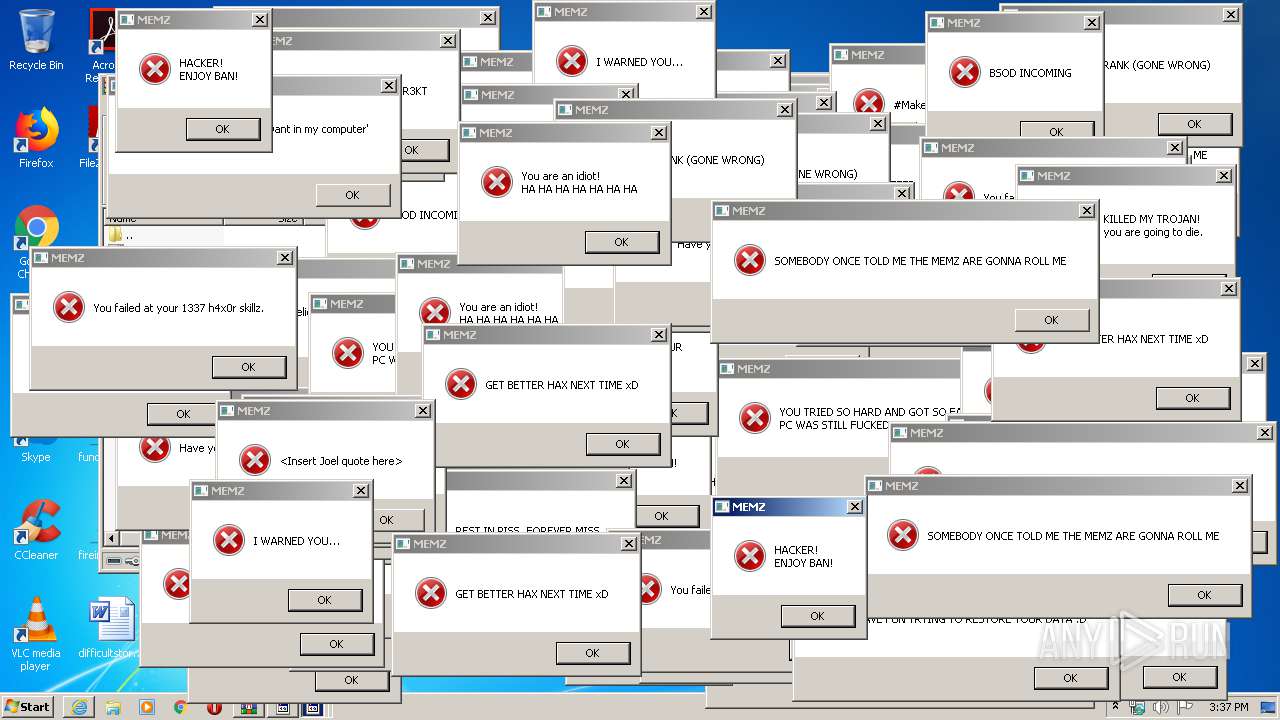
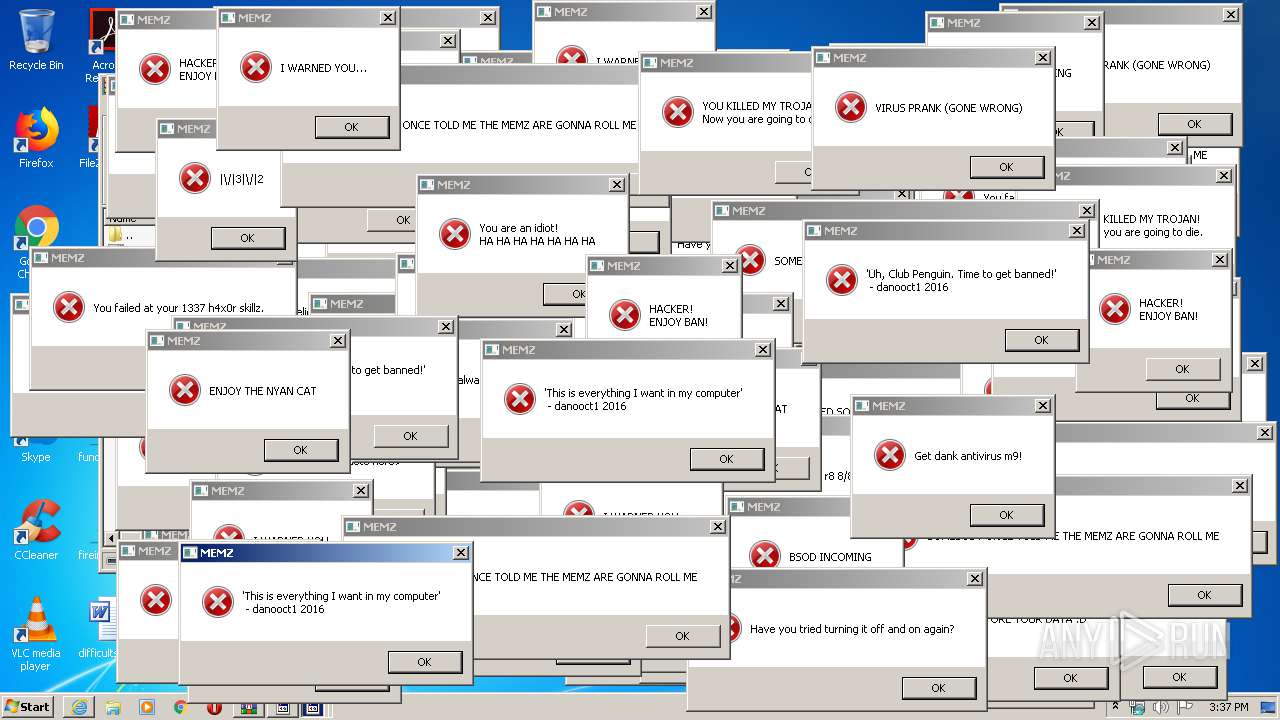
| URL: | https://github.com/OwO-Studio/MEMZ-4.0/archive/master.zip |
| Full analysis: | https://app.any.run/tasks/412e3113-9c90-4198-a77a-d7afc3e0f9e6 |
| Verdict: | Malicious activity |
| Analysis date: | May 19, 2020, 14:36:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 42DECB4F92B8BABD5CBDCCC5B9E9F4F3 |
| SHA1: | B8DE472A3D4E6180875A29EADA2AB63B9D1A05DD |
| SHA256: | C3F050C4ED10B45A23A5BB275F27D6A7D062E4665370674B5E220F303371C5EC |
| SSDEEP: | 3:N8tEdUI2gMFhKATJo:2uu1Fc2Jo |
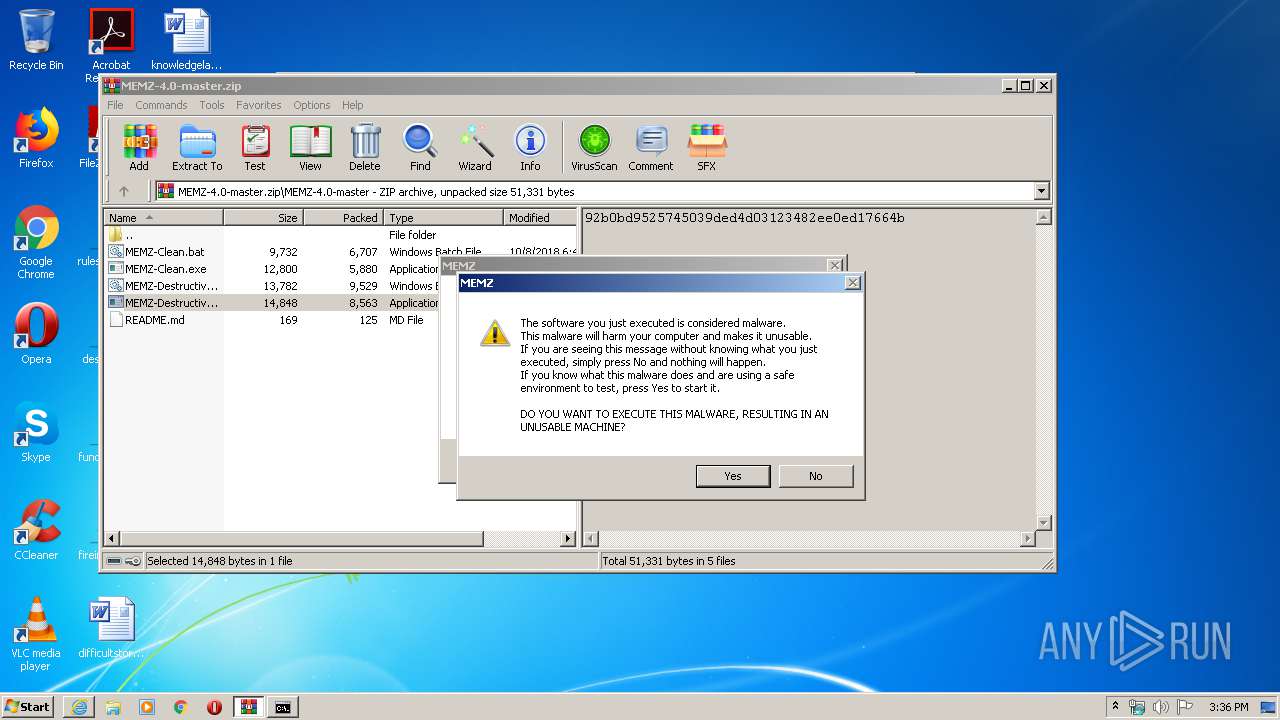
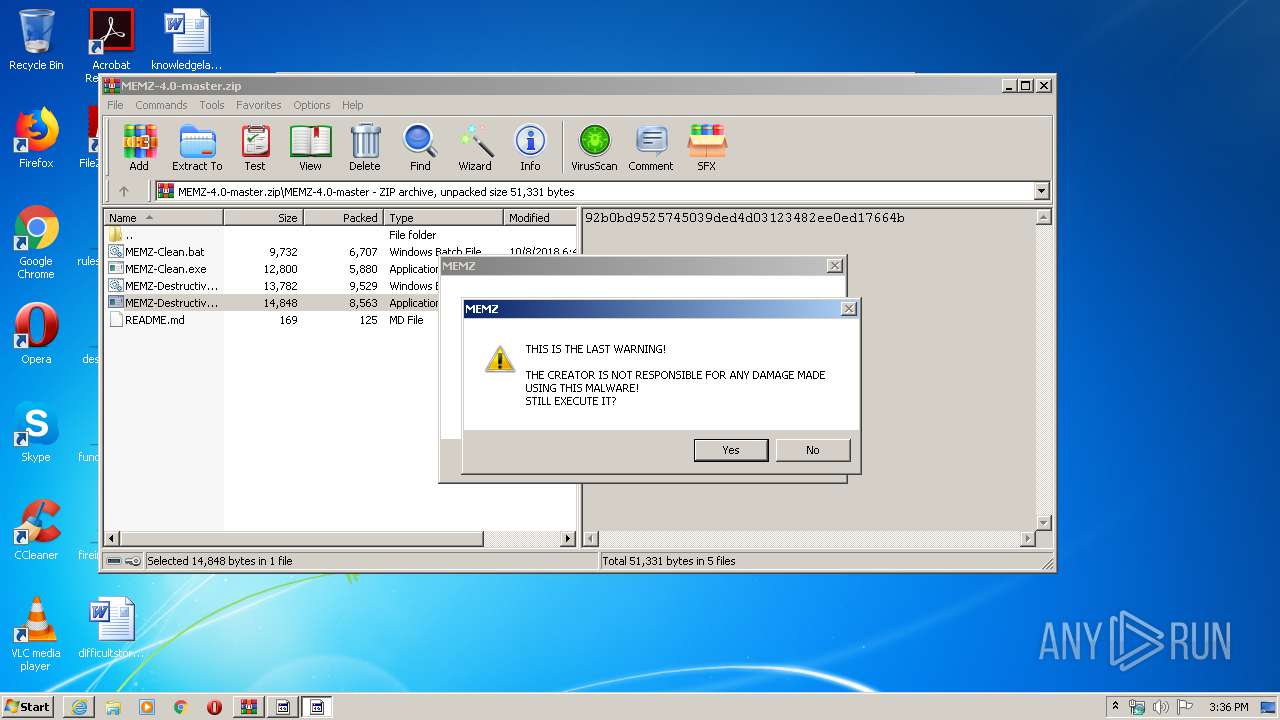
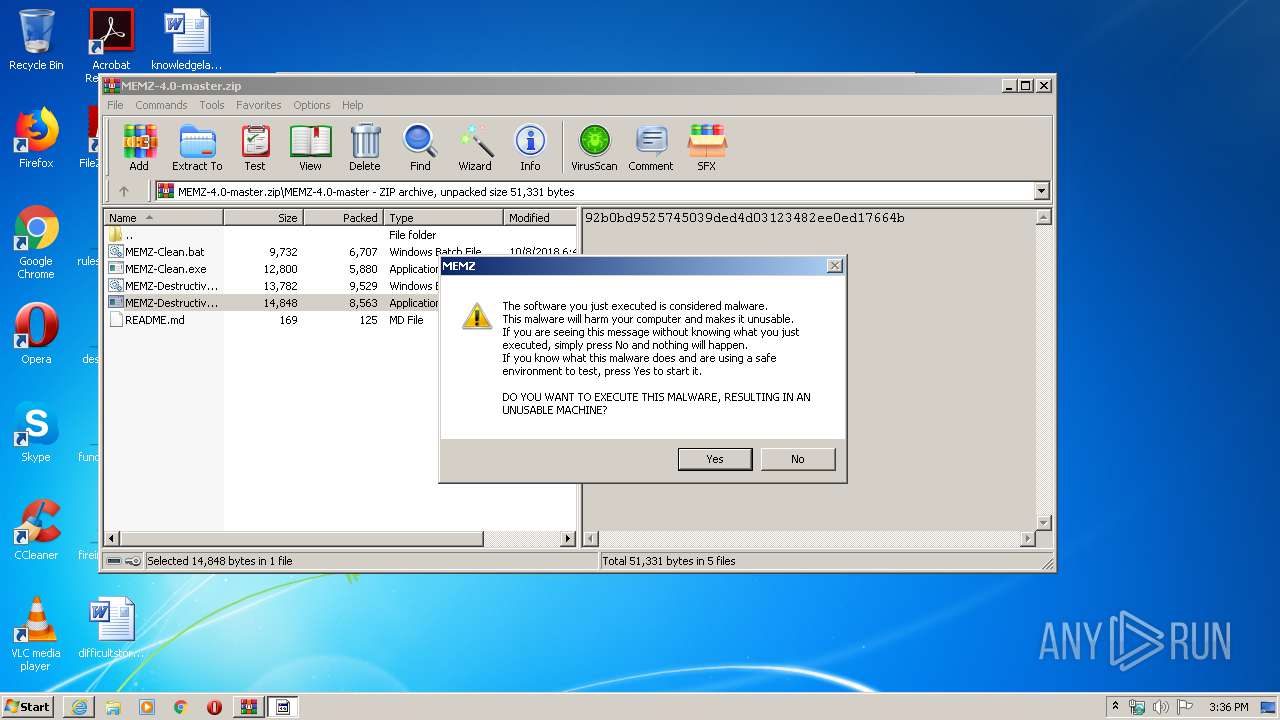
MALICIOUS
Application was dropped or rewritten from another process
- MEMZ.exe (PID: 3044)
- MEMZ.exe (PID: 3616)
- MEMZ.exe (PID: 2720)
- MEMZ-Destructive.exe (PID: 2280)
- MEMZ.exe (PID: 1432)
- MEMZ.exe (PID: 1392)
- MEMZ-Destructive.exe (PID: 3456)
- MEMZ.exe (PID: 3584)
- MEMZ.exe (PID: 3808)
- MEMZ.exe (PID: 576)
- MEMZ.exe (PID: 2932)
Low-level write access rights to disk partition
- MEMZ.exe (PID: 576)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3488)
- cscript.exe (PID: 2316)
Application launched itself
- MEMZ.exe (PID: 3616)
Low-level read access rights to disk partition
- MEMZ.exe (PID: 576)
Creates files in the user directory
- cscript.exe (PID: 2316)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 3488)
Executes scripts
- cmd.exe (PID: 2880)
INFO
Application launched itself
- iexplore.exe (PID: 2708)
Reads Internet Cache Settings
- iexplore.exe (PID: 2708)
- iexplore.exe (PID: 3648)
Changes internet zones settings
- iexplore.exe (PID: 2708)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2708)
Reads settings of System Certificates
- iexplore.exe (PID: 3648)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
62
Monitored processes
17
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 576 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /main | C:\Users\admin\AppData\Roaming\MEMZ.exe | MEMZ.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1073807364 Modules
| |||||||||||||||
| 1392 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1432 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
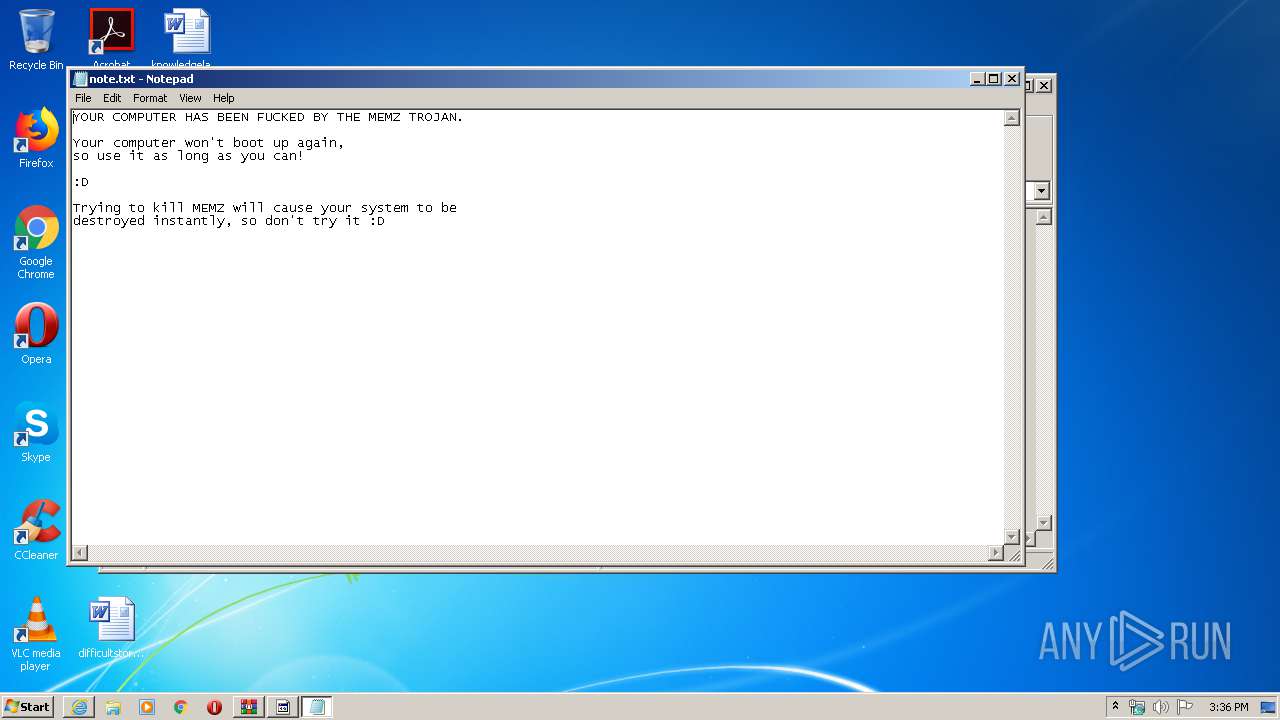
| 1708 | "C:\Windows\System32\notepad.exe" \note.txt | C:\Windows\System32\notepad.exe | — | MEMZ.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2280 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3488.33210\MEMZ-4.0-master\MEMZ-Destructive.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3488.33210\MEMZ-4.0-master\MEMZ-Destructive.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2316 | cscript x.js | C:\Windows\system32\cscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2708 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://github.com/OwO-Studio/MEMZ-4.0/archive/master.zip" | C:\Program Files\Internet Explorer\iexplore.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2720 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2880 | cmd /c ""C:\Users\admin\AppData\Local\Temp\Rar$DIa3488.32925\MEMZ-Destructive.bat" " | C:\Windows\system32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2932 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
2 186
Read events
2 087
Write events
99
Delete events
0
Modification events
| (PID) Process: | (2708) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 4021339496 | |||
| (PID) Process: | (2708) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30813674 | |||
| (PID) Process: | (2708) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2708) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2708) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2708) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2708) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2708) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2708) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2708) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
3
Suspicious files
13
Text files
74
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3648 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab8C12.tmp | — | |
MD5:— | SHA256:— | |||
| 3648 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar8C13.tmp | — | |
MD5:— | SHA256:— | |||
| 2708 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF7B45E620F94AE527.TMP | — | |
MD5:— | SHA256:— | |||
| 2708 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\MEMZ-4.0-master.zip.2h29jjr.partial:Zone.Identifier | — | |
MD5:— | SHA256:— | |||
| 3648 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EDC238BFF48A31D55A97E1E93892934B_C20E0DA2D0F89FE526E1490F4A2EE5AB | der | |
MD5:— | SHA256:— | |||
| 3648 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\35DDEDF268117918D1D277A171D8DF7B_B00CE8D5D4CF0E959CFDB61F636A135D | der | |
MD5:— | SHA256:— | |||
| 3648 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\35DDEDF268117918D1D277A171D8DF7B_B00CE8D5D4CF0E959CFDB61F636A135D | binary | |
MD5:— | SHA256:— | |||
| 3648 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\35DDEDF268117918D1D277A171D8DF7B_194FE46C1DB194819C88131C80396FC3 | der | |
MD5:— | SHA256:— | |||
| 3648 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\35DDEDF268117918D1D277A171D8DF7B_194FE46C1DB194819C88131C80396FC3 | binary | |
MD5:— | SHA256:— | |||
| 3648 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\MEMZ-4.0-master[1].zip | compressed | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
6
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3648 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | US | der | 471 b | whitelisted |
3648 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEAVXyAsoJoOhewoRRJMpa3k%3D | US | der | 471 b | whitelisted |
3648 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEAM3CrYov5jSu83hwnl9RjQ%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3648 | iexplore.exe | 140.82.113.9:443 | codeload.github.com | — | US | unknown |
3648 | iexplore.exe | 140.82.114.3:443 | github.com | — | US | suspicious |
3648 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
github.com |
| malicious |
ocsp.digicert.com |
| whitelisted |
codeload.github.com |
| whitelisted |