| URL: | https://tlauncher.org/en/ |
| Full analysis: | https://app.any.run/tasks/6b2af8cc-03e6-4fb7-8c9a-9d90d45799a4 |
| Verdict: | Malicious activity |
| Analysis date: | March 26, 2024, 01:39:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | C146A57F50544DCA592397189220E6B5 |
| SHA1: | 91D2079252AA9D349CA4BFDD7CA031A8D9CEA748 |
| SHA256: | C322DB70597221ED0C6CC05BB9208F5EF70614DBA14B01209EB4015E9EF96868 |
| SSDEEP: | 3:N8BEeLu5A+:2K5F |
MALICIOUS
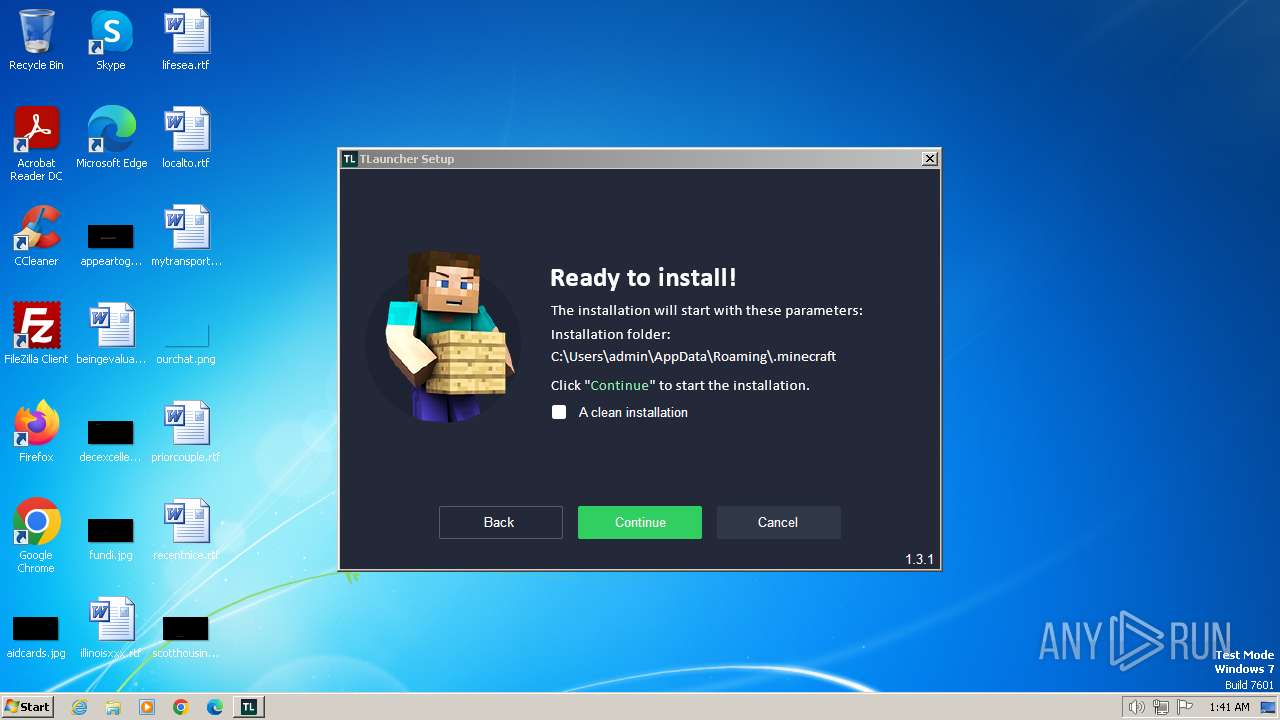
Drops the executable file immediately after the start
- TLauncher-2.899-Installer-1.3.1.exe (PID: 2256)
- irsetup.exe (PID: 2644)
- BrowserInstaller.exe (PID: 128)
- javaw.exe (PID: 1548)
- javaw.exe (PID: 3816)
Actions looks like stealing of personal data
- irsetup.exe (PID: 2644)
SUSPICIOUS
Executable content was dropped or overwritten
- TLauncher-2.899-Installer-1.3.1.exe (PID: 2256)
- irsetup.exe (PID: 2644)
- BrowserInstaller.exe (PID: 128)
- javaw.exe (PID: 1548)
- javaw.exe (PID: 3816)
Reads the Internet Settings
- TLauncher-2.899-Installer-1.3.1.exe (PID: 2256)
- irsetup.exe (PID: 2644)
- BrowserInstaller.exe (PID: 128)
- irsetup.exe (PID: 2760)
- WMIC.exe (PID: 1732)
- WMIC.exe (PID: 2492)
- WMIC.exe (PID: 1876)
- WMIC.exe (PID: 1636)
Reads security settings of Internet Explorer
- TLauncher-2.899-Installer-1.3.1.exe (PID: 2256)
- irsetup.exe (PID: 2644)
- BrowserInstaller.exe (PID: 128)
- irsetup.exe (PID: 2760)
Reads the Windows owner or organization settings
- irsetup.exe (PID: 2644)
- irsetup.exe (PID: 2760)
Checks for Java to be installed
- irsetup.exe (PID: 2644)
- TLauncher.exe (PID: 2424)
- TLauncher.exe (PID: 3548)
Checks Windows Trust Settings
- irsetup.exe (PID: 2644)
- irsetup.exe (PID: 2760)
Adds/modifies Windows certificates
- irsetup.exe (PID: 2644)
Reads settings of System Certificates
- irsetup.exe (PID: 2760)
- dxdiag.exe (PID: 1368)
- irsetup.exe (PID: 2644)
Creates a software uninstall entry
- irsetup.exe (PID: 2644)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 2380)
- cmd.exe (PID: 2740)
Starts application with an unusual extension
- cmd.exe (PID: 2740)
- cmd.exe (PID: 2380)
- cmd.exe (PID: 3124)
- cmd.exe (PID: 3120)
- cmd.exe (PID: 124)
- cmd.exe (PID: 3696)
- cmd.exe (PID: 1020)
Starts CMD.EXE for commands execution
- javaw.exe (PID: 1548)
- javaw.exe (PID: 3816)
Reads Internet Explorer settings
- irsetup.exe (PID: 2644)
The process drops C-runtime libraries
- javaw.exe (PID: 1548)
- javaw.exe (PID: 3816)
Process drops legitimate windows executable
- javaw.exe (PID: 1548)
- javaw.exe (PID: 3816)
Uses ICACLS.EXE to modify access control lists
- javaw.exe (PID: 3816)
Process requests binary or script from the Internet
- javaw.exe (PID: 3816)
Uses WMIC.EXE to obtain CPU information
- cmd.exe (PID: 3120)
Creates/Modifies COM task schedule object
- dxdiag.exe (PID: 1368)
Uses WMIC.EXE to obtain quick Fix Engineering (patches) data
- cmd.exe (PID: 3696)
The process creates files with name similar to system file names
- javaw.exe (PID: 3816)
Reads Microsoft Outlook installation path
- irsetup.exe (PID: 2644)
INFO
Application launched itself
- iexplore.exe (PID: 2120)
- chrome.exe (PID: 1576)
Manual execution by a user
- chrome.exe (PID: 1576)
- TLauncher.exe (PID: 3548)
Drops the executable file immediately after the start
- chrome.exe (PID: 1772)
- chrome.exe (PID: 1576)
The process uses the downloaded file
- chrome.exe (PID: 908)
- chrome.exe (PID: 1576)
Executable content was dropped or overwritten
- chrome.exe (PID: 1772)
- chrome.exe (PID: 1576)
Checks supported languages
- TLauncher-2.899-Installer-1.3.1.exe (PID: 2256)
- irsetup.exe (PID: 2644)
- BrowserInstaller.exe (PID: 128)
- irsetup.exe (PID: 2760)
- javaw.exe (PID: 1548)
- chcp.com (PID: 2556)
- chcp.com (PID: 668)
- TLauncher.exe (PID: 2424)
- TLauncher.exe (PID: 3548)
- javaw.exe (PID: 3416)
- javaw.exe (PID: 3816)
- chcp.com (PID: 840)
- chcp.com (PID: 2072)
- chcp.com (PID: 3504)
- chcp.com (PID: 3812)
- chcp.com (PID: 2904)
Create files in a temporary directory
- TLauncher-2.899-Installer-1.3.1.exe (PID: 2256)
- irsetup.exe (PID: 2644)
- BrowserInstaller.exe (PID: 128)
- irsetup.exe (PID: 2760)
- javaw.exe (PID: 1548)
- javaw.exe (PID: 3416)
- javaw.exe (PID: 3816)
Reads the computer name
- TLauncher-2.899-Installer-1.3.1.exe (PID: 2256)
- irsetup.exe (PID: 2644)
- BrowserInstaller.exe (PID: 128)
- irsetup.exe (PID: 2760)
- javaw.exe (PID: 1548)
- javaw.exe (PID: 3416)
- javaw.exe (PID: 3816)
Checks proxy server information
- irsetup.exe (PID: 2644)
- irsetup.exe (PID: 2760)
Reads the machine GUID from the registry
- irsetup.exe (PID: 2644)
- irsetup.exe (PID: 2760)
- javaw.exe (PID: 1548)
- javaw.exe (PID: 3816)
Reads the software policy settings
- irsetup.exe (PID: 2644)
- irsetup.exe (PID: 2760)
- dxdiag.exe (PID: 1368)
Creates files or folders in the user directory
- irsetup.exe (PID: 2644)
- javaw.exe (PID: 1548)
- javaw.exe (PID: 3416)
- javaw.exe (PID: 3816)
Creates files in the program directory
- irsetup.exe (PID: 2644)
- javaw.exe (PID: 1548)
- javaw.exe (PID: 3816)
Reads security settings of Internet Explorer
- dxdiag.exe (PID: 1368)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
113
Monitored processes
54
Malicious processes
9
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | cmd.exe /C chcp 437 & set processor | C:\Windows\System32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 128 | "C:\Users\admin\AppData\Local\Temp\BrowserInstaller.exe" /NOINIT /S:C:\Users\admin\AppData\Local\Temp\setuparguments.ini | C:\Users\admin\AppData\Local\Temp\BrowserInstaller.exe | irsetup.exe | ||||||||||||
User: admin Company: TLauncher Inc. Integrity Level: HIGH Description: Installer of Browser Offers in TLauncher Exit code: 0 Version: 2.6.0.0 Modules
| |||||||||||||||
| 668 | chcp 437 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 680 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1080 --field-trial-handle=892,i,6208108103792901040,2067340479357805860,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 840 | chcp 437 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 908 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=4120 --field-trial-handle=892,i,6208108103792901040,2067340479357805860,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 948 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=2288 --field-trial-handle=892,i,6208108103792901040,2067340479357805860,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1020 | cmd.exe /C chcp 437 & dxdiag /whql:off /t C:\Users\admin\AppData\Roaming\.minecraft\logs\tlauncher\dxdiag.txt | C:\Windows\System32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1168 | icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage\608ad60fbfdf0bc0.timestamp /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1368 | dxdiag /whql:off /t C:\Users\admin\AppData\Roaming\.minecraft\logs\tlauncher\dxdiag.txt | C:\Windows\System32\dxdiag.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft DirectX Diagnostic Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
57 808
Read events
57 177
Write events
532
Delete events
99
Modification events
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31096606 | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31096606 | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
391
Suspicious files
1 412
Text files
1 391
Unknown types
83
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2120 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | binary | |
MD5:849748FC4DB0BB637709F8B100D89AC8 | SHA256:49510E8B4F25F130409784F92C9F366BBA89BF810CB17B45672677434F17EA77 | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:4DD6C26BA34071E16E0616B9F6D241AA | SHA256:A5852C3C449B39843F2029A7311C82CB88B49CC0F2B7608C515049DF6C39619A | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:65A591E032F79D56E3B0B8E8326C8D4C | SHA256:E756605DC8465008D7DD7498E33B21F69BA48396B28BB3013862EBBB9FB177DF | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:DC83F7ACAED8A3525BC9A91778A357AF | SHA256:BCBA6E9A08BEEE95D60ACEA8C5B0646042759E4D125F2956BA3834FB84434970 | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:C2474BC1392A4B847CD3CBCAA4594A38 | SHA256:21501CD272F13C1EDF39551F4098DF93AA7615A1D77B53A90E39A4F75C626A15 | |||
| 1576 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF186193.TMP | — | |
MD5:— | SHA256:— | |||
| 1576 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:F0BA032DE86CEE2DDA99C39E085827A9 | SHA256:4F43FDBC4FA8772D63D2285A4D82C221B273CCD3AAB9784CA1B4F03FE2DDC410 | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | der | |
MD5:8202A1CD02E7D69597995CABBE881A12 | SHA256:58F381C3A0A0ACE6321DA22E40BD44A597BD98B9C9390AB9258426B5CF75A7A5 | |||
| 2120 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicon[2].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
123
DNS requests
71
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3092 | iexplore.exe | GET | 304 | 95.101.54.227:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?5259f1aa84763c8c | unknown | — | — | unknown |
3092 | iexplore.exe | GET | 304 | 2.16.202.65:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?7f30423e8f7249ff | unknown | — | — | unknown |
3092 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3092 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | binary | 2.18 Kb | unknown |
2120 | iexplore.exe | GET | 304 | 2.16.202.65:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4ad9b1827f1f75f1 | unknown | — | — | unknown |
3092 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
2120 | iexplore.exe | GET | 304 | 2.16.202.65:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?dca56d26e7d9ce15 | unknown | — | — | unknown |
2120 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 314 b | unknown |
2120 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
1080 | svchost.exe | GET | 200 | 95.101.54.243:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?aa4b77dd5ef709e5 | unknown | compressed | 67.5 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3092 | iexplore.exe | 104.20.64.88:443 | tlauncher.org | CLOUDFLARENET | — | unknown |
3092 | iexplore.exe | 2.16.202.65:80 | ctldl.windowsupdate.com | Akamai International B.V. | NL | unknown |
3092 | iexplore.exe | 95.101.54.227:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3092 | iexplore.exe | 104.18.38.233:80 | ocsp.usertrust.com | CLOUDFLARENET | — | shared |
3092 | iexplore.exe | 104.16.80.73:443 | static.cloudflareinsights.com | CLOUDFLARENET | — | unknown |
3092 | iexplore.exe | 172.217.18.3:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
2120 | iexplore.exe | 2.23.209.187:443 | www.bing.com | Akamai International B.V. | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
tlauncher.org |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
static.cloudflareinsights.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1772 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
— | — | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |
3816 | javaw.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |