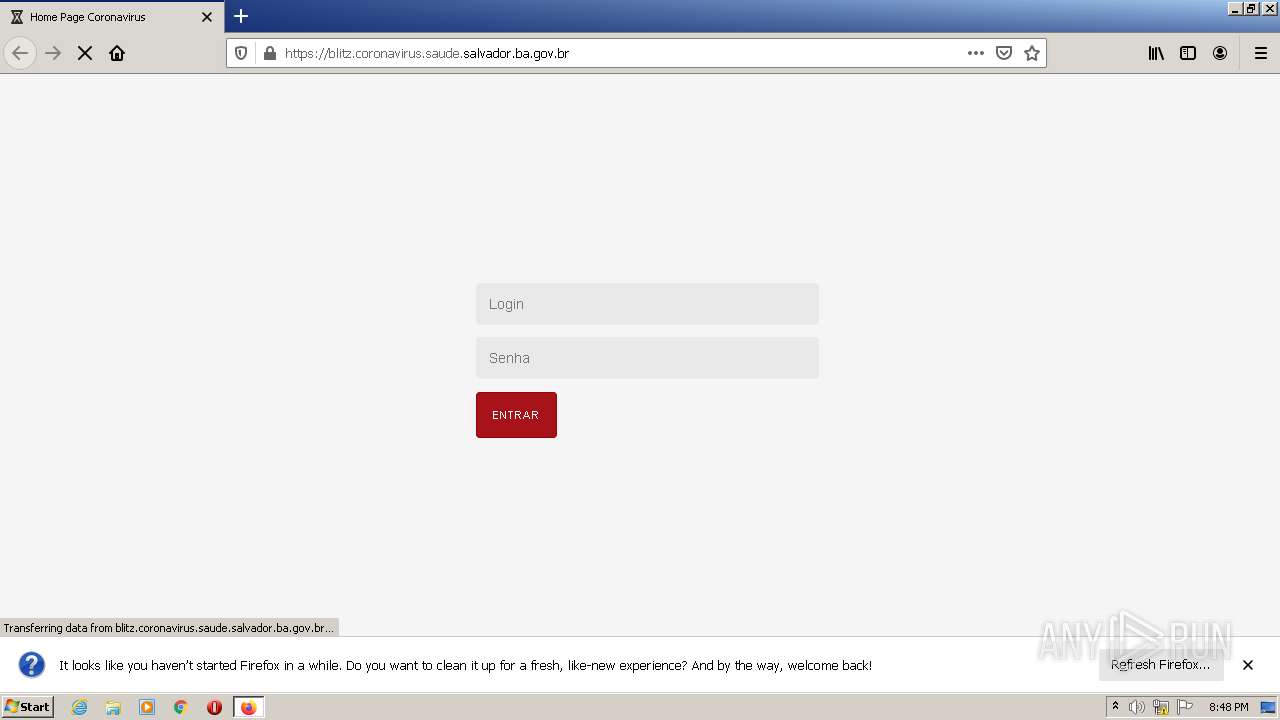
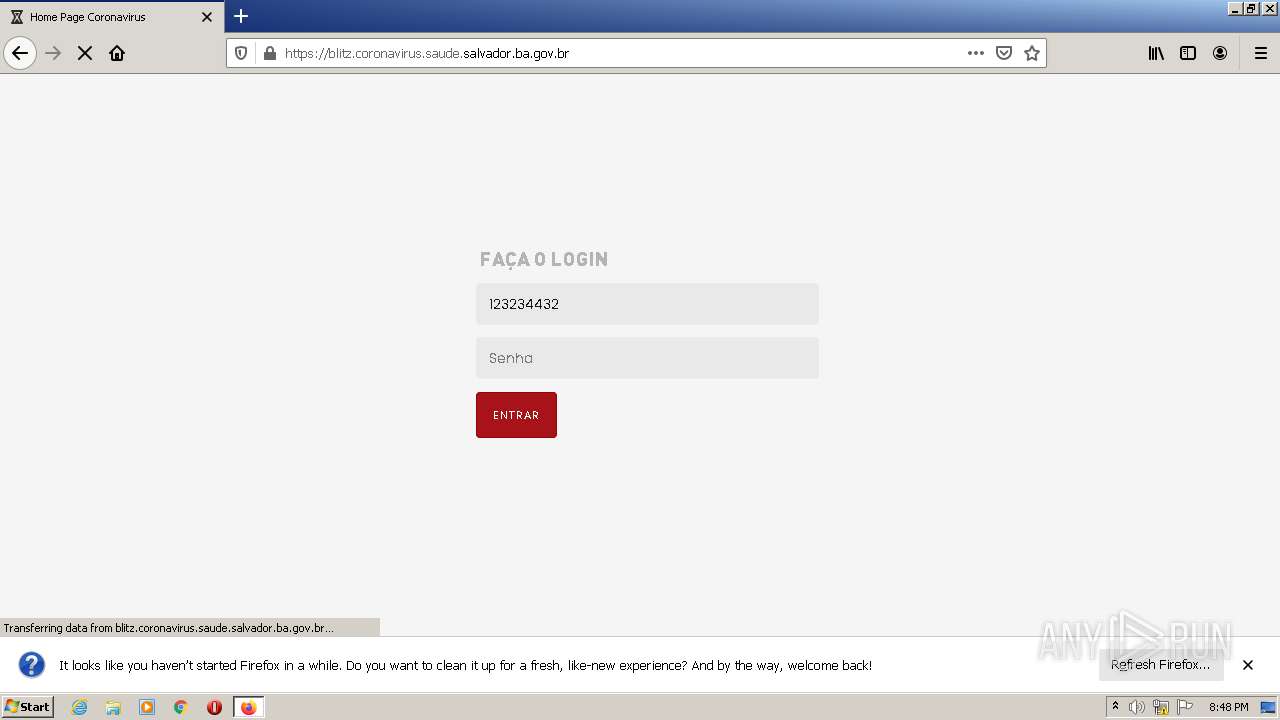
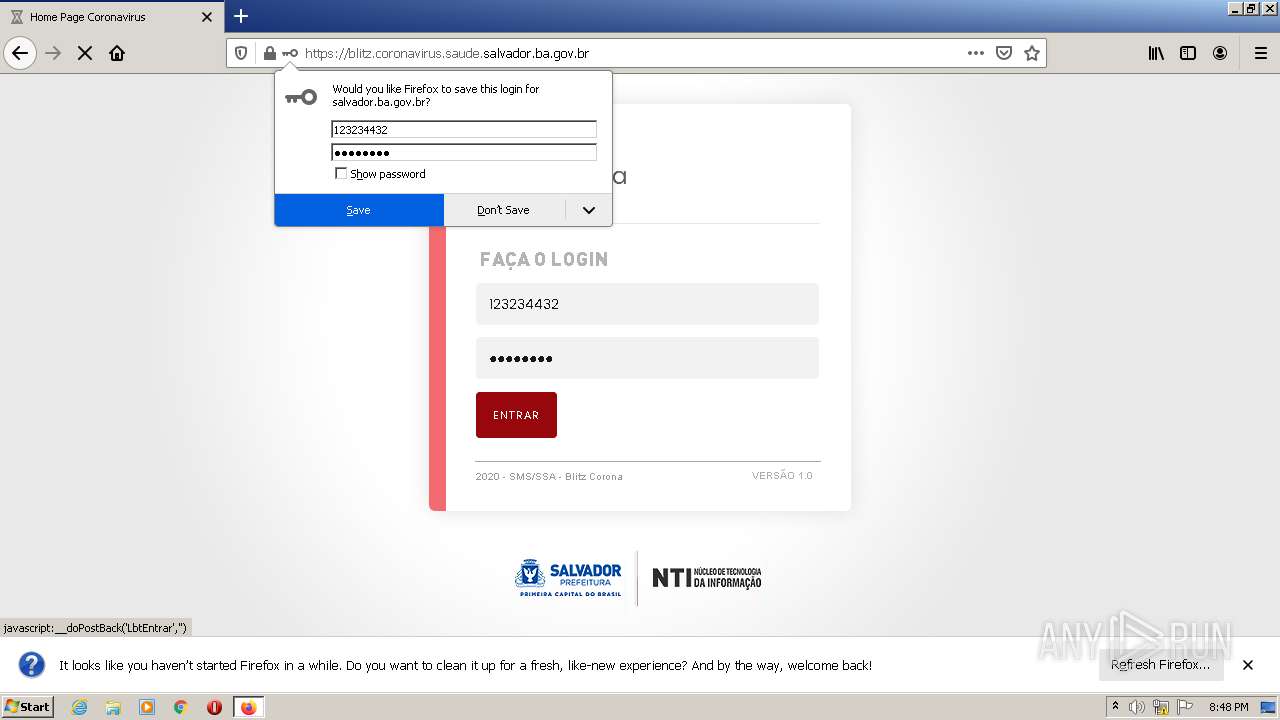
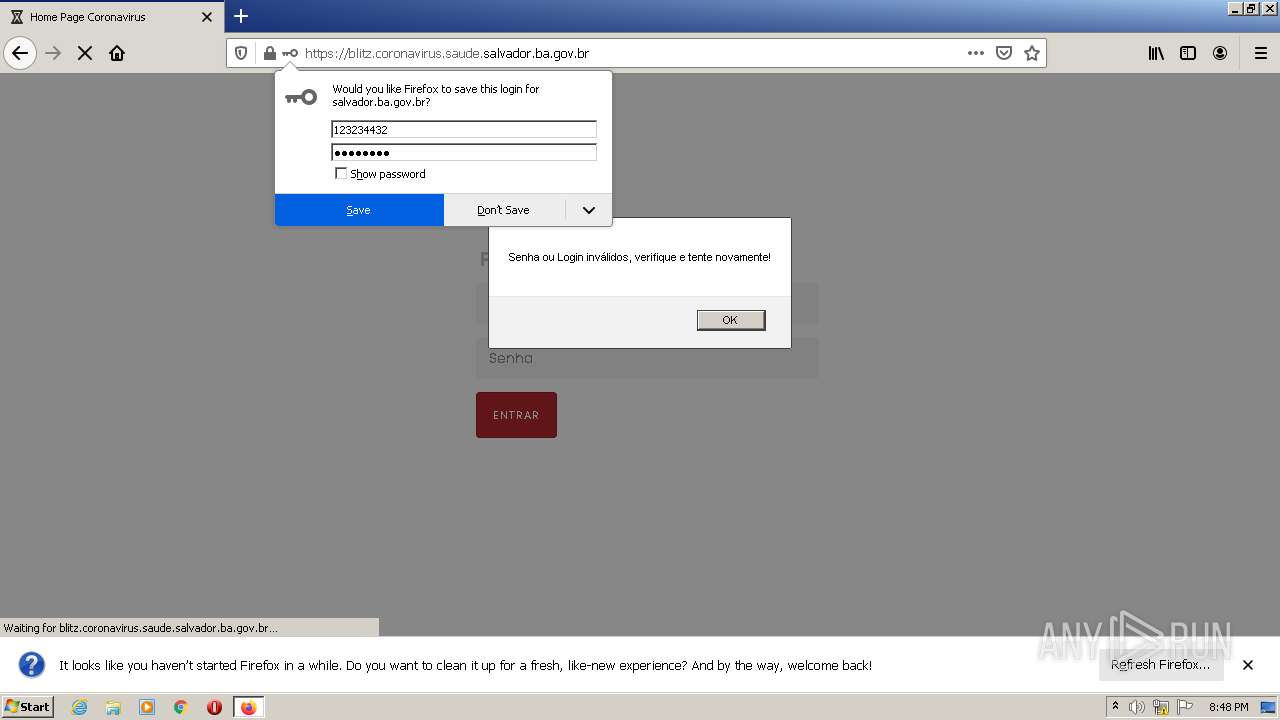
| URL: | http://blitz.coronavirus.saude.salvador.ba.gov.br/ |
| Full analysis: | https://app.any.run/tasks/1c7a40b6-b142-406f-b2d5-aeb773ba2197 |
| Verdict: | Malicious activity |
| Analysis date: | January 14, 2022, 20:48:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 43E9CC177BCA2D306C76C0ECFFD1A2A7 |
| SHA1: | 66A620D960ACA6BF225B1FD9682517872B02C082 |
| SHA256: | C3620326664CFC19F005E4EEF088D72CFE41854384D0031AFCF4CFA7AFFBD606 |
| SSDEEP: | 3:N1Kc9KAET5w8TLHa:Cc9KF5w8Tza |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- firefox.exe (PID: 3572)
Drops a file that was compiled in debug mode
- firefox.exe (PID: 3572)
INFO
Checks supported languages
- firefox.exe (PID: 2172)
- firefox.exe (PID: 3572)
- firefox.exe (PID: 2780)
- firefox.exe (PID: 2224)
- firefox.exe (PID: 3072)
- firefox.exe (PID: 3044)
- firefox.exe (PID: 120)
- firefox.exe (PID: 3604)
Application launched itself
- firefox.exe (PID: 2172)
- firefox.exe (PID: 3572)
Creates files in the program directory
- firefox.exe (PID: 3572)
Reads CPU info
- firefox.exe (PID: 3572)
Reads the computer name
- firefox.exe (PID: 3572)
- firefox.exe (PID: 3072)
- firefox.exe (PID: 2780)
- firefox.exe (PID: 2224)
- firefox.exe (PID: 120)
- firefox.exe (PID: 3044)
- firefox.exe (PID: 3604)
Reads the date of Windows installation
- firefox.exe (PID: 3572)
Creates files in the user directory
- firefox.exe (PID: 3572)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
42
Monitored processes
8
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3572.13.1893343306\706334963" -childID 2 -isForBrowser -prefsHandle 2080 -prefMapHandle 2044 -prefsLen 6644 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 3572 "\\.\pipe\gecko-crash-server-pipe.3572" 2064 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 2172 | "C:\Program Files\Mozilla Firefox\firefox.exe" "http://blitz.coronavirus.saude.salvador.ba.gov.br/" | C:\Program Files\Mozilla Firefox\firefox.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 2224 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3572.0.2004164357\281959064" -parentBuildID 20201112153044 -prefsHandle 1096 -prefMapHandle 836 -prefsLen 1 -prefMapSize 238726 -appdir "C:\Program Files\Mozilla Firefox\browser" - 3572 "\\.\pipe\gecko-crash-server-pipe.3572" 1192 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 2780 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3572.20.1699599980\642646350" -childID 3 -isForBrowser -prefsHandle 3392 -prefMapHandle 3468 -prefsLen 7307 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 3572 "\\.\pipe\gecko-crash-server-pipe.3572" 3512 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 3044 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3572.21.1853886829\1411147693" -childID 4 -isForBrowser -prefsHandle 3524 -prefMapHandle 2660 -prefsLen 7307 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 3572 "\\.\pipe\gecko-crash-server-pipe.3572" 3552 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 3072 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3572.6.890329556\242117353" -childID 1 -isForBrowser -prefsHandle 2984 -prefMapHandle 2980 -prefsLen 181 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 3572 "\\.\pipe\gecko-crash-server-pipe.3572" 2996 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 3572 | "C:\Program Files\Mozilla Firefox\firefox.exe" http://blitz.coronavirus.saude.salvador.ba.gov.br/ | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 3604 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3572.34.1537468122\1549518075" -childID 5 -isForBrowser -prefsHandle 3828 -prefMapHandle 3848 -prefsLen 7378 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 3572 "\\.\pipe\gecko-crash-server-pipe.3572" 3860 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
Total events
9 723
Read events
9 699
Write events
24
Delete events
0
Modification events
| (PID) Process: | (2172) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: C432CD4129000000 | |||
| (PID) Process: | (3572) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 2D3CCD4129000000 | |||
| (PID) Process: | (3572) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 0 | |||
| (PID) Process: | (3572) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (3572) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 1 | |||
| (PID) Process: | (3572) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableDefaultBrowserAgent |
Value: 0 | |||
| (PID) Process: | (3572) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|ServicesSettingsServer |
Value: https://firefox.settings.services.mozilla.com/v1 | |||
| (PID) Process: | (3572) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|SecurityContentSignatureRootHash |
Value: 97:E8:BA:9C:F1:2F:B3:DE:53:CC:42:A4:E6:57:7E:D6:4D:F4:93:C2:47:B4:14:FE:A0:36:81:8D:38:23:56:0E | |||
| (PID) Process: | (3572) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3572) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000003B010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A80164000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
4
Suspicious files
135
Text files
55
Unknown types
33
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3572 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 3572 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 3572 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-wal | binary | |
MD5:— | SHA256:— | |||
| 3572 | firefox.exe | C:\Users\admin\AppData\Local\Temp\mz_etilqs_jeCkpSUgBmTbp45 | binary | |
MD5:— | SHA256:— | |||
| 3572 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs-1.js | text | |
MD5:299A2B747C11E4BDA194E563FEA4A699 | SHA256:94EE461F62E8B4A0A65471A41E10C8C56722B73C0A019D76ACA7F5BAF109813E | |||
| 3572 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\settings\main\ms-language-packs\asrouter.ftl.tmp | text | |
MD5:— | SHA256:— | |||
| 3572 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3572 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\settings\main\ms-language-packs\asrouter.ftl | text | |
MD5:— | SHA256:— | |||
| 3572 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:994A33896BB41A278A315D0D796422B6 | SHA256:54EC50A20FFF8CC016710E49437CF6A11D3FE5EE7B28C185E4A9AAFEE2908B63 | |||
| 3572 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
80
DNS requests
86
Threats
29
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3572 | firefox.exe | POST | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gts1c3 | US | der | 471 b | whitelisted |
3572 | firefox.exe | GET | 301 | 177.20.6.55:80 | http://blitz.coronavirus.saude.salvador.ba.gov.br/ | BR | — | — | suspicious |
3572 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3572 | firefox.exe | POST | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gts1c3 | US | der | 471 b | whitelisted |
3572 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3572 | firefox.exe | POST | 200 | 2.16.186.10:80 | http://r3.o.lencr.org/ | unknown | der | 503 b | shared |
3572 | firefox.exe | POST | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gts1c3 | US | der | 471 b | whitelisted |
3572 | firefox.exe | POST | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gts1c3 | US | der | 472 b | whitelisted |
3572 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3572 | firefox.exe | POST | 200 | 2.16.186.10:80 | http://r3.o.lencr.org/ | unknown | der | 503 b | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3572 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | — | US | whitelisted |
3572 | firefox.exe | 177.20.6.55:80 | blitz.coronavirus.saude.salvador.ba.gov.br | Companhia de Governança Eletrônica do Salvador | BR | suspicious |
3572 | firefox.exe | 35.163.35.154:443 | location.services.mozilla.com | Amazon.com, Inc. | US | unknown |
3572 | firefox.exe | 177.20.6.55:443 | blitz.coronavirus.saude.salvador.ba.gov.br | Companhia de Governança Eletrônica do Salvador | BR | suspicious |
3572 | firefox.exe | 142.250.186.42:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
3572 | firefox.exe | 44.238.207.206:443 | push.services.mozilla.com | University of California, San Diego | US | unknown |
3572 | firefox.exe | 13.32.121.84:443 | firefox-settings-attachments.cdn.mozilla.net | Amazon.com, Inc. | US | suspicious |
3572 | firefox.exe | 13.32.121.7:443 | firefox.settings.services.mozilla.com | Amazon.com, Inc. | US | suspicious |
3572 | firefox.exe | 13.32.121.112:443 | snippets.cdn.mozilla.net | Amazon.com, Inc. | US | unknown |
3572 | firefox.exe | 18.66.139.67:443 | content-signature-2.cdn.mozilla.net | Massachusetts Institute of Technology | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
blitz.coronavirus.saude.salvador.ba.gov.br |
| suspicious |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
firefox.settings.services.mozilla.com |
| whitelisted |
location.services.mozilla.com |
| whitelisted |
locprod2-elb-us-west-2.prod.mozaws.net |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
content-signature-2.cdn.mozilla.net |
| whitelisted |
d2nxq2uap88usk.cloudfront.net |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET INFO Suspicious Domain Request for Possible COVID-19 Domain M2 |
— | — | Potentially Bad Traffic | ET INFO Suspicious Domain Request for Possible COVID-19 Domain M2 |
— | — | Potentially Bad Traffic | ET INFO Suspicious Domain Request for Possible COVID-19 Domain M2 |
3572 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
3572 | firefox.exe | Potentially Bad Traffic | ET INFO Suspicious GET Request with Possible COVID-19 Domain M2 |
3572 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
3572 | firefox.exe | Potentially Bad Traffic | ET INFO Suspicious TLS SNI Request for Possible COVID-19 Domain M2 |
3572 | firefox.exe | Potentially Bad Traffic | ET INFO Suspicious TLS SNI Request for Possible COVID-19 Domain M2 |
3572 | firefox.exe | Potentially Bad Traffic | ET INFO Suspicious TLS SNI Request for Possible COVID-19 Domain M2 |
3572 | firefox.exe | Potentially Bad Traffic | ET INFO Suspicious TLS SNI Request for Possible COVID-19 Domain M2 |