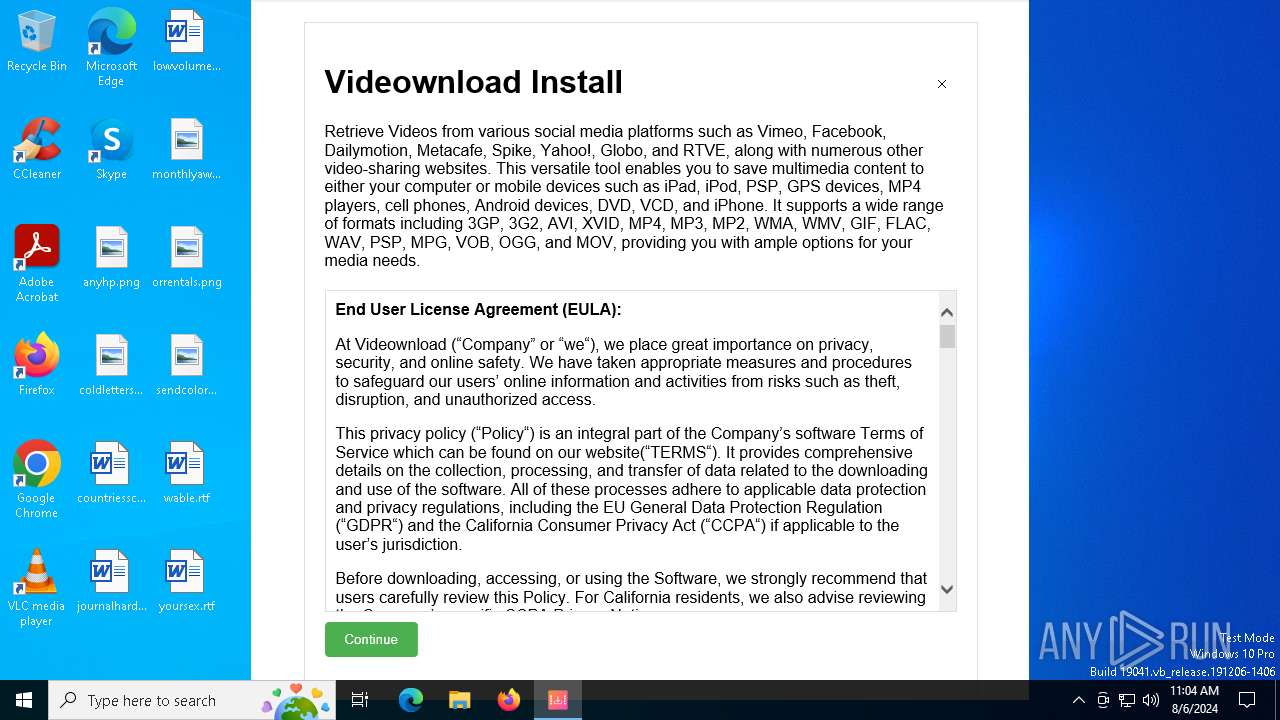
| File name: | VideoDownload.exe |
| Full analysis: | https://app.any.run/tasks/6bf79e3c-d68a-4803-9ce4-f9840f531487 |
| Verdict: | Malicious activity |
| Analysis date: | August 06, 2024, 11:04:29 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64 Mono/.Net assembly, for MS Windows |
| MD5: | E363405716E286A392FE6DF622B37C3E |
| SHA1: | E0BE8BB4D2A03BA4BFE86F6B3E1E8788FDB3942A |
| SHA256: | C3DA3E1C455E04CBDF0E10BEDD0A84549010ADF1A59ECA3081CDE4E7C1E5BE17 |
| SSDEEP: | 98304:8E6EQETEqaNpqRiFIs2LVI1kza8rlnFS3oQ1EIkrUxA1imX2/0wpjiDPcVlIWwG6:iyRXPMPeJ |
MALICIOUS
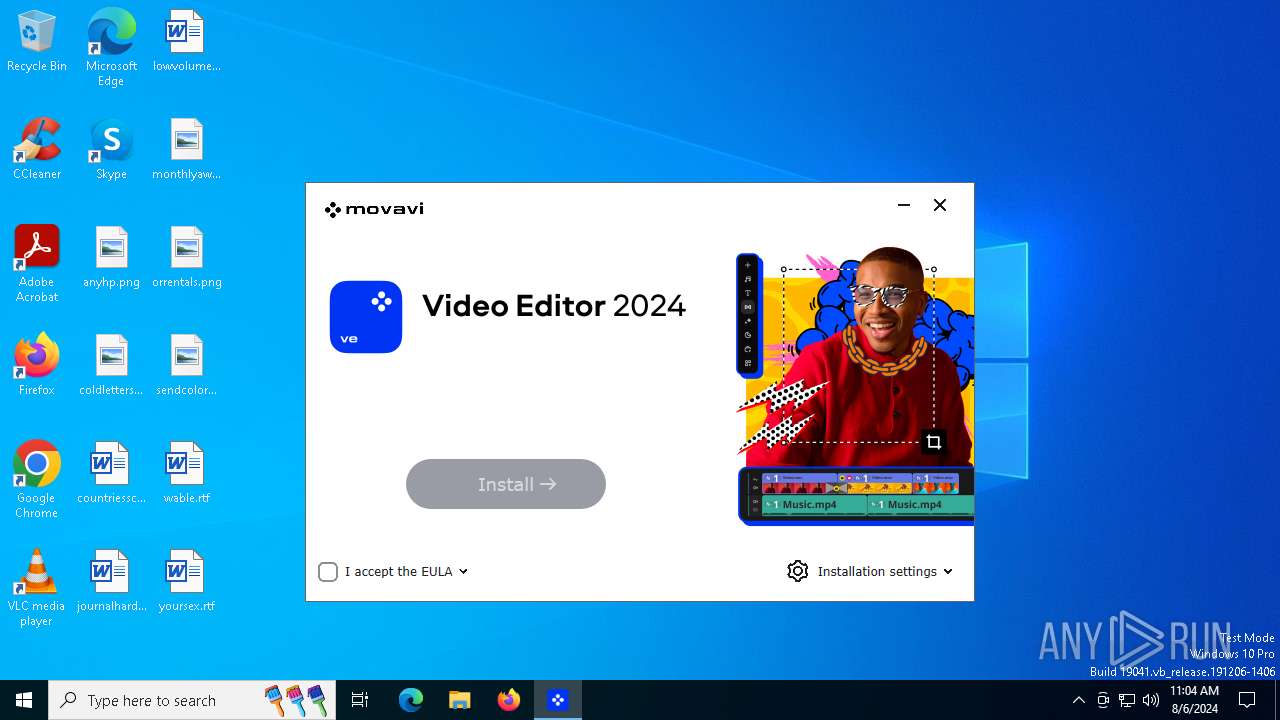
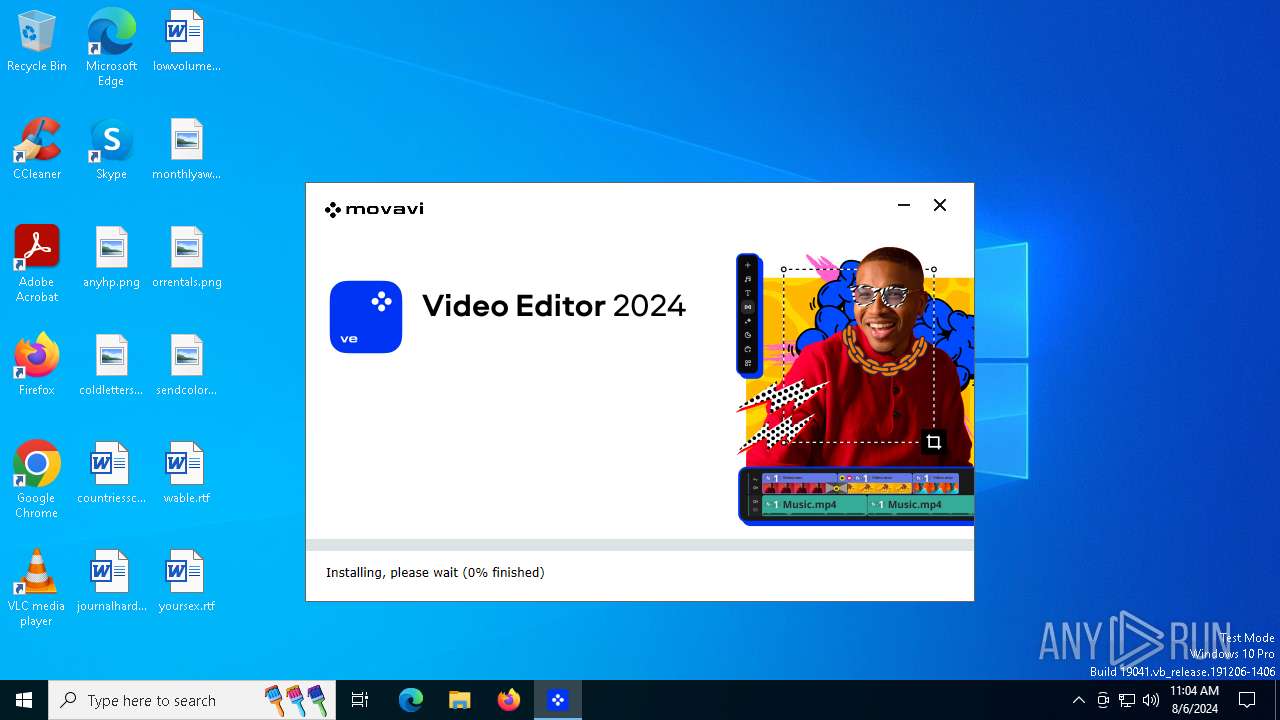
Drops the executable file immediately after the start
- VideoDownload.exe (PID: 6532)
- MovaviVideoEditorPlusSetupC_Wzz1gvo_.exe (PID: 6868)
- 1917697715_Wzz1gvo_.exe (PID: 7064)
- InstallerGUI.exe (PID: 5944)
Scans artifacts that could help determine the target
- VideoDownload.exe (PID: 6532)
SUSPICIOUS
Reads Microsoft Outlook installation path
- VideoDownload.exe (PID: 6532)
Reads security settings of Internet Explorer
- VideoDownload.exe (PID: 6532)
- installer.exe (PID: 6348)
Reads the date of Windows installation
- VideoDownload.exe (PID: 6532)
- installer.exe (PID: 6348)
Reads Internet Explorer settings
- VideoDownload.exe (PID: 6532)
Checks Windows Trust Settings
- VideoDownload.exe (PID: 6532)
Executable content was dropped or overwritten
- VideoDownload.exe (PID: 6532)
- MovaviVideoEditorPlusSetupC_Wzz1gvo_.exe (PID: 6868)
- 1917697715_Wzz1gvo_.exe (PID: 7064)
- InstallerGUI.exe (PID: 5944)
Process drops legitimate windows executable
- MovaviVideoEditorPlusSetupC_Wzz1gvo_.exe (PID: 6868)
- InstallerGUI.exe (PID: 5944)
- 1917697715_Wzz1gvo_.exe (PID: 7064)
The process creates files with name similar to system file names
- MovaviVideoEditorPlusSetupC_Wzz1gvo_.exe (PID: 6868)
- InstallerGUI.exe (PID: 5944)
- 1917697715_Wzz1gvo_.exe (PID: 7064)
Hides command output
- cmd.exe (PID: 1928)
Get information on the list of running processes
- installer.exe (PID: 6348)
- cmd.exe (PID: 1928)
Starts CMD.EXE for commands execution
- installer.exe (PID: 6348)
The process drops C-runtime libraries
- 1917697715_Wzz1gvo_.exe (PID: 7064)
- MovaviVideoEditorPlusSetupC_Wzz1gvo_.exe (PID: 6868)
