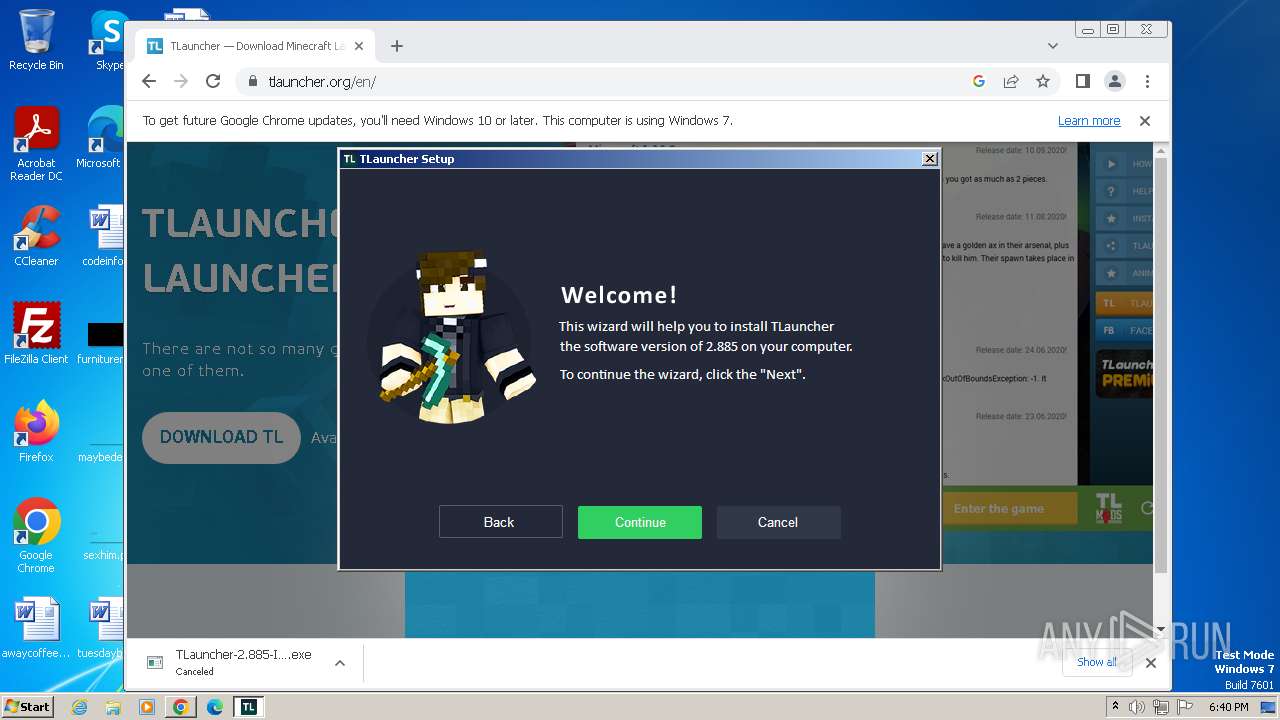
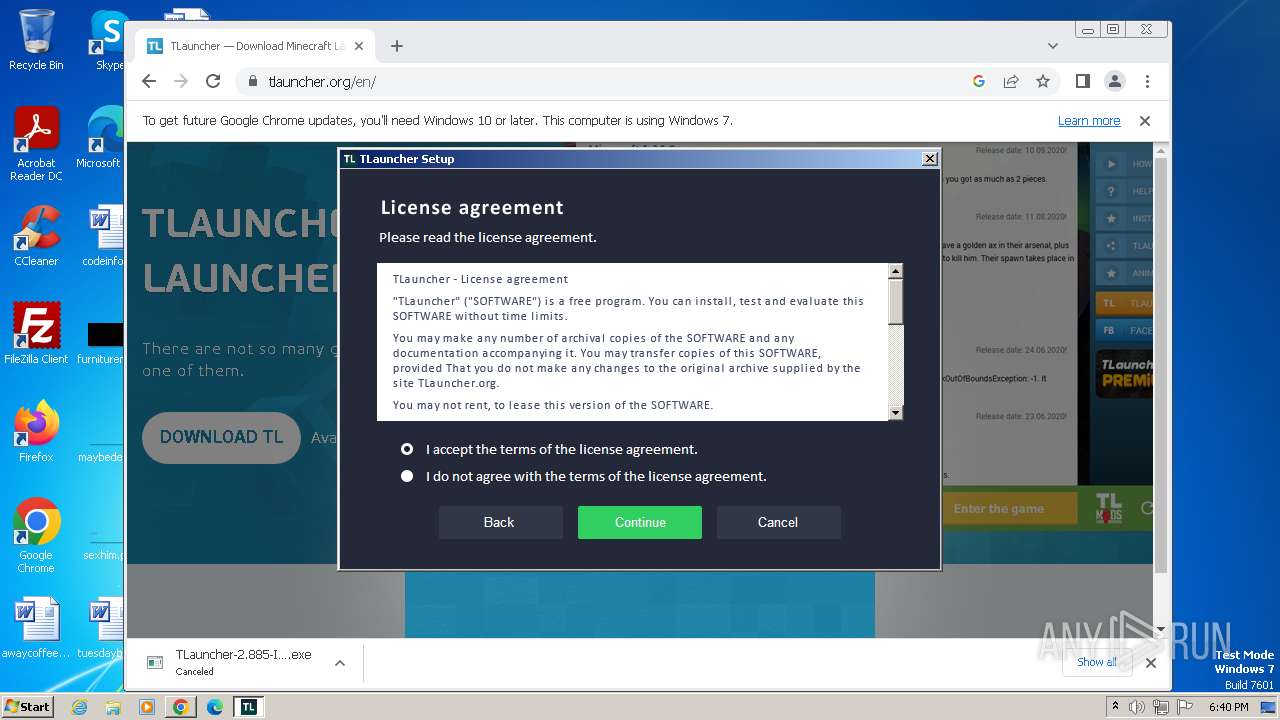
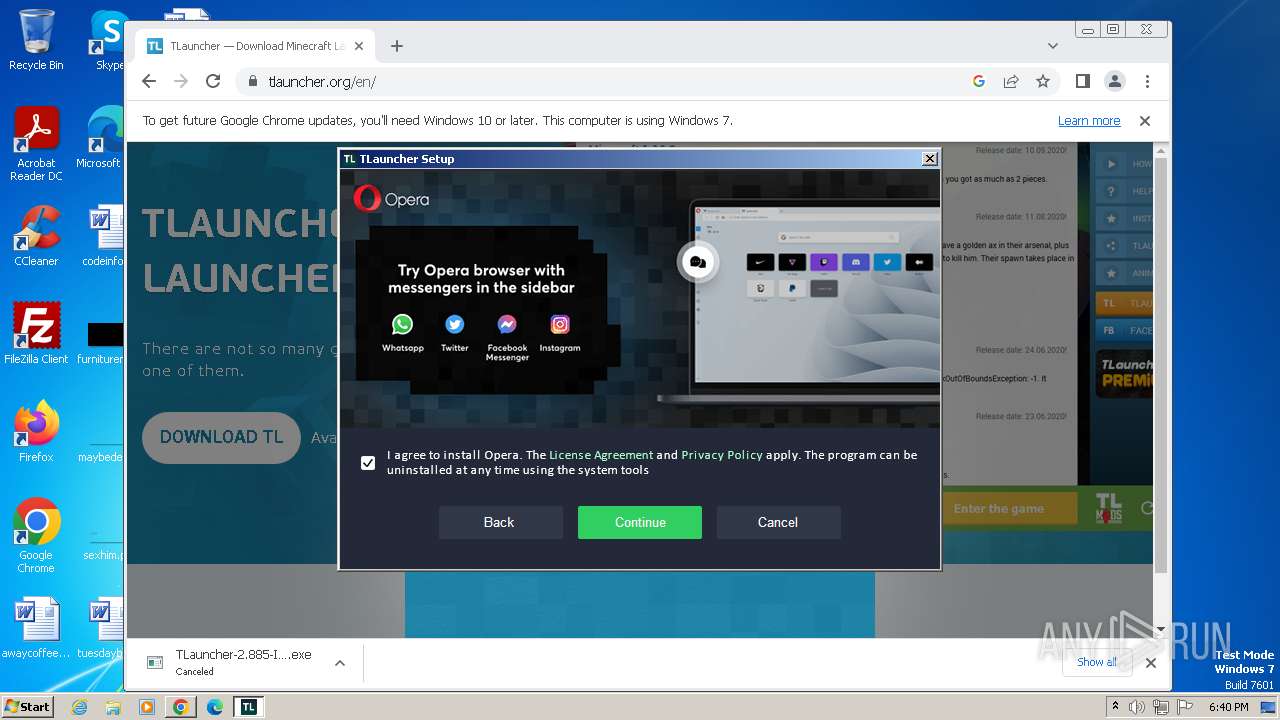
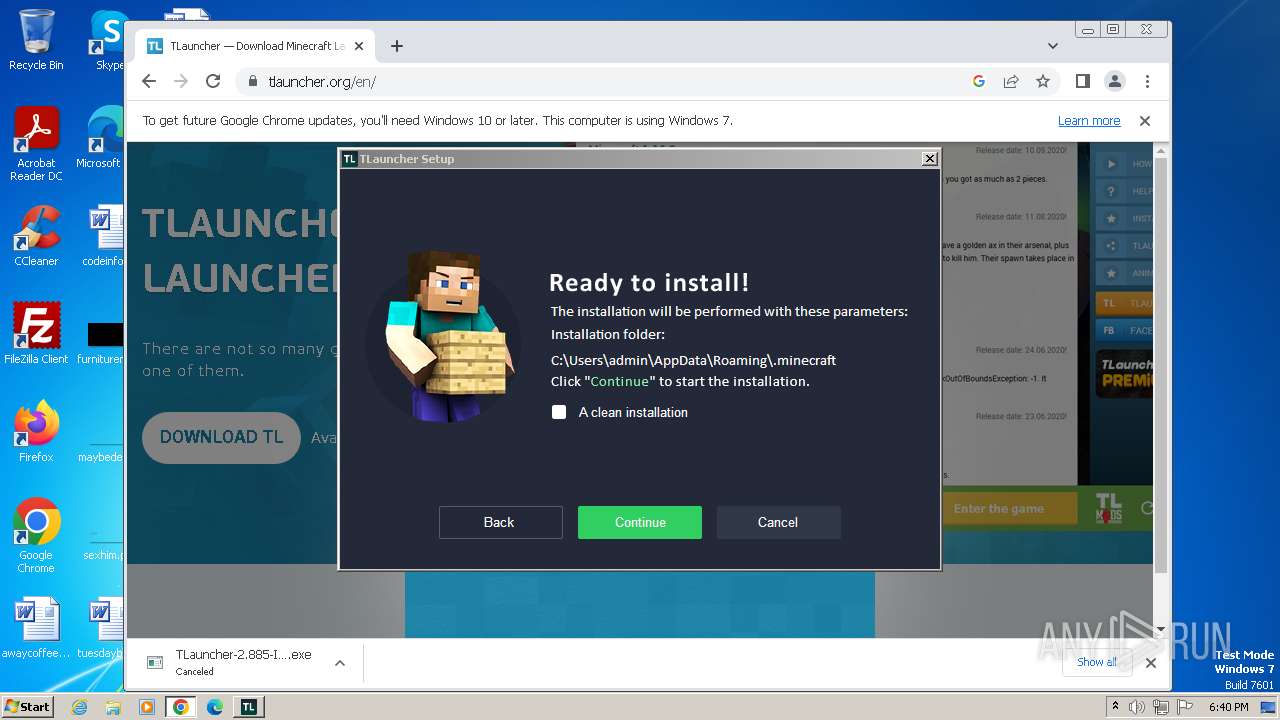
| URL: | https://tlauncher.org/en/ |
| Full analysis: | https://app.any.run/tasks/f6b45de5-7301-481c-bb14-fc76d7a17c59 |
| Verdict: | Malicious activity |
| Analysis date: | October 05, 2023, 17:39:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| SHA1: | 91D2079252AA9D349CA4BFDD7CA031A8D9CEA748 |
| SHA256: | C322DB70597221ED0C6CC05BB9208F5EF70614DBA14B01209EB4015E9EF96868 |
| SSDEEP: | 3:N8BEeLu5A+:2K5F |
MALICIOUS
Application was dropped or rewritten from another process
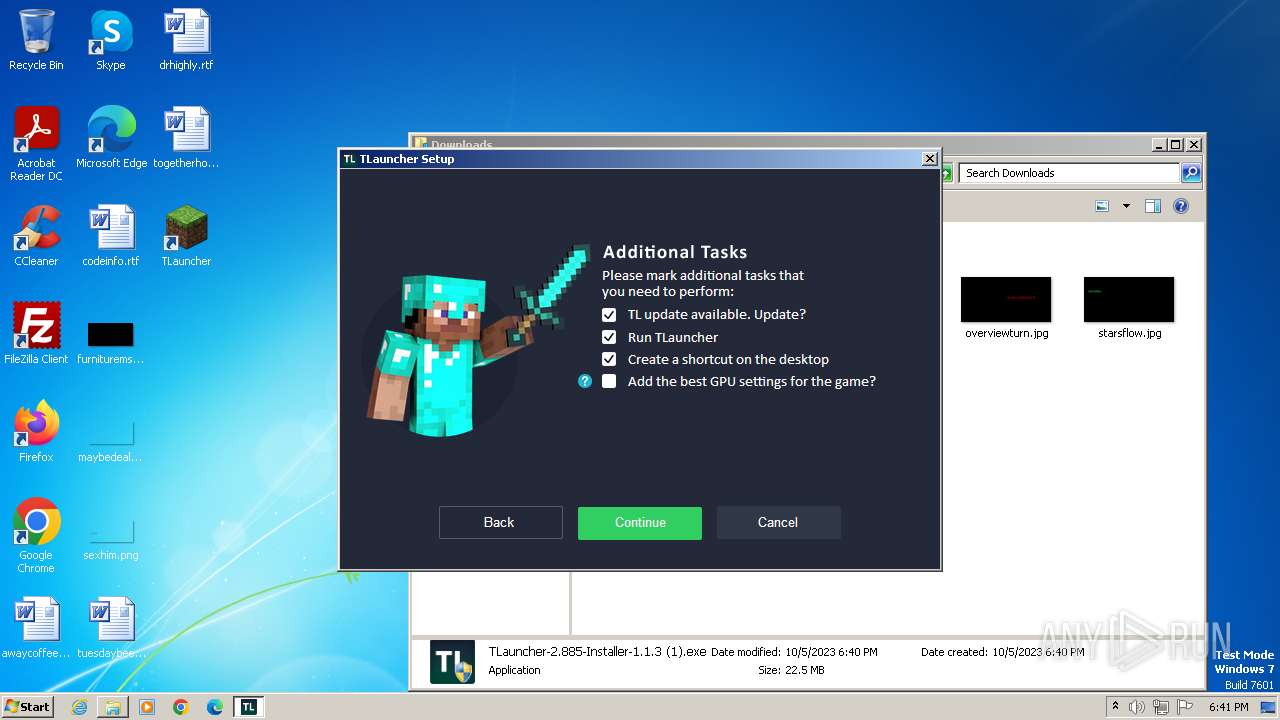
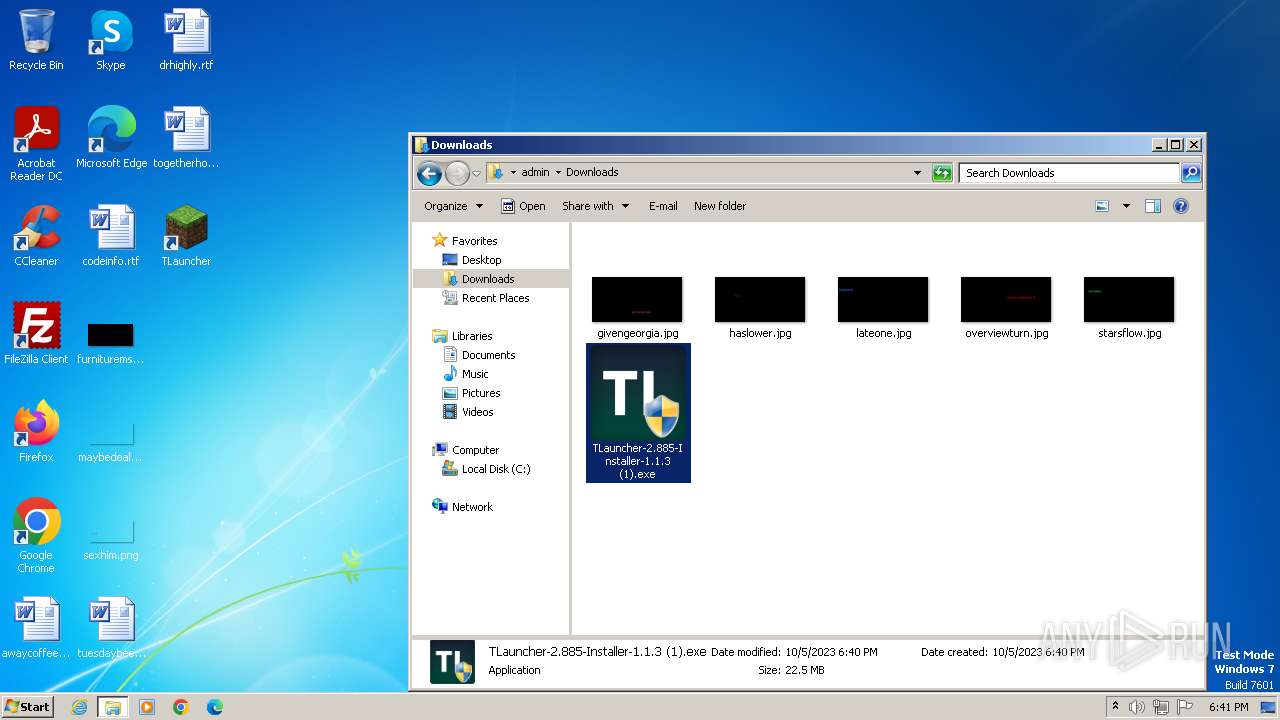
- TLauncher-2.885-Installer-1.1.3 (1).exe (PID: 3524)
- TLauncher-2.885-Installer-1.1.3 (1).exe (PID: 1764)
- irsetup.exe (PID: 2424)
- irsetup.exe (PID: 3196)
- BrowserInstaller.exe (PID: 2880)
- TLauncher.exe (PID: 2372)
- TLauncher.exe (PID: 2984)
- TLauncher-2.885-Installer-1.1.3 (1).exe (PID: 1840)
- TLauncher-2.885-Installer-1.1.3 (1).exe (PID: 1884)
- irsetup.exe (PID: 3372)
- BrowserInstaller.exe (PID: 3364)
- irsetup.exe (PID: 3440)
- TLauncher.exe (PID: 948)
- TLauncher.exe (PID: 3716)
Drops the executable file immediately after the start
- TLauncher-2.885-Installer-1.1.3 (1).exe (PID: 1764)
- irsetup.exe (PID: 2424)
- BrowserInstaller.exe (PID: 2880)
- irsetup.exe (PID: 3372)
- TLauncher-2.885-Installer-1.1.3 (1).exe (PID: 1884)
- BrowserInstaller.exe (PID: 3364)
Actions looks like stealing of personal data
- irsetup.exe (PID: 2424)
- irsetup.exe (PID: 3372)
Loads dropped or rewritten executable
- irsetup.exe (PID: 2424)
- irsetup.exe (PID: 3196)
- irsetup.exe (PID: 3372)
- irsetup.exe (PID: 3440)
SUSPICIOUS
Reads the Windows owner or organization settings
- irsetup.exe (PID: 2424)
- irsetup.exe (PID: 3196)
- irsetup.exe (PID: 3372)
- irsetup.exe (PID: 3440)
Checks for Java to be installed
- irsetup.exe (PID: 2424)
- TLauncher.exe (PID: 2372)
- TLauncher.exe (PID: 2984)
- irsetup.exe (PID: 3372)
- TLauncher.exe (PID: 948)
- TLauncher.exe (PID: 3716)
Reads the Internet Settings
- irsetup.exe (PID: 2424)
- TLauncher-2.885-Installer-1.1.3 (1).exe (PID: 1764)
- BrowserInstaller.exe (PID: 2880)
- irsetup.exe (PID: 3196)
- irsetup.exe (PID: 3372)
- TLauncher-2.885-Installer-1.1.3 (1).exe (PID: 1884)
- BrowserInstaller.exe (PID: 3364)
- irsetup.exe (PID: 3440)
- WMIC.exe (PID: 2844)
- WMIC.exe (PID: 3988)
Reads security settings of Internet Explorer
- irsetup.exe (PID: 2424)
- irsetup.exe (PID: 3196)
- irsetup.exe (PID: 3372)
- irsetup.exe (PID: 3440)
Reads settings of System Certificates
- irsetup.exe (PID: 2424)
- irsetup.exe (PID: 3196)
- irsetup.exe (PID: 3372)
- irsetup.exe (PID: 3440)
Checks Windows Trust Settings
- irsetup.exe (PID: 2424)
- irsetup.exe (PID: 3196)
- irsetup.exe (PID: 3372)
- irsetup.exe (PID: 3440)
Reads Microsoft Outlook installation path
- irsetup.exe (PID: 2424)
- irsetup.exe (PID: 3372)
Reads Internet Explorer settings
- irsetup.exe (PID: 2424)
- irsetup.exe (PID: 3372)
Adds/modifies Windows certificates
- TLauncher-2.885-Installer-1.1.3 (1).exe (PID: 1764)
Creates a software uninstall entry
- irsetup.exe (PID: 3372)
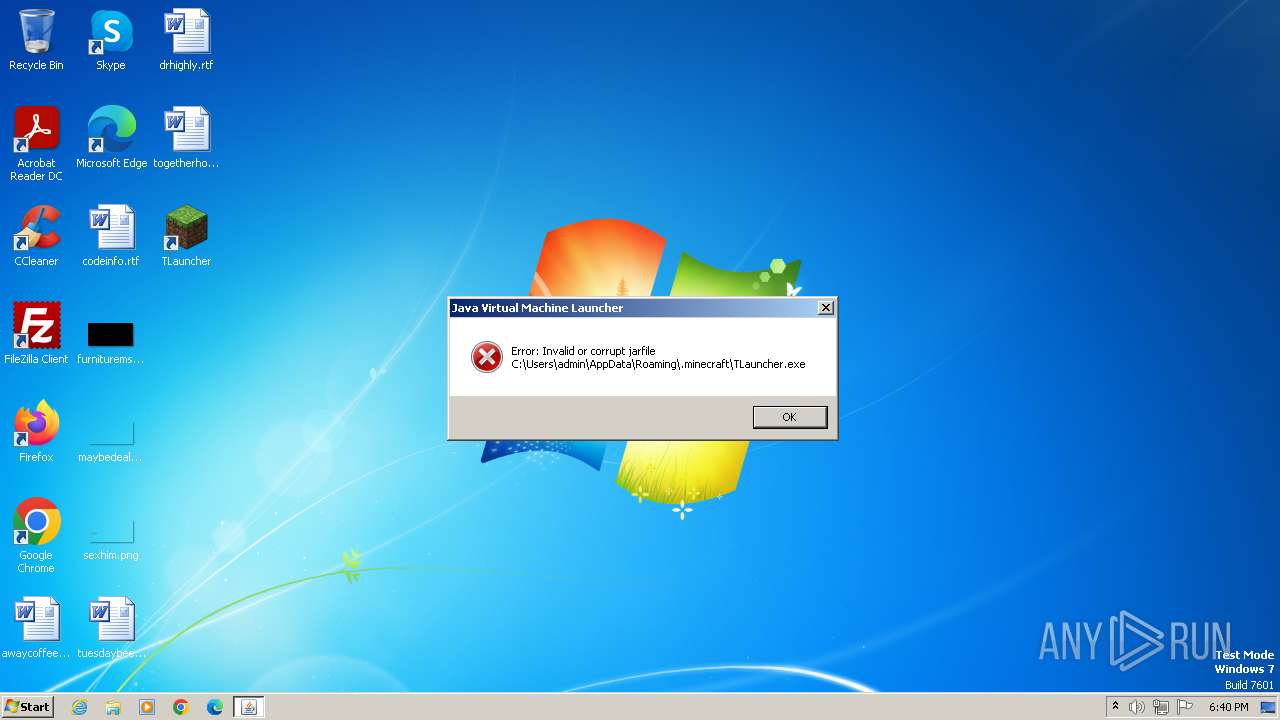
