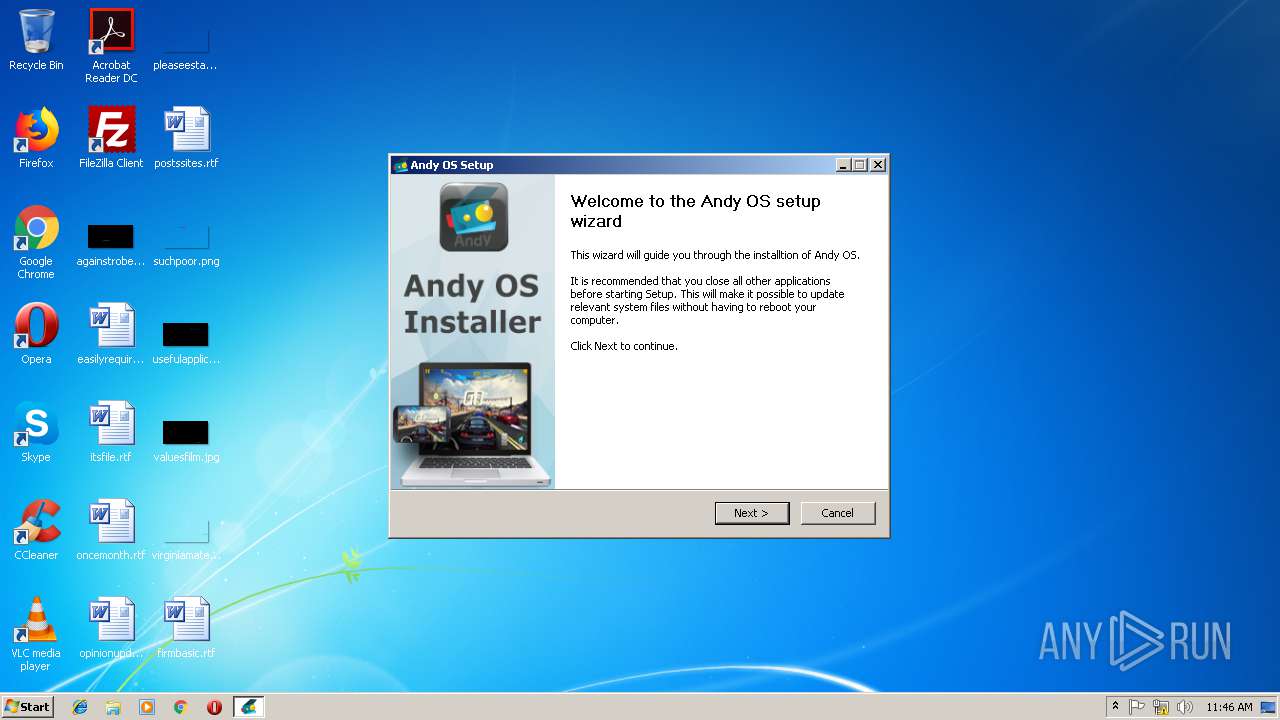
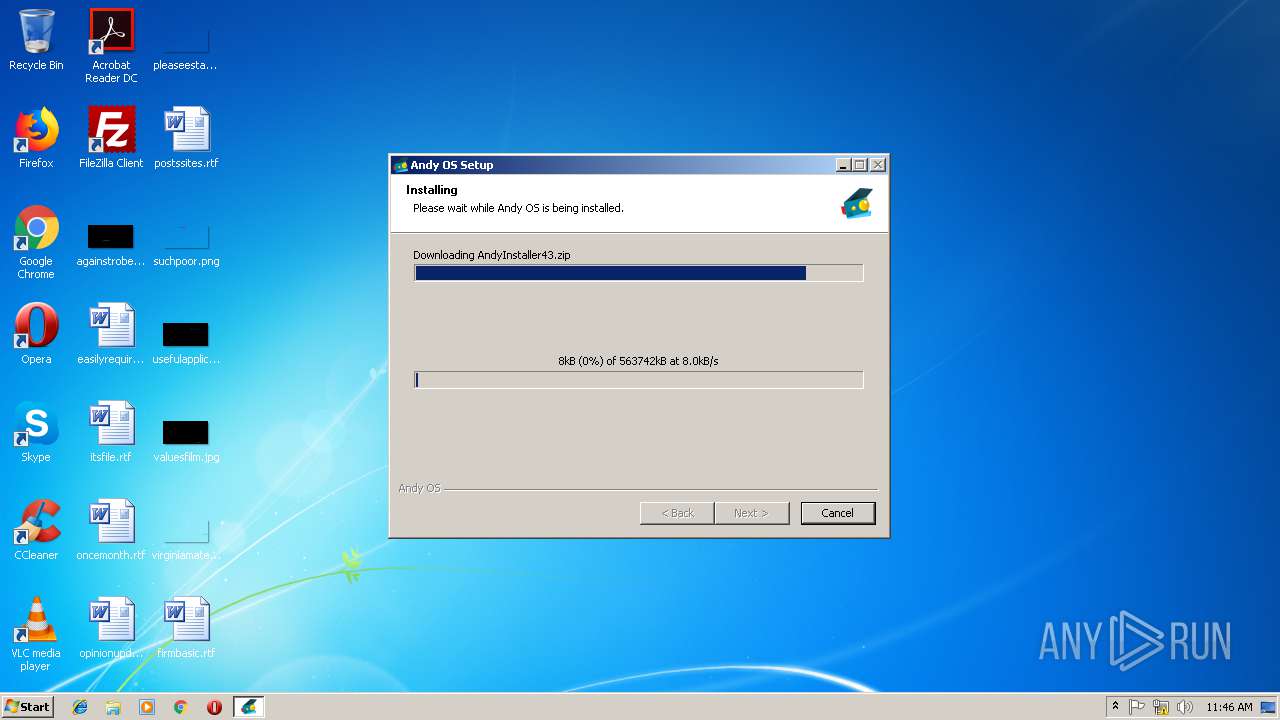
| File name: | Andy_Android_Emulator_v43_1.exe |
| Full analysis: | https://app.any.run/tasks/68cb0295-4ec9-4fea-a87c-6b9e0a77ec1e |
| Verdict: | Malicious activity |
| Analysis date: | November 15, 2018, 11:46:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 206E3706A33A76AA98CF310FF21123AF |
| SHA1: | F3E446C3DA91157FC1A9E006215A0E1268B4170C |
| SHA256: | C3AEA96792D7B0BBD07B4FCA1624234EC35DF8F1F643251C3B00BE220CE87BA1 |
| SSDEEP: | 12288:Pc8m/iKGKPVnjvYXVSsxbE4rC35TJAFLeyo3LnppmAgdDMs7LZ:PcPJVDYXEsxbGyFm6Agis7L |
MALICIOUS
Loads dropped or rewritten executable
- Andy_Android_Emulator_v43_1.exe (PID: 4052)
Changes the autorun value in the registry
- InfDefaultInstall.exe (PID: 2856)
- InfDefaultInstall.exe (PID: 2668)
SUSPICIOUS
Executable content was dropped or overwritten
- Andy_Android_Emulator_v43_1.exe (PID: 4052)
- InfDefaultInstall.exe (PID: 2668)
- InfDefaultInstall.exe (PID: 2856)
- msiexec.exe (PID: 568)
- MsiExec.exe (PID: 3208)
- DrvInst.exe (PID: 4000)
Creates files in the driver directory
- InfDefaultInstall.exe (PID: 2668)
- InfDefaultInstall.exe (PID: 2856)
- DrvInst.exe (PID: 3220)
- MsiExec.exe (PID: 3208)
- DrvInst.exe (PID: 4000)
Removes files from Windows directory
- InfDefaultInstall.exe (PID: 2668)
- InfDefaultInstall.exe (PID: 2856)
- MsiExec.exe (PID: 3208)
- DrvInst.exe (PID: 3220)
- rundll32.exe (PID: 2864)
- DrvInst.exe (PID: 4000)
Creates files in the Windows directory
- InfDefaultInstall.exe (PID: 2668)
- InfDefaultInstall.exe (PID: 2856)
- MsiExec.exe (PID: 3208)
- DrvInst.exe (PID: 3220)
- rundll32.exe (PID: 2864)
- DrvInst.exe (PID: 4000)
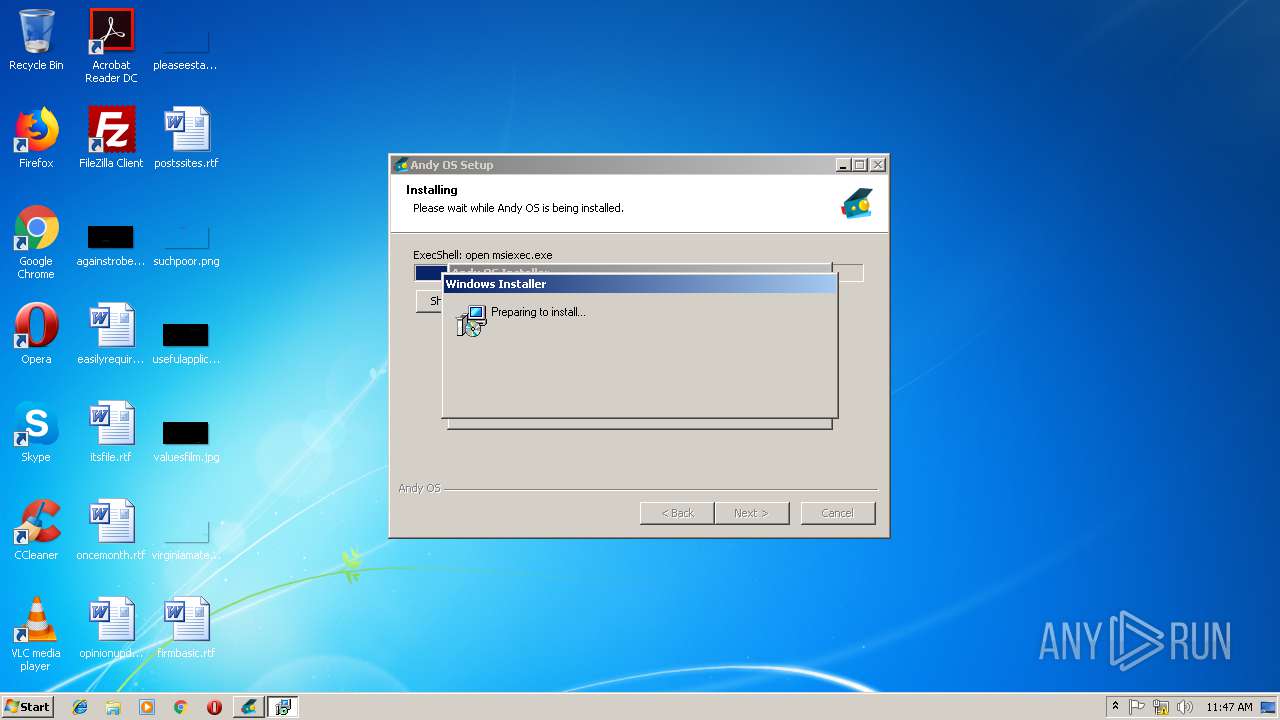
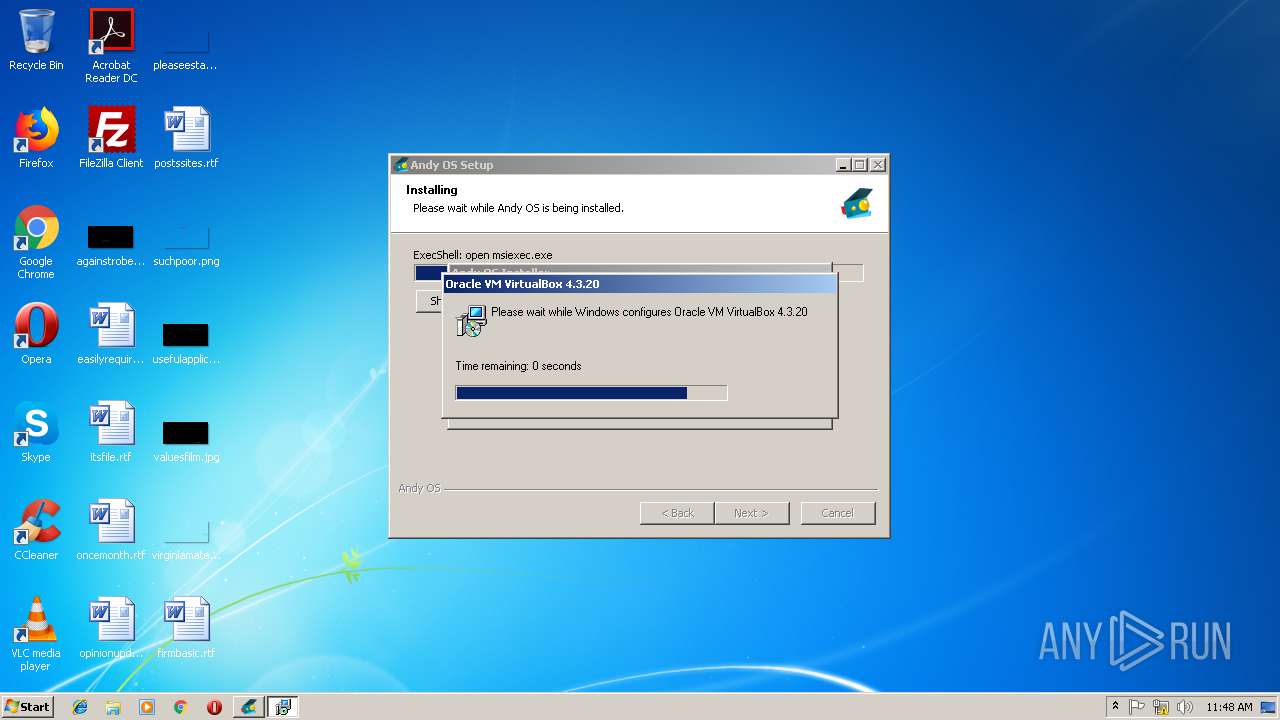
Starts Microsoft Installer
- Andy_Android_Emulator_v43_1.exe (PID: 4052)
Creates files in the program directory
- Andy_Android_Emulator_v43_1.exe (PID: 4052)
Uses RUNDLL32.EXE to load library
- DrvInst.exe (PID: 3220)
- DrvInst.exe (PID: 4000)
Creates COM task schedule object
- msiexec.exe (PID: 568)
Creates files in the user directory
- msiexec.exe (PID: 568)
Modifies the open verb of a shell class
- msiexec.exe (PID: 568)
INFO
Dropped object may contain Bitcoin addresses
- Andy_Android_Emulator_v43_1.exe (PID: 4052)
- msiexec.exe (PID: 568)
Low-level read access rights to disk partition
- vssvc.exe (PID: 3892)
Searches for installed software
- msiexec.exe (PID: 568)
Application launched itself
- msiexec.exe (PID: 568)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 3208)
Creates a software uninstall entry
- msiexec.exe (PID: 568)
Creates files in the program directory
- msiexec.exe (PID: 568)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (94.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.7) |
| .exe | | | Win32 Executable (generic) (0.5) |
| .exe | | | Generic Win/DOS Executable (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:12:05 23:52:06+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 23552 |
| InitializedDataSize: | 263168 |
| UninitializedDataSize: | 8192 |
| EntryPoint: | 0x323c |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.1.0.0 |
| ProductVersionNumber: | 1.1.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | ASCII |
| Comments: | ANDY setup |
| CompanyName: | andyroid.net |
| FileDescription: | ANDY setup |
| FileVersion: | 1.1 |
| LegalCopyright: | © andyroid.net (ANDY_BL_Standard_ANDY) |
| ProductName: | Andy OS |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 05-Dec-2009 22:52:06 |
| Detected languages: |
|
| Comments: | ANDY setup |
| CompanyName: | andyroid.net |
| FileDescription: | ANDY setup |
| FileVersion: | 1.1 |
| LegalCopyright: | © andyroid.net (ANDY_BL_Standard_ANDY) |
| ProductName: | Andy OS |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 05-Dec-2009 22:52:06 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00005A5A | 0x00005C00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.43485 |
.rdata | 0x00007000 | 0x00001190 | 0x00001200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.18163 |
.data | 0x00009000 | 0x0003DF98 | 0x00000400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.70286 |
.ndata | 0x00047000 | 0x000E2000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x00129000 | 0x00002300 | 0x00002400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.29135 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.21482 | 958 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 5.44296 | 1128 | UNKNOWN | English - United States | RT_ICON |
102 | 2.71813 | 180 | UNKNOWN | English - United States | RT_DIALOG |
103 | 2.05236 | 34 | UNKNOWN | English - United States | RT_GROUP_ICON |
105 | 2.73893 | 514 | UNKNOWN | English - United States | RT_DIALOG |
106 | 2.91148 | 248 | UNKNOWN | English - United States | RT_DIALOG |
107 | 2.52183 | 160 | UNKNOWN | English - United States | RT_DIALOG |
111 | 2.92787 | 238 | UNKNOWN | English - United States | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
VERSION.dll |
ole32.dll |
Total processes
56
Monitored processes
17
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 568 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 896 | "C:\Windows\system32\runonce.exe" -r | C:\Windows\system32\runonce.exe | — | InfDefaultInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2480 | DrvInst.exe "1" "200" "STORAGE\VolumeSnapshot\HarddiskVolumeSnapshot18" "" "" "6792c44eb" "00000000" "0000056C" "000004C8" | C:\Windows\system32\DrvInst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2548 | "C:\Windows\System32\grpconv.exe" -o | C:\Windows\System32\grpconv.exe | — | runonce.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Progman Group Converter Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2656 | "C:\Windows\system32\runonce.exe" -r | C:\Windows\system32\runonce.exe | — | InfDefaultInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
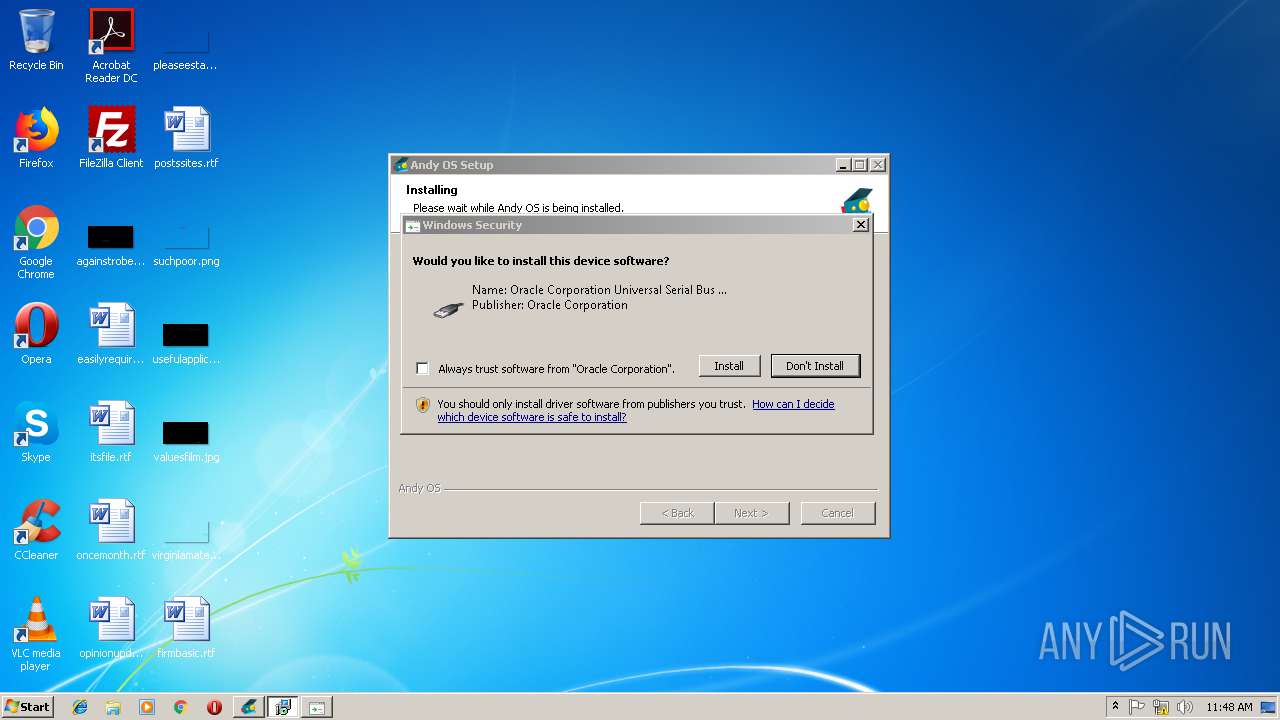
| 2668 | InfDefaultInstall "c:\Program Files\AndyDrivers\VBoxDrv.inf" | C:\Windows\system32\InfDefaultInstall.exe | Andy_Android_Emulator_v43_1.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: INF Default Install Exit code: 0 Version: 5.2.3668.0 Modules
| |||||||||||||||
| 2856 | InfDefaultInstall "c:\Program Files\AndyDrivers\VBoxUSBMon.inf" | C:\Windows\system32\InfDefaultInstall.exe | Andy_Android_Emulator_v43_1.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: INF Default Install Exit code: 0 Version: 5.2.3668.0 Modules
| |||||||||||||||
| 2864 | rundll32.exe C:\Windows\system32\pnpui.dll,InstallSecurityPromptRunDllW 20 Global\{1591f4c7-99a1-0f78-c9c2-553f361a0642} Global\{0a8de216-ee83-1ed8-f334-4b7e56f2ca0d} C:\Windows\System32\DriverStore\Temp\{17d3c9ba-c956-1b33-679d-9e13bbcd695e}\VBoxUSB.inf C:\Windows\System32\DriverStore\Temp\{17d3c9ba-c956-1b33-679d-9e13bbcd695e}\VBoxUSB.cat | C:\Windows\system32\rundll32.exe | — | DrvInst.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3160 | rundll32.exe C:\Windows\system32\pnpui.dll,InstallSecurityPromptRunDllW 20 Global\{5e151d17-f3da-41a2-1207-1058d08d1b7b} Global\{069592f8-44ed-08bb-e21b-aa480d6ebc37} C:\Windows\System32\DriverStore\Temp\{7b1b8dd0-7194-212f-53aa-7b09d967bd65}\VBoxNetAdp.inf C:\Windows\System32\DriverStore\Temp\{7b1b8dd0-7194-212f-53aa-7b09d967bd65}\VBoxNetAdp.cat | C:\Windows\system32\rundll32.exe | — | DrvInst.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3204 | "C:\Users\admin\AppData\Local\Temp\Andy_Android_Emulator_v43_1.exe" | C:\Users\admin\AppData\Local\Temp\Andy_Android_Emulator_v43_1.exe | — | explorer.exe | |||||||||||
User: admin Company: andyroid.net Integrity Level: MEDIUM Description: ANDY setup Exit code: 3221226540 Version: 1.1 | |||||||||||||||
Total events
2 165
Read events
979
Write events
1 185
Delete events
1
Modification events
| (PID) Process: | (896) runonce.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | delete value | Name: | GrpConv |
Value: grpconv -o | |||
| (PID) Process: | (896) runonce.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (896) runonce.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2668) InfDefaultInstall.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\Setup\SetupapiLogStatus |
| Operation: | write | Name: | setupapi.app.log |
Value: 4096 | |||
| (PID) Process: | (2668) InfDefaultInstall.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | GrpConv |
Value: grpconv -o | |||
| (PID) Process: | (2668) InfDefaultInstall.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 52 | |||
| (PID) Process: | (2856) InfDefaultInstall.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | GrpConv |
Value: grpconv -o | |||
| (PID) Process: | (2856) InfDefaultInstall.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 53 | |||
| (PID) Process: | (4052) Andy_Android_Emulator_v43_1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (4052) Andy_Android_Emulator_v43_1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
161
Suspicious files
33
Text files
175
Unknown types
32
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4052 | Andy_Android_Emulator_v43_1.exe | C:\ProgramData\AndyInstaller43.zip | — | |
MD5:— | SHA256:— | |||
| 4052 | Andy_Android_Emulator_v43_1.exe | C:\Users\admin\AppData\Local\Temp\nsu8F08.tmp\modern-wizard.bmp | image | |
MD5:CBE40FD2B1EC96DAEDC65DA172D90022 | SHA256:3AD2DC318056D0A2024AF1804EA741146CFC18CC404649A44610CBF8B2056CF2 | |||
| 4052 | Andy_Android_Emulator_v43_1.exe | C:\Program Files\AndyOfflineInstaller43\tools\fastboot.exe | executable | |
MD5:— | SHA256:— | |||
| 4052 | Andy_Android_Emulator_v43_1.exe | C:\Program Files\AndyOfflineInstaller43\SetupFiles\AndyUninstall.exe | executable | |
MD5:— | SHA256:— | |||
| 4052 | Andy_Android_Emulator_v43_1.exe | C:\Users\admin\AppData\Local\Temp\nsu8F08.tmp\nsDialogs.dll | executable | |
MD5:C10E04DD4AD4277D5ADC951BB331C777 | SHA256:E31AD6C6E82E603378CB6B80E67D0E0DCD9CF384E1199AC5A65CB4935680021A | |||
| 4052 | Andy_Android_Emulator_v43_1.exe | C:\Program Files\AndyOfflineInstaller43\VB\common.cab | — | |
MD5:— | SHA256:— | |||
| 4052 | Andy_Android_Emulator_v43_1.exe | C:\Program Files\AndyOfflineInstaller43\VB\vbox-x86.msi | — | |
MD5:— | SHA256:— | |||
| 4052 | Andy_Android_Emulator_v43_1.exe | C:\Program Files\AndyOfflineInstaller43\tools\AndyIcon.ico | image | |
MD5:— | SHA256:— | |||
| 4052 | Andy_Android_Emulator_v43_1.exe | C:\Program Files\AndyOfflineInstaller43\tools\adb.exe | executable | |
MD5:— | SHA256:— | |||
| 4052 | Andy_Android_Emulator_v43_1.exe | C:\Program Files\AndyOfflineInstaller43\tools\AndyIcon16.ico | image | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
5
DNS requests
5
Threats
930
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4052 | Andy_Android_Emulator_v43_1.exe | GET | — | 2.16.186.9:80 | http://andyroid.vonetize.com.edgesuite.net/vm/v43/Andy_43e_x86_3.zip | unknown | — | — | whitelisted |
4052 | Andy_Android_Emulator_v43_1.exe | GET | 301 | 67.199.248.10:80 | http://bit.ly/andywelcome | US | html | 129 b | shared |
4052 | Andy_Android_Emulator_v43_1.exe | GET | 301 | 52.205.222.157:80 | http://www.andyroid.net/trackinst.php?id=1 | US | html | 333 b | suspicious |
4052 | Andy_Android_Emulator_v43_1.exe | GET | 301 | 52.205.222.157:80 | http://www.andyroid.net/trackinst.php?id=1 | US | html | 333 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4052 | Andy_Android_Emulator_v43_1.exe | 67.199.248.10:80 | bit.ly | Bitly Inc | US | shared |
4052 | Andy_Android_Emulator_v43_1.exe | 52.205.222.157:80 | www.andyroid.net | Amazon.com, Inc. | US | unknown |
4052 | Andy_Android_Emulator_v43_1.exe | 2.16.186.9:80 | andyroid.vonetize.com.edgesuite.net | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
bit.ly |
| shared |
www.andyroid.net |
| suspicious |
dns.msftncsi.com |
| shared |
andyroid.vonetize.com.edgesuite.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4052 | Andy_Android_Emulator_v43_1.exe | unknown | SURICATA IPv4 invalid checksum |
4052 | Andy_Android_Emulator_v43_1.exe | unknown | SURICATA TCPv4 invalid checksum |
4052 | Andy_Android_Emulator_v43_1.exe | unknown | SURICATA TCPv4 invalid checksum |
4052 | Andy_Android_Emulator_v43_1.exe | unknown | SURICATA IPv4 invalid checksum |
4052 | Andy_Android_Emulator_v43_1.exe | unknown | SURICATA IPv4 invalid checksum |
4052 | Andy_Android_Emulator_v43_1.exe | unknown | SURICATA IPv4 invalid checksum |
4052 | Andy_Android_Emulator_v43_1.exe | unknown | SURICATA TCPv4 invalid checksum |
4052 | Andy_Android_Emulator_v43_1.exe | unknown | SURICATA TCPv4 invalid checksum |
4052 | Andy_Android_Emulator_v43_1.exe | unknown | SURICATA IPv4 invalid checksum |
4052 | Andy_Android_Emulator_v43_1.exe | unknown | SURICATA IPv4 invalid checksum |
5 ETPRO signatures available at the full report