| File name: | DMDE_Pro_x64_4.2.0.814_Portable.zip |
| Full analysis: | https://app.any.run/tasks/1754a591-79ff-4a80-8287-da6fd8e71ff1 |
| Verdict: | Malicious activity |
| Analysis date: | January 01, 2025, 15:30:10 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 638A0C3B5E164EF4930BADFA15C5EA10 |
| SHA1: | D67CC780EB71A03D9BC6311CB600D56AE34DD23A |
| SHA256: | C27D9BCEE56C7560E6C78B25FFD81B99EE3A186AE8ABF3F7CAF14951CB6D6991 |
| SSDEEP: | 98304:j7YCuBGR74dPZ05vHMwNcTmzPa0tnfLHuTbz6nXZ7GKrtCtUeqq4r+i3xCzg/oiD:sb+Ly0ZjxS7sLWBhU |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the BIOS version
- Dmde.EXE (PID: 4624)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5652)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 5652)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 5652)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 5652)
Manual execution by a user
- Dmde.EXE (PID: 4628)
- Dmde.EXE (PID: 4624)
- notepad.exe (PID: 6012)
- notepad.exe (PID: 3952)
- notepad.exe (PID: 3524)
- notepad.exe (PID: 5604)
- notepad.exe (PID: 644)
- notepad.exe (PID: 3688)
- notepad.exe (PID: 556)
- OpenWith.exe (PID: 5432)
- OpenWith.exe (PID: 4824)
Reads security settings of Internet Explorer
- notepad.exe (PID: 6012)
- notepad.exe (PID: 3952)
- notepad.exe (PID: 3524)
- notepad.exe (PID: 5604)
- notepad.exe (PID: 644)
- notepad.exe (PID: 3688)
- notepad.exe (PID: 556)
Checks supported languages
- Dmde.EXE (PID: 4624)
- MpCmdRun.exe (PID: 6096)
Create files in a temporary directory
- Dmde.EXE (PID: 4624)
- MpCmdRun.exe (PID: 6096)
Reads the computer name
- Dmde.EXE (PID: 4624)
- MpCmdRun.exe (PID: 6096)
Process checks whether UAC notifications are on
- Dmde.EXE (PID: 4624)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 4824)
- OpenWith.exe (PID: 5432)
Themida protector has been detected
- Dmde.EXE (PID: 4624)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5652)
The process uses the downloaded file
- WinRAR.exe (PID: 5652)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | None |
| ZipModifyDate: | 2024:12:13 03:36:08 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | DMDE_Pro_x64_4.2.0.814_Portable/ |
Total processes
132
Monitored processes
15
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 556 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\dmde.ini | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 624 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR5652.26576\Rar$Scan34937.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\template.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3524 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\readme.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3688 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\eula.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3952 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\deviohsc.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4624 | "C:\Users\admin\Desktop\Dmde.EXE" | C:\Users\admin\Desktop\Dmde.EXE | explorer.exe | ||||||||||||
User: admin Company: DMDE Software Integrity Level: HIGH Description: DMDE 4.2.0.814 - Data Recovery Software Version: 4.2.0.814 Modules
| |||||||||||||||
| 4628 | "C:\Users\admin\Desktop\Dmde.EXE" | C:\Users\admin\Desktop\Dmde.EXE | — | explorer.exe | |||||||||||
User: admin Company: DMDE Software Integrity Level: MEDIUM Description: DMDE 4.2.0.814 - Data Recovery Software Exit code: 3221226540 Version: 4.2.0.814 Modules
| |||||||||||||||
| 4824 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\ja.lng | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5432 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\pt-pt.lng | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 757
Read events
3 747
Write events
10
Delete events
0
Modification events
| (PID) Process: | (5652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\DMDE_Pro_x64_4.2.0.814_Portable.zip | |||
| (PID) Process: | (5652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 32 | |||
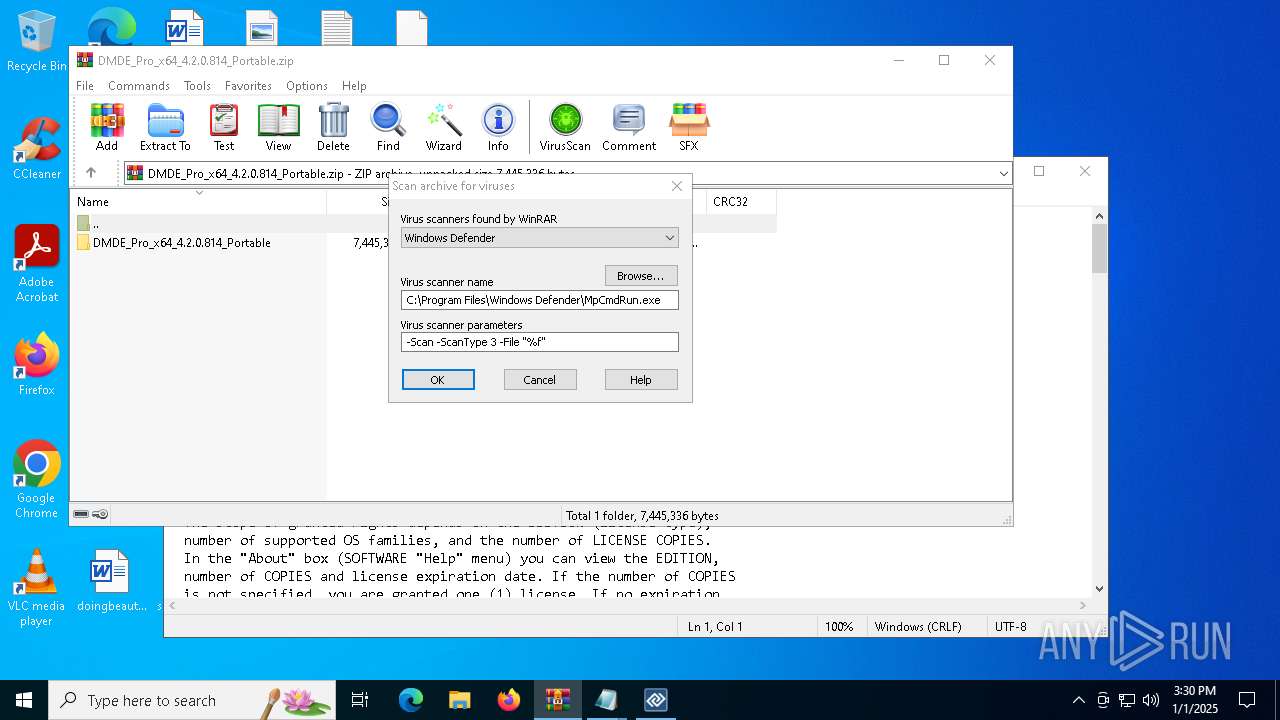
| (PID) Process: | (5652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
Executable files
1
Suspicious files
2
Text files
24
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
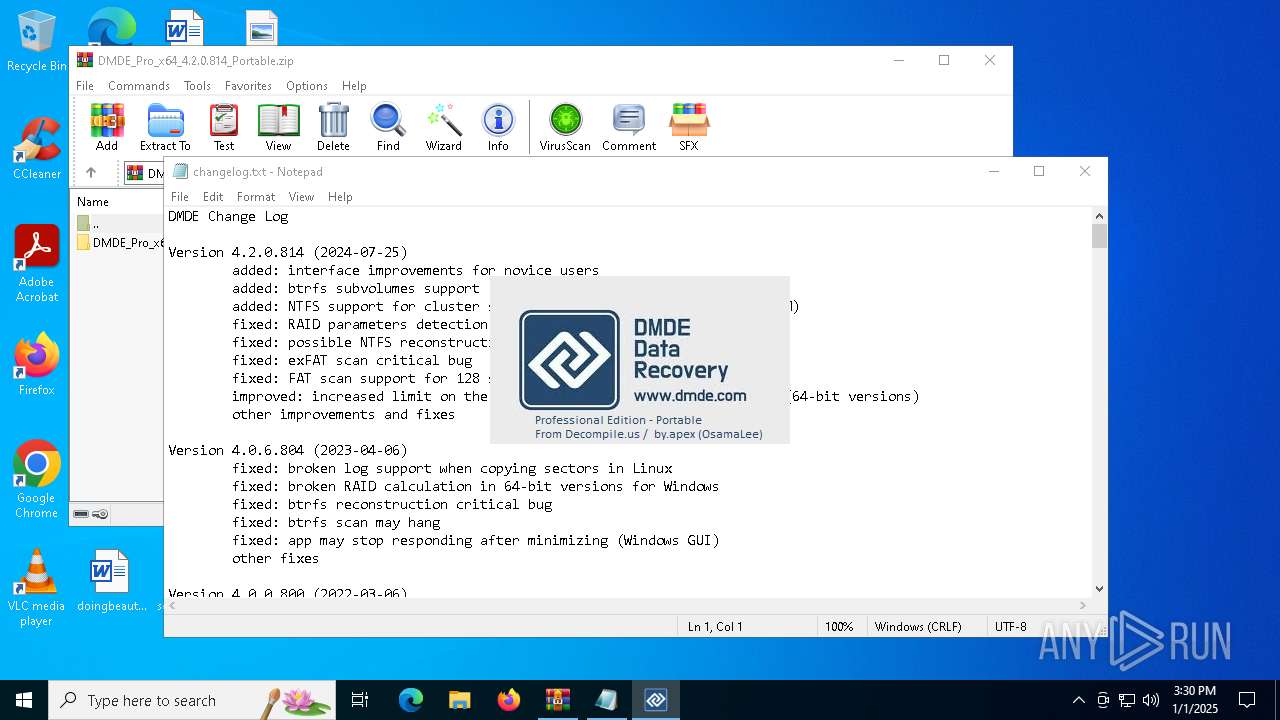
| 5652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5652.26576\DMDE_Pro_x64_4.2.0.814_Portable.zip\DMDE_Pro_x64_4.2.0.814_Portable\changelog.txt | text | |
MD5:5F5AC8E1755F6EFB84F4BF40CC696545 | SHA256:61F089CF6AA205429D3E72C6219B133B2DF0960C4F75E618B4FDA7F44BCC6294 | |||
| 5652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5652.26576\DMDE_Pro_x64_4.2.0.814_Portable.zip\DMDE_Pro_x64_4.2.0.814_Portable\Dmde.EXE | executable | |
MD5:CDDA3D1946CC701842B25B1B93F46F82 | SHA256:5C00FE6BED6ACDB8850EBBE229303CA39119FCBB42F8F0697C71B5F6C5208C5E | |||
| 4624 | Dmde.EXE | C:\Users\admin\Desktop\license.key | text | |
MD5:7CA6435956D6947F934E41494FCD1C35 | SHA256:5E574E416CD031F9929130414FE0D28FE04A84C43F3D2CF221CCA57B38765D8E | |||
| 5652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5652.26576\DMDE_Pro_x64_4.2.0.814_Portable.zip\DMDE_Pro_x64_4.2.0.814_Portable\dmde_en.chm | chm | |
MD5:B7A430D3A140FDD9492BB97698191FDB | SHA256:D7A415C4DD80C85A7336883D82B63431E6E8E464C3501B91677EA6D570A4F51D | |||
| 5652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5652.26576\DMDE_Pro_x64_4.2.0.814_Portable.zip\DMDE_Pro_x64_4.2.0.814_Portable\locals\dmde_pl.chm | chm | |
MD5:25F2D784D19C86AE0BA3767A912522D6 | SHA256:6C1E39D00C1D319CCBFE0F9F1EE9BCB270E7990F677508045DC5810D4A8CB990 | |||
| 5652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5652.26576\DMDE_Pro_x64_4.2.0.814_Portable.zip\DMDE_Pro_x64_4.2.0.814_Portable\locals\fa.lng | text | |
MD5:107AE9A8FA3634502AC5A0E3150E18F3 | SHA256:3D1C7CB6B2389146B6D39E32DEDA627FC84CCE8A3D7378FC5B1E5BDDE8E042BF | |||
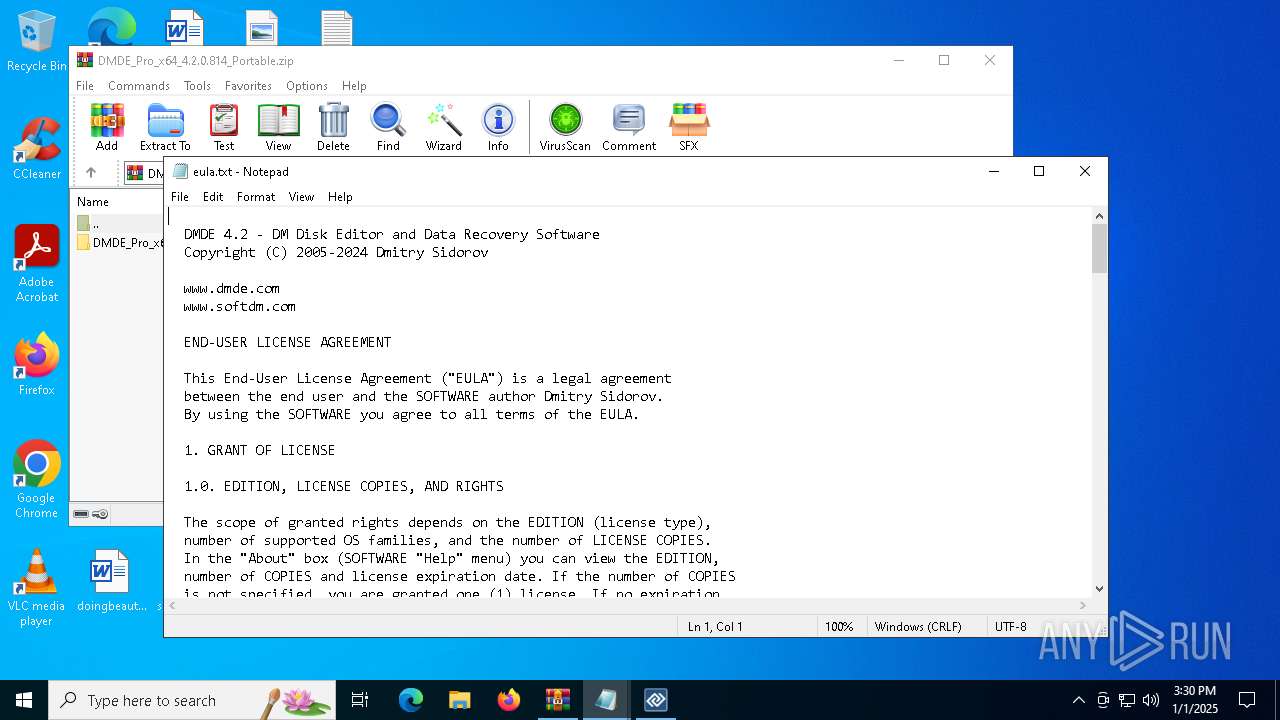
| 5652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5652.26576\DMDE_Pro_x64_4.2.0.814_Portable.zip\DMDE_Pro_x64_4.2.0.814_Portable\eula.txt | text | |
MD5:E94A686273CC4FCE294E3971FE41E5AB | SHA256:91A9C72C46C9A9E0ED1CC0AD6D3ABFA7EEE8289EAFDE02958A4B441B55B76285 | |||
| 5652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5652.26576\DMDE_Pro_x64_4.2.0.814_Portable.zip\DMDE_Pro_x64_4.2.0.814_Portable\locals\de.lng | text | |
MD5:5A92C21A4D56E0D23DC7F80B0B6F59DD | SHA256:A5CBB88937B9BC2CF5533CE184304BC26410454DC7E18974FCADB47E87273E6F | |||
| 5652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5652.26576\DMDE_Pro_x64_4.2.0.814_Portable.zip\DMDE_Pro_x64_4.2.0.814_Portable\locals\en.lng | text | |
MD5:5021C299052570771468412C59EB7E01 | SHA256:3D561216778106D2C7B7A48A850D64A7E4C882F5B476462158FDE0F1BDBFA40E | |||
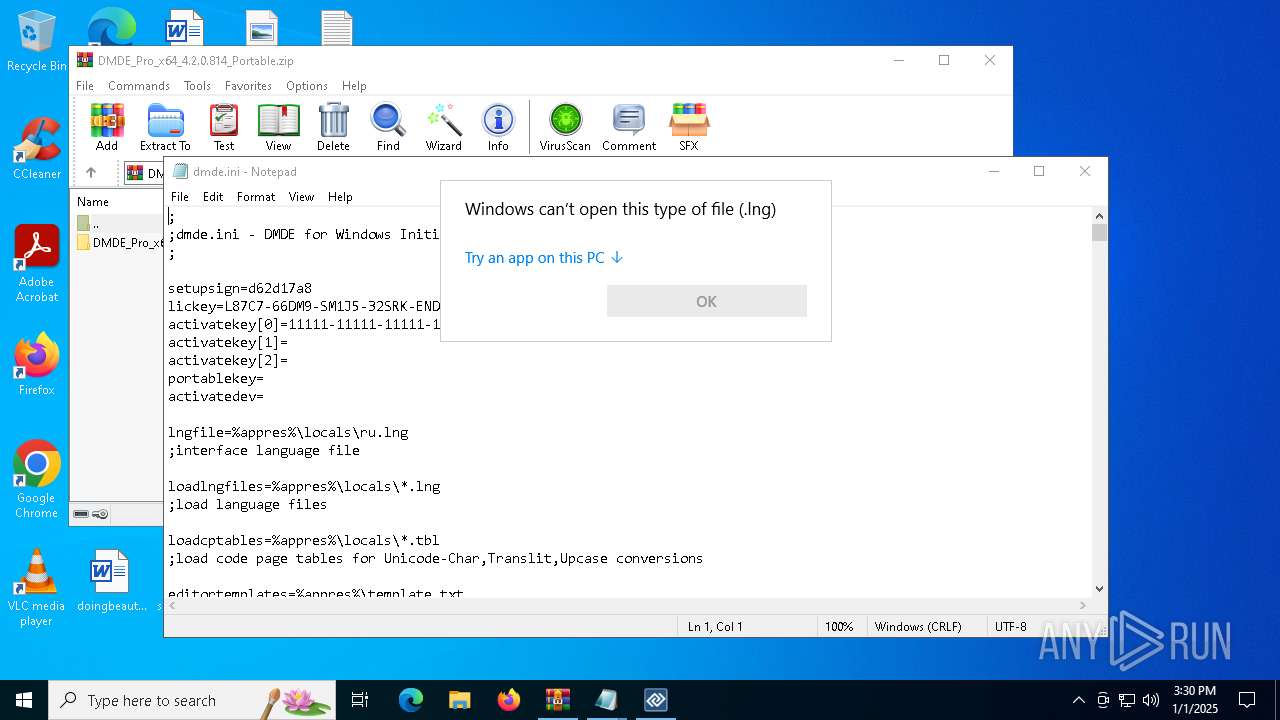
| 4624 | Dmde.EXE | C:\Users\admin\Desktop\dmde.ini | text | |
MD5:DC4C5151127CDAAE41E6A01100310A7E | SHA256:3903B1D2C3CC8520B5FFCCA2B804B90A664AD0A312760DE478B8F9F76EAA41A4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
23
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2224 | svchost.exe | GET | 200 | 23.48.23.147:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.147:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2224 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2224 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 104.126.37.131:443 | www.bing.com | Akamai International B.V. | DE | unknown |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
2224 | svchost.exe | 23.48.23.147:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.147:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2224 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |