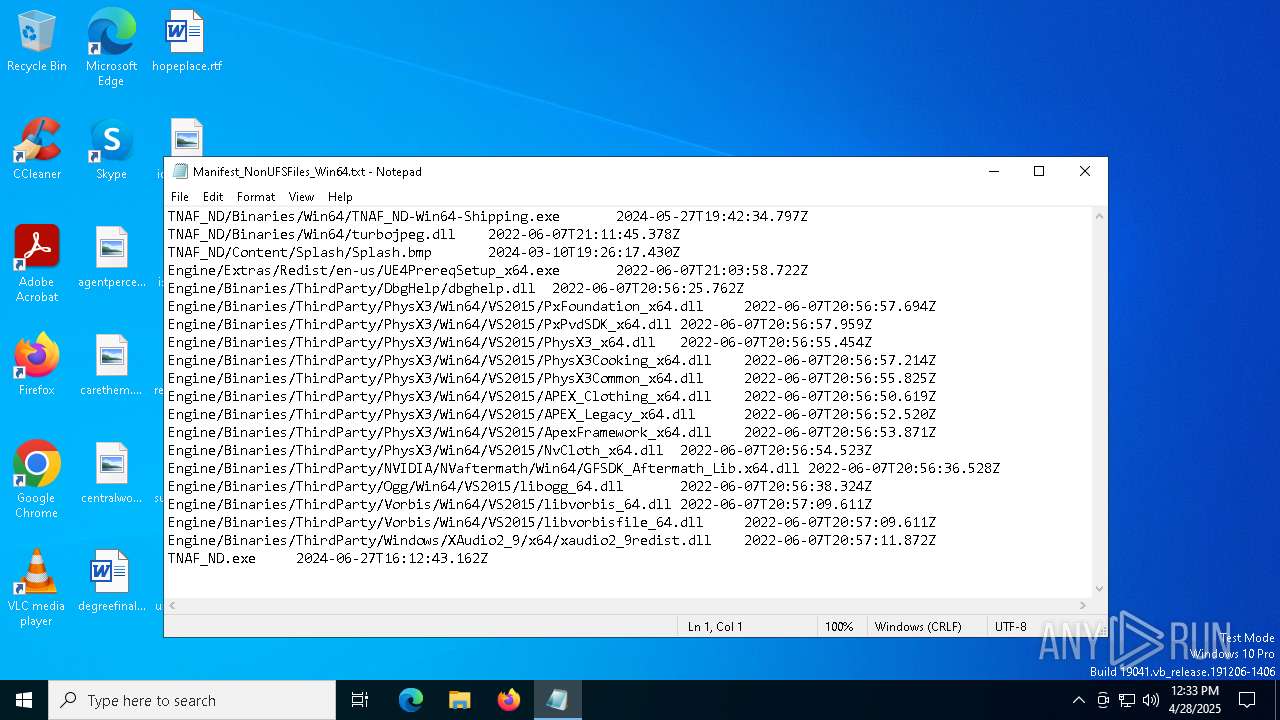
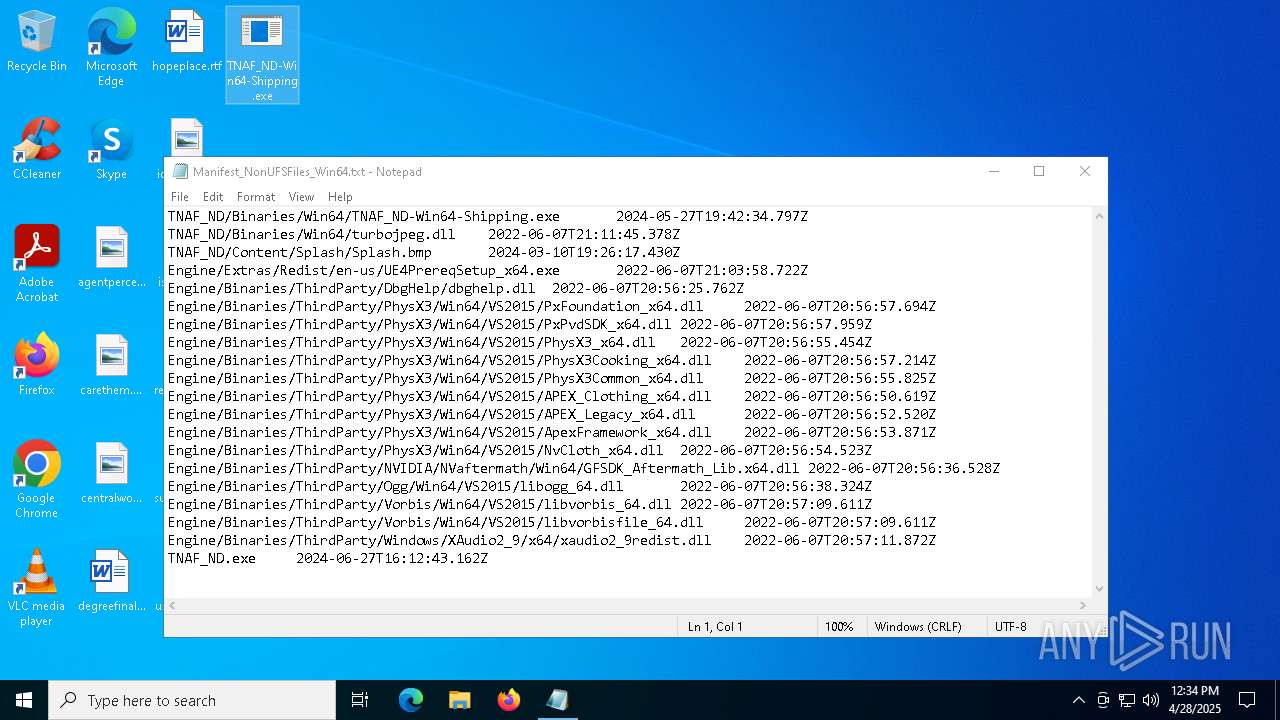
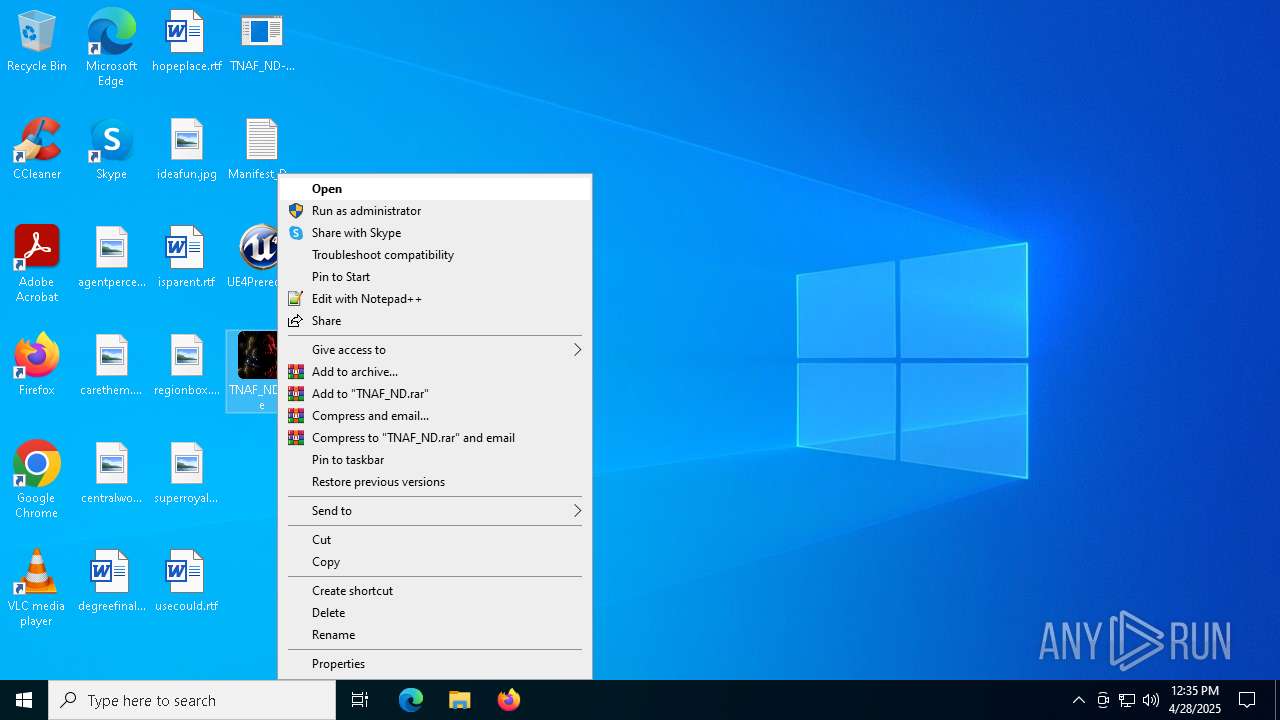
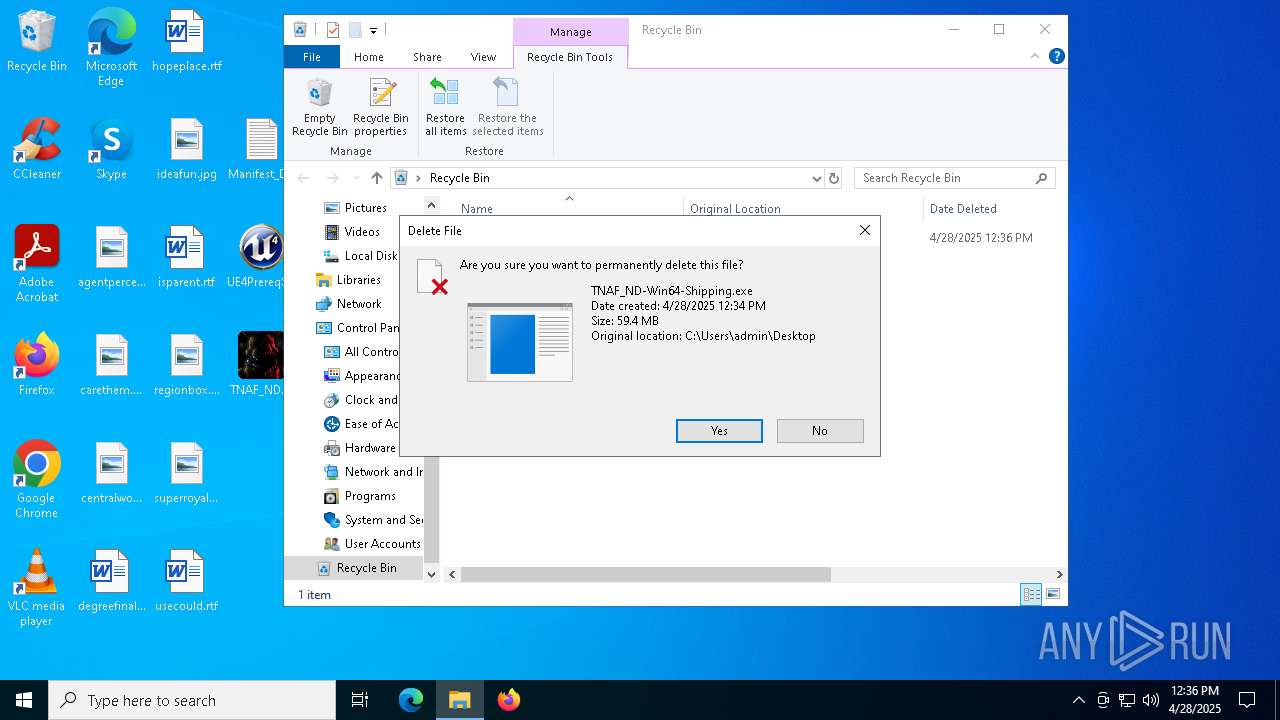
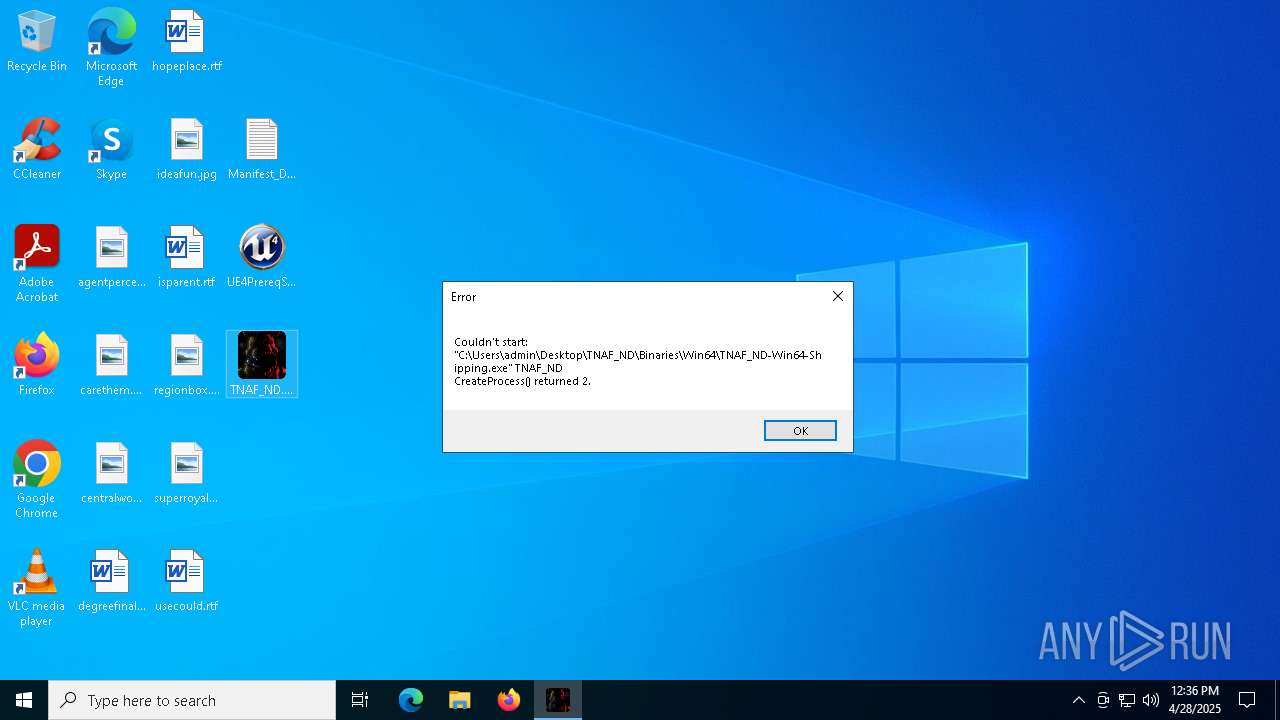
| File name: | Manifest_NonUFSFiles_Win64.txt |
| Full analysis: | https://app.any.run/tasks/2e4e47fc-38b8-4b28-a486-0e3d77a9576f |
| Verdict: | Malicious activity |
| Analysis date: | April 28, 2025, 12:33:23 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | 36E5F538B08726749619678ADC7D8109 |
| SHA1: | C3A02679DB6441439FBBC765D5E062E40626FA58 |
| SHA256: | C317E27E8D7C0A5B77EE800707767F3462F0950ADAE910AF810CCCCA6748AF37 |
| SSDEEP: | 48:saeMrSNVai9urO3aPskB00Q6+lcehChclVE:HLrfi9EO3aUkB00QdWehChMi |
MALICIOUS
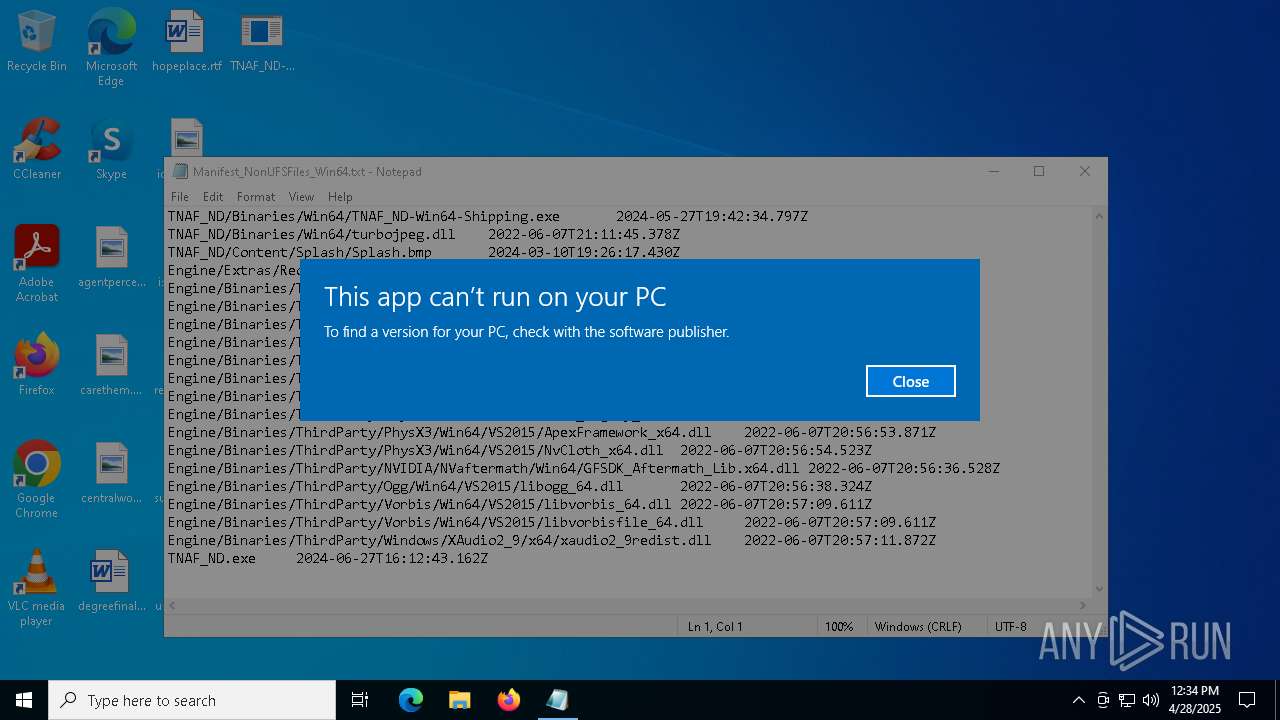
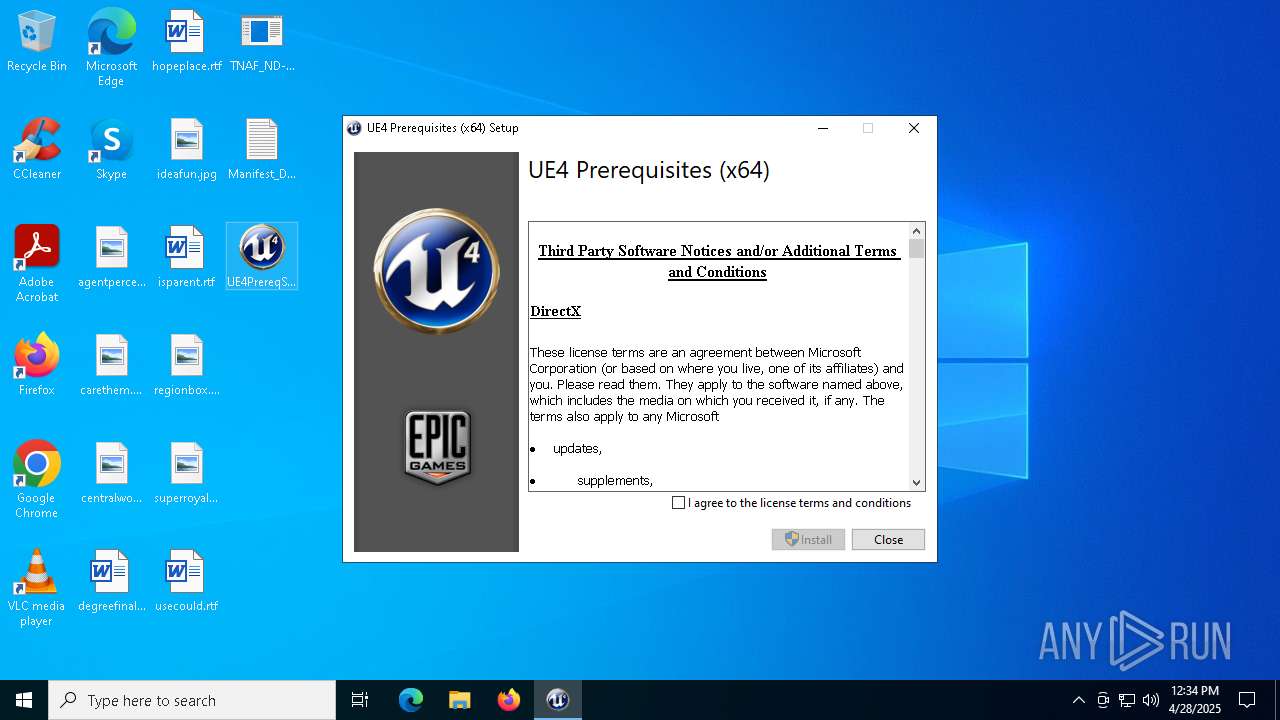
Executing a file with an untrusted certificate
- UE4PrereqSetup_x64.exe (PID: 4892)
- UE4PrereqSetup_x64.exe (PID: 1660)
- DXSETUP.exe (PID: 1568)
- infinst.exe (PID: 2092)
- infinst.exe (PID: 3896)
- infinst.exe (PID: 744)
- infinst.exe (PID: 2644)
- infinst.exe (PID: 7924)
- infinst.exe (PID: 5680)
- infinst.exe (PID: 7372)
- infinst.exe (PID: 1276)
Registers / Runs the DLL via REGSVR32.EXE
- DXSETUP.exe (PID: 1568)
SUSPICIOUS
Searches for installed software
- UE4PrereqSetup_x64.exe (PID: 4892)
- dllhost.exe (PID: 1056)
Executes as Windows Service
- VSSVC.exe (PID: 1188)
There is functionality for taking screenshot (YARA)
- UE4PrereqSetup_x64.exe (PID: 1660)
- UE4PrereqSetup_x64.exe (PID: 4892)
Process drops legitimate windows executable
- UE4PrereqSetup_x64.exe (PID: 4892)
- vcredist_x86.exe (PID: 7976)
- vcredist_x64.exe (PID: 7896)
- msiexec.exe (PID: 8096)
- DXSETUP.exe (PID: 1568)
- infinst.exe (PID: 2092)
- UE4PrereqSetup_x64.exe (PID: 1660)
- infinst.exe (PID: 3896)
- infinst.exe (PID: 7924)
- infinst.exe (PID: 744)
- infinst.exe (PID: 1276)
- infinst.exe (PID: 5680)
- infinst.exe (PID: 7372)
- infinst.exe (PID: 2644)
Executable content was dropped or overwritten
- UE4PrereqSetup_x64.exe (PID: 1660)
- vcredist_x64.exe (PID: 7896)
- vcredist_x86.exe (PID: 7976)
- vcredist_x86.exe (PID: 8024)
- UE4PrereqSetup_x64.exe (PID: 4892)
- vcredist_x64.exe (PID: 7796)
- rundll32.exe (PID: 6512)
- DXSETUP.exe (PID: 1568)
- infinst.exe (PID: 2092)
- infinst.exe (PID: 7924)
- infinst.exe (PID: 3896)
- infinst.exe (PID: 744)
- infinst.exe (PID: 2644)
- infinst.exe (PID: 5680)
- infinst.exe (PID: 1276)
- infinst.exe (PID: 7372)
Starts a Microsoft application from unusual location
- vcredist_x86.exe (PID: 8024)
- vcredist_x64.exe (PID: 7796)
The process drops C-runtime libraries
- msiexec.exe (PID: 8096)
Reads security settings of Internet Explorer
- UE4PrereqSetup_x64.exe (PID: 4892)
Application launched itself
- msiexec.exe (PID: 8096)
Uses RUNDLL32.EXE to load library
- msiexec.exe (PID: 4944)
INFO
Reads security settings of Internet Explorer
- notepad.exe (PID: 7560)
Reads the software policy settings
- slui.exe (PID: 7712)
Manual execution by a user
- UE4PrereqSetup_x64.exe (PID: 4892)
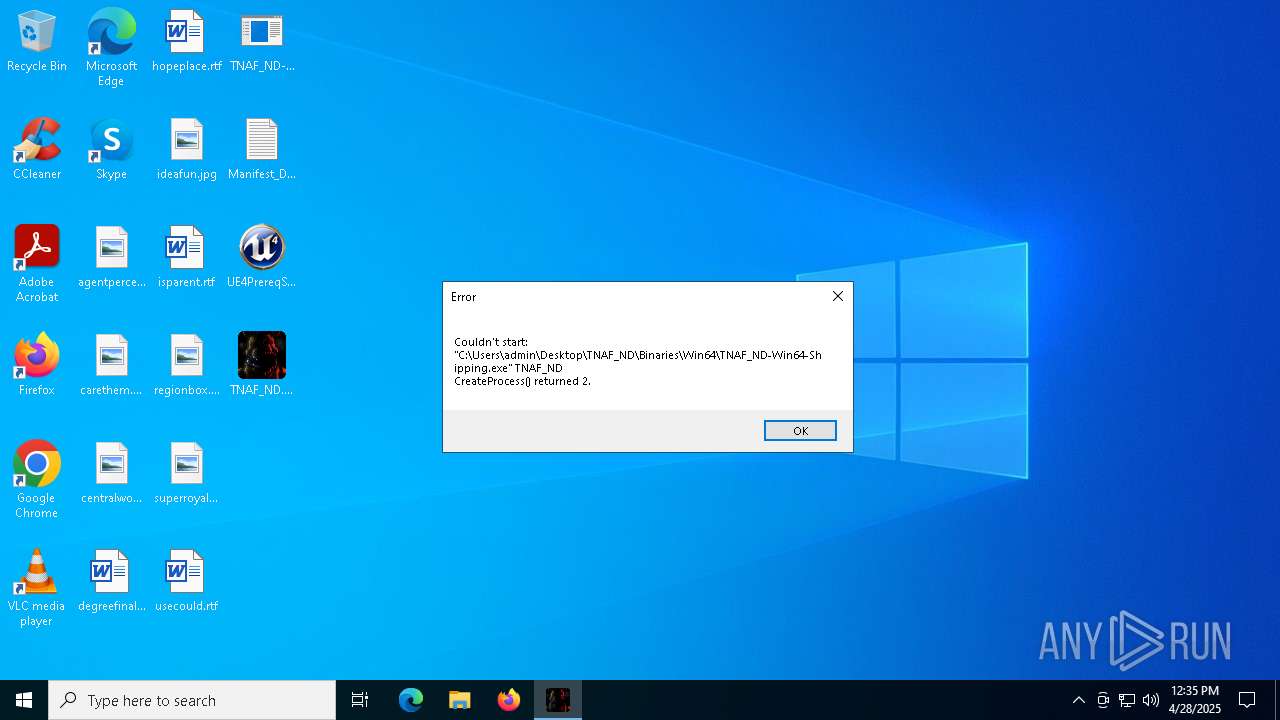
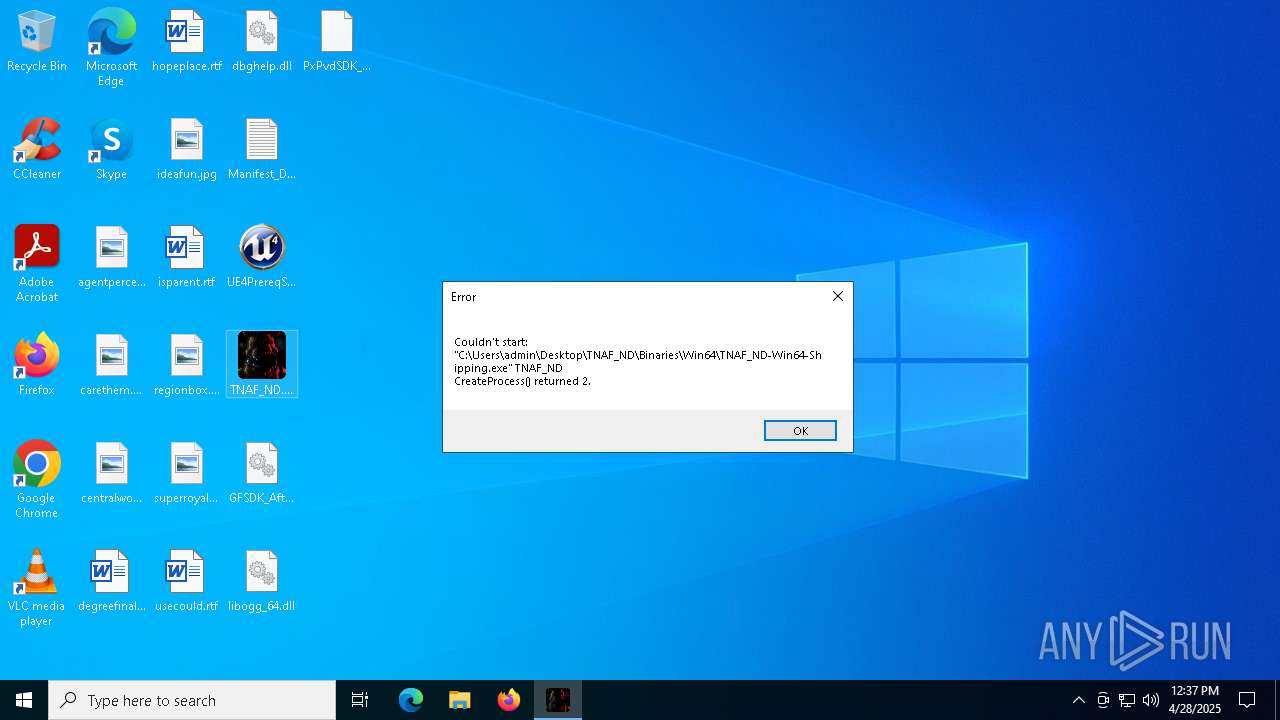
- TNAF_ND.exe (PID: 1244)
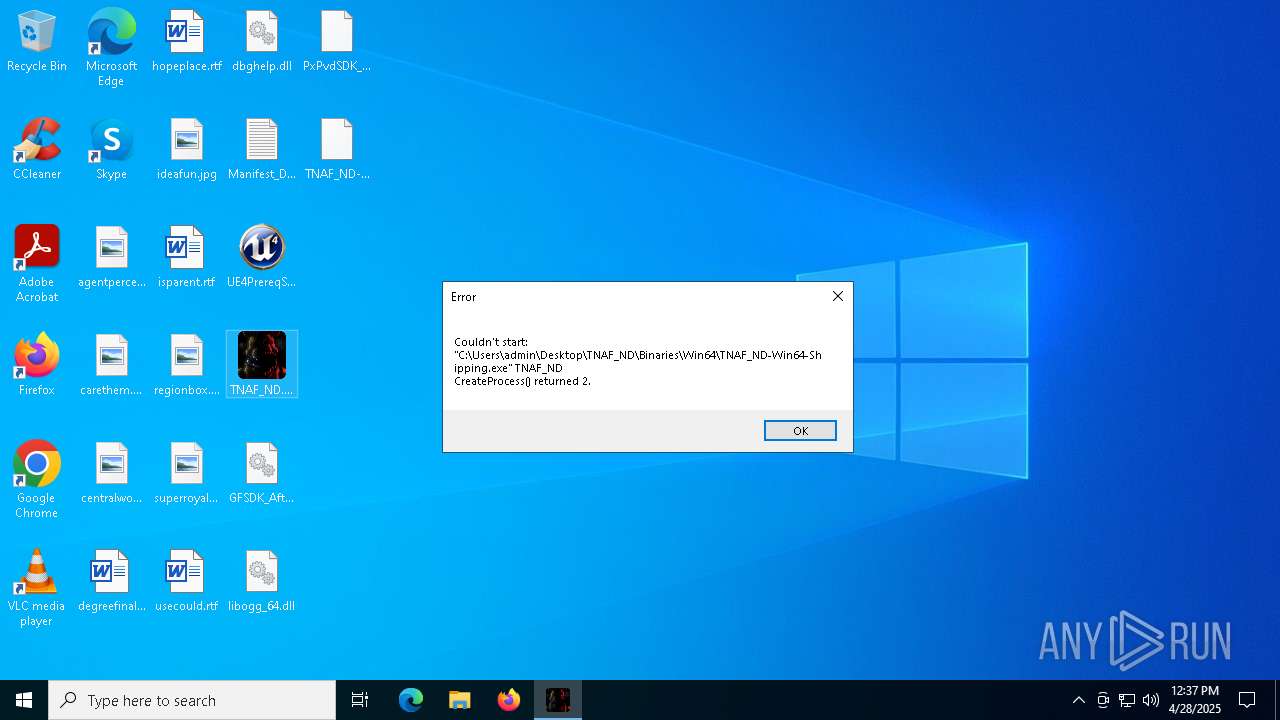
- TNAF_ND.exe (PID: 7536)
- TNAF_ND.exe (PID: 5364)
- TNAF_ND.exe (PID: 3992)
- TNAF_ND.exe (PID: 2108)
Checks supported languages
- UE4PrereqSetup_x64.exe (PID: 4892)
- UE4PrereqSetup_x64.exe (PID: 1660)
Create files in a temporary directory
- UE4PrereqSetup_x64.exe (PID: 4892)
Reads the computer name
- UE4PrereqSetup_x64.exe (PID: 4892)
- UE4PrereqSetup_x64.exe (PID: 1660)
The sample compiled with english language support
- UE4PrereqSetup_x64.exe (PID: 4892)
- vcredist_x86.exe (PID: 7976)
- vcredist_x86.exe (PID: 8024)
- vcredist_x64.exe (PID: 7896)
- vcredist_x64.exe (PID: 7796)
- msiexec.exe (PID: 8096)
- rundll32.exe (PID: 6512)
- DXSETUP.exe (PID: 1568)
- infinst.exe (PID: 2092)
- UE4PrereqSetup_x64.exe (PID: 1660)
- infinst.exe (PID: 3896)
- infinst.exe (PID: 7924)
- infinst.exe (PID: 744)
- infinst.exe (PID: 2644)
- infinst.exe (PID: 5680)
- infinst.exe (PID: 7372)
- infinst.exe (PID: 1276)
Process checks computer location settings
- UE4PrereqSetup_x64.exe (PID: 4892)
Manages system restore points
- SrTasks.exe (PID: 7752)
Executable content was dropped or overwritten
- msiexec.exe (PID: 8096)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
171
Monitored processes
33
Malicious processes
15
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 744 | C:\Users\admin\AppData\Local\Temp\DX6DA6.tmp\infinst.exe d3dx10_43_x64.inf | C:\Users\admin\AppData\Local\Temp\DX6DA6.tmp\infinst.exe | DXSETUP.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 1056 | C:\WINDOWS\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1188 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
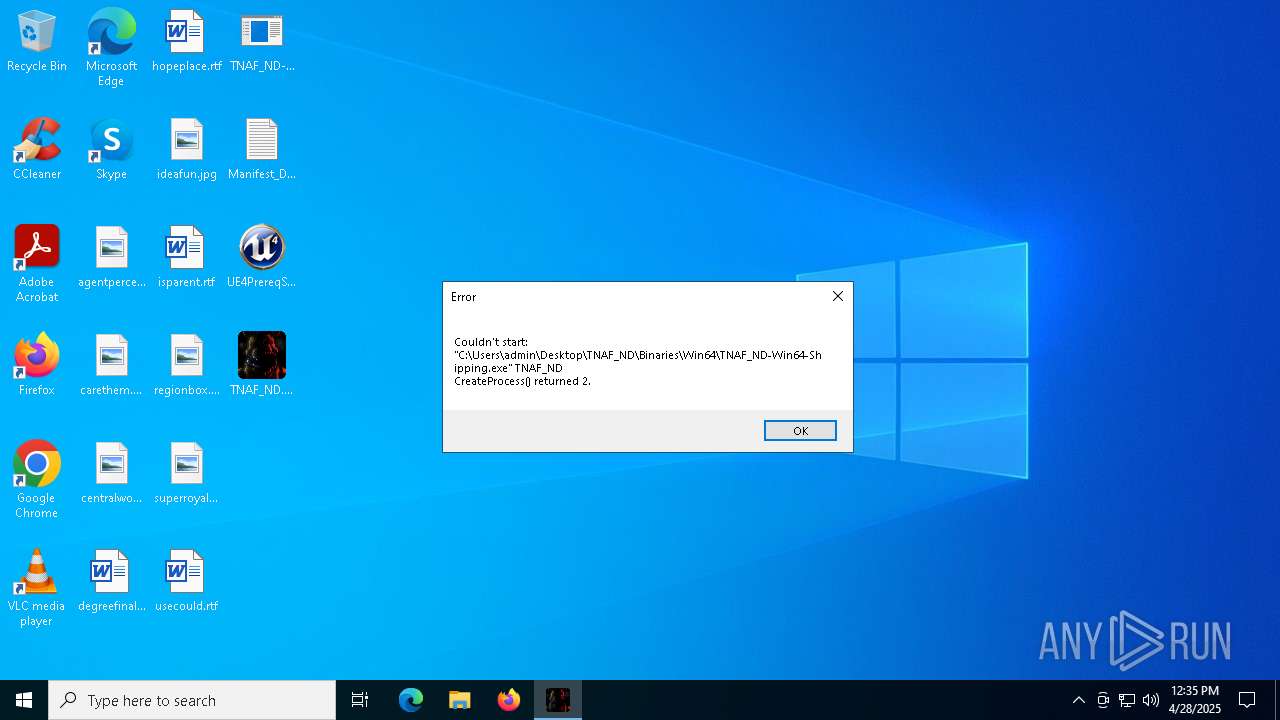
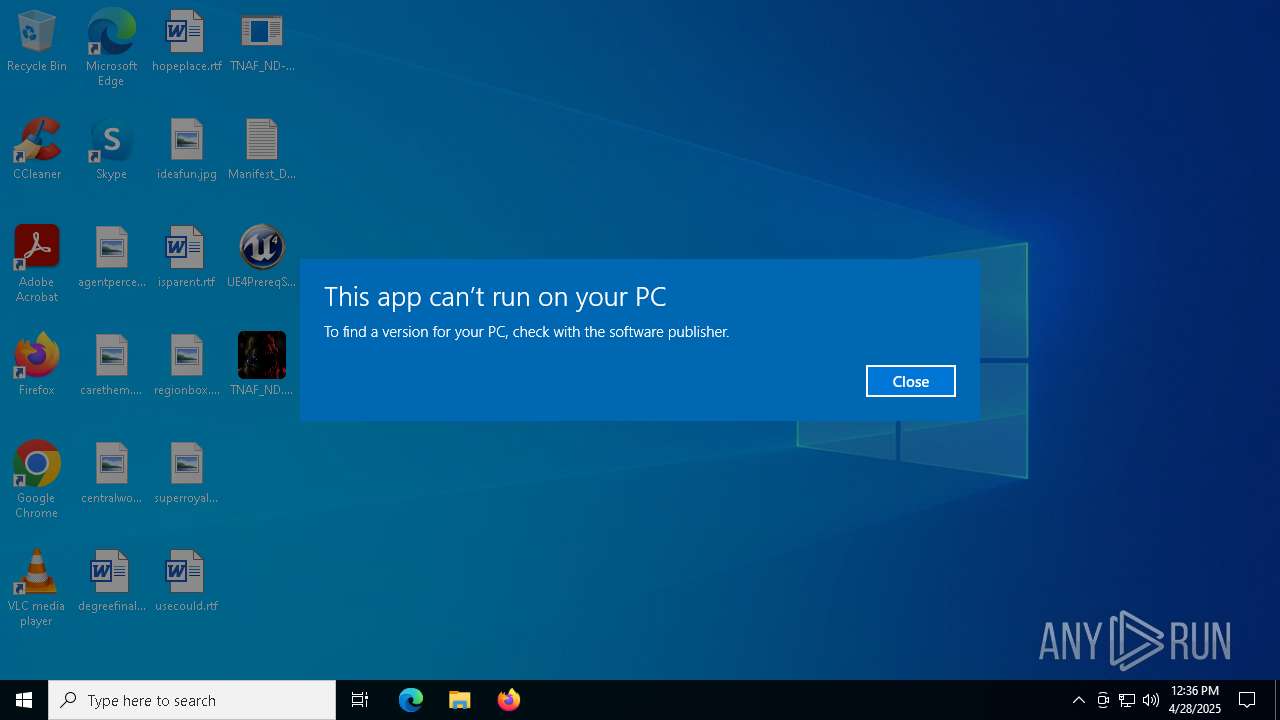
| 1244 | "C:\Users\admin\Desktop\TNAF_ND.exe" | C:\Users\admin\Desktop\TNAF_ND.exe | — | explorer.exe | |||||||||||
User: admin Company: Epic Games, Inc. Integrity Level: MEDIUM Description: BootstrapPackagedGame Exit code: 9005 Modules
| |||||||||||||||
| 1276 | C:\Users\admin\AppData\Local\Temp\DX6DA6.tmp\infinst.exe D3DCompiler_43_x64.inf | C:\Users\admin\AppData\Local\Temp\DX6DA6.tmp\infinst.exe | DXSETUP.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 1568 | "C:\WINDOWS\Installer\MSI67AC.tmp-\DXSetup.exe" /silent | C:\Windows\Installer\MSI67AC.tmp-\DXSETUP.exe | rundll32.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft DirectX Setup Exit code: 0 Version: 4.9.0.0904 Modules
| |||||||||||||||
| 1660 | "C:\Users\admin\AppData\Local\Temp\{0d995f46-317b-4b5f-bf3e-9f98bae9d339}\.be\UE4PrereqSetup_x64.exe" -q -burn.elevated BurnPipe.{D5F4F225-000A-4581-BB83-10698A028F02} {F675368C-8863-40F7-96B5-4BEDECC252B0} 4892 | C:\Users\admin\AppData\Local\Temp\{0d995f46-317b-4b5f-bf3e-9f98bae9d339}\.be\UE4PrereqSetup_x64.exe | UE4PrereqSetup_x64.exe | ||||||||||||
User: admin Company: Epic Games, Inc. Integrity Level: HIGH Description: UE4 Prerequisites (x64) Exit code: 0 Version: 1.0.14.0 Modules
| |||||||||||||||
| 2092 | C:\Users\admin\AppData\Local\Temp\DX6DA6.tmp\infinst.exe xinput1_3_x64.inf, Install_Driver | C:\Users\admin\AppData\Local\Temp\DX6DA6.tmp\infinst.exe | DXSETUP.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 2108 | "C:\Users\admin\Desktop\TNAF_ND.exe" | C:\Users\admin\Desktop\TNAF_ND.exe | — | explorer.exe | |||||||||||
User: admin Company: Epic Games, Inc. Integrity Level: MEDIUM Description: BootstrapPackagedGame Exit code: 9005 Modules
| |||||||||||||||
| 2644 | C:\Users\admin\AppData\Local\Temp\DX6DA6.tmp\infinst.exe d3dx11_43_x64.inf | C:\Users\admin\AppData\Local\Temp\DX6DA6.tmp\infinst.exe | DXSETUP.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
Total events
16 454
Read events
15 972
Write events
448
Delete events
34
Modification events
| (PID) Process: | (1660) UE4PrereqSetup_x64.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000E4A8FBF339B8DB017C060000F0100000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1056) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000E4A8FBF339B8DB012004000080180000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1056) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000A7713EF439B8DB012004000080180000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1056) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000A7713EF439B8DB012004000080180000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1056) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 480000000000000047D540F439B8DB012004000080180000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1056) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000049D45F439B8DB012004000080180000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1056) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (1056) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 48000000000000000DC9BCF439B8DB012004000080180000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1056) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000009A2DBFF439B8DB0120040000A8020000E80300000100000000000000000000002DB2F63B1847F5408A19AAAB3F2CE00700000000000000000000000000000000 | |||
| (PID) Process: | (1188) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4800000000000000C09FD4F439B8DB01A404000064180000E80300000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
88
Suspicious files
129
Text files
78
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1056 | dllhost.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 4892 | UE4PrereqSetup_x64.exe | C:\Users\admin\AppData\Local\Temp\{0d995f46-317b-4b5f-bf3e-9f98bae9d339}\PrereqSetup | — | |
MD5:— | SHA256:— | |||
| 4892 | UE4PrereqSetup_x64.exe | C:\Users\admin\AppData\Local\Temp\{0d995f46-317b-4b5f-bf3e-9f98bae9d339}\.ba1\wixstdba.dll | executable | |
MD5:36B53C5299A3B39E5C9CDBBD28A09506 | SHA256:97F1901E7C928B9231E503CD3A1315F0D8449356B9F25E7EB4C2CEBEEE72012A | |||
| 4892 | UE4PrereqSetup_x64.exe | C:\Users\admin\AppData\Local\Temp\{0d995f46-317b-4b5f-bf3e-9f98bae9d339}\.ba1\logo.png | image | |
MD5:8346E21859A269DCCF1E408DC7593CCA | SHA256:CD2E8ED1FBB308D9D166F49794D323A9B22EFBA1033CDF906D1F4B030319E01B | |||
| 4892 | UE4PrereqSetup_x64.exe | C:\Users\admin\AppData\Local\Temp\{0d995f46-317b-4b5f-bf3e-9f98bae9d339}\.ba1\BootstrapperApplicationData.xml | xml | |
MD5:0F62A5FADF01C56B6E7DF5301E54EBD4 | SHA256:8493DF9FCBFFCF666777EFA7A94F59219F88E914324866FC5FD5F7C5B145D7A0 | |||
| 4892 | UE4PrereqSetup_x64.exe | C:\Users\admin\AppData\Local\Temp\{0d995f46-317b-4b5f-bf3e-9f98bae9d339}\.ba1\license.rtf | text | |
MD5:37EC54C5DA383498C2662742AF83F502 | SHA256:71BB04E77BFDAECA81AEBEF50B7862EACEB7A18816B3C6D7FB81AB1928E84AC7 | |||
| 1660 | UE4PrereqSetup_x64.exe | C:\ProgramData\Package Cache\.unverified\VC140_X86 | executable | |
MD5:24E8177B25C072F4FB0D37496CCDBB34 | SHA256:E59AE3E886BD4571A811FE31A47959AE5C40D87C583F786816C60440252CD7EC | |||
| 1660 | UE4PrereqSetup_x64.exe | C:\ProgramData\Package Cache\{0d995f46-317b-4b5f-bf3e-9f98bae9d339}\UE4PrereqSetup_x64.exe | executable | |
MD5:DDF7B1641565DA963C4B5FA54DA0C6FB | SHA256:62182DA08E543EDB383BE4CCCBA214E30F1DCD73395F461AF3A142A69893F254 | |||
| 1660 | UE4PrereqSetup_x64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:3B5E0BD6640456A749D9155E6C135727 | SHA256:C362A3D2B661C6066A02FC169FAAA1976C2F6160DA5837C7E68B7E0F67B794ED | |||
| 4892 | UE4PrereqSetup_x64.exe | C:\Users\admin\AppData\Local\Temp\{0d995f46-317b-4b5f-bf3e-9f98bae9d339}\vc140_X64 | executable | |
MD5:BE433764FA9BBE0F2F9C654F6512C9E0 | SHA256:40EA2955391C9EAE3E35619C4C24B5AAF3D17AEAA6D09424EE9672AA9372AEED | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
44
DNS requests
29
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.119:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.168.119:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7408 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1660 | UE4PrereqSetup_x64.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
1660 | UE4PrereqSetup_x64.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7408 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.119:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
— | — | 2.16.168.119:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |