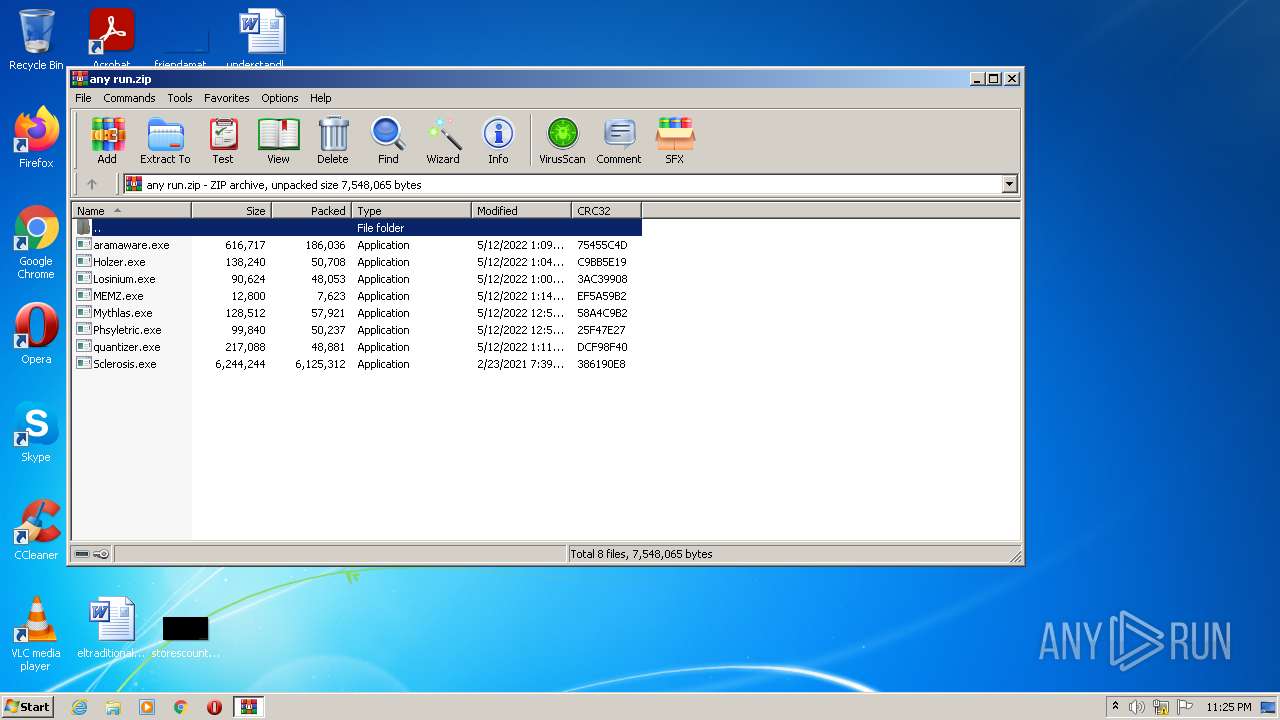
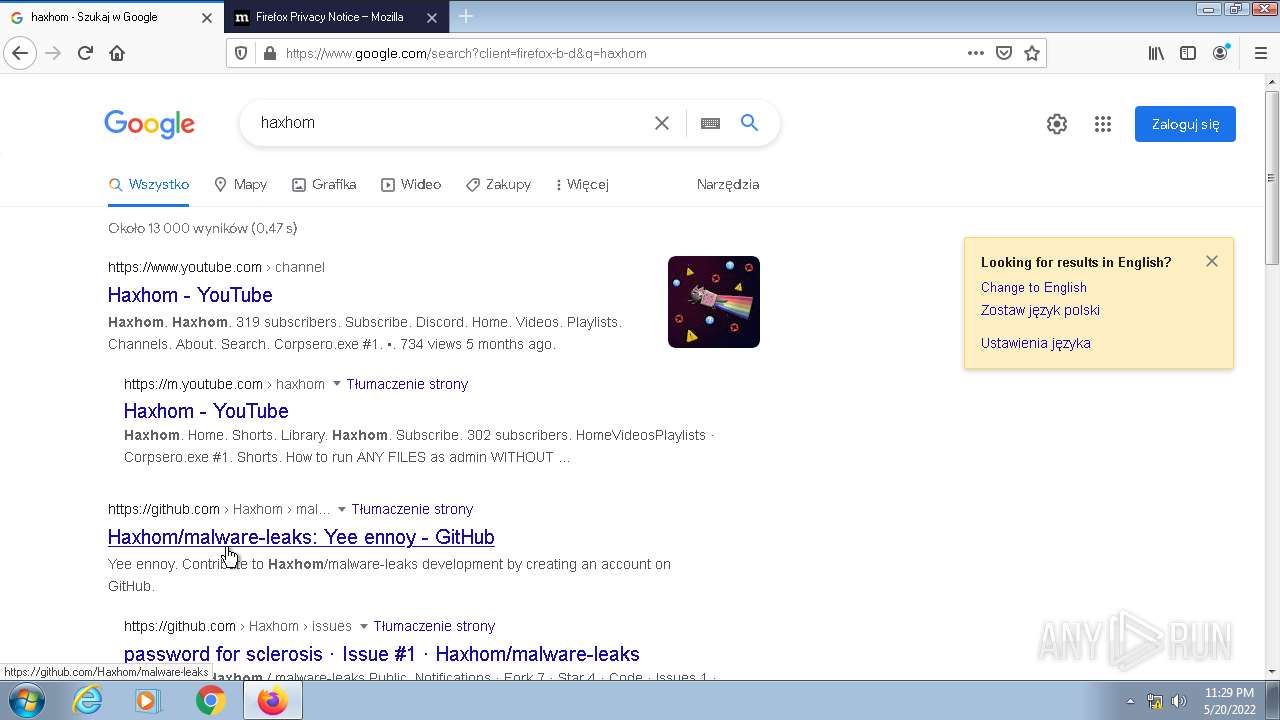
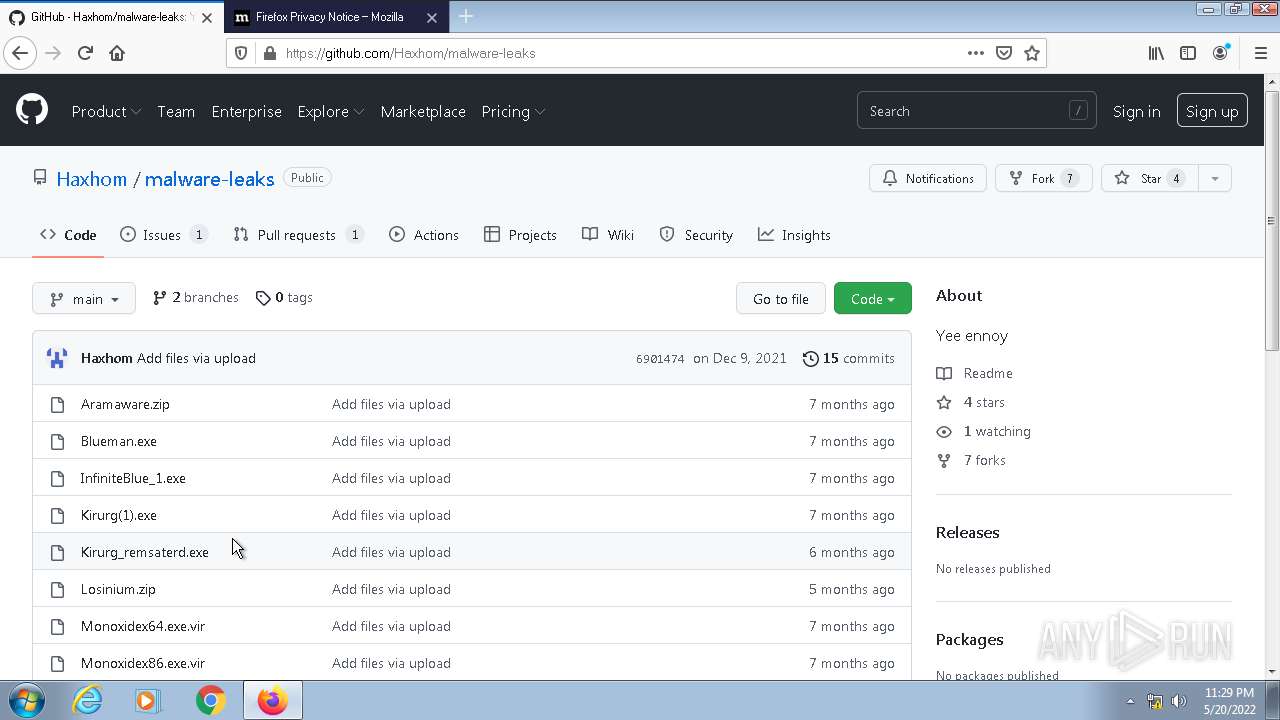
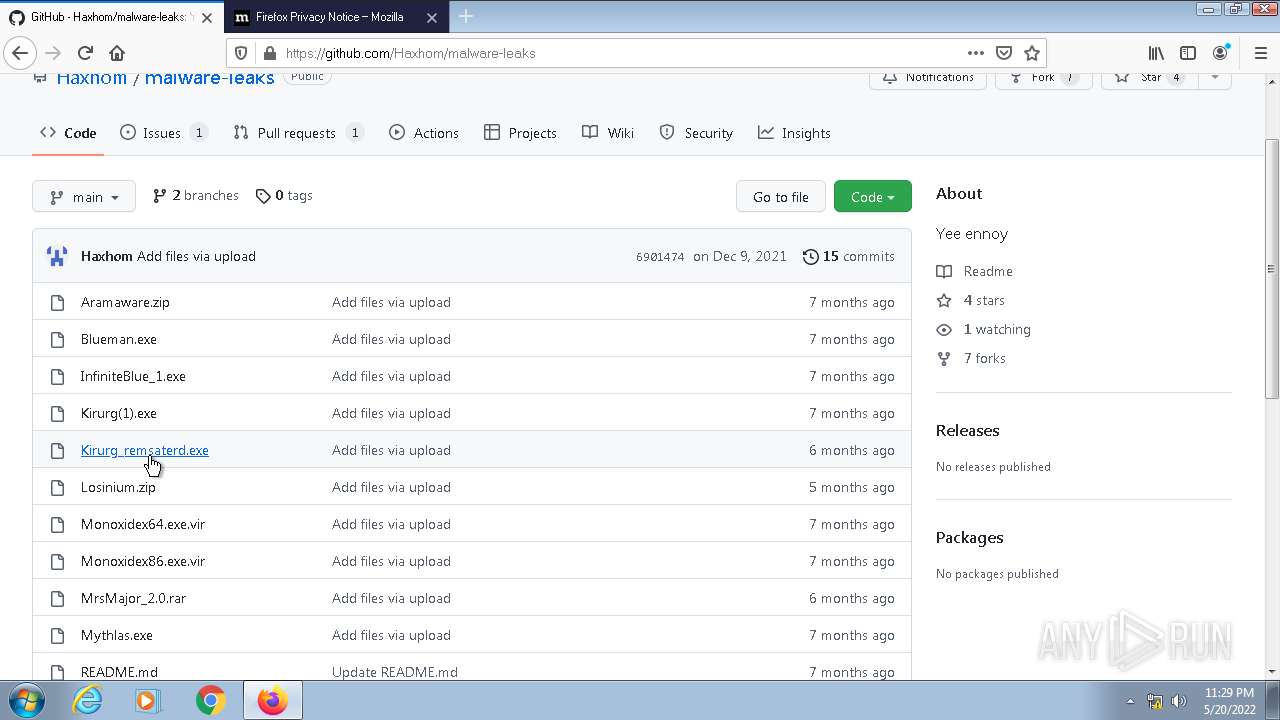
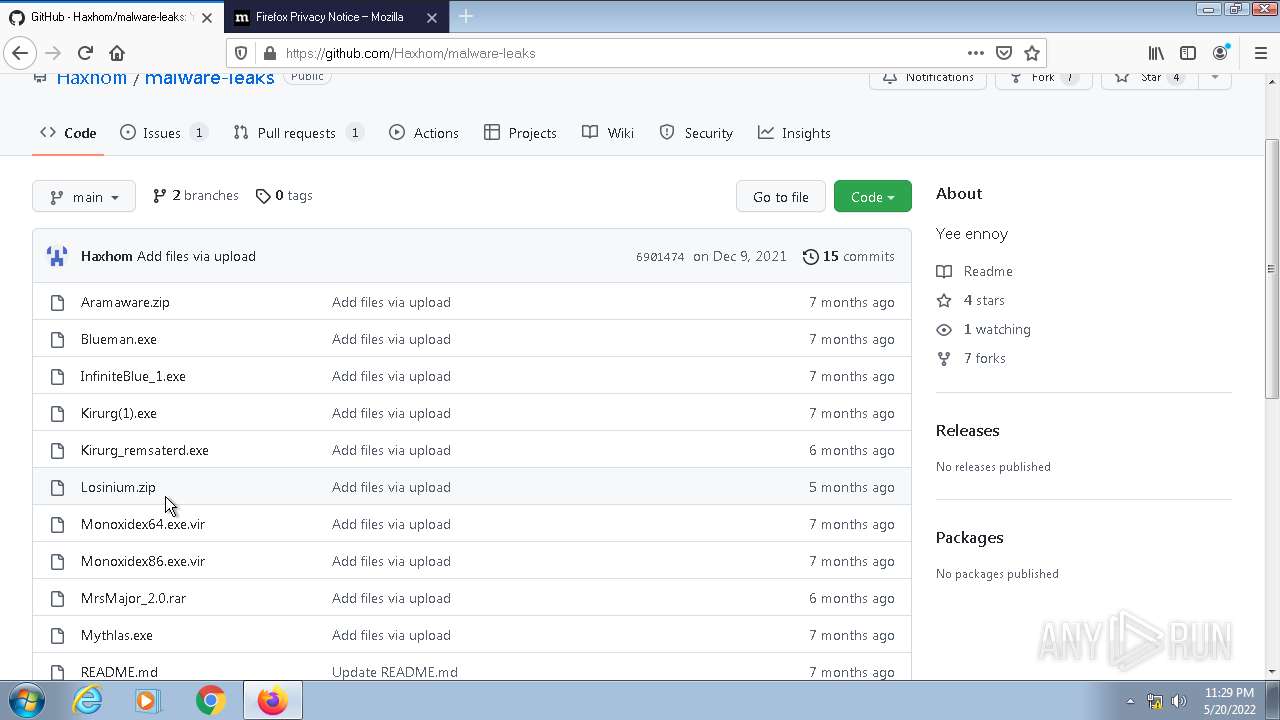
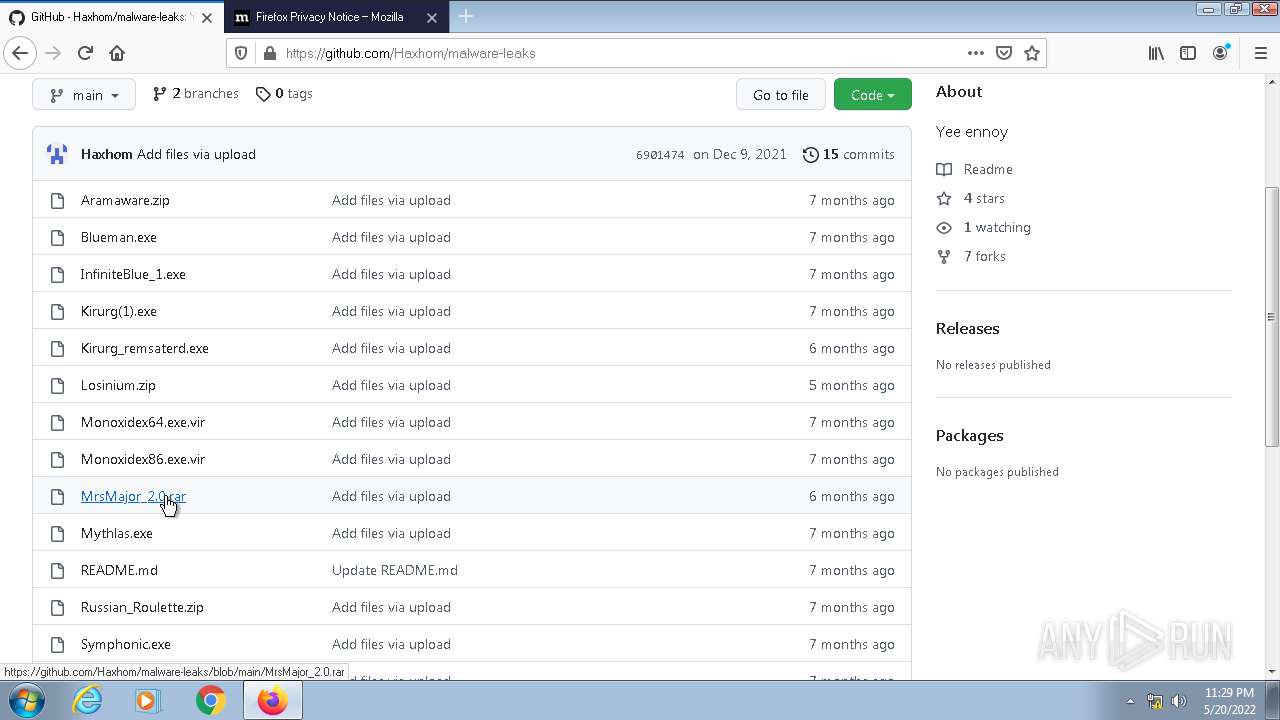
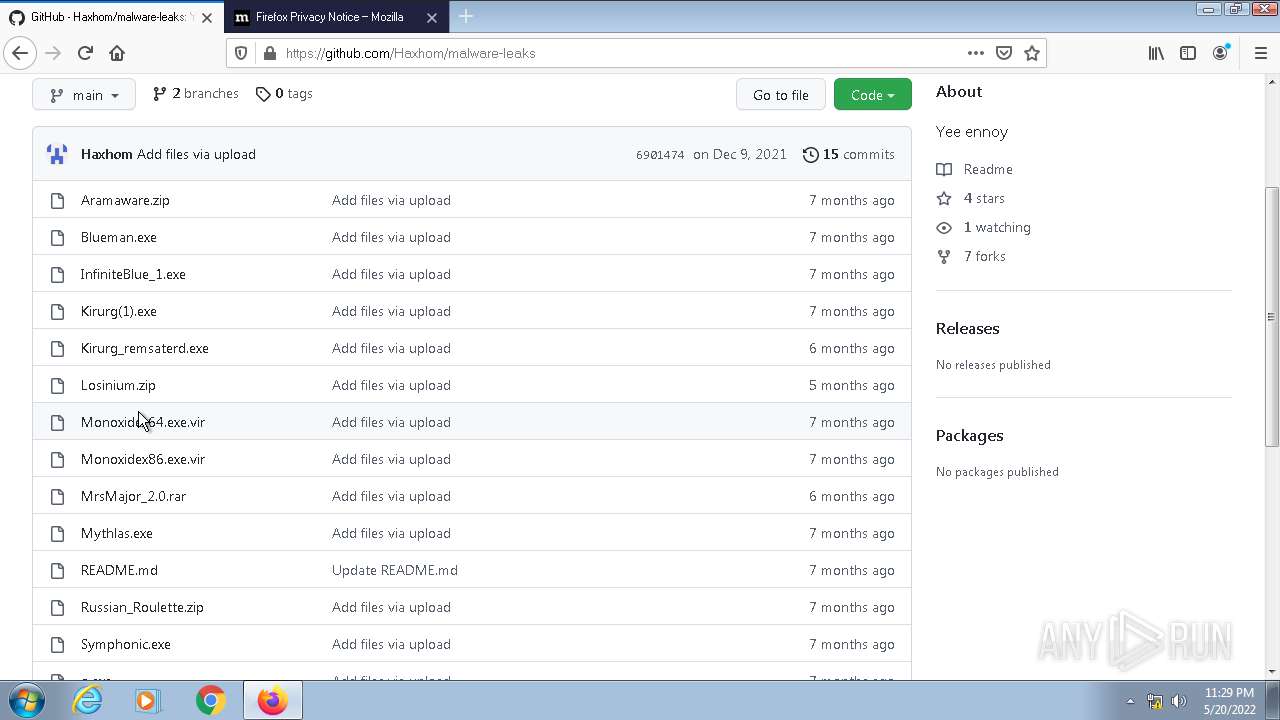
| File name: | any run.zip |
| Full analysis: | https://app.any.run/tasks/d5112b62-e515-4eeb-8dc2-578a0a2c80d1 |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2022, 22:25:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | D5580C9560F5FF87A09FC6100654D4E4 |
| SHA1: | 5F42337E5F30A7D73546BFBB399453D2328E5A8D |
| SHA256: | C33C4CC5639886BFF516F52872C773EC9D7D15B6CAAE3530753A0458B334C60B |
| SSDEEP: | 196608:XH/djrRJhxwSAGm7eGfp4mFWjsa0e1y8ky+q:XVvfH2lpbafT+q |
MALICIOUS
Changes internet zones settings
- ie4uinit.exe (PID: 1732)
- rundll32.exe (PID: 3428)
Writes to a start menu file
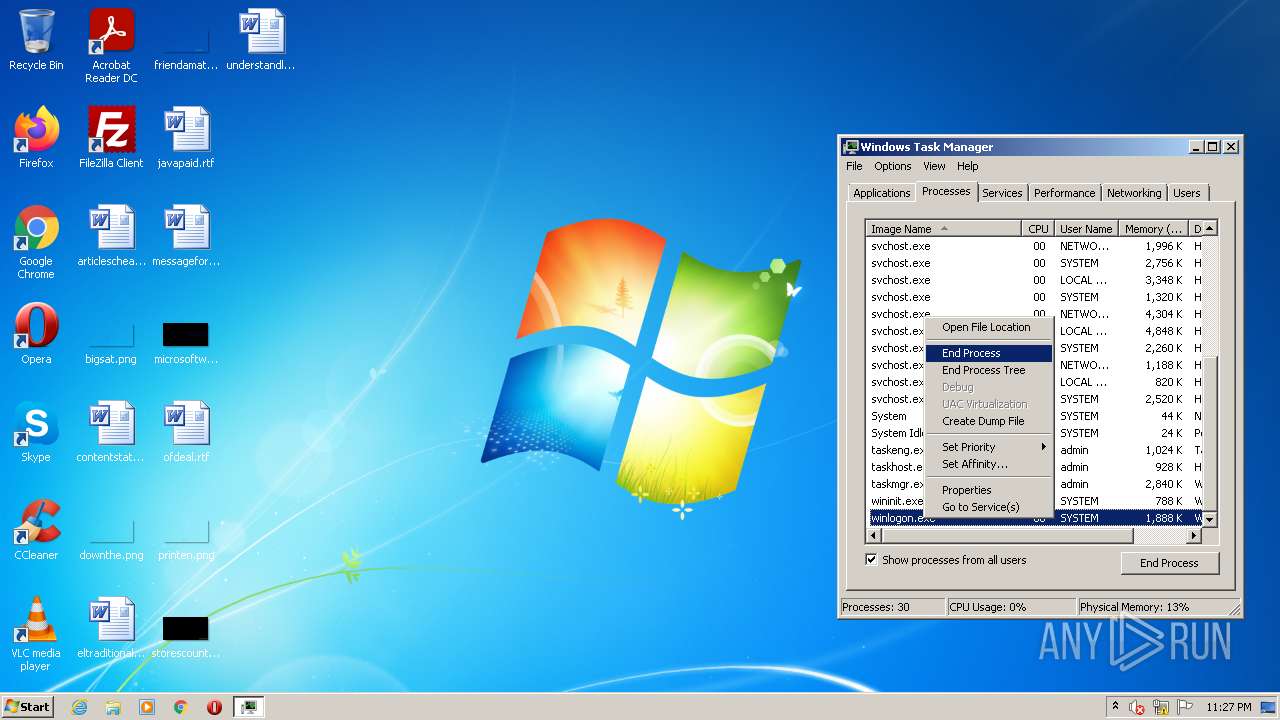
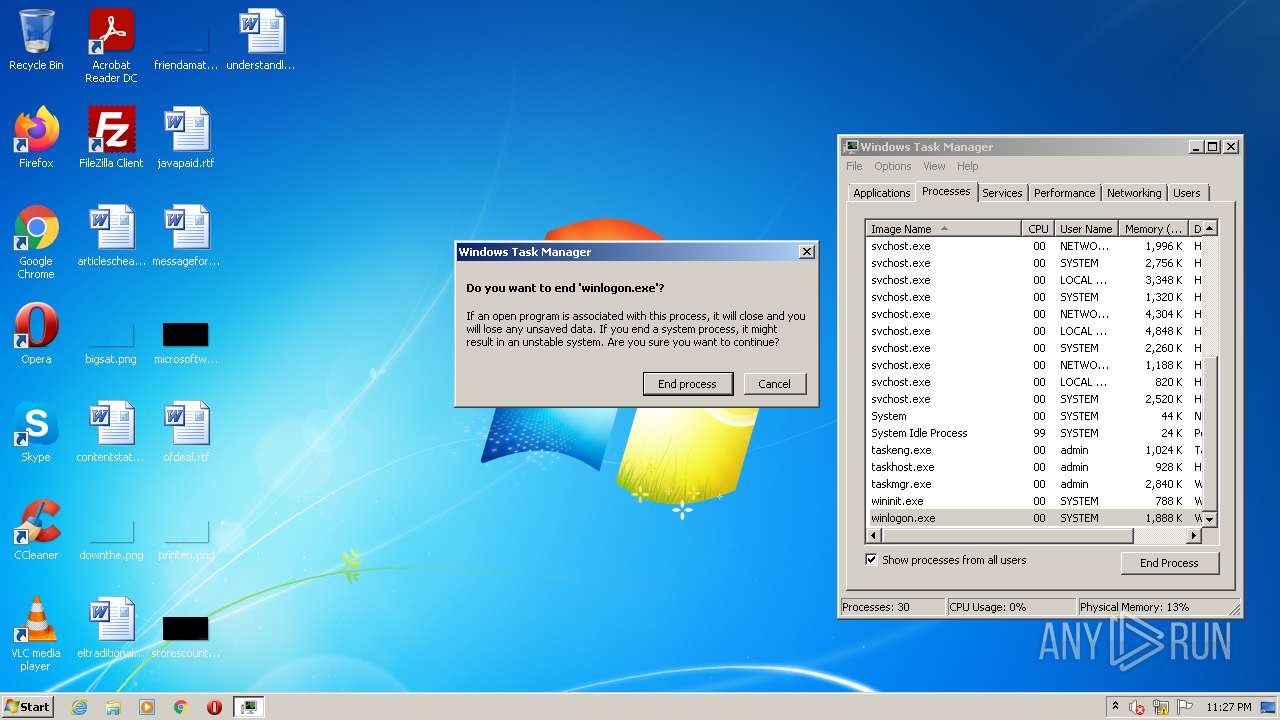
- regsvr32.exe (PID: 2536)
Changes the Startup folder
- regsvr32.exe (PID: 2536)
Drops executable file immediately after starts
- firefox.exe (PID: 3900)
Application was dropped or rewritten from another process
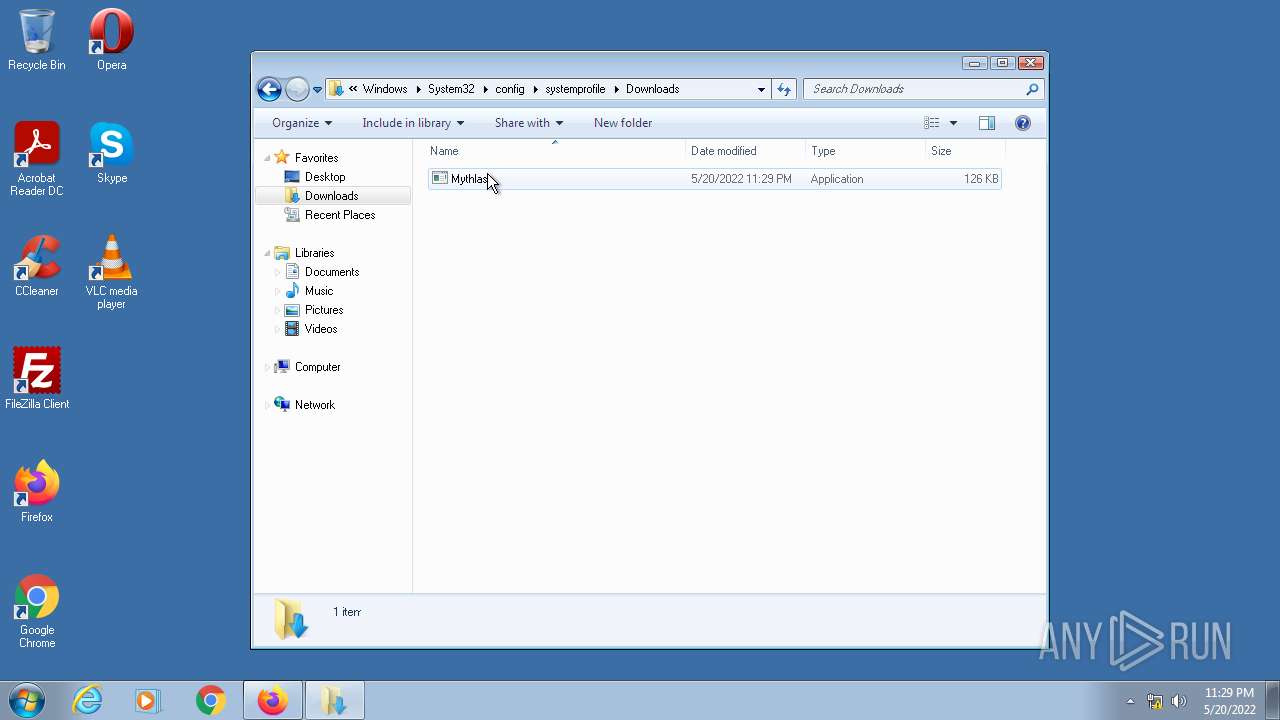
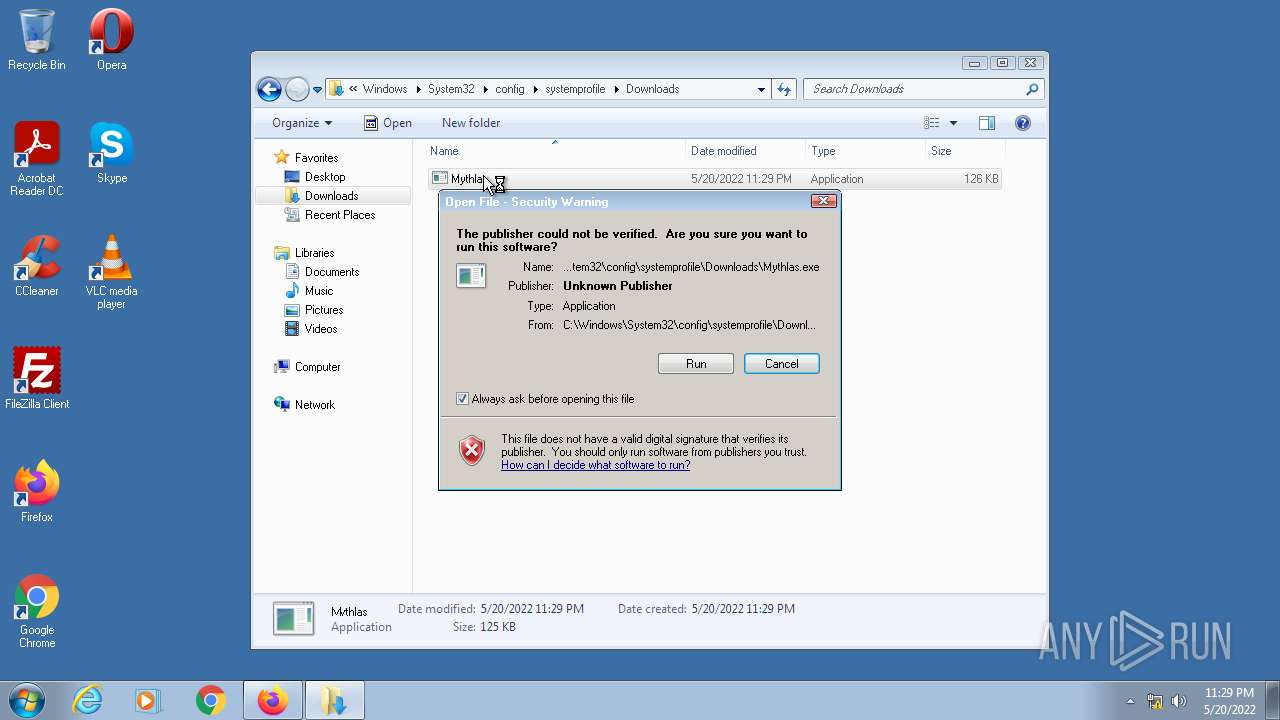
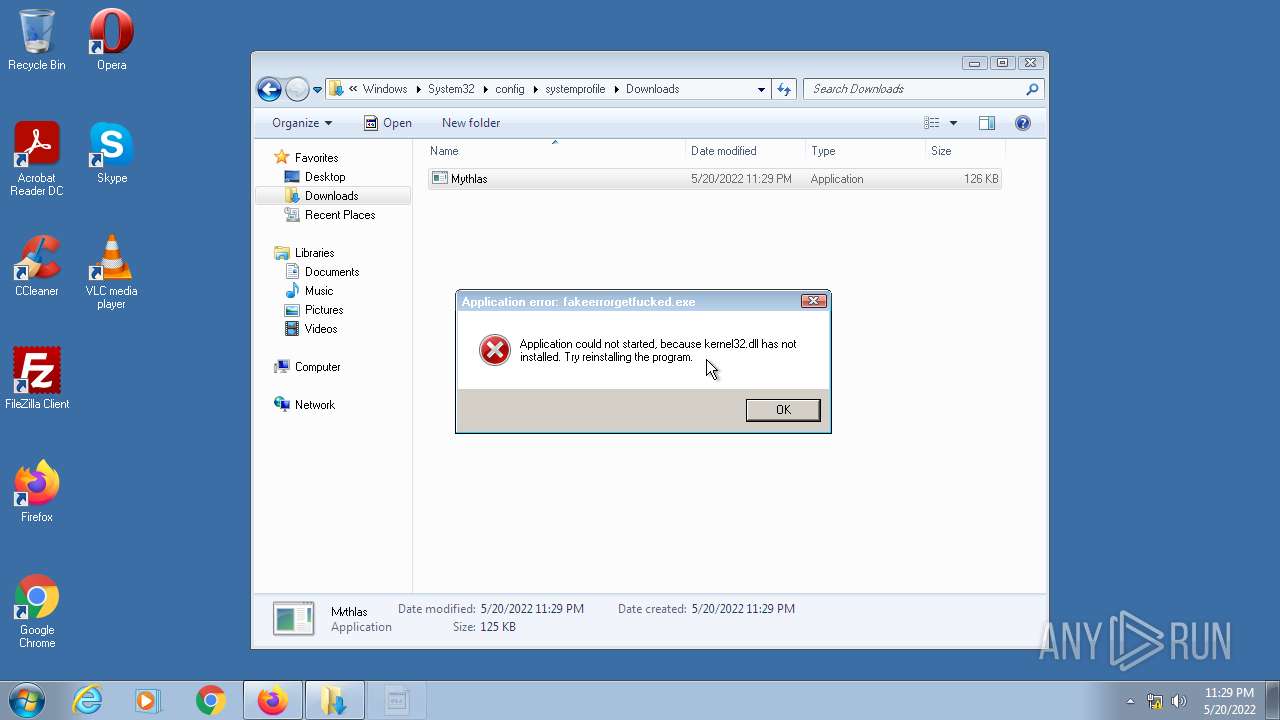
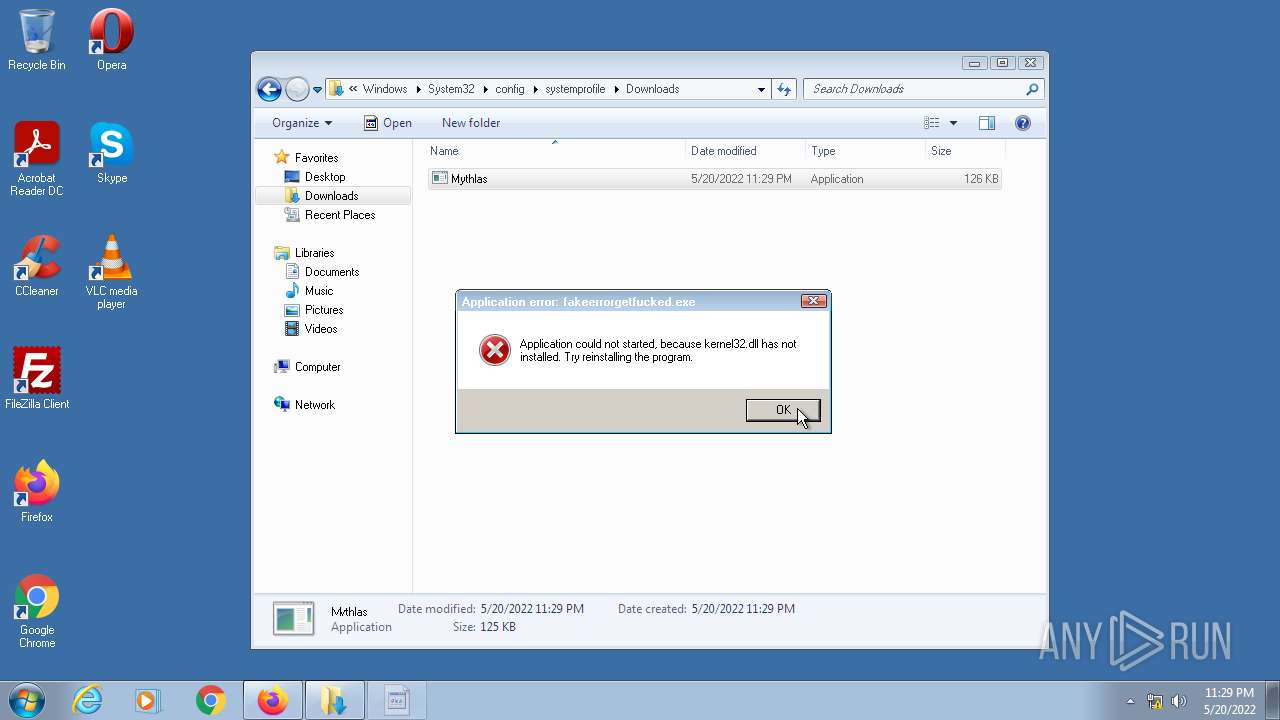
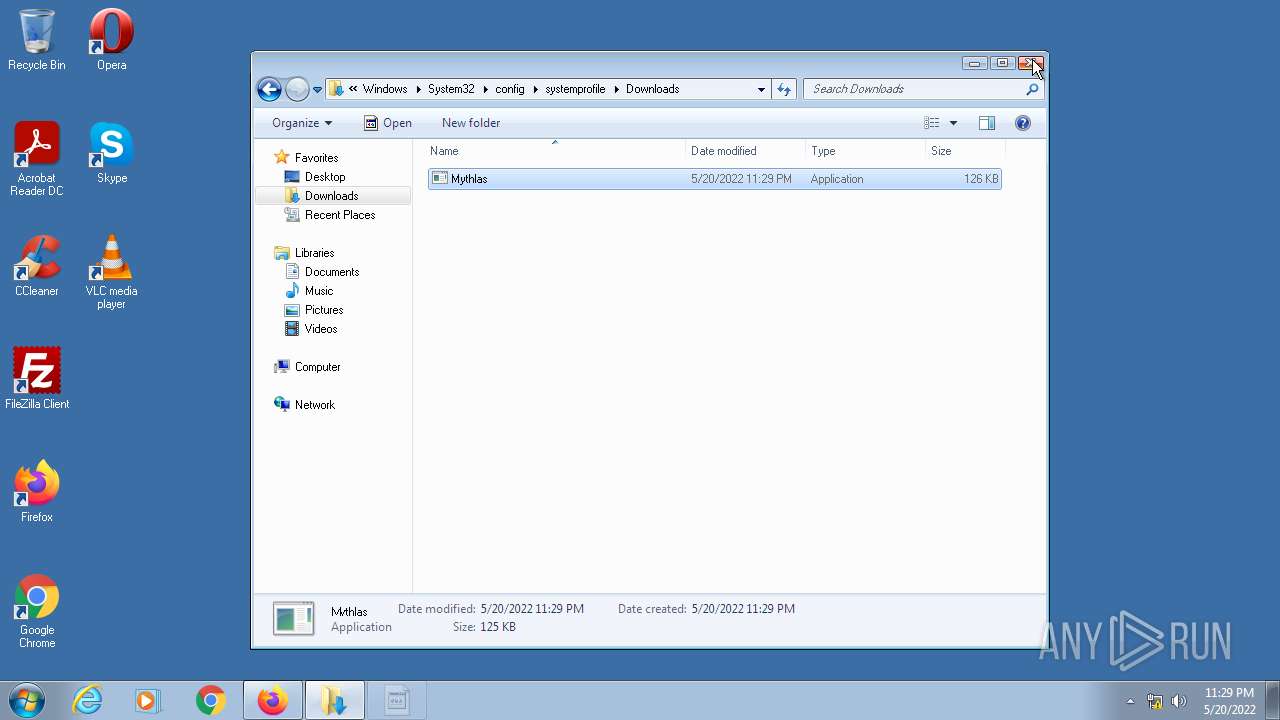
- Mythlas.exe (PID: 1836)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 2972)
- WinMail.exe (PID: 2332)
- chrmstp.exe (PID: 1876)
- chrmstp.exe (PID: 2804)
- IMEKLMG.EXE (PID: 2352)
- IMEKLMG.EXE (PID: 2464)
- jusched.exe (PID: 1188)
- imkrmig.exe (PID: 2956)
- Mythlas.exe (PID: 1836)
Reads the computer name
- WinRAR.exe (PID: 2972)
