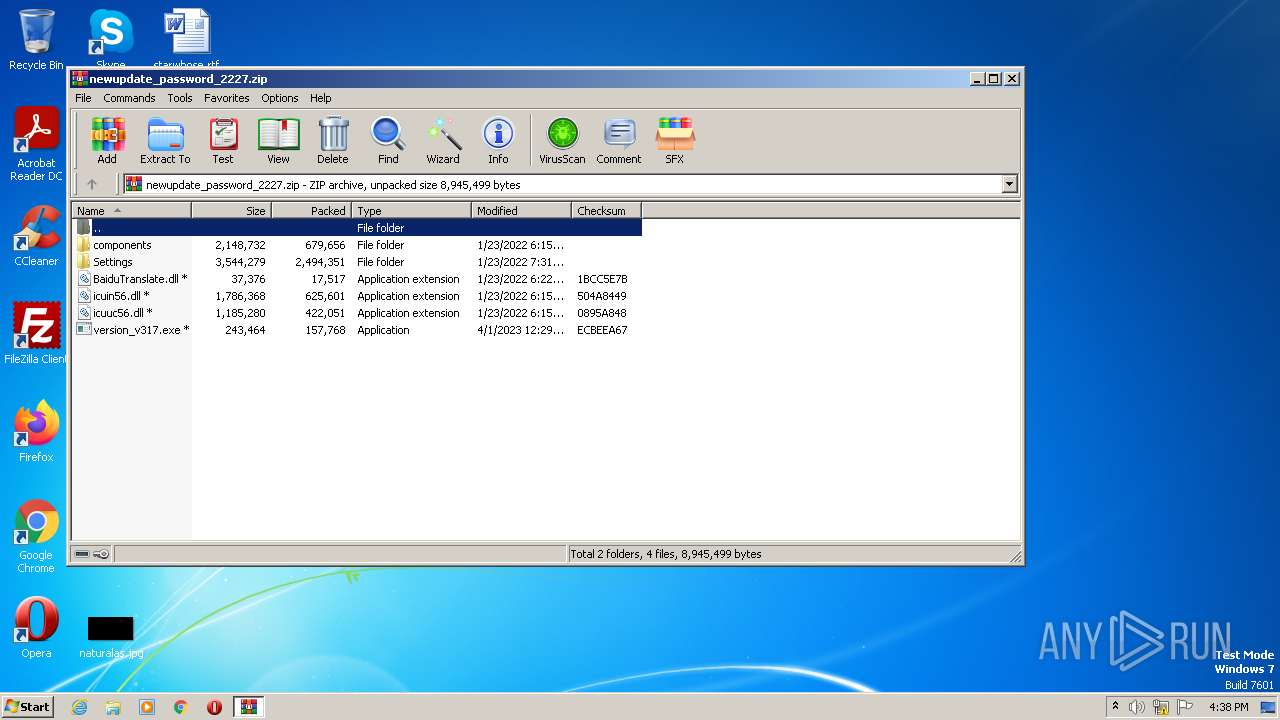
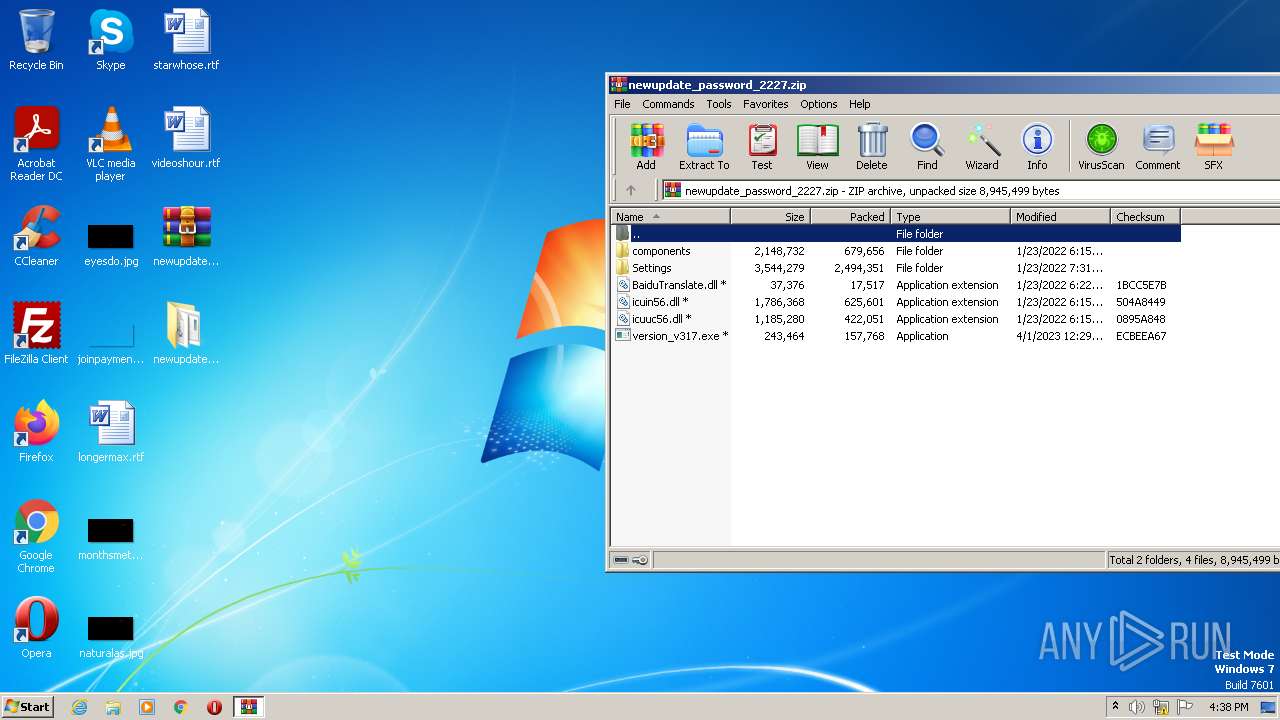
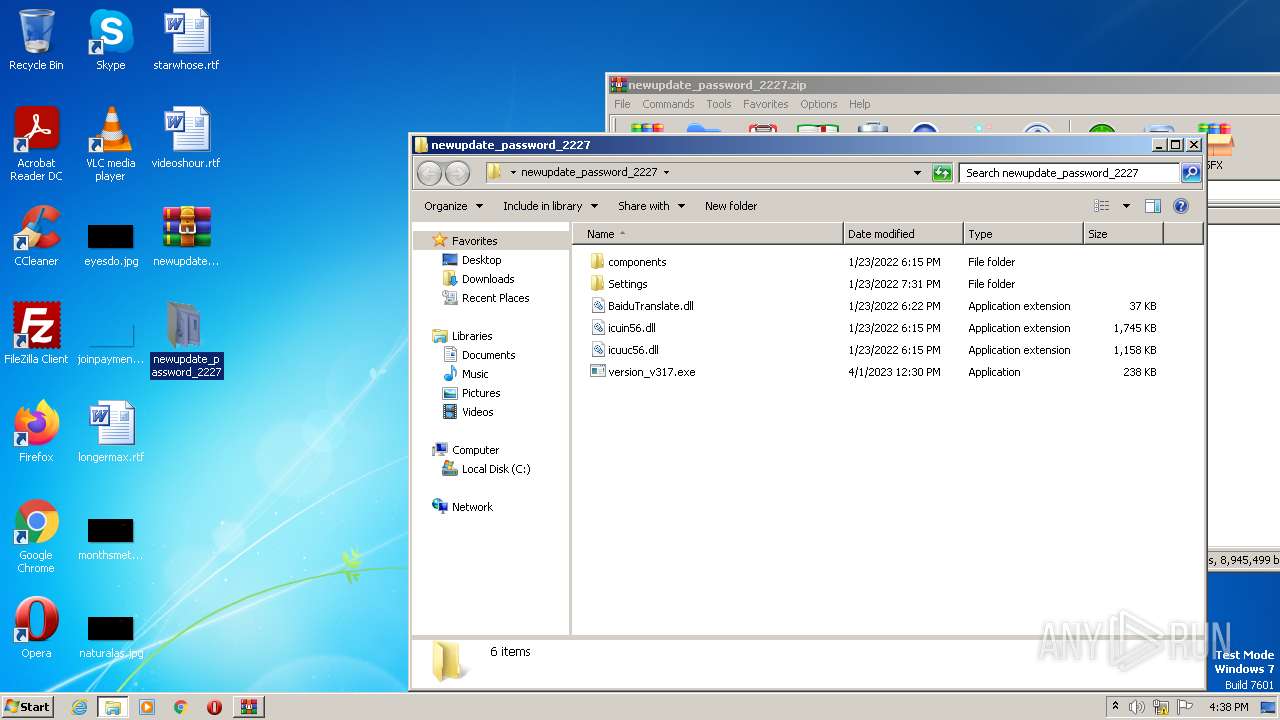
| File name: | newupdate_password_2227.zip |
| Full analysis: | https://app.any.run/tasks/3fb674bb-8716-4448-8b01-5e31ae04e9bf |
| Verdict: | Malicious activity |
| Analysis date: | April 01, 2023, 15:38:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 902E6FEBB705BE9D5A81E80191C5256A |
| SHA1: | 70097464419F45EDB280199E068B52158D724DCE |
| SHA256: | C299E07C1A2FD29A21C075A5467F1AF42ECE26452B1607F76EA6E500D69B77E7 |
| SSDEEP: | 98304:3fioND+IQgyWaU0bn3Phved6/MJdCLglwZ5l2wAjhK8O:qSfQbWaU43JevJdd42wA9c |
MALICIOUS
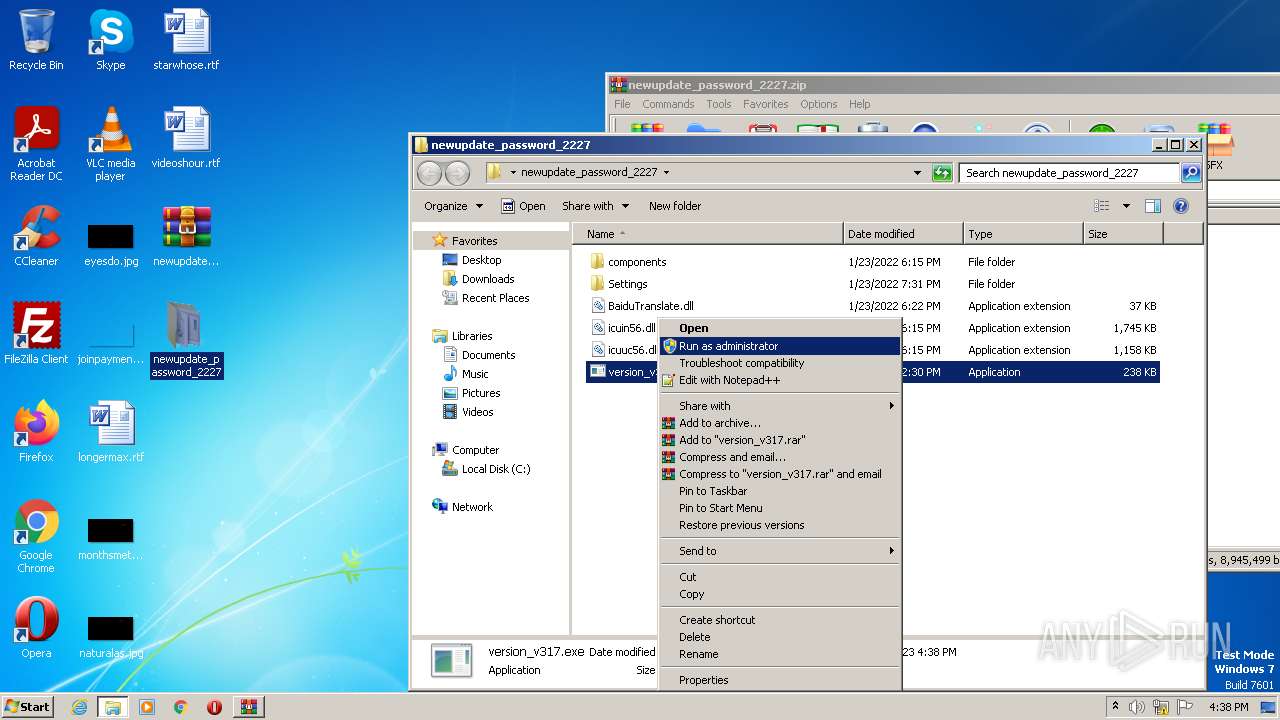
Application was dropped or rewritten from another process
- version_v317.exe (PID: 3092)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1956)
Actions looks like stealing of personal data
- AppLaunch.exe (PID: 3444)
SUSPICIOUS
Searches for installed software
- AppLaunch.exe (PID: 3444)
Reads browser cookies
- AppLaunch.exe (PID: 3444)
Loads DLL from Mozilla Firefox
- AppLaunch.exe (PID: 3444)
Reads the Internet Settings
- AppLaunch.exe (PID: 3444)
Checks for external IP
- AppLaunch.exe (PID: 3444)
Connects to unusual port
- AppLaunch.exe (PID: 3444)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2064)
Manual execution by a user
- version_v317.exe (PID: 3092)
- wmpnscfg.exe (PID: 3156)
Checks supported languages
- version_v317.exe (PID: 3092)
- AppLaunch.exe (PID: 3444)
- wmpnscfg.exe (PID: 3156)
Reads the computer name
- AppLaunch.exe (PID: 3444)
- wmpnscfg.exe (PID: 3156)
The process checks LSA protection
- AppLaunch.exe (PID: 3444)
- wmpnscfg.exe (PID: 3156)
Reads the machine GUID from the registry
- AppLaunch.exe (PID: 3444)
- wmpnscfg.exe (PID: 3156)
Reads Environment values
- AppLaunch.exe (PID: 3444)
Create files in a temporary directory
- AppLaunch.exe (PID: 3444)
Creates files or folders in the user directory
- AppLaunch.exe (PID: 3444)
Reads CPU info
- AppLaunch.exe (PID: 3444)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | icuin56.dll |
|---|---|
| ZipUncompressedSize: | 1786368 |
| ZipCompressedSize: | 625601 |
| ZipCRC: | 0x504a8449 |
| ZipModifyDate: | 2022:01:24 02:15:04 |
| ZipCompression: | Unknown (99) |
| ZipBitFlag: | 0x0009 |
| ZipRequiredVersion: | 20 |
Total processes
47
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1956 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 2064 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\newupdate_password_2227.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3092 | "C:\Users\admin\Desktop\newupdate_password_2227\version_v317.exe" | C:\Users\admin\Desktop\newupdate_password_2227\version_v317.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3156 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3444 | "C:\\Windows\\Microsoft.NET\\Framework\\v4.0.30319\\AppLaunch.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe | version_v317.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET ClickOnce Launch Utility Exit code: 2148734499 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
Total events
11 224
Read events
11 196
Write events
22
Delete events
6
Modification events
| (PID) Process: | (2064) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2064) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2064) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2064) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2064) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2064) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2064) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2064) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1956) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3156) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{299238F0-8D1D-459E-94E5-7C17A4B64456}\{B9D45DA0-6F38-4E40-AB1A-B913CF38B1D3} |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
12
Suspicious files
2
Text files
426
Unknown types
364
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2064 | WinRAR.exe | C:\Users\admin\Desktop\newupdate_password_2227\components\accessibility.xpt | xpt | |
MD5:— | SHA256:— | |||
| 2064 | WinRAR.exe | C:\Users\admin\Desktop\newupdate_password_2227\components\ActivityWrapper.js | text | |
MD5:5B7E48E5EBB0312591F7AC2843BA4E8E | SHA256:FE510D8FC2EA30C085010E158067A26ABB31A0616E2BC7D48FDF374AF8E66D3D | |||
| 2064 | WinRAR.exe | C:\Users\admin\Desktop\newupdate_password_2227\components\AlarmsManager.manifest | text | |
MD5:0FC29B3560C56A5EAB931CC0526DB4B8 | SHA256:1ECC2D36492FC3D537D3326997F4E10BAF53BD680025C5BEFC8C133E4B885A9F | |||
| 2064 | WinRAR.exe | C:\Users\admin\Desktop\newupdate_password_2227\components\ActivityProxy.js | text | |
MD5:18B159534F17E4ECFE583D0D9BB5DC40 | SHA256:72D64C65530EA288072661271A0ABB3CFB56349CCC50B06C711641709D5581B7 | |||
| 2064 | WinRAR.exe | C:\Users\admin\Desktop\newupdate_password_2227\components\addonManager.js | text | |
MD5:FEE4AAB83B139A9F171DDFA27ADDDC90 | SHA256:F4E3BD9E64163E9F45C9219C728C47BF11EA6F7DE50D92EA6B66F8D8648F9804 | |||
| 2064 | WinRAR.exe | C:\Users\admin\Desktop\newupdate_password_2227\components\AlarmsManager.js | text | |
MD5:424A1C9971BE1F1C4DCE01076281E07D | SHA256:CE3A0C14B6148E58EC396922D6FEAC1E1D3112C241B82315791A5424C489AEA2 | |||
| 2064 | WinRAR.exe | C:\Users\admin\Desktop\newupdate_password_2227\components\amWebInstallListener.js | text | |
MD5:A8281CCC8C3C6850709546D2E6AE733C | SHA256:C0D1A9D9DF3640080AC06D2F908A07FF29362A6B91C6989034EA6CCCDA708F2C | |||
| 2064 | WinRAR.exe | C:\Users\admin\Desktop\newupdate_password_2227\components\AppsService.manifest | text | |
MD5:5D313DA91CD541FCBEFB89E96390782A | SHA256:57A51334E208023046001C8F4F717AB96B6E7332B0028549B46DE5EF3A943F2F | |||
| 2064 | WinRAR.exe | C:\Users\admin\Desktop\newupdate_password_2227\components\AppsService.js | text | |
MD5:54ADA449A3DA01208951D6450F01DB36 | SHA256:B32DB5720ACB0E057E11ADF9E9B7597963F2A5326E10F4ED26DAA0EE8846FB8C | |||
| 2064 | WinRAR.exe | C:\Users\admin\Desktop\newupdate_password_2227\components\amContentHandler.js | text | |
MD5:24B4A2E9F7AEEC416ADCC5417B9E1D23 | SHA256:BCC9CFE21D5AFFB8F38AFF6DA5A8809AF1E5F0A0C4689224DF50E1FD849548ED | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
2
DNS requests
1
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3444 | AppLaunch.exe | POST | 200 | 185.220.35.84:5002 | http://185.220.35.84:5002/uploadfile | RU | text | 7 b | malicious |
3444 | AppLaunch.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | binary | 294 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3444 | AppLaunch.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | malicious |
3444 | AppLaunch.exe | 185.220.35.84:5002 | — | LLC Vpsville | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ip-api.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3444 | AppLaunch.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
3444 | AppLaunch.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
3444 | AppLaunch.exe | A Network Trojan was detected | ET MALWARE Suspicious Zipped Filename in Outbound POST Request (Passwords.txt) |
3444 | AppLaunch.exe | A Network Trojan was detected | ET MALWARE Suspicious Zipped Filename in Outbound POST Request (passwords.txt) M2 |
3444 | AppLaunch.exe | A Network Trojan was detected | ET MALWARE Suspicious Zipped Filename in Outbound POST Request (Passwords.txt) M2 |
3444 | AppLaunch.exe | A Network Trojan was detected | ET HUNTING Observed Malicious Filename in Outbound POST Request (Information.txt) |
4 ETPRO signatures available at the full report
Process | Message |
|---|---|
AppLaunch.exe | CLR: Managed code called FailFast without specifying a reason.
|
AppLaunch.exe | CLR: Managed code called FailFast without specifying a reason.
|