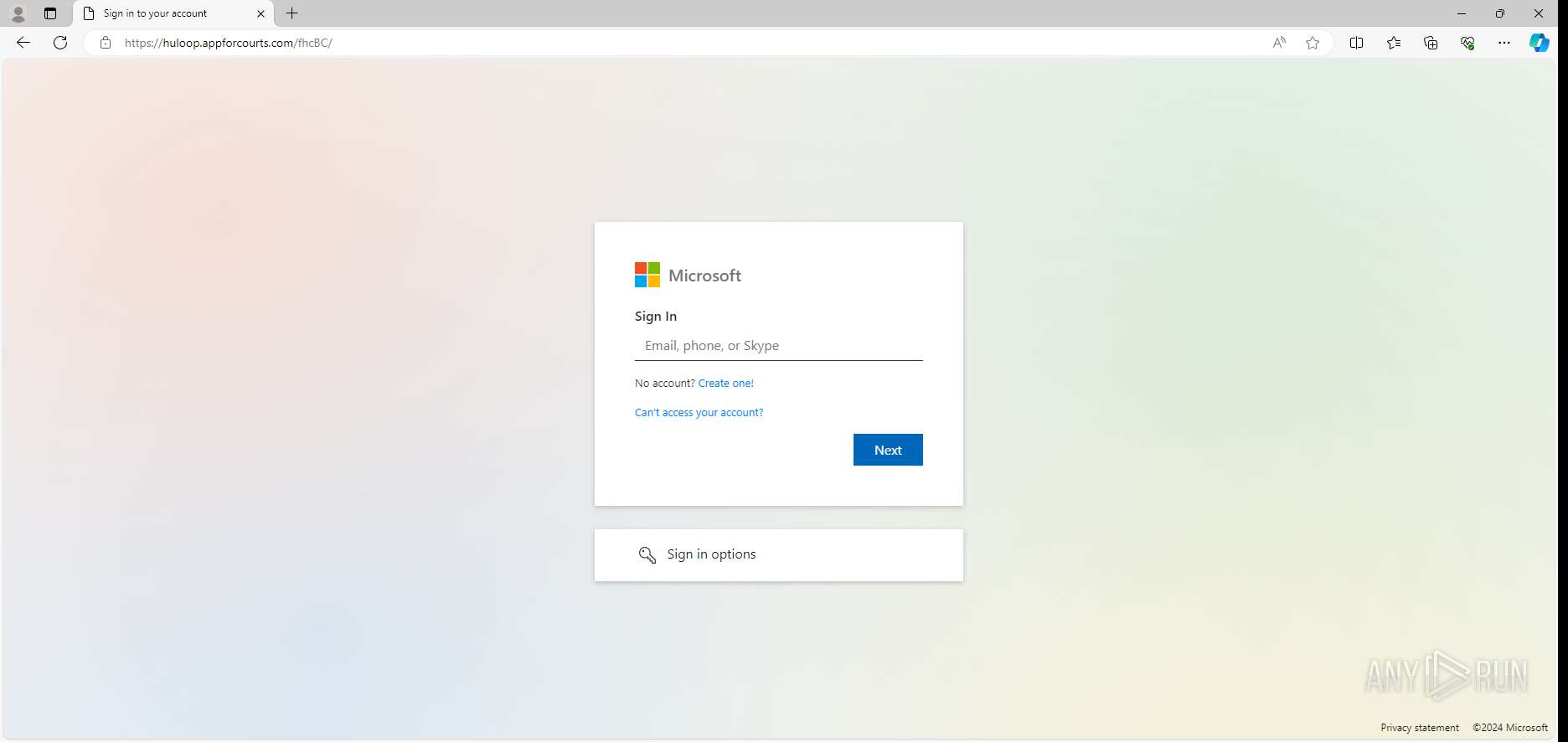
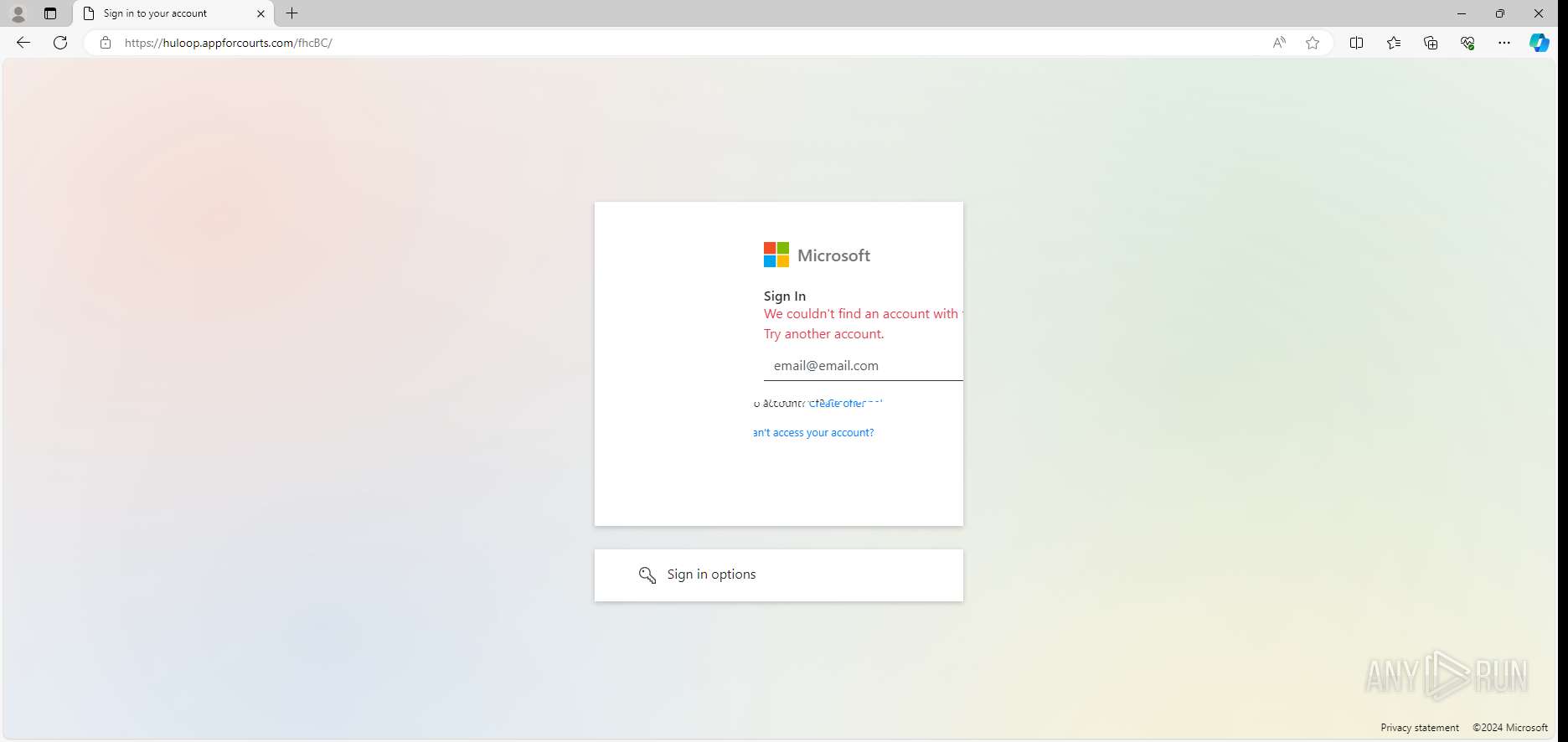
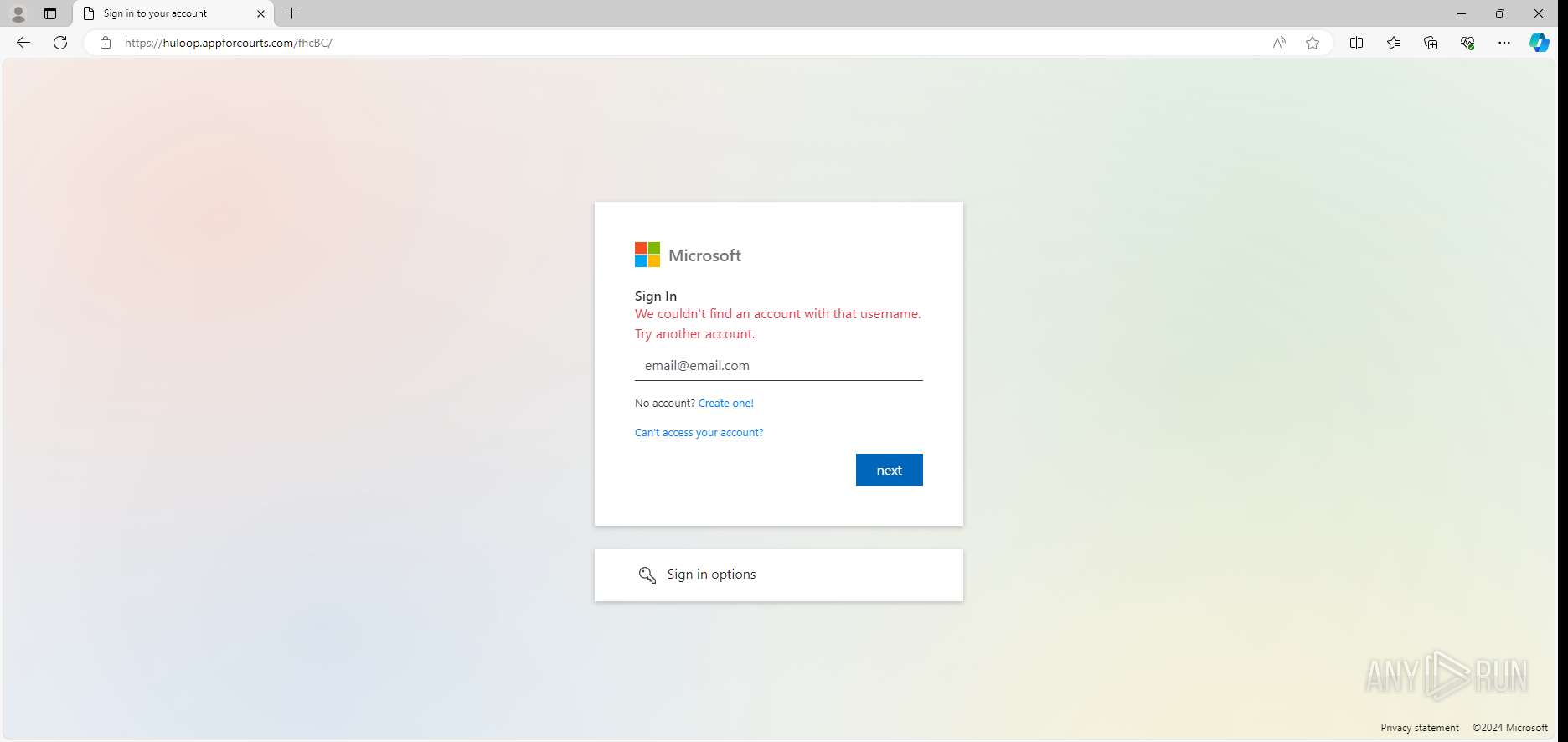
| URL: | huloop.appforcourts.com/fhcBC |
| Full analysis: | https://app.any.run/tasks/5328baf9-35f5-4abb-80cd-66cd6120de31 |
| Verdict: | Malicious activity |
| Analysis date: | December 13, 2024, 19:09:27 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 283938753DCEF98DEFCD9F075B4C019D |
| SHA1: | 207AA2235C77E4E9D187B00B399392EB8B147933 |
| SHA256: | C2B4259145932B59F73D61289290C19CEB3B9F668E3FB84350B377C3E10CC1A4 |
| SSDEEP: | 3:0NNCwtDZ:0NNCwf |
MALICIOUS
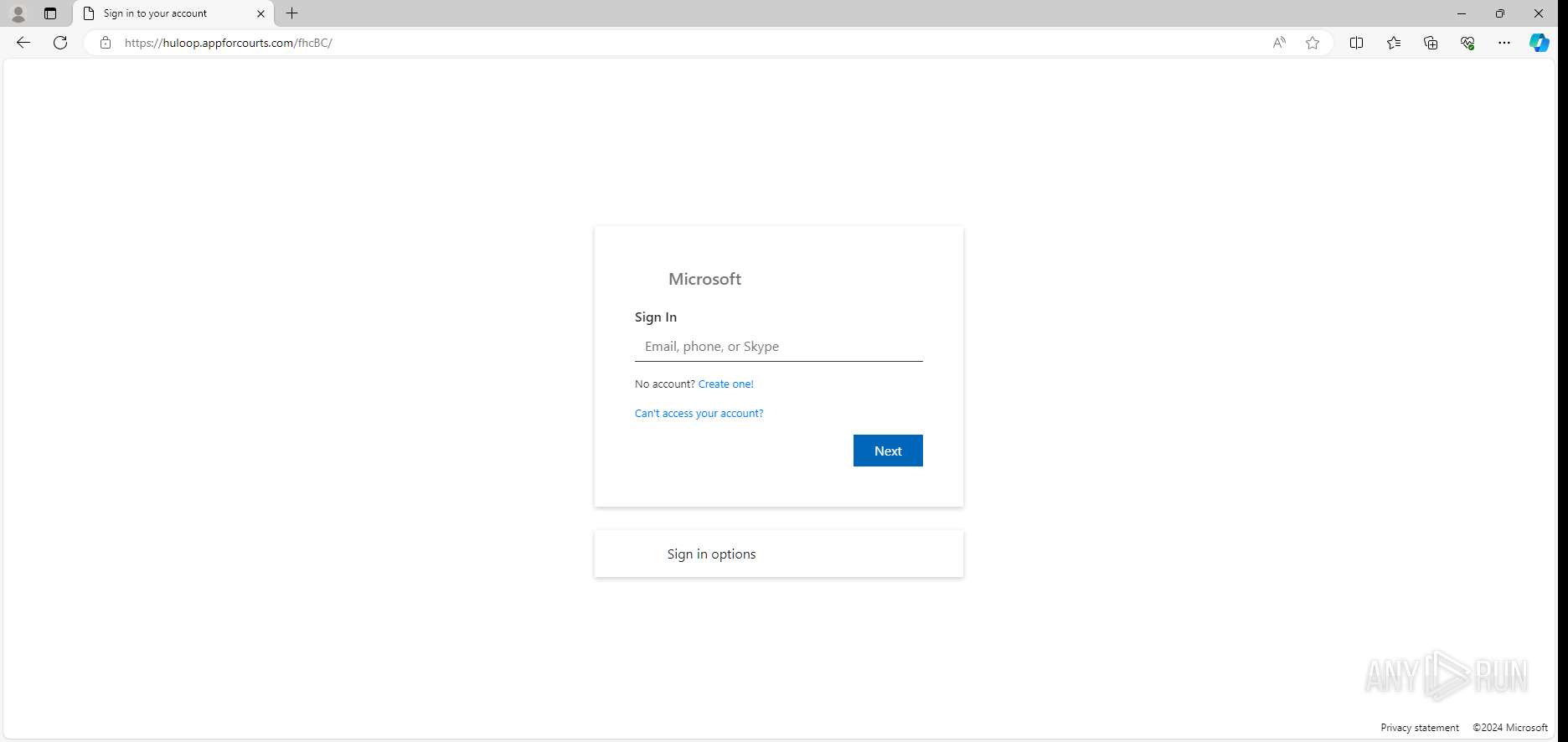
PHISHING has been detected (SURICATA)
- msedge.exe (PID: 4792)
SUSPICIOUS
No suspicious indicators.INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
137
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 4792 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2604 --field-trial-handle=2320,i,16194277592197507296,15814343983252007256,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
19
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\TransportSecurity~RF2b6ce1.TMP | binary | |
MD5:15D26FA4E16467BE658F42074AC0DBAA | SHA256:D287407BD901A32E3F38F4392984507184D596C3694FAA69DD0B2E68F9F3A8FE | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000bc | compressed | |
MD5:373C5BFDE8DAB5190258BA2BB62C1D12 | SHA256:C28013B8A76E02E213229DA7DE13EF50AF6EC6A40237D908BAEB12F4A00A084C | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000bf | image | |
MD5:12E3DAC858061D088023B2BD48E2FA96 | SHA256:90CDAF487716184E4034000935C605D1633926D348116D198F355A98B8C6CD21 | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\Network Persistent State~RF2c45dc.TMP | binary | |
MD5:2A21453795942FD88CBB06714604B9FD | SHA256:5DFE0384325B556EE4B8668E502312B9BA6ADC298CD9213DDFA528CB959ADC06 | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\Network Persistent State~RF2caca5.TMP | binary | |
MD5:4BDD6EC8322AD6C84F2FEBD549695BB5 | SHA256:281406907D68AE0CE2DA575014C93291D49F32AA498C2D53EF8849216F997D48 | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000bd | compressed | |
MD5:6D973C8B7E2439D958E09C0A1AB9FE50 | SHA256:F3C122DC227E829ED96B2A754296809201BD78ABBAD7BA50EF5079654E1CC894 | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000be | text | |
MD5:93F195E6C49B265A0BAE1165289061EE | SHA256:8ABA1FBE793D3AD01DCCD898B051F55FA26898AAC4F9C10EC04048863D20B502 | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\2602c28d-ecb4-497a-afc8-55a3fd9be366.tmp | binary | |
MD5:4BDD6EC8322AD6C84F2FEBD549695BB5 | SHA256:281406907D68AE0CE2DA575014C93291D49F32AA498C2D53EF8849216F997D48 | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\Network Persistent State~RF2e0a8f.TMP | binary | |
MD5:FE5426D09D45B32473017C7004A8E0B9 | SHA256:F3F5B9F19D8F5C3705532F8CEC5433604AFD5A7D472478EAC518236E9BD2BFAA | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\fadc028f-05d2-4f07-afa0-b2310e5a35a7.tmp | binary | |
MD5:8EE4B6AAA45E5E7C92C18BF0E419CA46 | SHA256:2E904934AB5991C1ABF52D09652631DB276CD8E84584099A3DA9702F337B66AF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
34
TCP/UDP connections
77
DNS requests
69
Threats
53
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4304 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | OPTIONS | 200 | 35.190.80.1:443 | https://a.nel.cloudflare.com/report/v4?s=8xGJGNJiDyT65EcE2omwlRxjJllPSEappZKh%2FYCEnbKJ2hEgR0fXthXzGlT07ADfOrqB%2FZbShoJGyey1%2FgW92GnOOaHJxjK7V%2BHJMT4uxyzvUp0q8hkwTpLLHbyTaLVKFh7tIOdPyewO%2BA%3D%3D | unknown | — | — | — |
— | — | GET | 302 | 104.18.94.41:443 | https://challenges.cloudflare.com/turnstile/v0/api.js | unknown | — | — | — |
— | — | HEAD | 200 | 23.218.208.109:443 | https://fs.microsoft.com/fs/windows/config.json | unknown | — | — | — |
6984 | svchost.exe | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5896 | RUXIMICS.exe | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6984 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4304 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 104.21.53.141:443 | https://huloop.appforcourts.com/fhcBC/ | unknown | html | 2.63 Kb | — |
— | — | GET | 200 | 142.250.185.206:443 | https://ajax.googleapis.com/ajax/libs/jquery/2.2.4/jquery.min.js | unknown | s | 83.5 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6984 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5896 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4304 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4792 | msedge.exe | 52.182.141.63:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 224.0.0.251:5353 | — | — | — | unknown |
4792 | msedge.exe | 104.21.53.141:443 | huloop.appforcourts.com | CLOUDFLARENET | — | unknown |
5988 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5348 | svchost.exe | 23.218.208.109:443 | fs.microsoft.com | AKAMAI-AS | DE | whitelisted |
4792 | msedge.exe | 104.18.95.41:443 | challenges.cloudflare.com | CLOUDFLARENET | — | whitelisted |
4792 | msedge.exe | 104.126.37.178:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
huloop.appforcourts.com |
| unknown |
fs.microsoft.com |
| whitelisted |
challenges.cloudflare.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
xpaywalletcdn.azureedge.net |
| whitelisted |
a.nel.cloudflare.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] BootstrapCDN (stackpath .bootstrapcdn .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] BootstrapCDN (maxcdn .bootstrapcdn .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] BootstrapCDN (maxcdn .bootstrapcdn .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |