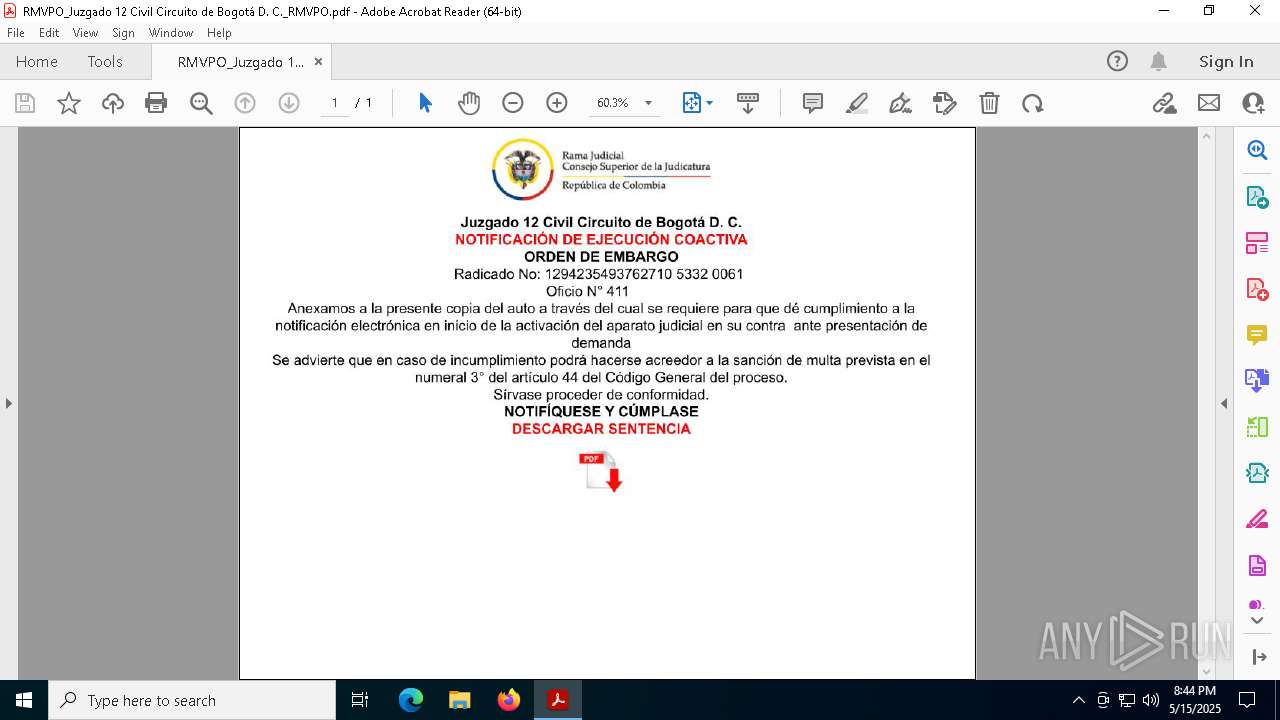
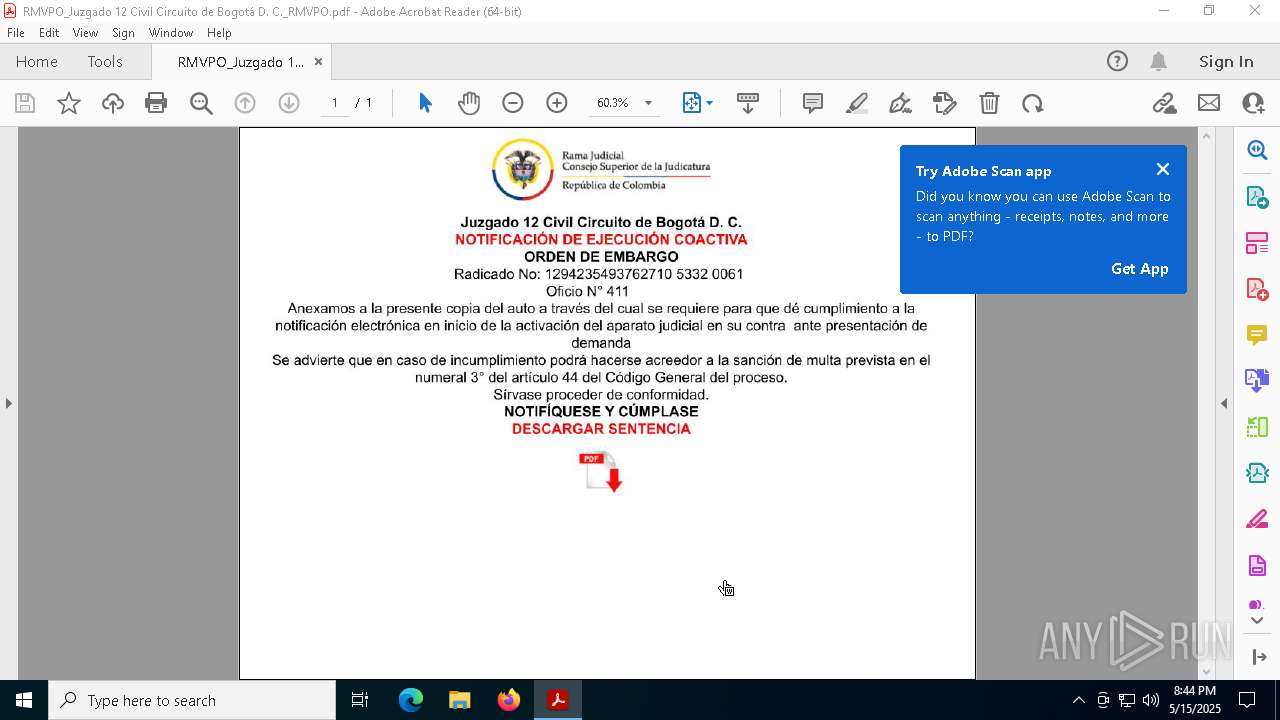
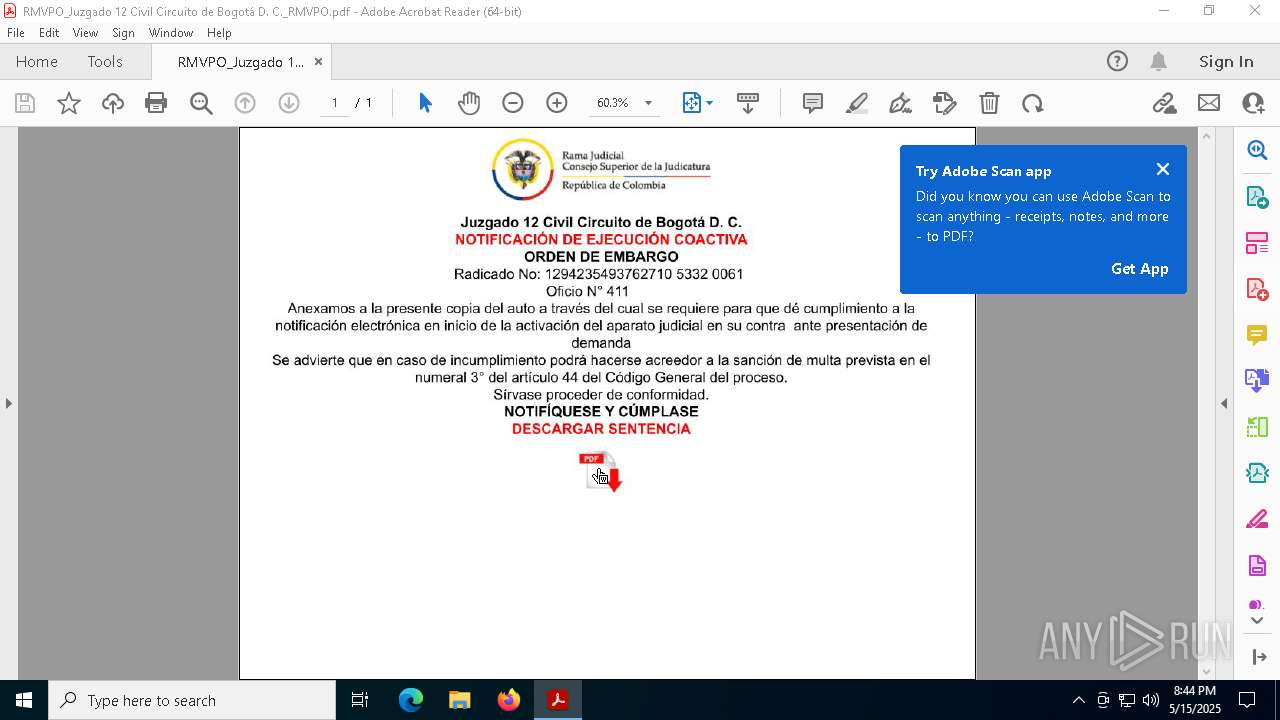
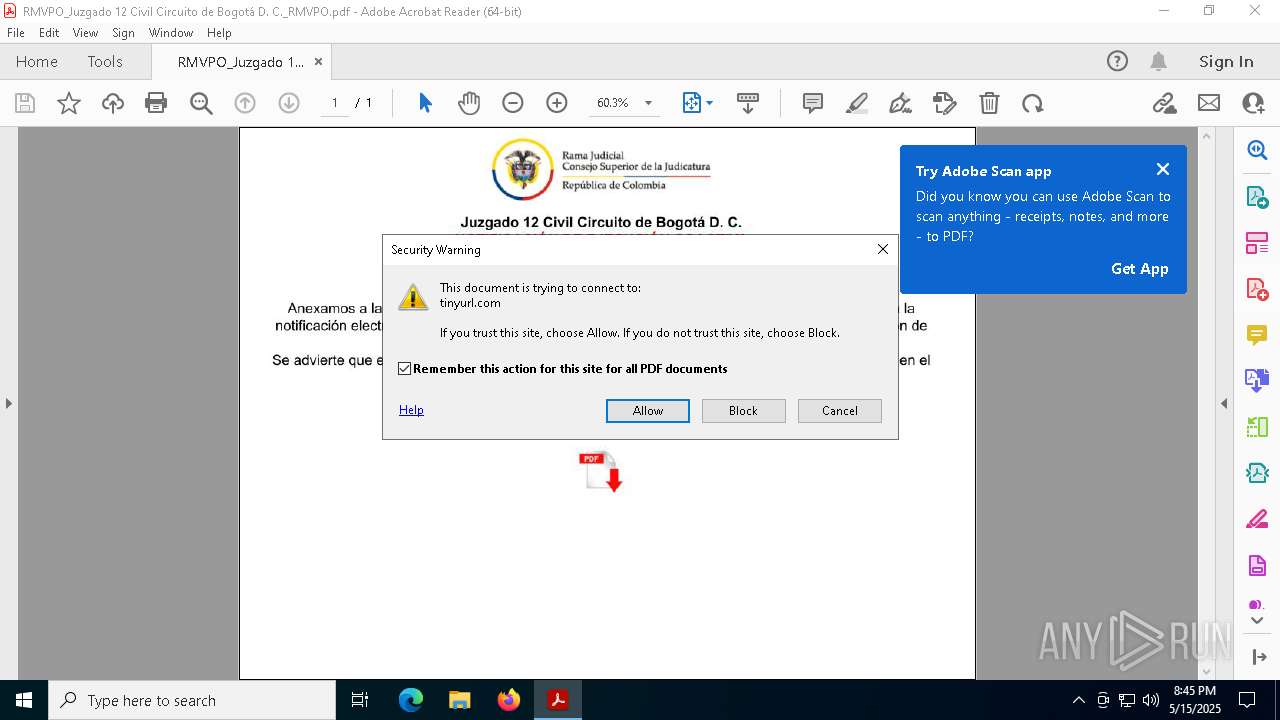
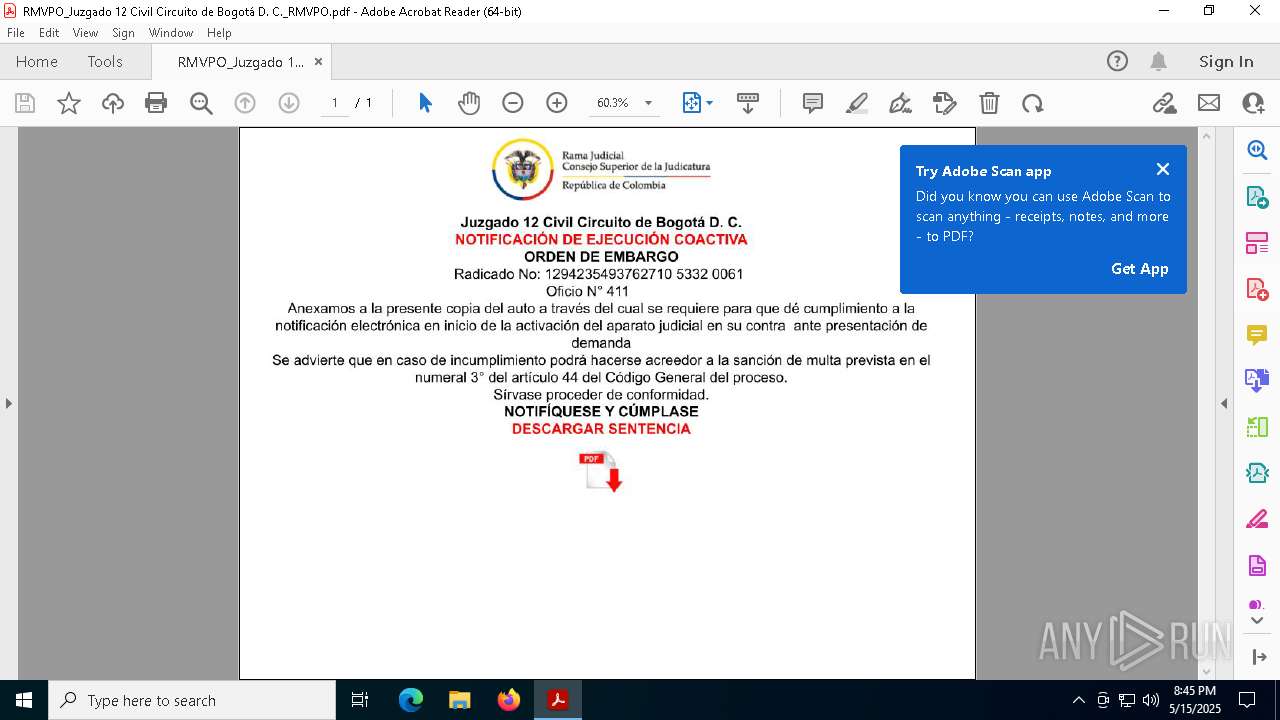
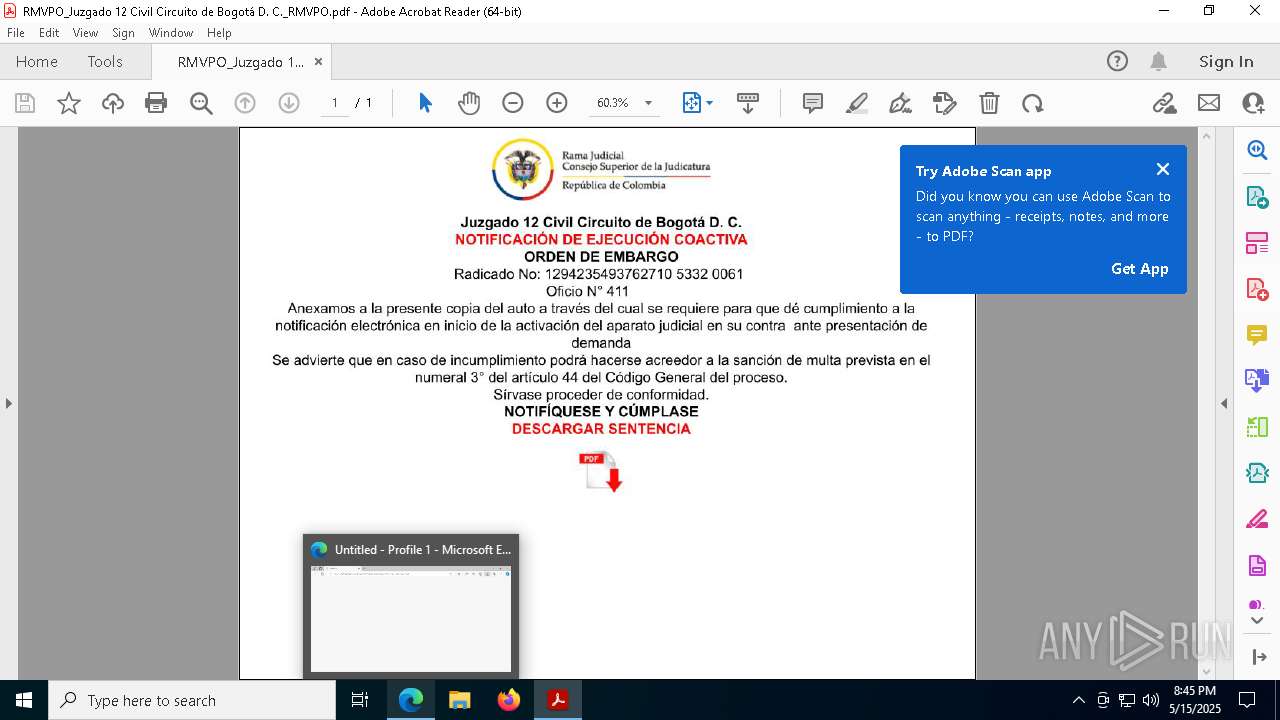
| File name: | RMVPO_Juzgado 12 Civil Circuito de Bogotá D. C._RMVPO.pdf |
| Full analysis: | https://app.any.run/tasks/39bf53b1-61ef-46b7-9c23-2d0bb04c6003 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2025, 20:44:35 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/pdf |
| File info: | PDF document, version 1.4, 1 page(s) |
| MD5: | 2F0652001B36330CF38060B490A43547 |
| SHA1: | 20072A373786E338285B2E2B6214652EB642286A |
| SHA256: | C34891CA435044D22897E10667E59E36DEDFF95A3F6623010B1715B0B0977AC6 |
| SSDEEP: | 49152:seaUSvvuolKyW98X2Y9Dvv3sSoMbsUTDtJri2m5IJYtxxDSIneMDOK8ngqaEYELo:n8H1MnK9Dvv3/oMZTDv+2m5gYtx1nLSq |
MALICIOUS
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 2852)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 2852)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 2852)
Run PowerShell with an invisible window
- powershell.exe (PID: 8820)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 8820)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 8820)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 2852)
The process executes JS scripts
- msedge.exe (PID: 7728)
Potential Corporate Privacy Violation
- wscript.exe (PID: 2852)
Runs shell command (SCRIPT)
- wscript.exe (PID: 2852)
Base64-obfuscated command line is found
- wscript.exe (PID: 2852)
The process bypasses the loading of PowerShell profile settings
- wscript.exe (PID: 2852)
Possibly malicious use of IEX has been detected
- wscript.exe (PID: 2852)
Executes script without checking the security policy
- powershell.exe (PID: 8820)
Probably obfuscated PowerShell command line is found
- wscript.exe (PID: 2852)
There is functionality for taking screenshot (YARA)
- AcroCEF.exe (PID: 1764)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 8820)
INFO
Application launched itself
- Acrobat.exe (PID: 7348)
- msedge.exe (PID: 7728)
- AcroCEF.exe (PID: 7884)
An automatically generated document
- Acrobat.exe (PID: 7348)
Reads the computer name
- identity_helper.exe (PID: 8908)
Reads Environment values
- identity_helper.exe (PID: 8908)
Reads Microsoft Office registry keys
- msedge.exe (PID: 7728)
Checks supported languages
- identity_helper.exe (PID: 8908)
Checks proxy server information
- wscript.exe (PID: 2852)
- powershell.exe (PID: 8820)
- slui.exe (PID: 5972)
Reads the software policy settings
- slui.exe (PID: 5972)
- slui.exe (PID: 7600)
Disables trace logs
- powershell.exe (PID: 8820)
Gets data length (POWERSHELL)
- powershell.exe (PID: 8820)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 8820)
Executable content was dropped or overwritten
- msedge.exe (PID: 3676)
The sample compiled with english language support
- msedge.exe (PID: 3676)
Converts byte array into Unicode string (POWERSHELL)
