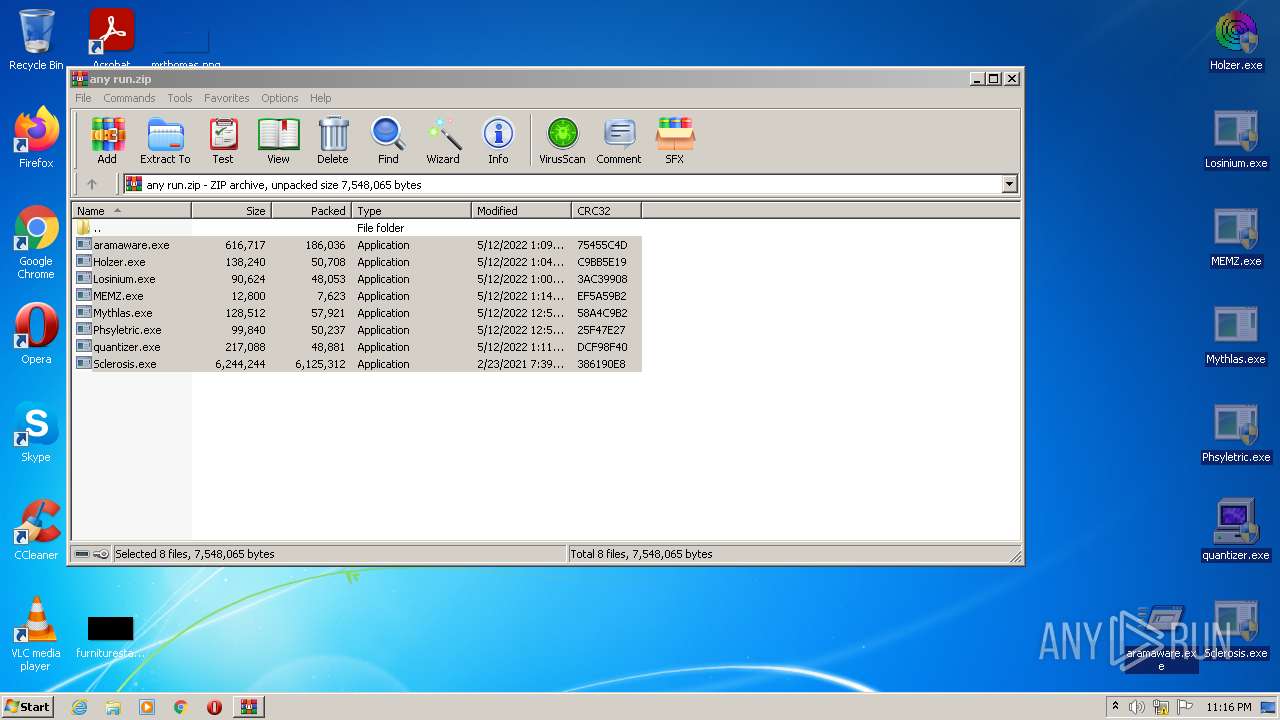
| File name: | any run.zip |
| Full analysis: | https://app.any.run/tasks/94667e6f-672f-4ee9-97d5-8e6dbef620cc |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2022, 22:16:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | D5580C9560F5FF87A09FC6100654D4E4 |
| SHA1: | 5F42337E5F30A7D73546BFBB399453D2328E5A8D |
| SHA256: | C33C4CC5639886BFF516F52872C773EC9D7D15B6CAAE3530753A0458B334C60B |
| SSDEEP: | 196608:XH/djrRJhxwSAGm7eGfp4mFWjsa0e1y8ky+q:XVvfH2lpbafT+q |
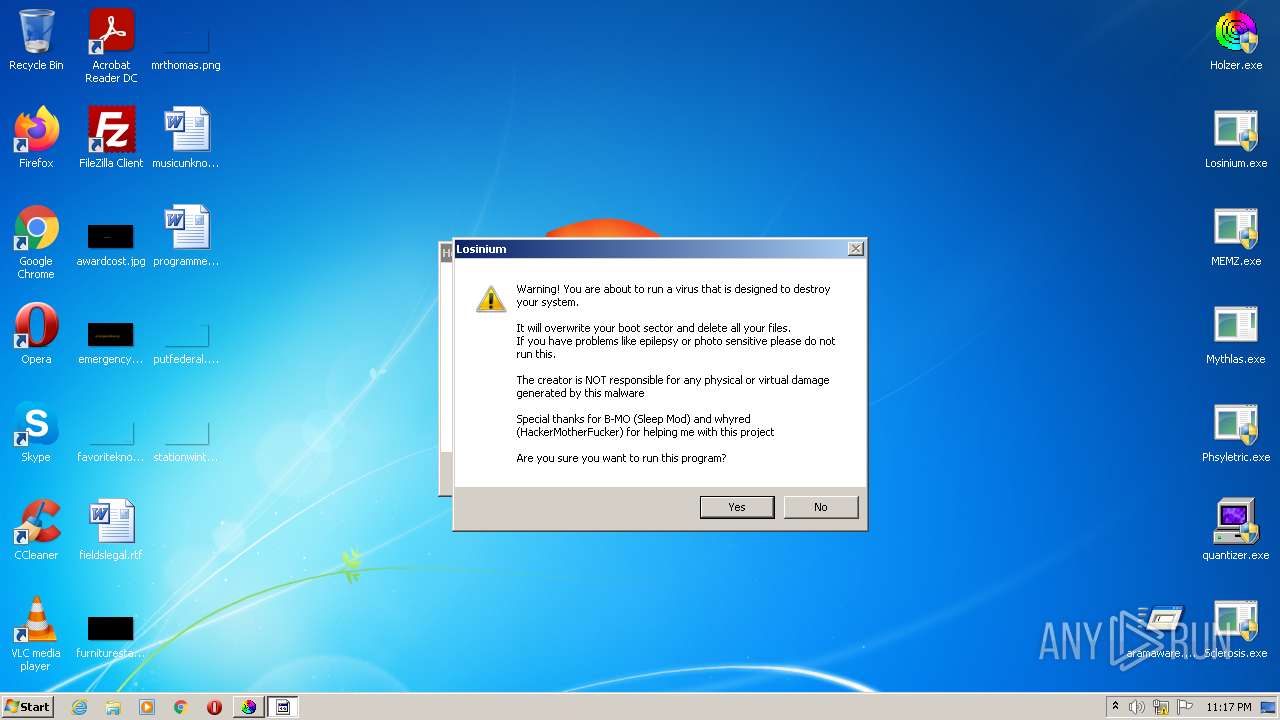
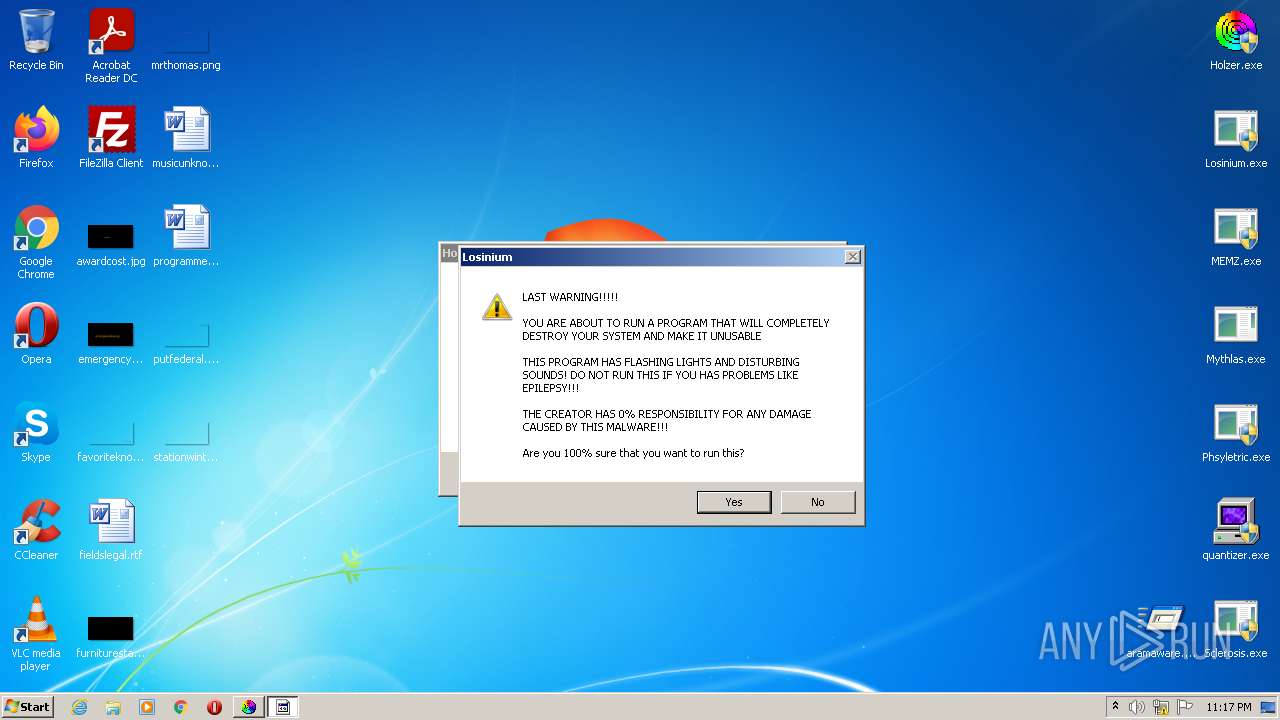
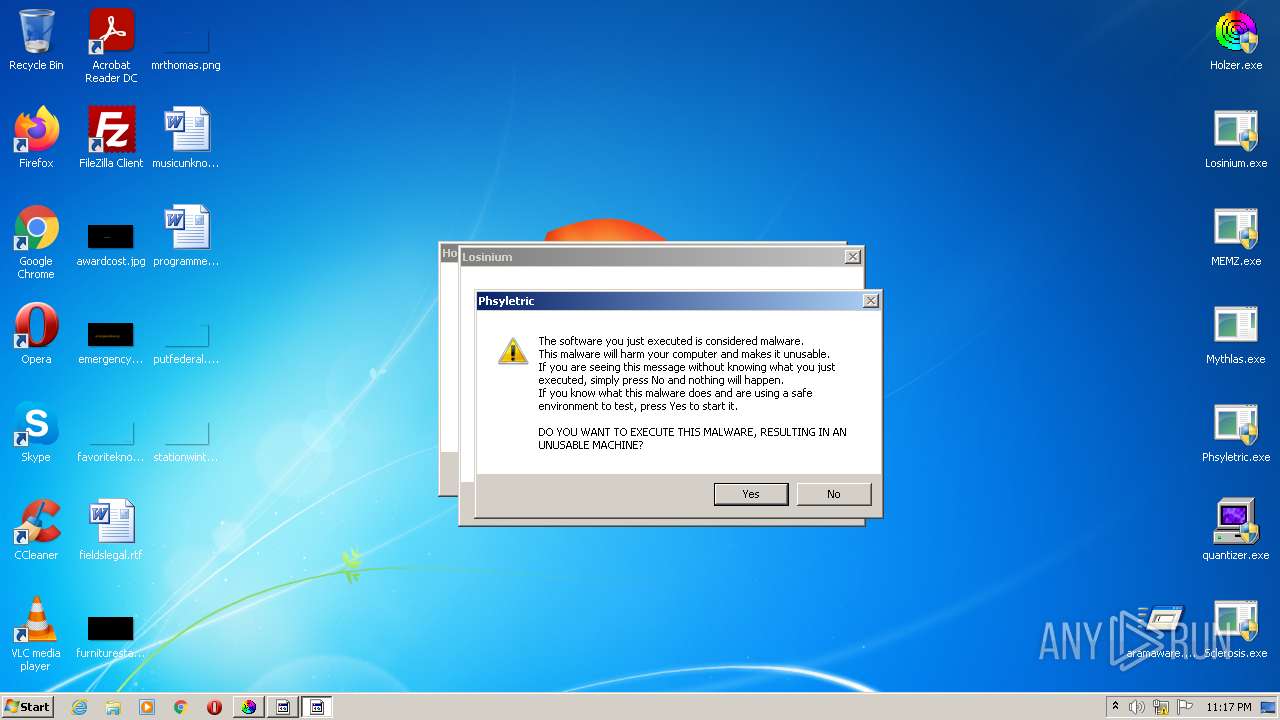
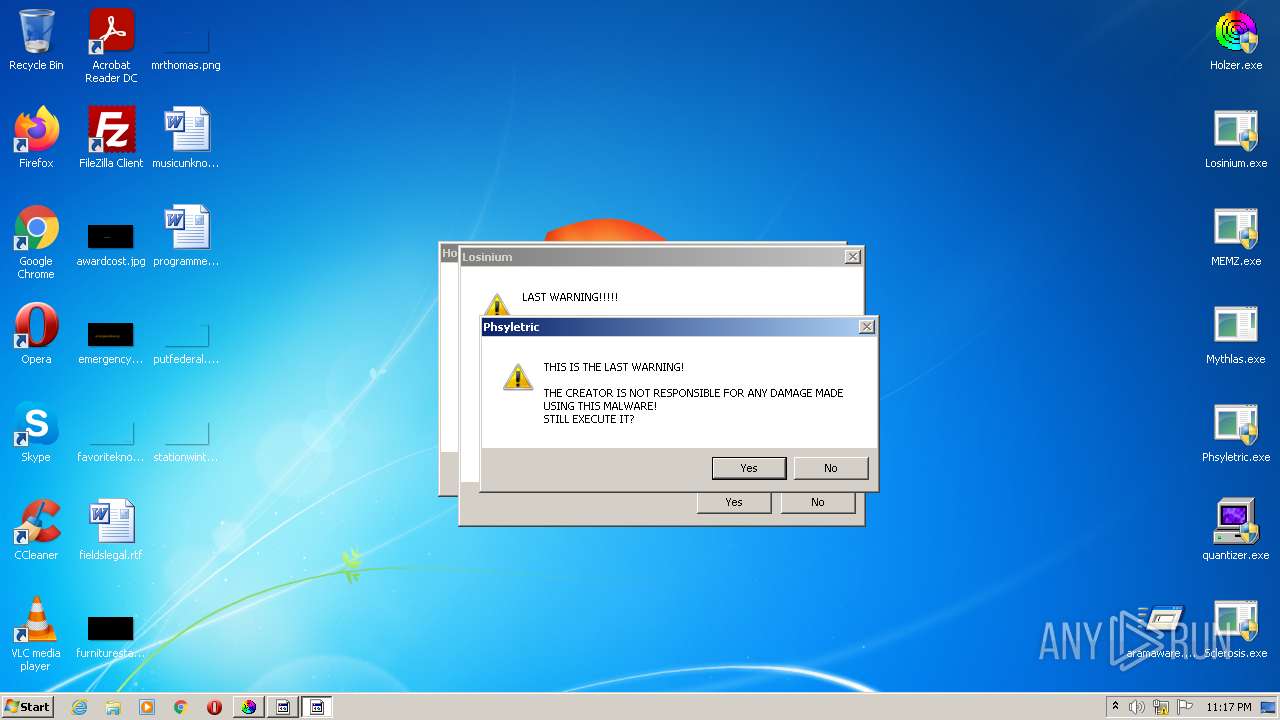
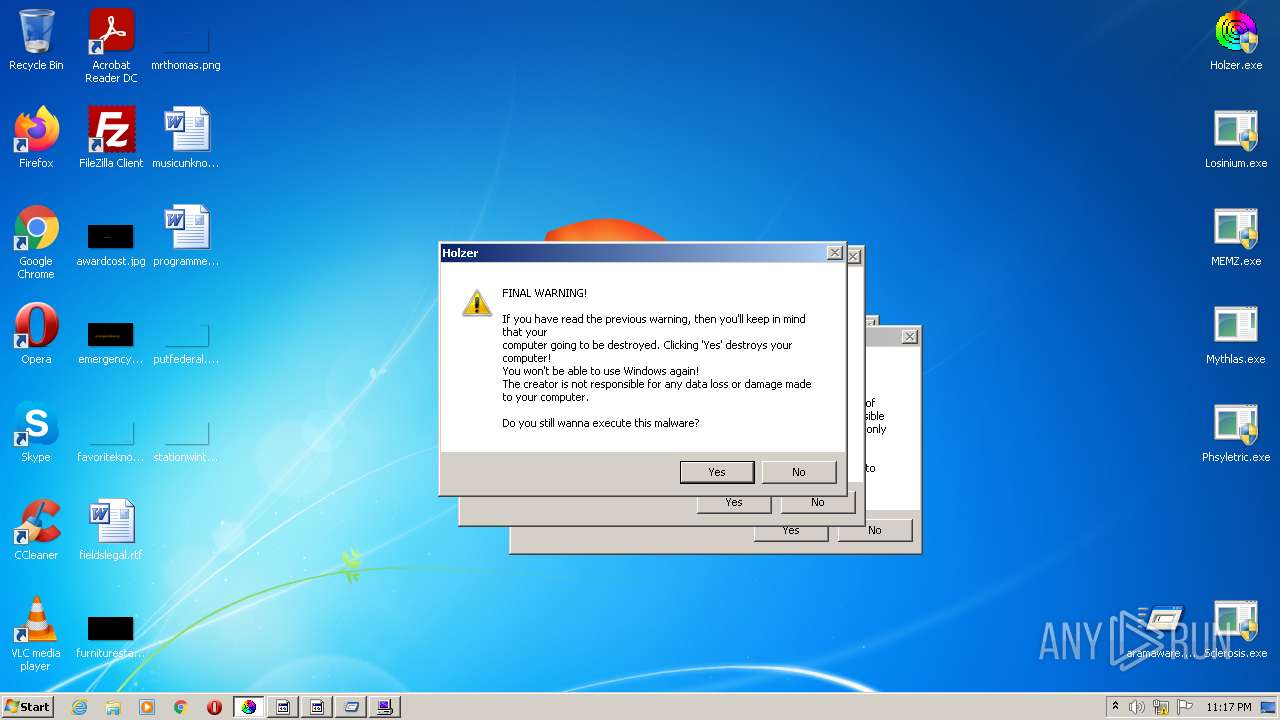
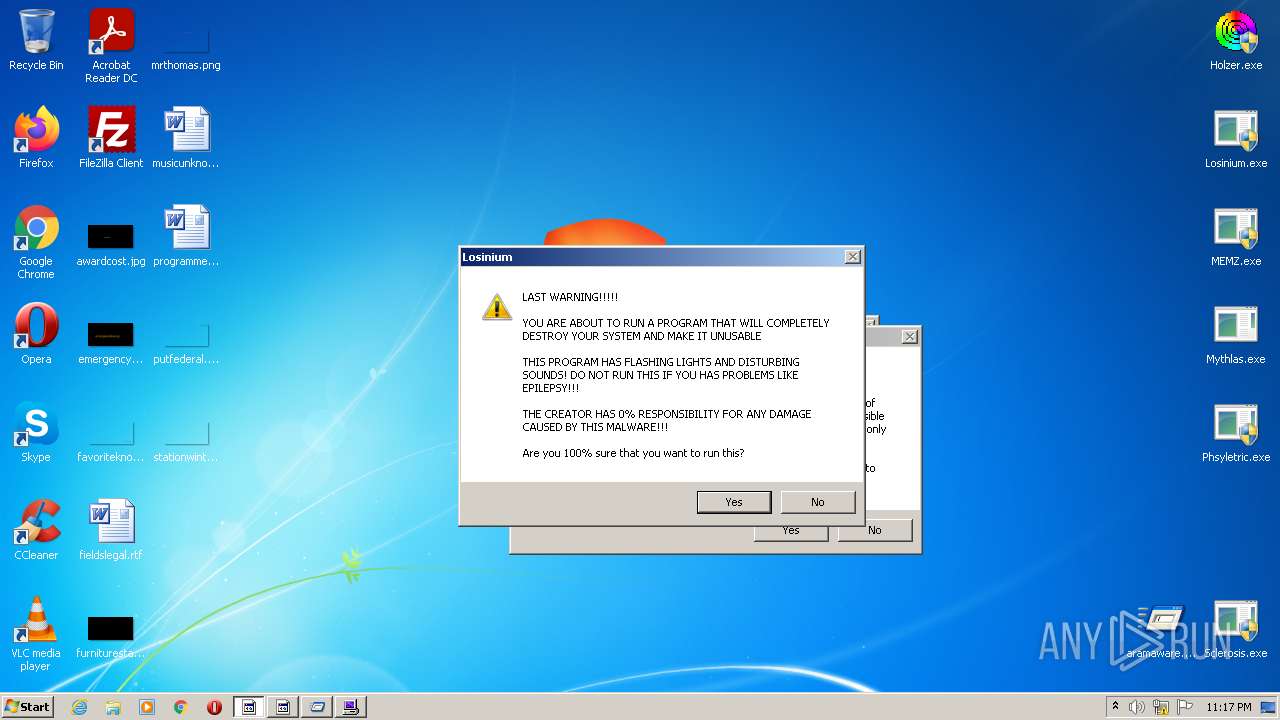
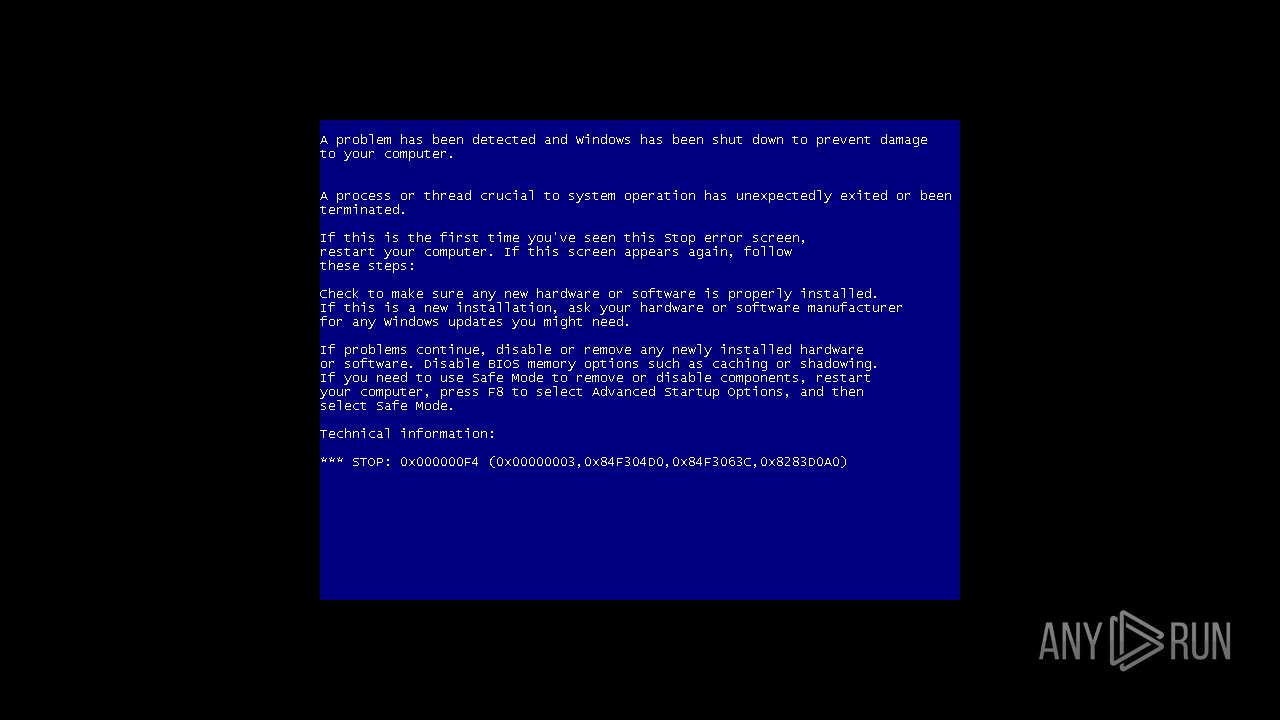
MALICIOUS
Application was dropped or rewritten from another process
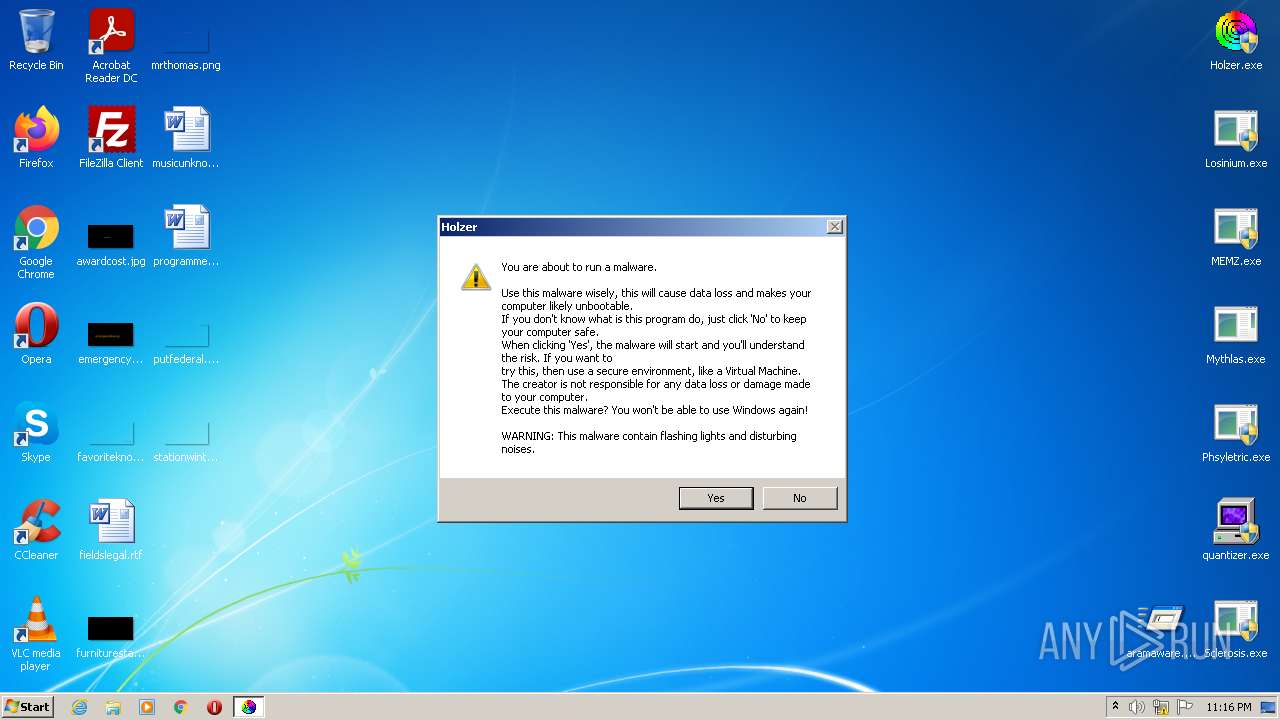
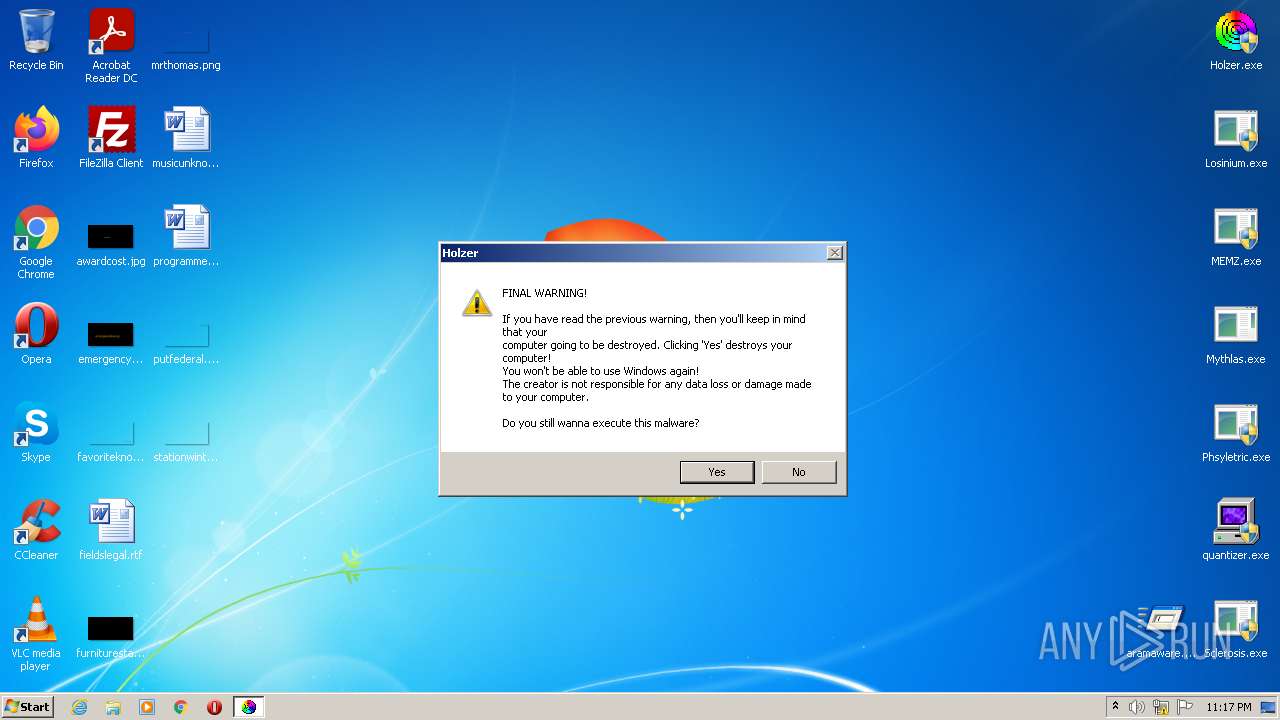
- Holzer.exe (PID: 2608)
- Holzer.exe (PID: 2820)
- Losinium.exe (PID: 3608)
- Losinium.exe (PID: 2092)
- Phsyletric.exe (PID: 2480)
- Phsyletric.exe (PID: 2940)
- 一一一一一一一一一一一一一一一一.exe (PID: 2980)
- Sclerosis.exe (PID: 2852)
- Mythlas.exe (PID: 3984)
- Sclerosis.exe (PID: 2336)
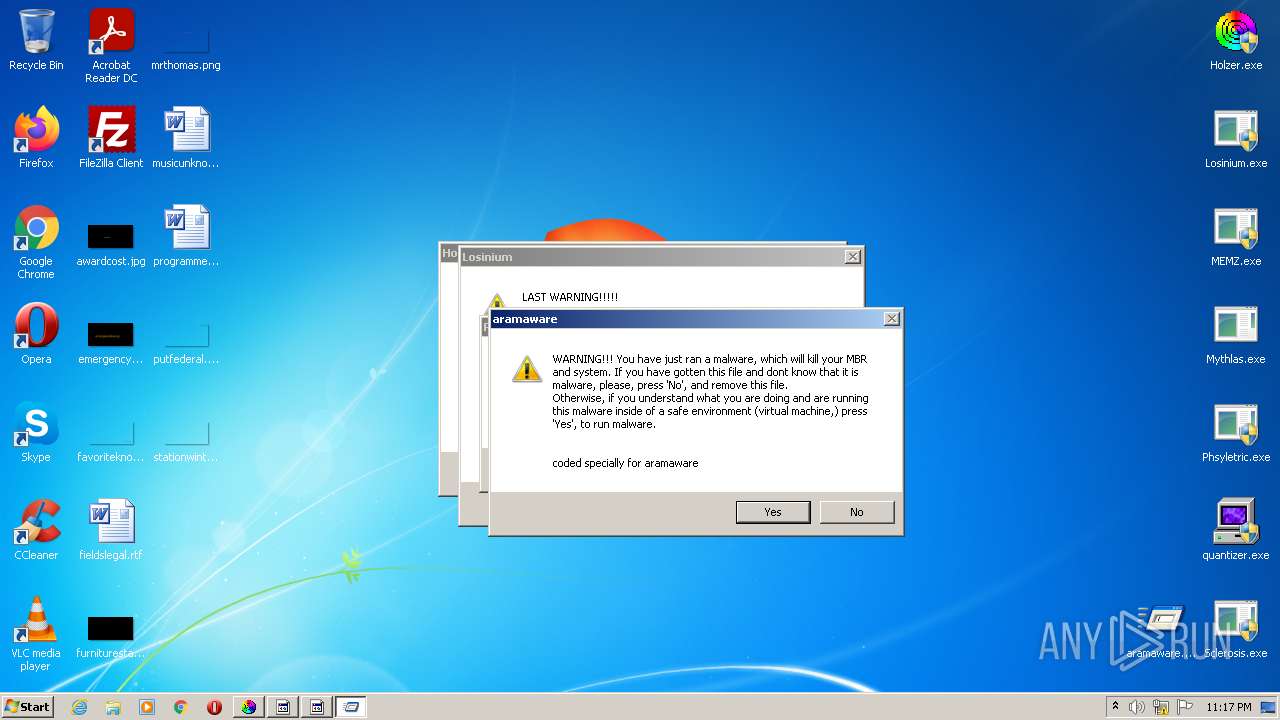
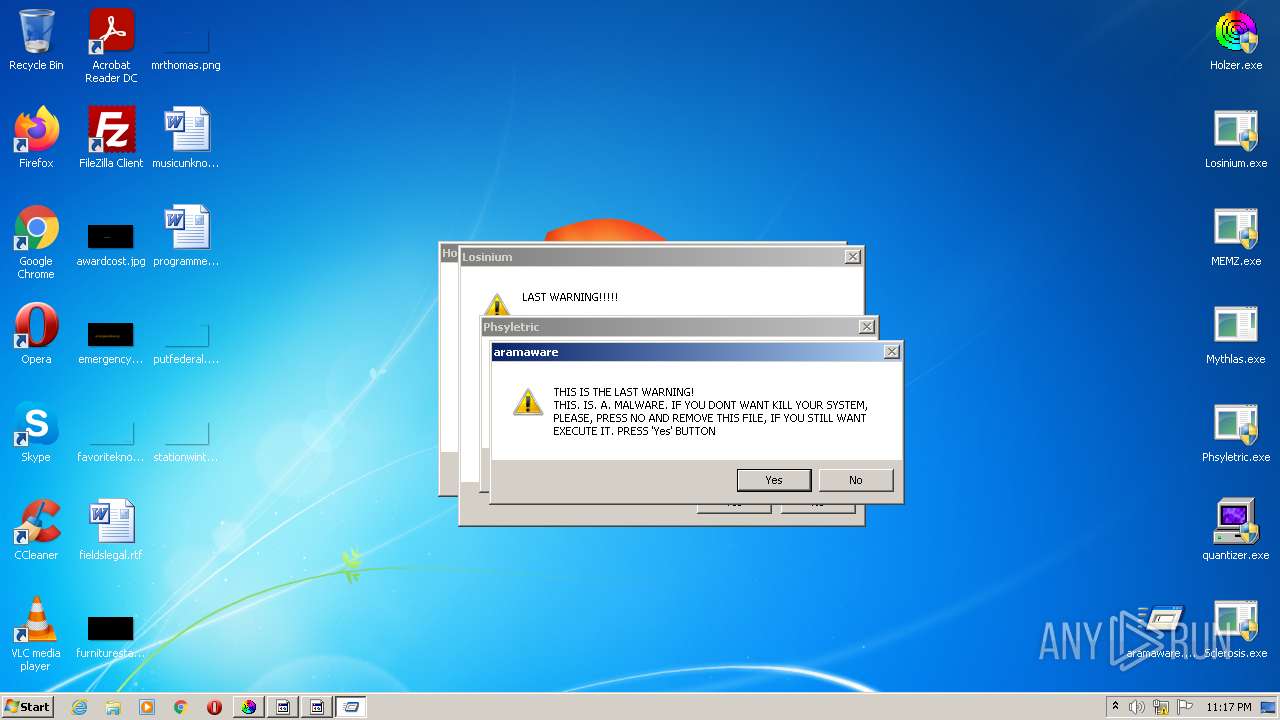
- aramaware.exe (PID: 1208)
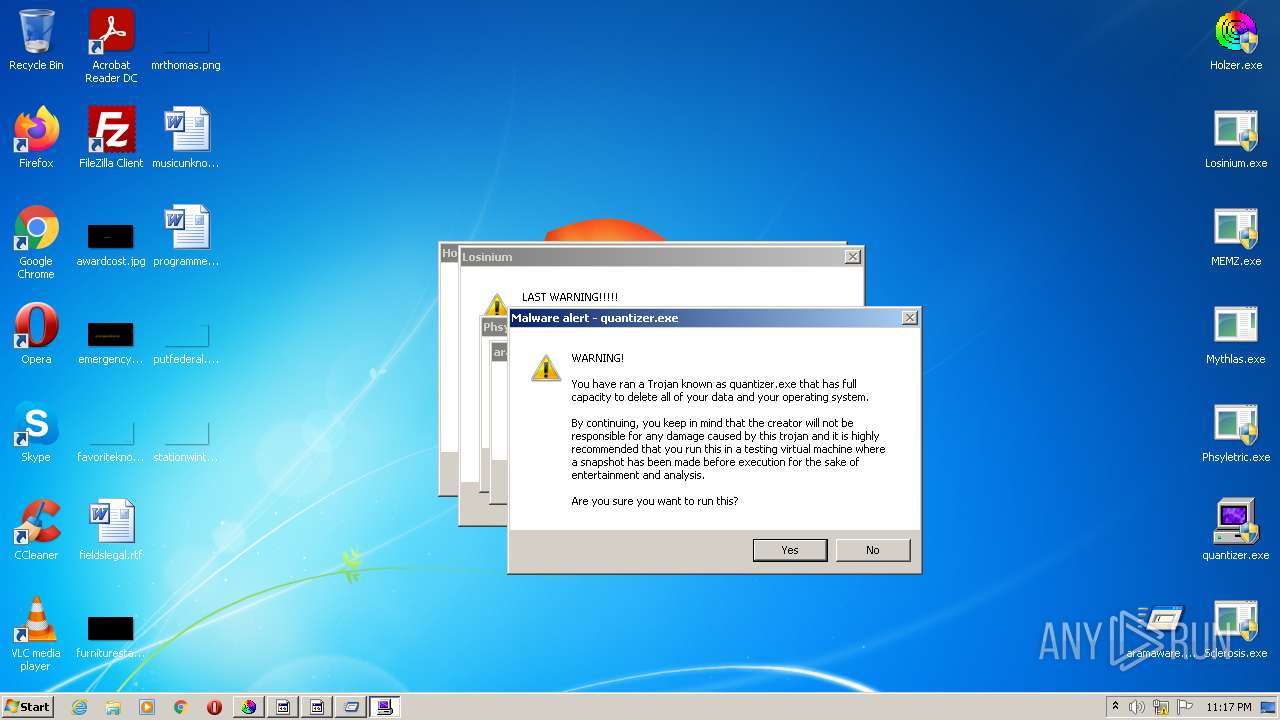
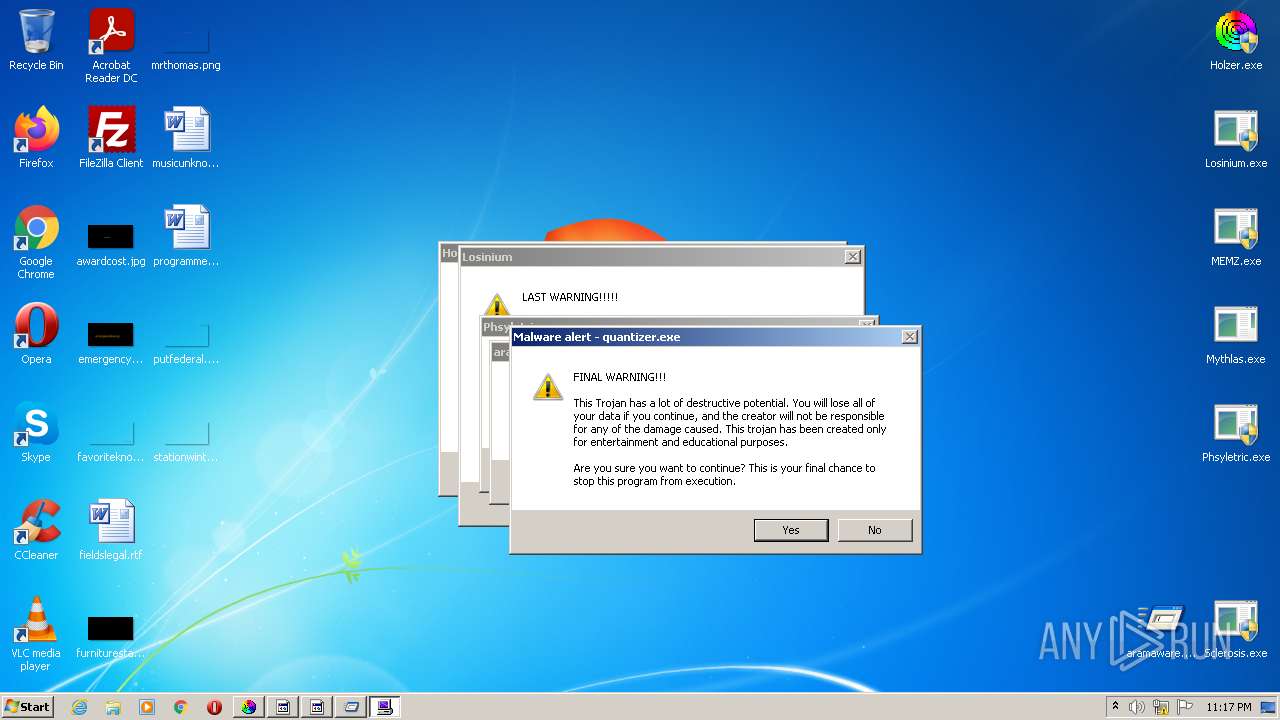
- quantizer.exe (PID: 4060)
- quantizer.exe (PID: 1932)
- glit.exe (PID: 1812)
- mbr.exe (PID: 3048)
- invpaint.exe (PID: 4088)
- first.exe (PID: 4080)
Drops executable file immediately after starts
- WinRAR.exe (PID: 2944)
- quantizer.exe (PID: 1932)
- Sclerosis.exe (PID: 2852)
Task Manager has been disabled (taskmgr)
- Holzer.exe (PID: 2820)
- 一一一一一一一一一一一一一一一一.exe (PID: 2980)
- reg.exe (PID: 1868)
Disables registry editing tools (regedit)
- Holzer.exe (PID: 2820)
- 一一一一一一一一一一一一一一一一.exe (PID: 2980)
Disables the Command Prompt (cmd)
- Holzer.exe (PID: 2820)
Loads dropped or rewritten executable
- glit.exe (PID: 1812)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 2944)
- Sclerosis.exe (PID: 2852)
- WScript.exe (PID: 3136)
- glit.exe (PID: 1812)
- 一一一一一一一一一一一一一一一一.exe (PID: 2980)
- Losinium.exe (PID: 2092)
- Holzer.exe (PID: 2820)
- Mythlas.exe (PID: 3984)
Checks supported languages
- Holzer.exe (PID: 2820)
- WinRAR.exe (PID: 2944)
- Losinium.exe (PID: 2092)
- Phsyletric.exe (PID: 2940)
- quantizer.exe (PID: 1932)
- Mythlas.exe (PID: 3984)
- aramaware.exe (PID: 1208)
- 一一一一一一一一一一一一一一一一.exe (PID: 2980)
- WScript.exe (PID: 3136)
- cmd.exe (PID: 3548)
- Sclerosis.exe (PID: 2852)
- first.exe (PID: 4080)
- mbr.exe (PID: 3048)
- glit.exe (PID: 1812)
- invpaint.exe (PID: 4088)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2944)
- quantizer.exe (PID: 1932)
- Sclerosis.exe (PID: 2852)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 2944)
- quantizer.exe (PID: 1932)
- Sclerosis.exe (PID: 2852)
Starts itself from another location
- quantizer.exe (PID: 1932)
Creates files in the Windows directory
- Sclerosis.exe (PID: 2852)
Executes scripts
- Sclerosis.exe (PID: 2852)
Starts CMD.EXE for commands execution
- WScript.exe (PID: 3136)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 3548)
Removes files from Windows directory
- Sclerosis.exe (PID: 2852)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 3548)
INFO
Manual execution by user
- Losinium.exe (PID: 3608)
- Holzer.exe (PID: 2608)
- aramaware.exe (PID: 1208)
- Holzer.exe (PID: 2820)
- Losinium.exe (PID: 2092)
- Phsyletric.exe (PID: 2480)
- Phsyletric.exe (PID: 2940)
- Sclerosis.exe (PID: 2336)
- Mythlas.exe (PID: 3984)
- quantizer.exe (PID: 4060)
- quantizer.exe (PID: 1932)
- Sclerosis.exe (PID: 2852)
Checks Windows Trust Settings
- WScript.exe (PID: 3136)
Checks supported languages
- reg.exe (PID: 1868)
- timeout.exe (PID: 2532)
- timeout.exe (PID: 3868)
- timeout.exe (PID: 2780)
- taskkill.exe (PID: 3740)
Reads the computer name
- taskkill.exe (PID: 3740)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
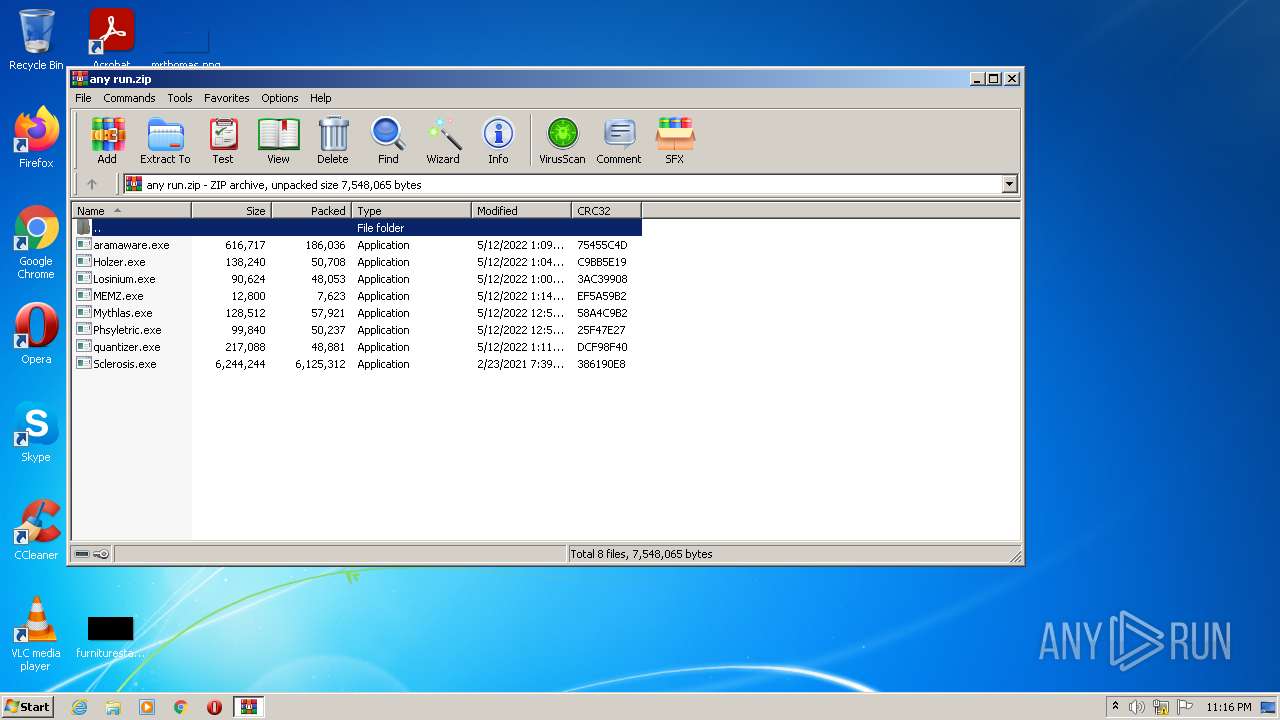
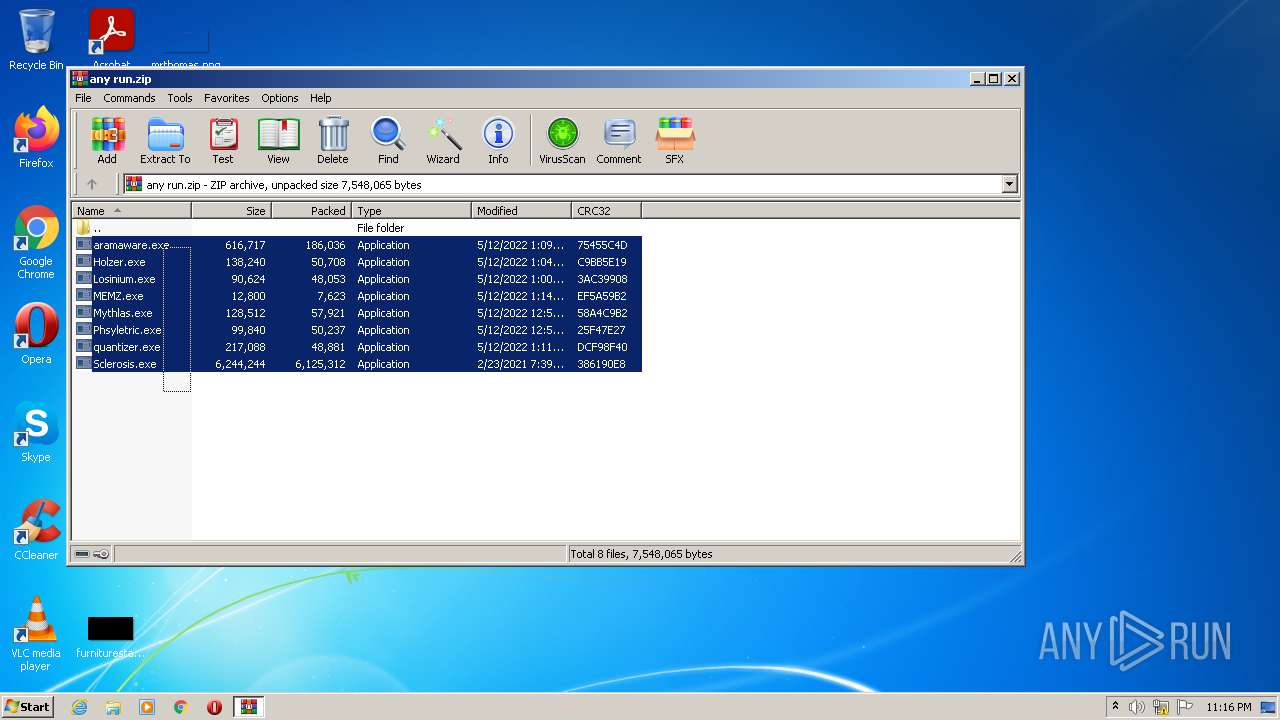
| ZipFileName: | aramaware.exe |
|---|---|
| ZipUncompressedSize: | 616717 |
| ZipCompressedSize: | 186036 |
| ZipCRC: | 0x75455c4d |
| ZipModifyDate: | 2022:05:12 13:09:21 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
76
Monitored processes
25
Malicious processes
10
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1208 | "C:\Users\admin\Desktop\aramaware.exe" | C:\Users\admin\Desktop\aramaware.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1812 | glit.exe | C:\Windows\Sclerosis\glit.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1868 | REG add HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System /v DisableTaskMgr /t REG_DWORD /d 1 /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1932 | "C:\Users\admin\Desktop\quantizer.exe" | C:\Users\admin\Desktop\quantizer.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2092 | "C:\Users\admin\Desktop\Losinium.exe" | C:\Users\admin\Desktop\Losinium.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2336 | "C:\Users\admin\Desktop\Sclerosis.exe" | C:\Users\admin\Desktop\Sclerosis.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2480 | "C:\Users\admin\Desktop\Phsyletric.exe" | C:\Users\admin\Desktop\Phsyletric.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2532 | timeout 6 | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2608 | "C:\Users\admin\Desktop\Holzer.exe" | C:\Users\admin\Desktop\Holzer.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2780 | timeout 9 | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 821
Read events
2 766
Write events
55
Delete events
0
Modification events
| (PID) Process: | (2944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2944) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\any run.zip | |||
| (PID) Process: | (2944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
22
Suspicious files
1
Text files
3
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2852 | Sclerosis.exe | C:\Windows\Sclerosis\glit.mp3 | mp3 | |
MD5:— | SHA256:— | |||
| 1932 | quantizer.exe | C:\Users\admin\AppData\Local\Temp\一一一一一一一一一一一一一一一一.txt | binary | |
MD5:FBD764BB552CC046ED7CAAD72D824568 | SHA256:93B11153F421C7170473E8AE1F579B6D92196CB3C979C1D39B7CCF6E85B096A6 | |||
| 1932 | quantizer.exe | C:\Users\admin\AppData\Local\Temp\一一一一一一一一一一一一一一一一.exe | executable | |
MD5:1458480CF8803569195F934D47AC7481 | SHA256:68D528F9AC891E920449188198A233B71B2860838AF4FB970B9966F941CE82CA | |||
| 2944 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2944.17066\Losinium.exe | executable | |
MD5:3FAD30EF9BBB47488E86DEFA0F81ACAB | SHA256:69D2AD4DDD61C4B2E6FF350FD87B61DB5DE36218626812E69C4289DE5782CD0C | |||
| 2944 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2944.17066\MEMZ.exe | executable | |
MD5:A7BCF7EA8E9F3F36EBFB85B823E39D91 | SHA256:3FF64F10603F0330FA2386FF99471CA789391ACE969BD0EC1C1B8CE1B4A6DB42 | |||
| 2852 | Sclerosis.exe | C:\Windows\Sclerosis\main.bat | text | |
MD5:— | SHA256:— | |||
| 2944 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2944.17066\aramaware.exe | executable | |
MD5:3ACDCDEE17825753CACC8DFD414E57D3 | SHA256:82BB1809904786AFC0C13ABEC22A48B320581EC913BF5BBDDDD02FCE05EF77E8 | |||
| 2852 | Sclerosis.exe | C:\Windows\Sclerosis\paint2.exe | executable | |
MD5:3B60C7A7181BC6C7360FC7E19D06B050 | SHA256:DF158403CD77171271292F9119C99A6AA3721F36941BA91B8EFF7ADD82651E8A | |||
| 2944 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2944.17066\Holzer.exe | executable | |
MD5:C971C68B4E58CCC82802B21AE8488BC7 | SHA256:CEDE0B15D88C20BC750B516858F8BF31EE472F6CBD01640840890736C4333CCE | |||
| 2944 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2944.17066\Mythlas.exe | executable | |
MD5:1BCCDB1CBBDB299F4053DBAB4236DADC | SHA256:E65C793A31137AE75A6F30AE2933BD7CAE74FCD4330B6C8770C14466BC3A878F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report