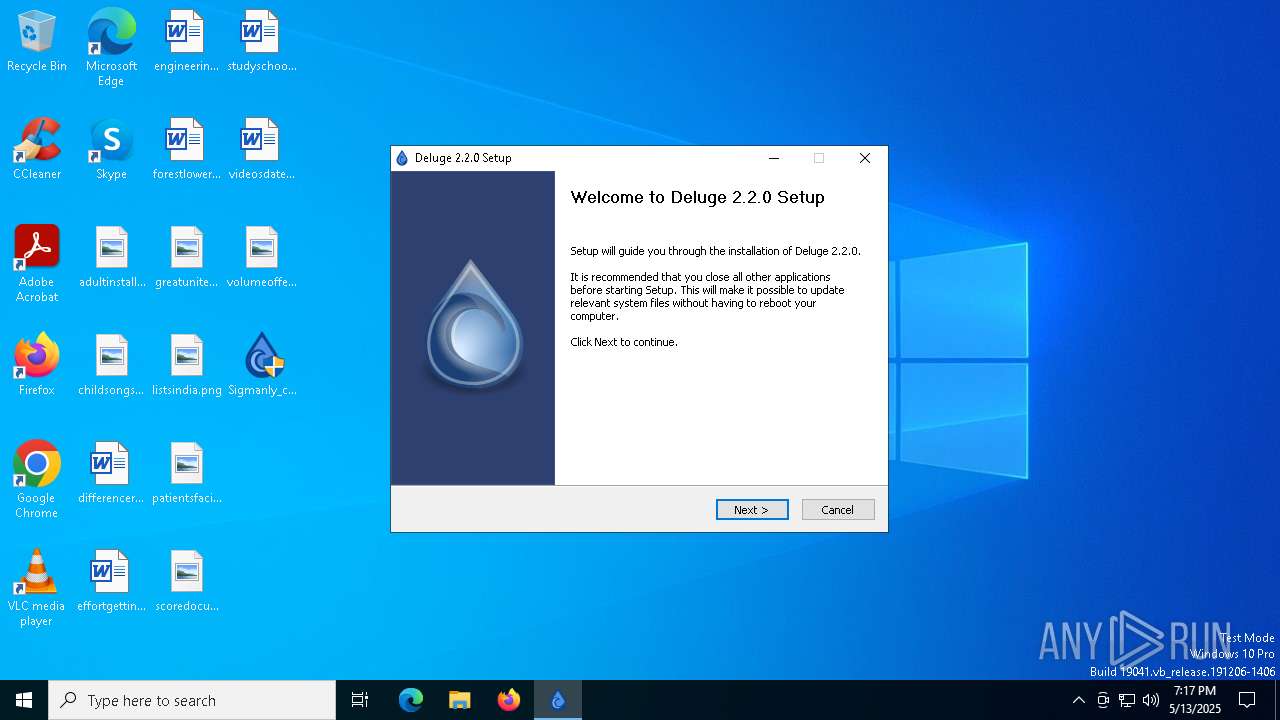
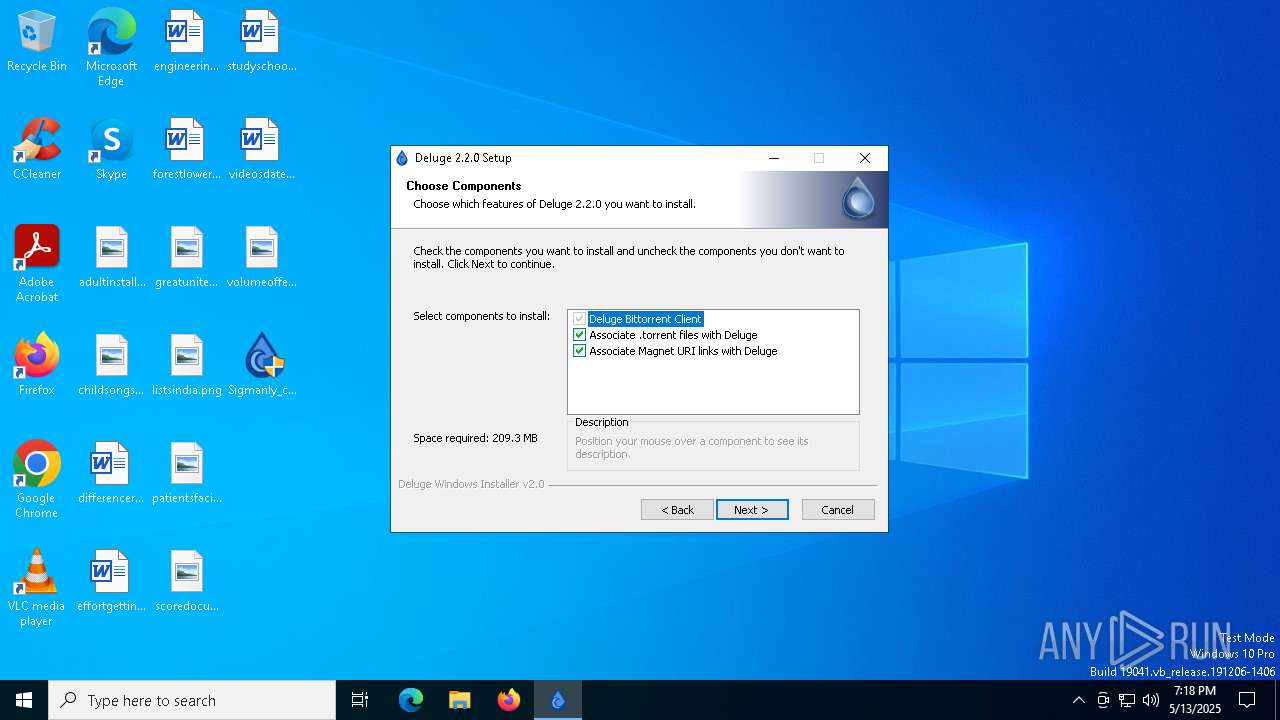
| File name: | Sigmanly_c35dbaea459fad5a3e45910735c1fffdfbbeab24296a0820878312df7285c2be |
| Full analysis: | https://app.any.run/tasks/84c0aa56-b29e-4315-8eca-2b44ac4ad141 |
| Verdict: | Malicious activity |
| Analysis date: | May 13, 2025, 19:17:44 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
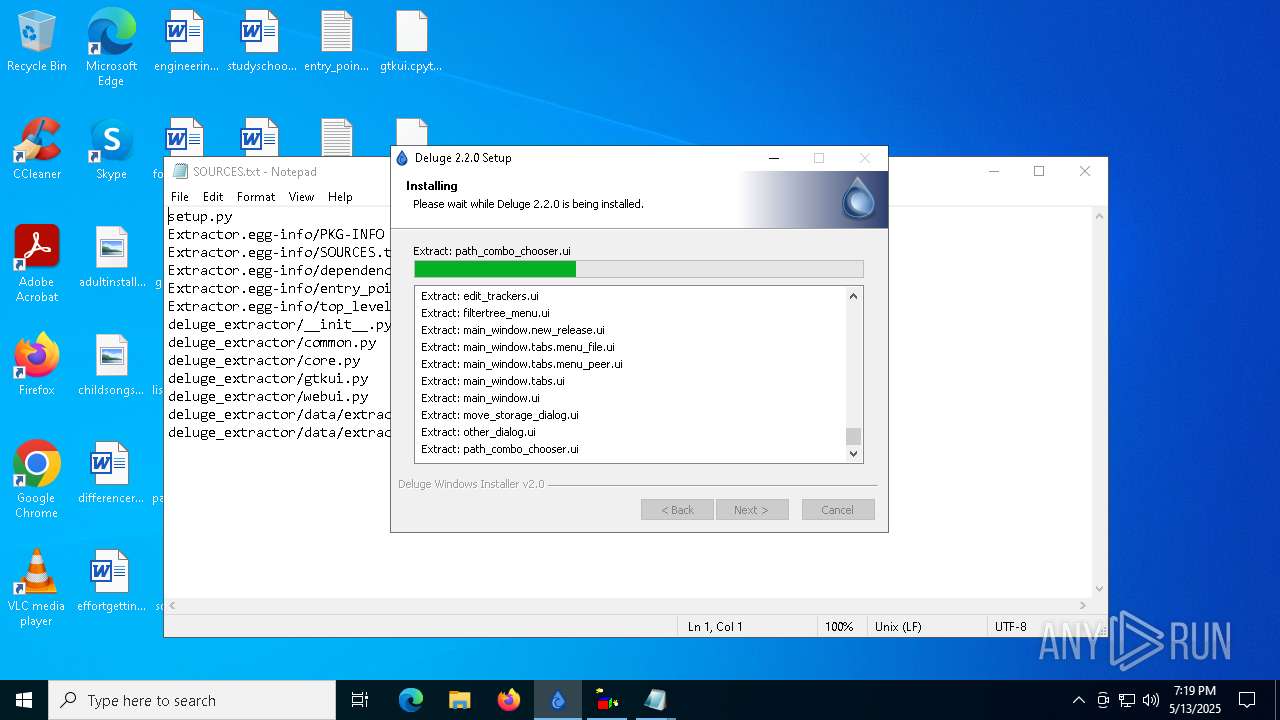
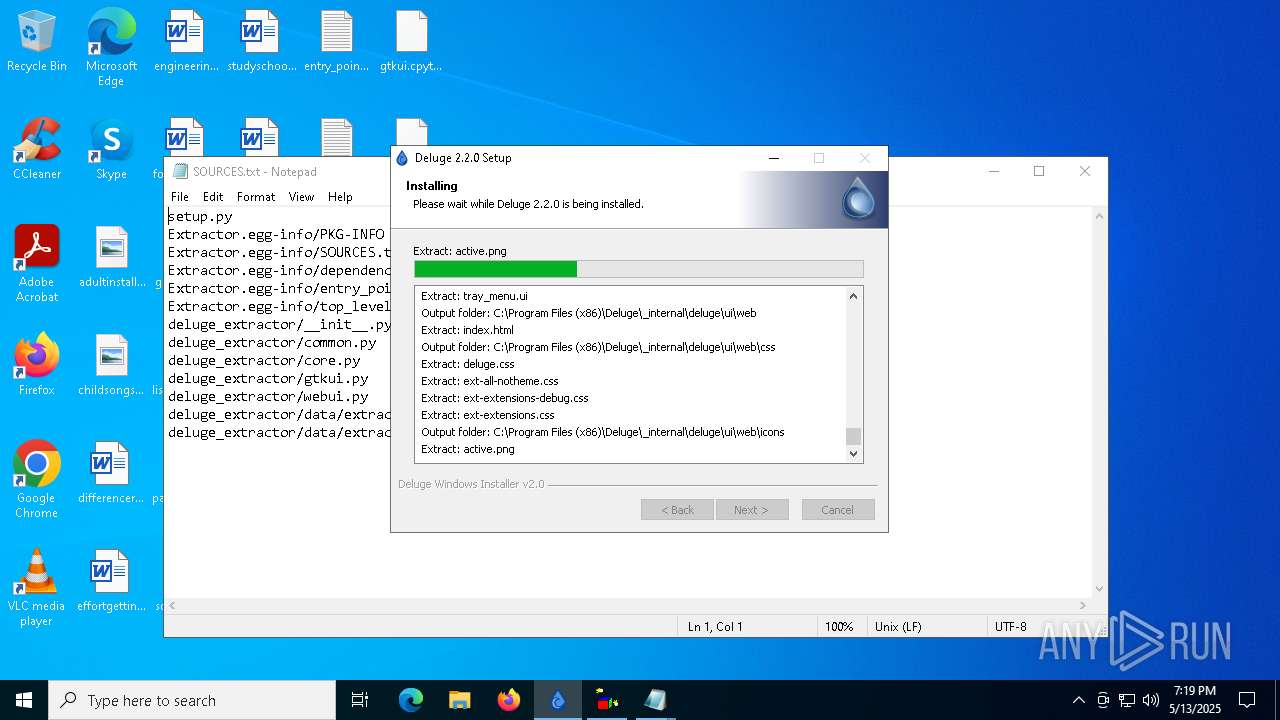
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | D89045DBF5CBD131890BEC3E9DFF0F64 |
| SHA1: | AAE6D3C6F0FC366CBF0700916961F6358F49F825 |
| SHA256: | C35DBAEA459FAD5A3E45910735C1FFFDFBBEAB24296A0820878312DF7285C2BE |
| SSDEEP: | 393216:L0jt2JRYL28qmRTXeg6qw/4j1mHKbNICD/R:g52JRh8GxNwuKbiCD/R |
MALICIOUS
No malicious indicators.SUSPICIOUS
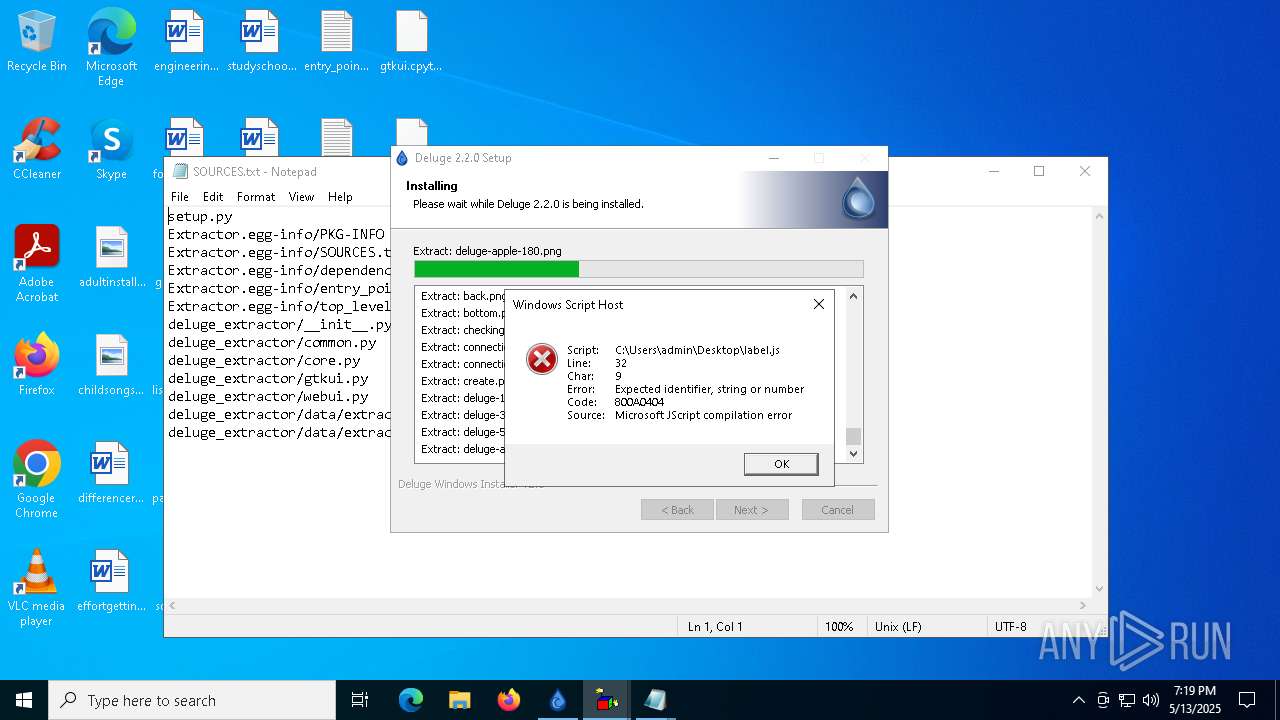
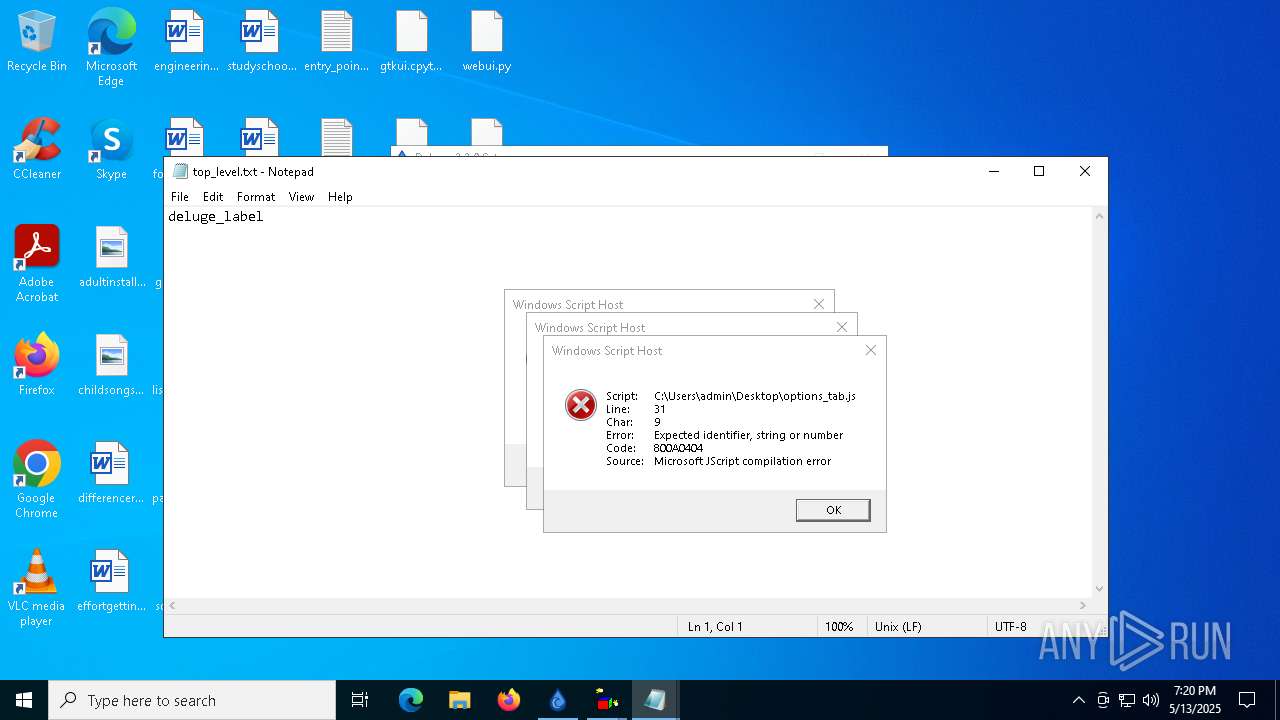
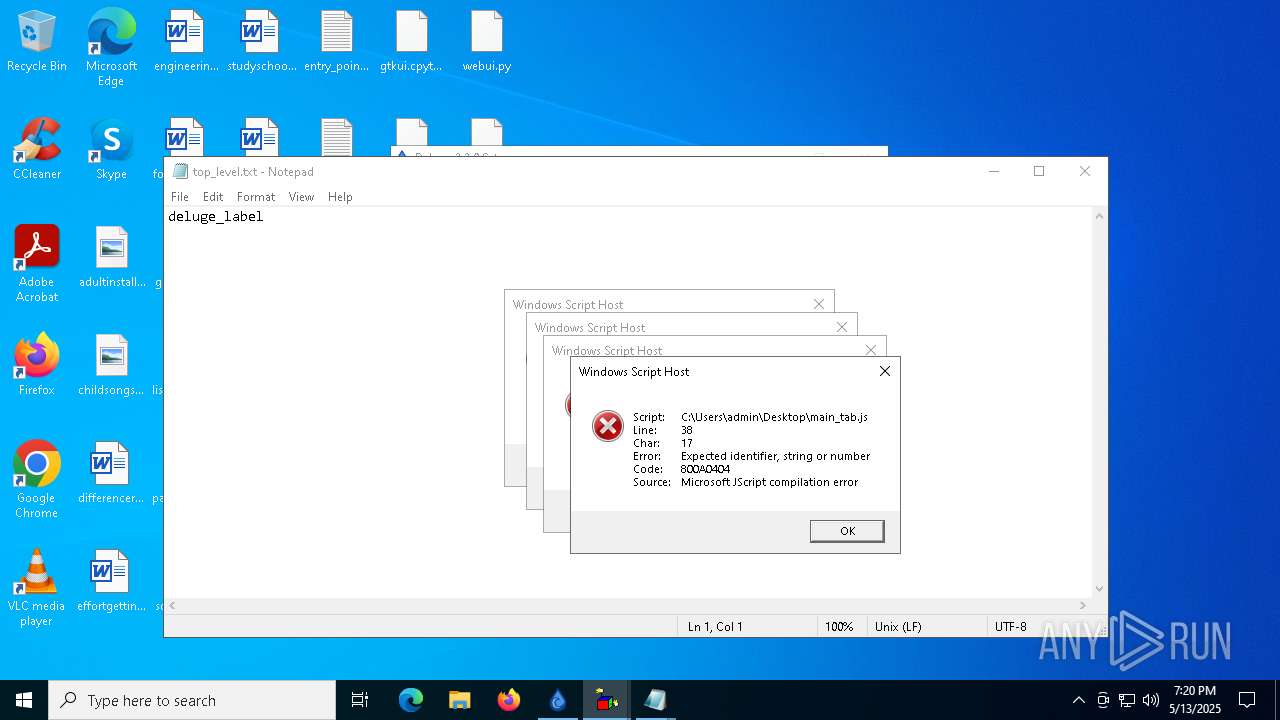
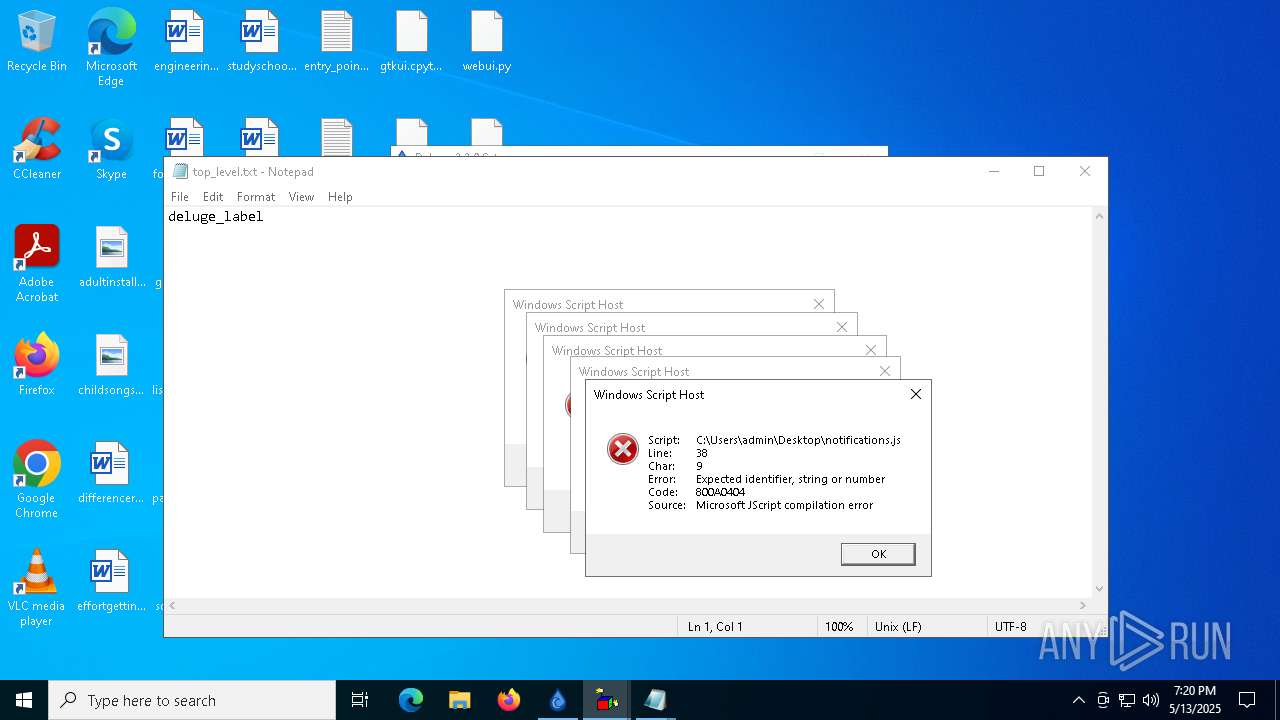
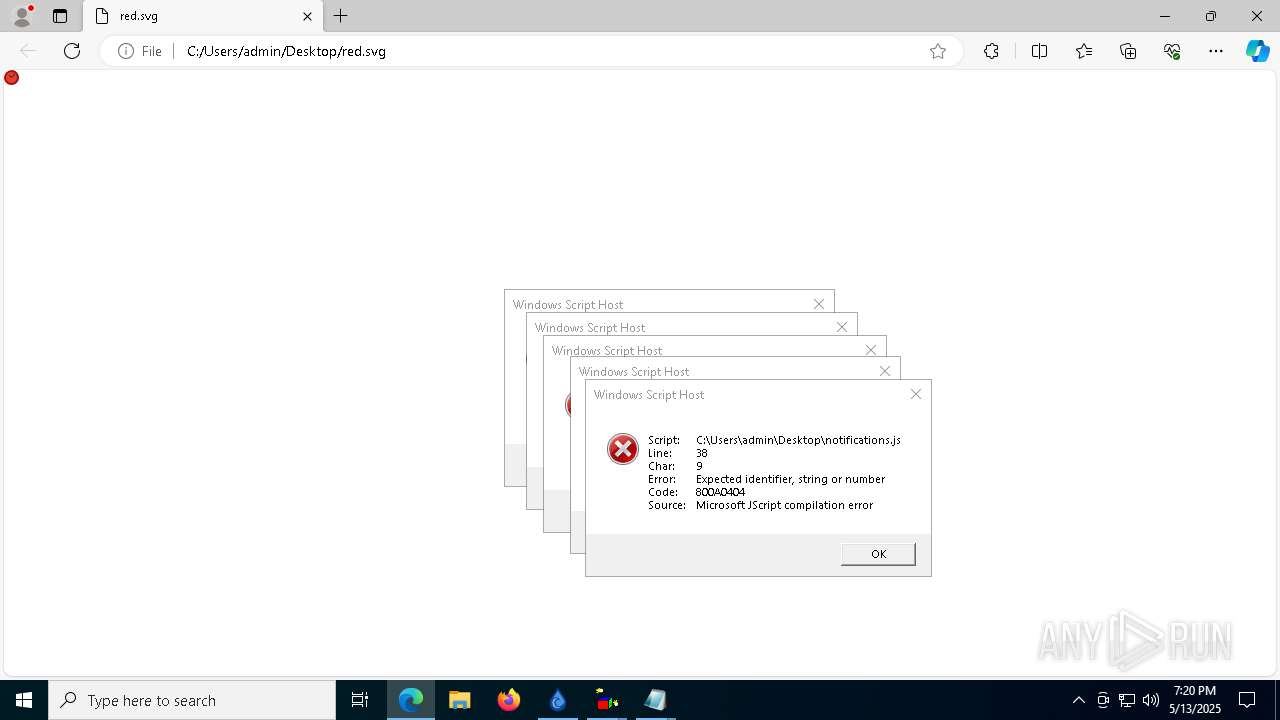
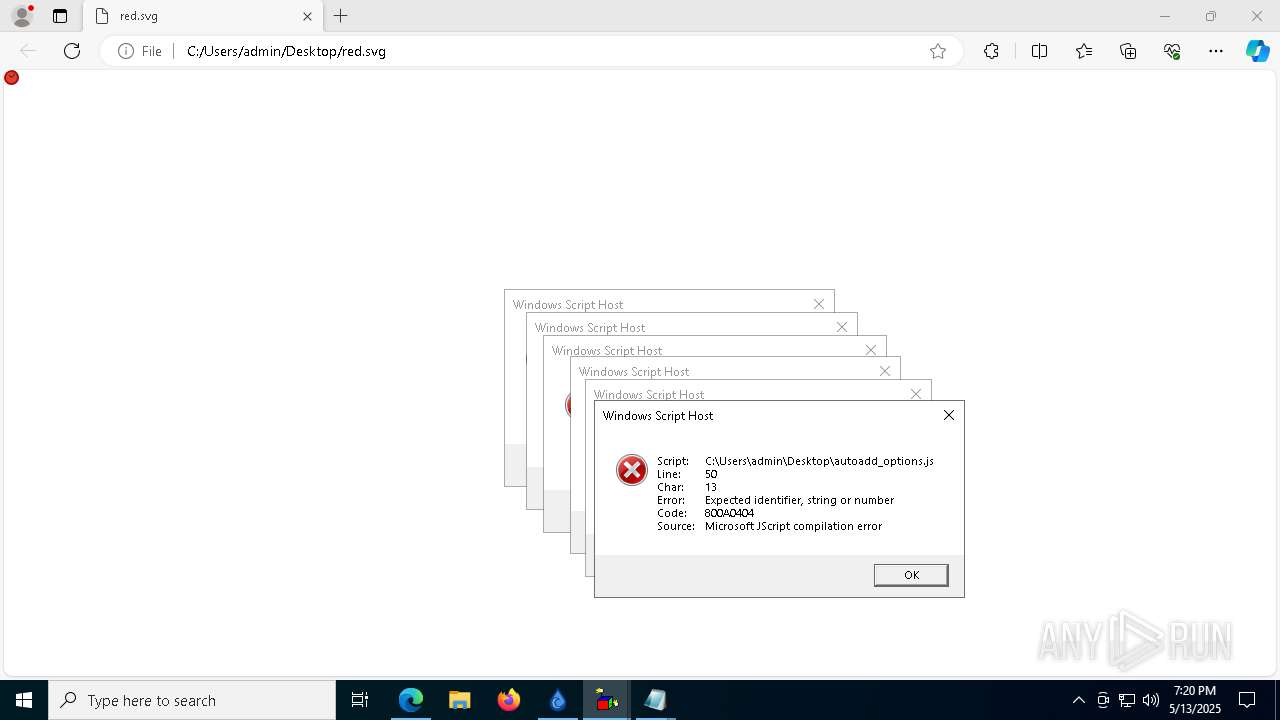
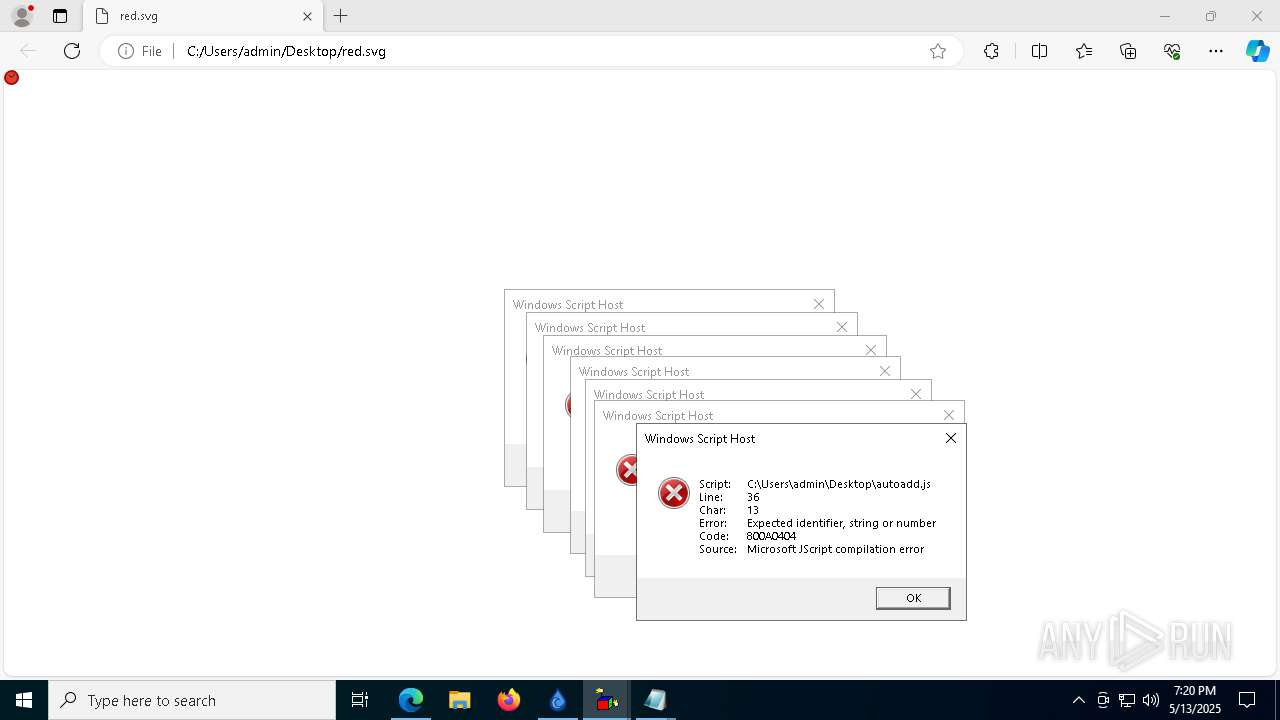
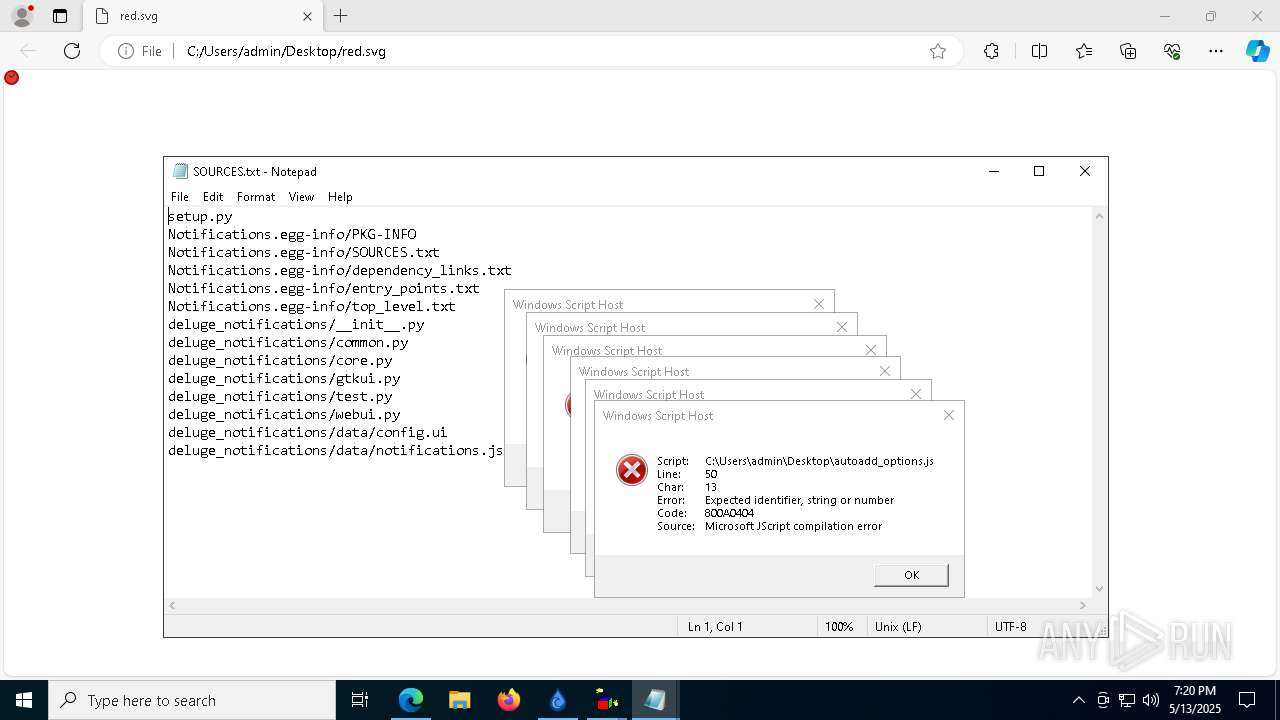
Malware-specific behavior (creating "System.dll" in Temp)
- Sigmanly_c35dbaea459fad5a3e45910735c1fffdfbbeab24296a0820878312df7285c2be.exe (PID: 7764)
There is functionality for taking screenshot (YARA)
- Sigmanly_c35dbaea459fad5a3e45910735c1fffdfbbeab24296a0820878312df7285c2be.exe (PID: 7764)
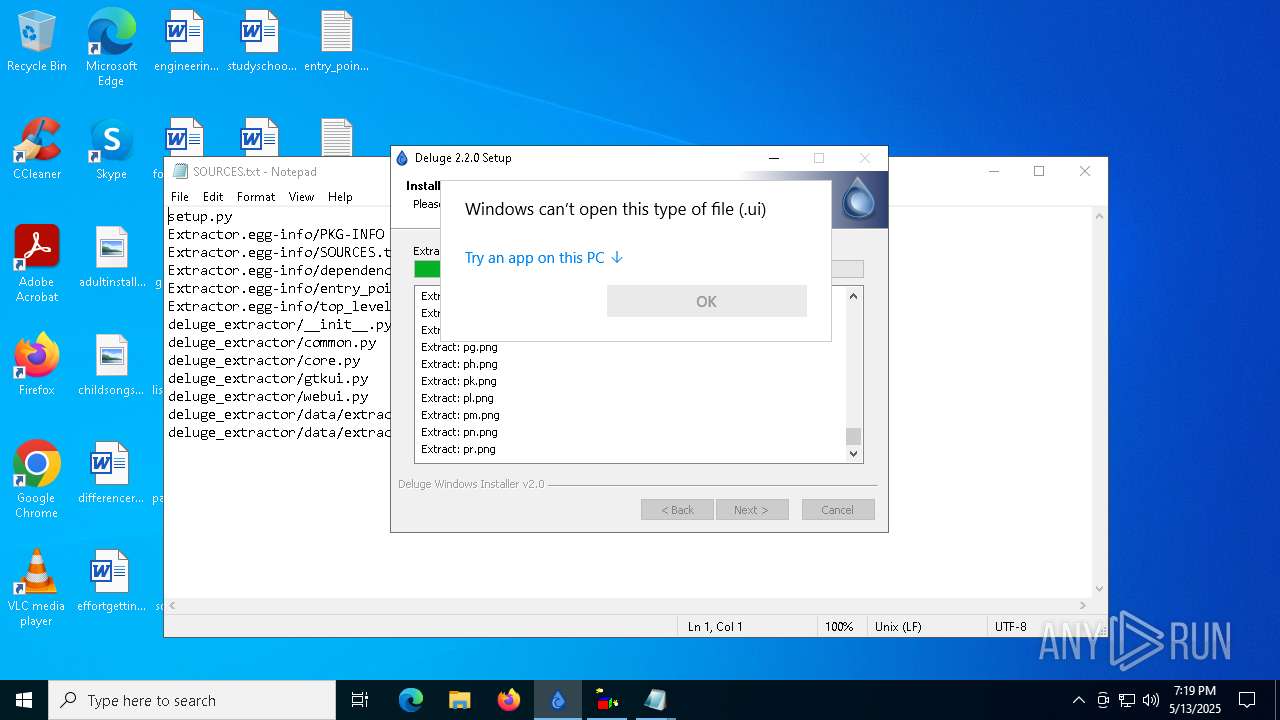
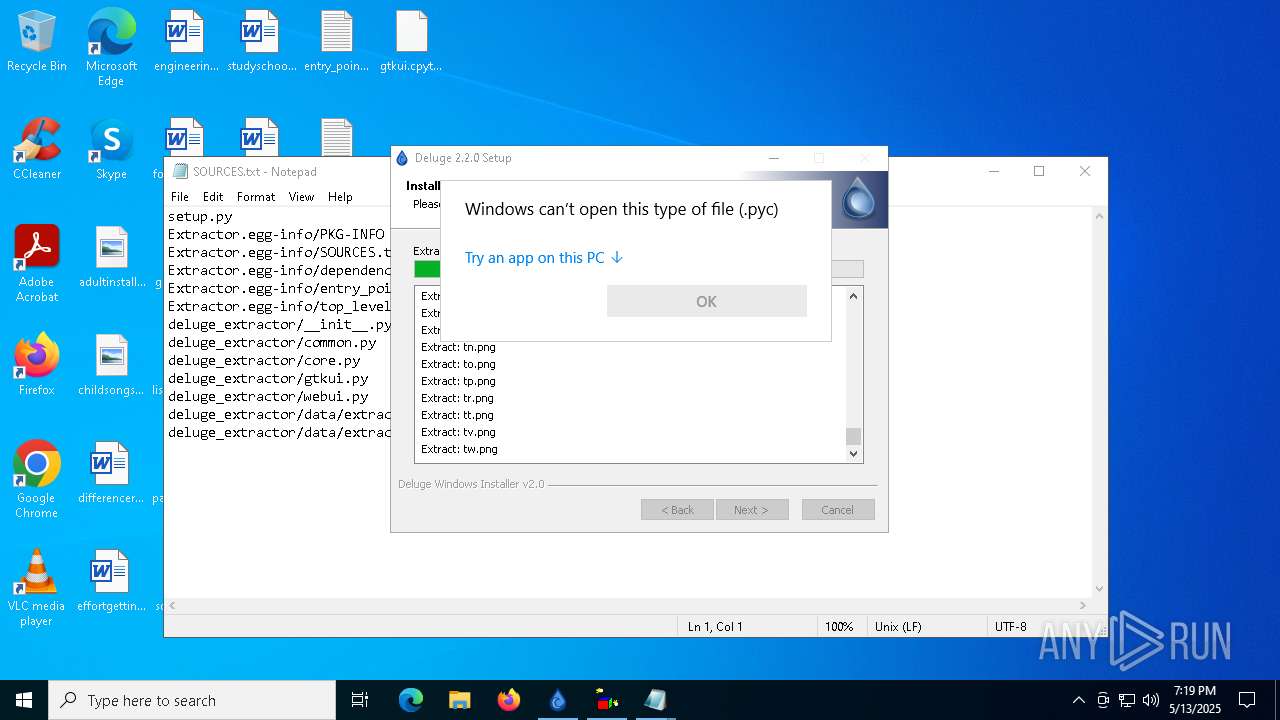
The process creates files with name similar to system file names
- Sigmanly_c35dbaea459fad5a3e45910735c1fffdfbbeab24296a0820878312df7285c2be.exe (PID: 7764)
Process drops python dynamic module
- Sigmanly_c35dbaea459fad5a3e45910735c1fffdfbbeab24296a0820878312df7285c2be.exe (PID: 7764)
The process drops C-runtime libraries
- Sigmanly_c35dbaea459fad5a3e45910735c1fffdfbbeab24296a0820878312df7285c2be.exe (PID: 7764)
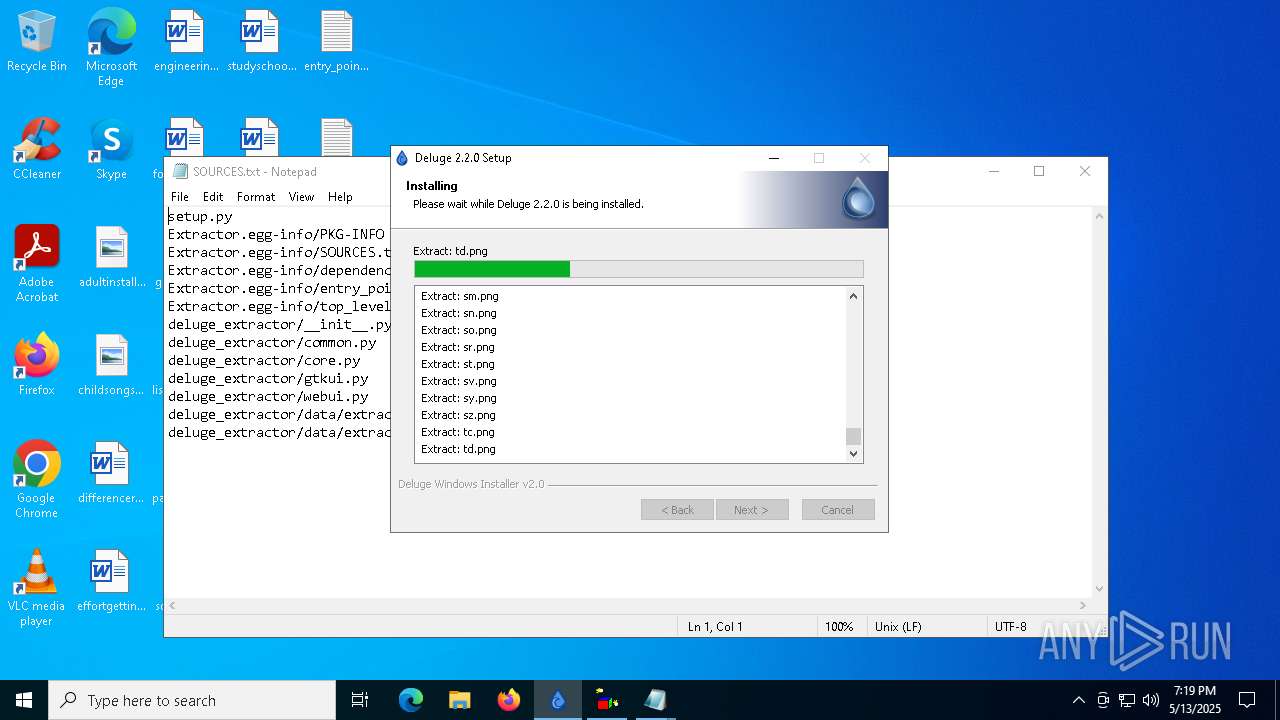
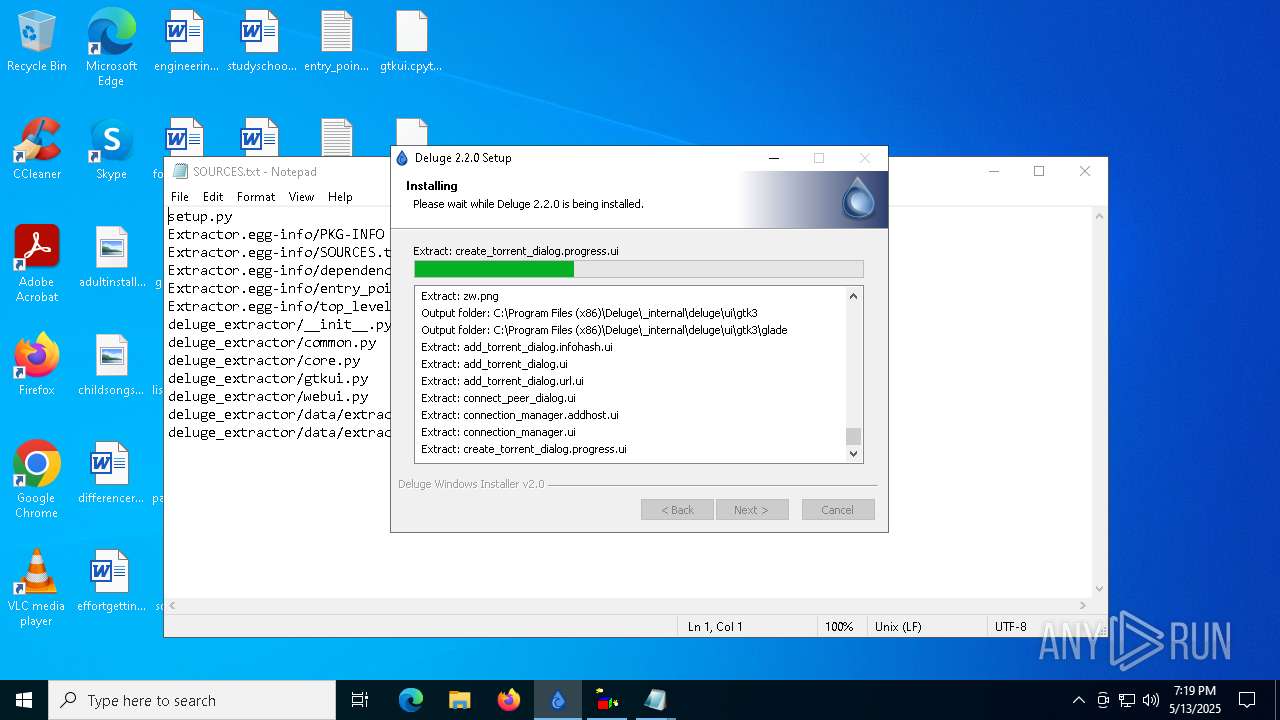
Executable content was dropped or overwritten
- Sigmanly_c35dbaea459fad5a3e45910735c1fffdfbbeab24296a0820878312df7285c2be.exe (PID: 7764)
Process drops legitimate windows executable
- Sigmanly_c35dbaea459fad5a3e45910735c1fffdfbbeab24296a0820878312df7285c2be.exe (PID: 7764)
INFO
Checks supported languages
- Sigmanly_c35dbaea459fad5a3e45910735c1fffdfbbeab24296a0820878312df7285c2be.exe (PID: 7764)
- identity_helper.exe (PID: 7336)
The sample compiled with english language support
- Sigmanly_c35dbaea459fad5a3e45910735c1fffdfbbeab24296a0820878312df7285c2be.exe (PID: 7764)
Creates files in the program directory
- Sigmanly_c35dbaea459fad5a3e45910735c1fffdfbbeab24296a0820878312df7285c2be.exe (PID: 7764)
Reads the computer name
- Sigmanly_c35dbaea459fad5a3e45910735c1fffdfbbeab24296a0820878312df7285c2be.exe (PID: 7764)
- identity_helper.exe (PID: 7336)
Create files in a temporary directory
- Sigmanly_c35dbaea459fad5a3e45910735c1fffdfbbeab24296a0820878312df7285c2be.exe (PID: 7764)
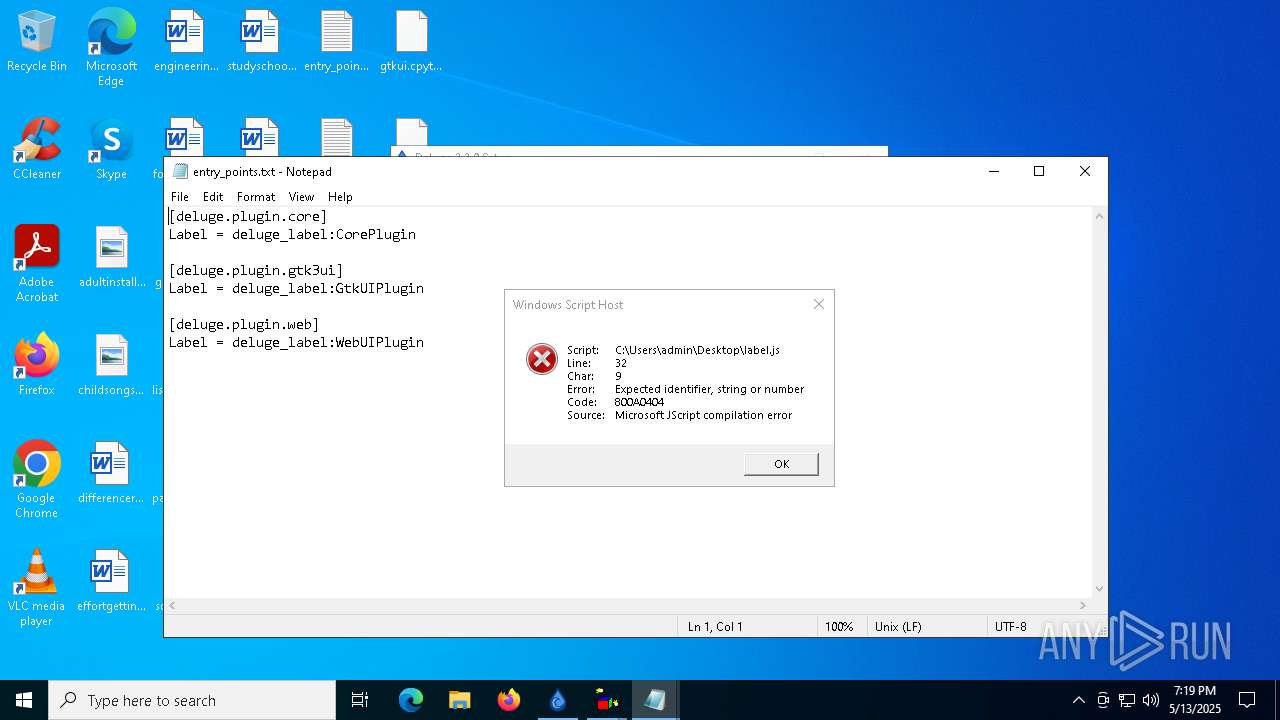
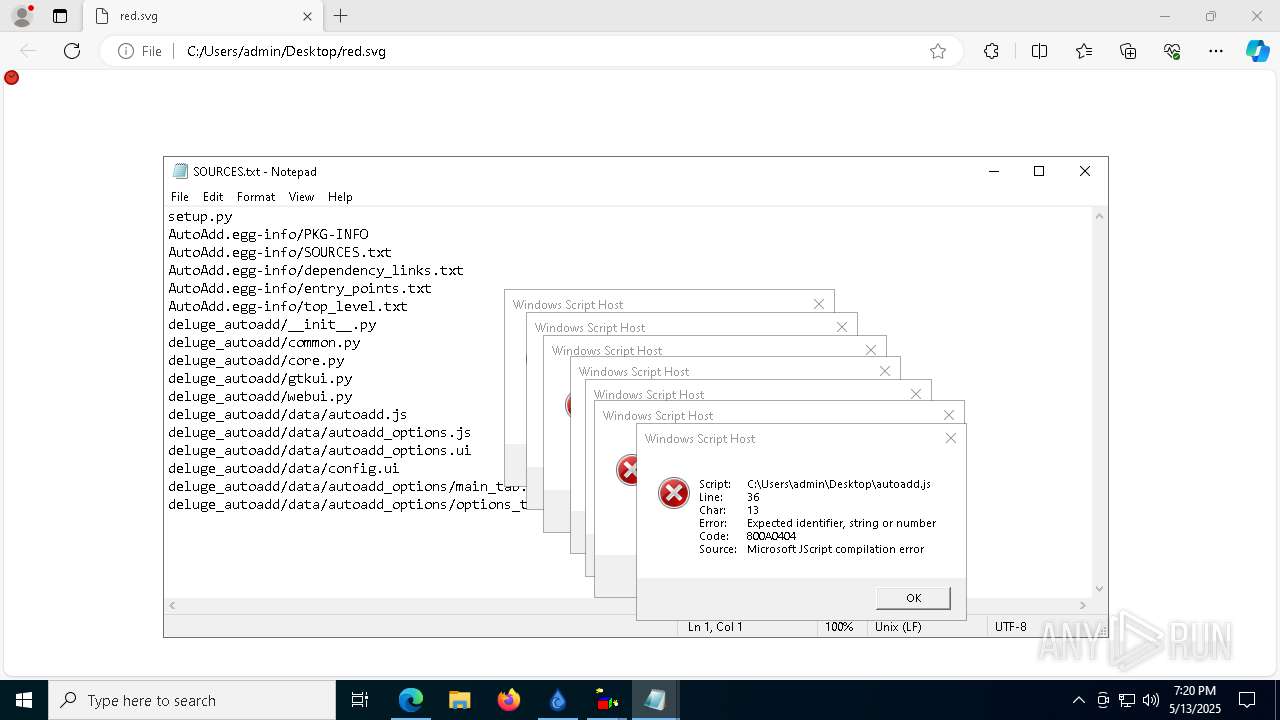
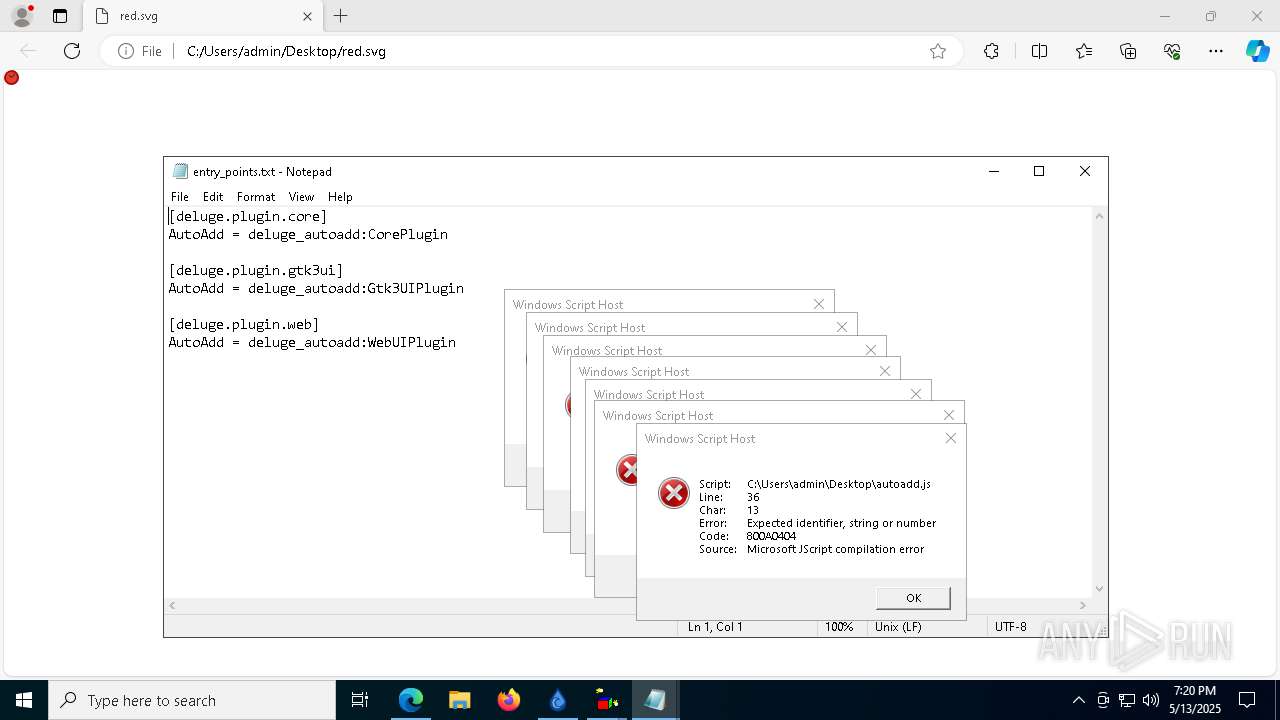
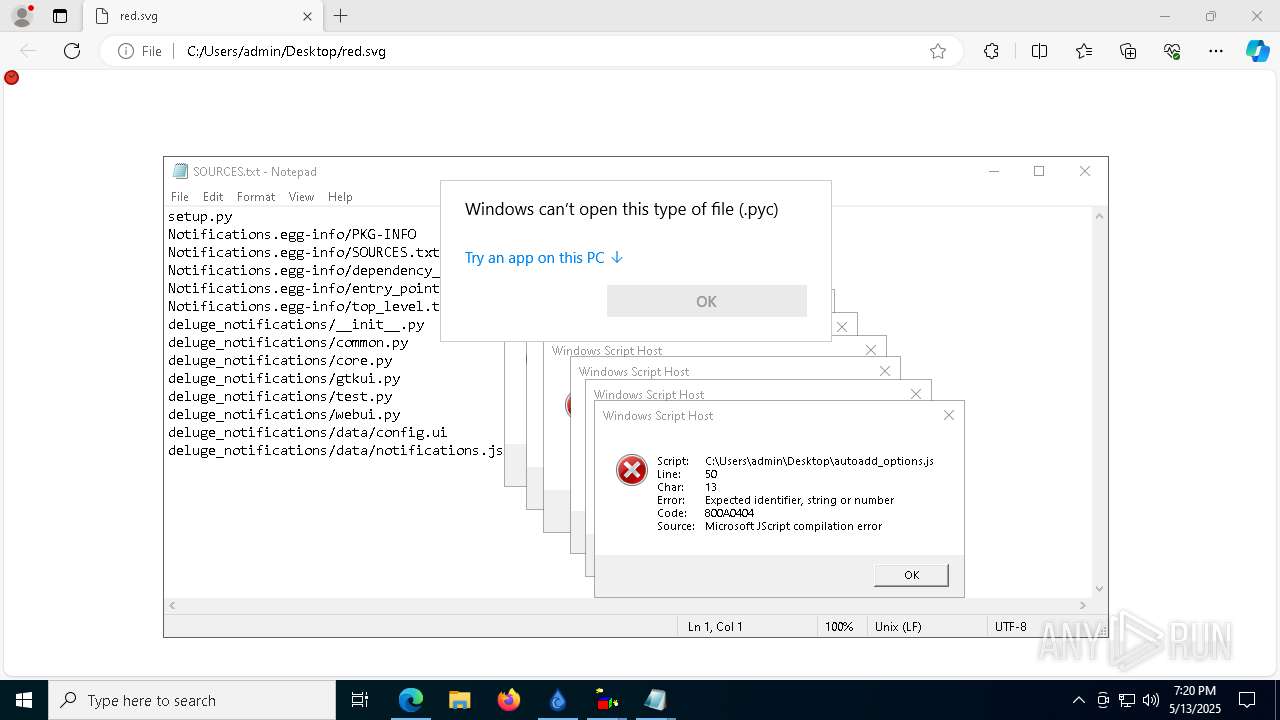
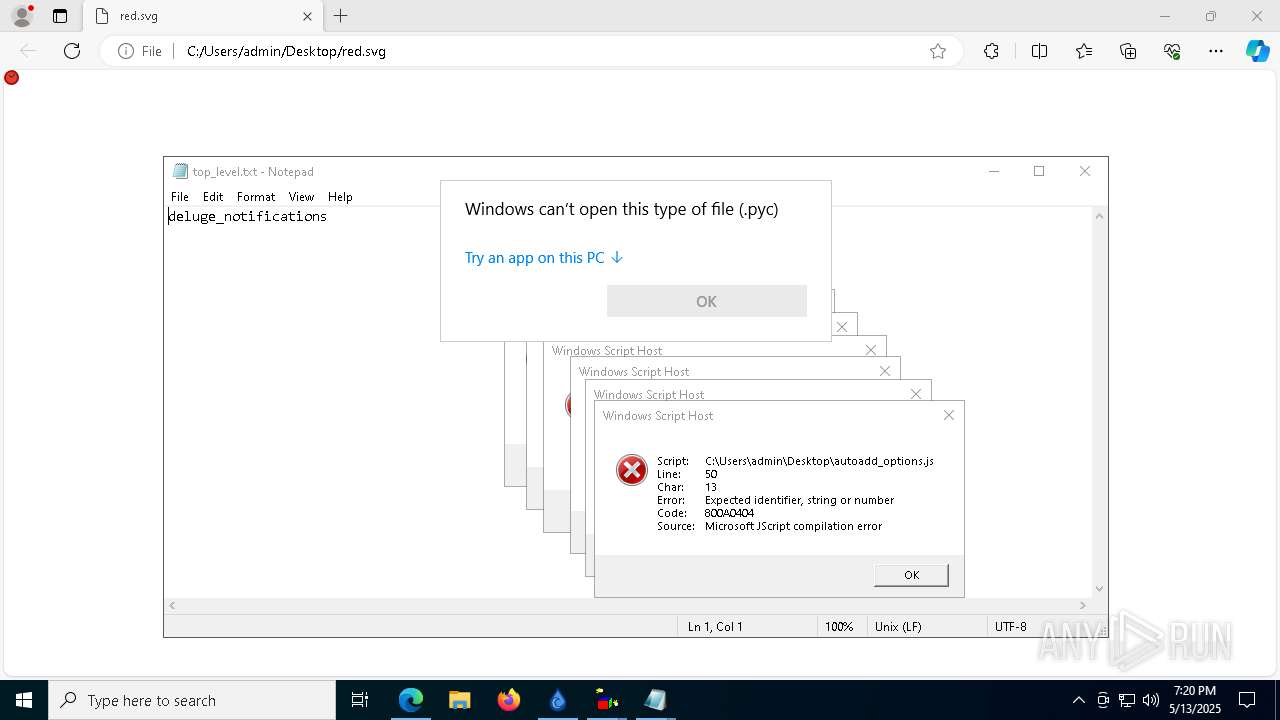
Manual execution by a user
- wscript.exe (PID: 664)
- notepad.exe (PID: 5968)
- notepad.exe (PID: 976)
- notepad.exe (PID: 3332)
- notepad.exe (PID: 6944)
- OpenWith.exe (PID: 680)
- OpenWith.exe (PID: 1280)
- OpenWith.exe (PID: 7052)
- notepad.exe (PID: 3156)
- OpenWith.exe (PID: 5720)
- wscript.exe (PID: 5956)
- notepad.exe (PID: 7580)
- notepad.exe (PID: 3768)
- OpenWith.exe (PID: 6740)
- OpenWith.exe (PID: 7628)
- OpenWith.exe (PID: 7568)
- OpenWith.exe (PID: 732)
- OpenWith.exe (PID: 7684)
- OpenWith.exe (PID: 1388)
- wscript.exe (PID: 1568)
- notepad.exe (PID: 536)
- notepad.exe (PID: 1812)
- notepad.exe (PID: 4200)
- wscript.exe (PID: 3900)
- OpenWith.exe (PID: 4728)
- msedge.exe (PID: 7944)
- wscript.exe (PID: 6516)
- notepad.exe (PID: 7324)
- wscript.exe (PID: 5260)
- msedge.exe (PID: 6760)
- notepad.exe (PID: 2796)
- notepad.exe (PID: 5892)
- notepad.exe (PID: 1020)
- wscript.exe (PID: 8088)
- wscript.exe (PID: 7900)
- OpenWith.exe (PID: 7480)
- notepad.exe (PID: 7744)
Reads security settings of Internet Explorer
- notepad.exe (PID: 976)
- notepad.exe (PID: 5968)
- notepad.exe (PID: 6944)
- notepad.exe (PID: 7580)
- notepad.exe (PID: 3768)
- notepad.exe (PID: 3156)
- notepad.exe (PID: 3332)
- notepad.exe (PID: 536)
- notepad.exe (PID: 1812)
- notepad.exe (PID: 4200)
- notepad.exe (PID: 2796)
- notepad.exe (PID: 7324)
- notepad.exe (PID: 5892)
- notepad.exe (PID: 1020)
- notepad.exe (PID: 7744)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 1280)
- OpenWith.exe (PID: 680)
- OpenWith.exe (PID: 7052)
- OpenWith.exe (PID: 5720)
- OpenWith.exe (PID: 6740)
- OpenWith.exe (PID: 7684)
- OpenWith.exe (PID: 732)
- OpenWith.exe (PID: 1388)
- OpenWith.exe (PID: 4728)
- OpenWith.exe (PID: 7568)
- OpenWith.exe (PID: 7628)
Checks proxy server information
- slui.exe (PID: 8164)
Reads the software policy settings
- slui.exe (PID: 8164)
Application launched itself
- msedge.exe (PID: 7944)
Reads Environment values
- identity_helper.exe (PID: 7336)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:03:30 16:55:19+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 139776 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x3665 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.0.0 |
| ProductVersionNumber: | 2.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
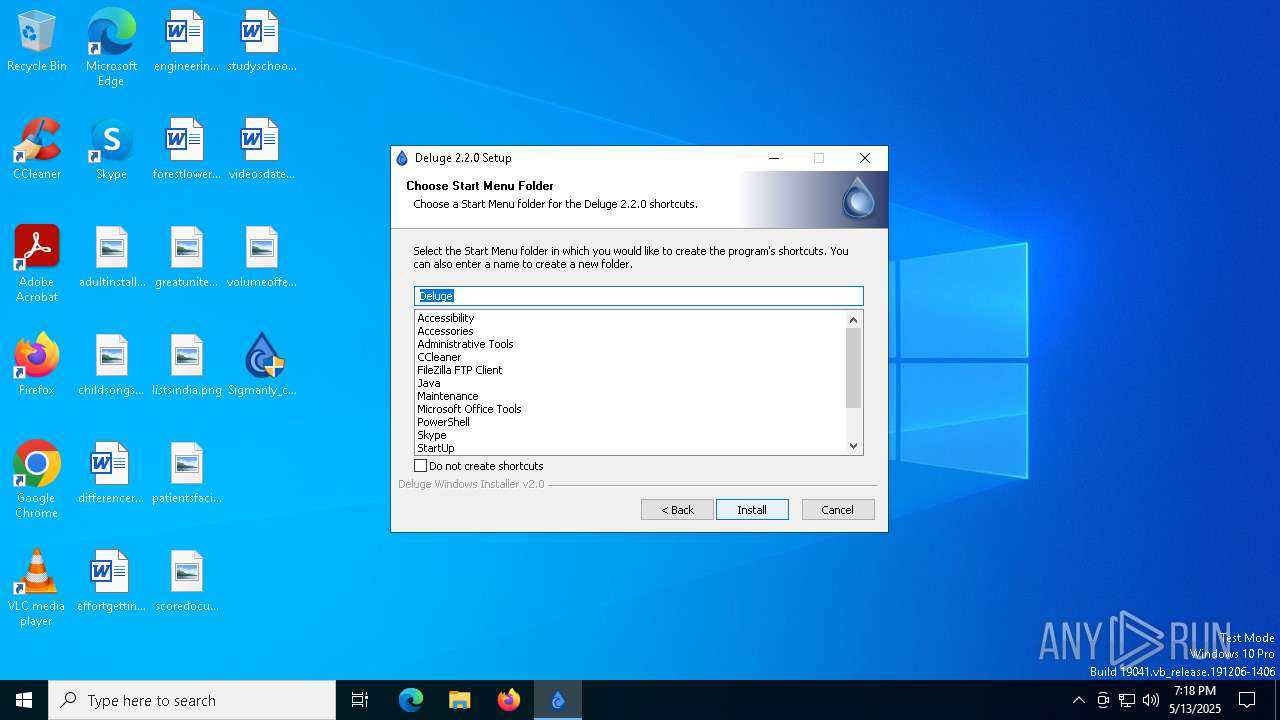
| Comments: | Deluge Bittorrent Client |
| CompanyName: | Deluge Team |
| FileDescription: | Deluge Application Installer |
| FileVersion: | 2.0.0.0 |
| LegalCopyright: | Deluge Team |
| OriginalFileName: | deluge-2.2.0-win32-setup.exe |
| ProductName: | Deluge |
| ProductVersion: | 2.2.0.0 |
Total processes
185
Monitored processes
60
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\SOURCES.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6132 --field-trial-handle=2356,i,15256097712729356018,14648531158765701660,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
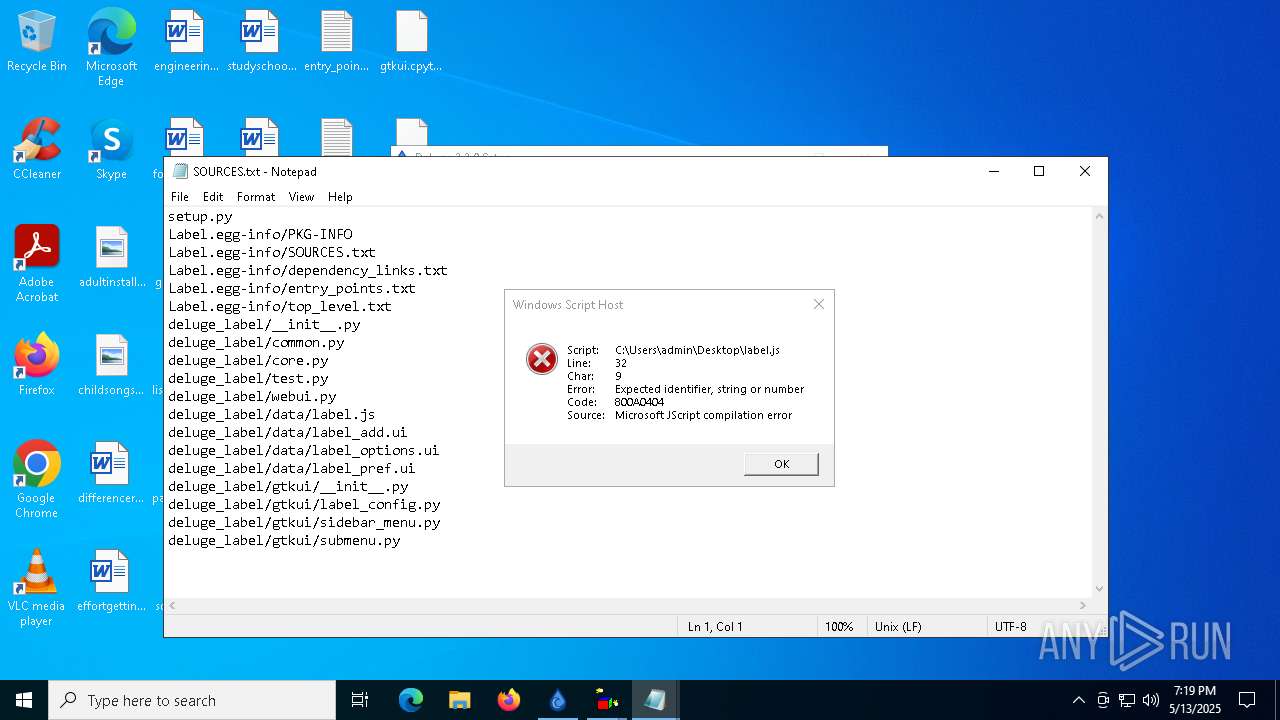
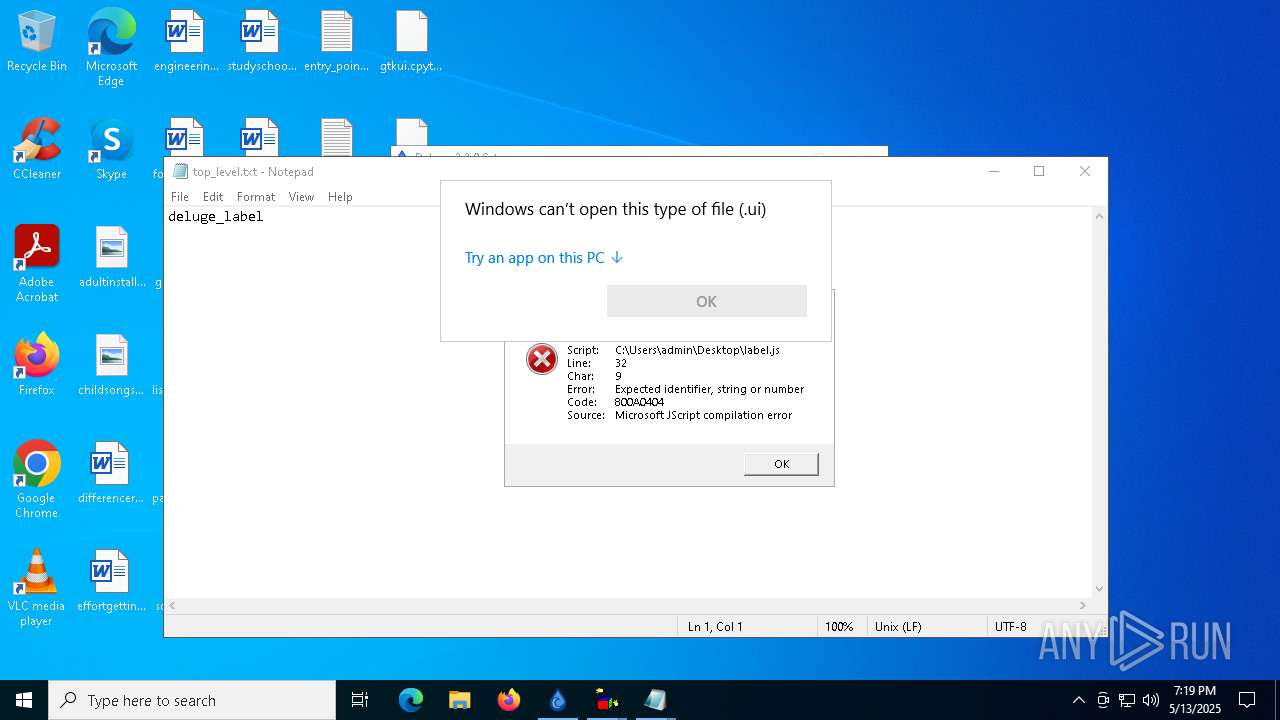
| 664 | "C:\Windows\System32\WScript.exe" C:\Users\admin\Desktop\extractor.js | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
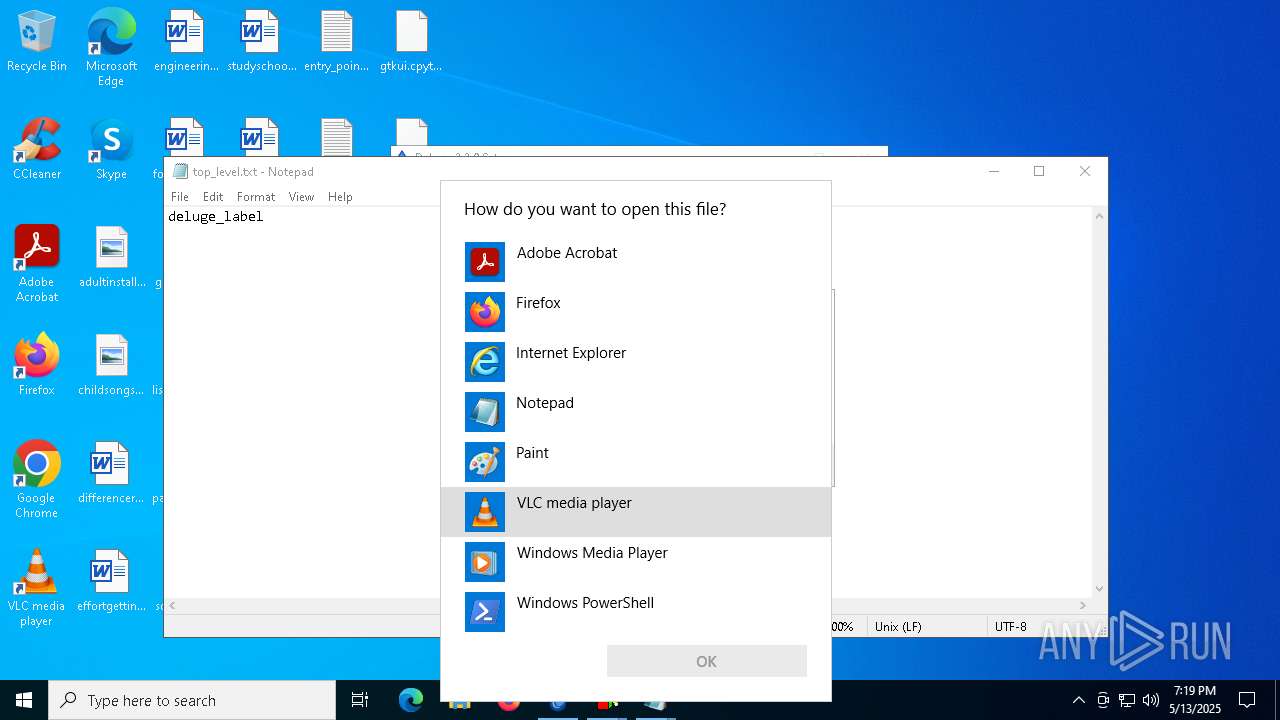
| 680 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\extractor_prefs.ui | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\label_options.ui | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 960 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6100 --field-trial-handle=2356,i,15256097712729356018,14648531158765701660,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
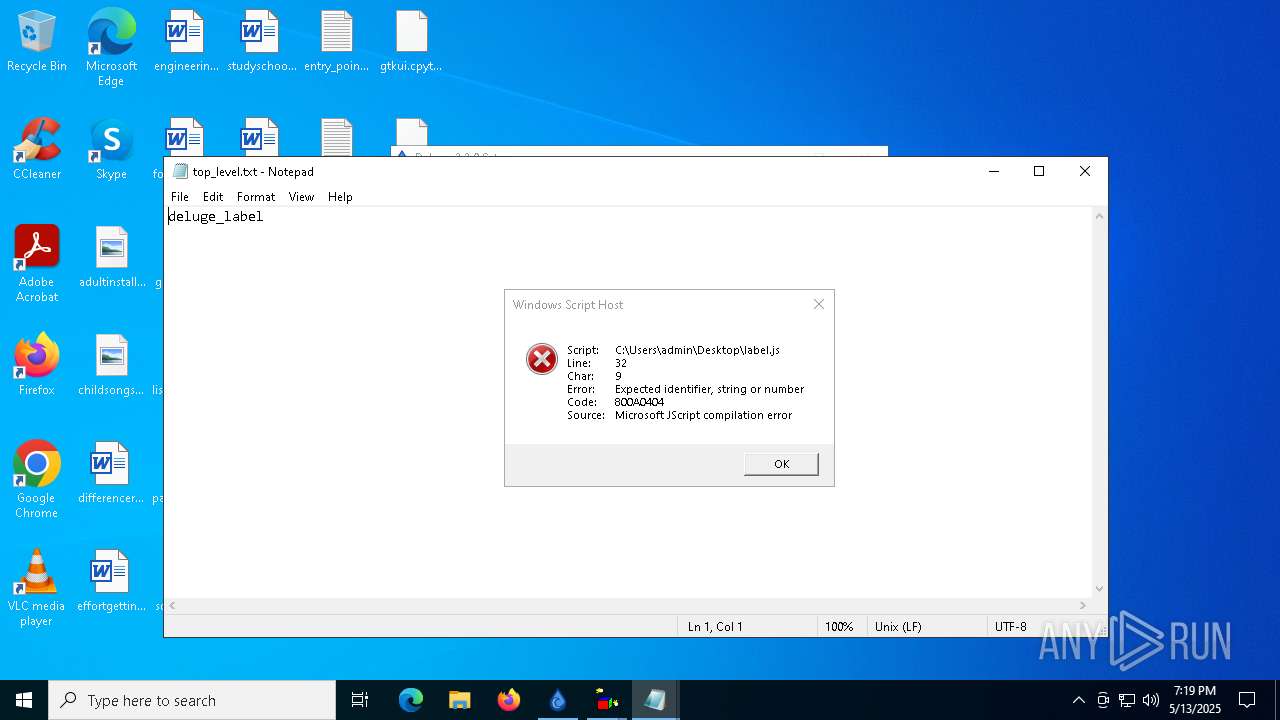
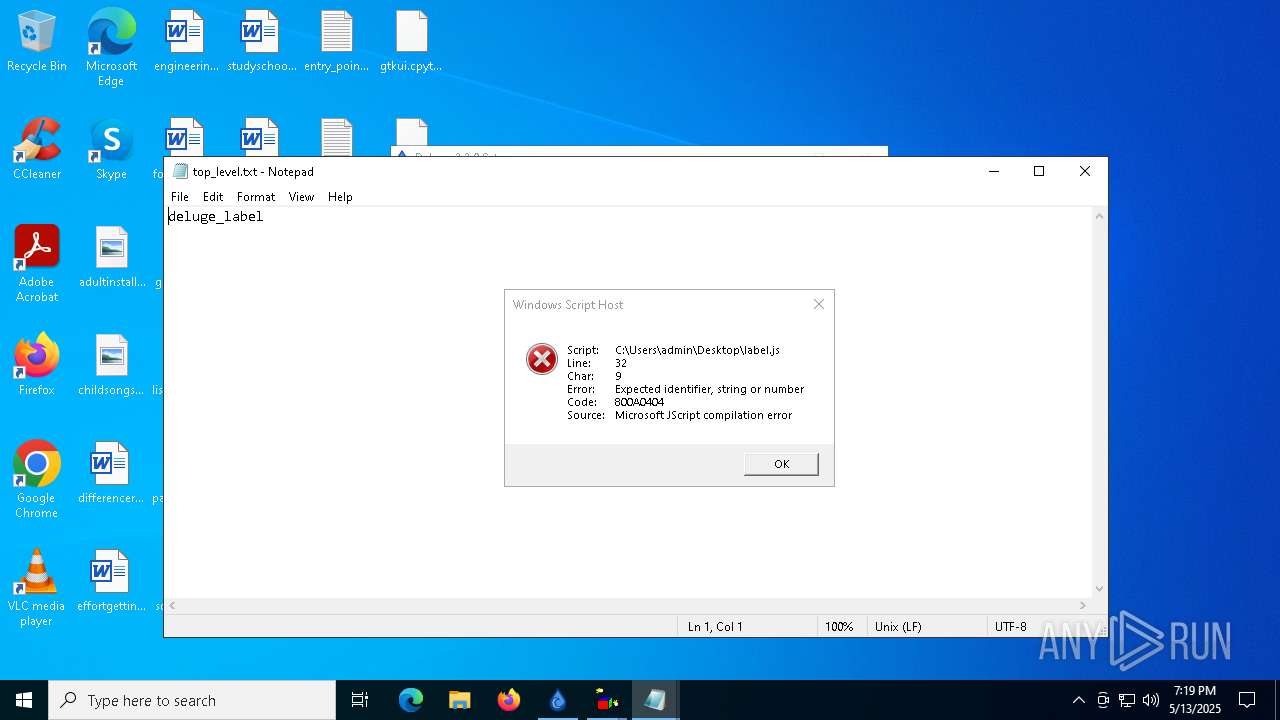
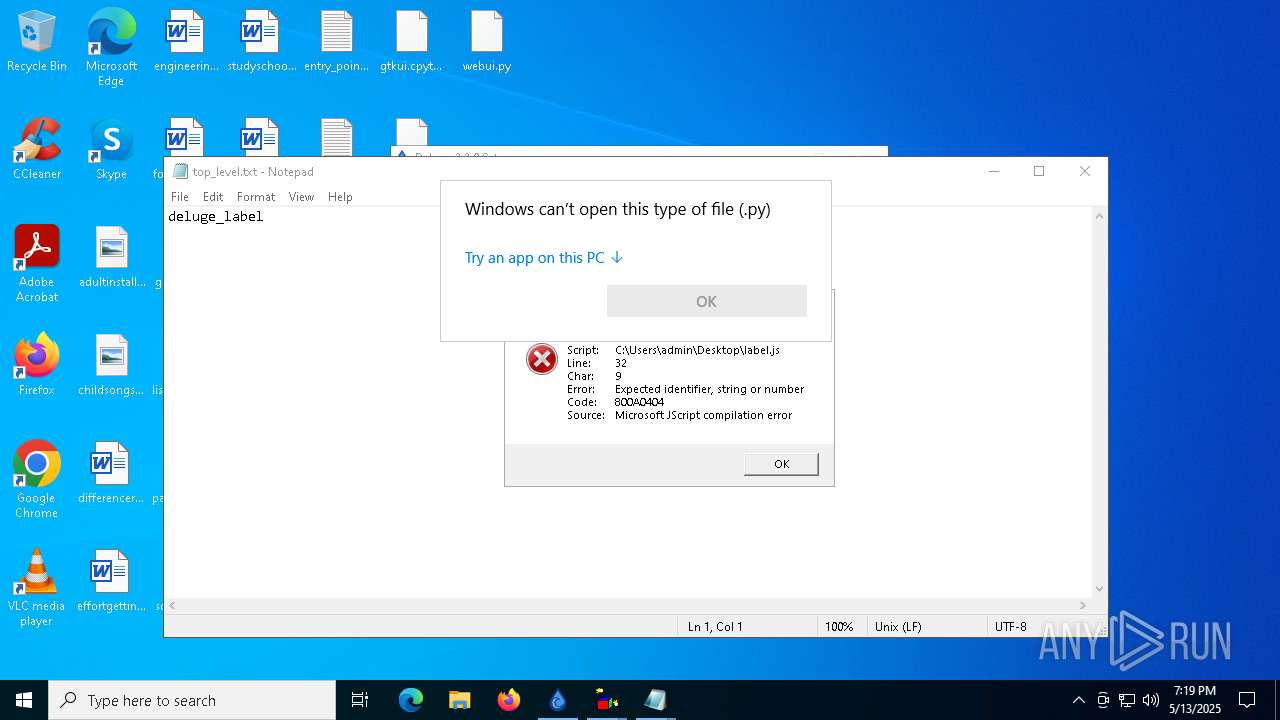
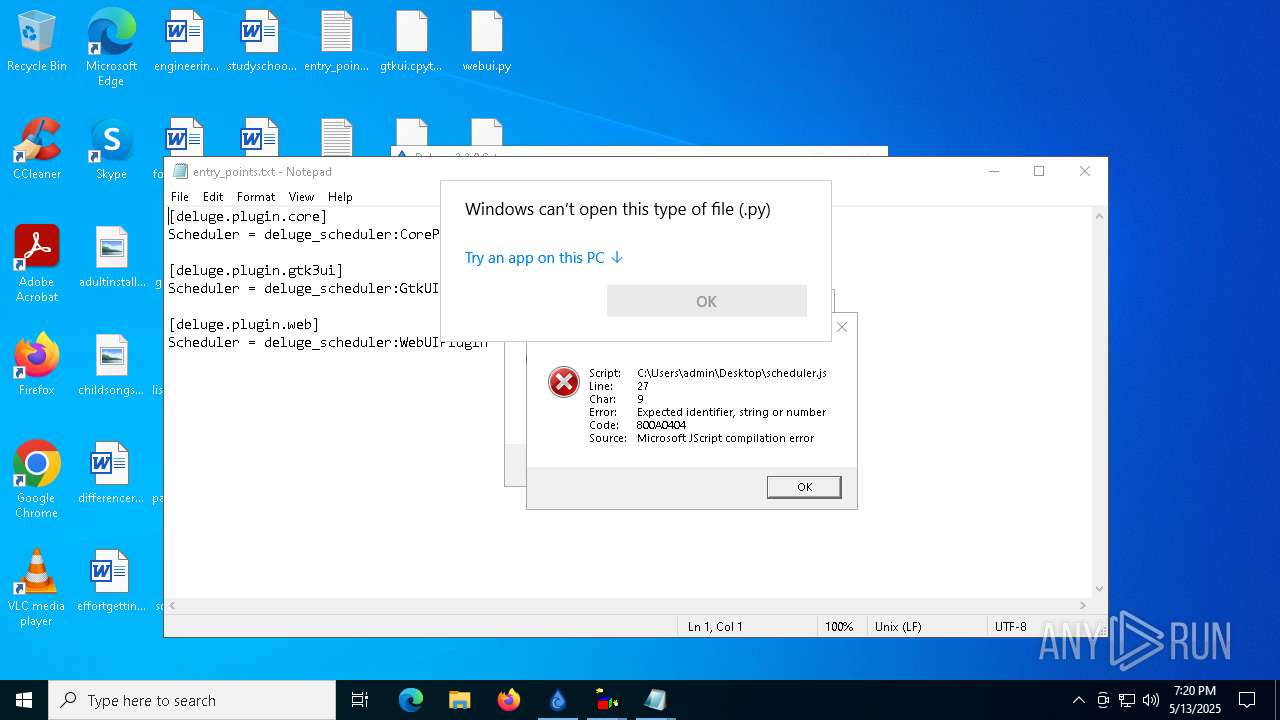
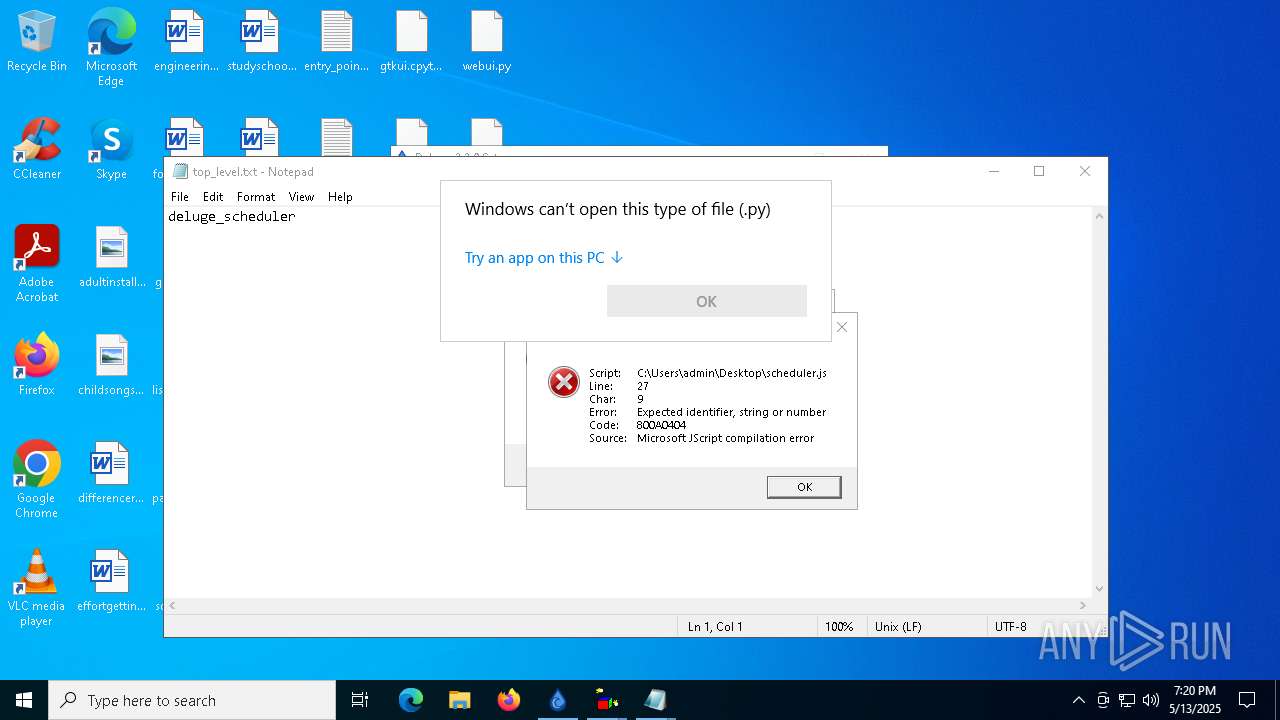
| 976 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\top_level.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1020 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\SOURCES.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1280 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\common.cpython-39.pyc | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1388 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\common.py | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
16 159
Read events
16 144
Write events
15
Delete events
0
Modification events
| (PID) Process: | (7944) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (7944) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: C9F9079B9F932F00 | |||
| (PID) Process: | (7944) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (7944) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (7944) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (7944) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: E1D80F9B9F932F00 | |||
| (PID) Process: | (7944) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\66518 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {FA4F76CD-086C-4F71-84CB-5917C7137196} | |||
| (PID) Process: | (7944) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: F424309B9F932F00 | |||
| (PID) Process: | (7944) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicrosoftEdgeAutoLaunch_29EBC4579851B72EE312C449CF839B1A |
Value: "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window --win-session-start | |||
| (PID) Process: | (7944) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\Clients\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\Commands\on-logon-autolaunch |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
Executable files
106
Suspicious files
310
Text files
1 941
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
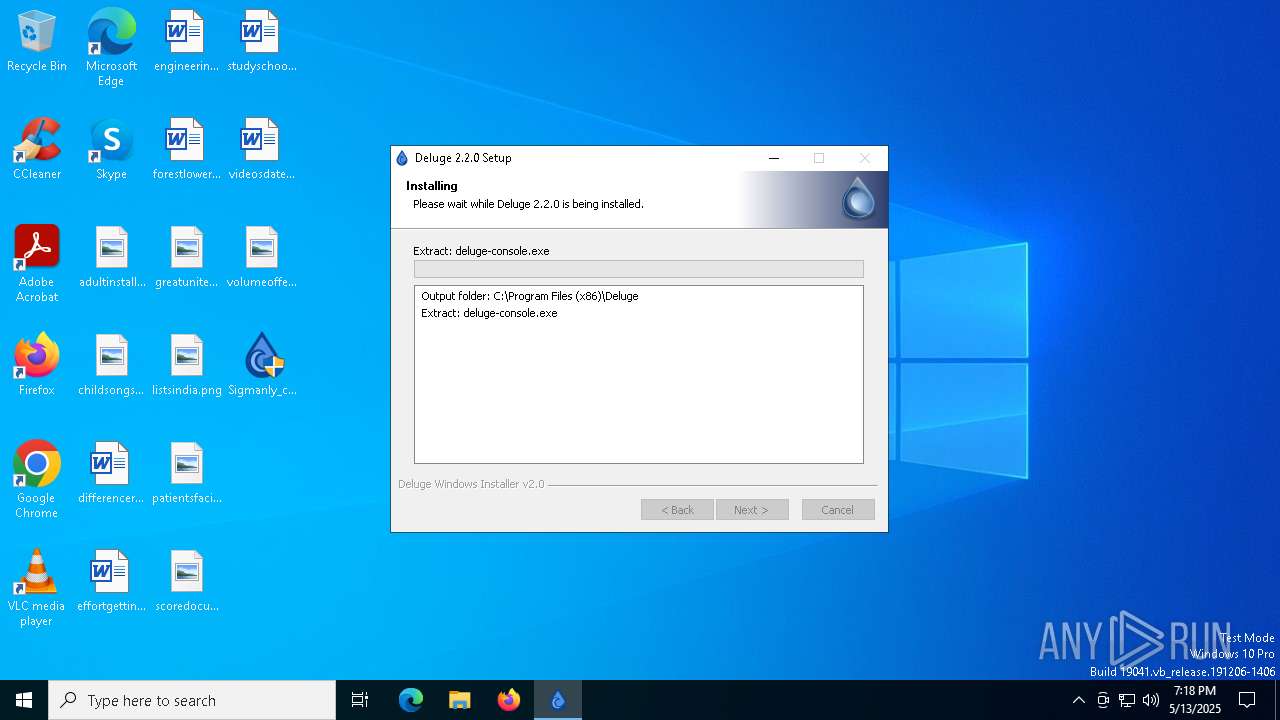
| 7764 | Sigmanly_c35dbaea459fad5a3e45910735c1fffdfbbeab24296a0820878312df7285c2be.exe | C:\Program Files (x86)\Deluge\deluged-debug.exe | executable | |
MD5:7D6A4FC616FDF77E45F7ADA0796AB97C | SHA256:8243F79F30771AC035C8A698A1CBEBC6A4812A7C9A25BAFB2E65803CB3C87E90 | |||
| 7764 | Sigmanly_c35dbaea459fad5a3e45910735c1fffdfbbeab24296a0820878312df7285c2be.exe | C:\Program Files (x86)\Deluge\deluge.exe | executable | |
MD5:9B091C801ADB67340BB4B929D1FED646 | SHA256:E6984B9EBE53EC7B207B1E46E7EA960807E692801F009F5FBFB1632EC8E66389 | |||
| 7764 | Sigmanly_c35dbaea459fad5a3e45910735c1fffdfbbeab24296a0820878312df7285c2be.exe | C:\Users\admin\AppData\Local\Temp\nsvD257.tmp\StartMenu.dll | executable | |
MD5:DC91F181F9CB870FFF0C58BC0EA63EDA | SHA256:E74F442771F034A24B77D3A849B343551BDEF69EF151C622CB9FD5F34DCCDA81 | |||
| 7764 | Sigmanly_c35dbaea459fad5a3e45910735c1fffdfbbeab24296a0820878312df7285c2be.exe | C:\Program Files (x86)\Deluge\deluge-web.exe | executable | |
MD5:73DB9C191E0753436715CB0101783691 | SHA256:11A41F4AF2EE03D894DDF4A332A36E9C9A3E96E15A11A038F2ECC854CF2130A8 | |||
| 7764 | Sigmanly_c35dbaea459fad5a3e45910735c1fffdfbbeab24296a0820878312df7285c2be.exe | C:\Program Files (x86)\Deluge\deluge-web-debug.exe | executable | |
MD5:AE614B6FB360E600A0B0FF0ABA90864A | SHA256:ED8FCC9FF7C6D379F9FC5EC0D183AA65971E0386A5927ED12DAAA5B0F2EA8B93 | |||
| 7764 | Sigmanly_c35dbaea459fad5a3e45910735c1fffdfbbeab24296a0820878312df7285c2be.exe | C:\Program Files (x86)\Deluge\deluge-console.exe | executable | |
MD5:A312DDB612BD4E8E8F79A26AB8059B31 | SHA256:D299BFF6E9DBCC765A52C80359BFD446A9604F9D93FC23F468C0FE699A03118F | |||
| 7764 | Sigmanly_c35dbaea459fad5a3e45910735c1fffdfbbeab24296a0820878312df7285c2be.exe | C:\Program Files (x86)\Deluge\deluge-debug.exe | executable | |
MD5:5F6922D98B39C53B6AAA503EABEF406D | SHA256:D9DFF0BC397F9D4ADBFE037C670462F682CA244F755BB6D194BBC89B6D4C4CE7 | |||
| 7764 | Sigmanly_c35dbaea459fad5a3e45910735c1fffdfbbeab24296a0820878312df7285c2be.exe | C:\Program Files (x86)\Deluge\deluge-gtk.exe | executable | |
MD5:BFD289EFE862120E6174FE055F281C5C | SHA256:E0B27EF545300892212CC6C6277526B7C9085B184E736FAEF86EE604C4C5DABA | |||
| 7764 | Sigmanly_c35dbaea459fad5a3e45910735c1fffdfbbeab24296a0820878312df7285c2be.exe | C:\Users\admin\AppData\Local\Temp\nsvD257.tmp\modern-wizard.bmp | image | |
MD5:33A41A56364A4ACD1D88153DDD4AF716 | SHA256:98D9C64CF6E0B137C78B09E65C46D688A2723F53570801AF766BBA16732157C8 | |||
| 7764 | Sigmanly_c35dbaea459fad5a3e45910735c1fffdfbbeab24296a0820878312df7285c2be.exe | C:\Users\admin\AppData\Local\Temp\nsvD257.tmp\modern-header.bmp | image | |
MD5:92016B43B022594E035C13F84C9C8783 | SHA256:2EB485BB2731F23B04064571BA4F3B465F2FD1CF13CC5CDE13BA2C84BE6E68C8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
44
TCP/UDP connections
69
DNS requests
35
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 4.245.163.56:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 4.245.163.56:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | compressed | 23.9 Kb | whitelisted |
7924 | SIHClient.exe | GET | 200 | 104.124.11.17:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7924 | SIHClient.exe | GET | 200 | 104.124.11.17:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
7924 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7924 | SIHClient.exe | GET | 200 | 104.124.11.17:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
7924 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
7924 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
7924 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 40.69.42.241:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7924 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7924 | SIHClient.exe | 104.124.11.17:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
7924 | SIHClient.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
7924 | SIHClient.exe | 13.85.23.206:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7316 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Generic Protocol Command Decode | SURICATA STREAM suspected RST injection |
— | — | Generic Protocol Command Decode | SURICATA STREAM suspected RST injection |
— | — | Generic Protocol Command Decode | SURICATA STREAM suspected RST injection |
— | — | Generic Protocol Command Decode | SURICATA HTTP Request abnormal Content-Encoding header |
— | — | Potentially Bad Traffic | ET INFO Possible Chrome Plugin install |