- powershell.exe (PID: 8820)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 8820)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| | | Adobe Portable Document Format (100) |
EXIF
| PDFVersion: | 1.4 |
|---|---|
| Linearized: | No |
| PageCount: | 1 |
| Producer: | iTextSharp™ 5.5.13.4 ©2000-2024 iText Group NV (AGPL-version) |
| CreateDate: | 2025:05:15 15:16:40-05:00 |
| ModifyDate: | 2025:05:15 15:16:40-05:00 |
| Title: | Unique PDF Document |
| Author: | Generated by Application |
| Subject: | Unique File 1 |
| Keywords: | ID-3d6d3d56-bebe-4b18-b892-02b765cf6c98 |
Total processes
198
Monitored processes
65
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 680 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2476 --field-trial-handle=2344,i,17246864893180527984,3294487202286528047,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 684 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7304 --field-trial-handle=2344,i,17246864893180527984,3294487202286528047,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 900 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6988 --field-trial-handle=2344,i,17246864893180527984,3294487202286528047,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1184 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --mojo-platform-channel-handle=3416 --field-trial-handle=1604,i,2441936684185260254,9335262927079121208,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1764 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=disabled --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=1728 --field-trial-handle=1604,i,2441936684185260254,9335262927079121208,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1852 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=1348 --field-trial-handle=2344,i,17246864893180527984,3294487202286528047,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2040 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3216 --field-trial-handle=2344,i,17246864893180527984,3294487202286528047,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2284 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=4032 --field-trial-handle=2344,i,17246864893180527984,3294487202286528047,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
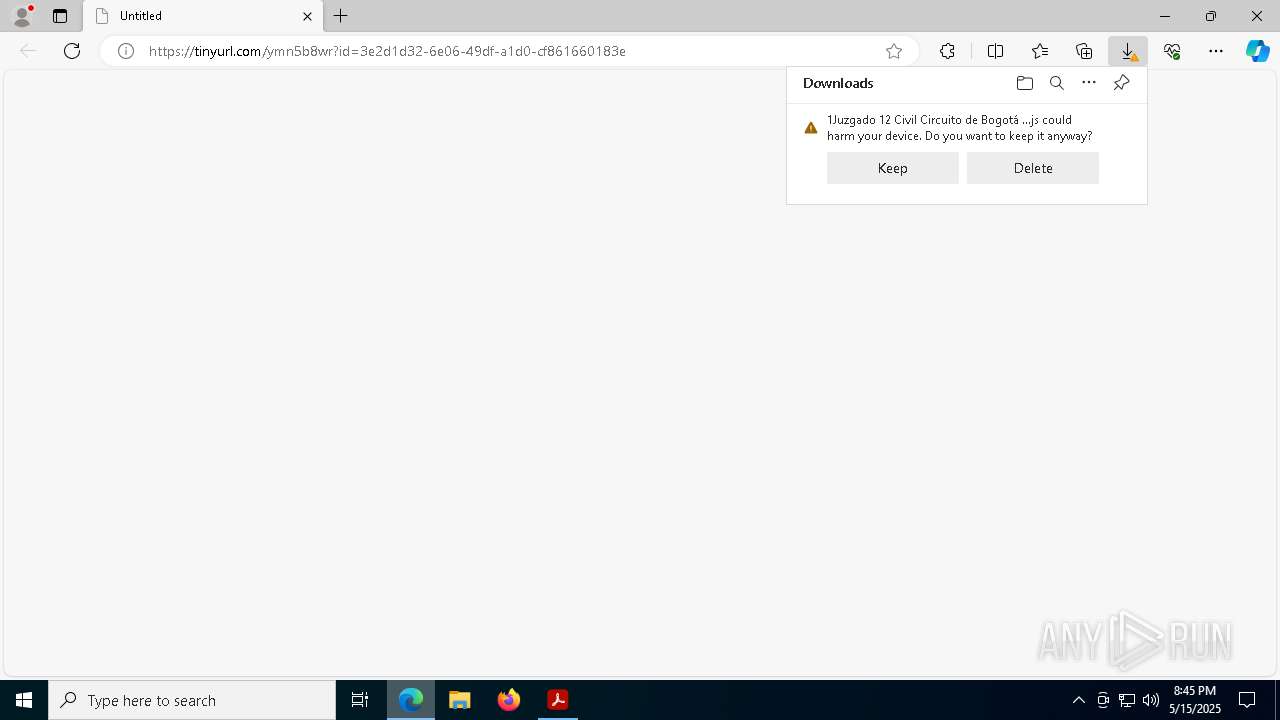
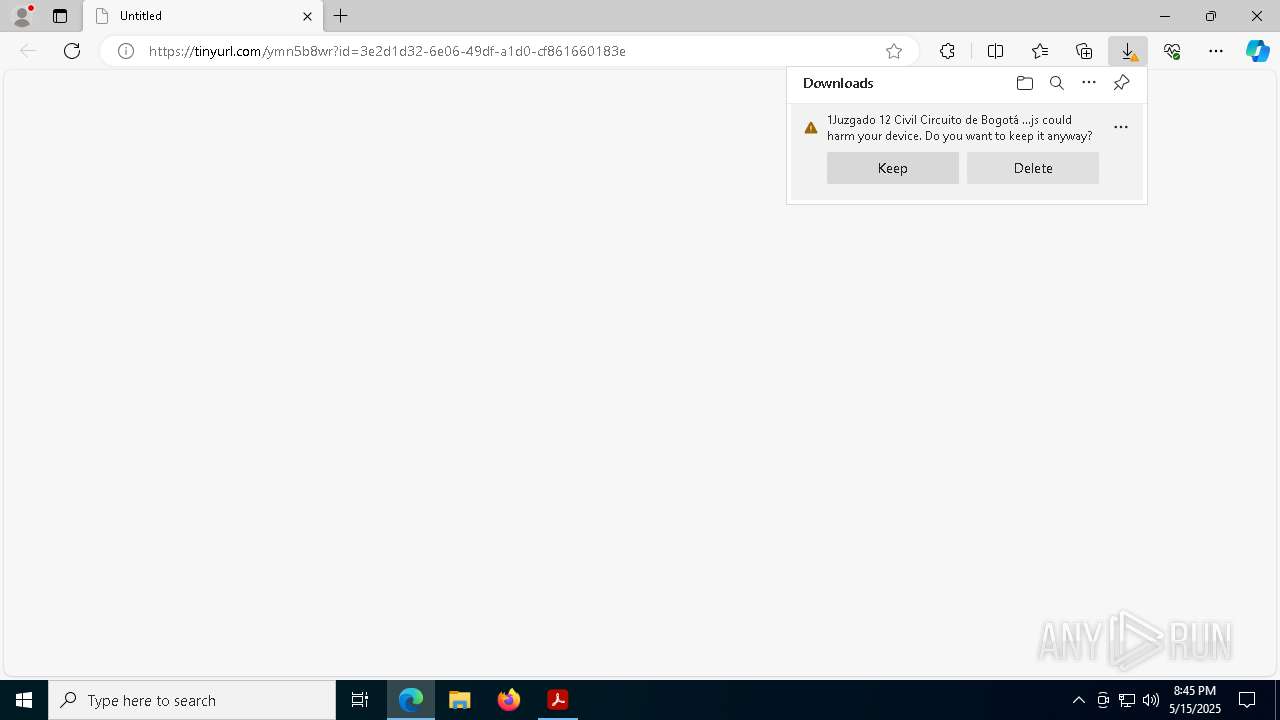
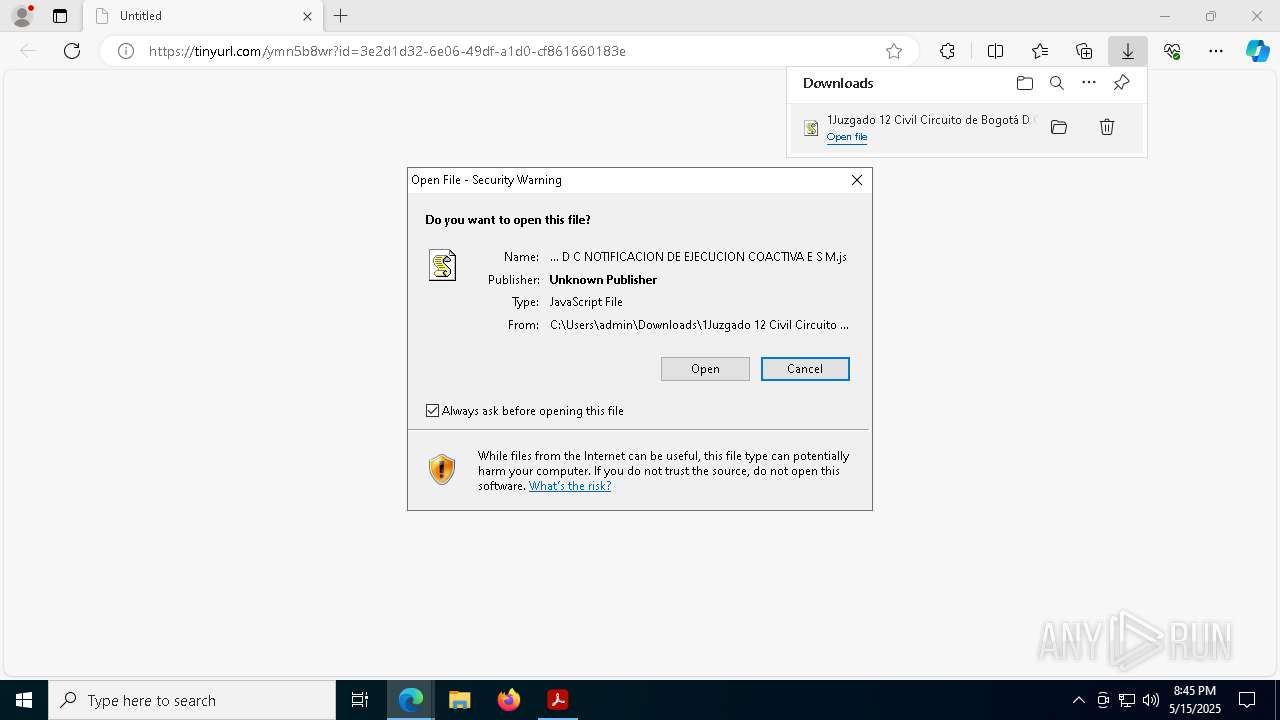
| 2852 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Downloads\1Juzgado 12 Civil Circuito de Bogotá D C NOTIFICACION DE EJECUCION COACTIVA E S M.js" | C:\Windows\System32\wscript.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 2908 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4140 --field-trial-handle=2344,i,17246864893180527984,3294487202286528047,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
29 021
Read events
28 897
Write events
122
Delete events
2
Modification events
| (PID) Process: | (7348) Acrobat.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Mappings\S-1-15-2-2034283098-2252572593-1072577386-2659511007-3245387615-27016815-3920691934 |
| Operation: | write | Name: | DisplayName |
Value: Adobe Acrobat Reader Protected Mode | |||
| (PID) Process: | (7516) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (7516) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\Collab\cDocumentCenter |
| Operation: | write | Name: | bAlwaysUseServer |
Value: 0 | |||
| (PID) Process: | (7516) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\Collab\cDocumentCenter |
| Operation: | write | Name: | bAlwaysUseServerFD |
Value: 0 | |||
| (PID) Process: | (7516) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\Collab\cDocumentCenter |
| Operation: | write | Name: | bDefault |
Value: 1 | |||
| (PID) Process: | (7516) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\Collab\cDocumentCenter |
| Operation: | write | Name: | bDefaultFD |
Value: 1 | |||
| (PID) Process: | (7516) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\Collab\cDocumentCenter |
| Operation: | write | Name: | tDistMethod |
Value: UPLOAD | |||
| (PID) Process: | (7516) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\Collab\cDocumentCenter\cSettings |
| Operation: | write | Name: | tcSetting |
Value: https://api.share.acrobat.com | |||
| (PID) Process: | (7516) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\Collab\cDocumentCenter |
| Operation: | write | Name: | tUI |
Value: Adobe online services (Recommended) | |||
| (PID) Process: | (7516) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\Collab\cDocumentCenter |
