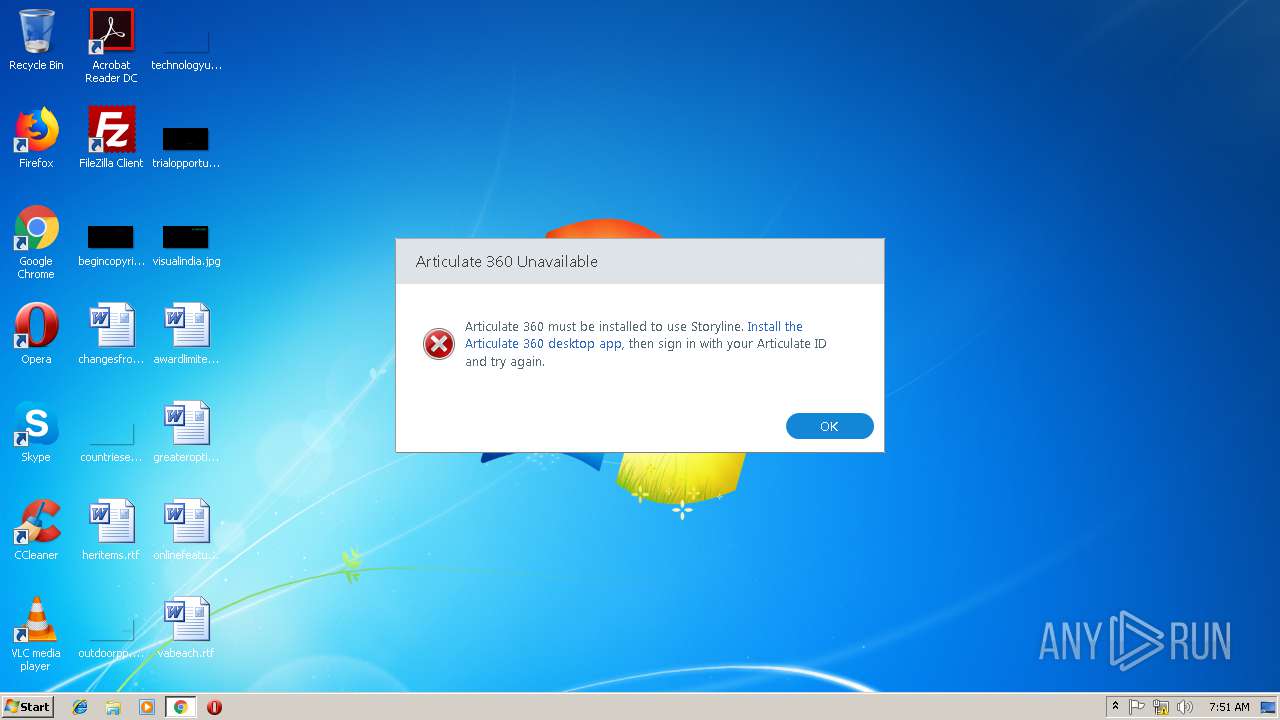
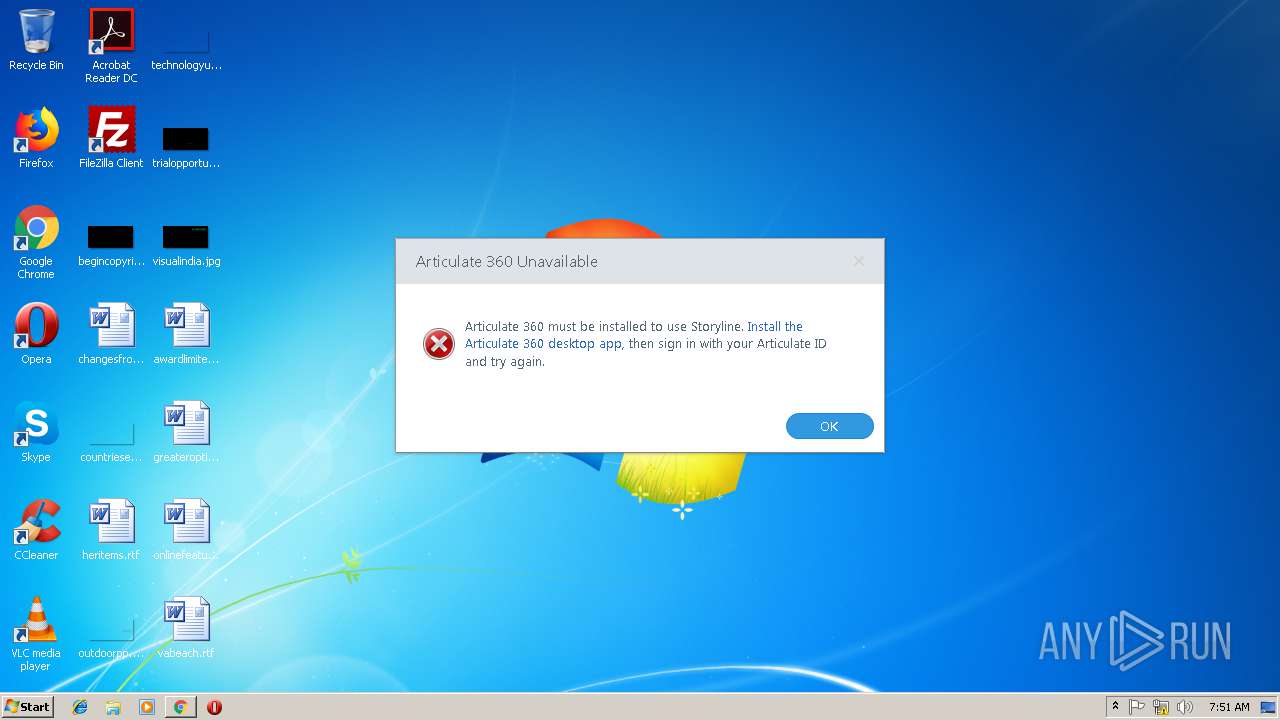
| URL: | https://cdn.articulate.com/products/uploads/oN3GCRdY_Jm0XTkO/storyline-stable-release-3-24-17733-0.exe |
| Full analysis: | https://app.any.run/tasks/aa7945e5-702a-43ab-9af5-ee8205280008 |
| Verdict: | Malicious activity |
| Analysis date: | January 23, 2019, 07:46:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 441E5B3C74C7B40323C9BD8361458E4D |
| SHA1: | 2A231E1E1CD40A92E32731480510FDC1B1197D9F |
| SHA256: | C2C73D194BEC8B28D638D55C1CDAC89EEFDBA98CD27F694360E9D38B83385D52 |
| SSDEEP: | 3:N8cWHkyCXaQGRWLzpB86vgXWX4Kpnx1OSRWNn:2c6FRWLzpB86YXWX4KpzOSg |
MALICIOUS
Loads dropped or rewritten executable
- storyline-stable-release-3-24-17733-0.exe (PID: 2916)
- csrss.exe (PID: 400)
- vc_redist.x86.exe (PID: 3300)
- Storyline.exe (PID: 3748)
- csrss.exe (PID: 344)
Application was dropped or rewritten from another process
- storyline-stable-release-3-24-17733-0.exe (PID: 2916)
- Articulate.Storyline.Bundle.exe (PID: 2748)
- Storyline.exe (PID: 3748)
- vc_redist.x86.exe (PID: 2132)
- vc_redist.x86.exe (PID: 3300)
Changes the autorun value in the registry
- vc_redist.x86.exe (PID: 2132)
- Articulate.Storyline.Bundle.exe (PID: 2748)
SUSPICIOUS
Executable content was dropped or overwritten
- storyline-stable-release-3-24-17733-0.exe (PID: 3912)
- storyline-stable-release-3-24-17733-0.exe (PID: 2916)
- Articulate.Storyline.Bundle.exe (PID: 2748)
- vc_redist.x86.exe (PID: 3300)
- msiexec.exe (PID: 3224)
Searches for installed software
- Articulate.Storyline.Bundle.exe (PID: 2748)
- vc_redist.x86.exe (PID: 2132)
Starts itself from another location
- storyline-stable-release-3-24-17733-0.exe (PID: 2916)
Creates files in the program directory
- Articulate.Storyline.Bundle.exe (PID: 2748)
- Storyline.exe (PID: 3748)
Creates a software uninstall entry
- Articulate.Storyline.Bundle.exe (PID: 2748)
- vc_redist.x86.exe (PID: 2132)
Creates files in the Windows directory
- msiexec.exe (PID: 3224)
Creates COM task schedule object
- msiexec.exe (PID: 3224)
Modifies the open verb of a shell class
- msiexec.exe (PID: 3224)
Reads Environment values
- Storyline.exe (PID: 3748)
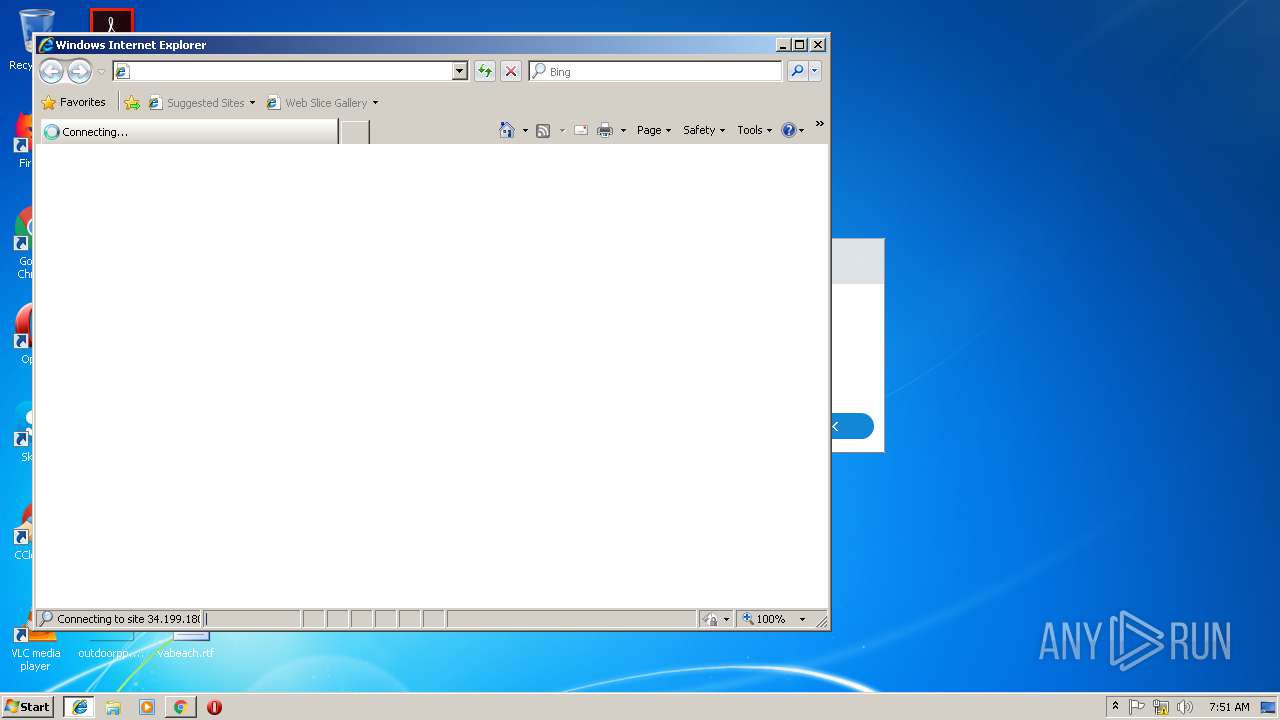
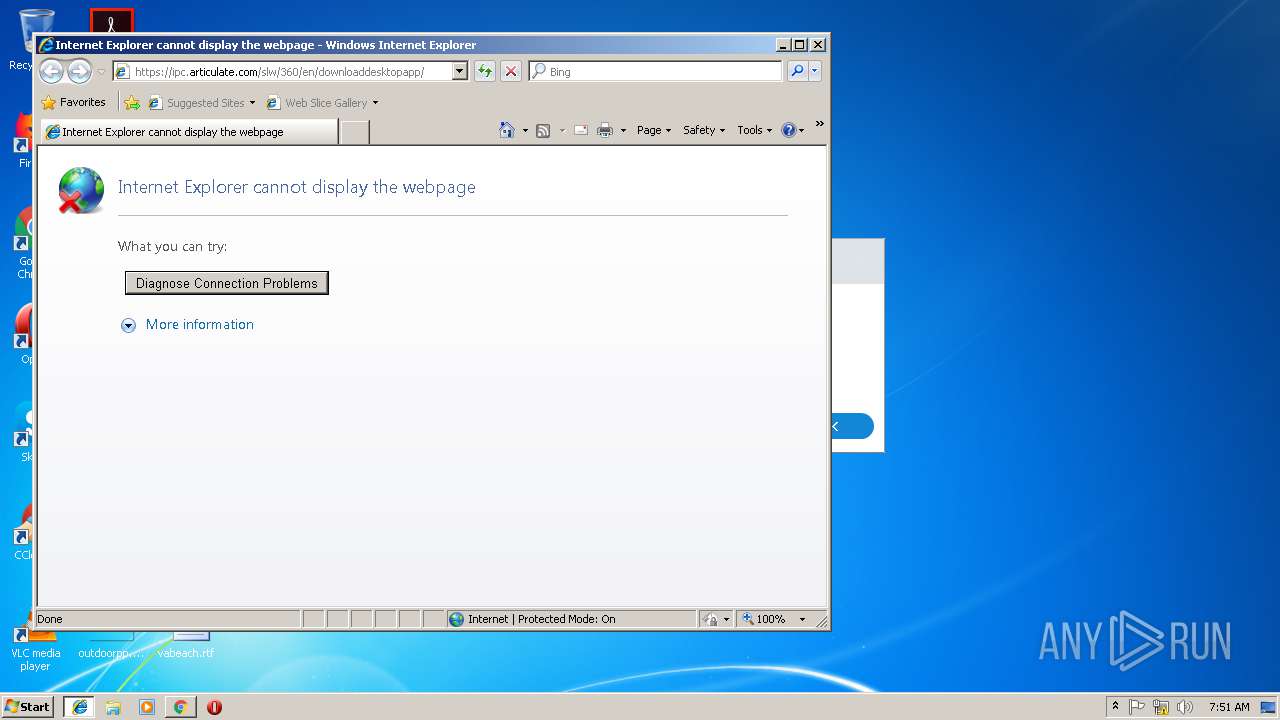
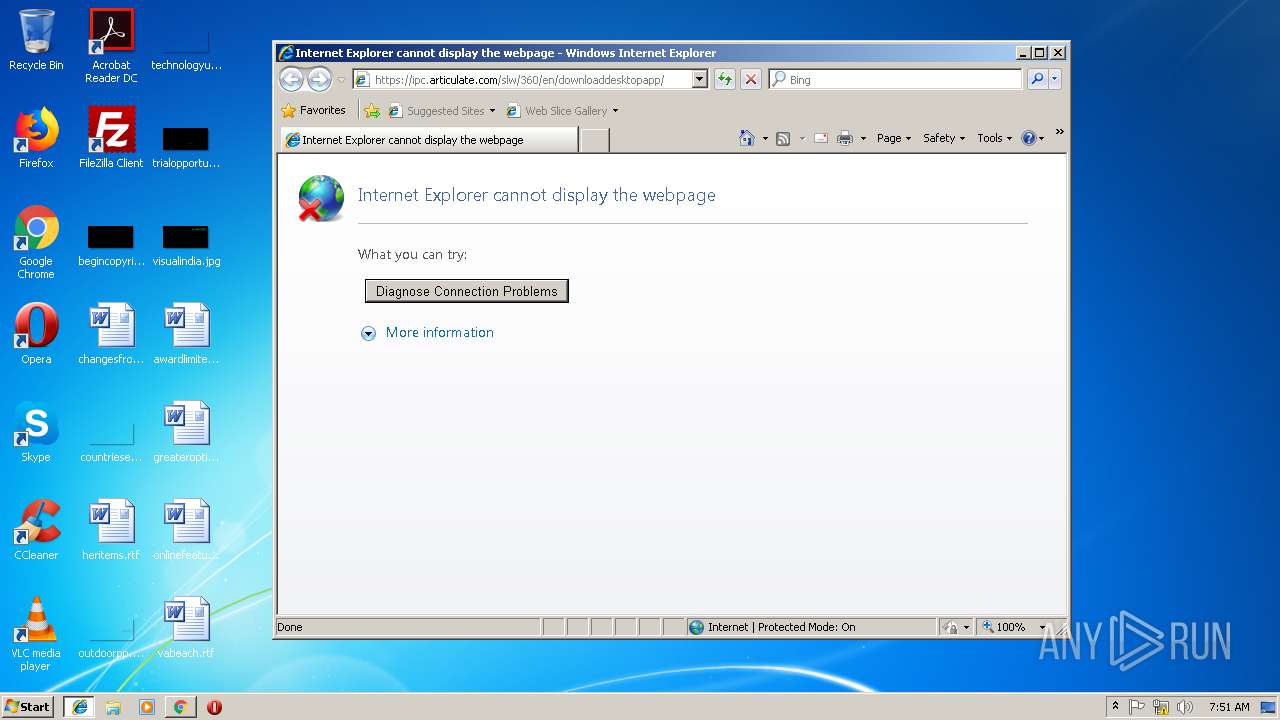
Starts Internet Explorer
- Storyline.exe (PID: 3748)
Creates files in the user directory
- Storyline.exe (PID: 3748)
Application launched itself
- vc_redist.x86.exe (PID: 2132)
INFO
Reads settings of System Certificates
- chrome.exe (PID: 3652)
- Storyline.exe (PID: 3748)
Application launched itself
- chrome.exe (PID: 3652)
- iexplore.exe (PID: 1656)
Reads Internet Cache Settings
- chrome.exe (PID: 3652)
- iexplore.exe (PID: 1740)
Changes settings of System certificates
- DrvInst.exe (PID: 2328)
Adds / modifies Windows certificates
- DrvInst.exe (PID: 2328)
Low-level read access rights to disk partition
- vssvc.exe (PID: 2152)
Creates a software uninstall entry
- msiexec.exe (PID: 3224)
Dropped object may contain Bitcoin addresses
- msiexec.exe (PID: 3224)
Changes internet zones settings
- iexplore.exe (PID: 1656)
Reads internet explorer settings
- iexplore.exe (PID: 1740)
Creates files in the program directory
- msiexec.exe (PID: 3224)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
59
Monitored processes
24
Malicious processes
9
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=944,242606157672125368,8062065844879851193,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=E71961EDDA9308F393280807069FE95F --mojo-platform-channel-handle=796 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 344 | %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,12288,512 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 | C:\Windows\System32\csrss.exe | — | — | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Client Server Runtime Process Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 400 | %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,12288,512 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 | C:\Windows\System32\csrss.exe | — | — | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Client Server Runtime Process Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1656 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | Storyline.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1728 | DrvInst.exe "1" "200" "STORAGE\VolumeSnapshot\HarddiskVolumeSnapshot19" "" "" "61530dda3" "00000000" "00000390" "000005C4" | C:\Windows\system32\DrvInst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1740 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1656 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2132 | "C:\ProgramData\Package Cache\0164F835D549FF03296DD615CF13CEFC042CC495\vc_redist.x86.exe" /quiet /norestart | C:\ProgramData\Package Cache\0164F835D549FF03296DD615CF13CEFC042CC495\vc_redist.x86.exe | Articulate.Storyline.Bundle.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2017 Redistributable (x86) - 14.15.26706 Exit code: 0 Version: 14.15.26706.0 Modules
| |||||||||||||||
| 2152 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2160 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=944,242606157672125368,8062065844879851193,131072 --enable-features=PasswordImport --service-pipe-token=17B6551D34E6DD072F91D6ADBA1871ED --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17B6551D34E6DD072F91D6ADBA1871ED --renderer-client-id=3 --mojo-platform-channel-handle=2144 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2328 | DrvInst.exe "1" "200" "STORAGE\VolumeSnapshot\HarddiskVolumeSnapshot18" "" "" "6792c44eb" "00000000" "000005BC" "00000390" | C:\Windows\system32\DrvInst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
4 250
Read events
2 176
Write events
2 042
Delete events
32
Modification events
| (PID) Process: | (3652) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3652) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3652) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3604) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 3652-13192703200266750 |
Value: 259 | |||
| (PID) Process: | (3652) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3652) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3652) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3516-13180984670829101 |
Value: 0 | |||
| (PID) Process: | (3652) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3652) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3652-13192703200266750 |
Value: 259 | |||
| (PID) Process: | (3652) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
287
Suspicious files
139
Text files
745
Unknown types
243
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3652 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\1f26b8eb-87d5-4a32-b245-296b04b7c2a1.tmp | — | |
MD5:— | SHA256:— | |||
| 3652 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3652 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3652 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\CURRENT | — | |
MD5:— | SHA256:— | |||
| 3652 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\CURRENT | — | |
MD5:— | SHA256:— | |||
| 3652 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\CURRENT~RF198d90.TMP | — | |
MD5:— | SHA256:— | |||
| 3652 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\d1f09d95-e09a-4e48-b0ca-069bc53c1e54.tmp | — | |
MD5:— | SHA256:— | |||
| 3652 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF198ce4.TMP | text | |
MD5:— | SHA256:— | |||
| 3652 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Translate Ranker Model~RF199149.TMP | binary | |
MD5:— | SHA256:— | |||
| 3652 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Translate Ranker Model | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
18
DNS requests
11
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3652 | chrome.exe | GET | 200 | 205.185.216.10:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 55.2 Kb | whitelisted |
3652 | chrome.exe | GET | 200 | 52.85.188.155:80 | http://x.ss2.us/x.cer | US | der | 1.27 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3652 | chrome.exe | 172.217.16.195:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3652 | chrome.exe | 172.217.23.163:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3652 | chrome.exe | 54.230.93.15:443 | cdn.articulate.com | Amazon.com, Inc. | US | malicious |
3652 | chrome.exe | 205.185.216.10:80 | www.download.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
3652 | chrome.exe | 172.217.22.46:443 | clients4.google.com | Google Inc. | US | whitelisted |
3652 | chrome.exe | 172.217.22.78:443 | clients1.google.com | Google Inc. | US | whitelisted |
3652 | chrome.exe | 172.217.22.42:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
3652 | chrome.exe | 216.58.205.238:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
3748 | Storyline.exe | 54.230.93.203:443 | — | Amazon.com, Inc. | US | unknown |
1740 | iexplore.exe | 34.199.180.87:443 | — | Amazon.com, Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
cdn.articulate.com |
| whitelisted |
x.ss2.us |
| whitelisted |
www.download.windowsupdate.com |
| whitelisted |
accounts.google.com |
| shared |
ssl.gstatic.com |
| whitelisted |
clients4.google.com |
| whitelisted |
clients1.google.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
Threats
Process | Message |
|---|---|
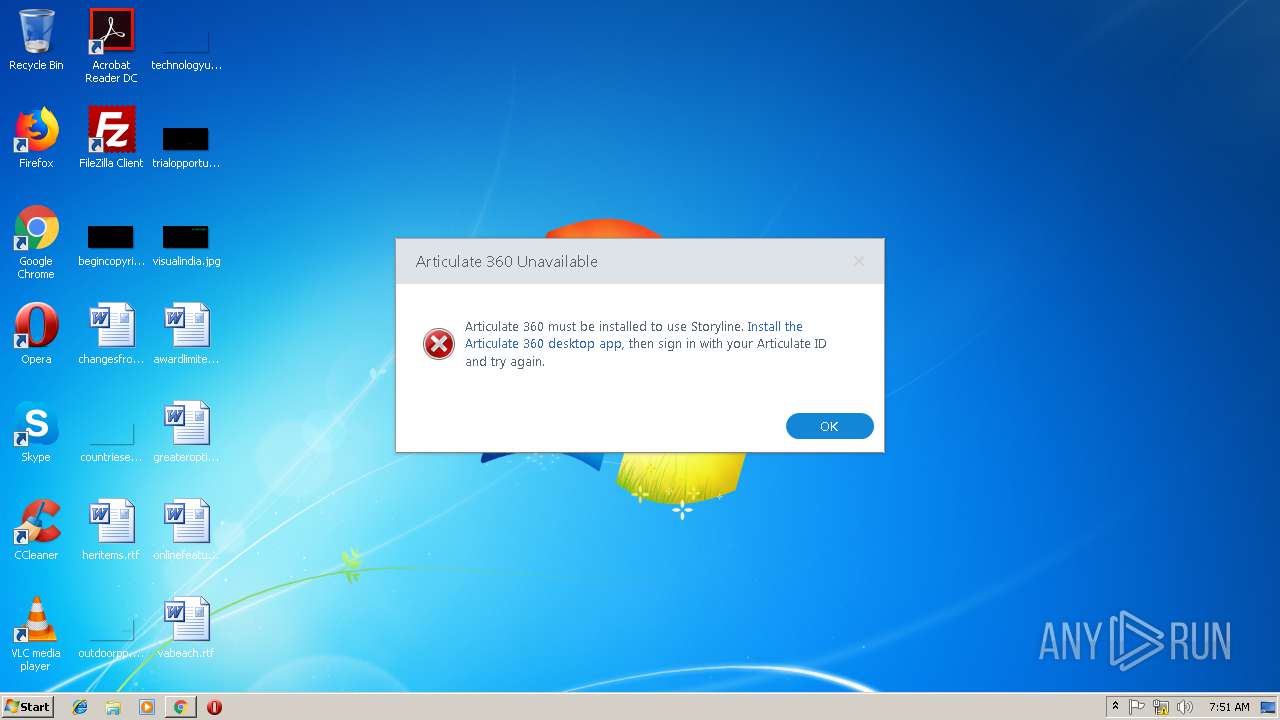
Storyline.exe | ThreeSixtyRemoting Error: 0 : |
Storyline.exe | [2019-01-23T07:51:18.0245625+00:00][00000ea4:00000e78:00000001] ServiceProcess.IsAlive the service process is not currently running
|
Storyline.exe | ThreeSixtyRemoting Error: 0 : |
Storyline.exe | [2019-01-23T07:51:18.0245625+00:00][00000ea4:00000e78:00000001] ServiceProcess.IsAlive the service process is not currently running
|
Storyline.exe | ThreeSixtyRemoting Error: 0 : |
Storyline.exe | [2019-01-23T07:51:18.0245625+00:00][00000ea4:00000e78:00000001] ServiceProcess.IsAlive the service process is not currently running
|
Storyline.exe | ThreeSixtyRemoting Error: 0 : |
Storyline.exe | [2019-01-23T07:51:18.0245625+00:00][00000ea4:00000e78:00000001] ServiceProcess.IsAlive the service process is not currently running
|
Storyline.exe | [2019-01-23T07:51:18.0401875+00:00][00000ea4:00000e78:00000001] ServiceProcess.Start() unable to find the service process on the user's system
|
Storyline.exe | [2019-01-23T07:51:18.0401875+00:00][00000ea4:00000e78:00000001] ServiceProcess.Start() unable to find the service process on the user's system
|