- InstallerGUI.exe (PID: 5944)
Reads the BIOS version
- InstallerGUI.exe (PID: 5944)
INFO
Reads the computer name
- VideoDownload.exe (PID: 6532)
- installer.exe (PID: 6348)
- InstallerGUI.exe (PID: 5944)
- PluginChecker.exe (PID: 3140)
- PluginChecker.exe (PID: 6392)
- PluginChecker.exe (PID: 5904)
- PluginChecker.exe (PID: 5484)
- PluginChecker.exe (PID: 5760)
- PluginChecker.exe (PID: 5328)
- PluginChecker.exe (PID: 3360)
- PluginChecker.exe (PID: 2616)
- PluginChecker.exe (PID: 1568)
- PluginChecker.exe (PID: 6840)
- PluginChecker.exe (PID: 3672)
- PluginChecker.exe (PID: 7100)
- PluginChecker.exe (PID: 3508)
- PluginChecker.exe (PID: 3008)
- PluginChecker.exe (PID: 7008)
- PluginChecker.exe (PID: 4192)
- PluginChecker.exe (PID: 4276)
- PluginChecker.exe (PID: 4056)
- PluginChecker.exe (PID: 4308)
- PluginChecker.exe (PID: 5464)
- PluginChecker.exe (PID: 3324)
- PluginChecker.exe (PID: 3476)
- PluginChecker.exe (PID: 6056)
- PluginChecker.exe (PID: 3848)
- PluginChecker.exe (PID: 1664)
- PluginChecker.exe (PID: 5408)
- PluginChecker.exe (PID: 2272)
- PluginChecker.exe (PID: 7024)
- PluginChecker.exe (PID: 6472)
- PluginChecker.exe (PID: 3692)
- PluginChecker.exe (PID: 6948)
- CoreChecker.exe (PID: 5140)
- PluginChecker.exe (PID: 6964)
- CodecChecker.exe (PID: 6268)
- CodecChecker.exe (PID: 6916)
- CodecChecker.exe (PID: 3812)
- CodecChecker.exe (PID: 6172)
- CodecChecker.exe (PID: 6080)
- CodecChecker.exe (PID: 6548)
- CodecChecker.exe (PID: 3160)
- PluginChecker.exe (PID: 888)
- PluginChecker.exe (PID: 6976)
Process checks Internet Explorer phishing filters
- VideoDownload.exe (PID: 6532)
Checks supported languages
- VideoDownload.exe (PID: 6532)
- MovaviVideoEditorPlusSetupC_Wzz1gvo_.exe (PID: 6868)
- crashpad_handler.exe (PID: 6396)
- 1917697715_Wzz1gvo_.exe (PID: 7064)
- InstallerGUI.exe (PID: 5944)
- crashpad_handler.exe (PID: 6900)
- installer.exe (PID: 6348)
- CoreChecker.exe (PID: 5140)
- PluginChecker.exe (PID: 3140)
- PluginChecker.exe (PID: 3508)
- PluginChecker.exe (PID: 6392)
- PluginChecker.exe (PID: 5904)
- PluginChecker.exe (PID: 5484)
- PluginChecker.exe (PID: 5760)
- PluginChecker.exe (PID: 3360)
- PluginChecker.exe (PID: 5328)
- PluginChecker.exe (PID: 2616)
- PluginChecker.exe (PID: 6840)
- PluginChecker.exe (PID: 1568)
- PluginChecker.exe (PID: 3672)
- PluginChecker.exe (PID: 7100)
- PluginChecker.exe (PID: 6976)
- PluginChecker.exe (PID: 3008)
- PluginChecker.exe (PID: 4192)
- PluginChecker.exe (PID: 4056)
- PluginChecker.exe (PID: 3324)
- PluginChecker.exe (PID: 3848)
- PluginChecker.exe (PID: 4308)
- PluginChecker.exe (PID: 5464)
- PluginChecker.exe (PID: 3476)
- PluginChecker.exe (PID: 6056)
- PluginChecker.exe (PID: 888)
- PluginChecker.exe (PID: 1664)
- PluginChecker.exe (PID: 5408)
- PluginChecker.exe (PID: 2272)
- PluginChecker.exe (PID: 6472)
- PluginChecker.exe (PID: 7024)
- PluginChecker.exe (PID: 3692)
- PluginChecker.exe (PID: 6948)
- PluginChecker.exe (PID: 6964)
- CodecChecker.exe (PID: 6916)
- CodecChecker.exe (PID: 6268)
- CodecChecker.exe (PID: 3812)
- CodecChecker.exe (PID: 6172)
- CodecChecker.exe (PID: 6080)
- CodecChecker.exe (PID: 3160)
- PluginChecker.exe (PID: 7008)
- CodecChecker.exe (PID: 6548)
- PluginChecker.exe (PID: 4276)
Reads the machine GUID from the registry
- VideoDownload.exe (PID: 6532)
- installer.exe (PID: 6348)
- PluginChecker.exe (PID: 3672)
- CoreChecker.exe (PID: 5140)
- CodecChecker.exe (PID: 6172)
- CodecChecker.exe (PID: 6268)
- CodecChecker.exe (PID: 6916)
- CodecChecker.exe (PID: 3812)
- CodecChecker.exe (PID: 6548)
- CodecChecker.exe (PID: 3160)
- CodecChecker.exe (PID: 6080)
Checks proxy server information
- VideoDownload.exe (PID: 6532)
- installer.exe (PID: 6348)
- InstallerGUI.exe (PID: 5944)
Reads the software policy settings
- VideoDownload.exe (PID: 6532)
Create files in a temporary directory
- MovaviVideoEditorPlusSetupC_Wzz1gvo_.exe (PID: 6868)
- installer.exe (PID: 6348)
- 1917697715_Wzz1gvo_.exe (PID: 7064)
- InstallerGUI.exe (PID: 5944)
Creates files or folders in the user directory
- installer.exe (PID: 6348)
- crashpad_handler.exe (PID: 6396)
- VideoDownload.exe (PID: 6532)
- InstallerGUI.exe (PID: 5944)
- crashpad_handler.exe (PID: 6900)
- PluginChecker.exe (PID: 3140)
- PluginChecker.exe (PID: 6392)
- PluginChecker.exe (PID: 3508)
- PluginChecker.exe (PID: 5904)
- PluginChecker.exe (PID: 5484)
- PluginChecker.exe (PID: 5760)
- PluginChecker.exe (PID: 3360)
- PluginChecker.exe (PID: 2616)
- PluginChecker.exe (PID: 5328)
- PluginChecker.exe (PID: 1568)
- PluginChecker.exe (PID: 6840)
- PluginChecker.exe (PID: 3672)
- PluginChecker.exe (PID: 7100)
- PluginChecker.exe (PID: 3008)
- PluginChecker.exe (PID: 4192)
- PluginChecker.exe (PID: 6976)
- PluginChecker.exe (PID: 4276)
- PluginChecker.exe (PID: 4056)
- PluginChecker.exe (PID: 5464)
- PluginChecker.exe (PID: 3848)
- PluginChecker.exe (PID: 4308)
- PluginChecker.exe (PID: 3324)
- PluginChecker.exe (PID: 3476)
- PluginChecker.exe (PID: 1664)
- PluginChecker.exe (PID: 5408)
- PluginChecker.exe (PID: 6056)
- PluginChecker.exe (PID: 888)
- PluginChecker.exe (PID: 6472)
- PluginChecker.exe (PID: 2272)
- PluginChecker.exe (PID: 7024)
- PluginChecker.exe (PID: 3692)
- PluginChecker.exe (PID: 6964)
- PluginChecker.exe (PID: 6948)
- CoreChecker.exe (PID: 5140)
- CodecChecker.exe (PID: 6916)
- CodecChecker.exe (PID: 6268)
- CodecChecker.exe (PID: 6172)
- PluginChecker.exe (PID: 7008)
- CodecChecker.exe (PID: 3812)
- CodecChecker.exe (PID: 6080)
- CodecChecker.exe (PID: 6548)
- CodecChecker.exe (PID: 3160)
Reads Environment values
- installer.exe (PID: 6348)
- InstallerGUI.exe (PID: 5944)
Process checks computer location settings
- installer.exe (PID: 6348)
- VideoDownload.exe (PID: 6532)
Dropped object may contain TOR URL's
- 1917697715_Wzz1gvo_.exe (PID: 7064)
- InstallerGUI.exe (PID: 5944)
Creates files in the program directory
- InstallerGUI.exe (PID: 5944)
Reads CPU info
- CodecChecker.exe (PID: 6268)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2047:01:01 17:13:13+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 80 |
| CodeSize: | 5350912 |
| InitializedDataSize: | 117248 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x0000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | VideoDownload |
| FileVersion: | 1.0.0.0 |
| InternalName: | VideoDownload.exe |
| LegalCopyright: | Copyright © 2024 |
| LegalTrademarks: | - |
| OriginalFileName: | VideoDownload.exe |
| ProductName: | VideoDownload |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
226
Monitored processes
95
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | PluginChecker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 232 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | PluginChecker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 236 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | PluginChecker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 368 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | PluginChecker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 888 | "C:\Users\admin\AppData\Local\Temp\Movavi-installer-44814fc7-e5d7-48ea-8b3e-91ef617ae1ab\PluginChecker.exe" MuxerFF MuxerFactory | C:\Users\admin\AppData\Local\Temp\Movavi-installer-44814fc7-e5d7-48ea-8b3e-91ef617ae1ab\PluginChecker.exe | — | CoreChecker.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 904 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | PluginChecker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1020 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | PluginChecker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1236 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | CodecChecker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1568 | "C:\Users\admin\AppData\Local\Temp\Movavi-installer-44814fc7-e5d7-48ea-8b3e-91ef617ae1ab\PluginChecker.exe" DecoderMF CodecFactory | C:\Users\admin\AppData\Local\Temp\Movavi-installer-44814fc7-e5d7-48ea-8b3e-91ef617ae1ab\PluginChecker.exe | — | CoreChecker.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1636 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | CodecChecker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
42 150
Read events
42 116
Write events
32
Delete events
2
Modification events
| (PID) Process: | (6532) VideoDownload.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6532) VideoDownload.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6532) VideoDownload.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6532) VideoDownload.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6532) VideoDownload.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6532) VideoDownload.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6532) VideoDownload.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6532) VideoDownload.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFavoritesInitialSelection |
Value: | |||
| (PID) Process: | (6532) VideoDownload.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFeedsInitialSelection |
Value: | |||
| (PID) Process: | (6348) installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Movavi\User |
| Operation: | write | Name: | WEBUID |
Value: zz1gvo | |||
Executable files
526
Suspicious files
1 463
Text files
1 688
Unknown types
318
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6532 | VideoDownload.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:CABCADC4E1B5C3C63B2A53B8FE33391C | SHA256:BE37F7BCD4671FBABAEF8A2A7CC6ABEA85F16086D0B8BDFEE779F349A8069876 | |||
| 6532 | VideoDownload.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | der | |
MD5:7FB5FA1534DCF77F2125B2403B30A0EE | SHA256:33A39E9EC2133230533A686EC43760026E014A3828C703707ACBC150FE40FD6F | |||
| 6532 | VideoDownload.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B3513D73A177A2707D910183759B389B_5CF45833F44BFC2995315451A3896ACA | der | |
MD5:0FC32D2C8458C81E1437A74D239AE780 | SHA256:180DBF307BCA96685896E2DC23B962C912EBAAB5037FB58D61D1E5C8C61C68B3 | |||
| 6532 | VideoDownload.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\05DDC6AA91765AACACDB0A5F96DF8199 | der | |
MD5:E935BC5762068CAF3E24A2683B1B8A88 | SHA256:A8ACCFCFEB51BD73DF23B91F4D89FF1A9EB7438EF5B12E8AFDA1A6FF1769E89D | |||
| 6868 | MovaviVideoEditorPlusSetupC_Wzz1gvo_.exe | C:\Users\admin\AppData\Local\Temp\Movavi-installer-d4897fcd-8241-4aa7-b0b6-c43299595f24\InstallerData.7z | compressed | |
MD5:1E19ACEEBA8204DA1B6C0F2316746EB5 | SHA256:CD391CDEDE2BC9B415CD8E57A9184148B588B799A80947BDF7B0C3DEAFCF5E36 | |||
| 6532 | VideoDownload.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\email-decode.min[1].js | html | |
MD5:9E8F56E8E1806253BA01A95CFC3D392C | SHA256:2595496FE48DF6FCF9B1BC57C29A744C121EB4DD11566466BC13D2E52E6BBCC8 | |||
| 6532 | VideoDownload.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\font[1].eot | eot | |
MD5:C6B85601ADBF8C674B4B444DAD696A5D | SHA256:EC8671B432FF49E1E77F48692397E57ECFA584555AC664C932DCCEA0C9A16044 | |||
| 6868 | MovaviVideoEditorPlusSetupC_Wzz1gvo_.exe | C:\Users\admin\AppData\Local\Temp\Movavi-installer-d4897fcd-8241-4aa7-b0b6-c43299595f24\api-ms-win-core-console-l1-2-0.dll | executable | |
MD5:57193BFBCCEFE3D5DF8C1A0D27C4E8D4 | SHA256:F5025E74DE2C1C6EA74E475B57771AC32205E6F1FA6A0390298BBE1F4049AC5D | |||
| 6868 | MovaviVideoEditorPlusSetupC_Wzz1gvo_.exe | C:\Users\admin\AppData\Local\Temp\Movavi-installer-d4897fcd-8241-4aa7-b0b6-c43299595f24\api-ms-win-core-datetime-l1-1-0.dll | executable | |
MD5:557405C47613DE66B111D0E2B01F2FDB | SHA256:913EAAA7997A6AEE53574CFFB83F9C9C1700B1D8B46744A5E12D76A1E53376FD | |||
| 6532 | VideoDownload.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\css2[1].css | text | |
MD5:593563DEFDA42F8FAD22F5EA3F89B775 | SHA256:2F02D38536746DAE6535E3354B5B844C48C26589AE1B499BE5CB35EF66EAB511 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
75
DNS requests
27
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6532 | VideoDownload.exe | GET | 200 | 142.250.185.67:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
4592 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6532 | VideoDownload.exe | GET | 200 | 142.250.185.67:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
6532 | VideoDownload.exe | GET | 200 | 142.250.184.195:80 | http://o.pki.goog/wr2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEQCjHbN8Q48ByBJsBZfEZOeO | unknown | — | — | whitelisted |
6532 | VideoDownload.exe | GET | 200 | 142.250.185.67:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
2656 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
6532 | VideoDownload.exe | GET | 200 | 142.250.184.195:80 | http://o.pki.goog/wr2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEQDAezvzBOn2FxIghPLaMkP6 | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6980 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5796 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3068 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6532 | VideoDownload.exe | 188.114.97.3:443 | pixel.videownload.com | CLOUDFLARENET | NL | unknown |
6532 | VideoDownload.exe | 142.250.185.67:80 | c.pki.goog | GOOGLE | US | whitelisted |
6532 | VideoDownload.exe | 142.250.185.202:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
6532 | VideoDownload.exe | 142.250.184.195:80 | o.pki.goog | GOOGLE | US | whitelisted |
6532 | VideoDownload.exe | 142.250.184.227:443 | fonts.gstatic.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
pixel.videownload.com |
| unknown |
c.pki.goog |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
o.pki.goog |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
Process | Message |
|---|---|
installer.exe | E0806 11:04:46.067047 6332 WebUidManager.cpp:66] Can't find WebUid by RegistryKey. Key: User, error: Cannot read string from registry. Return empty.
|
installer.exe | E0806 11:04:46.067047 6332 WebUidManager.cpp:66] Can't find WebUid by RegistryKey. Key: VideoEditorPlus24, error: Cannot read string from registry. Return empty.
|
PluginChecker.exe | qt.qpa.gl: QWindowsIntegration::createPlatformOpenGLContext QSurfaceFormat(version 4.6, options QFlags<QSurfaceFormat::FormatOption>(DeprecatedFunctions), depthBufferSize -1, redBufferSize -1, greenBufferSize -1, blueBufferSize -1, alphaBufferSize -1, stencilBufferSize -1, samples -1, swapBehavior QSurfaceFormat::DefaultSwapBehavior, swapInterval 1, colorSpace QSurfaceFormat::DefaultColorSpace, profile QSurfaceFormat::CompatibilityProfile)
|
PluginChecker.exe | qt.qpa.gl: Qt: Using WGL and OpenGL from "opengl32.dll"
|
PluginChecker.exe | qt.qpa.gl: QOpenGLStaticContext::create OpenGL: "Microsoft Corporation","GDI Generic" default ContextFormat: v1.1 profile: QSurfaceFormat::NoProfile options: QFlags<QSurfaceFormat::FormatOption>(DeprecatedFunctions)
Extensions: 3
|
PluginChecker.exe | qt.qpa.gl: GPU features: QSet()
|
PluginChecker.exe | qt.qpa.gl: QWindowsOpenGLTester::supportedRenderers GpuDescription(vendorId=0x1414, deviceId=0x8c, subSysId=0x0, revision=0, driver: "d3d10warp.dll", version=10.0.19041.3636, "Microsoft Basic Render Driver""") 1 renderer: QFlags(0x1|0x2|0x4|0x8|0x20)
|
PluginChecker.exe | qt.qpa.gl: QWindowsGLContext::QWindowsGLContext 0x1fc7d372290 GDI requested: QSurfaceFormat(version 4.6, options QFlags<QSurfaceFormat::FormatOption>(DeprecatedFunctions), depthBufferSize -1, redBufferSize -1, greenBufferSize -1, blueBufferSize -1, alphaBufferSize -1, stencilBufferSize -1, samples -1, swapBehavior QSurfaceFormat::DefaultSwapBehavior, swapInterval 1, colorSpace QSurfaceFormat::DefaultColorSpace, profile QSurfaceFormat::CompatibilityProfile)
obtained # 7 GDI QSurfaceFormat(version 1.1, options QFlags<QSurfaceFormat::FormatOption>(DeprecatedFunctions), depthBufferSize 32, redBufferSize 8, greenBufferSize 8, blueBufferSize 8, alphaBufferSize 8, stencilBufferSize 8, samples -1, swapBehavior QSurfaceFormat::DoubleBuffer, swapInterval 1, colorSpace QSurfaceFormat::DefaultColorSpace, profile QSurfaceFormat::NoProfile)
PIXELFORMATDESCRIPTOR dwFlags=0x8465 PFD_DRAW_TO_WINDOW PFD_SUPPORT_OPENGL PFD_SUPPORT_COMPOSITION PFD_GENERIC_FORMAT PFD_DOUBLEBUFFER iPixelType=0 cColorBits=32 cRedBits=8 cRedShift=16 cGreenBits=8 cGreenShift=8 cBlueBits=8 cBlueShift=0 cDepthBits=32 cStencilBits=8 iLayerType=0 cAlphaBits=8 cAlphaShift=0 cAccumBits=64 cAccumRedBits=16 cAccumGreenBits=16 cAccumBlueBits=16 cAccumAlphaBits=16 swap interval: -1
default: ContextFormat: v1.1 profile: QSurfaceFormat::NoProfile options: QFlags<QSurfaceFormat::FormatOption>(DeprecatedFunctions)
HGLRC= 0x20000
|