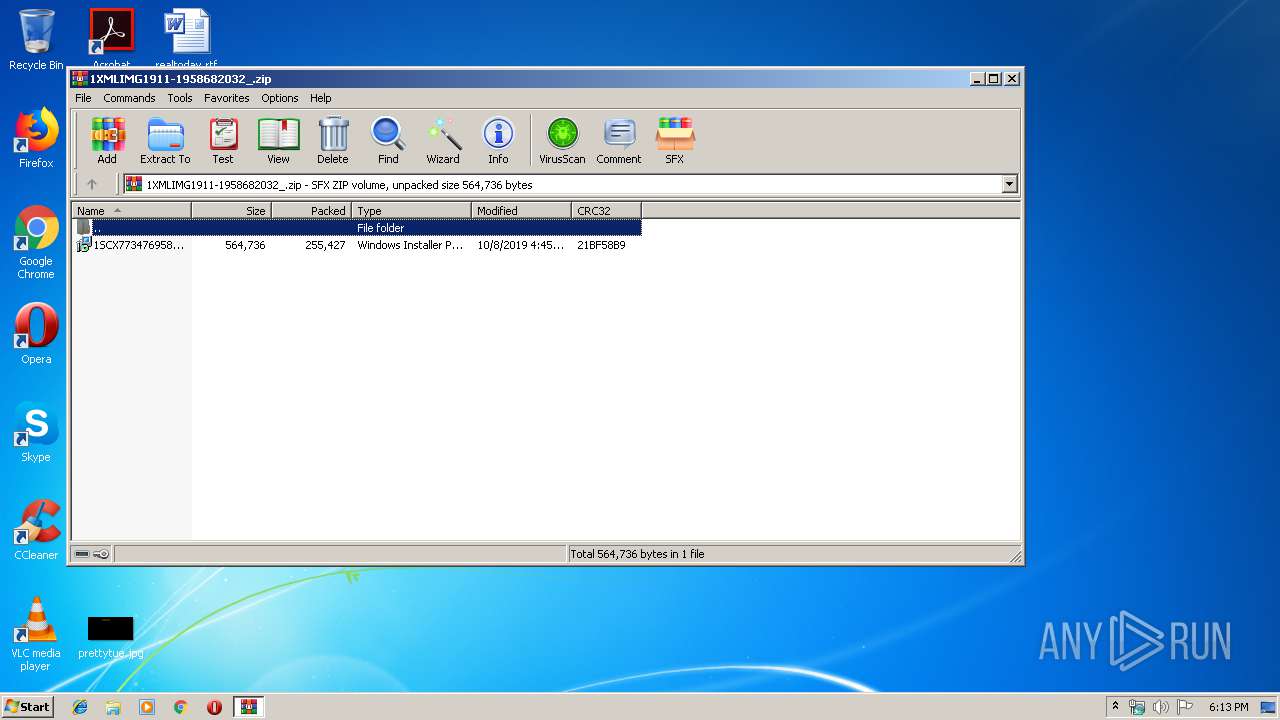
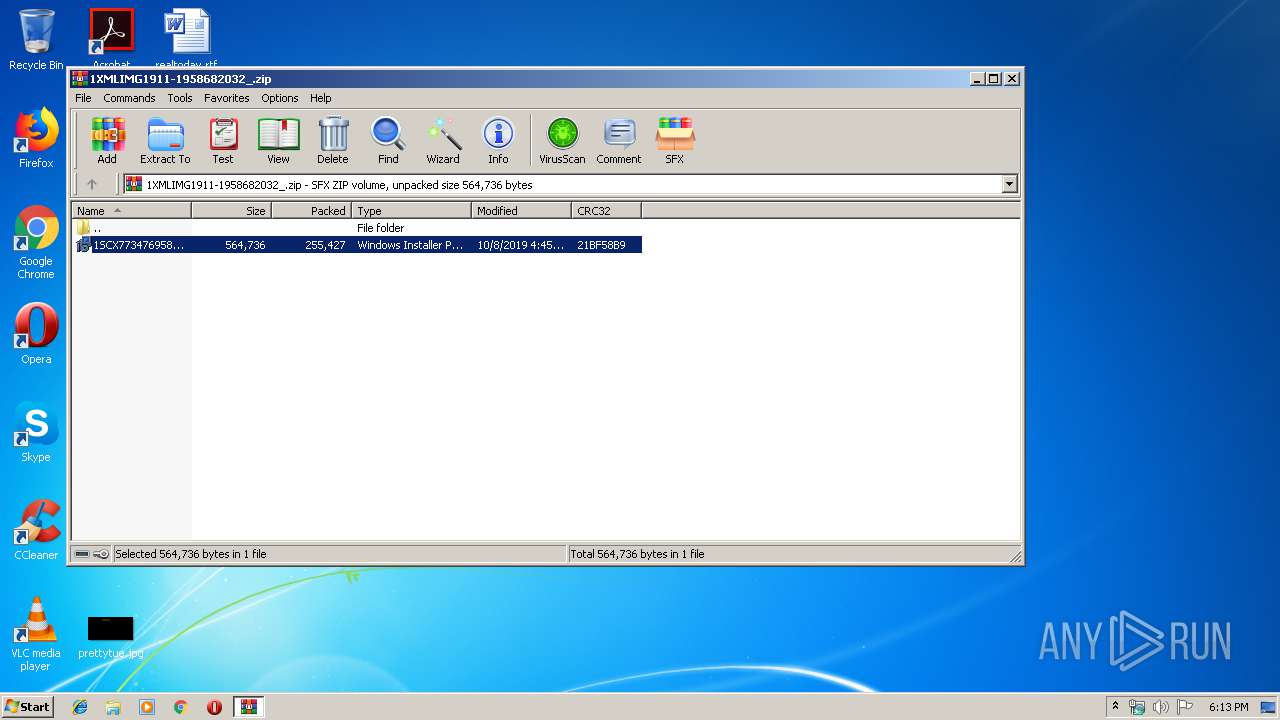
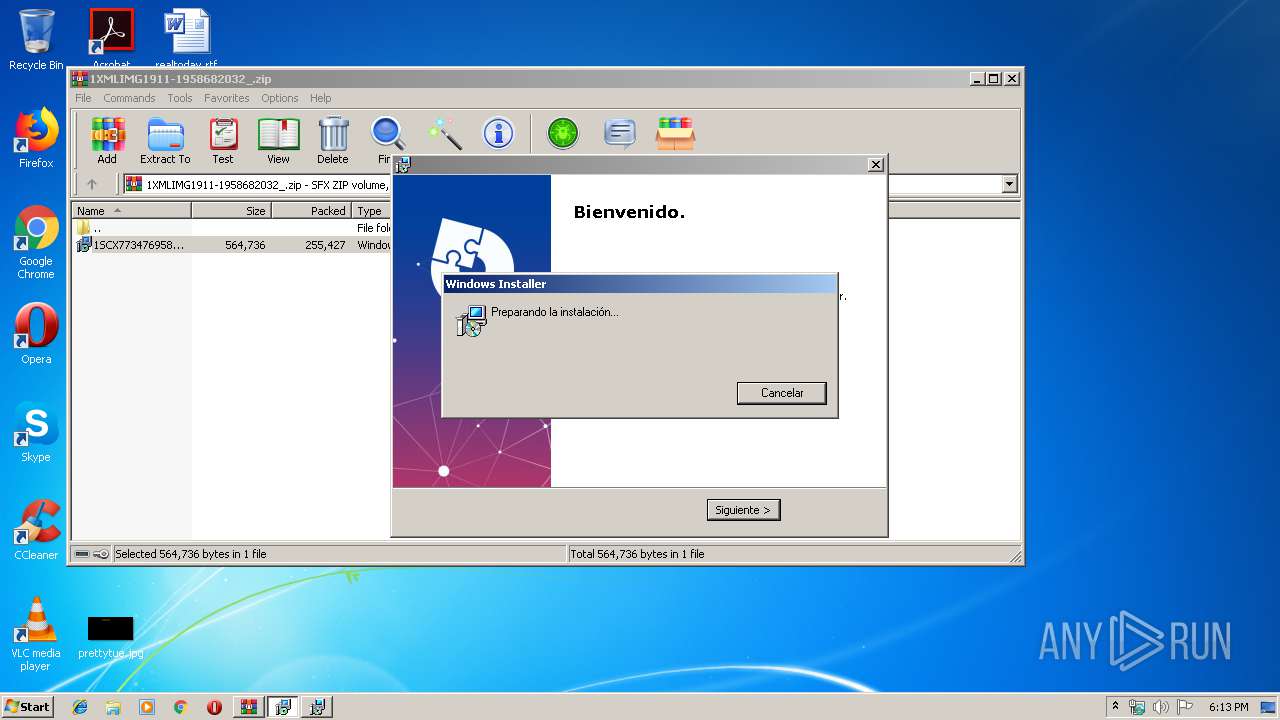
| File name: | 1XMLIMG1911-1958682032_.zip |
| Full analysis: | https://app.any.run/tasks/f9b1d0d6-e828-4df4-9c3f-bc03f2ff5ee4 |
| Verdict: | Malicious activity |
| Analysis date: | October 09, 2019, 17:13:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | data |
| MD5: | 155182584992C8E4F717CB64E08C7AC4 |
| SHA1: | BFF088121F847544885C709656083CB4F580A440 |
| SHA256: | C304D47F318FDE337BCB32B22A1938A544B0835169DDE182A40820666A01B169 |
| SSDEEP: | 6144:jOdsD1vjSQA6z87QbskebenZVSRqQPWcXFyr:IIvj/A6zFbTyYZYkazYr |
MALICIOUS
Changes settings of System certificates
- msiexec.exe (PID: 3468)
Writes to a start menu file
- MsiExec.exe (PID: 3056)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2912)
- msiexec.exe (PID: 3468)
- msiexec.exe (PID: 3260)
Starts Microsoft Installer
- WinRAR.exe (PID: 2912)
Executed as Windows Service
- vssvc.exe (PID: 3156)
Executed via COM
- DrvInst.exe (PID: 3364)
Creates files in the user directory
- MsiExec.exe (PID: 3056)
INFO
Application launched itself
- msiexec.exe (PID: 3260)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 2864)
- MsiExec.exe (PID: 2668)
- MsiExec.exe (PID: 3056)
Searches for installed software
- msiexec.exe (PID: 3260)
Low-level read access rights to disk partition
- vssvc.exe (PID: 3156)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
42
Monitored processes
9
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2668 | C:\Windows\system32\MsiExec.exe -Embedding 8168C7AD0F4DB7D1C47D1B42A385B2BA C | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2864 | C:\Windows\system32\MsiExec.exe -Embedding 74D0DC856EAAF8DFD79FD4BB19B1FC00 C | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
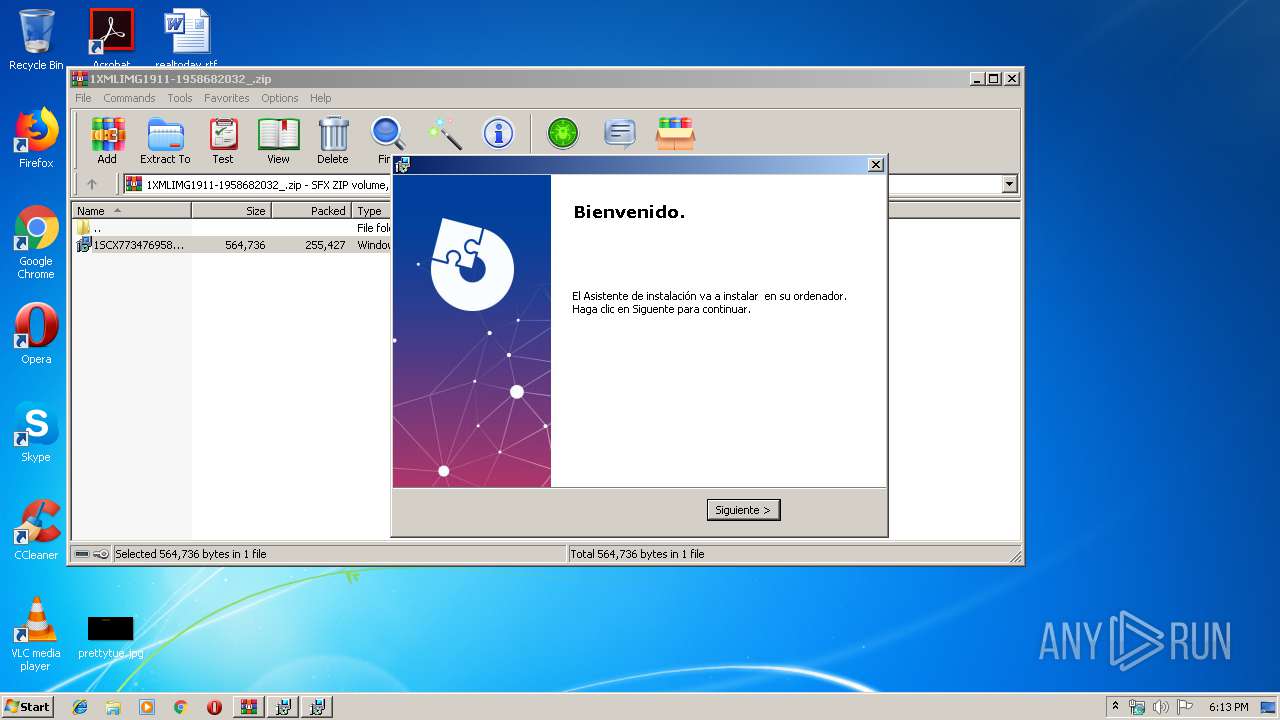
| 2912 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\1XMLIMG1911-1958682032_.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3056 | C:\Windows\system32\MsiExec.exe -Embedding 43530338BA8696290EE91D5C5F39F1C1 | C:\Windows\system32\MsiExec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3156 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3260 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3364 | DrvInst.exe "1" "200" "STORAGE\VolumeSnapshot\HarddiskVolumeSnapshot22" "" "" "695c3f483" "00000000" "00000390" "000005BC" | C:\Windows\system32\DrvInst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3468 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\Rar$EXa2912.23469\1SCX7734769589574545.msi" | C:\Windows\System32\msiexec.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3812 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\Rar$EXa2912.23546\1SCX7734769589574545.msi" | C:\Windows\System32\msiexec.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 295
Read events
1 097
Write events
198
Delete events
0
Modification events
| (PID) Process: | (2912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2912) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\1XMLIMG1911-1958682032_.zip | |||
| (PID) Process: | (2912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3468) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
5
Suspicious files
6
Text files
30
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3468 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIAF97.tmp | — | |
MD5:— | SHA256:— | |||
| 3468 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIAFB7.tmp | — | |
MD5:— | SHA256:— | |||
| 3468 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIB006.tmp | — | |
MD5:— | SHA256:— | |||
| 3812 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIB10D.tmp | — | |
MD5:— | SHA256:— | |||
| 3812 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIB18B.tmp | — | |
MD5:— | SHA256:— | |||
| 3812 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIB19C.tmp | — | |
MD5:— | SHA256:— | |||
| 3812 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIB1CC.tmp | — | |
MD5:— | SHA256:— | |||
| 3260 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3260 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF45F0438323D2D206.TMP | — | |
MD5:— | SHA256:— | |||
| 3156 | vssvc.exe | C: | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3468 | msiexec.exe | GET | 200 | 91.199.212.52:80 | http://crt.usertrust.com/USERTrustRSAAddTrustCA.crt | GB | der | 1.37 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3468 | msiexec.exe | 91.199.212.52:80 | crt.usertrust.com | Comodo CA Ltd | GB | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crt.usertrust.com |
| whitelisted |