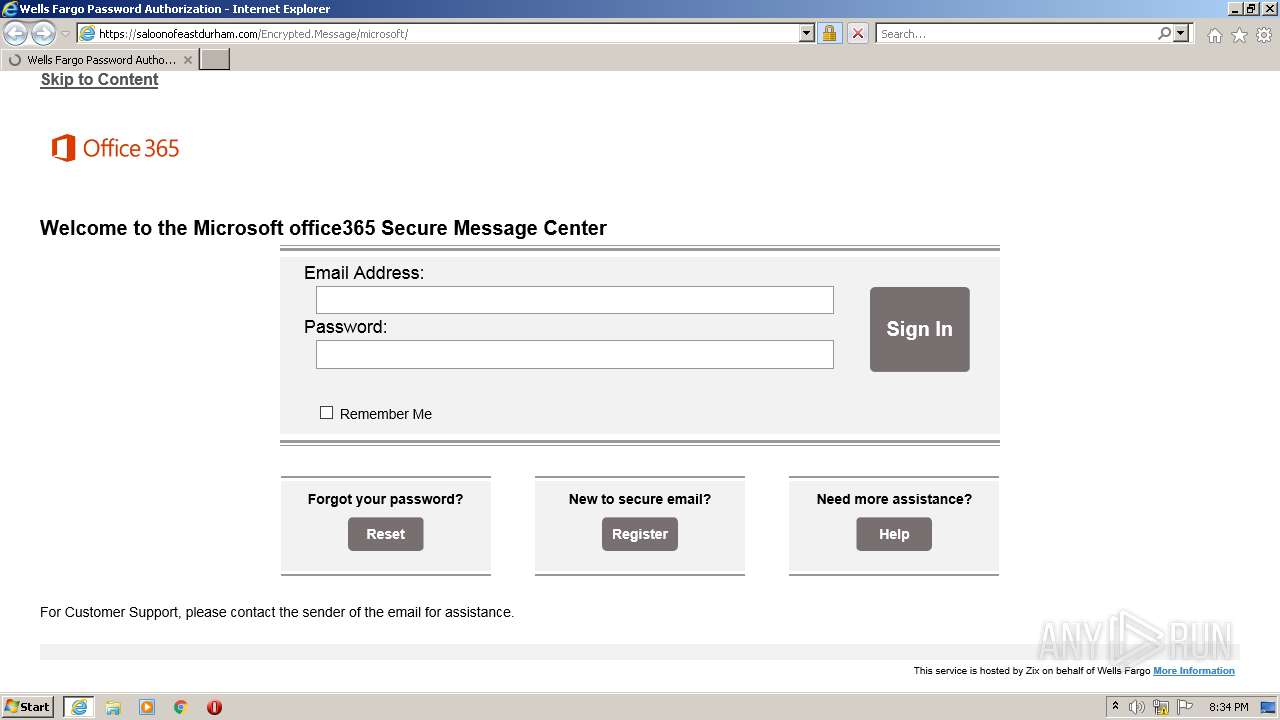
| URL: | https://saloonofeastdurham.com/Encrypted.Message/microsoft/ |
| Full analysis: | https://app.any.run/tasks/9b889b3e-27bc-4e3f-b166-ad9555262e51 |
| Verdict: | Malicious activity |
| Analysis date: | January 14, 2022, 20:33:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 2383A3D72FFC92DD0BCE66CDD7C2FC0C |
| SHA1: | FDABA2CA3141251104136A6871523319EE59FB47 |
| SHA256: | C3D8D7580D5AC8D708741ABAD0A5E7CF3C698A314AAE5E795C43436930F02EA3 |
| SSDEEP: | 3:N8JEK8ACx3pMEbWTHdYsn:2qHZ91sn |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3704)
INFO
Checks supported languages
- iexplore.exe (PID: 2256)
- iexplore.exe (PID: 3704)
Reads the computer name
- iexplore.exe (PID: 2256)
- iexplore.exe (PID: 3704)
Changes internet zones settings
- iexplore.exe (PID: 2256)
Application launched itself
- iexplore.exe (PID: 2256)
Checks Windows Trust Settings
- iexplore.exe (PID: 2256)
- iexplore.exe (PID: 3704)
Reads settings of System Certificates
- iexplore.exe (PID: 2256)
- iexplore.exe (PID: 3704)
Reads internet explorer settings
- iexplore.exe (PID: 3704)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
36
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2256 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://saloonofeastdurham.com/Encrypted.Message/microsoft/" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3704 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2256 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
11 535
Read events
11 420
Write events
115
Delete events
0
Modification events
| (PID) Process: | (2256) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2256) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 274572720 | |||
| (PID) Process: | (2256) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30935430 | |||
| (PID) Process: | (2256) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 574737720 | |||
| (PID) Process: | (2256) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30935430 | |||
| (PID) Process: | (2256) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2256) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2256) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2256) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2256) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
8
Text files
6
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2256 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2256 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:— | SHA256:— | |||
| 2256 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:— | SHA256:— | |||
| 3704 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:— | SHA256:— | |||
| 3704 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\microsoft[1].htm | text | |
MD5:— | SHA256:— | |||
| 2256 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 2256 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | der | |
MD5:— | SHA256:— | |||
| 2256 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:— | SHA256:— | |||
| 2256 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 2256 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
45
DNS requests
23
Threats
24
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2256 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
2256 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
3704 | iexplore.exe | GET | 200 | 67.26.81.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?4a60cee1206ff0b1 | US | compressed | 59.9 Kb | whitelisted |
2256 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?0b79f5cc38430cd1 | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2256 | iexplore.exe | 13.107.21.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3704 | iexplore.exe | 69.49.231.110:443 | saloonofeastdurham.com | Ecommerce Corporation | US | unknown |
3704 | iexplore.exe | 104.89.32.83:80 | x1.c.lencr.org | Akamai Technologies, Inc. | NL | suspicious |
2256 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2256 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3704 | iexplore.exe | 67.26.81.254:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
3704 | iexplore.exe | 199.30.236.209:443 | securemail.wf.com | Zix Corporation | US | suspicious |
2256 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
— | — | 199.30.236.209:443 | securemail.wf.com | Zix Corporation | US | suspicious |
2256 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
saloonofeastdurham.com |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
securemail.wf.com |
| suspicious |
r20swj13mr.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3704 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3704 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3704 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3704 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3704 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3704 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3704 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3704 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3704 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3704 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |