| File name: | GalaxyM63.zip |
| Full analysis: | https://app.any.run/tasks/9419ae1d-d1e7-4cd6-8768-c9ef158173d8 |
| Verdict: | Malicious activity |
| Analysis date: | November 08, 2019, 15:50:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 101357E79A95471EE76A6406A9A20FE9 |
| SHA1: | 1A0EC4DF090F3D347E35859527E8840CD7051FD5 |
| SHA256: | C38FD1ACD0C805C3C1C204C26AA7ECBAE0DC01E0BC106378EC68428569EB9DE4 |
| SSDEEP: | 1536:ozpwdfyCKM4RmRNlaG71p+Sps/gG+6IAaDlu3AsIiJR3z0oEyuQnASQWWH:iq1XTJN31pLps/gGN+Dk3AsIaFuIASk |
MALICIOUS
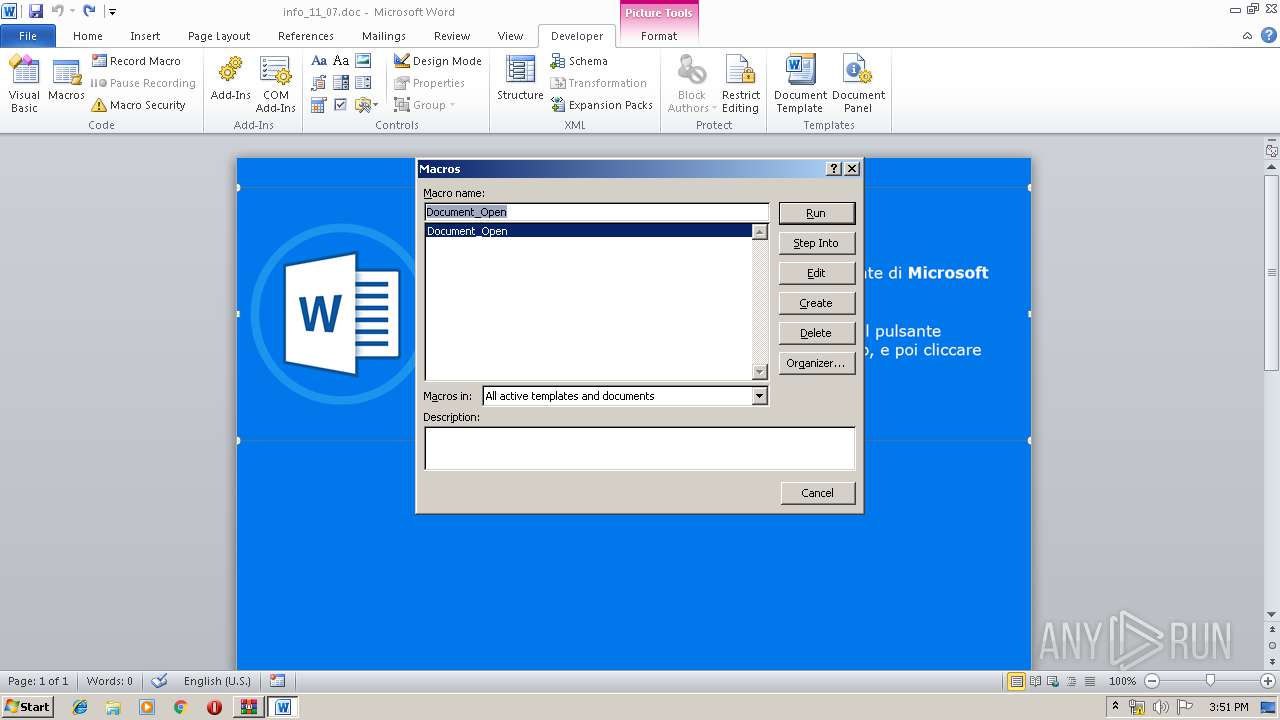
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 3524)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 3524)
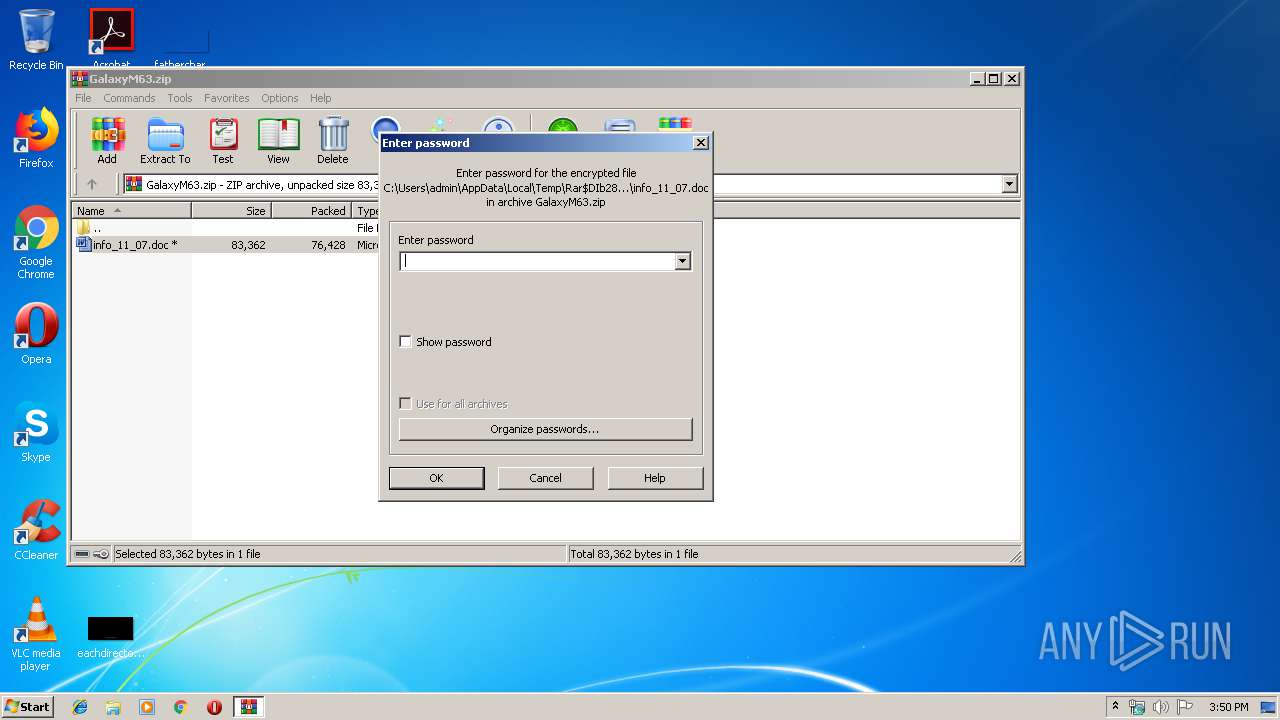
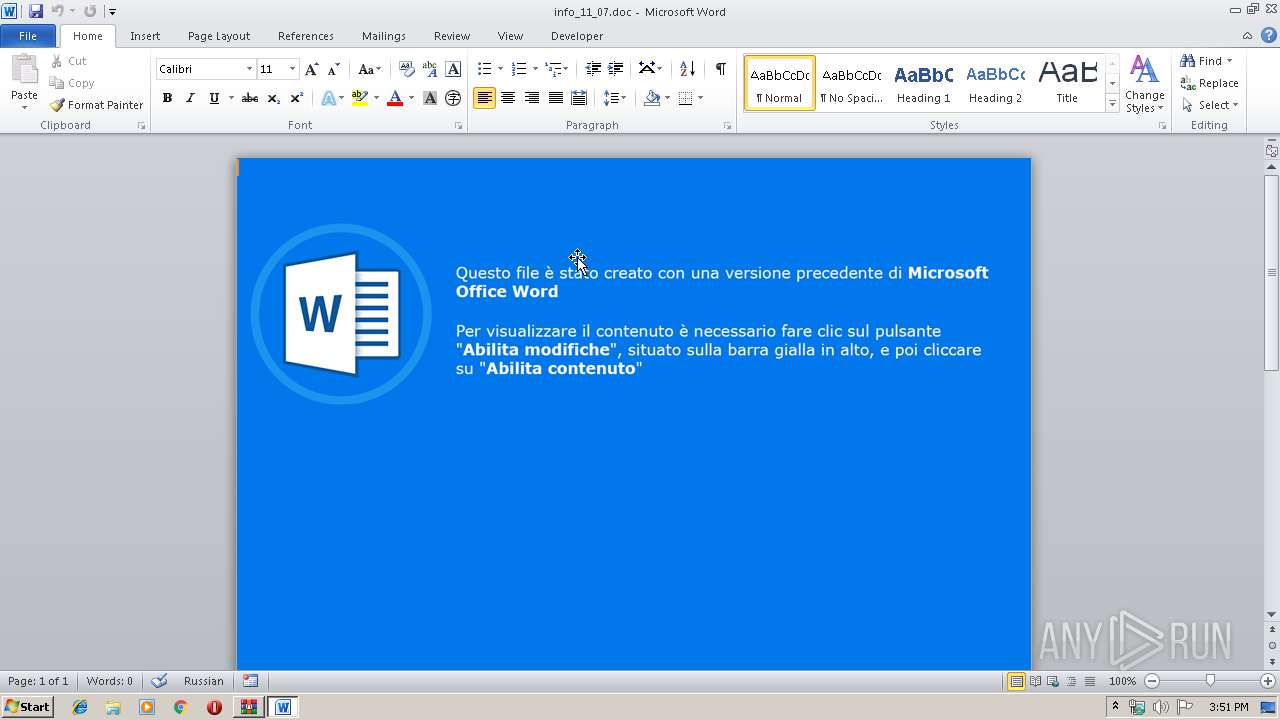
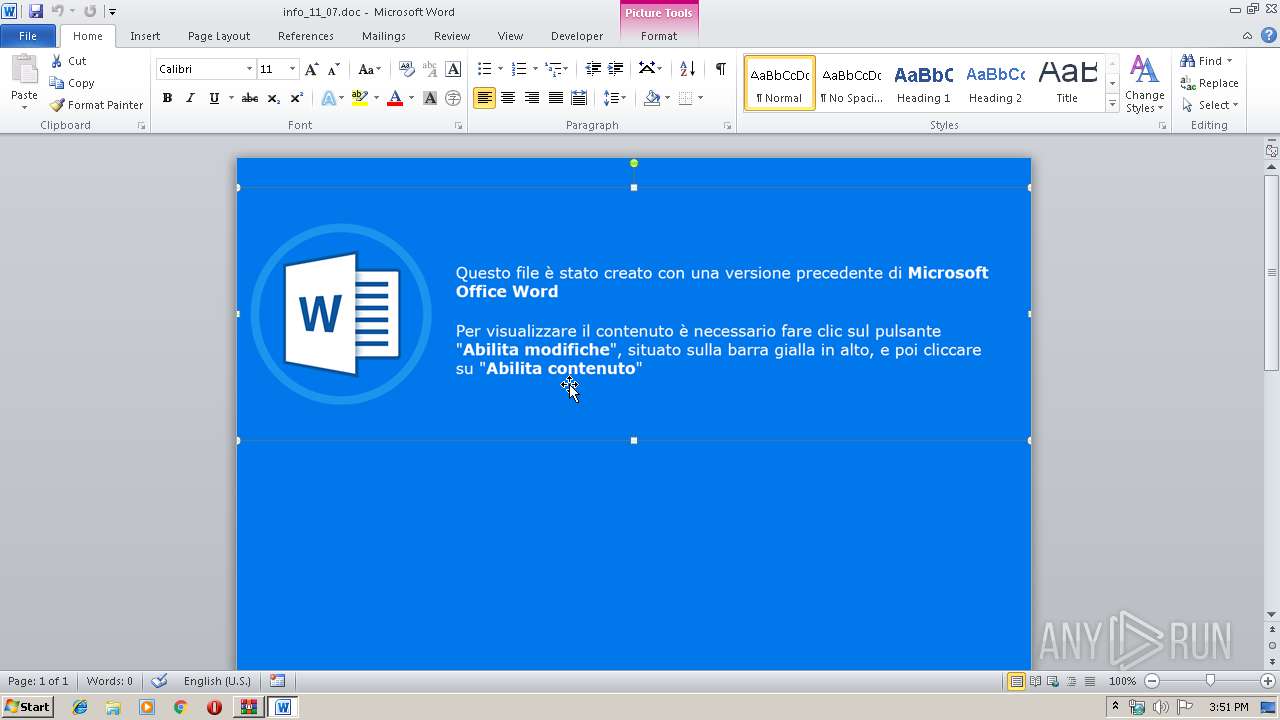
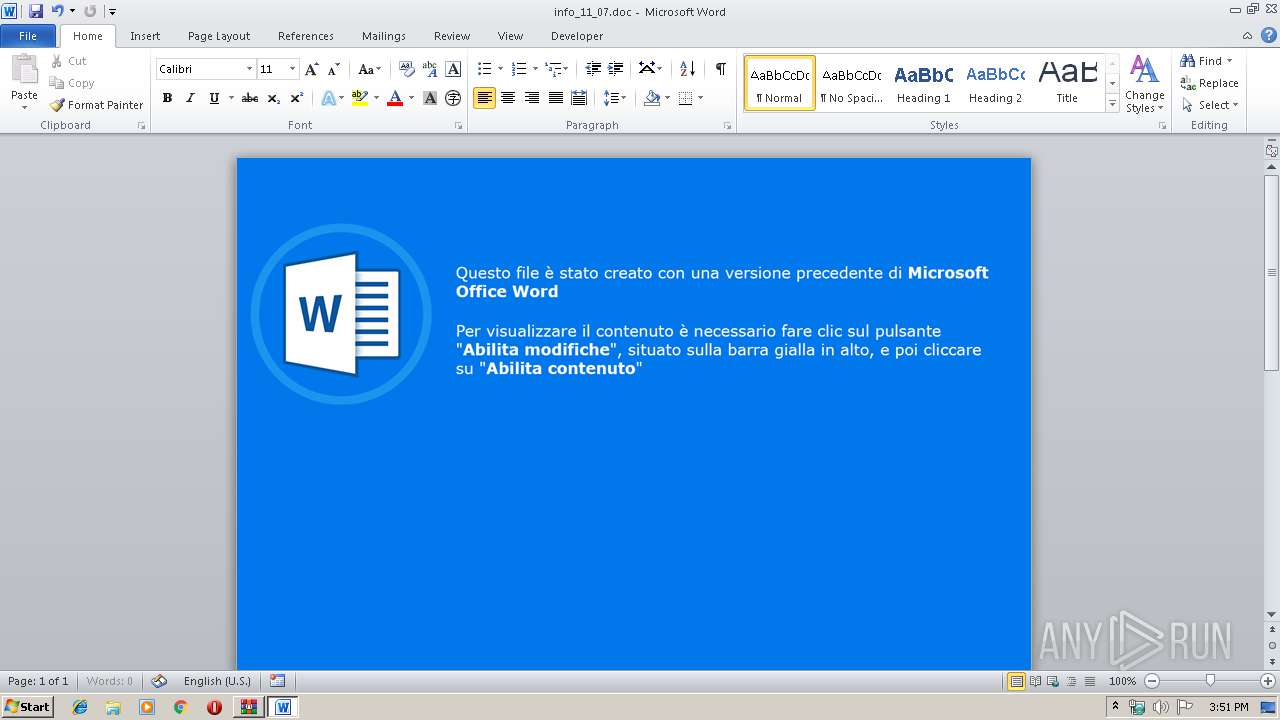
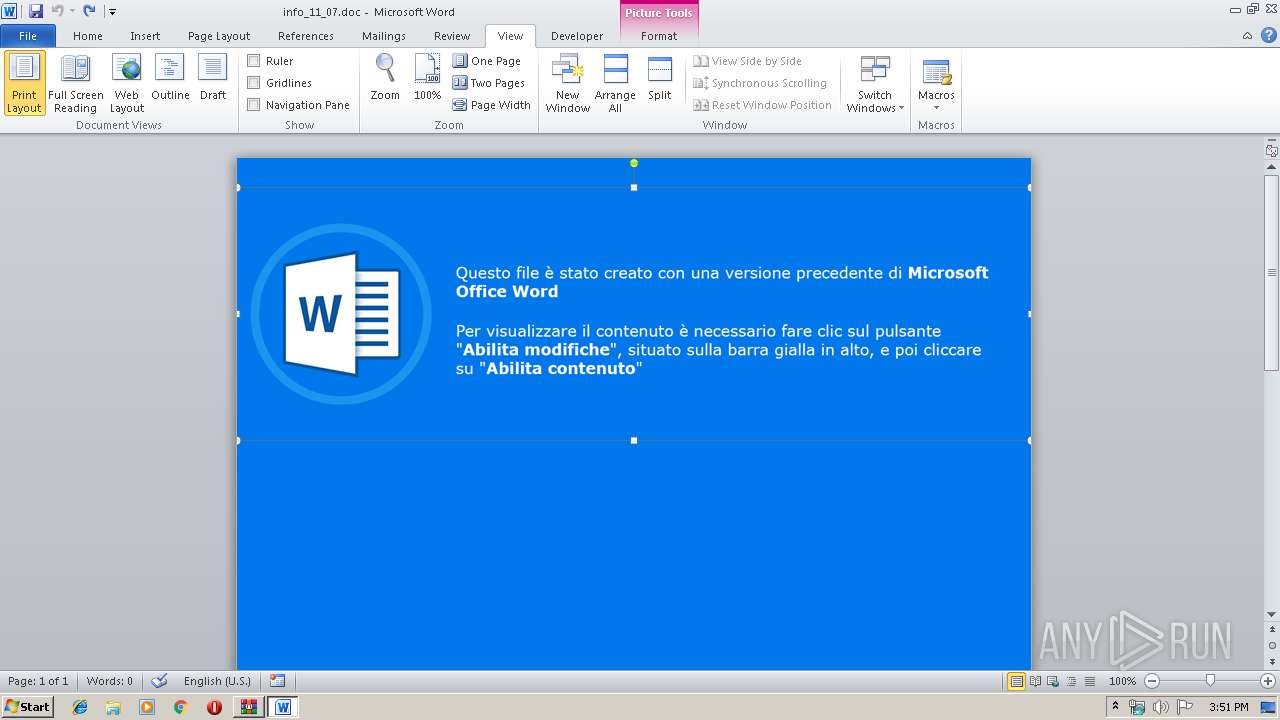
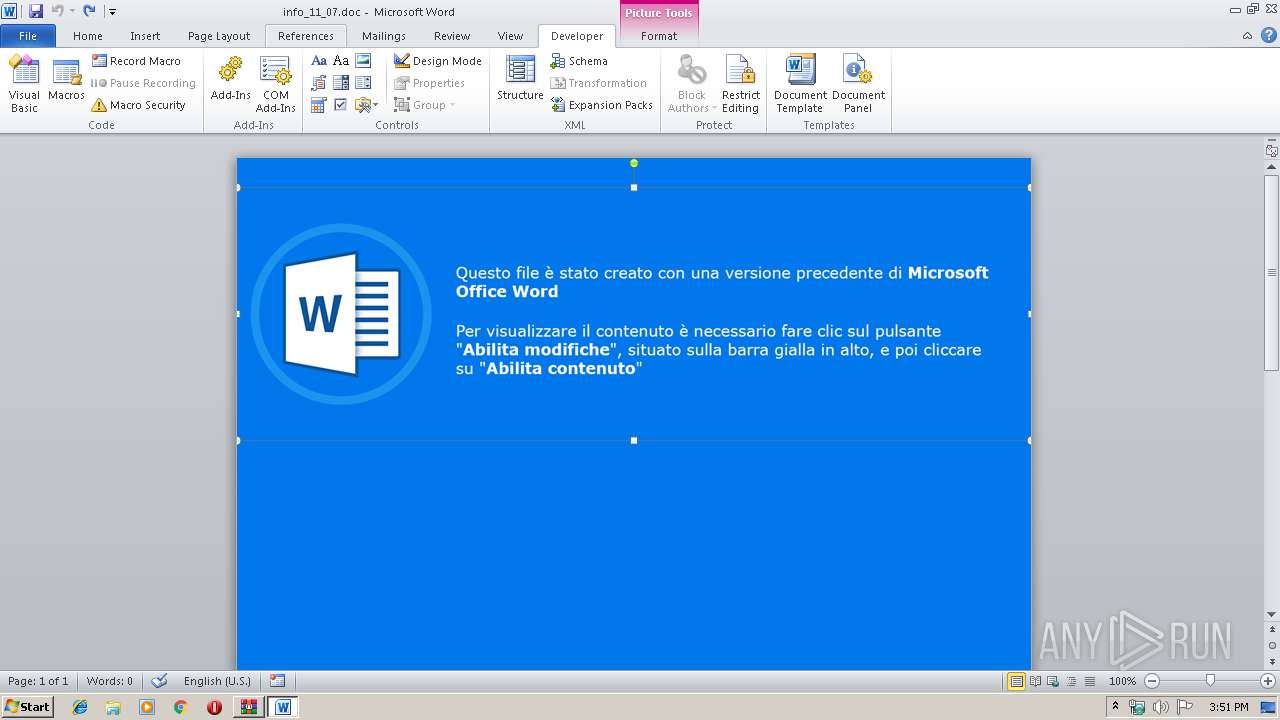
Drops known malicious document
- WinRAR.exe (PID: 2828)
SUSPICIOUS
Uses WMIC.EXE to obtain a system information
- cmd.exe (PID: 3348)
Starts Microsoft Office Application
- WinRAR.exe (PID: 2828)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 3524)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3524)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:11:07 03:37:17 |
| ZipCRC: | 0x2fc39932 |
| ZipCompressedSize: | 76428 |
| ZipUncompressedSize: | 83362 |
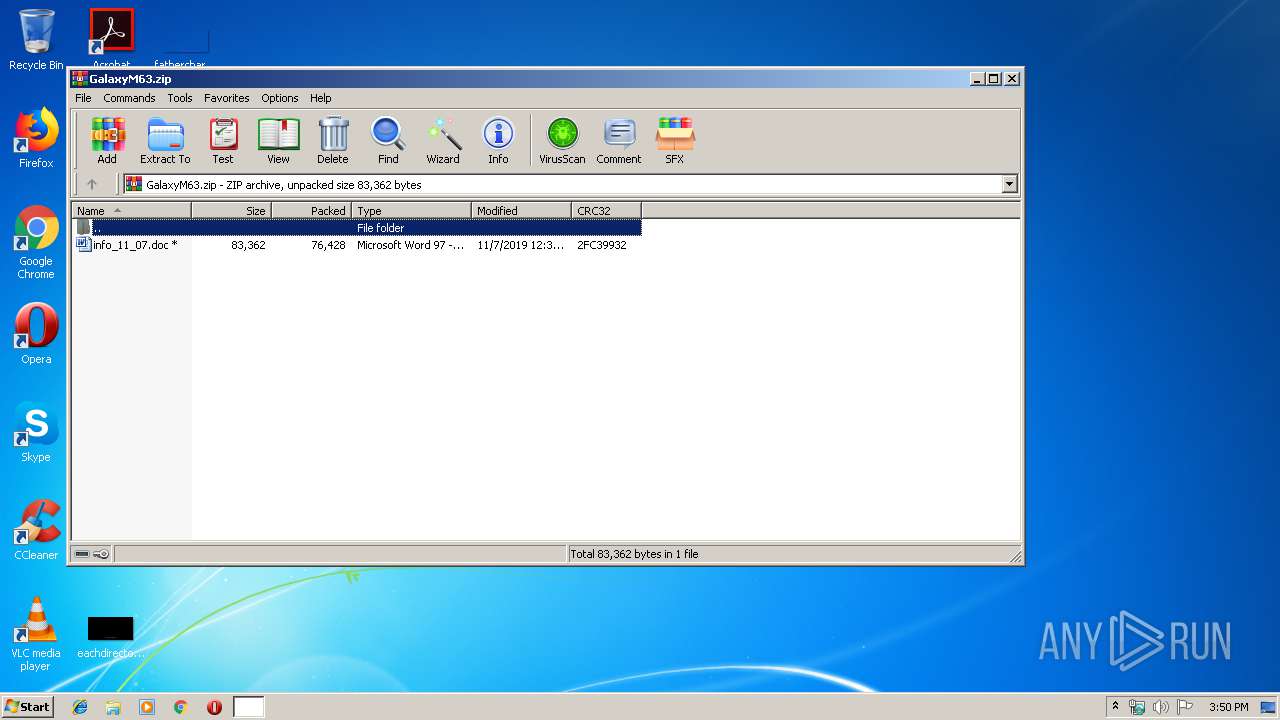
| ZipFileName: | info_11_07.doc |
Total processes
42
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1976 | "C:\Windows\System32\cmd.exe" /c wmic process list /format:"C:\Users\admin\AppData\Local\Temp\aWtKUm" | C:\Windows\System32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | |||||||||||||||
| 2828 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\GalaxyM63.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2868 | wmic process list /format:"C:\Users\admin\AppData\Local\Temp\aWtKUm" | C:\Windows\System32\Wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 2147614729 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3348 | "C:\Windows\System32\cmd.exe" /c wmic process list /format:"C:\Users\admin\AppData\Local\Temp\aWtKUm" | C:\Windows\System32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 2147614729 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3524 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Rar$DIb2828.23650\info_11_07.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
2 813
Read events
1 600
Write events
1 039
Delete events
174
Modification events
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\GalaxyM63.zip | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1332215870 | |||
Executable files
0
Suspicious files
2
Text files
1
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3524 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRDFEB.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3524 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 3524 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Rar$DIb2828.23650\~$fo_11_07.doc | pgc | |
MD5:— | SHA256:— | |||
| 3524 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb2828.23650\info_11_07.doc | document | |
MD5:— | SHA256:— | |||
| 3524 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\aWtKUm.xsl | xml | |
MD5:— | SHA256:— | |||
| 3524 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\MSO1049.acl | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Domain | IP | Reputation |
|---|---|---|
xvobvgcssb.com |
| unknown |