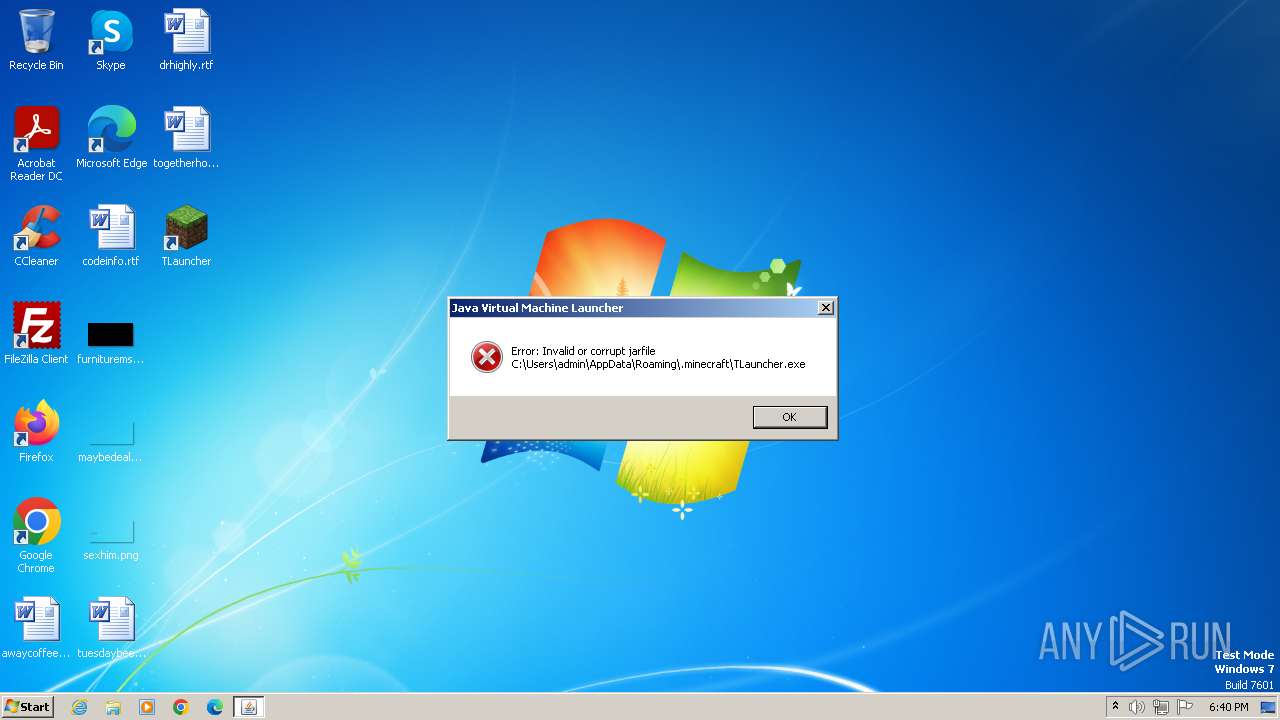
Starts application with an unusual extension
- cmd.exe (PID: 1052)
- cmd.exe (PID: 2852)
Starts CMD.EXE for commands execution
- javaw.exe (PID: 3084)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 1052)
- cmd.exe (PID: 2852)
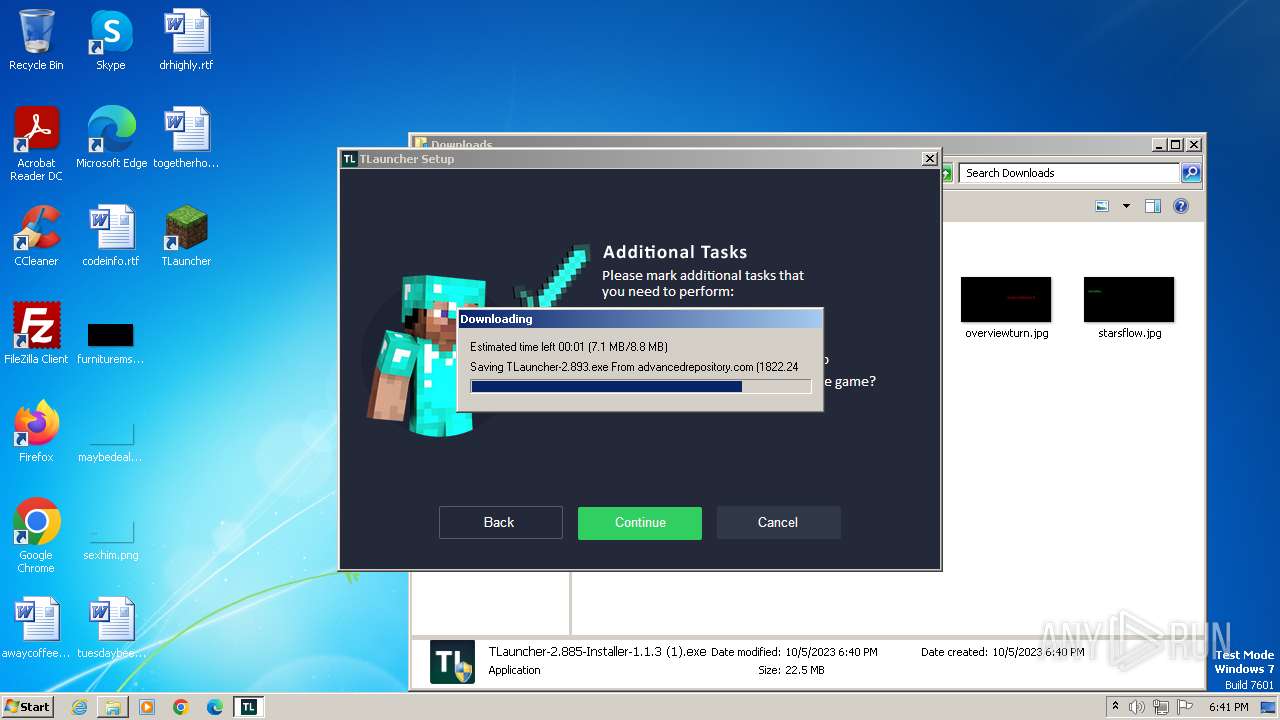
Process requests binary or script from the Internet
- javaw.exe (PID: 3084)
INFO
Drops the executable file immediately after the start
- chrome.exe (PID: 2140)
- chrome.exe (PID: 4052)
Application launched itself
- iexplore.exe (PID: 612)
- chrome.exe (PID: 2140)
Manual execution by a user
- chrome.exe (PID: 2140)
- TLauncher.exe (PID: 2984)
- TLauncher-2.885-Installer-1.1.3 (1).exe (PID: 1840)
- explorer.exe (PID: 3776)
- TLauncher-2.885-Installer-1.1.3 (1).exe (PID: 1884)
- TLauncher.exe (PID: 3716)
The process uses the downloaded file
- chrome.exe (PID: 1992)
- chrome.exe (PID: 2356)
- chrome.exe (PID: 3232)
- chrome.exe (PID: 2140)
- chrome.exe (PID: 2572)
Checks supported languages
- TLauncher-2.885-Installer-1.1.3 (1).exe (PID: 1764)
- irsetup.exe (PID: 2424)
- BrowserInstaller.exe (PID: 2880)
- irsetup.exe (PID: 3196)
- TLauncher.exe (PID: 2372)
- javaw.exe (PID: 3124)
- TLauncher.exe (PID: 2984)
- TLauncher-2.885-Installer-1.1.3 (1).exe (PID: 1884)
- javaw.exe (PID: 2500)
- irsetup.exe (PID: 3372)
- BrowserInstaller.exe (PID: 3364)
- irsetup.exe (PID: 3440)
- TLauncher.exe (PID: 948)
- javaw.exe (PID: 3084)
- chcp.com (PID: 604)
- TLauncher.exe (PID: 3716)
- javaw.exe (PID: 2352)
- chcp.com (PID: 3500)
Create files in a temporary directory
- TLauncher-2.885-Installer-1.1.3 (1).exe (PID: 1764)
- irsetup.exe (PID: 2424)
- irsetup.exe (PID: 3196)
- BrowserInstaller.exe (PID: 2880)
- irsetup.exe (PID: 3372)
- TLauncher-2.885-Installer-1.1.3 (1).exe (PID: 1884)
- BrowserInstaller.exe (PID: 3364)
- irsetup.exe (PID: 3440)
- javaw.exe (PID: 3084)
- javaw.exe (PID: 2352)
Reads the computer name
- TLauncher-2.885-Installer-1.1.3 (1).exe (PID: 1764)
- irsetup.exe (PID: 2424)
- BrowserInstaller.exe (PID: 2880)
- irsetup.exe (PID: 3196)
- irsetup.exe (PID: 3372)
- TLauncher-2.885-Installer-1.1.3 (1).exe (PID: 1884)
- BrowserInstaller.exe (PID: 3364)
- irsetup.exe (PID: 3440)
- javaw.exe (PID: 3084)
- javaw.exe (PID: 2352)
Reads the machine GUID from the registry
- irsetup.exe (PID: 2424)
- irsetup.exe (PID: 3196)
- irsetup.exe (PID: 3372)
- irsetup.exe (PID: 3440)
- javaw.exe (PID: 3084)
Checks proxy server information
- irsetup.exe (PID: 2424)
- irsetup.exe (PID: 3196)
- irsetup.exe (PID: 3372)
- irsetup.exe (PID: 3440)
Creates files or folders in the user directory
- irsetup.exe (PID: 2424)
- irsetup.exe (PID: 3372)
- javaw.exe (PID: 3084)
- javaw.exe (PID: 2352)
Creates files in the program directory
- irsetup.exe (PID: 2424)
- irsetup.exe (PID: 3372)
- javaw.exe (PID: 3084)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
111
Monitored processes
58
Malicious processes
15
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 560 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=14 --mojo-platform-channel-handle=2248 --field-trial-handle=1208,i,5614714107599738942,12366020625246581790,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 604 | chcp 437 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 612 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://tlauncher.org/en/" | C:\Program Files\Internet Explorer\iexplore.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
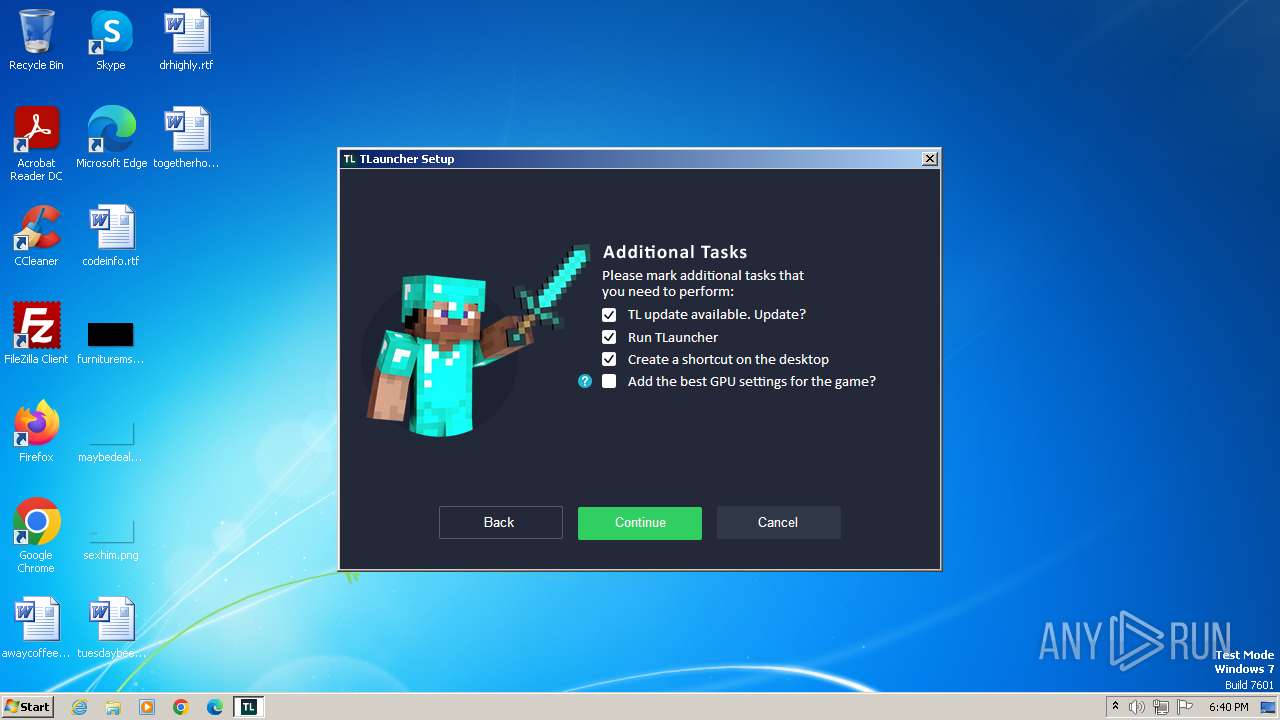
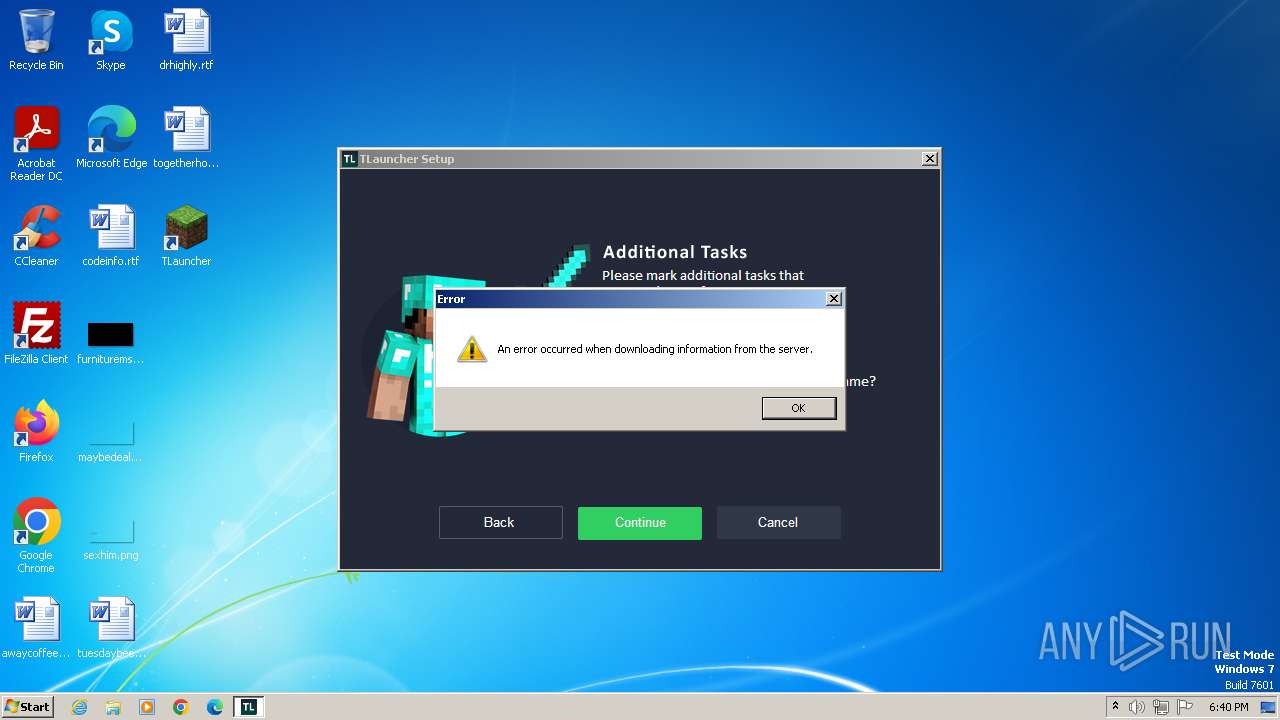
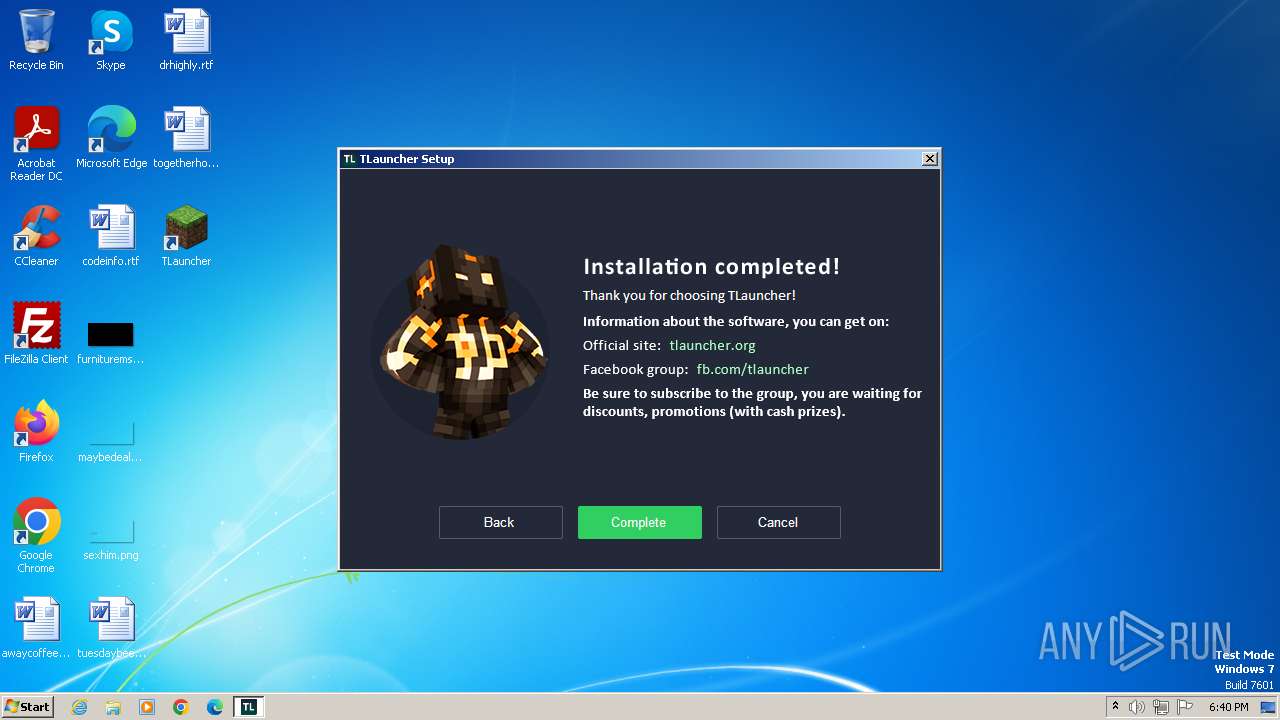
| 948 | "C:\Users\admin\AppData\Roaming\.minecraft\TLauncher.exe" | C:\Users\admin\AppData\Roaming\.minecraft\TLauncher.exe | — | irsetup.exe | |||||||||||
User: admin Company: TLauncher Inc. Integrity Level: HIGH Description: TLauncher Exit code: 0 Version: 2.893 Modules
| |||||||||||||||
| 1052 | cmd.exe /C chcp 437 & wmic os get osarchitecture | C:\Windows\System32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1432 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3560 --field-trial-handle=1208,i,5614714107599738942,12366020625246581790,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1560 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3744 --field-trial-handle=1208,i,5614714107599738942,12366020625246581790,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1620 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=4180 --field-trial-handle=1208,i,5614714107599738942,12366020625246581790,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1736 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --mojo-platform-channel-handle=4640 --field-trial-handle=1208,i,5614714107599738942,12366020625246581790,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
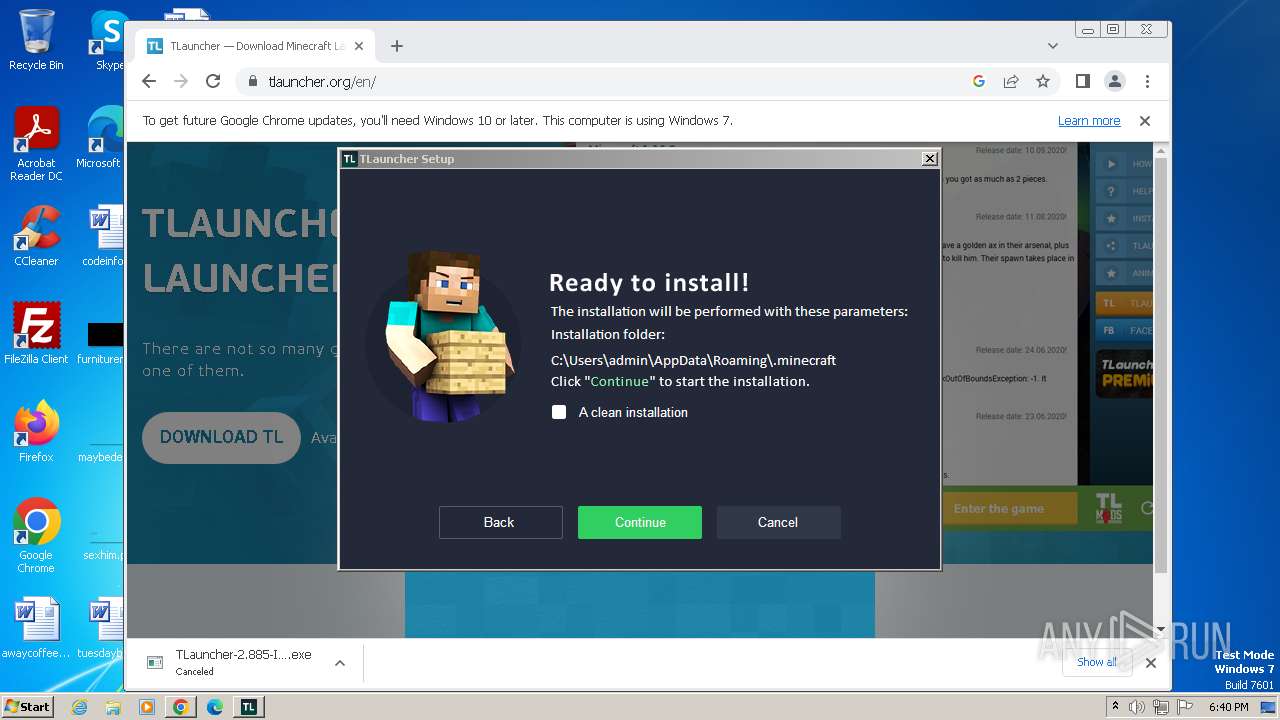
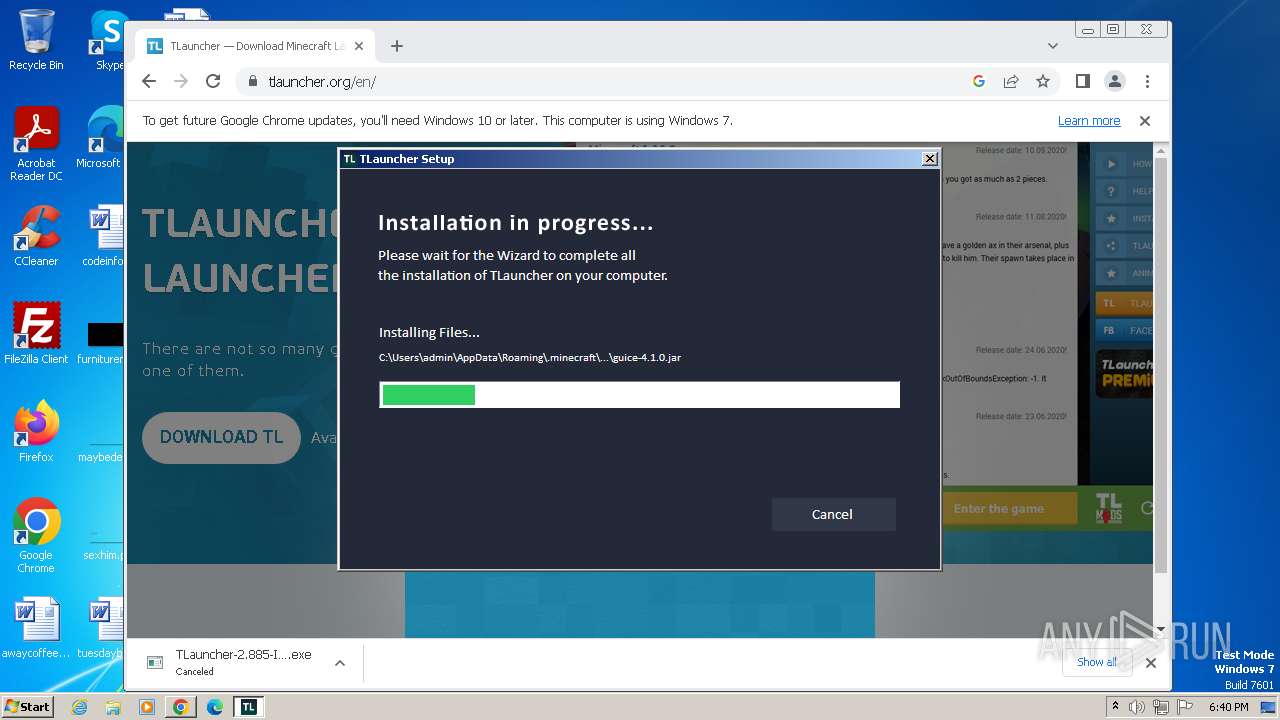
| 1764 | "C:\Users\admin\Downloads\TLauncher-2.885-Installer-1.1.3 (1).exe" | C:\Users\admin\Downloads\TLauncher-2.885-Installer-1.1.3 (1).exe | chrome.exe | ||||||||||||
User: admin Company: TLauncher Inc. Integrity Level: HIGH Description: TLauncher Setup Exit code: 0 Version: 1.1.3.0 Modules
| |||||||||||||||
Total events
36 192
Read events
35 791
Write events
400
Delete events
1
Modification events
| (PID) Process: | (612) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (612) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (612) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (612) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (612) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (612) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (612) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (612) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (612) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (612) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
48
Suspicious files
211
Text files
956
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3424 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 3424 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\0DA515F703BB9B49479E8697ADB0B955_96EEC010953ED454BBCDFA69FC071E7C | binary | |
MD5:05FC12172CD8C0DBE4805EA23A76A33E | SHA256:DCFB1B44D643D2745514C990E46C173708D257304D0F5966BCCB5B21443F6F6D | |||
| 2140 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1527f4.TMP | — | |
MD5:— | SHA256:— | |||
| 2140 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3424 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\v8b253dfea2ab4077af8c6f58422dfbfd1689876627854[1].js | text | |
MD5:EFEB2542712DCE8A2C51CF68396E4A05 | SHA256:C235F21017BCC11FCAA31D7DFD9855AAEBCBF5F6D7EE9BF9F2E98A910907C391 | |||
| 3424 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:FBD9B309407E0EC4B72357F6AEB4A481 | SHA256:36C2D7979520D8736404B4D3F0280E91D6CB21E99A78AC512F26979D59C04BC4 | |||
| 3424 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\0DA515F703BB9B49479E8697ADB0B955_96EEC010953ED454BBCDFA69FC071E7C | binary | |
MD5:8A77B81830E2018D24FFEC7AC6C3EFAD | SHA256:7F75B464B556A576E1814A5E837D8D9E9233FCED1E89E924CEA81D4831F216CC | |||
| 3424 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:CD019724C767B70D7BEF5B0E91BDCDE1 | SHA256:253C8A1C4405F465CDF58C41FC78FF882FA47C1CB70AA49DD8B44C63F3A0D2F9 | |||
| 612 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFB54CEAE42BC2654F.TMP | binary | |
MD5:931776B3D14F6B33A4A30BF848442066 | SHA256:1167657066F35C12740DBC68414110D120B2F7CE76CA8C48AD47997A3EF3B966 | |||
| 612 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\{24F8F826-63A6-11EE-B150-12A9866C77DE}.dat | binary | |
MD5:F23CCA218FF613F6EBD6C21340812C24 | SHA256:4063DA31D3A05486BD633AA28041B2A60658419699F15855A31C0C8A0A3E29AE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
65
DNS requests
61
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3084 | javaw.exe | GET | 302 | 78.46.66.120:80 | http://res.tlauncher.org/b/libraries/org/tlauncher/picture-bundle/3.72/picture-bundle-3.72.jar | unknown | — | — | unknown |
3084 | javaw.exe | GET | 302 | 78.46.66.120:80 | http://res.tlauncher.org/b/client/jre/windows/jre-8u111-windows-i586.tar.gz | unknown | — | — | unknown |
3424 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?717397429a10e56a | unknown | compressed | 4.66 Kb | unknown |
3424 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | binary | 1.47 Kb | unknown |
3424 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b79c52c977c97463 | unknown | compressed | 4.66 Kb | unknown |
3424 | iexplore.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/rootr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEH1NQqkrQx1%2BZFPnwZqNWHc%3D | unknown | binary | 1.41 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3424 | iexplore.exe | 104.20.235.70:443 | tlauncher.org | CLOUDFLARENET | — | unknown |
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3424 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3424 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
3424 | iexplore.exe | 104.18.21.226:80 | ocsp.globalsign.com | CLOUDFLARENET | — | shared |
3424 | iexplore.exe | 104.16.56.101:443 | static.cloudflareinsights.com | CLOUDFLARENET | — | unknown |
3424 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4052 | chrome.exe | 142.250.185.227:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
2140 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4052 | chrome.exe | 142.250.186.109:443 | accounts.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
static.cloudflareinsights.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
encrypted-tbn0.gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3084 | javaw.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |
3084 | javaw.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |