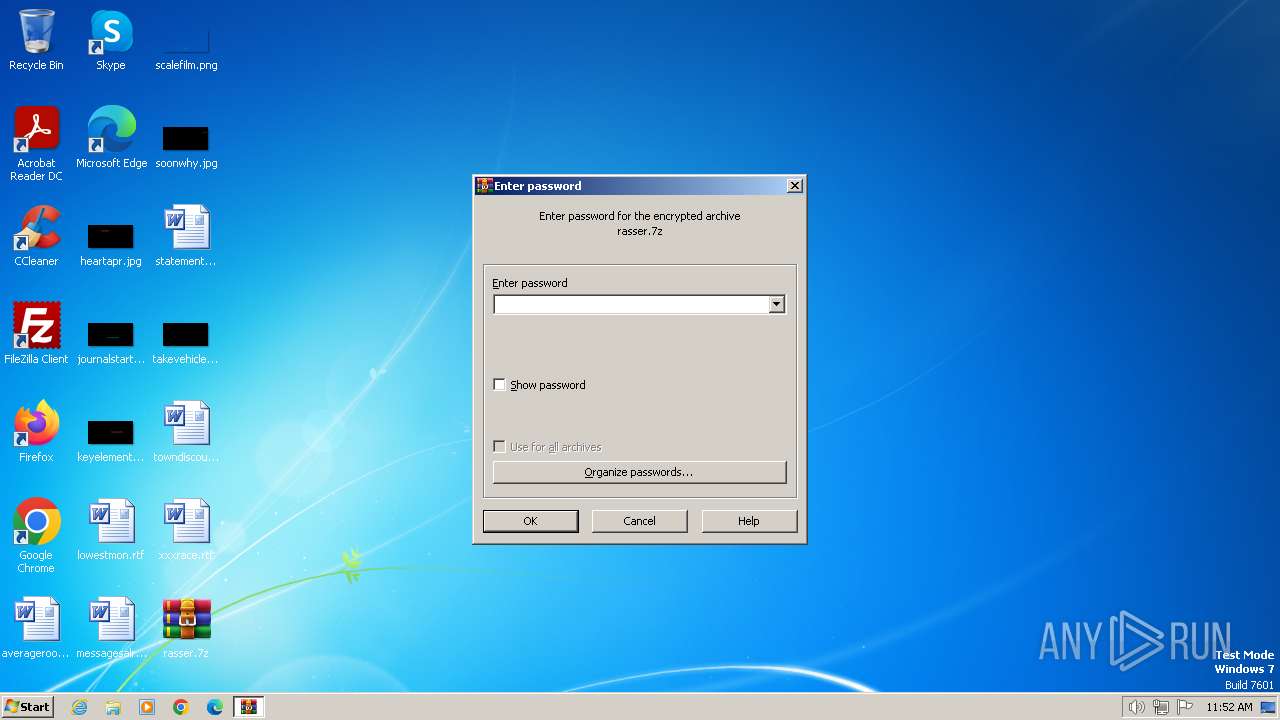
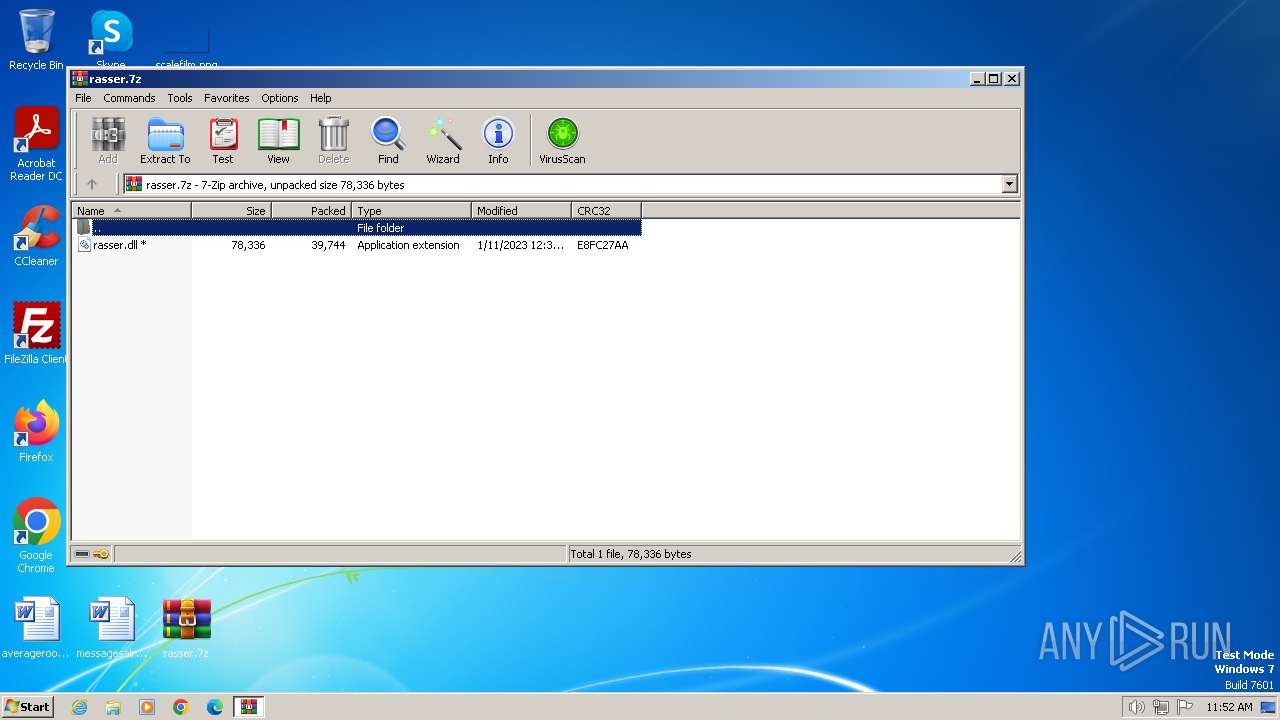
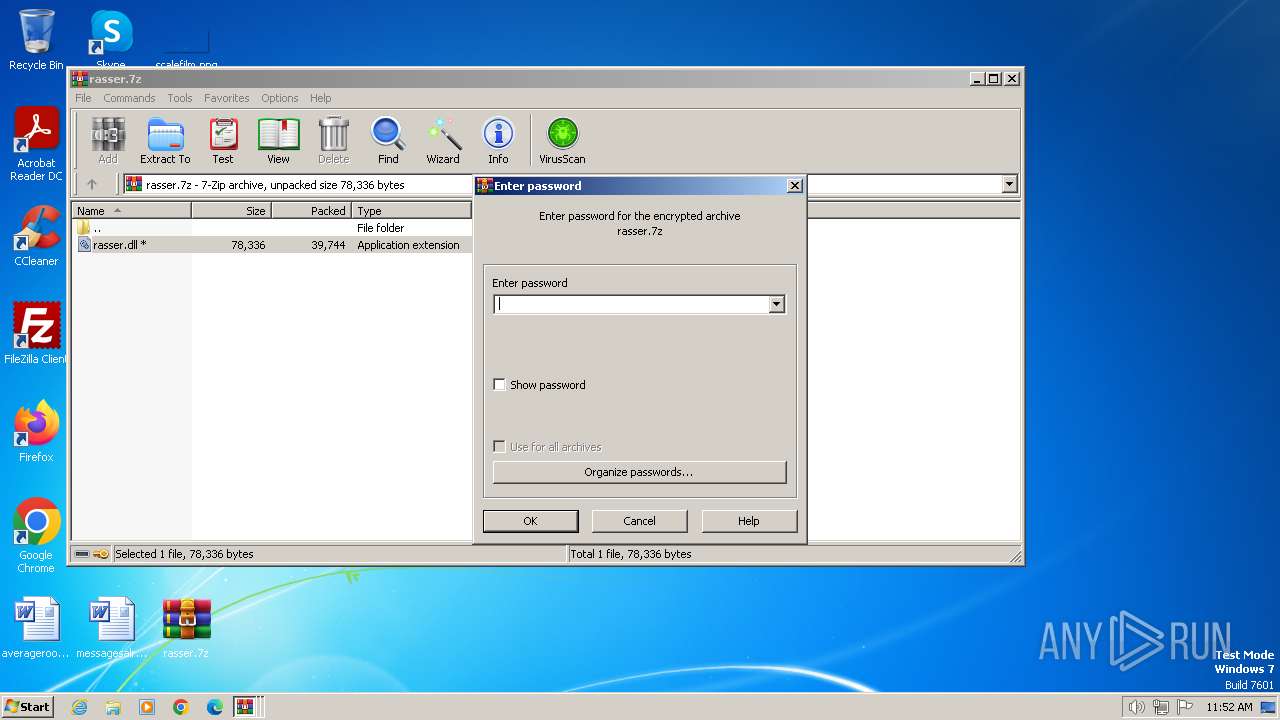
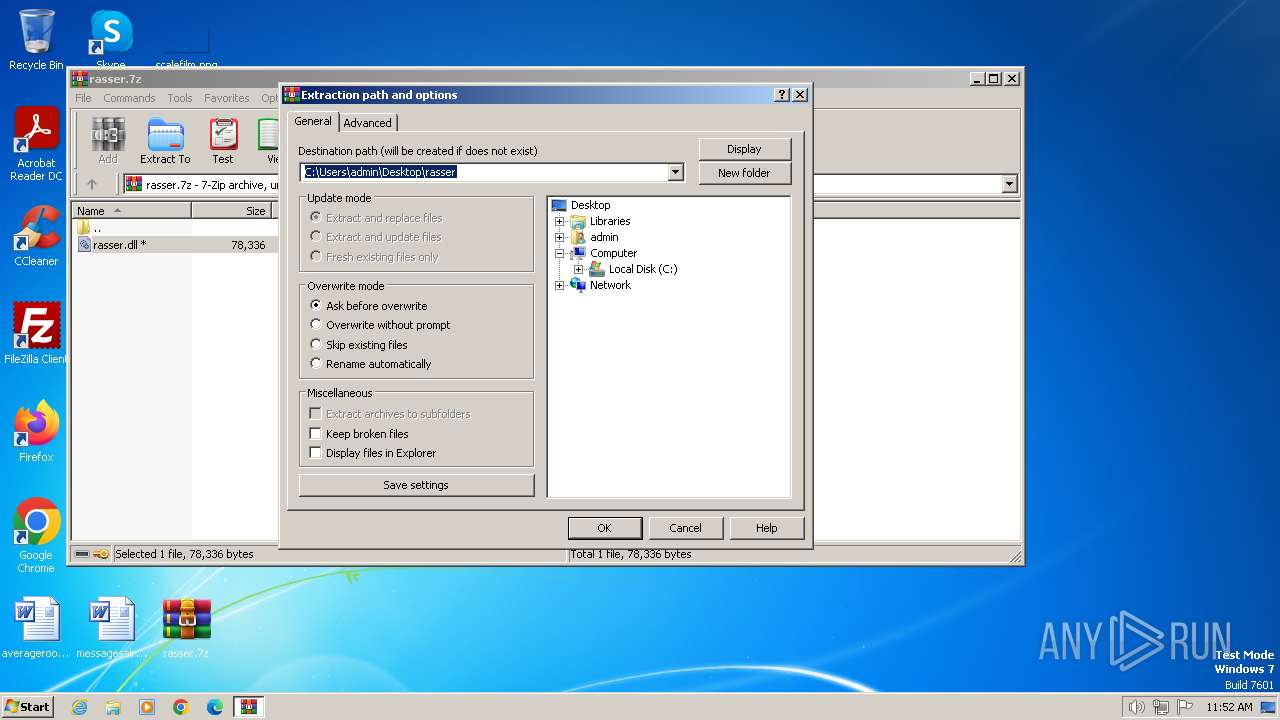
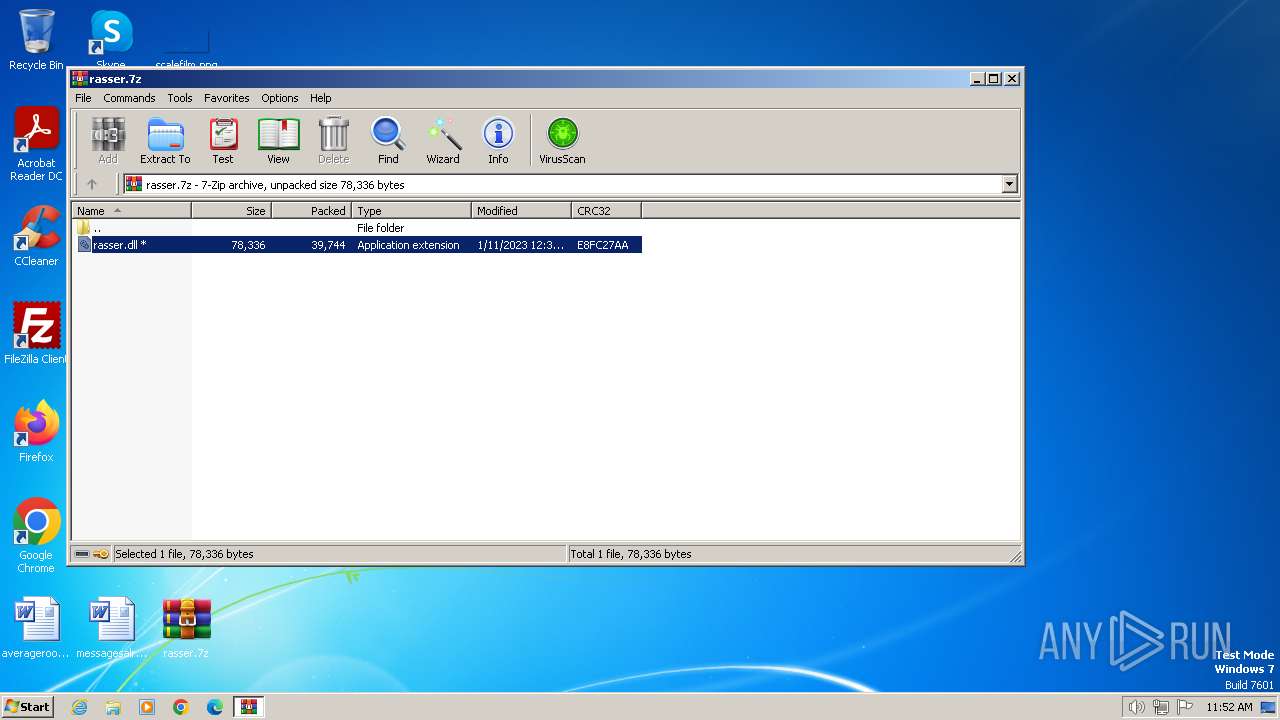
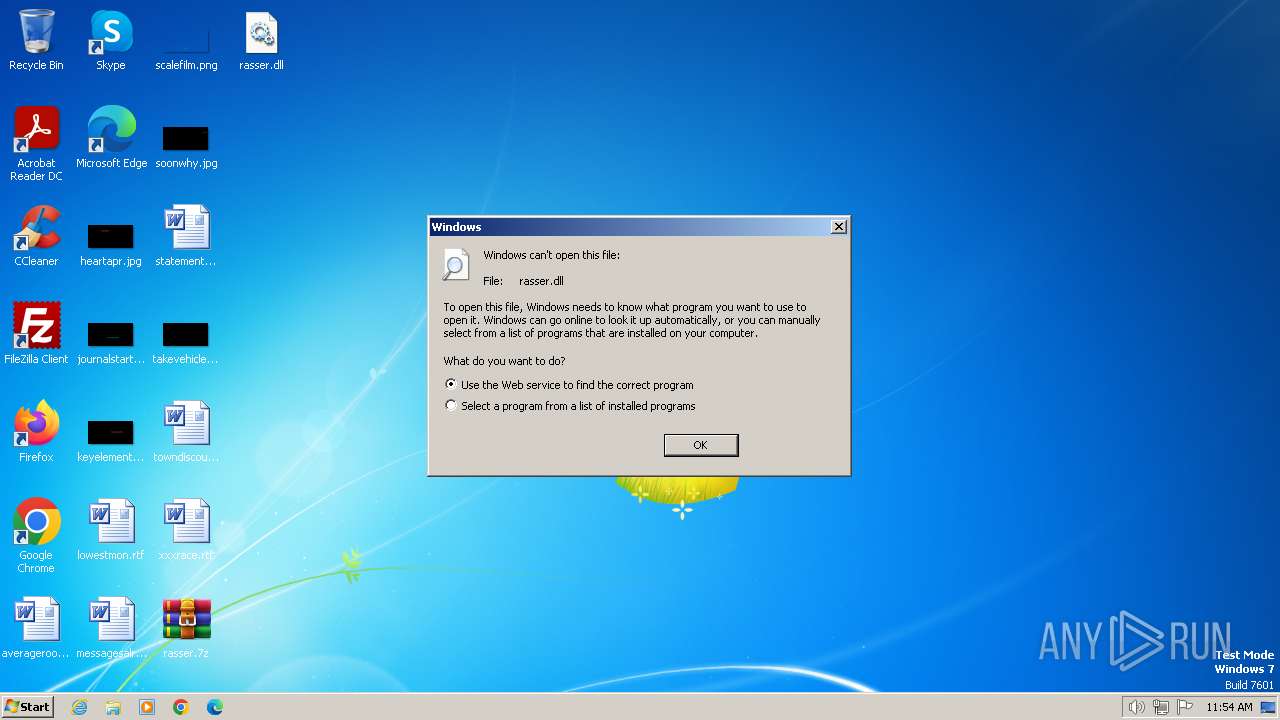
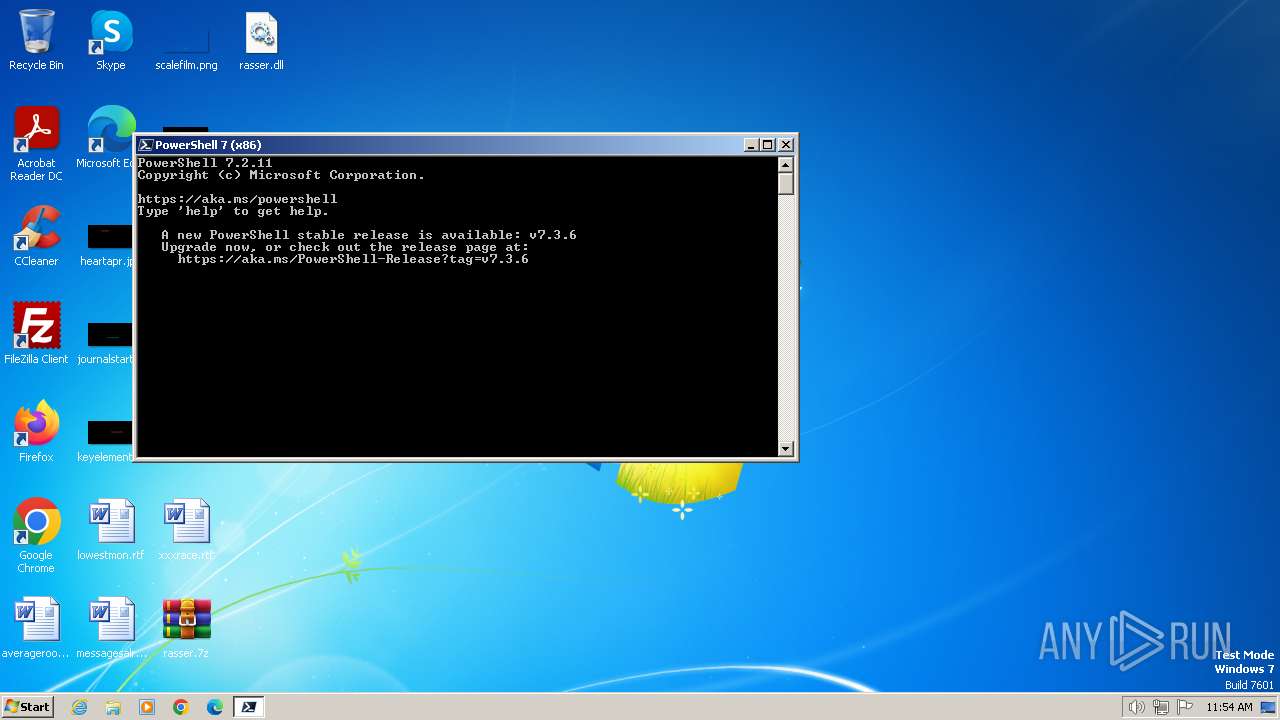
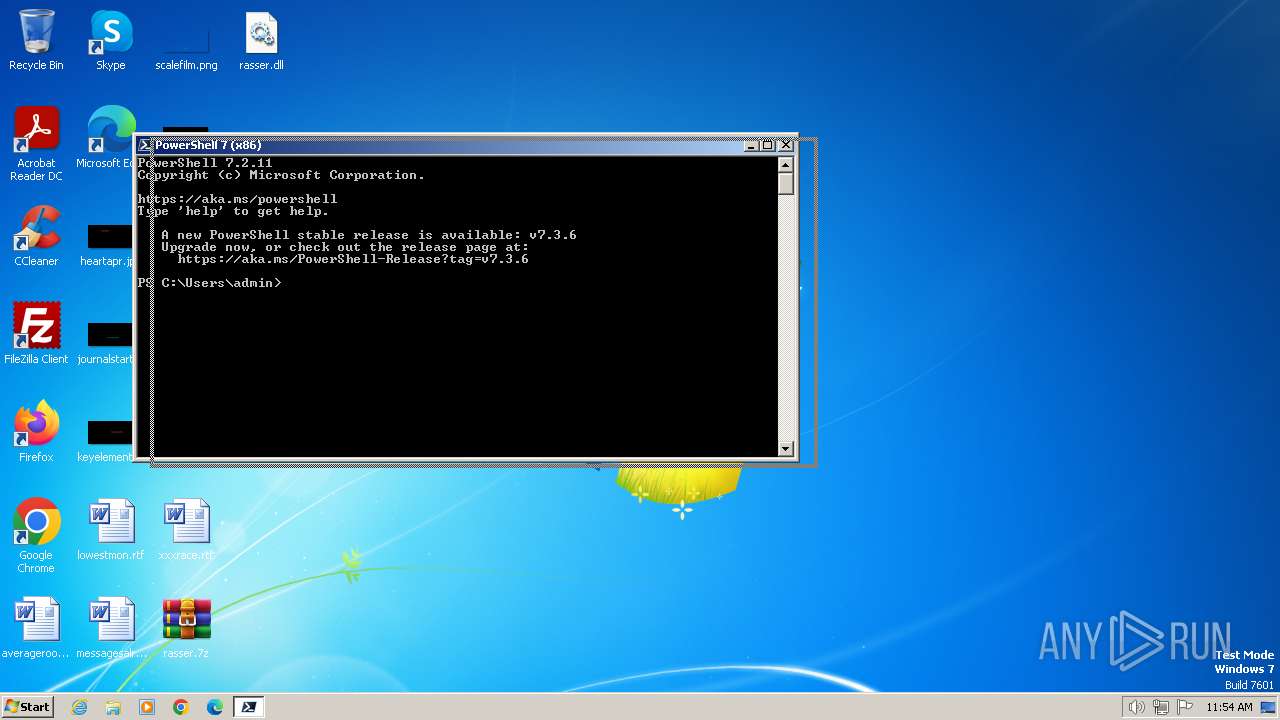
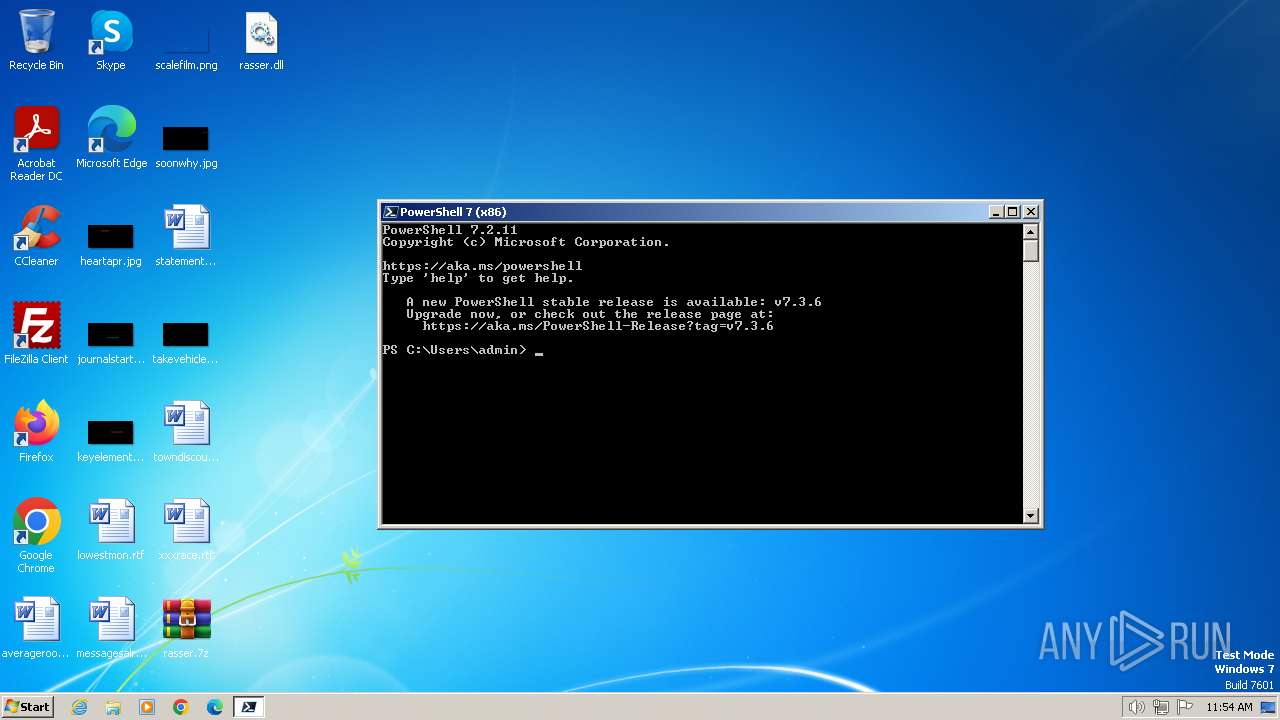
| File name: | rasser.7z |
| Full analysis: | https://app.any.run/tasks/0f49c4d9-416a-4274-be5b-d1cd2a949fb8 |
| Verdict: | Malicious activity |
| Analysis date: | December 18, 2023, 11:52:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | F1959440A6DB293EF0A1778E3BCF22BB |
| SHA1: | 66E943D471083DD581B19D2AEEBA11E3DE6ED5F9 |
| SHA256: | C39DDBC633303A232F946D827100E95592B863B291356CCF0E94B27A275F215A |
| SSDEEP: | 768:akyNlVXkybnMhdBf1Hz40iVdM4XN6vx6Y8/EQI4dU7nR4PMPfQOG7Wk0K5LI9uQU:aHNl1kXBtHz40AX8vDSp5iRaURvuBDT |
MALICIOUS
No malicious indicators.SUSPICIOUS
Application launched itself
- WinRAR.exe (PID: 2040)
Reads Microsoft Outlook installation path
- mmc.exe (PID: 3156)
- mmc.exe (PID: 3748)
Reads the Internet Settings
- mmc.exe (PID: 3156)
- mmc.exe (PID: 3748)
Reads Internet Explorer settings
- mmc.exe (PID: 3156)
- mmc.exe (PID: 3748)
Connects to the server without a host name
- pwsh.exe (PID: 3088)
INFO
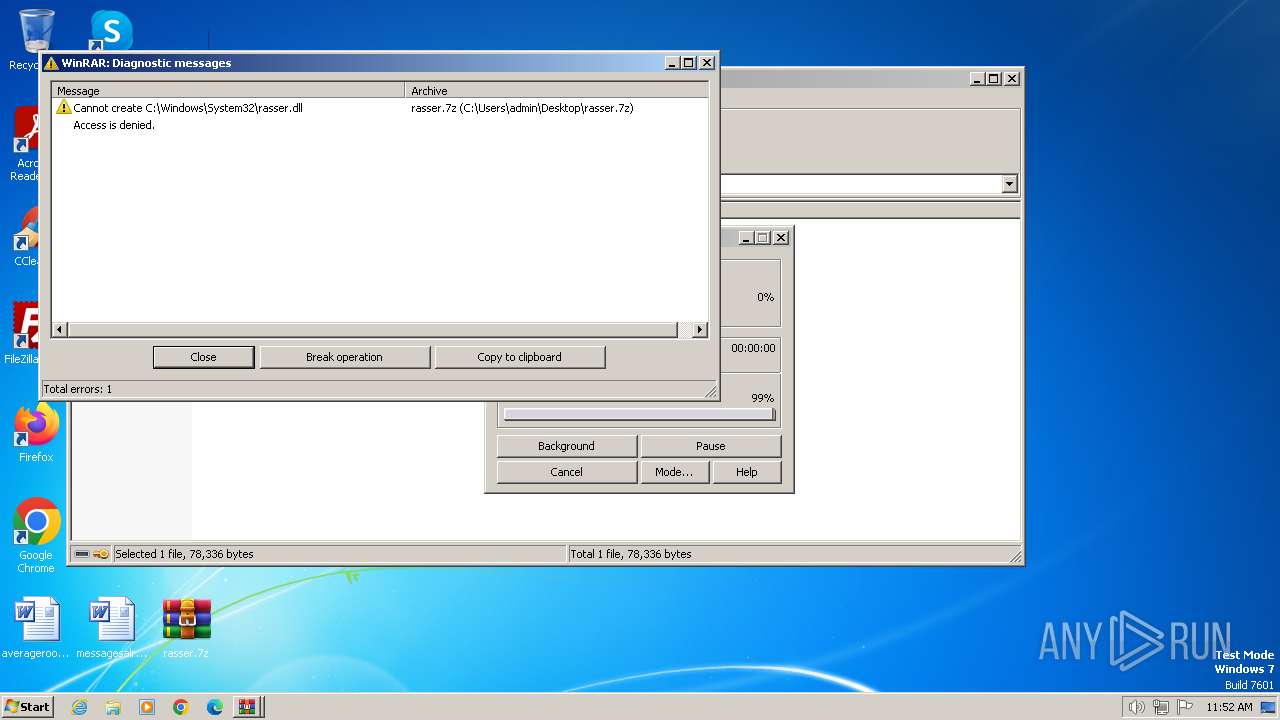
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2040)
Checks proxy server information
- mmc.exe (PID: 3156)
- mmc.exe (PID: 3748)
Manual execution by a user
- explorer.exe (PID: 844)
- mmc.exe (PID: 900)
- mmc.exe (PID: 3156)
- rundll32.exe (PID: 3292)
- pwsh.exe (PID: 3088)
- mmc.exe (PID: 4080)
- mmc.exe (PID: 3748)
Reads the computer name
- pwsh.exe (PID: 3088)
Checks supported languages
- pwsh.exe (PID: 3088)
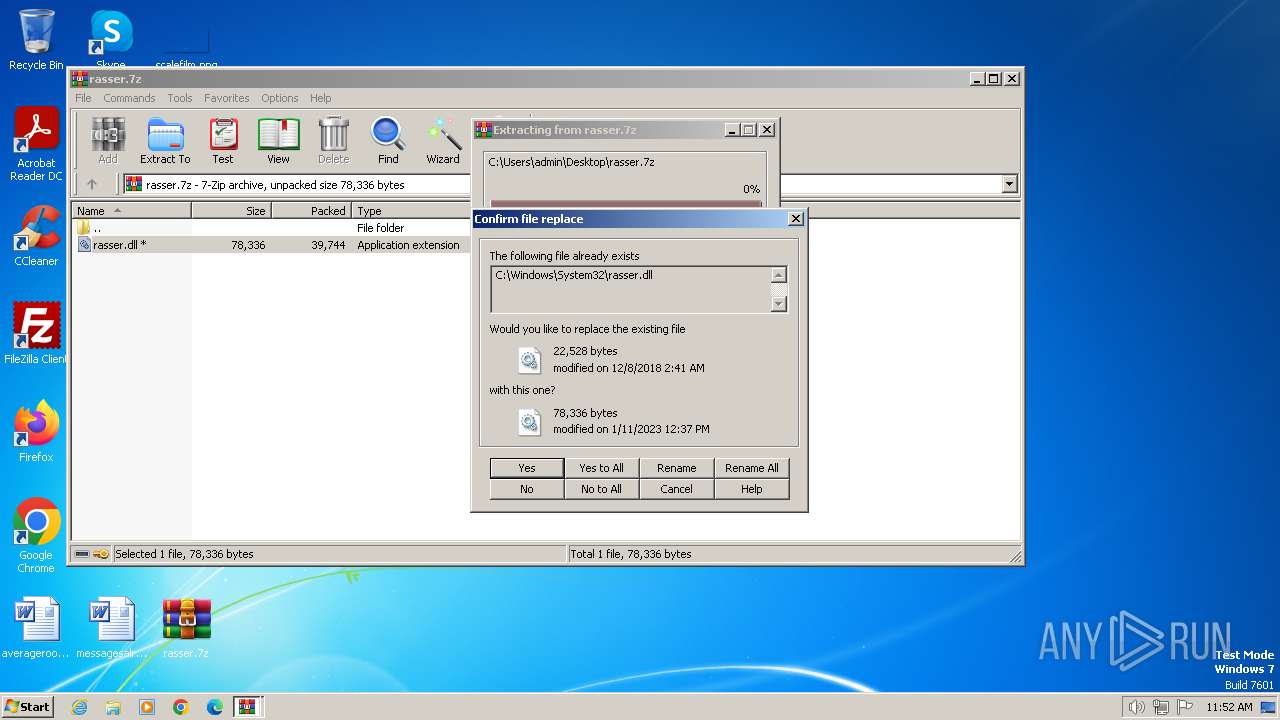
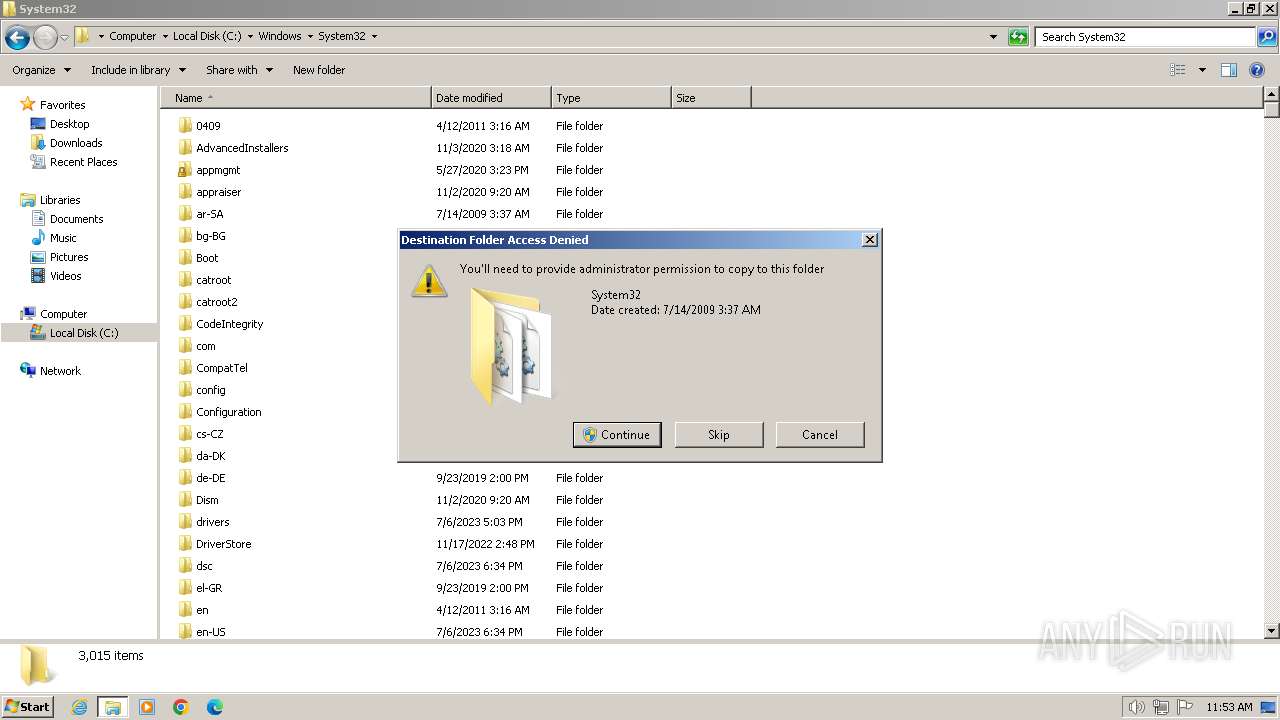
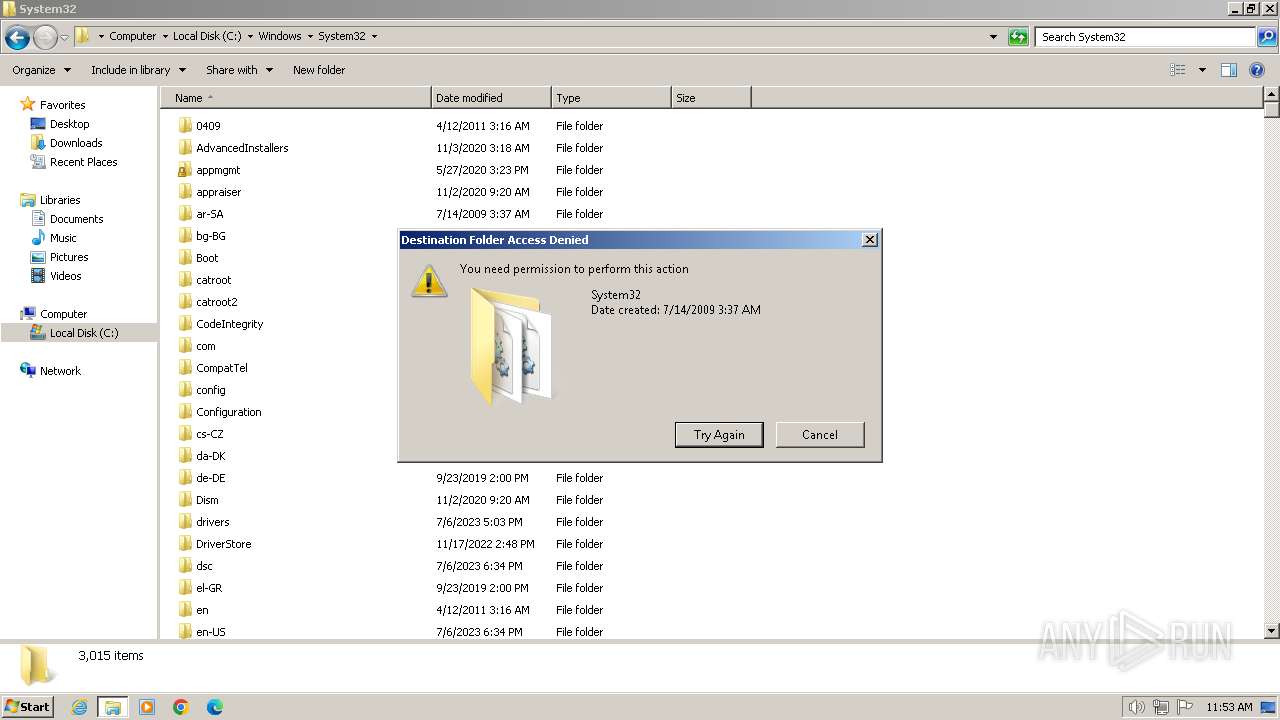
Creates files or folders in the user directory
- mmc.exe (PID: 3156)
- mmc.exe (PID: 3748)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
59
Monitored processes
11
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 584 | "C:\Program Files\WinRAR\WinRAR.exe" -elevate2040 | C:\Program Files\WinRAR\WinRAR.exe | WinRAR.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: HIGH Description: WinRAR archiver Exit code: 9 Version: 5.91.0 Modules
| |||||||||||||||
| 844 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
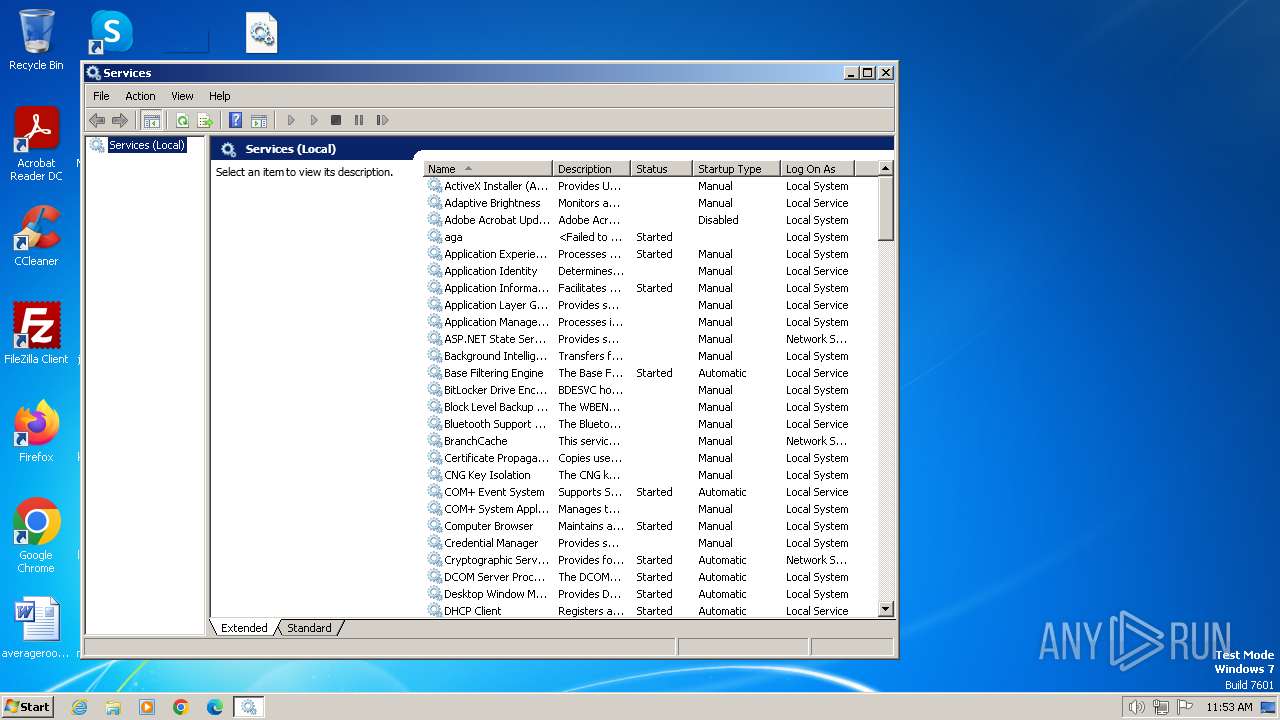
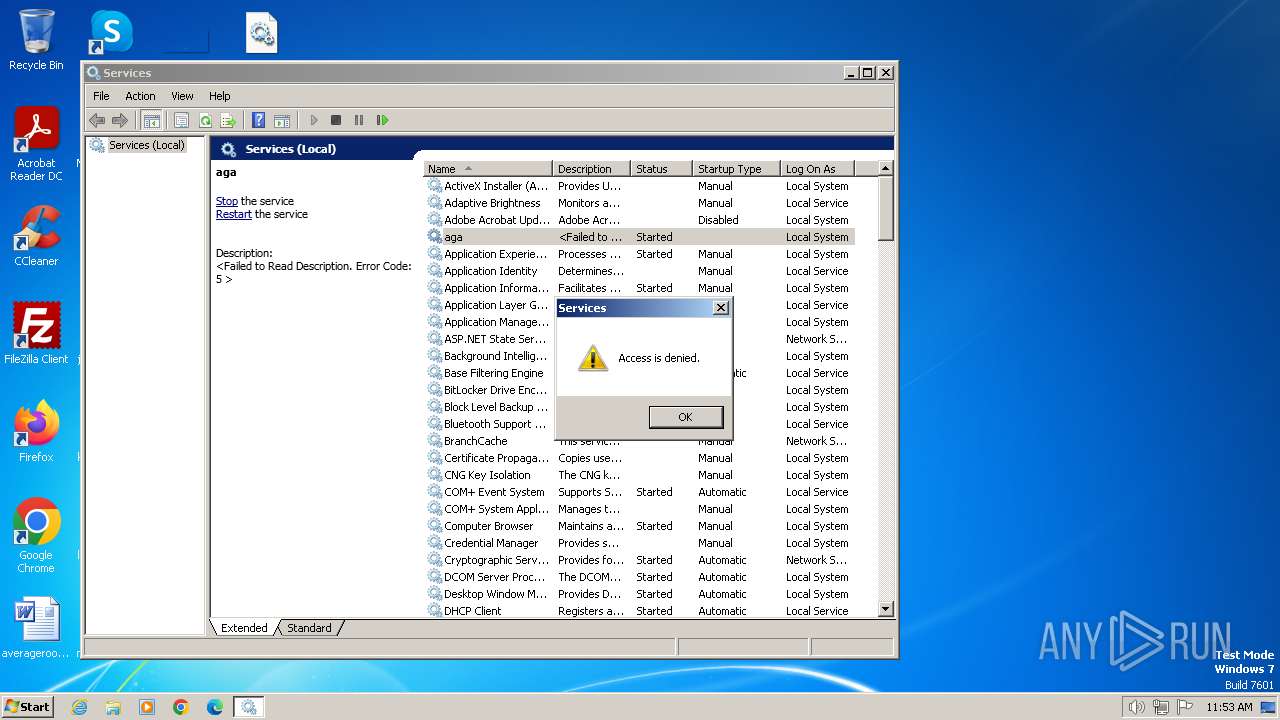
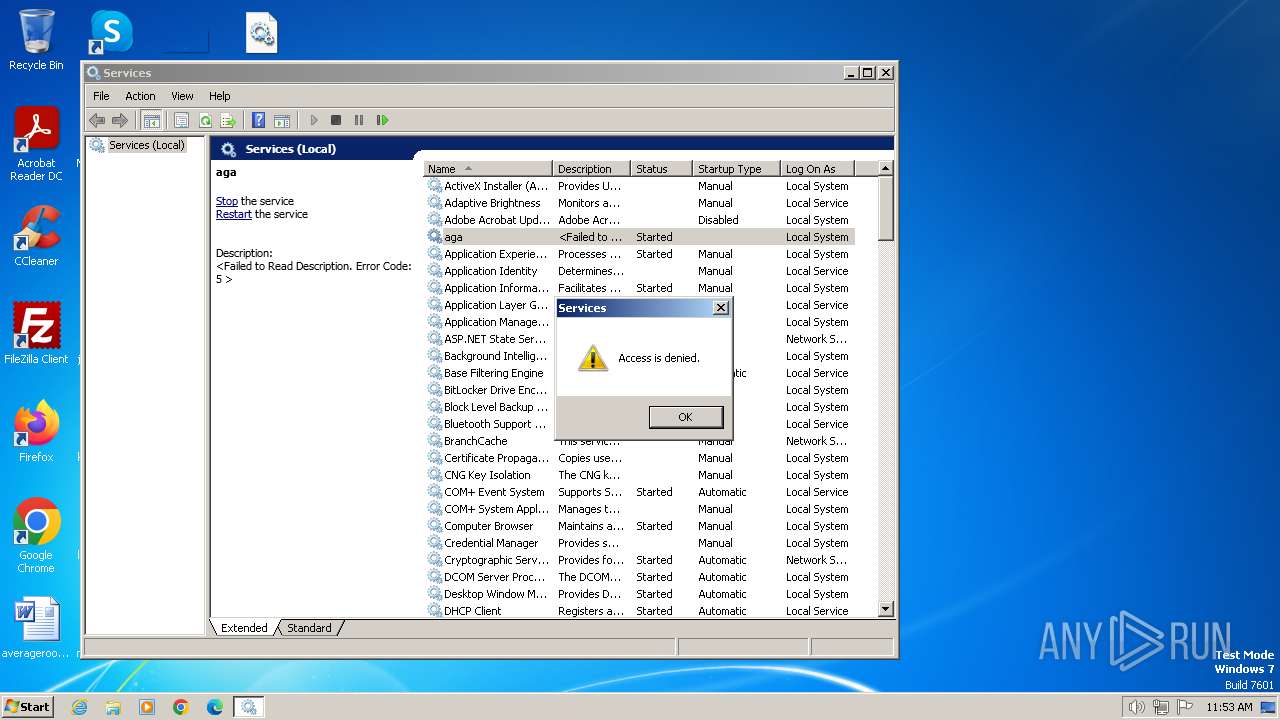
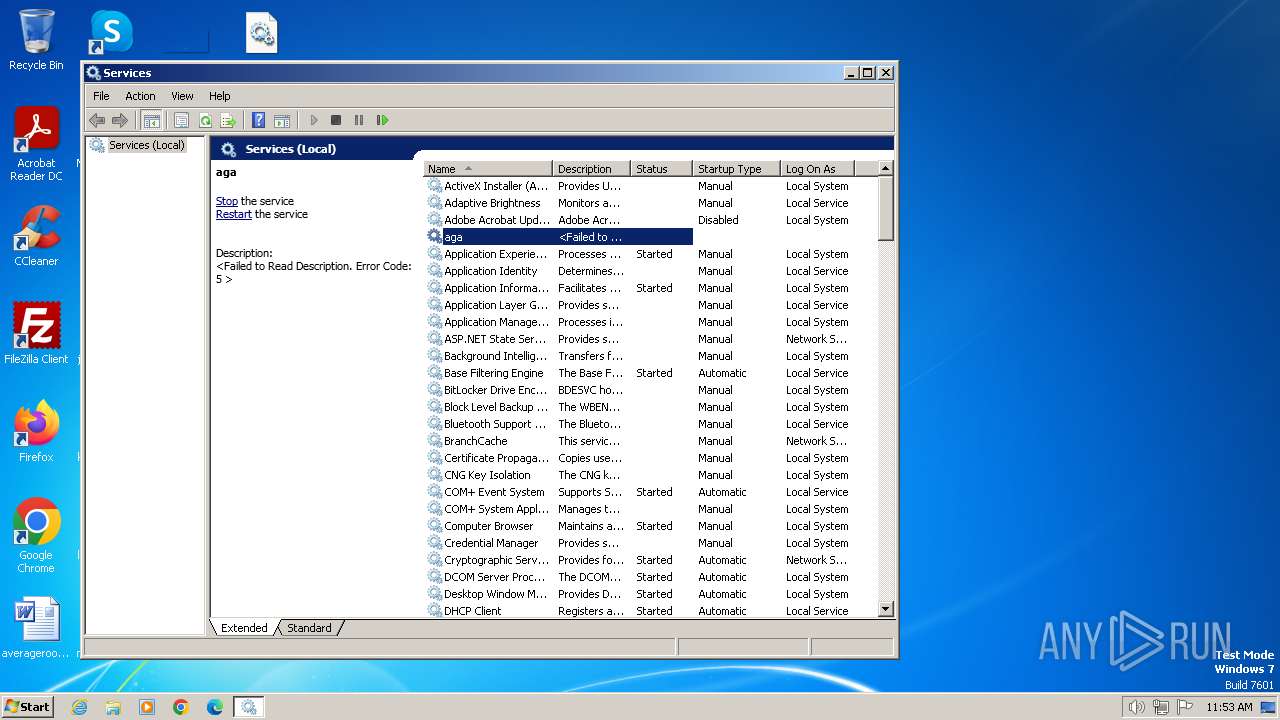
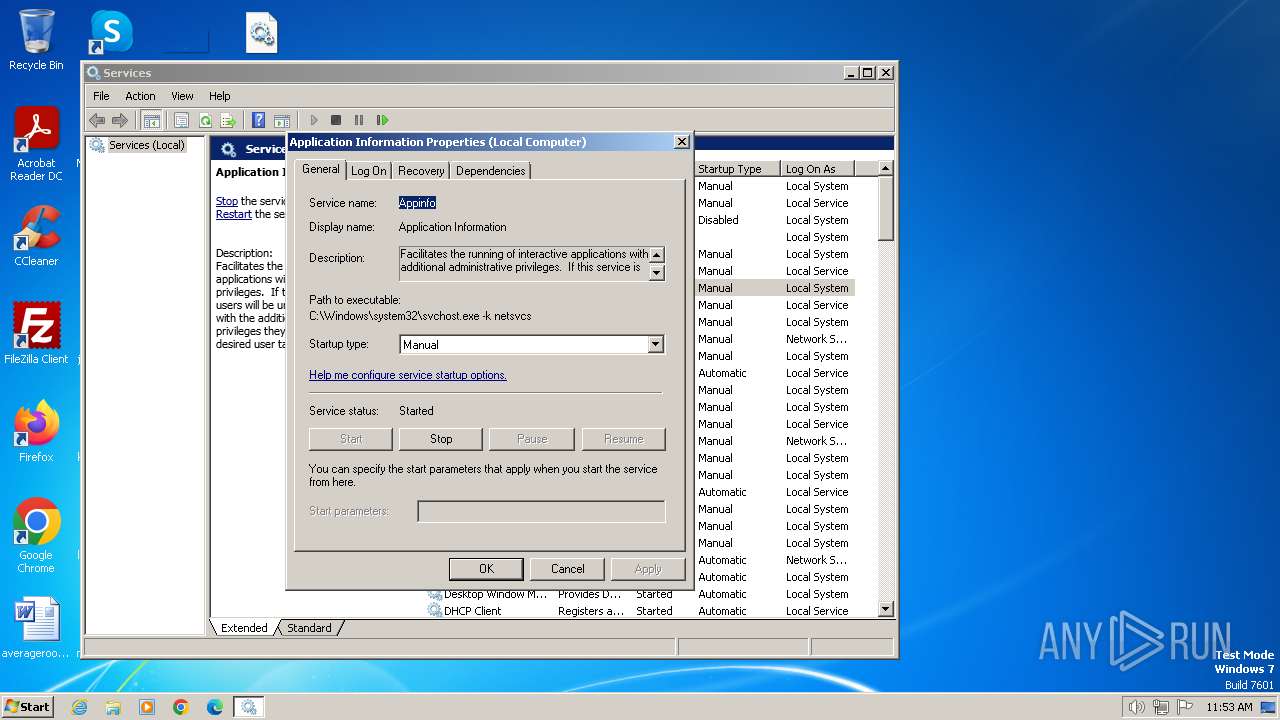
| 900 | "C:\Windows\system32\mmc.exe" "C:\Windows\system32\services.msc" | C:\Windows\System32\mmc.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Management Console Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2040 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\rasser.7z" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2488 | C:\Windows\system32\DllHost.exe /Processid:{3AD05575-8857-4850-9277-11B85BDB8E09} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3088 | "C:\Program Files\PowerShell\7\pwsh.exe" -WorkingDirectory ~ | C:\Program Files\PowerShell\7\pwsh.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: pwsh Exit code: 3221225786 Version: 7.2.11.500 Modules
| |||||||||||||||
| 3156 | "C:\Windows\system32\mmc.exe" "C:\Windows\system32\services.msc" | C:\Windows\System32\mmc.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
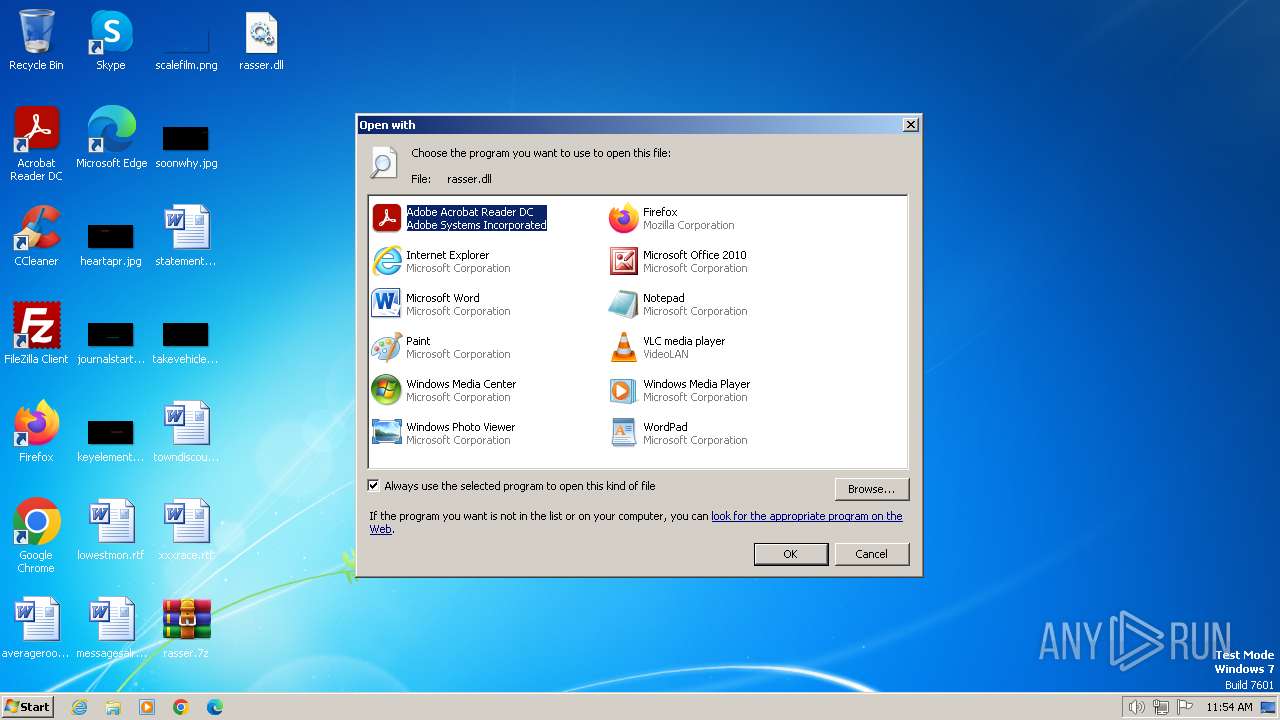
| 3292 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\rasser.dll | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3704 | "C:\Windows\system32\svchost.exe" -rasser .dll | C:\Windows\System32\svchost.exe | — | pwsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3748 | "C:\Windows\system32\mmc.exe" "C:\Windows\system32\services.msc" | C:\Windows\System32\mmc.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
6 908
Read events
6 773
Write events
133
Delete events
2
Modification events
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
1
Suspicious files
4
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3088 | pwsh.exe | C:\Users\admin\AppData\Local\Microsoft\PowerShell\StartupProfileData-Interactive | binary | |
MD5:6F0FBA3CEAFBD0A4414DDC89A9D7B485 | SHA256:1F40559DC733A215C784E5B8C64ACECD1483E352C449238CF43A635E12CCBCAB | |||
| 3088 | pwsh.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\e1a648060a327b80.customDestinations-ms~RF10205b.TMP | binary | |
MD5:A20A86C096ADCB3F2B94729E95AC8359 | SHA256:9B6C50119EFA806C4BD1CD2C2B0A8524F261AA19EC2B882AD52677A2A0ADC273 | |||
| 3088 | pwsh.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_wlrvtzhz.bdh.psm1 | text | |
MD5:FDBC22BDFA128AD922720EE1889FCD41 | SHA256:5EFFF42C7DBD9ACABA592DBA4BCAA9A4146D0523DDA9DD881BF4760B8AFDE139 | |||
| 3088 | pwsh.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\APY2IS6UIUJLK67ARQMD.temp | binary | |
MD5:A20A86C096ADCB3F2B94729E95AC8359 | SHA256:9B6C50119EFA806C4BD1CD2C2B0A8524F261AA19EC2B882AD52677A2A0ADC273 | |||
| 3088 | pwsh.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_jsjuy1ho.whp.ps1 | text | |
MD5:FDBC22BDFA128AD922720EE1889FCD41 | SHA256:5EFFF42C7DBD9ACABA592DBA4BCAA9A4146D0523DDA9DD881BF4760B8AFDE139 | |||
| 3088 | pwsh.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\e1a648060a327b80.customDestinations-ms | binary | |
MD5:A20A86C096ADCB3F2B94729E95AC8359 | SHA256:9B6C50119EFA806C4BD1CD2C2B0A8524F261AA19EC2B882AD52677A2A0ADC273 | |||
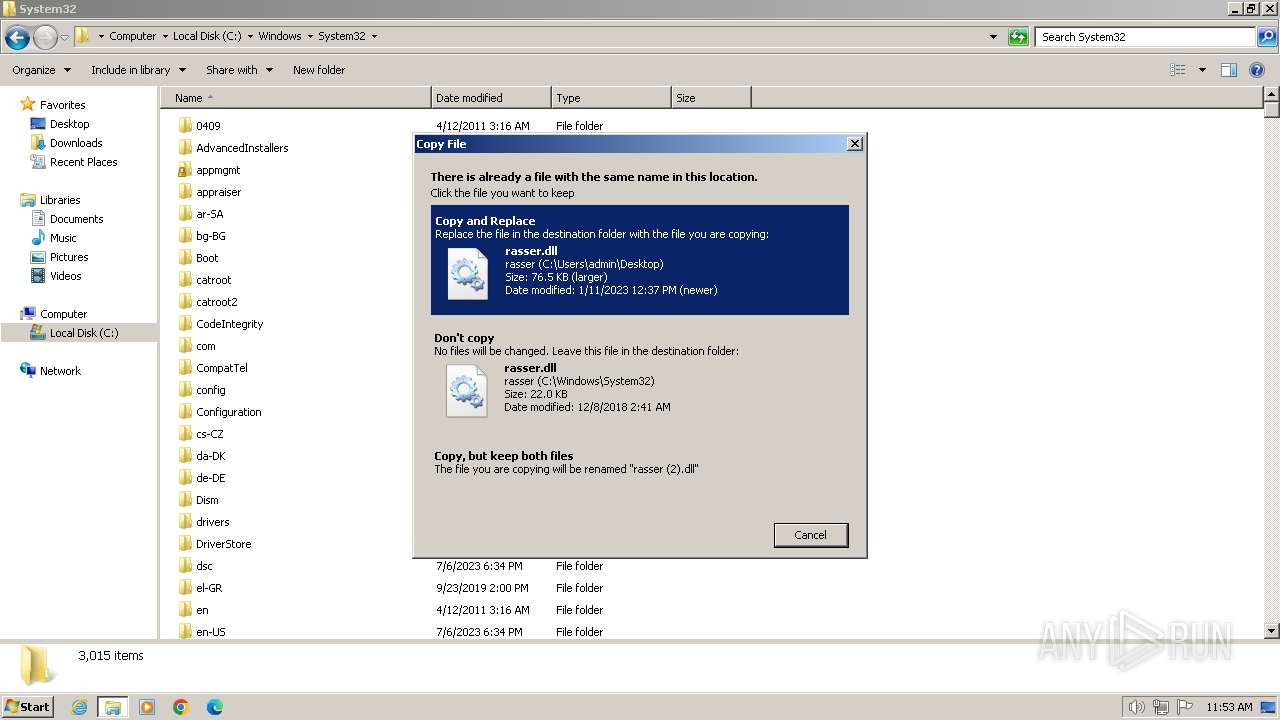
| 2040 | WinRAR.exe | C:\Users\admin\Desktop\rasser.dll | executable | |
MD5:2F48252024AD7719CF451E60547952C3 | SHA256:831ADD6148EFDEDB10159E06F36883BB30EA7969A58AF15D33230750EB222AD8 | |||
| 3088 | pwsh.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt | text | |
MD5:A3E12B61FACEEBD0EC8955E7E866CA1B | SHA256:932902F340F40B7842F91031048B7E7A7DE368ACD7D7D28BE8DC07B429F31E7A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
3
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3088 | pwsh.exe | GET | 404 | 49.13.77.253:443 | https://49.13.77.253/pwsh-buildinfo-stable | unknown | xml | 341 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3088 | pwsh.exe | 49.13.77.253:443 | aka.ms | Hetzner Online GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
aka.ms |
| whitelisted |
dc.services.visualstudio.com |
| unknown |
dns.msftncsi.com |
| shared |
Threats
Process | Message |
|---|---|
pwsh.exe | Profiler was prevented from loading notification profiler due to app settings.
Process ID (decimal): 3088. Message ID: [0x2509].
|