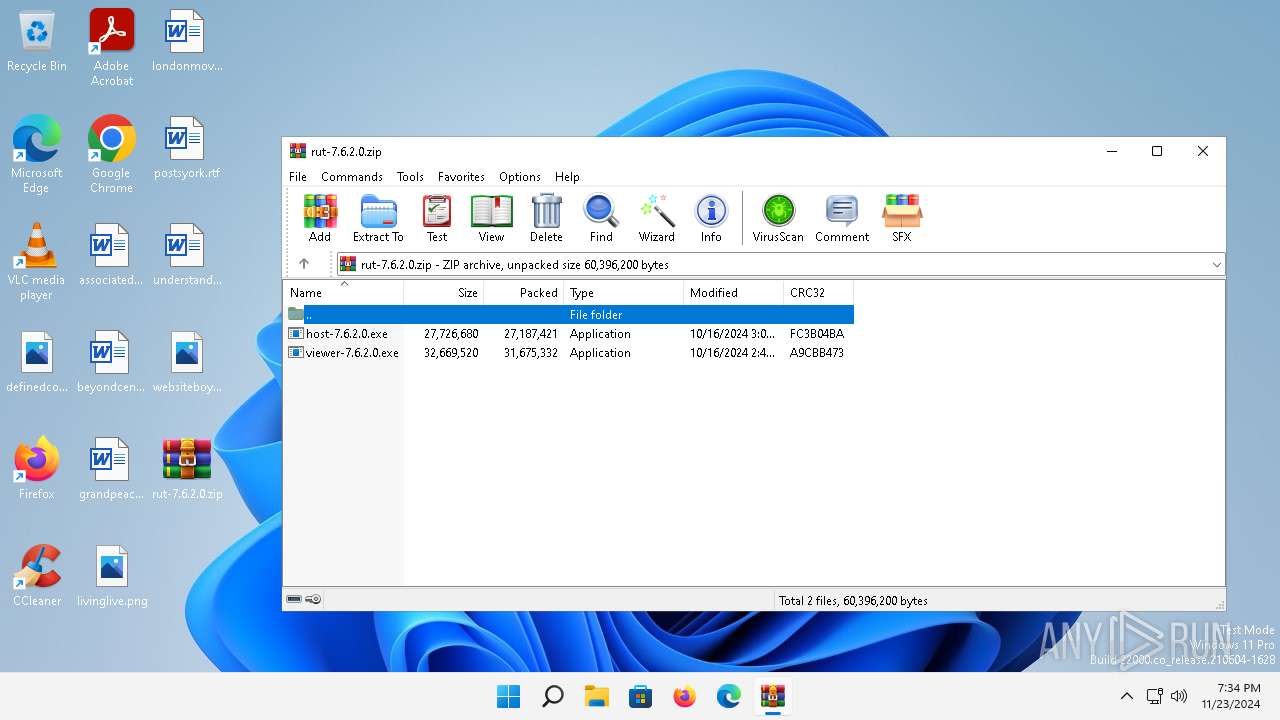
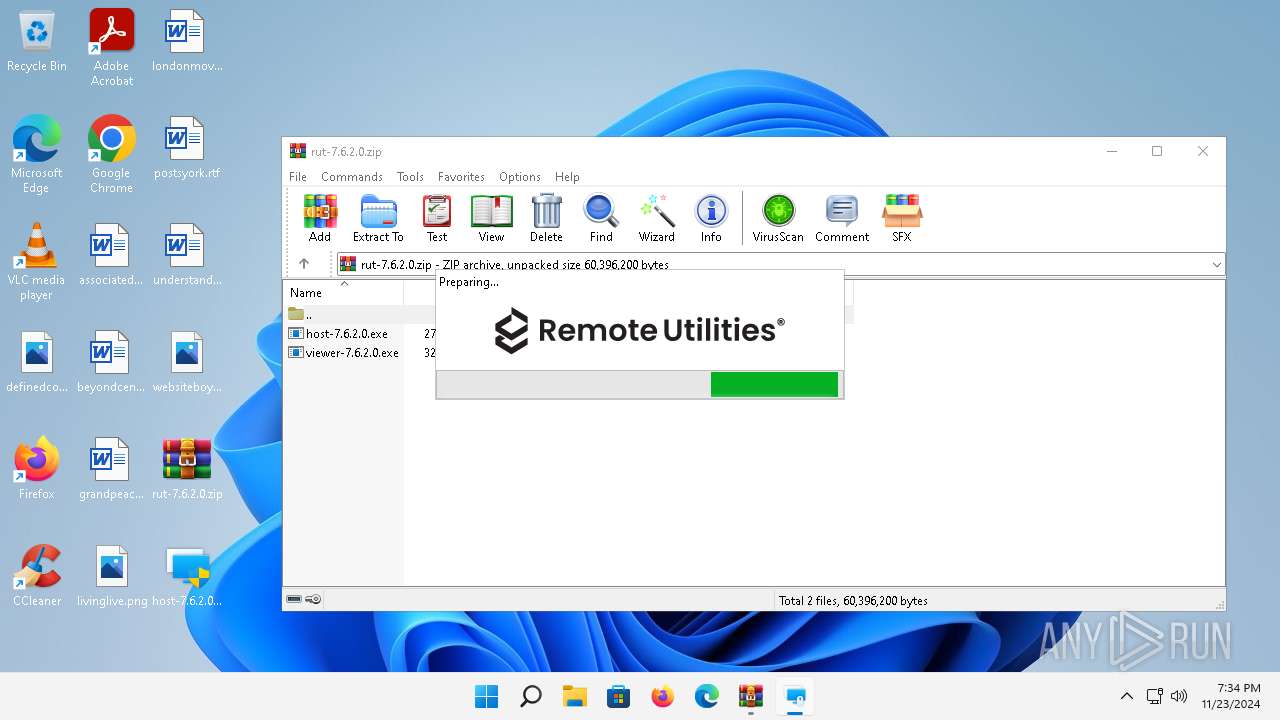
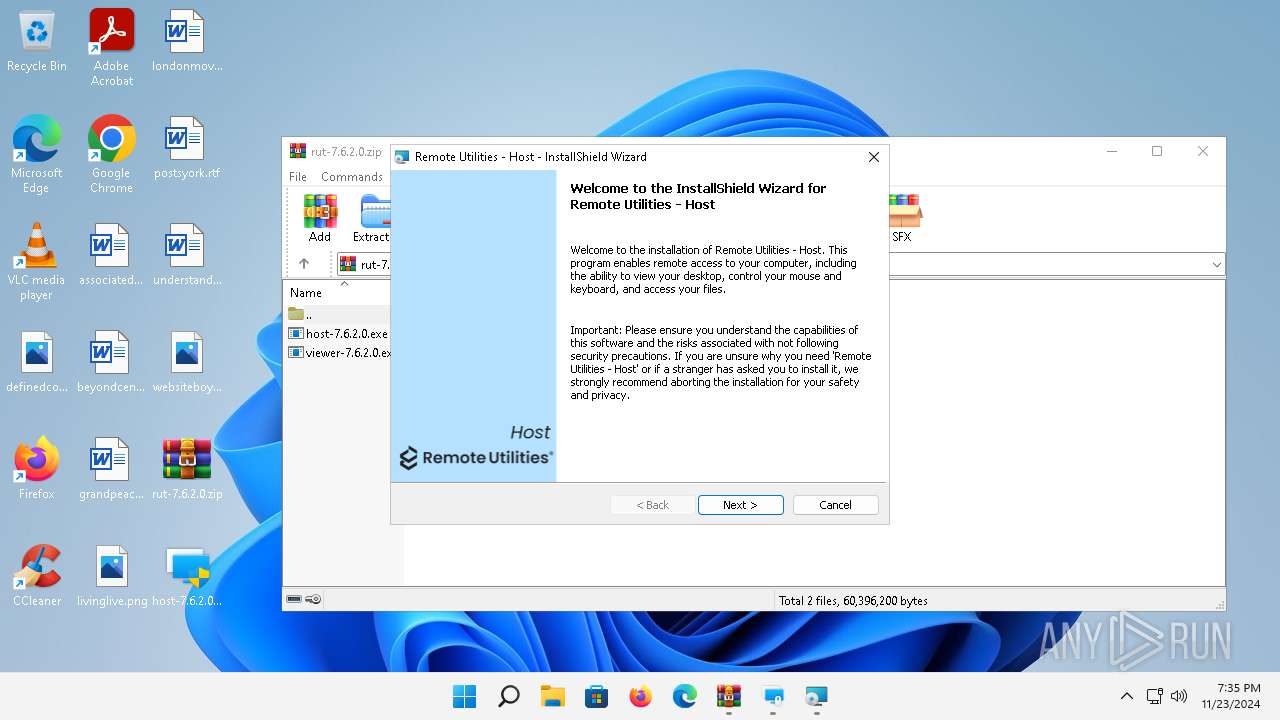
| File name: | rut-7.6.2.0.zip |
| Full analysis: | https://app.any.run/tasks/1a8c6896-52a4-401d-b2a0-3f5184e6ab81 |
| Verdict: | Malicious activity |
| Analysis date: | November 23, 2024, 19:34:17 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 886521555E4A872260353DD983FFA846 |
| SHA1: | F77B1F320BD6D9EF3B684C5BB0E370D6F65DAE6F |
| SHA256: | C3B91E1255BFFCA64D366364A04E1384984F983C86D9F9F0BD6805039D2EF14B |
| SSDEEP: | 393216:ieK3TcNIB15pFCCk2+wTJiRSMbBPyc5sFST9eKpokFPOTKPWBxB+ad68rOn:ieGT11MVWi0GBPCSTNorIWBx760On |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2240)
SUSPICIOUS
Searches for installed software
- host-7.6.2.0.exe (PID: 384)
Reads the Internet Settings
- host-7.6.2.0.exe (PID: 384)
- msiexec.exe (PID: 2452)
Reads security settings of Internet Explorer
- host-7.6.2.0.exe (PID: 384)
Adds/modifies Windows certificates
- msiexec.exe (PID: 2452)
INFO
Create files in a temporary directory
- host-7.6.2.0.exe (PID: 384)
Creates files in the program directory
- host-7.6.2.0.exe (PID: 384)
Reads the computer name
- msiexec.exe (PID: 5032)
- msiexec.exe (PID: 5644)
- host-7.6.2.0.exe (PID: 384)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 2452)
Manual execution by a user
- host-7.6.2.0.exe (PID: 384)
- host-7.6.2.0.exe (PID: 1196)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2452)
The process uses the downloaded file
- host-7.6.2.0.exe (PID: 384)
Checks proxy server information
- msiexec.exe (PID: 2452)
Checks supported languages
- msiexec.exe (PID: 5032)
- msiexec.exe (PID: 5644)
- host-7.6.2.0.exe (PID: 384)
Reads the software policy settings
- msiexec.exe (PID: 2452)
Creates files or folders in the user directory
- msiexec.exe (PID: 2452)
UPX packer has been detected
- host-7.6.2.0.exe (PID: 384)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:10:16 19:02:02 |
| ZipCRC: | 0xfc3b04ba |
| ZipCompressedSize: | 27187421 |
| ZipUncompressedSize: | 27726680 |
| ZipFileName: | host-7.6.2.0.exe |
Total processes
115
Monitored processes
6
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 384 | "C:\Users\admin\Desktop\host-7.6.2.0.exe" | C:\Users\admin\Desktop\host-7.6.2.0.exe | explorer.exe | ||||||||||||
User: admin Company: Remote Utilities Pte. Ltd. Integrity Level: HIGH Description: Remote Utilities Version: 7.6.2.0 Modules
| |||||||||||||||
| 1196 | "C:\Users\admin\Desktop\host-7.6.2.0.exe" | C:\Users\admin\Desktop\host-7.6.2.0.exe | — | explorer.exe | |||||||||||
User: admin Company: Remote Utilities Pte. Ltd. Integrity Level: MEDIUM Description: Remote Utilities Exit code: 3221226540 Version: 7.6.2.0 Modules
| |||||||||||||||
| 2240 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\rut-7.6.2.0.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2452 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\RUT_{606D0365-085A-4ACA-9338-F95672E3A0E4}\installer.msi" | C:\Windows\SysWOW64\msiexec.exe | host-7.6.2.0.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Version: 5.0.22000.653 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5032 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5644 | C:\Windows\syswow64\MsiExec.exe -Embedding 0A82417B87C79CDD14F1035277E98B82 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Version: 5.0.22000.653 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 454
Read events
8 425
Write events
25
Delete events
4
Modification events
| (PID) Process: | (2240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\rut-7.6.2.0.zip | |||
| (PID) Process: | (2240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (384) host-7.6.2.0.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
1
Suspicious files
6
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 384 | host-7.6.2.0.exe | C:\Users\admin\AppData\Local\Temp\RUT_{606D0365-085A-4ACA-9338-F95672E3A0E4}\installer.msi | — | |
MD5:— | SHA256:— | |||
| 2452 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B039FEA45CB4CC4BBACFC013C7C55604_50385F8EB1F713E33924A830D7A2A41C | binary | |
MD5:9BC5D8807AA7B4E3D98BE1CE82C73940 | SHA256:B55C22C65E7ECA301D41065319D750A19143EF8B592865E29FF7C283B4D671F6 | |||
| 2452 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\357F04AD41BCF5FE18FCB69F60C6680F_DF8B1CCAD690136970E760B4D18D549F | binary | |
MD5:B990431481AA067578072864416B103F | SHA256:761909A9F1CB590513EF271511529F7F936801A6A090F43E42B5F15B449DAF4C | |||
| 2452 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\357F04AD41BCF5FE18FCB69F60C6680F_DF8B1CCAD690136970E760B4D18D549F | binary | |
MD5:37A57CA8A522885151F78BC62D43B61E | SHA256:9D14B5D336765B92047896590E00029CDE0316767941E21E45AB2995D920571E | |||
| 384 | host-7.6.2.0.exe | C:\ProgramData\Remote Utilities\install.log | text | |
MD5:1357C8DD63C50EB04F3F0020AC733DDB | SHA256:E5AAA5C9410D336CCDAA5803FD2ECA2E603C2FBB7A40C31D0F4525C337E0789F | |||
| 2452 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI4EB7.tmp | executable | |
MD5:B5ADF92090930E725510E2AAFE97434F | SHA256:1F6F0D9F136BC170CFBC48A1015113947087AC27AED1E3E91673FFC91B9F390B | |||
| 2452 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B039FEA45CB4CC4BBACFC013C7C55604_50385F8EB1F713E33924A830D7A2A41C | binary | |
MD5:ECA296FCE13E94F113735E144B631FDD | SHA256:6CF13F8E9DD398776767C1CCD8E913C9B5F1EE5F54C03FAA73619772E3BF6A12 | |||
| 2452 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\9CB4373A4252DE8D2212929836304EC5_1AB74AA2E3A56E1B8AD8D3FEC287554E | binary | |
MD5:0485F528AF8E90EC5F9A0C45860D2B07 | SHA256:A6DBCE848E4DC8D9F5DC4D156D1067A115A33126E2C17484DC3F75E372121895 | |||
| 2452 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\9CB4373A4252DE8D2212929836304EC5_1AB74AA2E3A56E1B8AD8D3FEC287554E | binary | |
MD5:C97173A6E31F86A218FB38708F500CCF | SHA256:F72D4D8C9AC49FC7646CD6DCE81393074FB54C73AB50C70A165951DAA3B85FA5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
28
DNS requests
31
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2996 | firefox.exe | POST | 200 | 95.101.74.198:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
— | — | HEAD | 200 | 23.218.208.109:443 | https://fs.microsoft.com/fs/windows/config.json | unknown | — | — | unknown |
— | — | GET | 200 | 23.55.161.193:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | whitelisted |
2452 | msiexec.exe | GET | 200 | 151.101.66.133:80 | http://ocsp.globalsign.com/rootr3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCEHgDGEJFcIpBz28BuO60qVQ%3D | unknown | — | — | whitelisted |
2452 | msiexec.exe | GET | 200 | 151.101.66.133:80 | http://ocsp.globalsign.com/gsgccr45evcodesignca2020/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBQaCbVYh07WONuW4e63Ydlu4AlbDAQUJZ3Q%2FFkJhmPF7POxEztXHAOSNhECDBsXtMYQDn%2FUFWxfAQ%3D%3D | unknown | — | — | whitelisted |
4308 | MoUsoCoreWorker.exe | GET | 304 | 23.50.131.199:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?69f59635781f4c20 | unknown | — | — | whitelisted |
2452 | msiexec.exe | GET | 200 | 151.101.66.133:80 | http://ocsp.globalsign.com/codesigningrootr45/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQVFZP5vqhCrtRN5SWf40Rn6NM1IAQUHwC%2FRoAK%2FHg5t6W0Q9lWULvOljsCEHe9DgW3WQu2HUdhUx4%2Fde0%3D | unknown | — | — | whitelisted |
2860 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?c8be12605aaef0f9 | unknown | — | — | whitelisted |
2860 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?6c35f0c1573b9bee | unknown | — | — | whitelisted |
2860 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?ec4ee7ddfd5a1b79 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 52.109.76.240:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2996 | firefox.exe | 34.149.100.209:443 | firefox.settings.services.mozilla.com | GOOGLE | US | whitelisted |
2996 | firefox.exe | 34.120.208.123:443 | incoming.telemetry.mozilla.org | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
— | — | 34.149.100.209:443 | firefox.settings.services.mozilla.com | GOOGLE | US | whitelisted |
— | — | 34.120.208.123:443 | incoming.telemetry.mozilla.org | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
— | — | 23.55.161.193:80 | — | Akamai International B.V. | DE | unknown |
5552 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2996 | firefox.exe | 95.101.74.198:80 | r10.o.lencr.org | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
firefox.settings.services.mozilla.com |
| whitelisted |
prod.remote-settings.prod.webservices.mozgcp.net |
| whitelisted |
incoming.telemetry.mozilla.org |
| whitelisted |
telemetry-incoming.r53-2.services.mozilla.com |
| whitelisted |
google.com |
| whitelisted |
r10.o.lencr.org |
| whitelisted |
a1887.dscq.akamai.net |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Microsoft Connection Test |