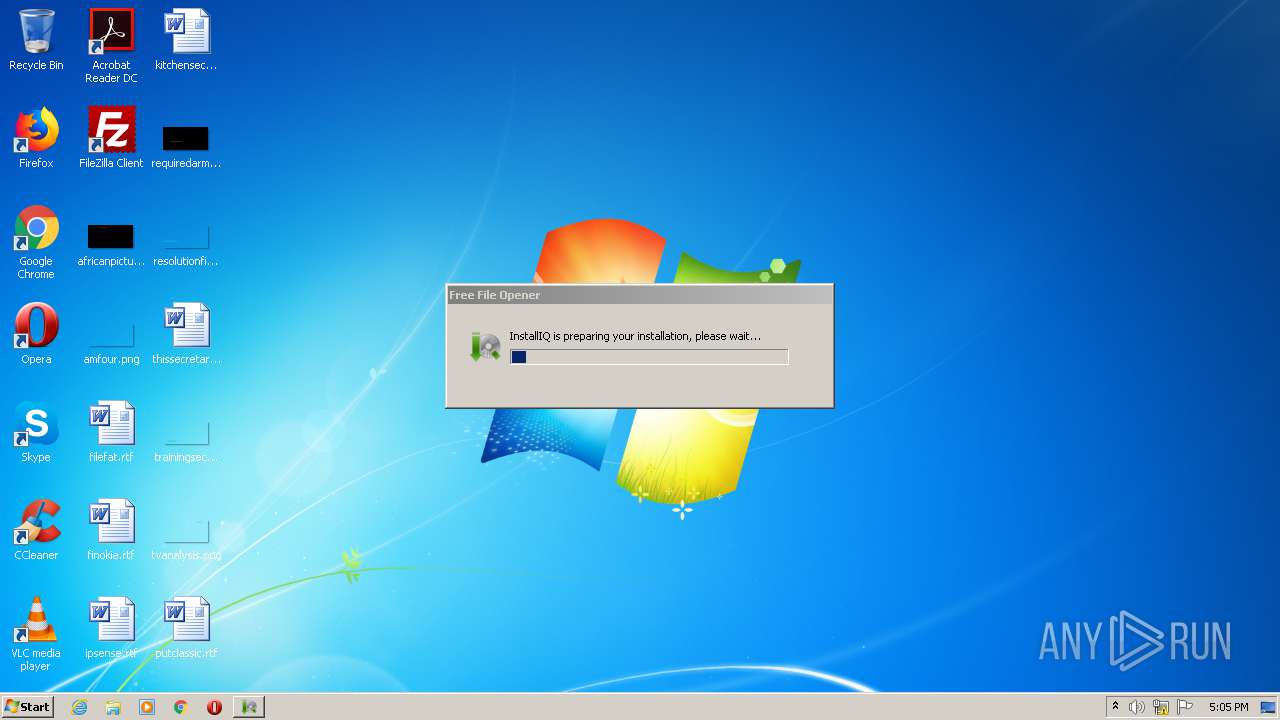
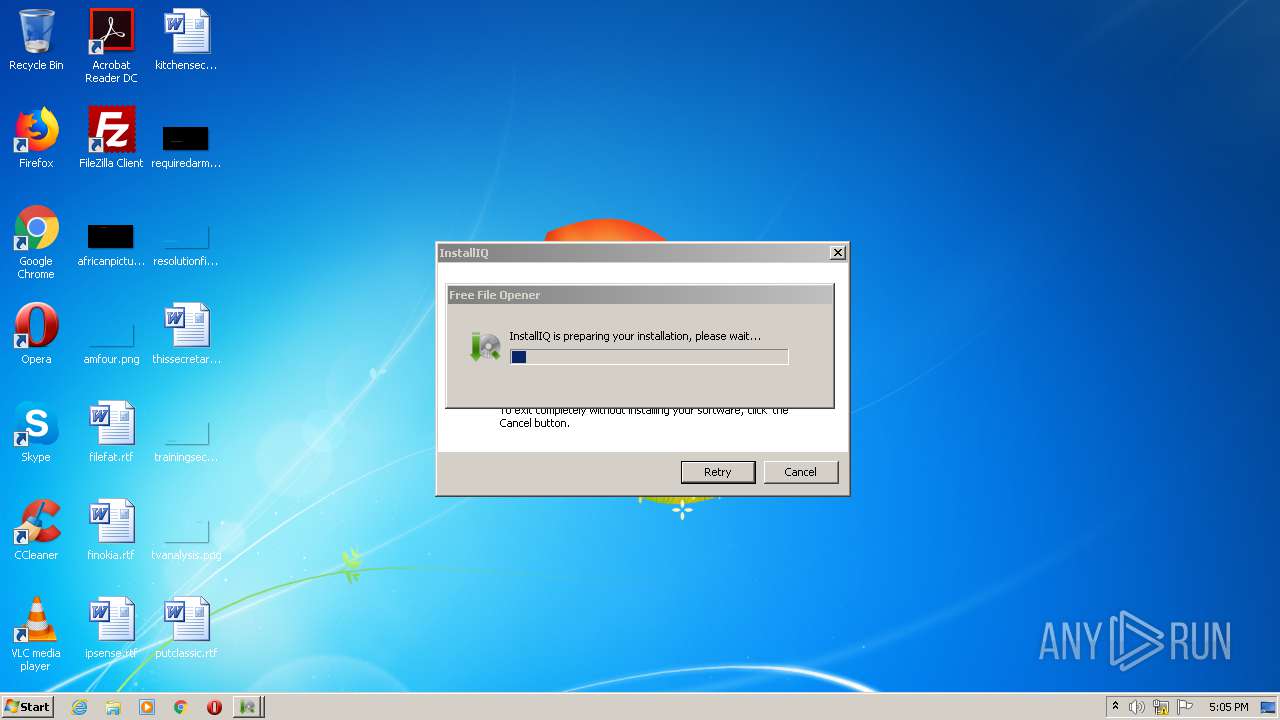
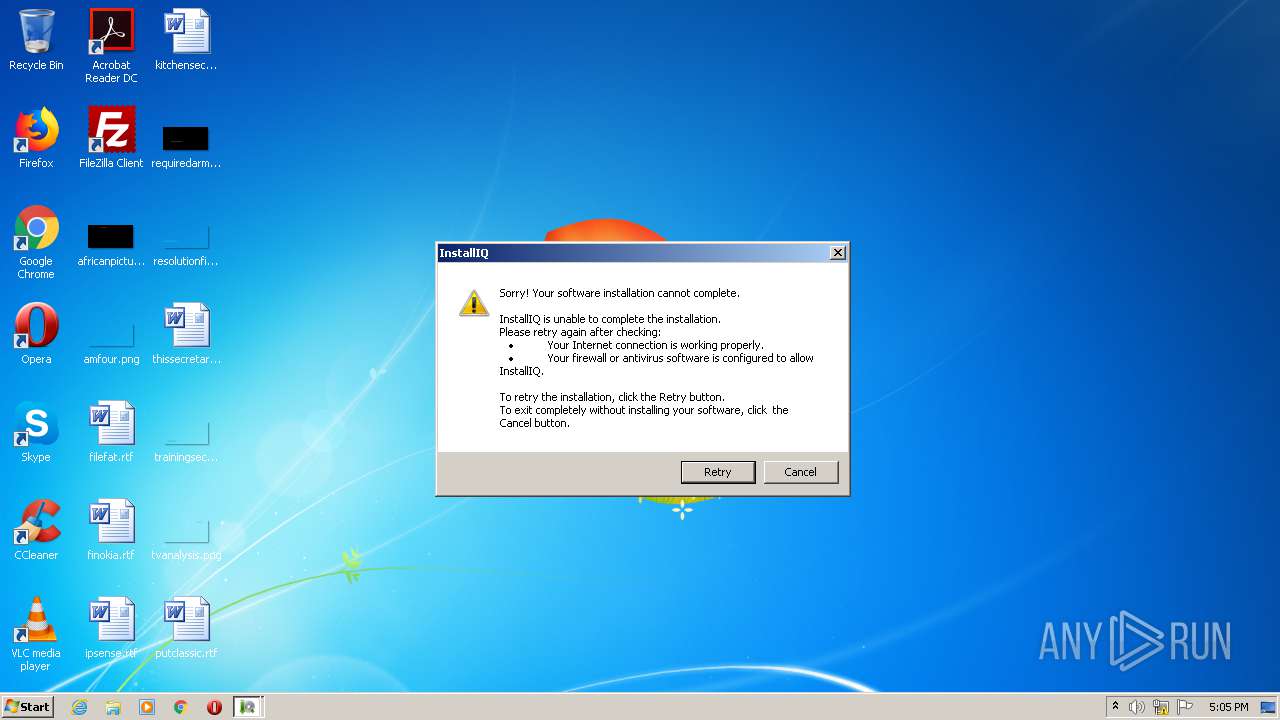
| File name: | installfreefileopener_553.exe |
| Full analysis: | https://app.any.run/tasks/95e60bf4-6178-4d77-a6a9-484e5929609b |
| Verdict: | Malicious activity |
| Analysis date: | September 28, 2020, 16:05:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 083B22E32BF5C30A02891B9AD4D49FE7 |
| SHA1: | 8B610F9E3348AB428635BCDFB3951FB022CE26D3 |
| SHA256: | C27F9E1D469C515AE1F7476462E5E73BA620F1EE293C2A819C0D2377669288DA |
| SSDEEP: | 24576:AZw3NNf/oQnzbEXwOkRKIMFP6+kYzZ/rS9p120KaVfEy37rLHmd/CN1kH3QlQPlv:x7f/rwLIoR6erSLTbpNa |
MALICIOUS
Actions looks like stealing of personal data
- installfreefileopener_553.exe (PID: 3180)
Application was dropped or rewritten from another process
- cookieman.exe (PID: 3528)
SUSPICIOUS
Application launched itself
- installfreefileopener_553.exe (PID: 3568)
Reads Internet Cache Settings
- cookieman.exe (PID: 3528)
- installfreefileopener_553.exe (PID: 3180)
Reads the cookies of Google Chrome
- installfreefileopener_553.exe (PID: 3180)
Reads the cookies of Mozilla Firefox
- installfreefileopener_553.exe (PID: 3180)
Creates files in the user directory
- installfreefileopener_553.exe (PID: 3180)
Executable content was dropped or overwritten
- installfreefileopener_553.exe (PID: 3180)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2011:06:29 00:04:10+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 942080 |
| InitializedDataSize: | 631296 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x41b49 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.97.0.0 |
| ProductVersionNumber: | 2.97.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | W3i, LLC |
| FileDescription: | InstallIQ Installation Utility |
| FileVersion: | 2.97.0.0 |
| InternalName: | InstallIQ.exe |
| LegalCopyright: | Copyright ©2011 W3i Holdings, LLC. All rights reserved. |
| OriginalFileName: | InstallIQ.exe |
| ProductName: | InstallIQ Installation Utility |
| ProductVersion: | 2.97.0.0 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 28-Jun-2011 22:04:10 |
| Detected languages: |
|
| Debug artifacts: |
|
| CompanyName: | W3i, LLC |
| FileDescription: | InstallIQ Installation Utility |
| FileVersion: | 2.97.0.0 |
| InternalName: | InstallIQ.exe |
| LegalCopyright: | Copyright ©2011 W3i Holdings, LLC. All rights reserved. |
| OriginalFilename: | InstallIQ.exe |
| ProductName: | InstallIQ Installation Utility |
| ProductVersion: | 2.97.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000108 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 38 |
| Time date stamp: | 28-Jun-2011 22:04:10 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0005A64D | 0x0005A800 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.65752 |
.text-co\x8aD | 0x0005C000 | 0x0000448A | 0x00004600 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.53125 |
.text-co\xcai\x01 | 0x00061000 | 0x000169CA | 0x00016A00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.48674 |
.text-coH\xc4 | 0x00078000 | 0x0000C448 | 0x0000C600 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.37587 |
.text-cov' | 0x00085000 | 0x00002776 | 0x00002800 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.32729 |
.text-co\xe5G | 0x00088000 | 0x000047E5 | 0x00004800 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.37655 |
.text-co}4 | 0x0008D000 | 0x0000347D | 0x00003600 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.26796 |
.text-co\xb5\x8a | 0x00091000 | 0x00008AB5 | 0x00008C00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.33284 |
.text-fr\xf2\x8c | 0x0009A000 | 0x00008CF2 | 0x00008E00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.23218 |
.text-co\xc6\x7f | 0x000A3000 | 0x00007FC6 | 0x00008000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.23697 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.19014 | 871 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 3.41351 | 296 | Latin 1 / Western European | English - United States | RT_ICON |
3 | 5.62084 | 3752 | Latin 1 / Western European | English - United States | RT_ICON |
4 | 5.7081 | 2216 | Latin 1 / Western European | English - United States | RT_ICON |
5 | 5.14122 | 1384 | Latin 1 / Western European | English - United States | RT_ICON |
6 | 5.34185 | 9640 | Latin 1 / Western European | English - United States | RT_ICON |
7 | 3.26328 | 2730 | Latin 1 / Western European | English - United States | RT_STRING |
8 | 3.22664 | 3594 | Latin 1 / Western European | English - United States | RT_STRING |
9 | 3.02695 | 308 | Latin 1 / Western European | English - United States | RT_CURSOR |
10 | 2.74274 | 180 | Latin 1 / Western European | English - United States | RT_CURSOR |
Imports
ADVAPI32.dll |
COMCTL32.dll |
COMDLG32.dll |
GDI32.dll |
KERNEL32.dll |
OLEAUT32.dll |
PSAPI.DLL |
SHELL32.dll |
SHLWAPI.dll |
USER32.dll |
Total processes
40
Monitored processes
4
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 308 | "C:\Users\admin\AppData\Local\Temp\installfreefileopener_553.exe" | C:\Users\admin\AppData\Local\Temp\installfreefileopener_553.exe | — | explorer.exe | |||||||||||
User: admin Company: W3i, LLC Integrity Level: MEDIUM Description: InstallIQ Installation Utility Exit code: 3221226540 Version: 2.97.0.0 Modules
| |||||||||||||||
| 3180 | "C:\Users\admin\AppData\Local\Temp\installfreefileopener_553.exe" /wrapper /dir="C:\Users\admin\AppData\Local\Temp\pkg_10516e70" /pproc="Explorer.EXE" | C:\Users\admin\AppData\Local\Temp\installfreefileopener_553.exe | installfreefileopener_553.exe | ||||||||||||
User: admin Company: W3i, LLC Integrity Level: HIGH Description: InstallIQ Installation Utility Exit code: 0 Version: 2.97.0.0 Modules
| |||||||||||||||
| 3528 | "C:\Users\admin\AppData\LocalLow\cookieman.exe" /mode=read installiq.com | C:\Users\admin\AppData\LocalLow\cookieman.exe | — | installfreefileopener_553.exe | |||||||||||
User: admin Integrity Level: LOW Exit code: 0 Modules
| |||||||||||||||
| 3568 | "C:\Users\admin\AppData\Local\Temp\installfreefileopener_553.exe" | C:\Users\admin\AppData\Local\Temp\installfreefileopener_553.exe | explorer.exe | ||||||||||||
User: admin Company: W3i, LLC Integrity Level: HIGH Description: InstallIQ Installation Utility Exit code: 0 Version: 2.97.0.0 Modules
| |||||||||||||||
Total events
65
Read events
49
Write events
13
Delete events
3
Modification events
| (PID) Process: | (3528) cookieman.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\LowCache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3528) cookieman.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\LowCache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3528) cookieman.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\LowCache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3180) installfreefileopener_553.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Freeze.com\Installer |
| Operation: | write | Name: | test |
Value: 1 | |||
| (PID) Process: | (3180) installfreefileopener_553.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Freeze.com\Installer |
| Operation: | delete value | Name: | test |
Value: 1 | |||
| (PID) Process: | (3180) installfreefileopener_553.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Freeze.com\Installer |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3180) installfreefileopener_553.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Freeze.com |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3180) installfreefileopener_553.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3180) installfreefileopener_553.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A5000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3180) installfreefileopener_553.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
1
Suspicious files
0
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3528 | cookieman.exe | C:\Users\admin\AppData\LocalLow\cookie.ini | — | |
MD5:— | SHA256:— | |||
| 3180 | installfreefileopener_553.exe | C:\Users\admin\AppData\Local\Temp\cookies.sqlite | — | |
MD5:— | SHA256:— | |||
| 3180 | installfreefileopener_553.exe | C:\Users\admin\AppData\Local\Temp\cookies.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3180 | installfreefileopener_553.exe | C:\Users\admin\AppData\Local\Temp\cookies | — | |
MD5:— | SHA256:— | |||
| 3568 | installfreefileopener_553.exe | C:\Users\admin\AppData\Local\Temp\pkg_10516e70\timings.txt | text | |
MD5:— | SHA256:— | |||
| 3180 | installfreefileopener_553.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\M9XPVMPY.txt | text | |
MD5:— | SHA256:— | |||
| 3180 | installfreefileopener_553.exe | C:\Users\admin\AppData\Local\Temp\pkg_10516e70\detectionrules.dat | html | |
MD5:— | SHA256:— | |||
| 3180 | installfreefileopener_553.exe | C:\Users\admin\AppData\LocalLow\cookieman.exe | executable | |
MD5:— | SHA256:— | |||
| 3568 | installfreefileopener_553.exe | C:\Users\admin\AppData\Local\Temp\pkg_10516e70\wrapper.xml | text | |
MD5:7DF4B6DB3FBBD712D68509779B2ED8FB | SHA256:357DA15A7E543CF183942D2E0E125D8814DD2BDB225AC5FE7D1FAE0601B4473B | |||
| 3568 | installfreefileopener_553.exe | C:\Users\admin\AppData\Local\Temp\pkg_10516e70\stub.log | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
8
DNS requests
2
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3180 | installfreefileopener_553.exe | GET | 200 | 37.48.65.143:80 | http://dl.installiq.com/api/detectionrequest.aspx?keyid=1&shortname=installfreefileopener&langid=0x0409 | NL | html | 551 b | malicious |
3180 | installfreefileopener_553.exe | GET | — | 37.48.65.143:80 | http://dl.installiq.com/api/detectionrequest.aspx?keyid=1&shortname=installfreefileopener&langid=0x0409 | NL | — | — | malicious |
3180 | installfreefileopener_553.exe | GET | 200 | 37.48.65.143:80 | http://dl.installiq.com/api/detectionrequest.aspx?keyid=1&shortname=installfreefileopener&langid=0x0409 | NL | html | 551 b | malicious |
3180 | installfreefileopener_553.exe | GET | 302 | 37.48.65.143:80 | http://dl.installiq.com/api/detectionrequest.aspx?keyid=1&shortname=installfreefileopener&langid=0x0409 | NL | text | 11 b | malicious |
3180 | installfreefileopener_553.exe | GET | 200 | 37.48.65.143:80 | http://dl.installiq.com/api/detectionrequest.aspx?keyid=1&shortname=installfreefileopener&langid=0x0409 | NL | html | 551 b | malicious |
3180 | installfreefileopener_553.exe | GET | 200 | 37.48.65.143:80 | http://dl.installiq.com/api/detectionrequest.aspx?keyid=1&shortname=installfreefileopener&langid=0x0409 | NL | html | 551 b | malicious |
3180 | installfreefileopener_553.exe | GET | 200 | 37.48.65.143:80 | http://dl.installiq.com/api/detectionrequest.aspx?keyid=1&shortname=installfreefileopener&langid=0x0409 | NL | html | 551 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3180 | installfreefileopener_553.exe | 37.48.65.143:80 | dl.installiq.com | LeaseWeb Netherlands B.V. | NL | malicious |
3180 | installfreefileopener_553.exe | 208.91.196.145:80 | ww1.installiq.com | Confluence Networks Inc | VG | malicious |
— | — | 37.48.65.143:80 | dl.installiq.com | LeaseWeb Netherlands B.V. | NL | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dl.installiq.com |
| malicious |
ww1.installiq.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3180 | installfreefileopener_553.exe | Potential Corporate Privacy Violation | ET POLICY InstallIQ Updater Software request |
3180 | installfreefileopener_553.exe | Potential Corporate Privacy Violation | ET POLICY InstallIQ Updater Software request |
3180 | installfreefileopener_553.exe | Potential Corporate Privacy Violation | ET POLICY InstallIQ Updater Software request |
3180 | installfreefileopener_553.exe | Potential Corporate Privacy Violation | ET POLICY InstallIQ Updater Software request |
3180 | installfreefileopener_553.exe | Potential Corporate Privacy Violation | ET POLICY InstallIQ Updater Software request |
3180 | installfreefileopener_553.exe | Potential Corporate Privacy Violation | ET POLICY InstallIQ Updater Software request |