- WinMail.exe (PID: 2332)
- chrmstp.exe (PID: 1876)
- IMEKLMG.EXE (PID: 2464)
- IMEKLMG.EXE (PID: 2352)
- Mythlas.exe (PID: 1836)
Application launched itself
- taskmgr.exe (PID: 2392)
- ie4uinit.exe (PID: 1732)
- rundll32.exe (PID: 3632)
- chrmstp.exe (PID: 1876)
Executed as Windows Service
- taskhost.exe (PID: 1728)
- EOSNotify.exe (PID: 2272)
Creates files in the Windows directory
- ie4uinit.exe (PID: 1732)
- regsvr32.exe (PID: 3648)
- WinMail.exe (PID: 2332)
- unregmp2.exe (PID: 2908)
- regsvr32.exe (PID: 2536)
- chrmstp.exe (PID: 1876)
- chrmstp.exe (PID: 2804)
- jusched.exe (PID: 1188)
- IMEKLMG.EXE (PID: 2352)
- firefox.exe (PID: 3900)
Writes to a desktop.ini file (may be used to cloak folders)
- ie4uinit.exe (PID: 1732)
- WinMail.exe (PID: 2332)
- unregmp2.exe (PID: 2908)
- regsvr32.exe (PID: 2536)
Removes files from Windows directory
- ie4uinit.exe (PID: 1732)
- RunDll32.exe (PID: 3720)
- WinMail.exe (PID: 2332)
- unregmp2.exe (PID: 2908)
- regsvr32.exe (PID: 2536)
- firefox.exe (PID: 3900)
Uses RUNDLL32.EXE to load library
- ie4uinit.exe (PID: 1732)
- rundll32.exe (PID: 3632)
Changes the started page of IE
- ie4uinit.exe (PID: 1732)
Creates files in the program directory
- ie4uinit.exe (PID: 1732)
- chrmstp.exe (PID: 1876)
Reads Microsoft Outlook installation path
- ie4uinit.exe (PID: 1732)
Reads Environment values
- unregmp2.exe (PID: 2908)
Changes default file association
- unregmp2.exe (PID: 2908)
Reads the date of Windows installation
- chrmstp.exe (PID: 1876)
Executed via Task Scheduler
- sipnotify.exe (PID: 2276)
Check for Java to be installed
- jusched.exe (PID: 1188)
Executable content was dropped or overwritten
- firefox.exe (PID: 3900)
Drops a file with a compile date too recent
- firefox.exe (PID: 3900)
INFO
Manual execution by user
- taskmgr.exe (PID: 2392)
- ie4uinit.exe (PID: 1732)
- regsvr32.exe (PID: 3648)
- WinMail.exe (PID: 2332)
- ie4uinit.exe (PID: 3640)
- unregmp2.exe (PID: 2908)
- ie4uinit.exe (PID: 1024)
- regsvr32.exe (PID: 2536)
- rundll32.exe (PID: 3428)
- chrmstp.exe (PID: 1876)
- IMEKLMG.EXE (PID: 2352)
- IMEKLMG.EXE (PID: 2464)
- jusched.exe (PID: 1188)
- firefox.exe (PID: 440)
- Mythlas.exe (PID: 1836)
Reads the computer name
- taskmgr.exe (PID: 2392)
- taskmgr.exe (PID: 3096)
- ie4uinit.exe (PID: 1732)
- taskhost.exe (PID: 1728)
- rundll32.exe (PID: 3632)
- rundll32.exe (PID: 3556)
- RunDll32.exe (PID: 3180)
- RunDll32.exe (PID: 3720)
- regsvr32.exe (PID: 3648)
- regsvr32.exe (PID: 2536)
- EOSNotify.exe (PID: 2272)
- ie4uinit.exe (PID: 3452)
- sipnotify.exe (PID: 2276)
- firefox.exe (PID: 3900)
- firefox.exe (PID: 2856)
- firefox.exe (PID: 3392)
- firefox.exe (PID: 1588)
- firefox.exe (PID: 1768)
- firefox.exe (PID: 3332)
- firefox.exe (PID: 3992)
- firefox.exe (PID: 952)
- firefox.exe (PID: 2860)
- unregmp2.exe (PID: 2908)
Checks supported languages
- taskmgr.exe (PID: 3096)
- taskhost.exe (PID: 1728)
- ie4uinit.exe (PID: 3452)
- ie4uinit.exe (PID: 1732)
- taskmgr.exe (PID: 2392)
- rundll32.exe (PID: 3556)
- RunDll32.exe (PID: 3720)
- RunDll32.exe (PID: 3180)
- regsvr32.exe (PID: 3648)
- rundll32.exe (PID: 3632)
- ie4uinit.exe (PID: 3640)
- unregmp2.exe (PID: 2908)
- ie4uinit.exe (PID: 1024)
- regsvr32.exe (PID: 2536)
- rundll32.exe (PID: 3428)
- EOSNotify.exe (PID: 2272)
- sipnotify.exe (PID: 2276)
- firefox.exe (PID: 440)
- firefox.exe (PID: 3900)
- firefox.exe (PID: 3332)
- firefox.exe (PID: 2856)
- firefox.exe (PID: 1768)
