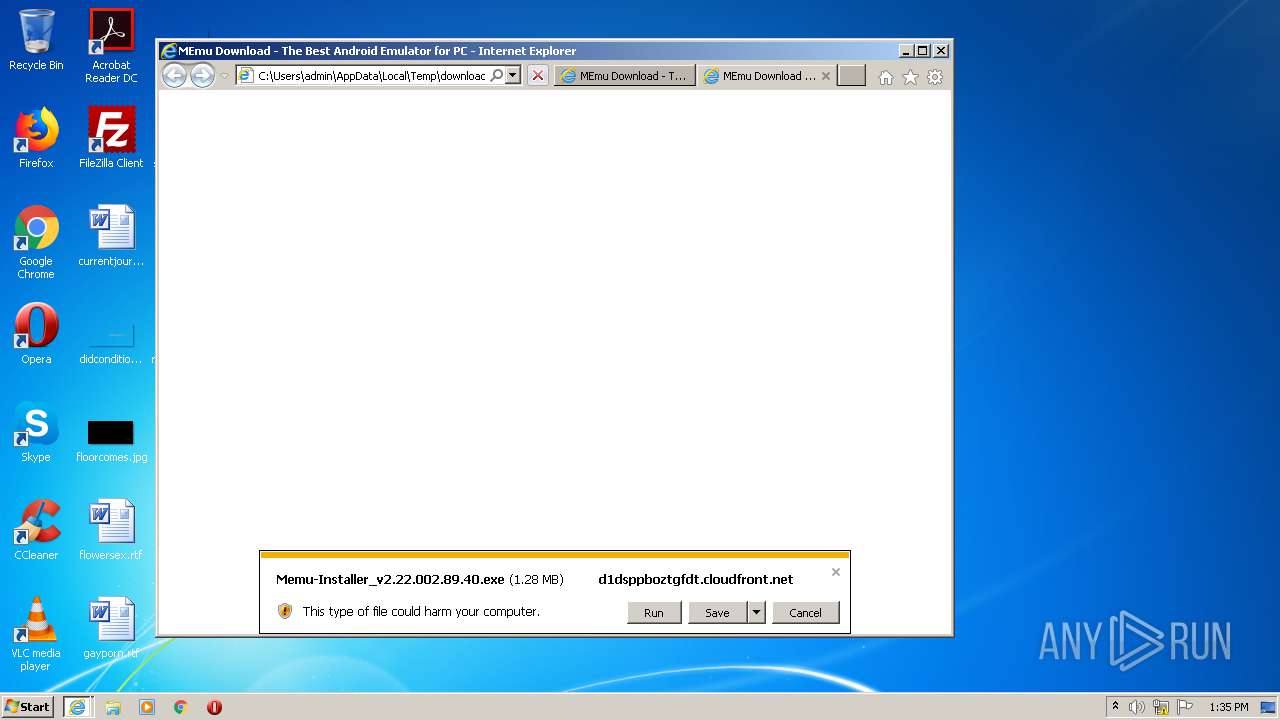
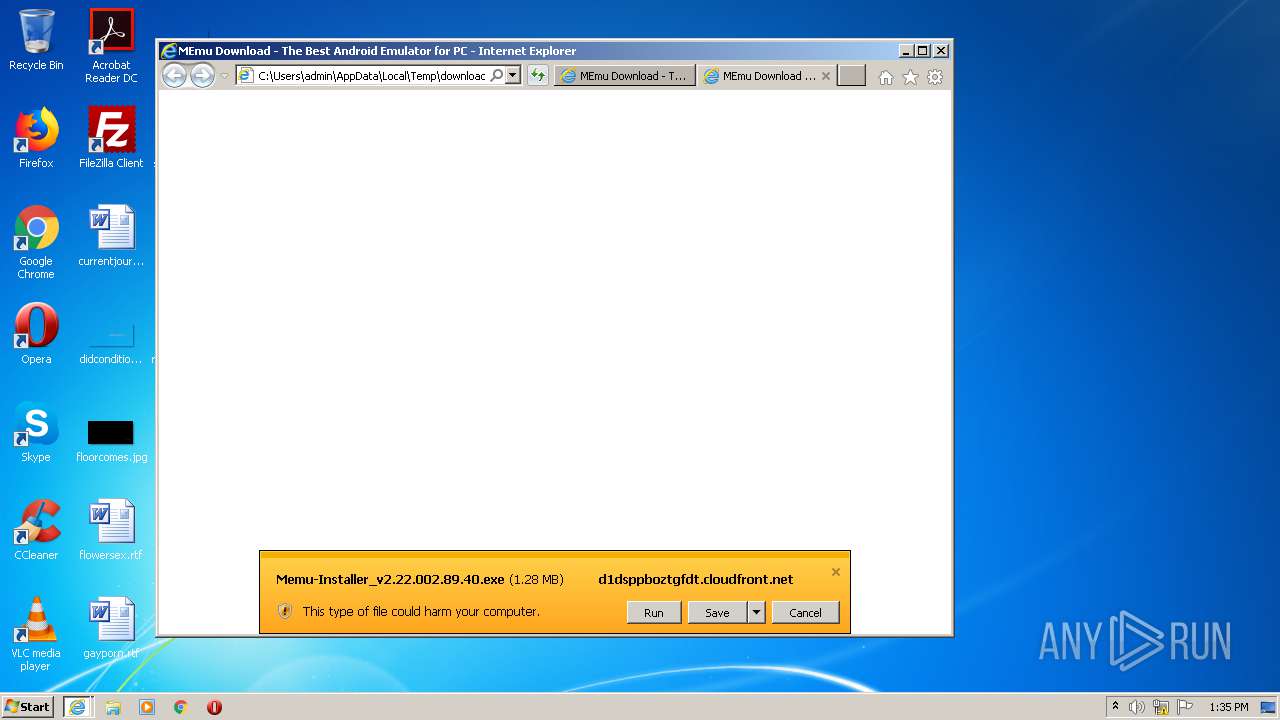
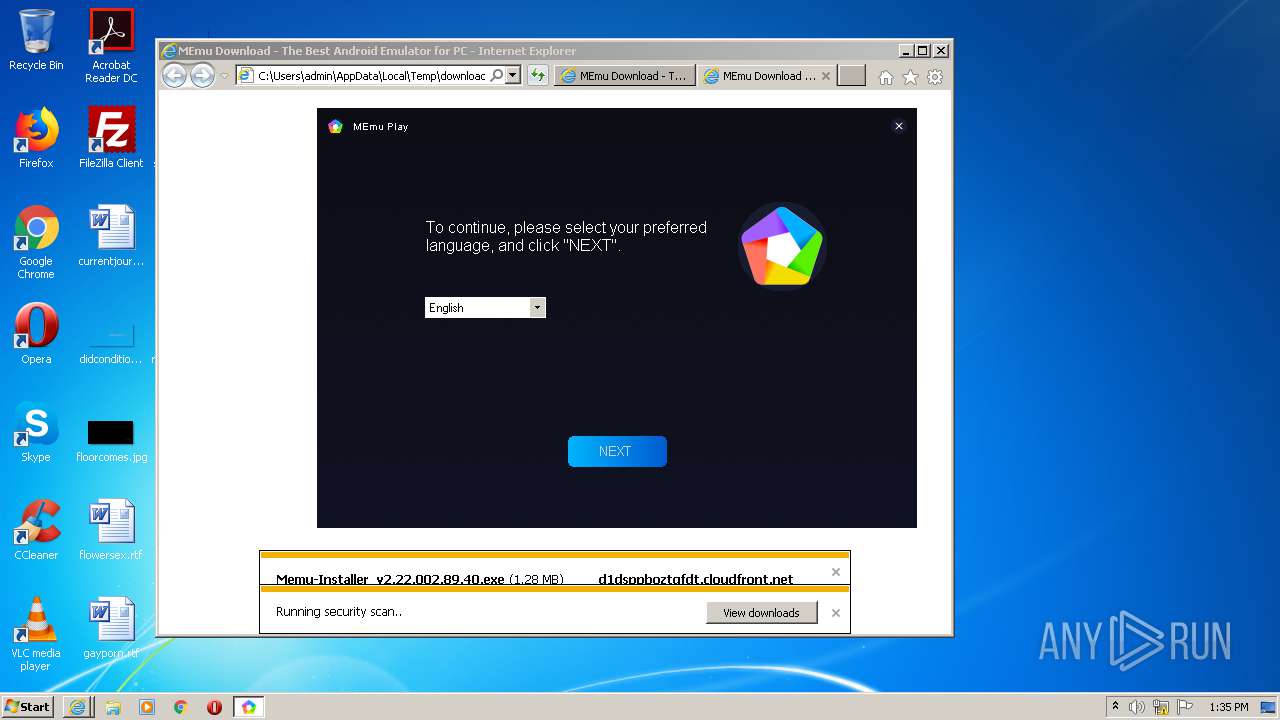
| download: | download-memu-on-pc.html |
| Full analysis: | https://app.any.run/tasks/40acb74d-399e-40a1-827e-db63a31d50be |
| Verdict: | Malicious activity |
| Analysis date: | January 13, 2021, 13:34:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, UTF-8 Unicode text, with very long lines |
| MD5: | 985FC71A0E3735055EB4B36B02A19322 |
| SHA1: | F4D829FAA5D46D03324282B4B49226C43552981C |
| SHA256: | C31A30C0AC0325151204ACBF91EACED920A7C5E99FC433C19814989091148D13 |
| SSDEEP: | 1536:xpOdu54ZZfdLirkawDpPt7leCb99UhNMS:rOdpdpTaG9JsyG |
MALICIOUS
Application was dropped or rewritten from another process
- Memu-Installer_v2.22.002.89.40.exe (PID: 2508)
- Memu-Installer_v2.22.002.89.40.exe (PID: 864)
SUSPICIOUS
Drops a file with a compile date too recent
- iexplore.exe (PID: 2260)
- iexplore.exe (PID: 2560)
Executable content was dropped or overwritten
- iexplore.exe (PID: 2260)
- iexplore.exe (PID: 2560)
INFO
Changes internet zones settings
- iexplore.exe (PID: 2560)
Application launched itself
- iexplore.exe (PID: 2560)
Reads internet explorer settings
- iexplore.exe (PID: 2188)
- iexplore.exe (PID: 2200)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2188)
- iexplore.exe (PID: 2200)
- iexplore.exe (PID: 2560)
Changes settings of System certificates
- iexplore.exe (PID: 2200)
- iexplore.exe (PID: 2188)
- iexplore.exe (PID: 2560)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2560)
Reads settings of System Certificates
- iexplore.exe (PID: 2560)
- iexplore.exe (PID: 2188)
- iexplore.exe (PID: 2200)
- iexplore.exe (PID: 2260)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .htm/html | | | HyperText Markup Language with DOCTYPE (80.6) |
|---|---|---|
| .html | | | HyperText Markup Language (19.3) |
EXIF
HTML
| viewport: | width=device-width, initial-scale=1.0, maximum-scale=1.0, user-scalable=0 |
|---|---|
| Title: | MEmu Download - The Best Android Emulator for PC |
| Keywords: | memu, memuplay, memu play, memu app player, memu player, memu emulator, memu emulador, memu download, download memu, memu official, download memuplay, memuplay download, pubg pc download, free fire pc download |
| Description: | Download MEmu Play - The Best Android Emulator for Windows 10. Join over 100 million users to play Android games on PC with MEmu Play. |
| YahooSeeker: | Index,Follow |
| GoogleBot: | Index,Follow |
| allowSearch: | Yes |
| Robots: | all, index, follow |
Total processes
42
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 864 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\Memu-Installer_v2.22.002.89.40.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\Memu-Installer_v2.22.002.89.40.exe | iexplore.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Product Installer Exit code: 0 Version: 1.86.2.7677 Modules
| |||||||||||||||
| 2188 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2560 CREDAT:144385 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2200 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2560 CREDAT:78856 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2260 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2560 CREDAT:464129 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2508 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\Memu-Installer_v2.22.002.89.40.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\Memu-Installer_v2.22.002.89.40.exe | — | iexplore.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Product Installer Exit code: 3221226540 Version: 1.86.2.7677 Modules
| |||||||||||||||
| 2560 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Temp\download-memu-on-pc.html.htm | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
3 721
Read events
3 538
Write events
173
Delete events
10
Modification events
| (PID) Process: | (2560) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 3853454526 | |||
| (PID) Process: | (2560) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30861744 | |||
| (PID) Process: | (2560) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2560) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2560) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2560) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2560) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2560) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A5000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2560) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2560) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
4
Suspicious files
30
Text files
15
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2188 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Cab32F0.tmp | — | |
MD5:— | SHA256:— | |||
| 2188 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Tar32F1.tmp | — | |
MD5:— | SHA256:— | |||
| 2560 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2200 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Cab51D3.tmp | — | |
MD5:— | SHA256:— | |||
| 2200 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Tar51D4.tmp | — | |
MD5:— | SHA256:— | |||
| 2188 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_86C2A03C133240EC4C95180B9FD368BB | der | |
MD5:— | SHA256:— | |||
| 2188 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_86C2A03C133240EC4C95180B9FD368BB | binary | |
MD5:— | SHA256:— | |||
| 2188 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\com.activision.callofduty.shooter.icon.2020-12-20-21-13-05[1].png | image | |
MD5:— | SHA256:— | |||
| 2188 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CC197601BE0898B7B0FCC91FA15D8A69_64896AE48D54B1B5A7D838BED3DEBE59 | binary | |
MD5:— | SHA256:— | |||
| 2188 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CC197601BE0898B7B0FCC91FA15D8A69_64896AE48D54B1B5A7D838BED3DEBE59 | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
60
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2188 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAeYNgOt45kIIZygDCe8imw%3D | US | der | 471 b | whitelisted |
2188 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAeYNgOt45kIIZygDCe8imw%3D | US | der | 471 b | whitelisted |
2188 | iexplore.exe | GET | 200 | 216.58.206.3:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQD9enfDLjOiuAUAAAAAgwva | US | der | 472 b | whitelisted |
2188 | iexplore.exe | GET | 304 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAeYNgOt45kIIZygDCe8imw%3D | US | der | 471 b | whitelisted |
2188 | iexplore.exe | GET | 200 | 216.58.206.3:80 | http://crl.pki.goog/gsr2/gsr2.crl | US | der | 950 b | whitelisted |
2188 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAeYNgOt45kIIZygDCe8imw%3D | US | der | 471 b | whitelisted |
2188 | iexplore.exe | GET | 304 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAeYNgOt45kIIZygDCe8imw%3D | US | der | 471 b | whitelisted |
2188 | iexplore.exe | GET | 200 | 216.58.206.3:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
2188 | iexplore.exe | GET | 200 | 216.58.206.3:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQD9enfDLjOiuAUAAAAAgwva | US | der | 472 b | whitelisted |
2188 | iexplore.exe | GET | 200 | 216.58.206.3:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEFXE245%2FYPvoAwAAAADDJDU%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 216.58.208.40:443 | www.googletagmanager.com | Google Inc. | US | whitelisted |
— | — | 172.217.23.162:443 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
2188 | iexplore.exe | 172.217.23.162:443 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
2188 | iexplore.exe | 205.185.216.42:443 | dl.memuplay.com | Highwinds Network Group, Inc. | US | whitelisted |
2188 | iexplore.exe | 205.185.216.10:443 | dl.memuplay.com | Highwinds Network Group, Inc. | US | whitelisted |
2188 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2188 | iexplore.exe | 216.58.206.3:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
2200 | iexplore.exe | 205.185.216.42:443 | dl.memuplay.com | Highwinds Network Group, Inc. | US | whitelisted |
2200 | iexplore.exe | 172.217.23.162:443 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
2200 | iexplore.exe | 216.58.208.40:443 | www.googletagmanager.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.googletagmanager.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
dl.memuplay.com |
| suspicious |
www.memuplay.com |
| malicious |
ocsp.digicert.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.bing.com |
| whitelisted |
api.bing.com |
| whitelisted |
d1dsppboztgfdt.cloudfront.net |
| whitelisted |
crl.pki.goog |
| whitelisted |