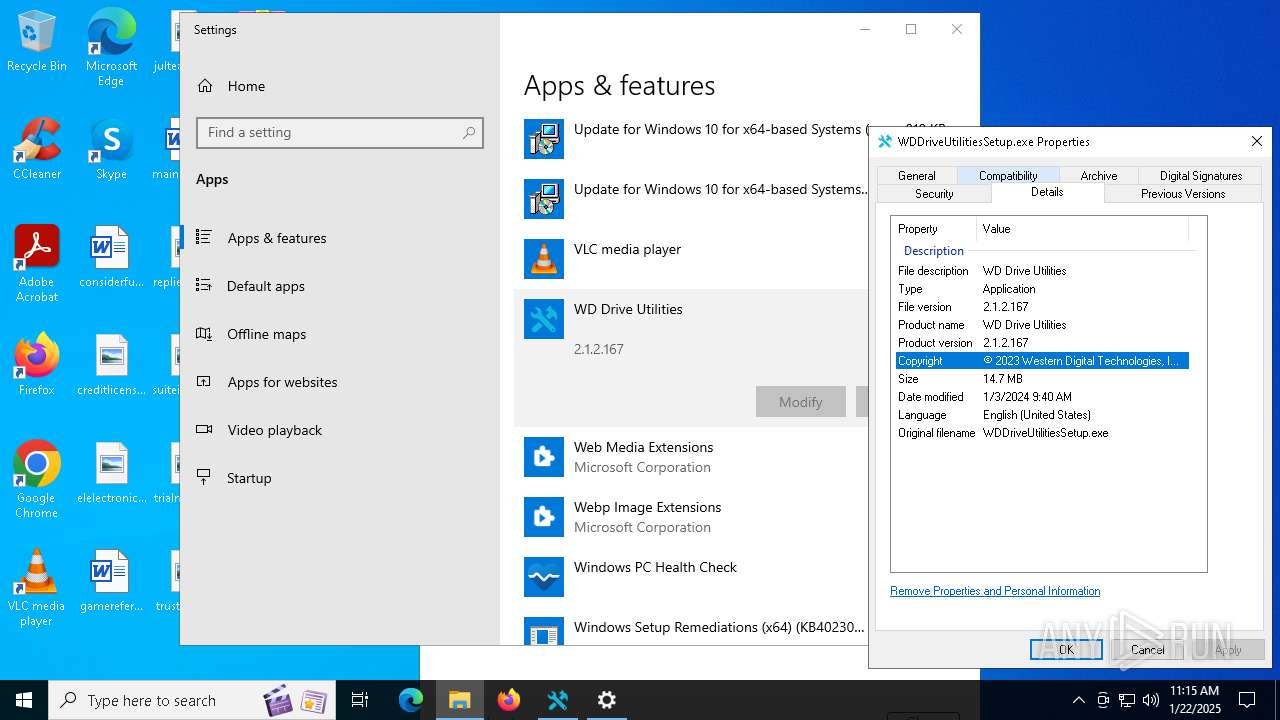
| download: | /wdapp/WDDriveUtilities_WIN.zip |
| Full analysis: | https://app.any.run/tasks/6b6175e1-fa99-448f-88e6-a6b1838d947e |
| Verdict: | Malicious activity |
| Analysis date: | January 22, 2025, 11:13:29 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 6065A8CBA1F6B928355A7114DDA02A2A |
| SHA1: | 9AC156D6E86E762C62FA67A5B56BB1C0046CBC89 |
| SHA256: | C3BB08F6D3602336F89913B84943815A0581A2D6DB0A19367A4EA2C80E6440F3 |
| SSDEEP: | 98304:Y/ubrfj5VttZn2kObZDdrzb5GtJH02vw6FrEuSTlQo2mYn3WId7l5972hizvOJQZ:BdZ3zYxzXrmVif16uFfLOJeT8M2r1 |
MALICIOUS
Changes the autorun value in the registry
- WDDriveUtilitiesSetup.exe (PID: 6880)
SUSPICIOUS
Executable content was dropped or overwritten
- WDDriveUtilitiesSetup.exe (PID: 6692)
- WDDriveUtilitiesSetup.exe (PID: 6720)
- WDDriveUtilitiesSetup.exe (PID: 6880)
The process creates files with name similar to system file names
- WDDriveUtilitiesSetup.exe (PID: 6720)
Reads security settings of Internet Explorer
- WDDriveUtilitiesSetup.exe (PID: 6720)
Starts itself from another location
- WDDriveUtilitiesSetup.exe (PID: 6720)
Creates a software uninstall entry
- WDDriveUtilitiesSetup.exe (PID: 6880)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6948)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 6948)
Searches for installed software
- WDDriveUtilitiesSetup.exe (PID: 6720)
Process drops legitimate windows executable
- msiexec.exe (PID: 6948)
There is functionality for taking screenshot (YARA)
- WDDriveUtilitiesSetup.exe (PID: 6720)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 6948)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4548)
- msiexec.exe (PID: 6948)
The process uses the downloaded file
- WinRAR.exe (PID: 4548)
- WDDriveUtilitiesSetup.exe (PID: 6720)
The sample compiled with english language support
- WinRAR.exe (PID: 4548)
- WDDriveUtilitiesSetup.exe (PID: 6692)
- WDDriveUtilitiesSetup.exe (PID: 6720)
- WDDriveUtilitiesSetup.exe (PID: 6880)
- msiexec.exe (PID: 6948)
Manual execution by a user
- WDDriveUtilitiesSetup.exe (PID: 6692)
Checks supported languages
- WDDriveUtilitiesSetup.exe (PID: 6692)
- WDDriveUtilitiesSetup.exe (PID: 6720)
- msiexec.exe (PID: 6948)
- msiexec.exe (PID: 7008)
- WDDriveUtilitiesSetup.exe (PID: 6880)
- MSIC633.tmp (PID: 5872)
- MSIC7AC.tmp (PID: 4944)
- MSIC6F0.tmp (PID: 4132)
- MSIC925.tmp (PID: 4444)
- MSIC9D2.tmp (PID: 6248)
- MSICC56.tmp (PID: 6240)
- MSICBB9.tmp (PID: 6268)
Create files in a temporary directory
- WDDriveUtilitiesSetup.exe (PID: 6692)
- WDDriveUtilitiesSetup.exe (PID: 6720)
- WDDriveUtilitiesSetup.exe (PID: 6880)
Reads the computer name
- WDDriveUtilitiesSetup.exe (PID: 6720)
- WDDriveUtilitiesSetup.exe (PID: 6880)
- msiexec.exe (PID: 6948)
- msiexec.exe (PID: 7008)
Reads the machine GUID from the registry
- WDDriveUtilitiesSetup.exe (PID: 6720)
- WDDriveUtilitiesSetup.exe (PID: 6880)
- MSIC7AC.tmp (PID: 4944)
- MSIC633.tmp (PID: 5872)
- MSIC6F0.tmp (PID: 4132)
- MSIC869.tmp (PID: 836)
- MSIC925.tmp (PID: 4444)
- MSIC9D2.tmp (PID: 6248)
Process checks computer location settings
- WDDriveUtilitiesSetup.exe (PID: 6720)
Creates files in the program directory
- WDDriveUtilitiesSetup.exe (PID: 6880)
Reads the software policy settings
- MSIC6F0.tmp (PID: 4132)
- MSIC7AC.tmp (PID: 4944)
- MSIC925.tmp (PID: 4444)
- MSIC633.tmp (PID: 5872)
- MSIC9D2.tmp (PID: 6248)
The sample compiled with arabic language support
- msiexec.exe (PID: 6948)
Starts application with an unusual extension
- msiexec.exe (PID: 6948)
Displays MAC addresses of computer network adapters
- getmac.exe (PID: 3988)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:01:03 09:40:18 |
| ZipCRC: | 0x9cce45ac |
| ZipCompressedSize: | 131 |
| ZipUncompressedSize: | 200 |
| ZipFileName: | manifest.json |
Total processes
159
Monitored processes
24
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 836 | "C:\WINDOWS\Installer\MSIC869.tmp" /U "C:\Program Files (x86)\Western Digital\WDCSAM_1.0.9.0\wdcsam.inf" /SW /D | C:\Windows\Installer\MSIC869.tmp | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Driver Package Installer Exit code: 2147483648 Version: 2.1 Modules
| |||||||||||||||
| 3808 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | getmac.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 3988 | "getmac" | C:\Windows\SysWOW64\getmac.exe | — | WDDriveUtilities.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Displays NIC MAC information Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 4132 | "C:\WINDOWS\Installer\MSIC6F0.tmp" /U "C:\Program Files (x86)\Western Digital\WDCSAM_prev\wdcsam.inf" /SW /D | C:\Windows\Installer\MSIC6F0.tmp | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Driver Package Installer Exit code: 2147483648 Version: 2.1 Modules
| |||||||||||||||
| 4136 | "C:\WINDOWS\Installer\MSICA9E.tmp" /U "C:\Program Files (x86)\Western Digital\WDCSAM_1.0.7.1\wdcsam.inf" /SW /D | C:\Windows\Installer\MSICA9E.tmp | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Driver Package Installer Exit code: 2147483648 Version: 2.1 Modules
| |||||||||||||||
| 4444 | "C:\WINDOWS\Installer\MSIC925.tmp" /U "C:\Program Files (x86)\Western Digital\WDCSAM_1.0.8.0\wdcsam.inf" /SW /D | C:\Windows\Installer\MSIC925.tmp | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Driver Package Installer Exit code: 2147483648 Version: 2.1 Modules
| |||||||||||||||
| 4548 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\WDDriveUtilities_WIN.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4944 | "C:\WINDOWS\Installer\MSIC7AC.tmp" /U "C:\Program Files (x86)\Western Digital\WDCSAM_1.1.0.0\wdcsam.inf" /SW /D | C:\Windows\Installer\MSIC7AC.tmp | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Driver Package Installer Exit code: 2147483648 Version: 2.1 Modules
| |||||||||||||||
| 5872 | "C:\WINDOWS\Installer\MSIC633.tmp" /U "C:\Program Files (x86)\Western Digital\WDCSAM\wdcsam.inf" /SW /D | C:\Windows\Installer\MSIC633.tmp | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Driver Package Installer Exit code: 2147483648 Version: 2.1 Modules
| |||||||||||||||
| 6220 | cmd.exe /c "del drivers\wdcsam64.sys" | C:\Windows\System32\cmd.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
25 747
Read events
25 019
Write events
726
Delete events
2
Modification events
| (PID) Process: | (4548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\WDDriveUtilities_WIN.zip | |||
| (PID) Process: | (4548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (4548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
219
Suspicious files
28
Text files
291
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4548 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4548.24515\WDDriveUtilitiesSetup.exe | executable | |
MD5:50BD1511D22BAB0165908E61C747B6D5 | SHA256:9BCDF9D04632A71F264294760D0B4269CF70E91A78C9E9F56BBB8B72098F86D5 | |||
| 6720 | WDDriveUtilitiesSetup.exe | C:\Users\admin\AppData\Local\Temp\{E652D2F1-8DA7-40E9-8878-F36CDEDAB133}\.ba\1036\mbapreq.wxl | xml | |
MD5:AA32A059AADD42431F7837CB1BE7257F | SHA256:88E7DDACD6B714D94D5322876BD50051479B7A0C686DC2E9EB06B3B7A0BC06C9 | |||
| 6720 | WDDriveUtilitiesSetup.exe | C:\Users\admin\AppData\Local\Temp\{E652D2F1-8DA7-40E9-8878-F36CDEDAB133}\.ba\1041\mbapreq.wxl | xml | |
MD5:DB0F5BAB42403FD67C0A18E35E6880EC | SHA256:CCDCDB111EFA152C5F9FF4930033698B843390A549699AE802098D87431F16FE | |||
| 6720 | WDDriveUtilitiesSetup.exe | C:\Users\admin\AppData\Local\Temp\{E652D2F1-8DA7-40E9-8878-F36CDEDAB133}\.ba\1032\mbapreq.wxl | xml | |
MD5:074D5921AF07E6126049CB45814246ED | SHA256:B8E90E20EDF110AAAAEA54FBC8533872831777BE5589E380CFDD17E1F93147B5 | |||
| 6720 | WDDriveUtilitiesSetup.exe | C:\Users\admin\AppData\Local\Temp\{E652D2F1-8DA7-40E9-8878-F36CDEDAB133}\.ba\1030\mbapreq.wxl | xml | |
MD5:7C6E4CE87870B3B5E71D3EF4555500F8 | SHA256:CAC263E0E90A4087446A290055257B1C39F17E11F065598CB2286DF4332C7696 | |||
| 6720 | WDDriveUtilitiesSetup.exe | C:\Users\admin\AppData\Local\Temp\{E652D2F1-8DA7-40E9-8878-F36CDEDAB133}\.ba\BootstrapperCore.dll | executable | |
MD5:B0D10A2A622A322788780E7A3CBB85F3 | SHA256:F2C2B3CE2DF70A3206F3111391FFC7B791B32505FA97AEF22C0C2DBF6F3B0426 | |||
| 6692 | WDDriveUtilitiesSetup.exe | C:\Users\admin\AppData\Local\Temp\{CE66B742-1D7E-4DF4-8F27-6D92FB1B9AC6}\.cr\WDDriveUtilitiesSetup.exe | executable | |
MD5:573901EC7A0DAEC97A1F26EAE15AA515 | SHA256:B85B7516B8A6B80CB7E1EE90D60E05839F9D792100B8E958F7DE6788CCDDFEEA | |||
| 6720 | WDDriveUtilitiesSetup.exe | C:\Users\admin\AppData\Local\Temp\{E652D2F1-8DA7-40E9-8878-F36CDEDAB133}\.ba\mbapreq.wxl | xml | |
MD5:4D2C8D10C5DCCA6B938B71C8F02CA8A8 | SHA256:C63DE5F309502F9272402587A6BE22624D1BC2FEACD1BD33FB11E44CD6614B96 | |||
| 4548 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4548.24515\manifest.json | text | |
MD5:C44D4E1D87CB60DDB585D73E2995906C | SHA256:52D1421CCF2CE708B3A734C79020B9C2B79D5779510B28731876ED9D02B4D4BC | |||
| 6720 | WDDriveUtilitiesSetup.exe | C:\Users\admin\AppData\Local\Temp\{E652D2F1-8DA7-40E9-8878-F36CDEDAB133}\.ba\1042\mbapreq.wxl | xml | |
MD5:442F8463EF5CA42B99B2EFACA696BD01 | SHA256:D22F6ADA97DBFFC1E7548E52163807F982B30B11A2A5109E71F42985102CCCBD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
42
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7064 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7064 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1200 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1076 | svchost.exe | 23.218.210.69:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
6068 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7064 | SIHClient.exe | 20.12.23.50:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7064 | SIHClient.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
7064 | SIHClient.exe | 40.69.42.241:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
downloads.mycloud.com |
| shared |