| Operation: | write | Name: | tURL |
Value: urn://ns.adobe.com/Collaboration/SharedReview/Acrobat.com | |||
Executable files
9
Suspicious files
440
Text files
78
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7516 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\Files\TESTING | binary | |
MD5:DC84B0D741E5BEAE8070013ADDCC8C28 | SHA256:81FF65EFC4487853BDB4625559E69AB44F19E0F5EFBD6D5B2AF5E3AB267C8E06 | |||
| 7884 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\aba6710fde0876af_0 | binary | |
MD5:D1F3EA14D07BFC10159EF8F0BB2A4288 | SHA256:F5662DAE031411A11B627DCA1F145AAA9C24232EDCC2105D42B90107A1BFDF0E | |||
| 7516 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SharedDataEvents-journal | binary | |
MD5:C9EDA681365B0D02910CB504F379FE8D | SHA256:C7A22B7FC96640C89CD4B68BAA8ECF96E872B5E6B7EEFBAC508C6293534036DB | |||
| 7884 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\LOG.old~RF10cd35.TMP | text | |
MD5:D012E5B4EB91B61F6E8AE2F8EC3C623E | SHA256:1BDA750084F20306722008016420E1912BA608CA8EFB9C661F7E7EFCF5E89673 | |||
| 7884 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\LOG.old | text | |
MD5:2EF1F7C0782D1A46974286420D24F629 | SHA256:D3A9BB7E09E1F4B0C41FF7808E930DDACF5DB3BACD98ECCF5BC7DB4863D1FCF5 | |||
| 7884 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Session Storage\LOG.old~RF10d34f.TMP | text | |
MD5:7383516745DEC1E86152192435F92D1F | SHA256:E22D34BBD915EEB277D4F4138D176EACE5577CF035EF7C2C80A4BC4D9B6C0E1D | |||
| 7516 | Acrobat.exe | C:\Users\admin\AppData\Local\Temp\acrobat_sbx\acroNGLLog.txt | text | |
MD5:E52F79A6524342D6885E26AE8451A0C9 | SHA256:6244A2467C942745A4B0871EA79D74E4DDDDB241CDF06F376400964916543C78 | |||
| 7348 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeSysFnt23.lst | binary | |
MD5:366B140BAFC863B7E366AA1E51604759 | SHA256:CBC8B288DBD2C72432081CF33CEF431572A94C7FB89DBCD59973B99E3871814E | |||
| 7516 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeFnt23.lst.7516 | binary | |
MD5:366B140BAFC863B7E366AA1E51604759 | SHA256:CBC8B288DBD2C72432081CF33CEF431572A94C7FB89DBCD59973B99E3871814E | |||
| 7516 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\SOPHIA.json | binary | |
MD5:837C1211E392A24D64C670DC10E8DA1B | SHA256:8013AC030684B86D754BBFBAB8A9CEC20CAA4DD9C03022715FF353DC10E14031 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
47
TCP/UDP connections
62
DNS requests
73
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.141:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
8580 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8580 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7348 | Acrobat.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAfy81yHqHeveu%2FpR5k1Jb0%3D | unknown | — | — | whitelisted |
2852 | wscript.exe | GET | 301 | 23.186.113.60:80 | http://paste.ee/d/1dOoR2mD/0 | unknown | — | — | shared |
1052 | svchost.exe | HEAD | 200 | 208.89.74.27:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1747703958&P2=404&P3=2&P4=eX6GnEX9Cf6m348DFVrBioQP9h7lLa%2bBqzYmQbjvcsOr%2fsyin2qOG%2fuqoDz9oo6PfOhnZ0Yg9lUHIhlDnsMvHg%3d%3d | unknown | — | — | whitelisted |
1052 | svchost.exe | GET | 206 | 208.89.74.27:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1747703958&P2=404&P3=2&P4=eX6GnEX9Cf6m348DFVrBioQP9h7lLa%2bBqzYmQbjvcsOr%2fsyin2qOG%2fuqoDz9oo6PfOhnZ0Yg9lUHIhlDnsMvHg%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.141:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
8044 | AcroCEF.exe | 23.213.164.167:443 | geo2.adobe.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |
p13n.adobe.io |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] URL Shortener TinyURL (tinyurl .com) |
2196 | svchost.exe | Misc activity | INFO [ANY.RUN] Possible short link service (tinyurl .com) |
680 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] URL Shortener TinyURL (tinyurl .com) |
680 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] URL Shortener TinyURL (tinyurl .com) |
680 | msedge.exe | Misc activity | INFO [ANY.RUN] Possible short link service (tinyurl .com) |
680 | msedge.exe | Misc activity | INFO [ANY.RUN] Possible short link service (tinyurl .com) |
680 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
680 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
2196 | svchost.exe | Misc activity | ET INFO Pastebin-like Service Domain in DNS Lookup (paste .ee) |
2852 | wscript.exe | Potential Corporate Privacy Violation | ET INFO Pastebin-style Service (paste .ee) in TLS SNI |