- firefox.exe (PID: 952)
- firefox.exe (PID: 3992)
- firefox.exe (PID: 3392)
- firefox.exe (PID: 2860)
- firefox.exe (PID: 1588)
Application launched itself
- firefox.exe (PID: 440)
- firefox.exe (PID: 3900)
Creates files in the program directory
- firefox.exe (PID: 3900)
Reads CPU info
- firefox.exe (PID: 3900)
Reads the date of Windows installation
- firefox.exe (PID: 3900)
Checks Windows Trust Settings
- firefox.exe (PID: 3900)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | aramaware.exe |
|---|---|
| ZipUncompressedSize: | 616717 |
| ZipCompressedSize: | 186036 |
| ZipCRC: | 0x75455c4d |
| ZipModifyDate: | 2022:05:12 13:09:21 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
94
Monitored processes
36
Malicious processes
7
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 440 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | Explorer.EXE |
User: Administrator Company: Mozilla Corporation Integrity Level: HIGH Description: Firefox Exit code: 0 Version: 83.0 | ||||
| 952 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3900.6.2045576270\1078056272" -childID 1 -isForBrowser -prefsHandle 2196 -prefMapHandle 2192 -prefsLen 1360 -prefMapSize 228868 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 3900 "\\.\pipe\gecko-crash-server-pipe.3900" 2208 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe |
User: Administrator Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 | ||||
| 1024 | "C:\Windows\System32\ie4uinit.exe" -DisableSSL3 | C:\Windows\System32\ie4uinit.exe | — | Explorer.EXE |
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: IE Per-User Initialization Utility Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) | ||||
| 1188 | "C:\Program Files\Common Files\Java\Java Update\jusched.exe" | C:\Program Files\Common Files\Java\Java Update\jusched.exe | — | Explorer.EXE |
User: Administrator Company: Oracle Corporation Integrity Level: HIGH Description: Java Update Scheduler Exit code: 0 Version: 2.8.271.9 | ||||
| 1588 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3900.34.343091855\469503767" -childID 5 -isForBrowser -prefsHandle 3016 -prefMapHandle 1576 -prefsLen 11691 -prefMapSize 228868 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 3900 "\\.\pipe\gecko-crash-server-pipe.3900" 3384 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe |
User: Administrator Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 | ||||
| 1728 | "taskhost.exe" | C:\Windows\system32\taskhost.exe | — | services.exe |
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Host Process for Windows Tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 1732 | "C:\Windows\System32\ie4uinit.exe" -UserConfig | C:\Windows\System32\ie4uinit.exe | — | Explorer.EXE |
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: IE Per-User Initialization Utility Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) | ||||
| 1768 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3900.20.1473059443\111549355" -childID 3 -isForBrowser -prefsHandle 5392 -prefMapHandle 5388 -prefsLen 1797 -prefMapSize 228868 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 3900 "\\.\pipe\gecko-crash-server-pipe.3900" 5404 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe |
User: Administrator Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 | ||||
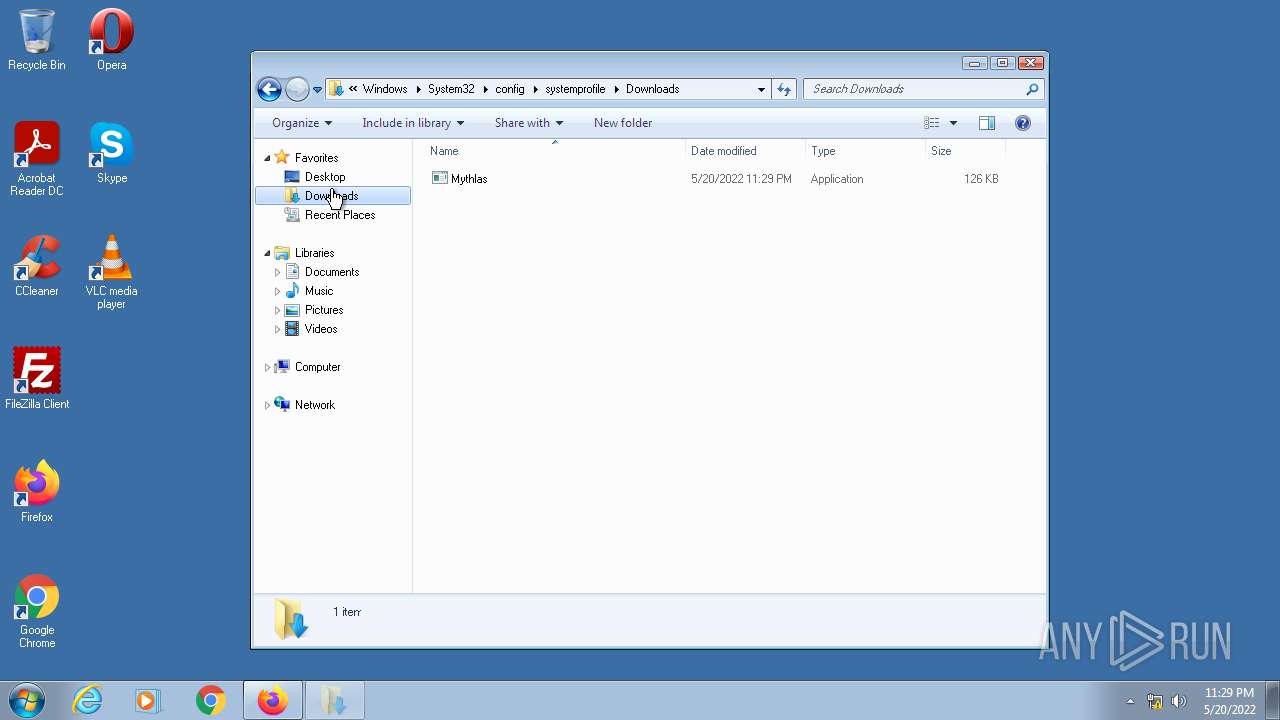
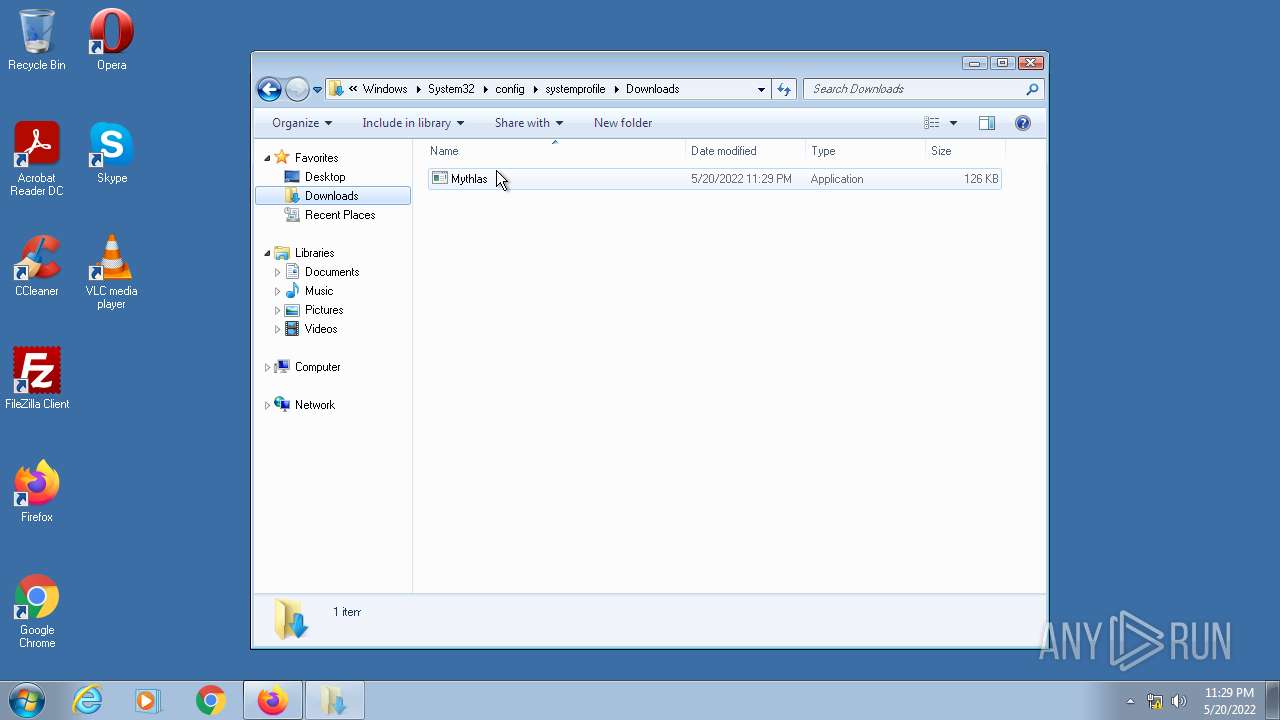
| 1836 | "C:\Windows\System32\config\systemprofile\Downloads\Mythlas.exe" | C:\Windows\System32\config\systemprofile\Downloads\Mythlas.exe | — | Explorer.EXE |
User: Administrator Integrity Level: HIGH Exit code: 0 | ||||
| 1876 | "C:\Program Files\Google\Chrome\Application\86.0.4240.198\Installer\chrmstp.exe" --configure-user-settings --verbose-logging --system-level | C:\Program Files\Google\Chrome\Application\86.0.4240.198\Installer\chrmstp.exe | — | Explorer.EXE |
User: Administrator Company: Google LLC Integrity Level: HIGH Description: Google Chrome Installer Exit code: 0 Version: 86.0.4240.198 | ||||
Total events
21 954
Read events
20 120
Write events
1 813
Delete events
21
Modification events
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\any run.zip | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
2
Suspicious files
334
Text files
199
Unknown types
93
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1732 | ie4uinit.exe | C:\Windows\system32\config\systemprofile\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Accessories\System Tools\Internet Explorer (No Add-ons).lnk | lnk | |
MD5:— | SHA256:— | |||
| 1732 | ie4uinit.exe | C:\Windows\INF\setupapi.app.log | ini | |
MD5:— | SHA256:— | |||
| 2332 | WinMail.exe | C:\Users\Administrator\Contacts\Administrator (1).contact | xml | |
MD5:— | SHA256:— | |||
| 2332 | WinMail.exe | C:\Windows\system32\config\systemprofile\AppData\Local\Microsoft\Windows Mail\edbtmp.log | binary | |
MD5:— | SHA256:— | |||
| 2332 | WinMail.exe | C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows Mail\edb.log | binary | |
MD5:— | SHA256:— | |||
| 1732 | ie4uinit.exe | C:\Windows\system32\config\systemprofile\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Explorer.lnk | lnk | |
MD5:— | SHA256:— | |||
| 1732 | ie4uinit.exe | C:\Windows\system32\config\systemprofile\AppData\Local\Microsoft\Internet Explorer\brndlog.txt | text | |
MD5:— | SHA256:— | |||
| 1732 | ie4uinit.exe | C:\Windows\system32\config\systemprofile\AppData\Local\Microsoft\Internet Explorer\Tiles\pin9728060290\msapplication.xml | xml | |
MD5:— | SHA256:— | |||
| 1732 | ie4uinit.exe | C:\Windows\system32\config\systemprofile\AppData\Local\Temp\RGI4E2B.tmp | ini | |
MD5:31CB7778F65DF8D02353E6C7B2B2CFFC | SHA256:647A8C7F316EF325F73C2037E8883854F9287584904C977C81D1662DB6471A58 | |||
| 1732 | ie4uinit.exe | C:\Windows\System32\config\systemprofile\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\desktop.ini | text | |
MD5:E4E50DFA455B2CBE356DFFDF7AA1FCAF | SHA256:9284BD835C20F5DA3F76BC1D8C591F970A74E62A7925422858E5B9FBEC08B927 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
56
DNS requests
156
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3900 | firefox.exe | POST | — | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | — | — | whitelisted |
3900 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3900 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3900 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3900 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3900 | firefox.exe | POST | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3 | US | der | 472 b | whitelisted |
3900 | firefox.exe | POST | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3 | US | der | 471 b | whitelisted |
3900 | firefox.exe | POST | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3 | US | der | 472 b | whitelisted |
3900 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3900 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 313 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3900 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | — | US | whitelisted |
3900 | firefox.exe | 13.32.119.185:443 | www.mozilla.org | Amazon.com, Inc. | US | suspicious |
3900 | firefox.exe | 52.222.214.84:443 | firefox.settings.services.mozilla.com | Amazon.com, Inc. | US | suspicious |
3900 | firefox.exe | 54.190.96.86:443 | accounts.firefox.com | Amazon.com, Inc. | US | unknown |
3900 | firefox.exe | 35.161.134.161:443 | location.services.mozilla.com | Amazon.com, Inc. | US | unknown |
3900 | firefox.exe | 34.120.208.123:443 | incoming.telemetry.mozilla.org | — | US | malicious |
3900 | firefox.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3900 | firefox.exe | 52.24.149.180:443 | shavar.services.mozilla.com | Amazon.com, Inc. | US | unknown |
3900 | firefox.exe | 142.250.185.196:443 | www.google.com | Google Inc. | US | whitelisted |
3900 | firefox.exe | 52.222.236.89:443 | firefox-settings-attachments.cdn.mozilla.net | Amazon.com, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
www.mozilla.org |
| whitelisted |
www.mozorg.moz.works |
| suspicious |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
firefox.settings.services.mozilla.com |
| whitelisted |
accounts.firefox.com |
| whitelisted |
incoming.telemetry.mozilla.org |
| whitelisted |
prod.ingestion-edge.prod.dataops.mozgcp.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3900 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
3900 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
3900 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
3900 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |