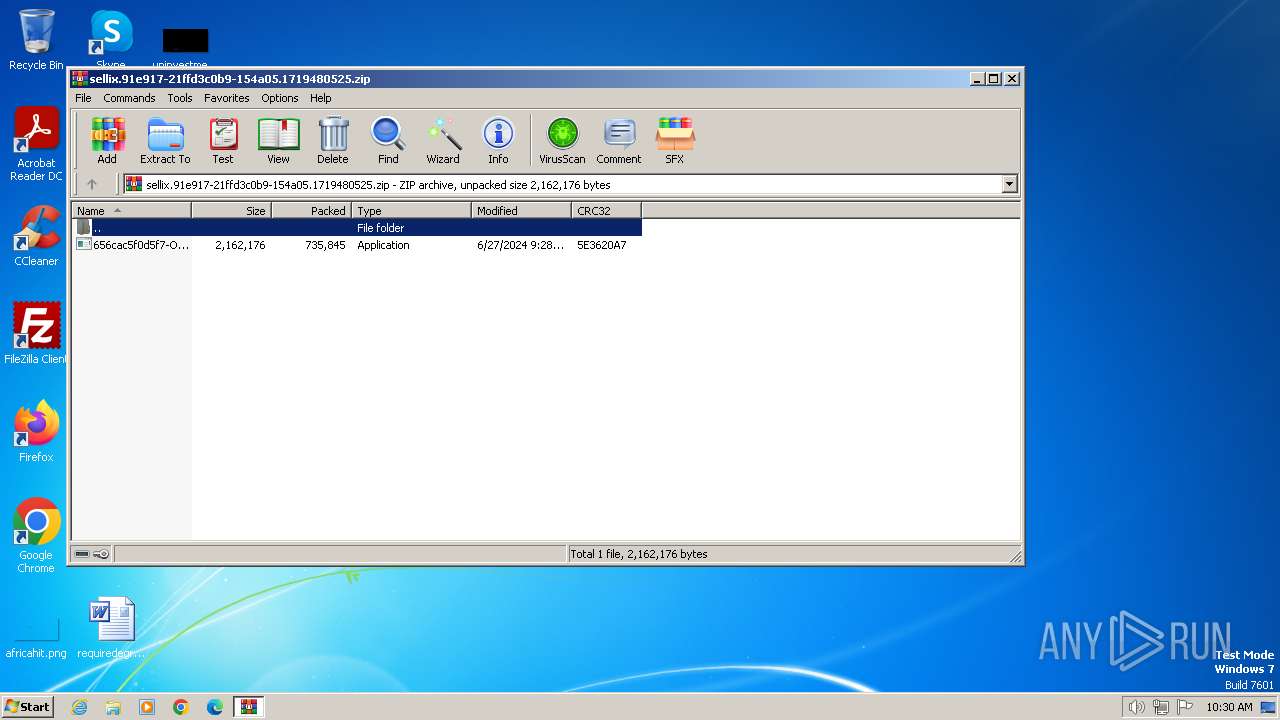
| File name: | sellix.91e917-21ffd3c0b9-154a05.1719480525.zip |
| Full analysis: | https://app.any.run/tasks/f954b8fc-14e1-4237-abb7-6467e622a936 |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2024, 09:29:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | D152EE717C306C1075863E04A8F3BD18 |
| SHA1: | 3CE6D8F47F7A8DF7337AB44FBE8B2D537AC71F00 |
| SHA256: | C2ADD7BA8B784F6190670A82DF2AF5C2479EA4F7642C6B1C2E3ED9343FB6CAD9 |
| SSDEEP: | 24576:hmbrUg3N6fQjwfsuUL1/unIkhfev58cVWlvkn8xaS4aq1k7+vSjJVNJjEQCo10OW:hmbrUg3N6fQjw0uUL1/uIkhfev58cVWY |
MALICIOUS
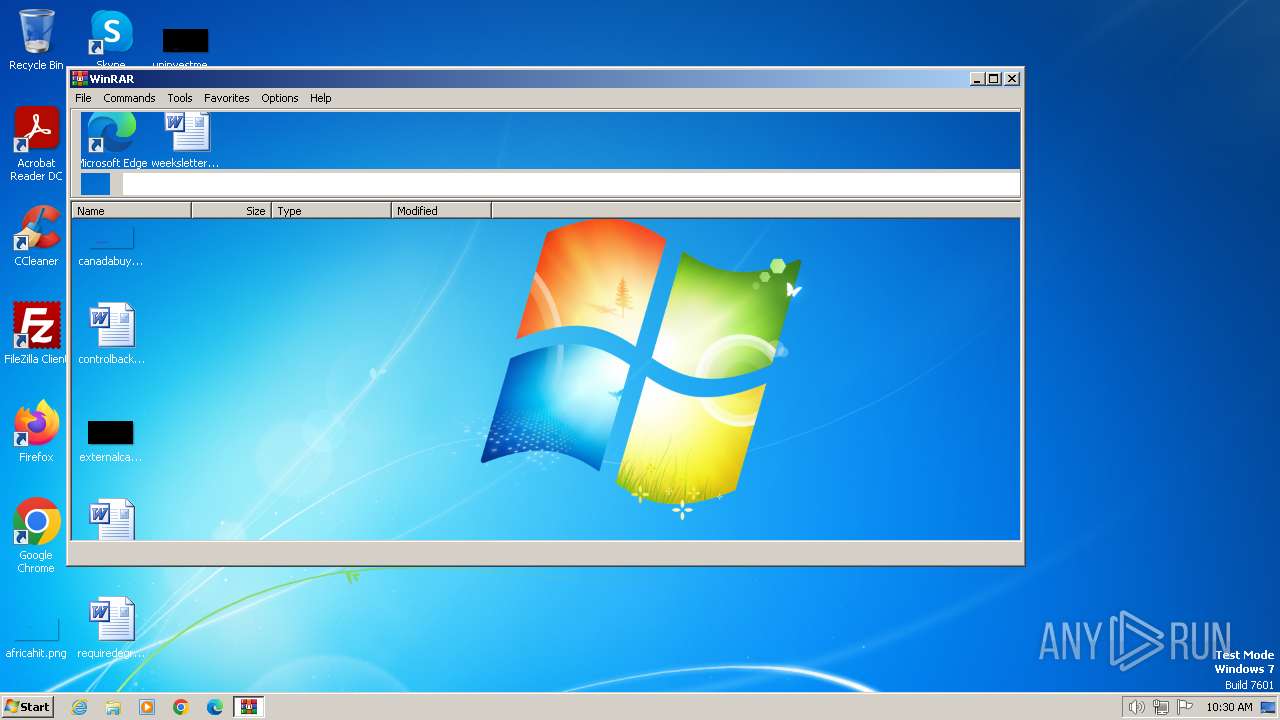
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3332)
SUSPICIOUS
Reads the Internet Settings
- 656cac5f0d5f7-Optimizer-14.6.exe.exe (PID: 3208)
- 656cac5f0d5f7-Optimizer-14.6.exe.exe (PID: 3176)
Reads security settings of Internet Explorer
- 656cac5f0d5f7-Optimizer-14.6.exe.exe (PID: 3208)
Application launched itself
- 656cac5f0d5f7-Optimizer-14.6.exe.exe (PID: 3208)
Reads settings of System Certificates
- 656cac5f0d5f7-Optimizer-14.6.exe.exe (PID: 3176)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3332)
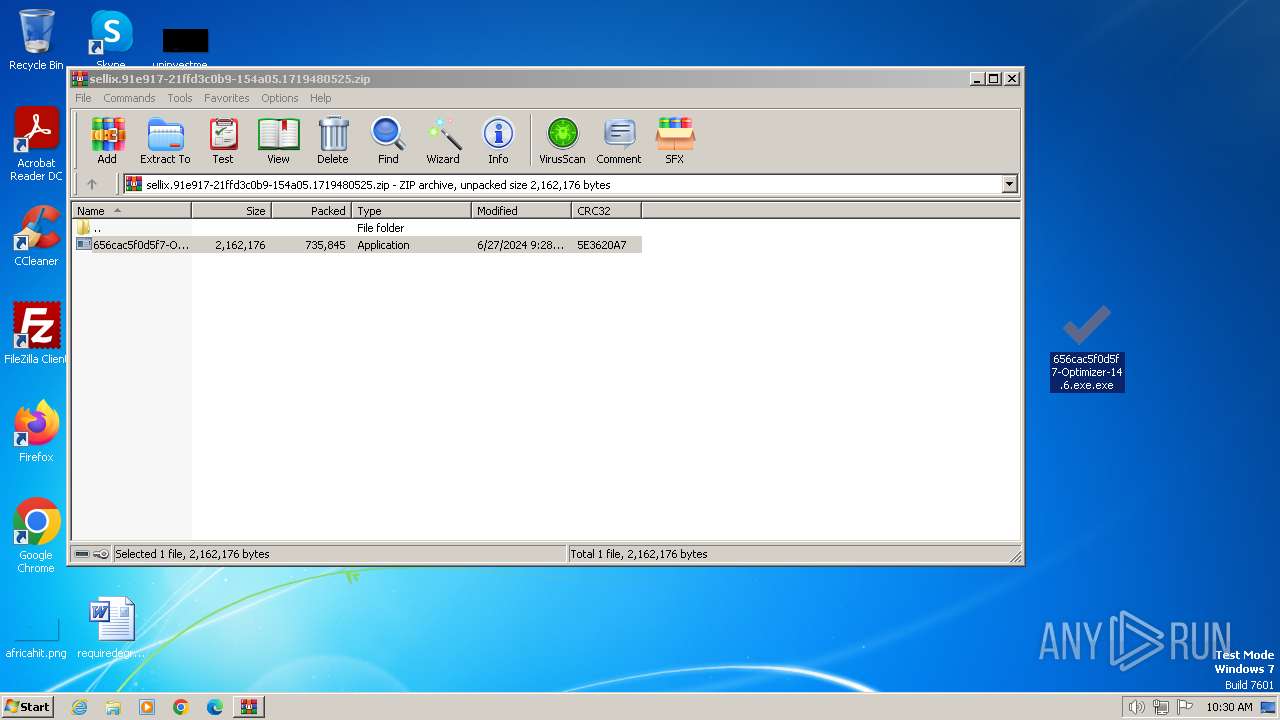
Manual execution by a user
- 656cac5f0d5f7-Optimizer-14.6.exe.exe (PID: 3208)
Reads the computer name
- 656cac5f0d5f7-Optimizer-14.6.exe.exe (PID: 3208)
- 656cac5f0d5f7-Optimizer-14.6.exe.exe (PID: 3176)
Checks supported languages
- 656cac5f0d5f7-Optimizer-14.6.exe.exe (PID: 3208)
- 656cac5f0d5f7-Optimizer-14.6.exe.exe (PID: 3176)
Reads the machine GUID from the registry
- 656cac5f0d5f7-Optimizer-14.6.exe.exe (PID: 3176)
- 656cac5f0d5f7-Optimizer-14.6.exe.exe (PID: 3208)
Reads Environment values
- 656cac5f0d5f7-Optimizer-14.6.exe.exe (PID: 3176)
Creates files in the program directory
- 656cac5f0d5f7-Optimizer-14.6.exe.exe (PID: 3176)
Reads product name
- 656cac5f0d5f7-Optimizer-14.6.exe.exe (PID: 3176)
Disables trace logs
- 656cac5f0d5f7-Optimizer-14.6.exe.exe (PID: 3176)
Reads the software policy settings
- 656cac5f0d5f7-Optimizer-14.6.exe.exe (PID: 3176)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:06:27 09:28:44 |
| ZipCRC: | 0x5e3620a7 |
| ZipCompressedSize: | 735845 |
| ZipUncompressedSize: | 2162176 |
| ZipFileName: | 656cac5f0d5f7-Optimizer-14.6.exe.exe |
Total processes
44
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3176 | "C:\Users\admin\Desktop\656cac5f0d5f7-Optimizer-14.6.exe.exe" | C:\Users\admin\Desktop\656cac5f0d5f7-Optimizer-14.6.exe.exe | 656cac5f0d5f7-Optimizer-14.6.exe.exe | ||||||||||||
User: admin Company: deadmoon © 2022 Integrity Level: HIGH Description: Optimizer Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 3208 | "C:\Users\admin\Desktop\656cac5f0d5f7-Optimizer-14.6.exe.exe" | C:\Users\admin\Desktop\656cac5f0d5f7-Optimizer-14.6.exe.exe | — | explorer.exe | |||||||||||
User: admin Company: deadmoon © 2022 Integrity Level: MEDIUM Description: Optimizer Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 3332 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\sellix.91e917-21ffd3c0b9-154a05.1719480525.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
10 689
Read events
10 633
Write events
56
Delete events
0
Modification events
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\sellix.91e917-21ffd3c0b9-154a05.1719480525.zip | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
1
Suspicious files
2
Text files
19
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3332.41531\656cac5f0d5f7-Optimizer-14.6.exe.exe | executable | |
MD5:4C9BBC9D4310645ACF7DAD53BCB77A42 | SHA256:38717DE36E9705D8B95EFE7D752982134BF8CCC398BF7369F205FA9329E0276B | |||
| 3176 | 656cac5f0d5f7-Optimizer-14.6.exe.exe | C:\ProgramData\Optimizer\ReadyMadeMenus\DesktopShortcuts.reg | text | |
MD5:1213A1260BE0789ADE56ED9BA6656FCA | SHA256:52B190CD52671BA5652AFE574245D72DD91AD0EC4168EA405EECC90BF6365BEA | |||
| 3176 | 656cac5f0d5f7-Optimizer-14.6.exe.exe | C:\ProgramData\Optimizer\ReadyMadeMenus\SystemTools.reg | text | |
MD5:13B285768D5140BC337089840E1A9A3B | SHA256:0DC2F4E580BF09632E0961F857556D5F9378A9EBDE76F4D89F302E02DD829C21 | |||
| 3176 | 656cac5f0d5f7-Optimizer-14.6.exe.exe | C:\ProgramData\Optimizer\ReadyMadeMenus\SystemShortcuts.reg | text | |
MD5:3B894F19CDEF342C0704E7774BB20AFA | SHA256:02C4C6610F2BAA98CEF5005A2155A76DD5D52B9B2C8BB49CB31E1A1EF5B74B9A | |||
| 3176 | 656cac5f0d5f7-Optimizer-14.6.exe.exe | C:\ProgramData\Optimizer\Required\EnableOfficeTelemetryTasks.reg | text | |
MD5:97A7511DF9DFCE26F0D26F5B6FEB04B9 | SHA256:D542F1DFA289BC49DBDBD3A2ED9D9C0A3134367396B5C9AEC8D554DDFB993067 | |||
| 3176 | 656cac5f0d5f7-Optimizer-14.6.exe.exe | C:\ProgramData\Optimizer\ReadyMadeMenus\PowerMenu.reg | text | |
MD5:2640EC954A779D0C212822991FF7CF57 | SHA256:1C842C9395AAF625908F6579D201AF2754A92F08859D49D1BC7B55BBA2EAACE5 | |||
| 3176 | 656cac5f0d5f7-Optimizer-14.6.exe.exe | C:\ProgramData\Optimizer\Required\EnableXboxTasks.bat | text | |
MD5:FABECE235B2BEE26CAFD321A676F85F5 | SHA256:DDD6EDECA0D2ABFF7DD9FAB08CB8C736D60B37648E7DFC2E8158798D7DDDF7F7 | |||
| 3176 | 656cac5f0d5f7-Optimizer-14.6.exe.exe | C:\ProgramData\Optimizer\Required\DisableTelemetryTasks.bat | text | |
MD5:CB03C3144AAFF8FB1C3497C403C2B60F | SHA256:ABD9B7C86E9186C4AF174C2A630629588EC89A716D3FF04D357D2610E490C8D3 | |||
| 3176 | 656cac5f0d5f7-Optimizer-14.6.exe.exe | C:\ProgramData\Optimizer\Optimizer.json | binary | |
MD5:44FA8041C0B44C4710B7CF5957819045 | SHA256:E2221008A9525A72771B25E02B0D607EB664EB7D1D9C72AC7EED8AF299C4F525 | |||
| 3176 | 656cac5f0d5f7-Optimizer-14.6.exe.exe | C:\ProgramData\Optimizer\Required\AddOpenWithCMD.reg | text | |
MD5:AECCA5BF312D5950969E111B13FD2634 | SHA256:CEEEFB012D6E66FF52E754090448E7956D9CA483DF54ADB8A4A0D7377D69BAE3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
13
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?fbe613066ac7852b | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
1372 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3176 | 656cac5f0d5f7-Optimizer-14.6.exe.exe | 185.199.110.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
1372 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
1372 | svchost.exe | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
1372 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1060 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
raw.githubusercontent.com |
| shared |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |