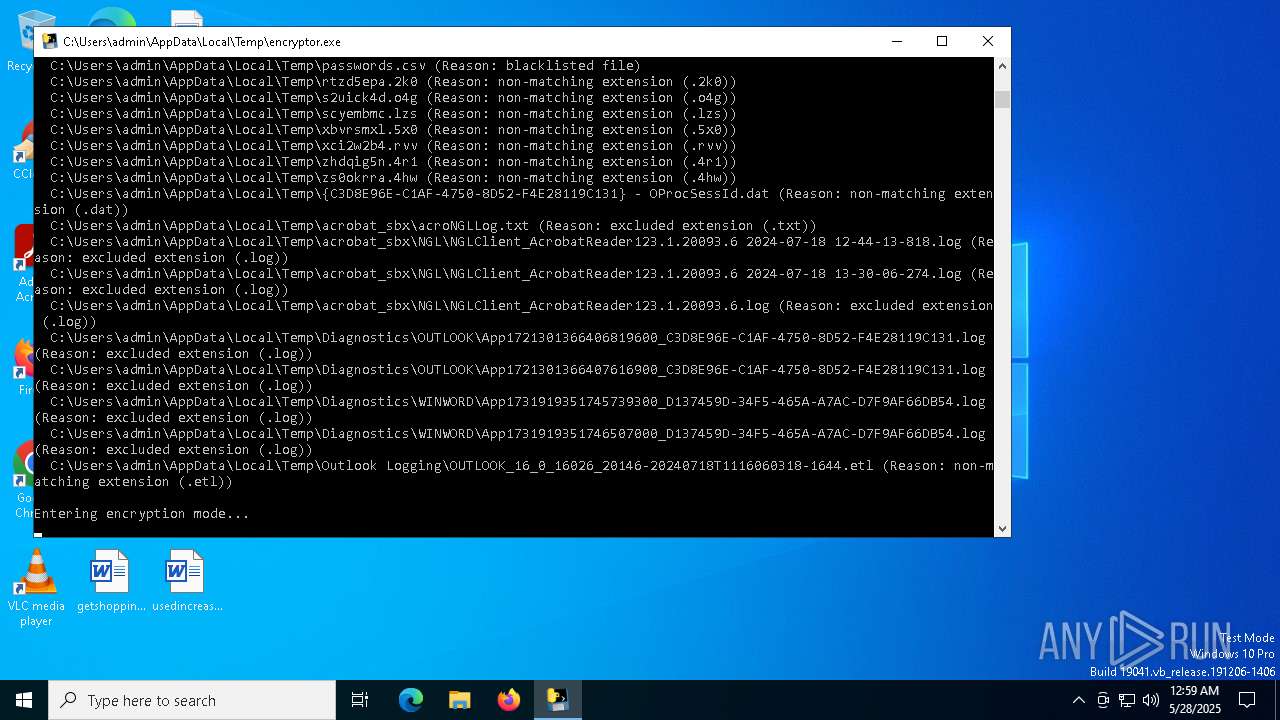
| File name: | encryptor.exe |
| Full analysis: | https://app.any.run/tasks/4303bcce-9773-4319-93d7-30cfa901b3a1 |
| Verdict: | Malicious activity |
| Analysis date: | May 28, 2025, 00:59:27 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 7 sections |
| MD5: | AD2C1142C52EB03D182645364E7E87E2 |
| SHA1: | 6C9A118E5FF1B8D3CA72915FB83B4FBAAD97D928 |
| SHA256: | C25ABD3F13EA5E98A8C3F433F7251DA497BDEE60321D67CDC07BB2B24B0BA2FB |
| SSDEEP: | 196608:7oxtYJFrFcwyK3TeRi/Bqannpet/eSgdVz:eYPpjyK3KRi5q8KeSgj |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops python dynamic module
- encryptor.exe (PID: 6728)
The process drops C-runtime libraries
- encryptor.exe (PID: 6728)
Executable content was dropped or overwritten
- encryptor.exe (PID: 6728)
Process drops legitimate windows executable
- encryptor.exe (PID: 6728)
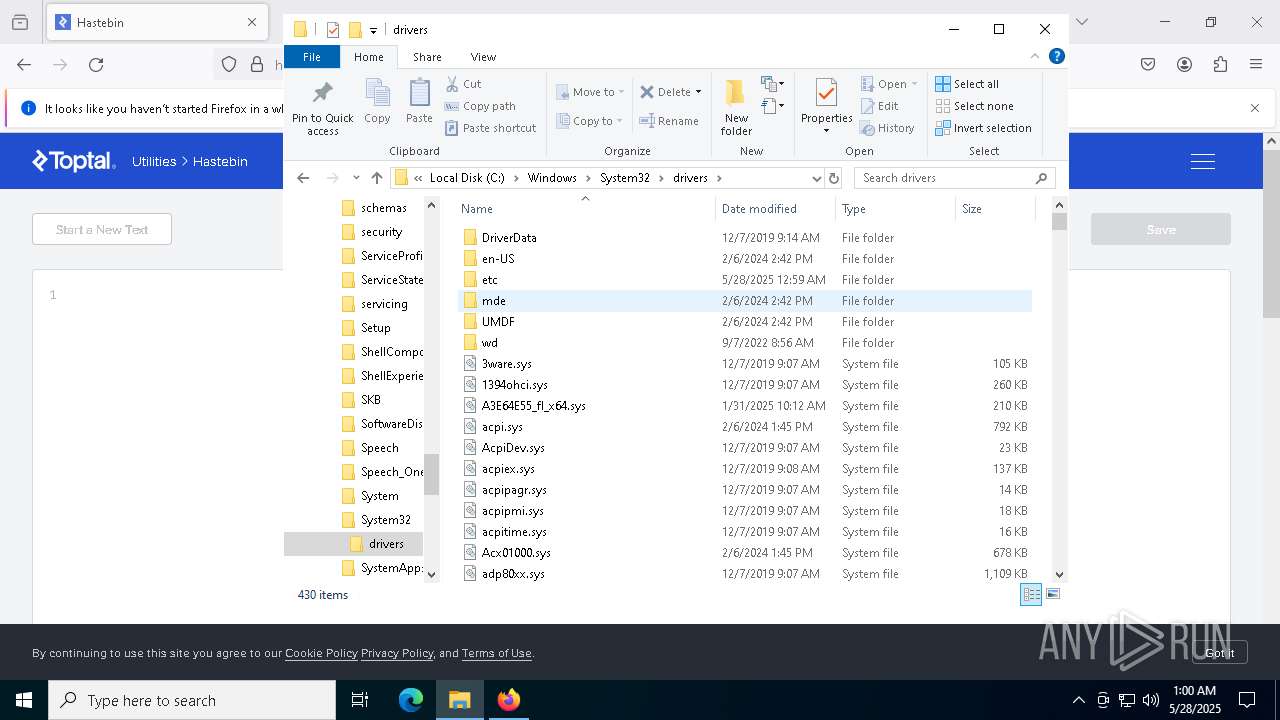
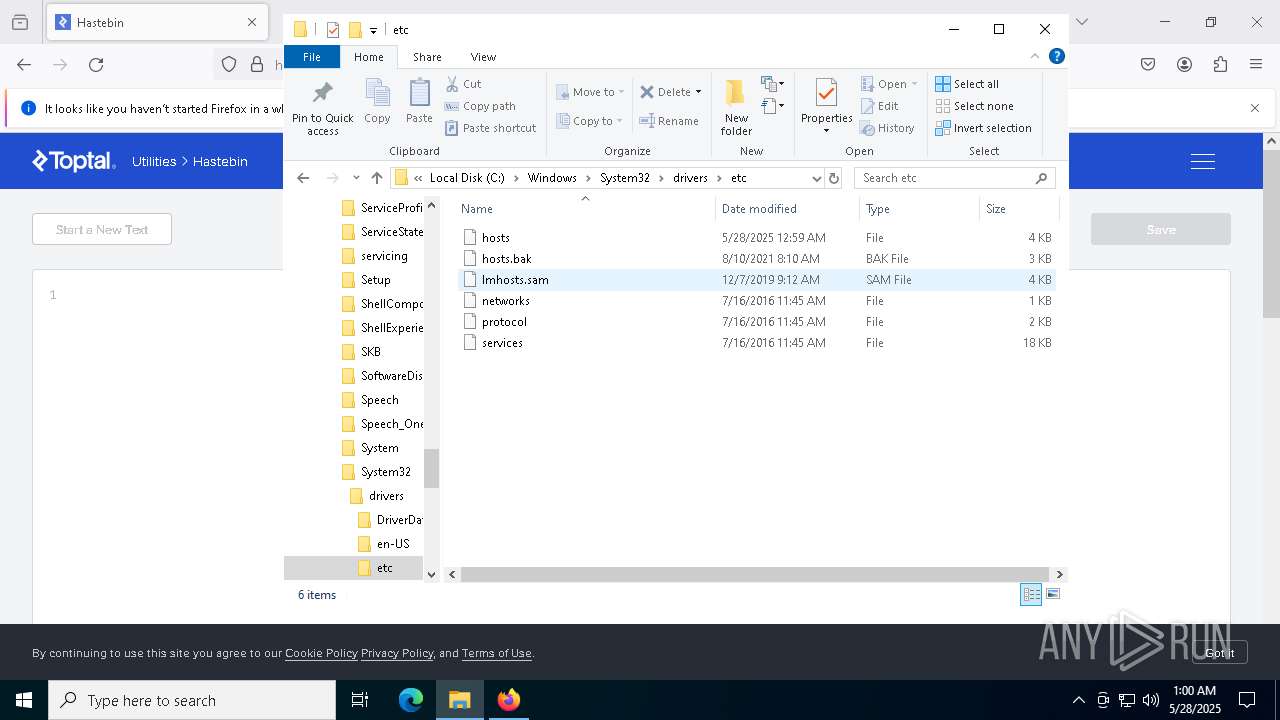
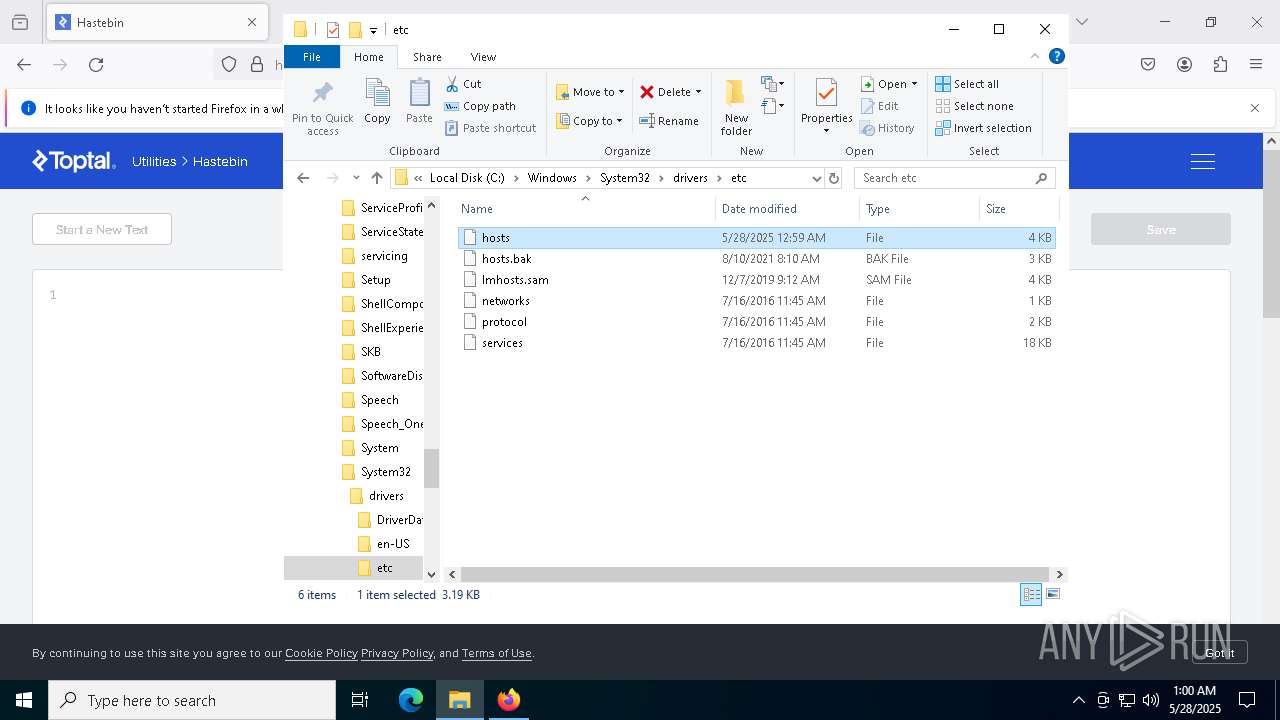
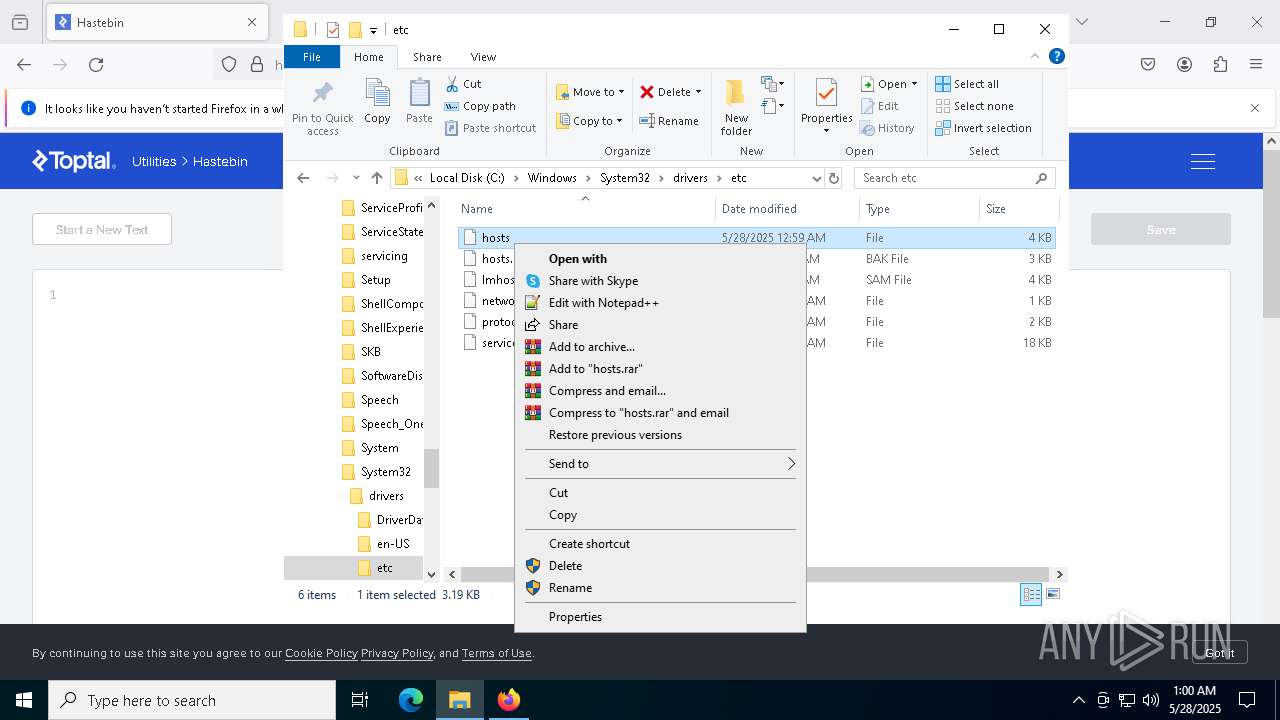
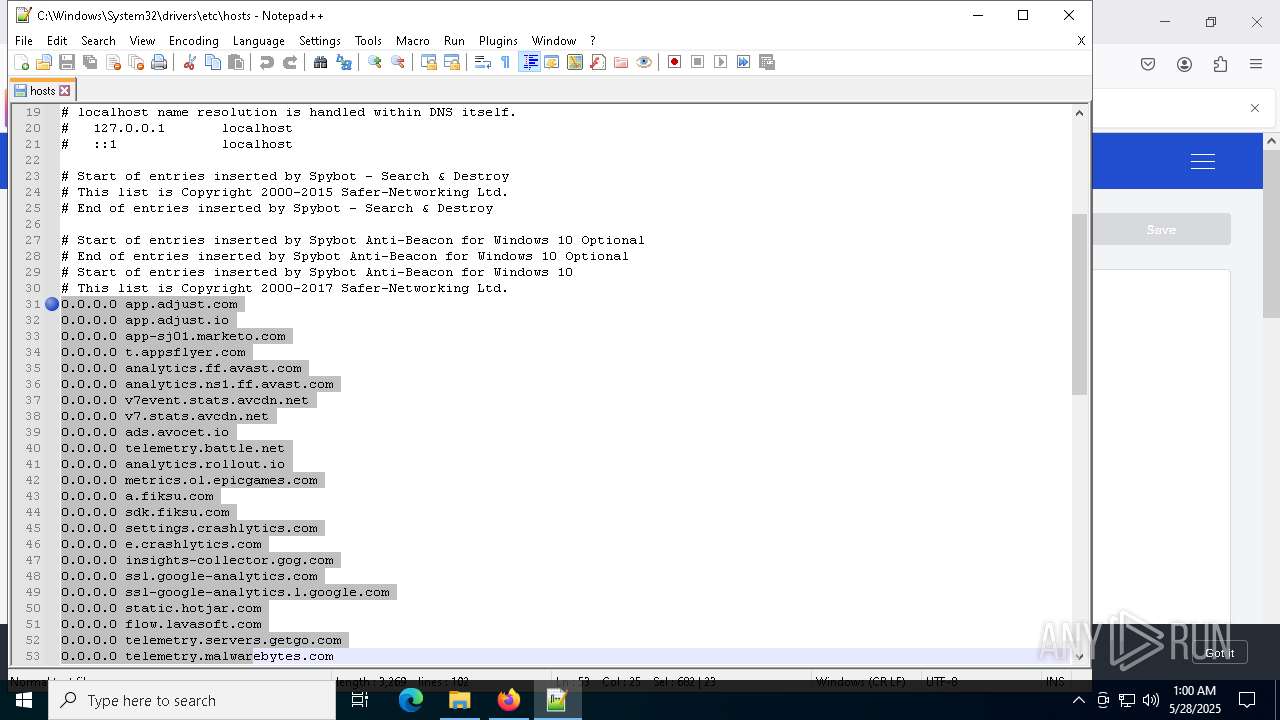
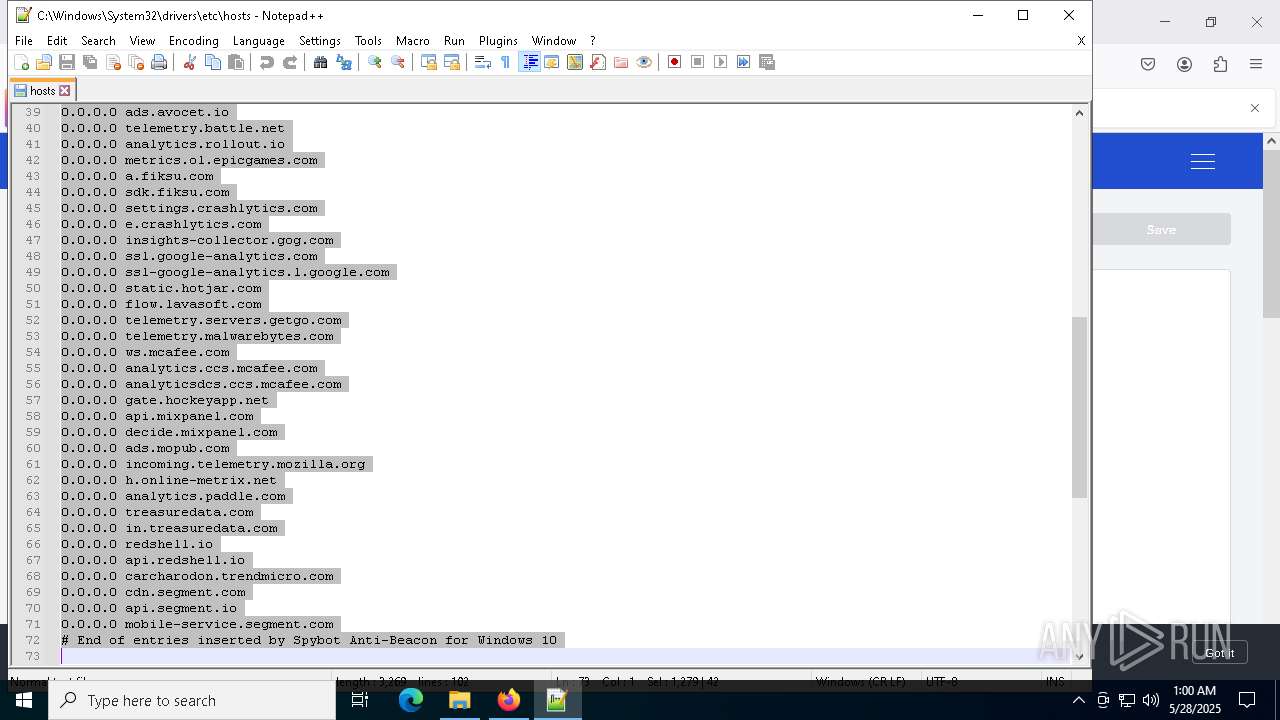
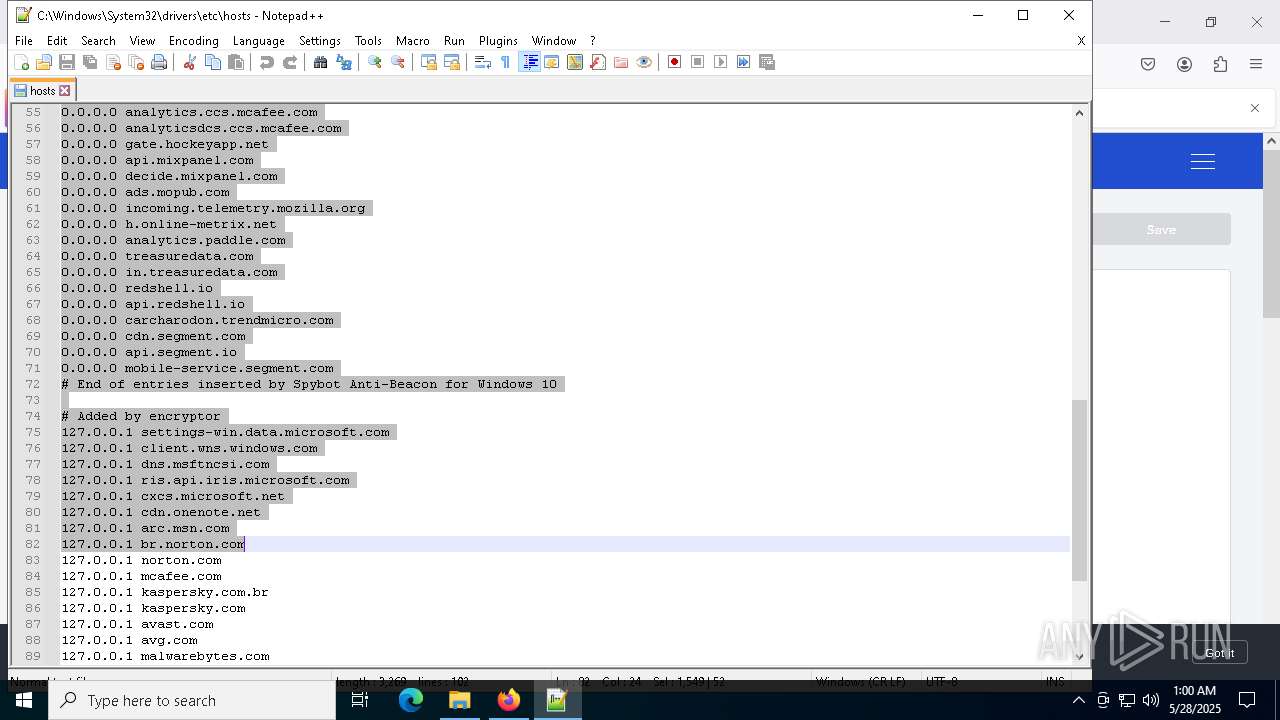
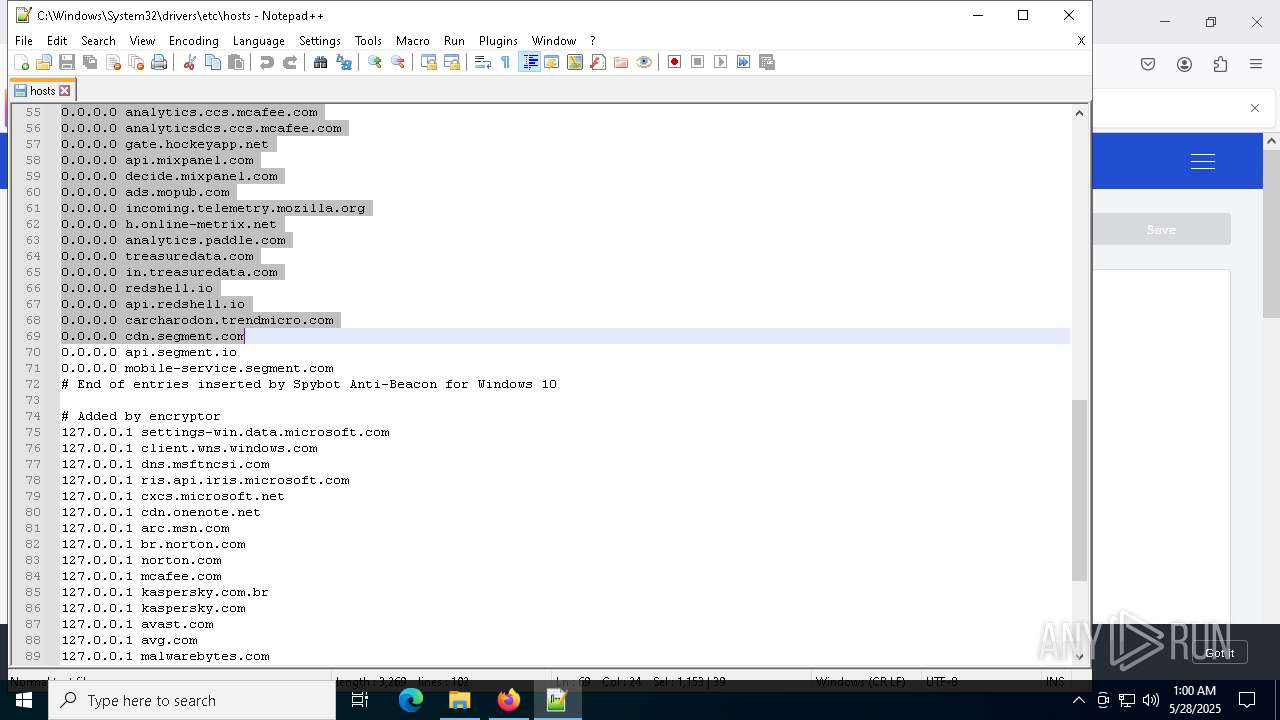
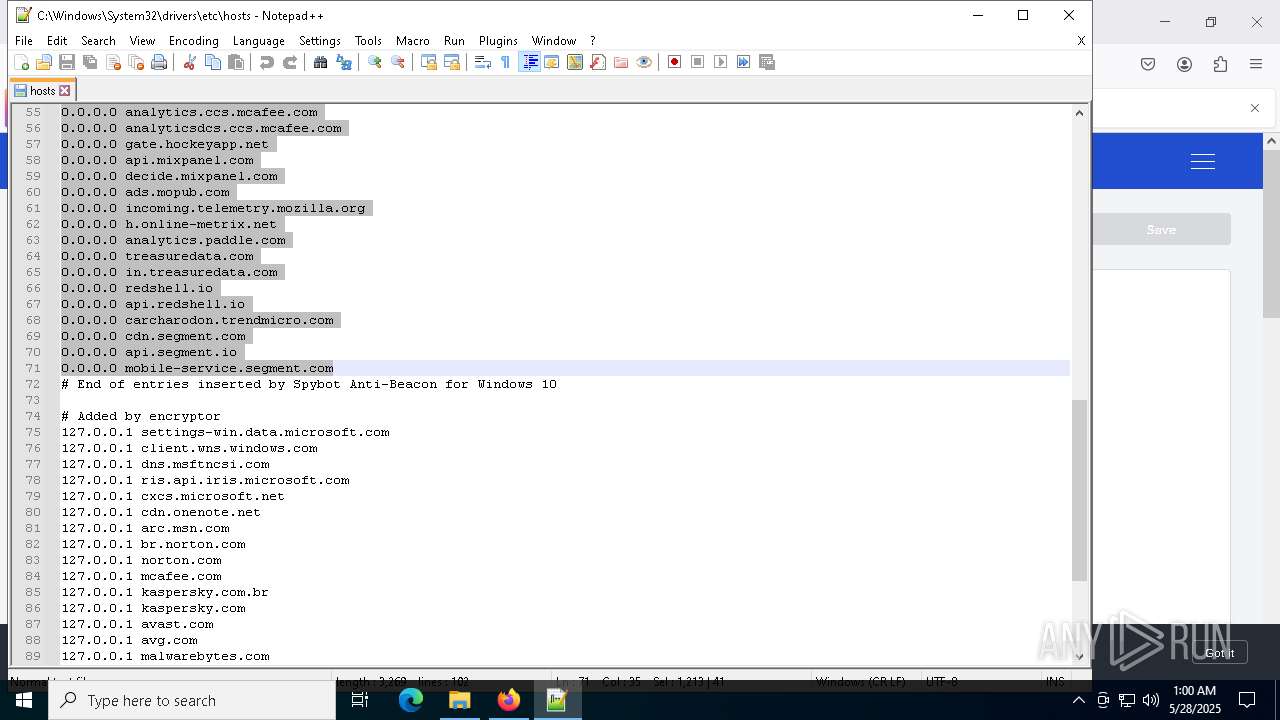
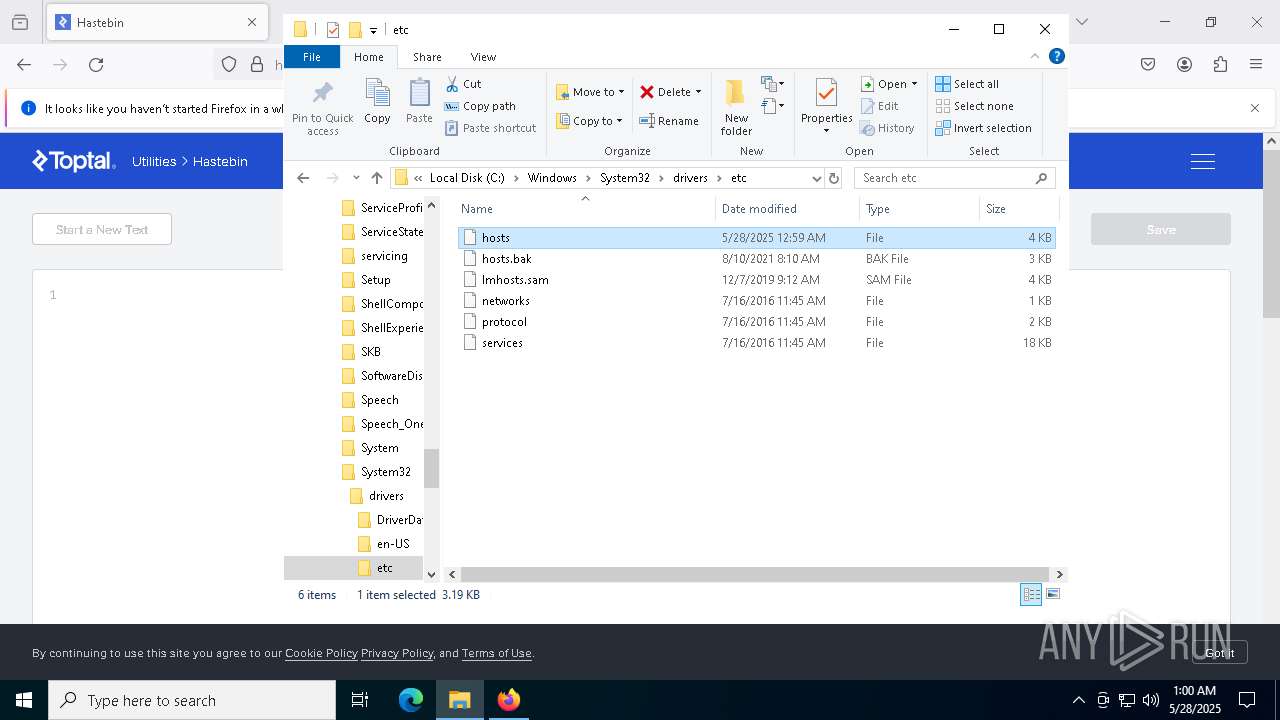
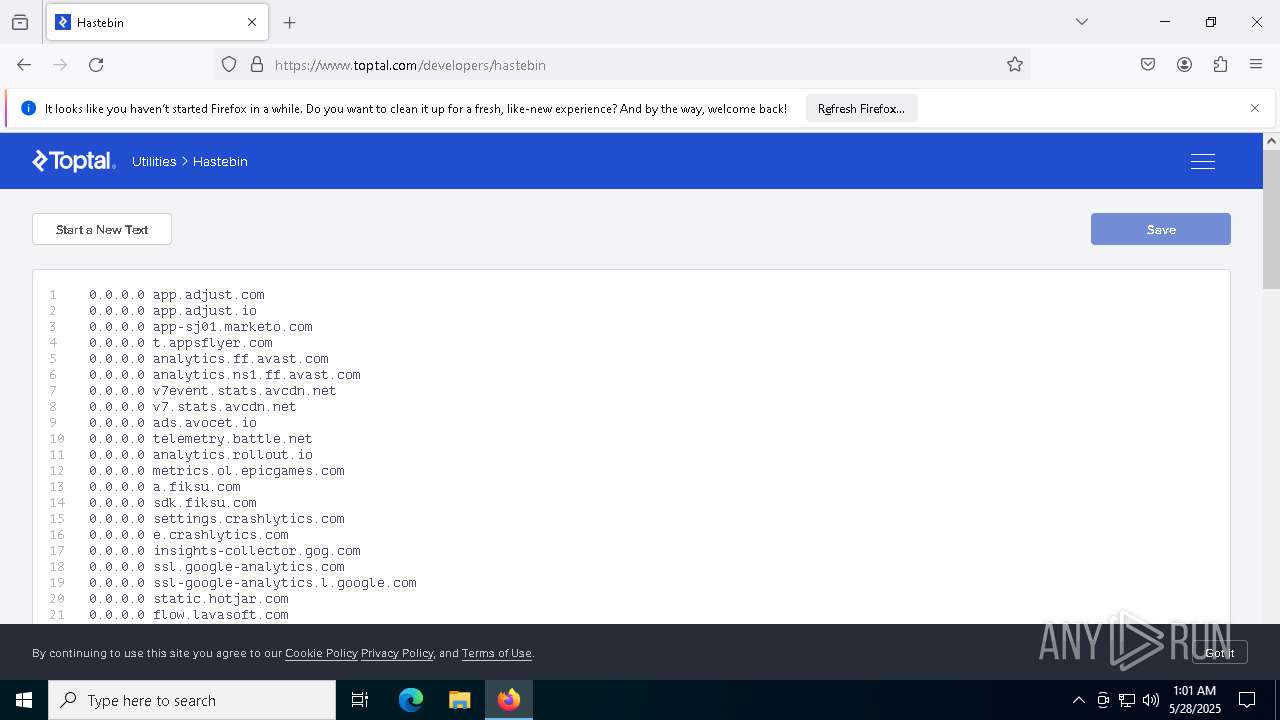
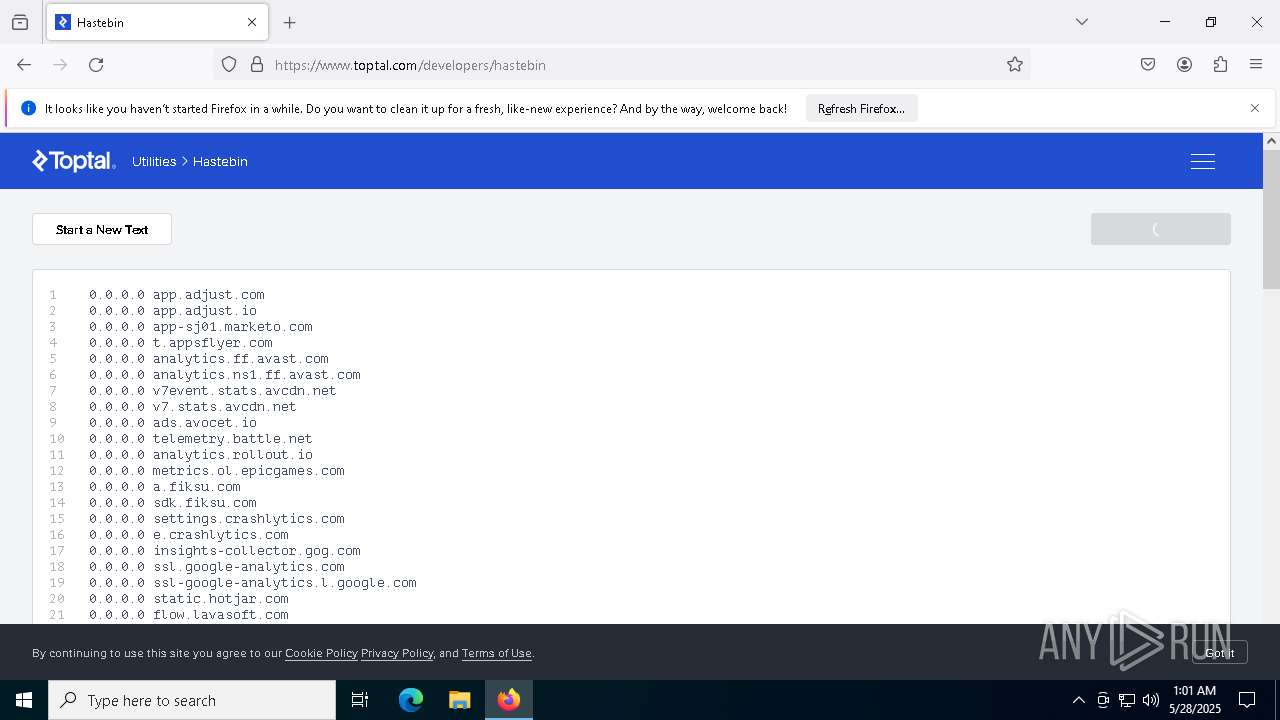
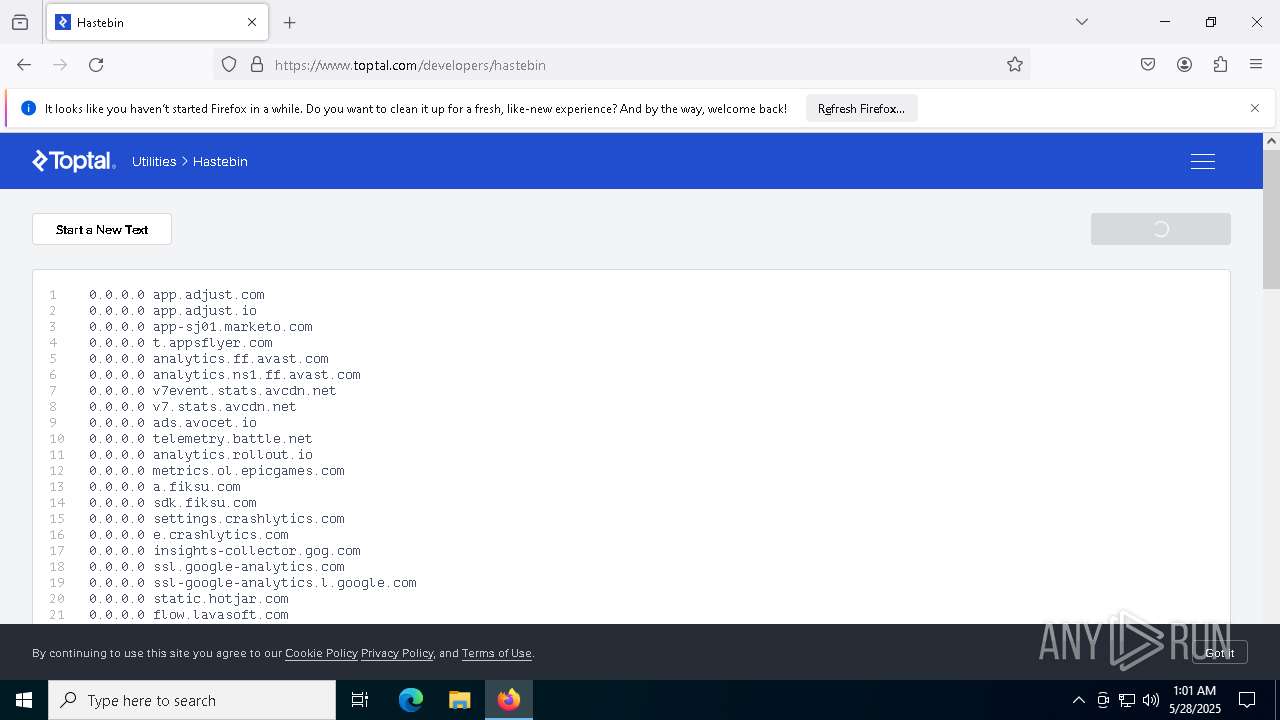
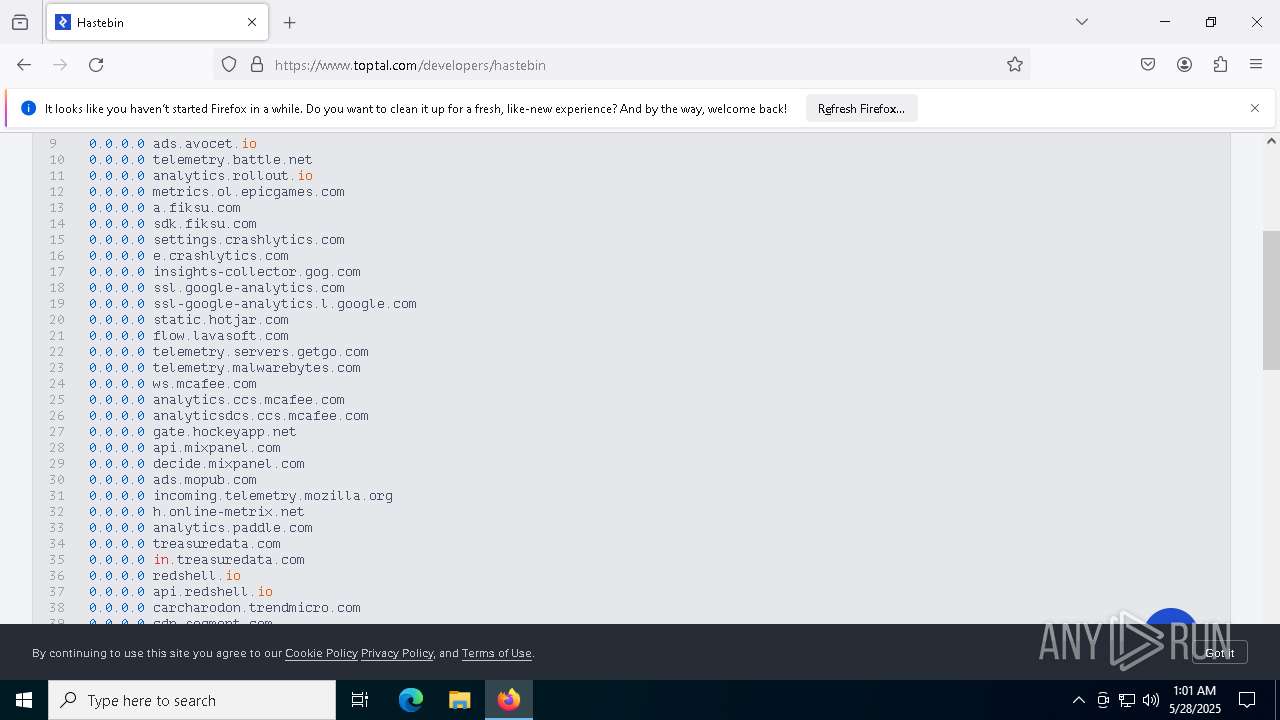
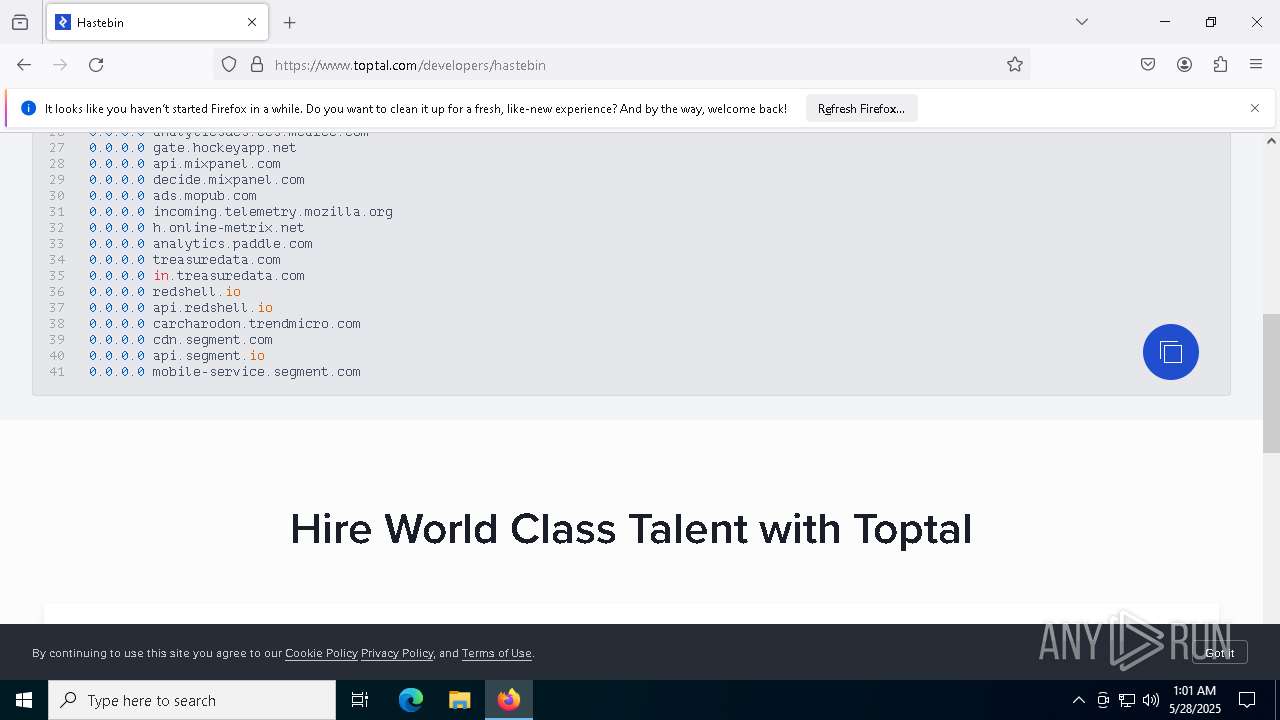
Modifies hosts file to alter network resolution
- encryptor.exe (PID: 1072)
Loads Python modules
- encryptor.exe (PID: 1072)
Creates files in the driver directory
- encryptor.exe (PID: 1072)
Application launched itself
- encryptor.exe (PID: 6728)
Starts CMD.EXE for commands execution
- encryptor.exe (PID: 1072)
INFO
Checks supported languages
- encryptor.exe (PID: 6728)
- encryptor.exe (PID: 1072)
Reads the computer name
- encryptor.exe (PID: 6728)
- encryptor.exe (PID: 1072)
Create files in a temporary directory
- encryptor.exe (PID: 6728)
- encryptor.exe (PID: 1072)
Checks operating system version
- encryptor.exe (PID: 1072)
Application launched itself
- firefox.exe (PID: 6516)
- firefox.exe (PID: 4920)
Reads the software policy settings
- slui.exe (PID: 6744)
- slui.exe (PID: 5212)
Checks proxy server information
- slui.exe (PID: 5212)
Manual execution by a user
- notepad++.exe (PID: 6032)
- firefox.exe (PID: 6516)
The sample compiled with english language support
- encryptor.exe (PID: 6728)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:05:28 00:52:47+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 178688 |
| InitializedDataSize: | 153600 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc380 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
154
Monitored processes
25
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1072 | "C:\Users\admin\AppData\Local\Temp\encryptor.exe" | C:\Users\admin\AppData\Local\Temp\encryptor.exe | — | encryptor.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4024 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4320 -childID 2 -isForBrowser -prefsHandle 4312 -prefMapHandle 4308 -prefsLen 36588 -prefMapSize 244583 -jsInitHandle 1544 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {afc9f45b-2df7-4459-8eda-85f53143cb46} 4920 "\\.\pipe\gecko-crash-server-pipe.4920" 215a48e9a10 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 4068 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2764 -childID 1 -isForBrowser -prefsHandle 2780 -prefMapHandle 2724 -prefsLen 31447 -prefMapSize 244583 -jsInitHandle 1544 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {040f140f-a313-45e2-95a2-16892c1b0dcf} 4920 "\\.\pipe\gecko-crash-server-pipe.4920" 215a249ef50 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 4448 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2144 -parentBuildID 20240213221259 -prefsHandle 2136 -prefMapHandle 2132 -prefsLen 31031 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {5b9e9c8a-9f33-49d0-a1c5-299f626cd6fe} 4920 "\\.\pipe\gecko-crash-server-pipe.4920" 2159087f510 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 4896 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1900 -parentBuildID 20240213221259 -prefsHandle 1840 -prefMapHandle 1832 -prefsLen 31031 -prefMapSize 244583 -appDir "C:\Program Files\Mozilla Firefox\browser" - {2af1bb79-f298-45f4-9922-f3ddce77f05e} 4920 "\\.\pipe\gecko-crash-server-pipe.4920" 2159d7eab10 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 4920 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 5212 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5352 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | encryptor.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5404 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
16 502
Read events
16 501
Write events
1
Delete events
0
Modification events
| (PID) Process: | (4920) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
Executable files
118
Suspicious files
200
Text files
49
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6728 | encryptor.exe | C:\Users\admin\AppData\Local\Temp\_MEI67282\Crypto\Cipher\_pkcs1_decode.pyd | executable | |
MD5:68FD499C14CDDA49C5460E377410C30E | SHA256:48958204C0CC8412758C33FB4A970C87A83BE5A8A889959FE8831793D8102E06 | |||
| 6728 | encryptor.exe | C:\Users\admin\AppData\Local\Temp\_MEI67282\Crypto\Cipher\_ARC4.pyd | executable | |
MD5:ABA0195EB33D86216170DCFF947DEBDB | SHA256:1F588A0D71C5378987FE05224493D85E93D02A52CE0B05809A06FC2BD489C325 | |||
| 6728 | encryptor.exe | C:\Users\admin\AppData\Local\Temp\_MEI67282\Crypto\Cipher\_raw_cast.pyd | executable | |
MD5:07D25B197C0E35BFD3C96550C5C64A6D | SHA256:FEFFAED6DBF10D4359DE74F6DA88C03C6A6B50D1568C5330343927E7797E3EC1 | |||
| 6728 | encryptor.exe | C:\Users\admin\AppData\Local\Temp\_MEI67282\Crypto\Cipher\_raw_cfb.pyd | executable | |
MD5:0DCA79C062F2F800132CF1748A8E147F | SHA256:2A63E504C8AA4D291BBD8108F26EECDE3DCD9BFBA579AE80B777FF6DFEC5E922 | |||
| 6728 | encryptor.exe | C:\Users\admin\AppData\Local\Temp\_MEI67282\Crypto\Cipher\_raw_ocb.pyd | executable | |
MD5:759AA7FF756F6EB615AB4890DEDD113D | SHA256:242B35BF5918BD1CBA69FEAAD47CBB50431D750EDCA6033875983E5FD4D9499C | |||
| 6728 | encryptor.exe | C:\Users\admin\AppData\Local\Temp\_MEI67282\Crypto\Cipher\_raw_des3.pyd | executable | |
MD5:DDBE90EDE6A159167987500E1F1FA56F | SHA256:77B8C96A7880961397D8B201F26D5C1608114FDDF9012614378472615D9F8CCE | |||
| 6728 | encryptor.exe | C:\Users\admin\AppData\Local\Temp\_MEI67282\Crypto\Cipher\_raw_blowfish.pyd | executable | |
MD5:AAF446AAF23C92FAD7D41B82DAA6F03C | SHA256:0432E9CF535C5C50DFA6776777BA89A2076BBF2DC6DB0EFA6C84483F501B00E3 | |||
| 6728 | encryptor.exe | C:\Users\admin\AppData\Local\Temp\_MEI67282\Crypto\Cipher\_raw_aesni.pyd | executable | |
MD5:0BA521EBCF0851B1283DC25766490460 | SHA256:782CB833FA04DAFA51BF1CB8CC811D71C9C6598208EED046EF5D8294E3651818 | |||
| 6728 | encryptor.exe | C:\Users\admin\AppData\Local\Temp\_MEI67282\Crypto\Cipher\_raw_arc2.pyd | executable | |
MD5:75A2D9A48DF773694E82534635BE7B9C | SHA256:B8D36C0ED8C994ED11F36B2ABC7D3C5116C215719BDC19C9596BB9E3FB811A4B | |||
| 6728 | encryptor.exe | C:\Users\admin\AppData\Local\Temp\_MEI67282\Crypto\Cipher\_raw_ctr.pyd | executable | |
MD5:785F15DC9E505ED828356D978009ECCE | SHA256:B2B68DE1D7E5997EB0C8A44C9F2EB958DE39B53DB8D77A51A84F1D1B197B58B1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
44
TCP/UDP connections
113
DNS requests
136
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4920 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4920 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
4920 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
4920 | firefox.exe | POST | 200 | 2.16.206.143:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.63.118.230:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4920 | firefox.exe | POST | 200 | 2.16.206.143:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
4920 | firefox.exe | POST | — | 142.250.185.163:80 | http://o.pki.goog/s/wr3/FIY | unknown | — | — | whitelisted |
4920 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://o.pki.goog/s/wr3/3H4 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 40.126.31.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 23.63.118.230:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4920 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
4920 | firefox.exe | 34.36.137.203:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
4920 | firefox.exe | 34.160.144.191:443 | content-signature-2.cdn.mozilla.net | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
example.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |